Scanguard is an antivirus company registered in Surrey, United Kingdom.
Its website claims it is trusted by millions of people around the world to secure their smartphones, tablets, lapto
While Scanguard’s website doesn’t give much information about the company and its history, a little digging into the legal terms of the website shows that Scanguard is owned by Protected.net, the same company that makes Total AV, a well-known brand in the antivirus sector.
Protected.net was established in 2016 and employs a team of 55 people. Its Total AV antivirus has been installed over 32,000,000 times worldwide.
In this review, I want to discuss how well Scanguard functions for the ordinary home PC user, as well as how effectively it protects them against malware and virus threats. I will also consider Scanguard’s all-around performance, features, customer support, and more.
This Scanguard review answers the following questions:
- What features do the programs offer?
- How much does Scanguard cost?
- How effective is Scanguard against malware?
- How does it affect PC performance?
- How easy is it to install and access support?
I looked at all of these things when I decided if Scanguard’s programs were worth recommending for the typical home PC user. If you want to know what I found out about Scanguard’s antivirus software, here is a quick summary before we go into the full review.
Scanguard review summary
Scanguard posted good speeds and doesn’t slow your device down. It also comes with some great features as part of the package. It’s good performance against common malware threats make it worth considering.
The downside? Scanguard failed to detect the lesser-known hidden threats when compared to competitors. This means you could be unprotected against new and intelligent online threats. Something to keep in mind if you subscribe.
TRY OUR TOP-RATED ANTIVIRUS RISK-FREE
Norton is our highest-rated antivirus software and is offering a completely free 7-day trial. This is a great way to try the service before subscribing.
After your trial, you can get huge discounts including up 83% off your first year of Norton Antivirus Plus.
Pros
- Password vault
- Data breach alerts
- VPN
Cons
- Limited product range
- Subscription only protects three devices
- Missed some hidden malware in independent tests
What’s new in the latest version of Scanguard?
Scanguard doesn’t publish release notes or a changelog so it’s not easy to find details on recent changes to the software or the features list. However, Scanguard does regularly update its database to protect users from the latest threats, and any new malware signatures that have been discovered.
How to get the latest version of Scanguard
If you already have an older version of Scanguard, you should be able to use the UI’s interface to get the new one. We recommend uninstalling Scanguard and reinstalling it with the new version if the update doesn’t show up in your product dashboard.
What versions of the software are available?
Scanguard Free Antivirus
The free version of Scanguard lets you find and remove all types of viruses and malware on your PC, but it doesn’t provide real-time protection to prevent the download of malicious files – you have to upgrade to the paid version for that. The free version is available for Windows, Mac, and Android operating systems and has a number of features on top of the antivirus scanner itself.
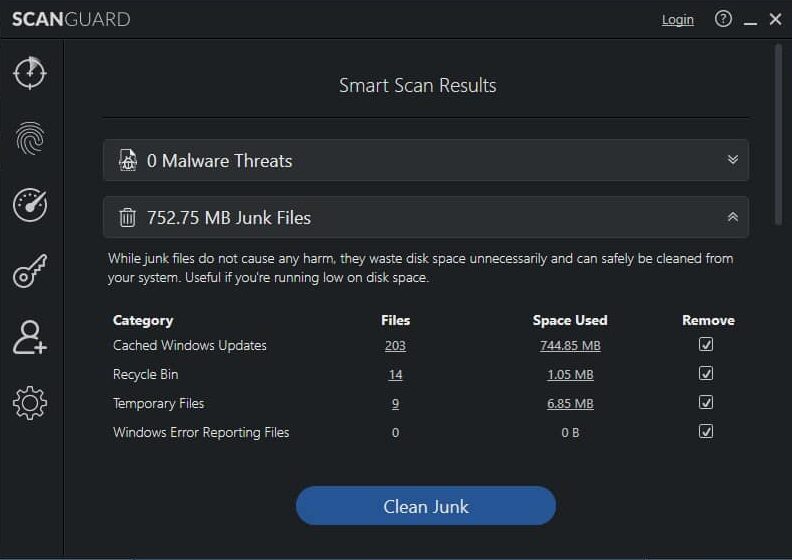
The features include phishing protection, data breach notifications, anti spyware tools, and an advanced web shield. It also offers a PC junk cleaner to speed up your device, as well as a browser cleaner and a tool to eliminate tracking cookies.
The free version does feature a lot of adverts to try and get you to upgrade to the paid version, which can be annoying.
Scanguard Essential Antivirus
Scanguard Essential Antivirus has all of the capabilities of the free version, and it also includes real-time scanning to provide additional protection against malware. There’s also a Safe Password Vault that lets you safely store all your passwords in one place.
There’s a Disk Cleaner that identifies and reclaims your valuable disc space that is currently being used by unnecessary files, plus System Tune-Up Optimization tools to identify any potential areas that could lead to your devices performing better and lasting longer. There’s also a web browser cleaner to improve both security and speed. Android Protection secures your smartphone with on the go protection for all your devices.
The mobile version has a VPN built into the app, plus an App Lock feature so you can make sure only the people you want can access the apps on your phone. This is good for parental use or for messaging apps for example. Finally, the paid for versions also come with 24/7 support via email, live-chat and a toll-free phone line.
Is Scanguard Antivirus effective against malware?
Malware includes viruses, trojans, and worms, so you need a solution that can eliminate them before they do major harm to your system.
Real-time scanning tests
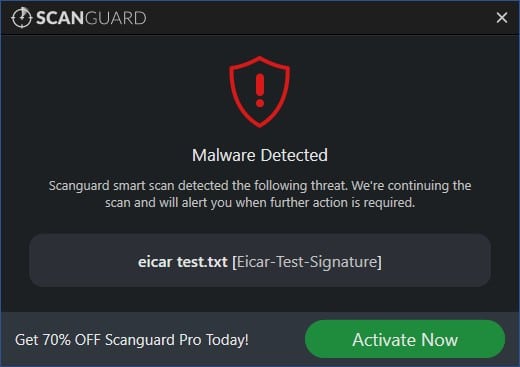
I’ll test Scanguard’s detection and removal rate using EICAR example files. I want the real-time scanner to detect the threats and stop them from being downloaded. These four example files simulate various viral risks.
The first file is an ASCII string. I copy this content, paste it into Wordpad, then save it to see whether the malware scanner discovers anything. The second file, eicar.com.txt, is a duplicate of the first. The third and fourth are archived in a zip folder, which is a good test to see how deep the scanner looks at files.
Scanguard’s results are summarized below:
| No value | Scanguard |
| Website | scanguard.com | Eicar Sample 1 | Allowed | Eicar Sample 2 | Blocked | Eicar Sample 3 | Blocked | Eicar Sample 4 | Blocked |
|---|---|
| Best deal (per month) | $2.49 SAVE 80% on a 1 year plan |
This table shows that Scanguard permitted the first EICAR file (the ASC11 string file copied to Wordpad), but it detected the other three EICAR files, even those within the zip folders.
I tested the software’s real-time scanner against several live malware files to see how well it worked. These live trials include potentially dangerous software such as trojans and adware. Scanguard blocked the two trojan files and one adware file I attempted to download, quarantining the malware swiftly.
The following table illustrates how it performed:
| No value | Scanguard |
| Website | scanguard.com | Live Sample 1 (Adware) | Blocked | Live Sample 2 (Trojan) | Blocked | Live Sample 3 (Trojan) | Blocked |
|---|---|
| Best deal (per month) | $2.49 SAVE 80% on a 1 year plan |
In my experiments, the Scanguard real-time scanner performed pretty well.
On-demand scanning tests
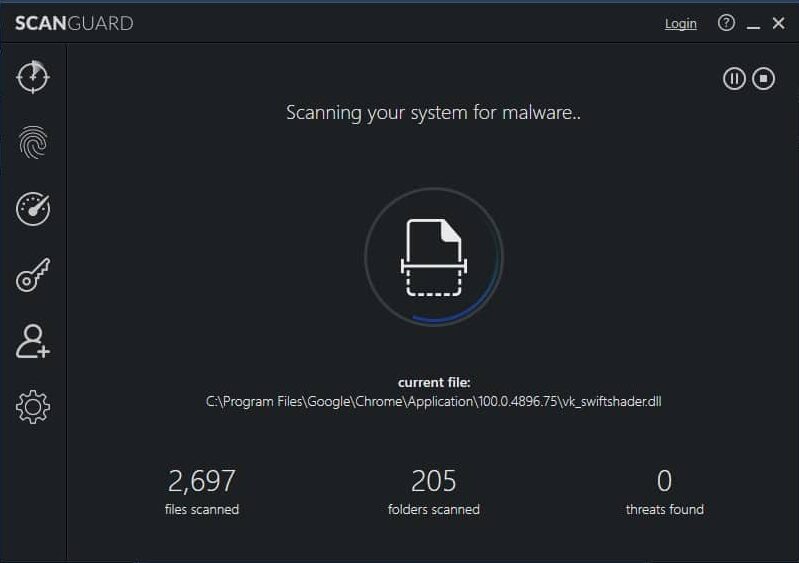
Next, I wanted to see how successfully the Scanguard suite’s on-demand scanner handled virus and malware files. I tested both the quick scan and full scan feature. The quick scan took 42 seconds to complete and found no test files, but that isn’t unusual.
Next, I ran the full scan for 12 minutes and found all seven malware files (four EICAR files and three live malware files).
The Scanguard interface disclosed how many files and how many folders were checked during the scan. 234,791 files were checked during its full scan, which is not as many as some other providers I’ve tested, but the scan was also faster to resolve than most other AV programs.
The table below compares the length of time of a full scan against many other providers I’ve tested.
| No value | Kaspersky | McAfee | Norton | Bitdefender | Scanguard | McAfee |
| Website | kaspersky.com | mcafee.com | Norton.com | Bitdefender.com | scanguard.com | mcafee.com | Full Scan Time (minutes) | 227 | 223 | 121 | 110 | 12 | 223 | Number of scanned objects | 2100000 | 785000 | 1,420,276 | 4200000 | 234791 | 785000 |
|---|---|---|---|---|---|---|
| Best deal (per month) | $2.49 GET 70% OFF | $3.33 SAVE $80 on a 2 year plan - 5 devices | $2.08 GET 73% off the first year! | $4.16 Get 50% OFF! | $2.49 SAVE 80% on a 1 year plan | $3.33 SAVE $80 on a 2 year plan - 5 devices |
Independent lab testing results
I want to see the latest results from leading independent test labs. I usually look at the popular tests run by AV-Comparatives and AV-Test to compare the results to my own test data. As Scanguard is yet to be tested by either lab, I will instead look to another well-known lab Virus Bulletin to see how Scanguad has done against a much larger set of samples than I can check in my own testing.
The latest VB100 test available for Scanguard is from February 2022.
In the VB100 test, Scanguard (run on Windows 10) was put against various malware samples between February 3 and February 4, 2022. It was also put up against a number of common and lesser known programs to test how many false positives it registered. A false positive occurs when antivirus blocks safe files by mistakenly marking them as dangerous.
The testing procedure contains test case sets that are updated on a regular basis to accommodate newly obtained samples. There are many subsets of test cases in a test case set:
Certification Set: A common and ubiquitous Windows malware that has been recently found. The size of the set varies, but it typically includes 1,000 to 2,000 entirely Microsoft PE (Portable Executable) file examples.
Clean Set: Legitimate application files that are generally and less extensively utilized. This collection comprises 100,000 samples chosen at random from a much bigger library of samples. This collection contains both PE (at least 25%) and other file formats.
Diversity Set: A collection of malicious Windows executables, encompassing less obvious examples and more hidden threats. Predominantly of the PE kind. Typically, 1,000 samples are chosen at random from a bigger library.
In the tests Scanguard performed well blocking 100 percent of the Certification Set of malware. In the clean set again Scanguard did very well scoring a perfect result with zero false positives found. In the final data set Scanguard scored a result of 85.09 detection rate against the more random and hidden threats included in the Diversity set.
As a quick comparison I checked a couple of other recent VB 100 reports for some rival antivirus products. I looked at AVG, Avast, and Emsisoft and all three of the programs detected 99.90 percent of the diversity set of malware.
This suggests while Scanguard did perform well, it might not do as well as some leading brands when it comes to less obvious and more hidden malware threats.
Scanguard features
Scanguard has a wealth of features. Below is a list of the most notable privacy tools that come with a Scanguard subscription.
Safe browsing (VPN)
When visiting the web, using a VPN can help you stay safe and keep your data private. Your IP address is hidden by the VPN and can’t be spied on as it is encrypted and rerouted via a global network of secure servers.
As a bonus, you will be able to access your home media material from all over the globe, circumventing geo restrictions (certain content may be blocked in some areas). Using a VPN gives you access to your favorite websites no matter where you are.
The Scanguard Superfast VPN service provides access to over 100 servers across six continents and can be used on a laptop, desktop computer, smartphone, or tablet.
Safe site web extension
The Safe Site web plugin, which works with Chrome, Firefox, Edge, and Safari browsers, helps prevent potentially malicious or fraudulent websites from affecting your system.
Because of Safe Site’s massive database of dangerous URLs, if you inadvertently try to visit a dangerous site, you will be safely redirected away and notified of the risk, letting you browse with confidence.
Performance features
Keeping your system optimized is critical if you want to get the most out of your gadgets. We all want our computers, phones, and tablets to be as quick as they were when we first bought them. Scanguard promises to have a variety of performance capabilities that may help you reclaim the gadget you love if it is acting sluggishly.
- Battery Monitor: Increase battery life by shutting off unnecessary processes and programs that are operating in the background.
- System Optimization Scan: Identifies any possible locations where your device could perform better and last longer.
- Browser Manager: Keeping your browsers clean can improve productivity, eliminate unwanted advertising, and help you avoid fraud.
- Disc Cleaner Pro: Assists you in identifying and reclaiming important disc space that is presently being used up by unneeded files.
What is Scanguard’s impact on performance?
I performed a fast scan and a thorough scan on my computer to see how much the antivirus application impacted PC performance. While I ran the quick scan and full scan, I used the Windows resource monitor to see how much of the system’s resources were being used. This allowed me to see the effect on CPU, RAM, and disk usage when the quick scan and full scan were running.
The control values in the table below indicate how much system resource was used before the scan was initiated, as well as how much was used throughout the rapid scan.
| No value | Scanguard |
| Website | scanguard.com | Control CPU Utliization % (no scan) | 6 | Control Memory Utilization % (no scan) | N/A | Control Disk Utilization (seconds) (no scan) | 4 | Quick Scan Time (seconds) | 42 | Quick Scan Memory Utilization % | N/A | Quick Scan Disk Utilization (seconds) | 607 |
|---|---|
| Best deal (per month) | $2.49 SAVE 80% on a 1 year plan |
As we can see, the CPU utilization pre scan was six percent and increased to 53 percent during the quick scan, while at the same time disk utilization increased substantially from 4 MB/s before the scan to 607 MB/s during the quickscan.
Memory consumption was not captured by the Windows performance tool on the remote server I utilized for this test. The short scan only took 42 seconds, so it shouldn’t have a big effect on the user.
Scanguard’s rapid scan duration seems shorter in length compared to other leading antivirus programs like Norton and Bitdefender.
| No value | Kaspersky | Norton | ESET | Bitdefender | Avast | McAfee | Scanguard |
| Website | kaspersky.com | Norton.com | eset.com | Bitdefender.com | avast.com | mcafee.com | scanguard.com | Quick Scan Time (seconds) | 273 | 171 | N/A | 338 | 64 | 633 | 42 |
|---|---|---|---|---|---|---|---|
| Best deal (per month) | $2.49 GET 70% OFF | $2.08 GET 73% off the first year! | $4.99 50% off all ESET Home Security products! | $4.16 Get 50% OFF! | $2.10 Holiday SALE! Save up to 65% | $3.33 SAVE $80 on a 2 year plan - 5 devices | $2.49 SAVE 80% on a 1 year plan |
Full scan
Next I ‘ll consider how the complete on-demand scan affected my computer’s speed. The table below displays the results before and after Scanguard’s thorough system check.
| No value | Scanguard |
| Website | scanguard.com | Full Scan CPU Utilization % | 46 | Full Scan Disk Utilization (seconds) | 547 | Full Scan Time (minutes) | 12 | Control CPU Utliization % (no scan) | 6 | Control Disk Utilization (seconds) (no scan) | 4 |
|---|---|
| Best deal (per month) | $2.49 SAVE 80% on a 1 year plan |
As we can see, the CPU utilization increased from 6 percent to 46 percent during the full scan, while disk utilization jumped from 4 MB/s to 547 MB/s.
During the 12 minute scan, users may notice a slowdown in tasks like downloading and installing programs or opening files while the scan is running in the background.
As with the malware protection tests, I would usually look at the results of the independent AV testing labs to see if the results were in line with my own test data. VB Bulletin does not run performance tests and Scanguard has not been tested by AV-Comparatives or AV-Test.
To add to the results recorded above I launched a couple of video streams and tested web browser and download performance for any discernible slow down of my PC. I noted that while Scanguard was running there was some impact on streaming quality on my device.
Is the interface easy to use?
The design and layout of Scanguard’s user interface are quite typical for a contemporary UI, and it is both practical and straightforward to use. Main features and crucial information are clearly stated in the main panel, and a list of other tools is accessible in a list along the left hand side, each with its own icon, which may be accessed by clicking on the icon. Using the user interface, you may do a quick, full, or custom scan, and you can also perform product updates and check that you are running the most current version of the application. If you are currently using the free version or the Pro version, you may also upgrade by selecting the appropriate link on the dashboard.
You will also get a clear notification from the user interface informing you if your system is secure or not, and whether you need to take any action to fix the situation.
Scanguard customer support
Scanguard has a really good FAQ with lots of helpful articles for each product clearly divided into separate sections for billing support and technical product support. There’s also video tutorials. You can also email support with any questions you have via a contact form on the website.
Scanguard provides a live chat function that lets you talk with a human representative. While there’s no mention of a phone number for technical assistance on the support pages, at least you can speak to a real person via the webchat.
The checkout process with Scanguard is simple, however it does require you to put in your email address before you can even get to the checkout area and see how much the product costs. It feels like a slight invasion of privacy and once you enter your email you do get the inevitable sales emails arriving from Scanguard over the coming days and weeks. Scanguard (and TotalAV, also owned by Protected.net) are the only AV products I’ve checked out that use this type of tactic, and I find it a bit off putting.
Once you do get to the checkout it’s quick to pay and download the installer file and the page is very clear about the subscription. It shows you the first year discount making it clear that the subscription rebills at the full price each subsequent year unless you cancel.
Compatibility
Scanguard is available on all major platforms including Android, Windows and Mac. Scanguard also needs an active internet connection to keep current with the most recent threat detection. In fact the first task the program runs after install is to connect to the internet and download the latest virus definitions before it runs a first scan of your system.
Windows system requirements
Operating system:
Microsoft Windows 7 Service Pack 1 or higher with the newest updates, hotfixes, and service packs installed
Memory:
2 GB of RAM or more
Disk space:
Minimum 1.5 GB of free disk space (additional space for temporary and quarantine files needed)
CPU:
Intel Pentium 4 / AMD Athlon 64 Processor or faster
Browser:
Internet Explorer 11 or newer
Additional requirements:
To install Scanguard, administrator rights are required, as well as an internet connection. Automatic updates require an internet connection and are required for optimal virus detection.
Mac OS system requirements
Operating system:
Mac OS X 10.9 Mavericks and higher
Memory:
2 GB of RAM or more
Disk space:
Minimum 1.5 GB of free disk space (additional space for temporary and quarantine files needed)
CPU:
64-Bit Intel Core 2 Duo processor or higher
Browser:
Safari 6 or newer
Additional note: .
As of late-2019 Scanguard ceased support for OS X 10.8 Mountain Lion but offers a legacy app for OSX 10.6 – 10.8. Apple stopped providing security updates to 10.8 in 2015. It is strongly advisable to stop use of 10.8 and upgrade.
Android system requirements
Requires Android:
Android 5.0
Permissions:
- Device and App History
- Photos/Media/Files
- Storage
- Wi-Fi connection information
- Device ID & call information
- Bind to an accessibility service
- Delete other apps’ caches
- Update component usage statistics
- Receive data from the Internet
- View network connections
- Read battery statistics
- Pair with Bluetooth devices
- Delete all app cache data
- Full network access
- Close other apps
- Run at startup
- Control vibration
- Prevent device from sleeping
- Install shortcuts
Scanguard pricing
Scanguard Free
Scanguard offers free antivirus software that can be downloaded from the company website and free of charge. The free version only offers on-demand scanning and does not include real-time scanning capabilities.
Scanguard Essential Antivirus
Scanguard Antivirus Pro costs £119 (US$152.79) per year to protect three devices.
Scanguard offers huge first year discounts of 80 percent, and this reduces the cost for the first year of subscription to £23.00 (US$29.53).
Overall Scanguard offers a good number of features and the first year price is pretty tempting. The downside is that it only covers three devices per subscription and many households have far more devices to protect than that. It would be better if Scanguard offered a few more options so users could choose to dial up or dial down how many devices are protected.
Best Alternatives
If you need a new antivirus, compare multiple alternatives to discover the best fit for you. Below are some of the top Scanguard alternatives that balance pricing, malware protection, and security and privacy features.
McAfee: Recent lab findings give McAfee’s real-world threat protection a near-perfect score. It features a robust malware scanner and has done well in both my personal and third-party tests. Other features may help you increase your online security and privacy.
AVG: Effective and powerful antivirus with a robust suite of security tools mean AVG has an excellent price-to-feature ratio, which is something I look for when selecting a security solution.
Bitdefender: Bitdefender Total Security strikes a good mix between pricing, virus protection, and privacy features. Bitdefender also performed well in my tests and those of the most recognised third party testing labs.
Scanguard verdict
In this review, I found that Scanguard performed well in my tests and also in the VB100 testing, particularly in the malware and false alarm tests. Scanguard did score lower protection against uncommon and hidden malware compared to some of its rivals such as AVG and Emsisoft.
With a very good first year discount, reasonable speed and performance numbers, and good features like a VPN, Scanguard is worth considering. It also includes performance optimization tools which might be something some users want to speed up their devices.
If you want to go for the best protection against hidden and less obvious malware threats, you might want to look at an alternative solution.
Antivirus testing methodology
We’ve structured our antivirus testing methodology to provide reliable data on how effective the software is at malware protection and performance.
Our testing process includes:
- Scanning malware test samples from EICAR in real-time and on-demand
- Testing live malware samples including Adware and Trojans in real-time and on-demand
- Comparing our own tests with independent antivirus lab test results
- Measuring impact on PC performance
In addition, we measure a number of PC performance metrics and analyze pricing, ease of use, compatibility, and additional features.
If you’d like to know more about how we analyze antivirus software, we have a dedicated post on our antivirus research and testing methodology.