Zero Trust Architecture (ZTA) is a security model that assumes no one, whether inside or outside the network, can be trusted by default. Instead of relying on traditional perimeter-based defenses, Zero Trust focuses on strict verification processes for every user, device, and system attempting to access network resources.
The ZTA approach is built on the principle of “never trust, always verify,” meaning that every access request is treated as potentially harmful and must be authenticated, authorized, and continuously monitored before granting access to sensitive data or systems.
In the traditional security model, once a user or device is inside the network perimeter, they are often trusted to move freely across systems and applications. However, the increase in remote work, cloud computing, and mobile device usage has blurred the lines of the network perimeter, making it easier for attackers to gain unauthorized access to systems.
Zero Trust addresses these challenges by enforcing granular security measures at every point of access, ensuring that only the right individuals and devices are allowed access to specific resources at any given time. Important components of a Zero Trust Architecture include identity and access management (IAM), multi-factor authentication (MFA), continuous monitoring, micro-segmentation, and strict enforcement of least-privilege access policies.
ZTA components work together to minimize the risk of insider threats, data breaches, and unauthorized access. Implementing Zero Trust often involves a shift in the way organizations think about cybersecurity, requiring a comprehensive and proactive approach to protecting sensitive data and systems.
As organizations face increasingly sophisticated cyber threats, Zero Trust Architecture has emerged as a powerful framework to enhance security, improve compliance, and reduce the overall attack surface.
What is Zero Trust Architecture (ZTA)?
Zero Trust Architecture (ZTA), also known as Zero Trust Security Model, or Zero Trust Network Access (ZTNA), is a shift in approach to security whereby access is denied unless it is explicitly granted and the right to have access is continuously verified. The idea behind ZTA is that the network devices should not be trusted by default, even if they are connected to a corporate network or have been previously verified. The zero-trust approach advocates checking the identity and integrity of devices irrespective of location and providing access to applications and services based on the confidence of device identity and device health combined with user authentication.
ZTA reduces insider threat risks by consistently verifying users and validating devices before granting access to sensitive resources. For outside users, services are hidden on the public internet, protecting them from attackers, and access will be provided only after approval from their trust broker. According to Gartner, by 2022, 80% of new digital business applications will be accessed via ZTNA. The US National Institute of Standards and Technology (NIST) Special Publication NIST SP 800-207 provides detailed vendor-neutral guidelines and recommendations for public and private organizations looking to implement ZTA principles.
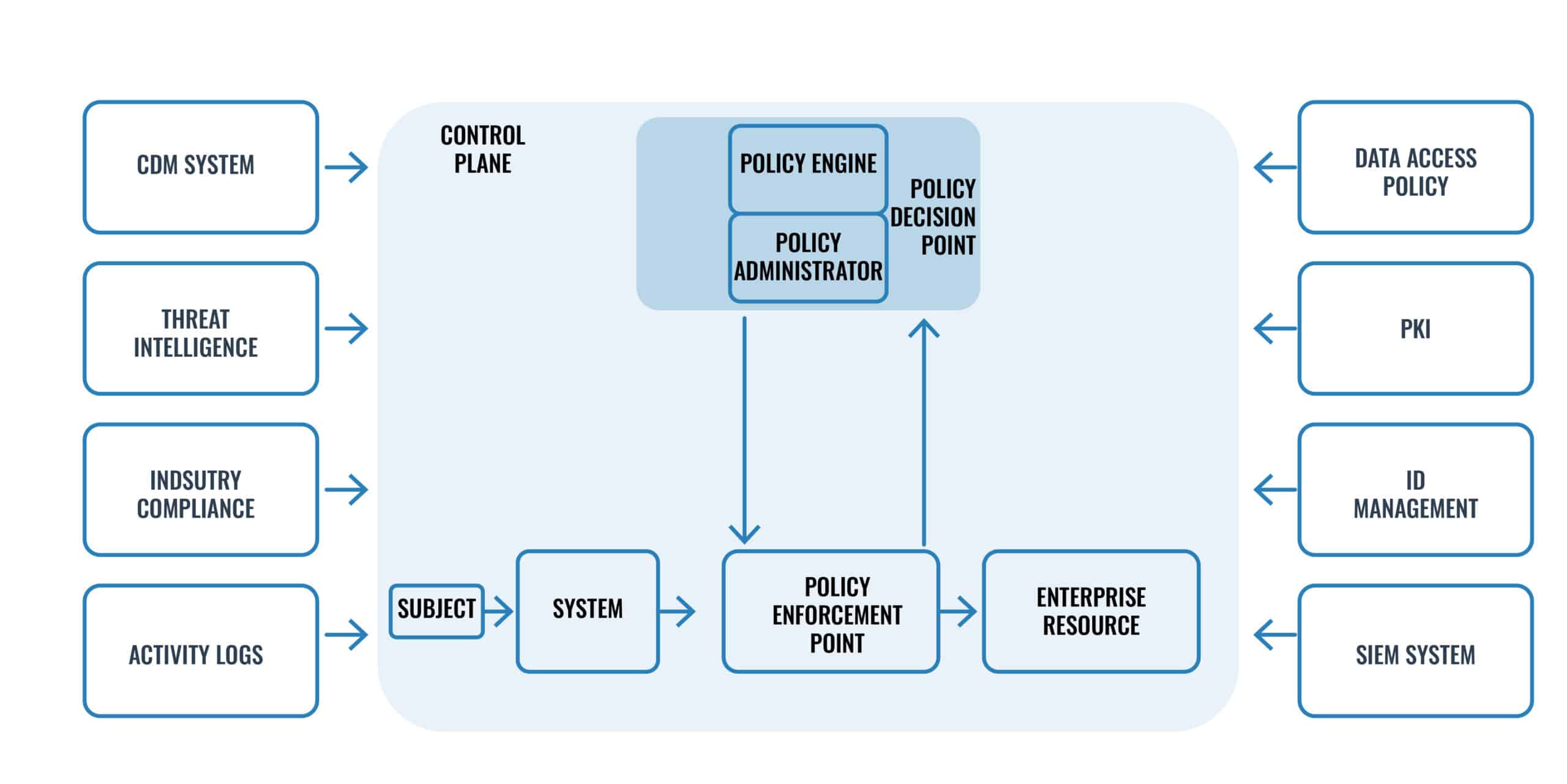
How Does Zero Trust Architecture Work?
ZTA works by bringing together various modern technologies that contribute one way or the other in fulfilling zero trust’s philosophy of “never trust, always verify”. The technologies include identity and access management (IAM), risk-based multi-factor authentication, next-generation endpoint security, next-generation firewall (NGFW), end-to-end encryption, and technologies that verify the health of assets and endpoints before they connect to applications, among others.
ZTA assumes any user, asset, or resource is untrustworthy and must be verified and continually evaluated for every session and activity before access is granted. This is a complete departure from the traditional network security model, which relied on the “trust but verify” principle. The conventional approach automatically trusted users and endpoints within the organization’s perimeter, putting the organization at risk from insider threat actors, allowing unauthorized and compromised accounts unrestrained access within the corporate network. This model became obsolete with the advent of cloud computing and the acceleration of a distributed work environment.
In ZTA, every attempt by a user or device to gain access to network resources must undergo strict identity verification. And this goes beyond the use of username and password and ID token for authentication. It must also include the who, what, where, when, why, and how parameters. This implies that the user, device used, location, time of day, the purpose of the access, and access privileges must be validated. Access may be rejected if any of those attributes are determined to fall outside of the acceptable use boundaries.
You can think of ZTA as similar to implementing physical access control to protect access to critical areas and locations in a building complex. So instead of having one access control device that authenticates users at the main gate or reception area, assume no one is trustworthy and have them installed at the entrance to an office, meeting room, server room, library, and other critical locations within the building to enforce strict access control. This, in a nutshell, explains how a ZTA works.
What are the Core Principles of the ZTA?
ZTA adopts certain core principles to prevent an attacker from moving across or within a network after gaining access to that network. A ZTA that implements those techniques can easily contain the lateral movement of malicious actors. Furthermore, the compromised device or user account can be quarantined and cut off from further access once the attacker’s presence is detected.
Core Principles of the ZTA
- Multi-factor authentication (MFA): MFA is a security technique in which a user is granted access to a system or network only after successfully presenting two or more pieces of evidence (authentication factor) to an authentication mechanism. ZTA utilizes this technique to reduce the incidence of identity theft.
- Least privilege access: This is a security concept in which a user is given only the minimum access or permissions needed to perform their job functions. ZTA utilizes this technique to limit “user blast radius” and exposure to sensitive parts of a network.
- Device access control: ZTA also requires strict rules on device access. It does this by monitoring the number of devices trying to access the network, ensuring that every device is authorized and meets the required health condition. In addition, ZTA utilizes this technique to limit “device blast radius” and exposure to sensitive parts of a network. This further minimizes the attack surface of the network.
- Microsegmentation: This security technique enables breaking up security perimeters into distinct security segments down to the individual workload level and then defining security controls and delivering services for each unique segment. ZTA utilizes this technique to ensure that a person or program with access to one of those segments will not access any of the other segments without separate authorization.
- Continuous monitoring and verification: This implies that no user or device (inside or outside) should be automatically trusted. ZTA verifies device and user identity and privileges and ensures that established sessions time out periodically, forcing devices and users to be continuously re-verified. For this to work effectively, risk-based conditional access ensures workflow is only interrupted when risk levels change must be in place. This provides continual verification, without sacrificing user experience.
When Should you Consider ZTA for Your Business?
You know your business is ripe for a zero trust model if the following scenarios apply to your organization:
- Your organization has a central headquarter and multiple remote offices and employees not joined by an enterprise-owned physical network connection. And because these offices and employees are remote, your organizations use cloud resources and applications to connect teams.
- Your organization hires outside help or gives third-party contractors, partners, and customers some level of access to corporate resources, internal applications, sensitive databases, services, or other protected assets.
- Your organization has IoT-based systems with massive amounts of data constantly collected from data sources such as connected cars, vehicles, ships, factory floors, roadways, farmlands, railways, etc., and transmitted to your cloud network.
- Your organization utilizes multiple cloud providers. It has a local network but uses two or more cloud service providers to host applications/services and data. And you are required to protect a network infrastructure that includes multi-cloud and cloud to cloud connections, hybrid, multi-identity, unmanaged devices, legacy systems, SaaS apps.
- Your organization needs to address a growing threat landscape that includes threats from malicious insiders, ransomware, supply chain attacks, among others.
If your organization is at this crossroad, this may be an excellent time to consider ZTA in your network. ZTA’s ability to accelerate awareness, prevent, detect, and respond to security events with minimal latency makes it the ideal security strategy to address those scenarios.
How do you Implement ZTA for Your Business?
So how should organizations go about applying the ZTA concepts to address their modern network reality? The NIST SP 800-207 framework on ZTA recommends that organizations seek to incrementally implement zero trust principles and technology solutions that protect their most valuable data assets instead of outrightly replacing infrastructure or processes at a go. Migration to a ZTA may not happen in a single technology refresh cycle. Instead, it should be seen as a journey. “Most enterprises will continue to operate in a hybrid zero-trust/perimeter-based mode for a period while continuing to invest in ongoing IT modernization initiatives”.
According to the NIST ZTA framework, “before undertaking an effort to bring ZTA to your organization, there should be a survey of assets, subjects, data flows, and workflows. This awareness forms the foundational state that must be reached before a ZTA deployment is possible”. The following is a five-step methodology for implementing ZTA in your organization. This will help you understand where you are in your implementation process and where to go next in a way that is cost-effective and non-disruptive.
Five-step methodology for implementing ZTA in your organization
- Define the protected surface: The first step is to define your protected surface by finding out what data is of value. With zero trust, you don’t focus on your attack surface but only on the critical data, applications, assets, and services most valuable for your organization (protected surface). Once defined, you can move your controls as close as possible to that protected surface to create a micro perimeter.
- Map transaction flows: The way traffic moves across a network determines how it should be protected. An enterprise cannot determine what new processes or systems need to be in place if there is no knowledge of the current state of operations. So the next step is to determine where the data is going, what it is being used for, and what it is doing. You do this by mapping the traffic flows of your data across your networks via your business applications. Once completed, you can apply ZTA to keep everything else out.
- Design your ZTA: Once you’ve defined the protected surface and mapped the data flow to know what should be allowed, you can then design a ZTA that enforces your network’s micro-perimeters. There’s no single, universal design for ZTA. Your ZTA is unique to your business and is constructed around the protected surface. Examples of technologies to consider at this stage include virtualization, next-generation firewall (NGFW), Software-Defined Perimeter (SDP), among others.
- Create your ZTA policy: Once the ZTA is designed, the next step is to create your ZTA policies to determine access. For example, you can adopt the who, what, where, when, why, and how concept to figure out who your users are, what applications they need to access, why they need access, and how they tend to connect to your applications. With this level of granular policy enforcement, you can be sure that only legitimate traffic will be allowed.
- Monitor and maintain your ZTA: Once your zero-trust network and policies are in place, you need to monitor everything for the sake of continuous improvement. The only way to know if there is a problem is by monitoring traffic across the entire infrastructure. This requires visibility into the network. Inspecting and logging all traffic will provide valuable insights into how to improve the network over time.
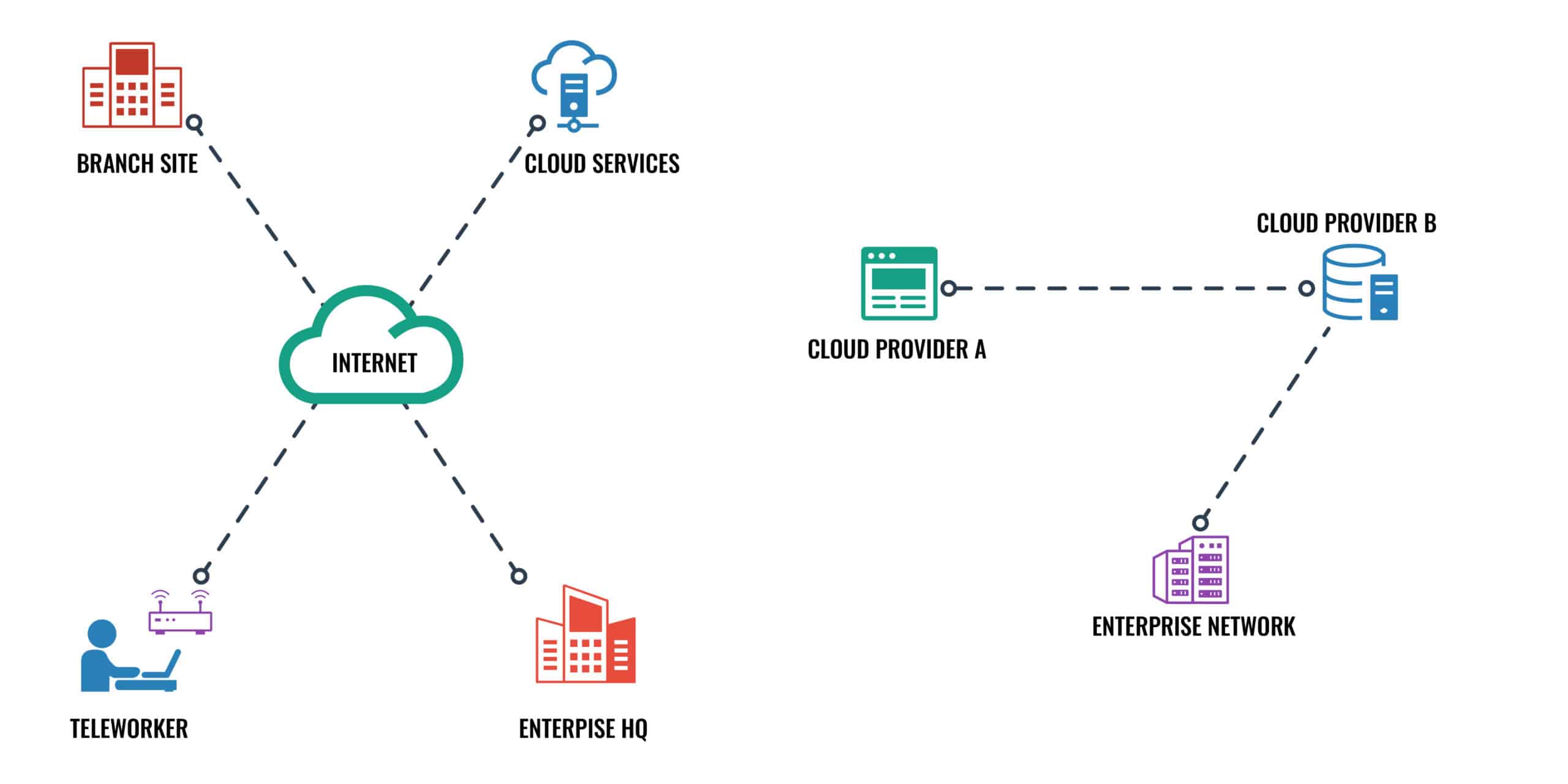
Choosing the Right ZTA solution for Your business
ZTA is not a single out-of-the-box product, and it’s certainly not a service. As you can deduce from this article, it means exactly what it says, zero trust–“never trust, always verify”. But there are a variety of ZTA vendors and solution providers out there, so choosing the right one for your business and budget can be challenging.
You need to consider various factors: Does the ZTA solution require an endpoint agent to be installed? Does the trust broker integrate with your existing identity provider? Is vendor NIST 800-207 compliant? Is vendor support available in your region, and to what extent? How geographically diverse are the vendor’s edge locations worldwide? What is the total cost of ownership? To help you wade through the noise, check out our piece on the seven best ZTA solutions for your business. Hopefully, this will guide you in the process of choosing the right one for your business.
Zero Trust Architecture FAQs
What is a zero trust architecture means?
Zero Trust encapsulates a security approach to the design of networks and services that expects both devices and users to be authenticated before being given access to company IT resources. This is a process that blocks intruders from progressing through a company network unnoticed and restricts users so that they are unable to represent a threat.
What are the three main concepts of Zero Trust?
The three main concepts of Zero Trust are:
- Trust – Access is usually granted to zones on a network that have been given a trust rating, for example, the internet has the lowest level of trust, a DMZ a slightly higher level, and the private internal network the highest level. In ZTA, trust isn’t allocated in zones. Every access event is a new challenge to trust, so, effectively, each resource is fenced and authentication has to be implemented before any access is granted.
- User authentication – Rather than providing a collection of assets in a zone to which a user can gain access, each individual asset represents a zone by itself. This is a concept called microsegmentation and it effectively means that each application (ie software package) is defended individually. Getting to that application also requires access to a network and the server that hosts the software and those assets also require user authentication. That means that every step in accessing a user-facing asset requires its own authentication process.
- Device authentication – Focusing security clearance only on users overlooks the current challenge of allowing users to access resources from their own devices. Even with company-owned devices, users can be roaming or in locations that were not originally expected, such as at home. A virus infection on one device, if not caught immediately, can quickly spread across all assets of the business. So, each asset access event should involve a check of the device’s identity and security posture before it is permitted to connect.
Why is IT called Zero Trust?
Zero Trust is the encapsulation of the concept “never trust, always verify.” This strategy was devised by John Kindervag of Forrester Research and it has been developed into the Zero Trust Architecture (ZTA) security model. What this boils down to is that security checks for authentication and authorization should occur as the user or device tries to access each resource individually rather than the usual practice of grouping resources into a collection to which access is granted.




