Extended Detection and Response (XDR) is a sophisticated, integrated cybersecurity solution designed to enhance an organization’s ability to detect and respond to advanced threats in real-time. Unlike traditional tools, which often function in isolation, XDR consolidates data from multiple security layers, including endpoints, networks, servers, and cloud environments, into a single platform.
The integrated approach of XDR allows for more efficient detection of malicious activity. It correlates data across different systems and identifies patterns that might go unnoticed in siloed solutions.
Here is our list of the best-extended detection and response systems:
- CrowdStrike Falcon Insight EDITOR’S CHOICE An XDR that combines an endpoint unit with a SaaS coordinator and is available in a range of editions that add on extra services.
- Palo Alto Cortex XDR This is the definitive XDR that created the sector. It is based around a SaaS platform with endpoint monitors.
- LogRhythm XDR Stack A stratified package divided into specialist elements and distributed between a central SaaS platform and endpoint modules.
- Rapid7 Insight Platform A classic XDR system delivered from a SaaS platform that also offers other security packages.
- Exabeam A SaaS XDR that evolved from a SIEM through the addition of device modules.
You can read more about each of these options in the following sections.
XDR leverages advanced machine learning, automation, and behavioral analytics to streamline threat detection and reduce the time required for incident response. It provides security teams with detailed insights and actionable intelligence, allowing them to act quickly and prevent potential breaches before they escalate. One of its primary benefits is the reduction of alert fatigue, as it minimizes the number of false positives and delivers more accurate, context-rich alerts.
With the increasing complexity of cyber threats, organizations need a solution that can not only detect but also predict and respond to attacks faster. XDR empowers security operations by automating routine tasks, such as threat analysis and response. It also enables analysts to focus on more strategic decisions. By improving efficiency and reducing human error, XDR helps enterprises build a more resilient security infrastructure.
These days, traditional defense mechanisms often struggle to keep up with sophisticated cybercriminals, so XDR is emerging as a critical tool. It enhances an organization’s cybersecurity resilience by providing a proactive, integrated defense strategy, ensuring quicker response times, and ultimately reducing the risk of successful attacks.
Dual-layer defense
An XDR is very similar to a SIEM. With the SIEM system, a central server receives log message uploads from the monitored system and sorts through them, looking for indicators of compromise (IoCs). Gathering all log data from all devices on the system gives the SIEM a bird’s eye view. For example, it will get a report of an unexpected event on one device, access to a communication utility, and then a series of failed connection attempts on another device. Thus, the SIEM can see that an intruder or a piece of malware is attempting to move across the network.
With a SIEM system, all of the processing occurs on a central server, and local modules on the protected system are only there to pick up log messages and upload them to the SIEM server. There are two problems with this strategy. One is that very often, the SIEM is provided by a SaaS platform over in the Cloud. Hackers can quickly isolate the network from all of its security services just by blocking the connection to the internet.
The second weakness of SIEM systems is that networks and endpoints and all of the software that runs on them generate a vast amount of log data in various formats. The SIEM server needs to consolidate all of these records into a standard format and then sort, filter, compare and merge them. Wading through all of that data can take a long time, and all regular status reports just clutter up the process.
A lot of log messages are just debugging notifications that have no relevance to security issues. However, until that has been uploaded to the SIEM and processed, there is no way to tell which messages are useless and which are essential.
With XDR, the local agent is more than just an uploader. It is a complete cyber security package. XDR is like a SIEM that has supersized agents.
The benefits of XDR
XDR improves on EDR because it facilitates information sharing between endpoint instances; thus, it can spot stealth attacks, such as self-replicating ransomware or an advanced persistent threat (APT) where hackers gain access to a system and access it regularly in secret to use resources and investigate data.
The XDR strategy is also better than the SIEM approach. The XDR local instance processes all log messages arising on the device that it is monitoring. It can sort through these and discard inconsequential messages.
The XDR instance makes sense of its local intel and then sends it to the central server, where it forms part of a “data lake”. This information gets summarized, and indicators of compromise get sent to all local XDR units as threat intelligence. The XDR server also receives a threat intelligence feed from the system provider or third-party threat intelligence services. This information also gets sent to the XDR units.
If the device is taken offline by a Trojan or an intruder, the installed XDR unit keeps protecting the device. This makes the XDR system harder for hackers to defeat than SIEM services.
The central server of the XDR also performs its threat hunting by processing information in the data lake. This unified detection system can provide more insights and spot cross-device threats that individual XDR instances can’t see.
XDR Architecture
A defining characteristic of an XDR system is that it is SaaS-based. That means that the XDR provider operates the central processing server on a Cloud platform. Therefore, the on-site element of the XDR is a package that needs to be installed on every device that is enrolled in the system.
Each provider decides on how much data processing should take place on the endpoint. However, the endpoint unit is more than just an agent. It can operate autonomously, and it should implement threat remediation as well as threat detection.
When the local unit detects a threat, it sends instructions to local system protection services, such as access rights managers and firewalls. This shuts down hijacked accounts and blocks communication with suspicious IP addresses. The XDR unit is also able to kill processes.
The central server’s threat hunting is supplementary to the local XDR activity. For example, if the server spots an IOC, it sends instructions to all local instances, scouring their protected device for signs of that threat and taking appropriate action.
The Best Extended Detection and Response Software
While each provider adds its expertise to get an edge over the competition, the basic format of all XDR systems is the same. Expect to see an external threat intelligence feed, machine learning for activity baselining, and anomaly detection as the primary threat-hunting strategy.
What should you look for in an extended detection and response tool?
We reviewed the market for XDR packages and analyzed the tools based on the following criteria:
- A system that is managed from the Cloud as a SaaS package
- Local XDR instances that can act autonomously
- A method to speed up threat detection using AI techniques
- Anomaly detection that looks for deviations from standard activity per user and per resource
- Machine learning to automatically adjust baselines and reduce false-positive reporting
- A free trial or a demo system for a risk-free assessment opportunity
- A system that offers value for money by repaying its price through disaster avoidance
It would be nice to include some free XDR options. However, in this cutting-edge cybersecurity category, there are no free systems that fully qualify.
1. CrowdStrike Falcon Insight
CrowdStrike Falcon Insight is delivered from a platform that hosts a range of security systems. The Insight module operates on the SaaS platform and interacts with instances of Falcon Prevent, which is a device-based EDR. By coordinating Prevent, Insight creates an enterprise-wide XDR.
Key Features:
- Two-layer protection
- Autonomous endpoint module
- Cloud-based coordinator
- Threat intelligence
- User and entity behavior analytics
Falcon Prevent is a complete protection system and can work autonomously without any connection to the Insight module. This configuration ensures that endpoint protection continues even without the Insight service being contactable. Once communications are re-established, the Insight system updates all Prevent instances with the latest intel, and the Prevent units upload their recent experiences to the Insight data lake.
The two layers of Falcon Insight use user and entity behavior analytics (UEBA) to establish a baseline of activities and detect deviations from that norm. The baseline is constantly adjusted, which makes threat detection more accurate.
Falcon Insight is sold as a package with other units. There is also a managed service option for the tool, in which CrowdStrike technicians watch the security monitor for you.
There isn’t a free trial available for Falcon Insight. However, you can get a 15-day free trial of the endpoint module, Falcon Prevent.
Pros:
- It can be implemented across sites
- Automated intelligence feed from CrowdStrike
- Shared intel within the network
- Continuous protection against malware and intruders
- Automatically adjusting baselines
Cons:
- No business continuity assistance
EDITOR'S CHOICE
CrowdStrike Falcon is our top pick for an extended detection and response tool because it is part of a more comprehensive platform of SaaS-provided cyber security systems. You can get extra features by picking the right plan or just getting the Insight XDR to protect your system. The package will shut down malware and block the intruders that it detects in an automated cycle, so you don’t have to worry about intervening or deciding how to deal with an attack.
OS: Cloud-based
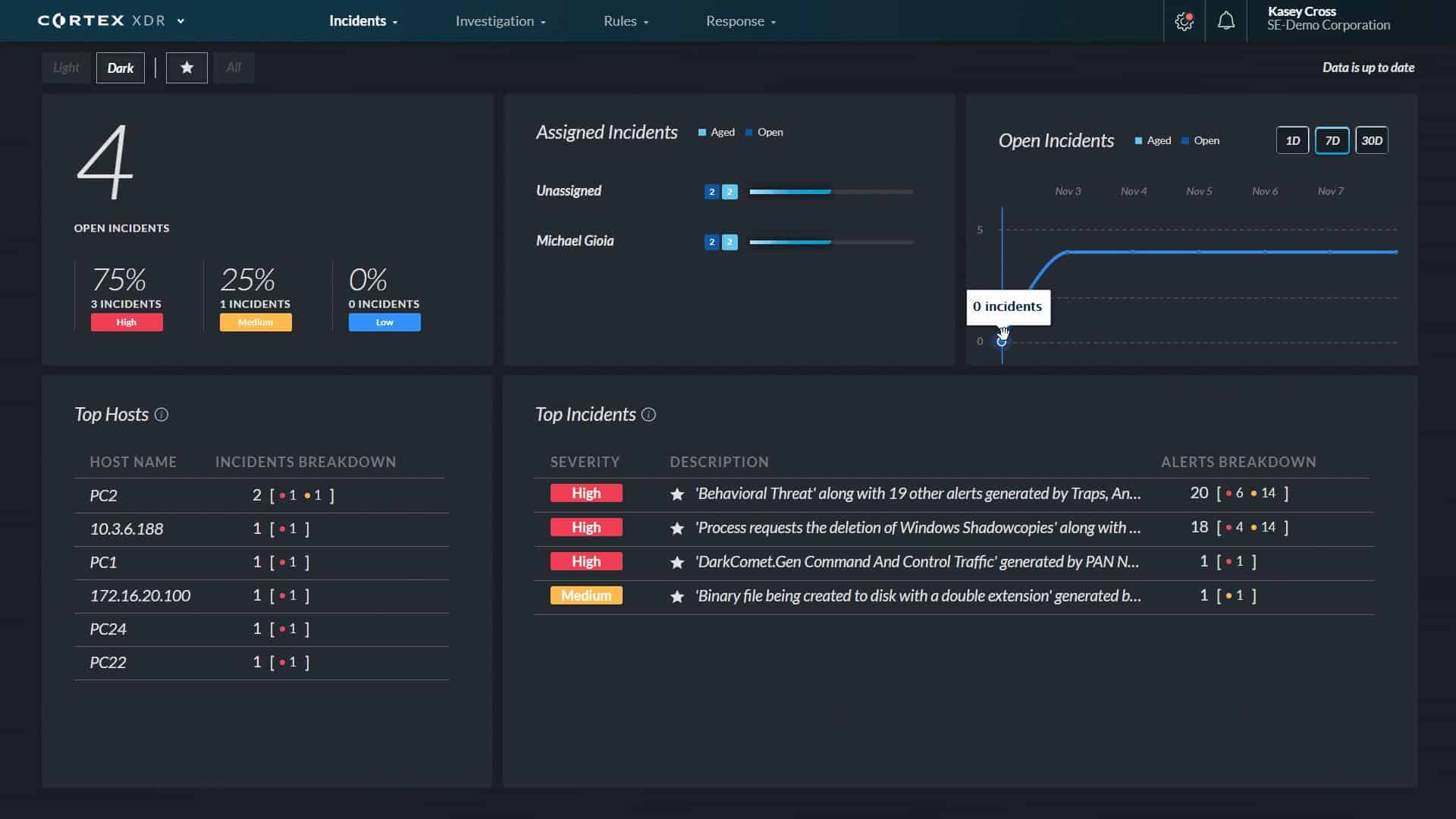
2. Palo Alto Cortex XDR
Palo Alto Networks invented the XDR concept in 2018, and they have continued evolving their standard package. This service is composed of a SaaS service that coordinates on-device EDR units. If you have a hybris system and need to protect cloud assets, you should opt for the business’s virtual firewall offering instead.
Key Features:
- UEBA and triage
- Dual-level security activity
- Autonomous endpoint protection modules
- Threat intelligence
The Cortex XDR system performs threat hunting on a data lake formed by uploads of reports from endpoint monitors. Those endpoint monitors are also capable of operating autonomously.
Cortex XDR receives a threat intelligence feed that distills the security experience of all Palo Alto Networks customers. Additionally, as all service clients are hosted at the same data centers, threat notification sharing is performed instantly.
Pros:
- Well-planned coordination between on-site and cloud-based elements
- Options to include Cloud resources in the protection scheme
- Includes a next-generation firewall
- Automatically re-assessed baselines
- Fast threat identification
Cons:
- Could just buy each element individually
The threat detection system works with machine learning to establish a baseline of regular, instantly performing threat notification-sharing activity and then looks for anomalous behavior. Remediation actions are implemented through orchestration, which interacts with firewalls and access rights managers to isolate accounts and block IP addresses. In addition, the Cortex XDR system includes a next-generation firewall, which also contributes to threat detection and response.
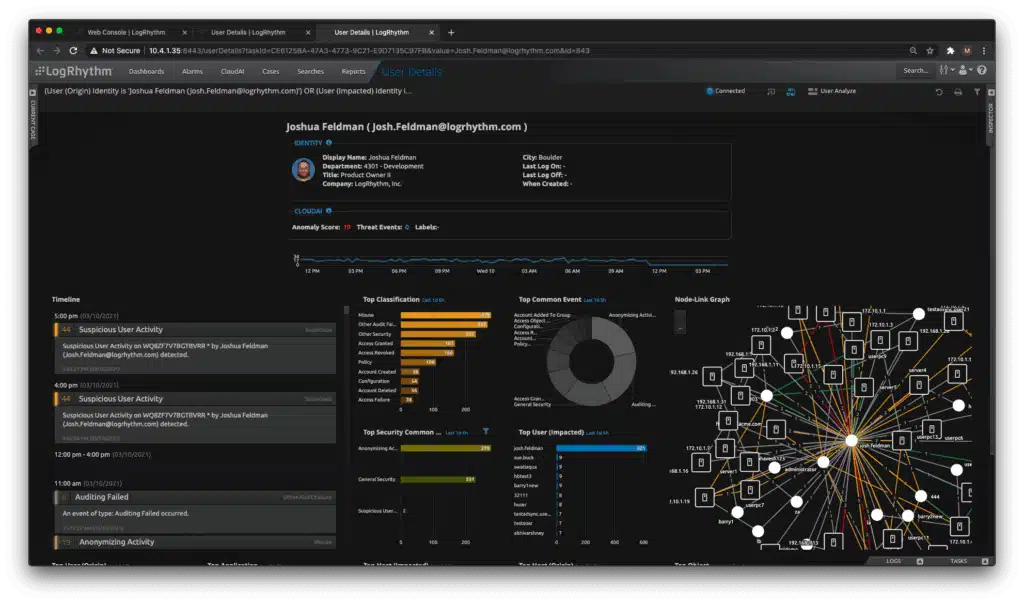
3. LogRhythm XDR Stack
LogRhythm represents its XDR as a stack of services, a little like the TCP/IP model. That’s a great help when conceptualizing how the security service works but in reality, all XDRs operate in the same way. This XDR evolved from a SIEM system, and its endpoint units are less potent than those of rival XDR systems. This means that a constant internet connection is essential to keep endpoints protected.
Key Features:
- Stratified defense
- UEBA
- Orchestrated threat response
The on-site elements in the stack are called UserXDR and NetworkXDR. These are the typical feeds of a SIEM system that upload log messages from endpoints plus network activity reports. The log server is called AnalytiX and that consolidates all incoming log messages into a standard format and files them. DetectX then searches through that data lake for indicators of compromise. A threat intelligence feed constantly updates the IOC database. The system also uses UEBA to work out what is considered regular activity on the protected system.
The remediation rules of LogRhythm XDR Stack are called RespondX, which uses SOAR to implement responses by coordinating with other on-site tools to block accounts and kill processes.
Pros:
- UEBA to reduce the incidences of false alarms
- Fast distribution of threat intelligence
- Option for on-site hosting
Cons:
- No free trial
- On-device modules are not autonomous
Although the classic structure of an XDR is SaaS-based, LogRhythm offers other deployment options as well. So, you can choose between the SaaS package, installation on Windows Server, or running the XDR Stack on your site as a virtual appliance.
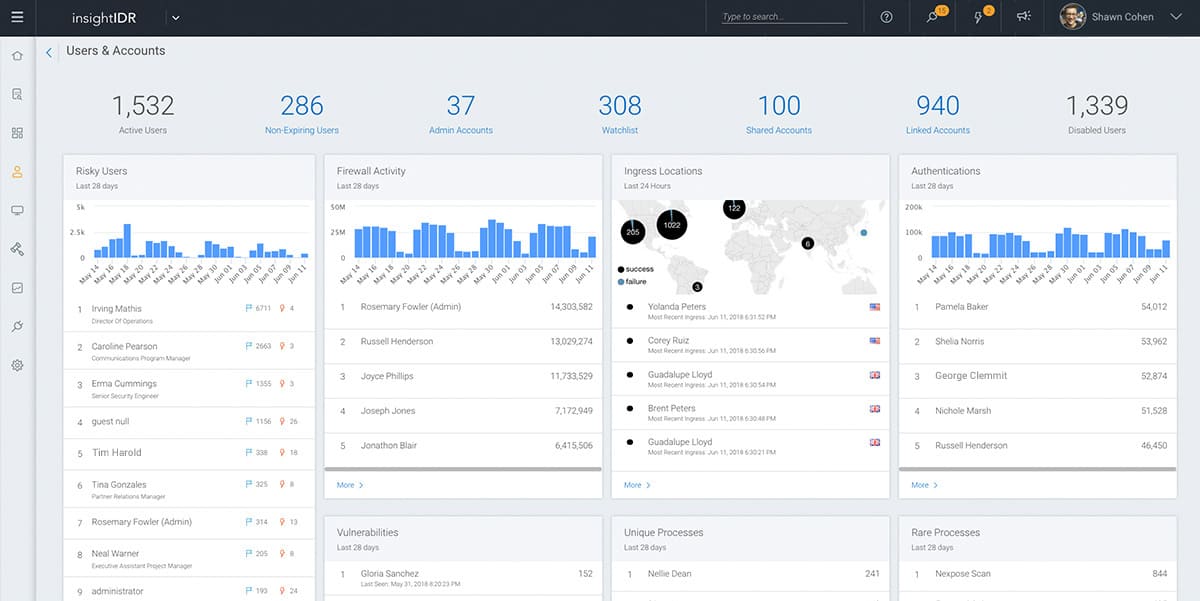
4. Rapid7 Insight Platform
Rapid7 Insight is a cloud platform that offers a range of cyber security systems. Choosing elements from this menu of services can give you an XDR system. InsightIDR is a SIEM system. Although this includes weak endpoint units, the package is probably a solid equivalent for the LogRhythm system. “IDR” stands for Incident Detection and Response.
Key Features:
- UEBA for low false-positive reporting
- Automated responses
- Lightweight on-site resources
InsightIDR uses UEBA for baselining, and it gets a threat intelligence feed called Attack Behavior Analytics (ABA). The response part of the Insight platform is called Insight Connect, and it is implemented through SOAR. This coordinates with firewalls, task managers, and access rights management systems to kill off malicious processes, block suspicious IP addresses, and isolate compromised user accounts.
Pros:
- Expandable service with extra modules available on the same platform
- A single on-site agent to feed multiple protection services
- Automatically adjusted activity baselines
Cons:
- On-device modules are not autonomous
- No free trial
Other modules on the Insight platform include a vulnerability manager, InsightVM, and protection for Cloud resources from a package called DivvyCloud. Additionally, businesses running a DevOps environment should opt for the Insight AppSec package.
5. Exabeam
Exabeam is a SIEM service, but it can also be regarded as an XDR. This system installs agents on all protected endpoints. However, the protected devices don’t need to all be on the same site, so this is a good service for businesses that have remote-based workers.
Key Features:
- UEBA for standard activity baselining
- A SaaS service
- Threat intelligence feed
The SaaS service delivers its console from the cloud, which can be accessed through any standard Web browser. Device agents upload reports, which are reformatted and stored in a data lake. As well as forming the source material for threat hunting, the records in the data lake can be accessed by the user through an analysis screen in the Exabeam console.
Exabeam deploys machine learning to track activities on each device and on the network and establish a normal behavior pattern. Then, threat hunting looks for deviations from this pattern and looks for known hacker attack strategies, which are indicators of compromise.
The threat response is triggered by the detection of an IOC or unusual behavior. The exact actions taken are laid down in playbooks. Although Exabeam writes these playbooks, it is also possible for the user to create custom rules. Exabeam can also perform log management tasks and archiving as an add-on service.
Pros:
- Almost all processing is performed on Cloud servers
- Light load on local devices
- Fast threat detection and automated response
Cons:
- Endpoint agents can’t operate independently
Exabeam XDR is available for a free trial.