Application layer attacks are a pervasive threat to modern enterprises. Applications and modern business operations go hand-in-hand and having an application security solution have become just as important as protecting physical hardware. Dynamic Application Security Testing (DAST) is one of the core testing methodologies that companies are using to detect cyber attacks. But what is DAST exactly?
DAST Explained
DAST is a type of black-box application testing that can test applications while they are running. When testing an application with DAST you don’t need to have access to the source code to find vulnerabilities. This is called a penetration test to find issues and configuration errors from outside of the application, from the perspective of an attacker.
DAST software works by automatically scanning application vulnerabilities in web applications. Once the software finds a vulnerability it sends an alert to the user so remediation measures can begin. The notification tells users the issues they need to resolve to secure the application.
Why is DAST Important?
DAST has an important role in helping to identify vulnerabilities in an application during production. DAST software tests the HTTP and HTML interfaces of applications that attackers would use to break into a service. Running a DAST penetration test helps you find those vulnerabilities before an attacker does.
Dynamic testing is also necessary to find specific issues and attacks that other testing methodologies would miss. For example, a DAST solution can detect SQL injection attacks that attempt to disrupt the database of a web application with bogus SQL code.
Now attackers are launching more and more attacks at the application layer it is a business necessity to implement a form of application testing. Companies that don’t are unable to identify these attacks when they occur, and can experience significant damage if an attacker successfully breaches the network.
DAST vs SAST
DAST is one of many application testing methodologies. One of the most popular alternative methodologies is Static Application Security Testing (SAST), a white box testing methodology, which can search through the source code of applications at rest.
SAST takes an inside-out perspective and can be used early in the software development lifecycle to fix vulnerabilities. SAST software highlights defective segments of code so that a developer can take steps to remedy the situation.
The main advantage SAST has over DAST is that it can not only find errors in source code but it can highlight those errors to the user so they can be changed. The use of these tools early in the SDLC also saves money. Although it is important to note these solutions also have to support the programming language and application framework being used by the application.
The edge DAST has over SAST is that you can test for vulnerabilities from the perspective of an attacker. Most attackers wouldn’t have access to the source code when trying to break into an application so running a penetration test has more real-world benefits. DAST also has the advantage of versatility. A DAST solution doesn’t need to have the same programming language or framework to scan an application for vulnerabilities.
However, for the best results, it is advisable to combine the two tools together. Using a combination of DAST and SAST tools provides you with the widest coverage against security threats.
DAST and SAST vs IAST
While DAST and SAST are still popular application testing models, many companies are starting to switch to hybrid solutions like Interactive Application Security Testing (IAST) to stay secure. An IAST installs an agent on an application server to run scans while an application is running.
The user can run automated or manual tests and the IAST Solution will report on any vulnerabilities found. IAST solutions are generally used during the testing phase of the SDLC. By finding faults early on in the SDLC, IAST keeps prices down and leads to more efficient releases.
The key advantage that IAST has over DAST is its automation. It can find vulnerabilities and drive remediation forward much faster than DAST. Its automation allows it to fit into the CI/CD pipeline and enables developers to fix issues in less time, highlighting bad code on the screen. In comparison DAST finds issues but it doesn’t highlight the code segments that caused the issue as a SAST tool does.
IAST’s advantage over SAST is that it can find vulnerabilities in running applications. However, it is important to note that IAST cannot replicate the penetration testing approach of DAST. Using a combination of DAST, SAST, and IAST tailored towards your use cases is the best approach for now.
DAST Tools
Our methodology for selecting DAST systems
We reviewed the market for DAST tools and analyzed the options based on the following criteria:
- Systems that can test web applications under development
- An IT operations mode to test third-party web applications
- Integration into CI/CD pipelines
- Autodiscovery for existing microservices
- Pre-development scans of APIs and development frameworks
- A free trial or a demo system to allow a pre-purchase assessment to be conducted
- Value for money from a DAST tool that is offered at a fair price
The simplicity of DAST tools makes them stand out against alternative platforms like SAST because you don’t need any special knowledge in order to use them. In this section we’re going to look at some of the top DAST tools:
- SOOS (EDITOR’S CHOICE) This cloud-based web application testing system has an SCA plan, which identifies third-party components with security weaknesses, and a higher edition that adds on a DAST system. Access a free Community Edition of the SCA plan or get a 30-day free trial of the DAST service.
- Appknox This automated DAST tool focuses on automated web application security scanning and higher versions offer on-demand tests. This is a cloud-based platform.
- Invicti This vulnerability scanning system can be used for development testing and includes DAST, SAST, and IAST capabilities. The service focuses on web application security. Available as a SaaS platform or for installation on Windows and Windows Server.
- Acunetix This security scanner offers DAST plus SAST and IAST. This is an on-demand vulnerability scanner for web applications that is also available in a continuous version. Offered as a cloud service or for installation on Windows, macOS, or Linux.
- Veracode Dynamic Analysis This is an automated DAST tool that implements continuous scans of development environments and operational systems. This tool is a SaaS platform and is very easy to use.
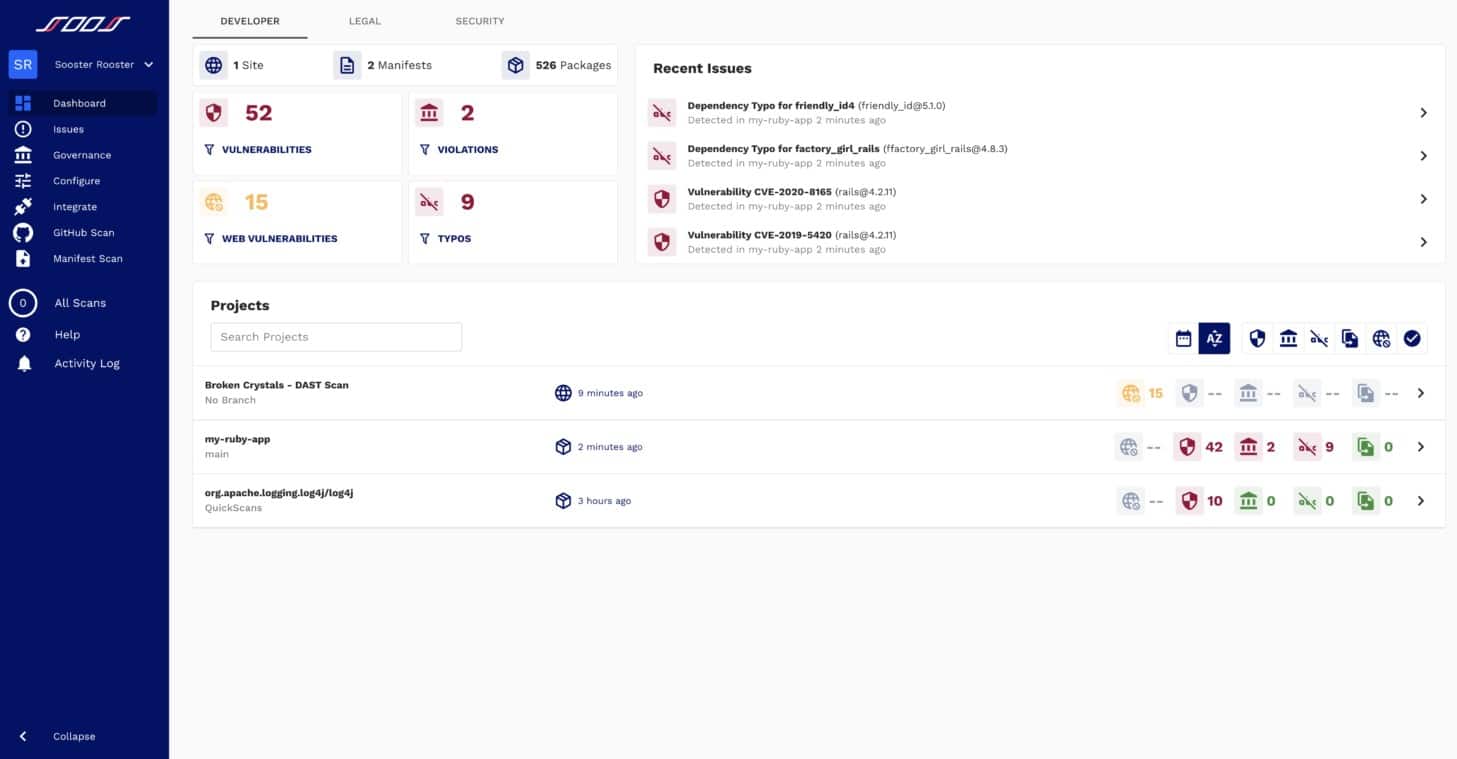
1. SOOS (FREE TRIAL)
SOOS is a web application testing platform that provides software composition analysis (SCA) to track the security of open-source content in any application. A higher plan for the SOOS service adds on a DAST service. Both services integrate into your development pipeline and provide automated testing.
Key Features:
- DAST Services: Dynamic application security testing runs functions
- SCA System: Software composition analysis looks for weaknesses in third-party components
- Development Management Tools Integration: Connects with Jira, Bamboo, and Jenkins
- Assesses APIs and Frameworks: Security testing
- Cloud-Based System: You don’t need to host or maintain the package
Why do we recommend it?
SOOS provides DAST and Software Composition Analysis (SCA), which looks for open-source code that has known weaknesses. The SOOS system is delivered from the cloud and so it is not bound by a hosting platform and can assess microservices hosted on different cloud systems.
The service tests web apps and APIs and it compliements the SCA system by checking through privately developed systems both in unit testing and acceptance testing. Your operations staff can also use the testing service on demand to track the security of live apps through domain scanning.
The DAST testing system runs your code in Docker, providing an isolated sandbox environment that keeps your servers safe from attack, should weaknesses exist in your new code. The system interfaces directly with the Jira and GitHub issue trackers so it will cycle results back into the team for adjustments, automatically updating your development schedule.
The SOOS service is a cloud platform and you can access the dashboard for your account through any standard web browser. The tool provides integration with a long list of development environments and project management systems, including Azure DevOps, Jenkins, and Bamboo.
Who is it recommended for?
This system is ideal for DevOps teams that develop and run web applications. It will scan third-party components before they are included in a development, check applications before they go live, and then continue to scan live applications. The tool will integrate with the major development and team management tools.
Pros:
- Use as a Continuous Tester: Deploy in a CI/CD pipeline
- On Demand Domain Scanning: Unlimited scans
- Simultaneous Domain Scanning: Examine many domains at the same time
- Runs Code for Testing: Contains execution in Docker for system protection
- Looks for Known Vulnerabilities: Identifies SQL injection, secret exposure, and other weaknesses
Cons:
- No On-Premises Version: Only available as a SaaS platform
SOOS is a subscription package at a price per month with unlimited seats. You can examine the SOOS system with a 30-day free trial.
EDITOR'S CHOICE
SOOS is our top pick for a DAST tool because it provides code analysis as well as dynamic application security testing. The service runs a range of tests by executing a web application and tries a number of commonly tried attacks. These tests are run within a Docker container to ensure that your system doesn’t actually get attacked by your own testing package. The tool can be set up to run automatically, which allows its use as a continuous tester in a CI/CD pipeline. This use is further enhanced by the package’s ability to interact with development project management tools. The SOOS service records whether security weaknesses are present, which either queues up the package for rework or flags it for release.
Download: Download a 30-Day Free Trial
Official Site: https://soos.io/
OS: Cloud-Based
2. Appknox
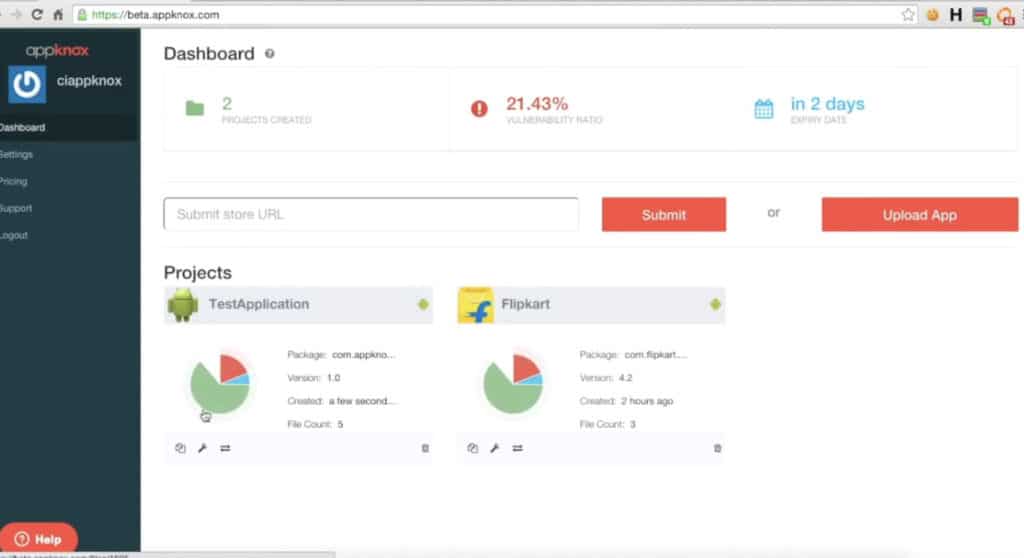
Appknox is a dynamic DAST solution that can detect vulnerabilities in running applications. The system is designed to flag vulnerabilities that are commonly used in like Man in the Middle Attacks (MiTM). All you need to do to install the solution is to upload the application binary to an Appknox cloud-hosted device.
Key Features:
- Scanning for Live Systems: Operates as a vulnerability scanner
- DAST and SAST: Provides static application security testing as well as dynamic application security testing
- API Scanning: Operates as a separate phase to the DAST service
- Specliaizes in Mobile Application Testing: Three plan levels
Why do we recommend it?
Appknox specializes in security scanning for the microservices behind mobile apps. The platform will perform Dynamic Application Security Testing (DAST) and also Static Application Security Testing (SAST). It counts API scanning as a separate phase of security testing. However, what method is used for this is not explained.
The platform is also very easy to use. You can launch a dynamic scan via the dashboard and then generate a report to highlight the vulnerabilities that need to be fixed.
One excellent feature for cutting down entry points is the API Scan. You can enter the endpoints of your server and then the program will attempt to break into your server. You can scan multiple endpoints in one setting to find any issues that could allow an attacker to hack into your network.
There are three versions of Appknox available to purchase; Essential, Professional, and Enterprise. The Essential version comes with unlimited scans, dynamic scans, API scans, continuous integration, and more.
The Professional version includes all of those features plus manual scans, a dedicated account manager, and more. The Enterprise version contains everything in the other versions plus a private cloud and customized reporting.
Who is it recommended for?
By default, Appknox is a SaaS platform but it is also possible to get the software and host it yourself. The base package provides on-demand and scheduled scanning. You need to get up to the two top plans if you want to integrate the testing system into a CI/CD pipeline for a DevSecOps strategy.
Pros:
- Operational Options: On demand scanning or scheduling options
- Operates in the Cloud: No need for an on-premise server
- CI/CD Pipeline Integration: In the top two plans
- Human Pentesting Team: Opt for a human probe of your applications
Cons:
- No Free Trial: The platform offers a demo
You can request a demo.
3. Invicti
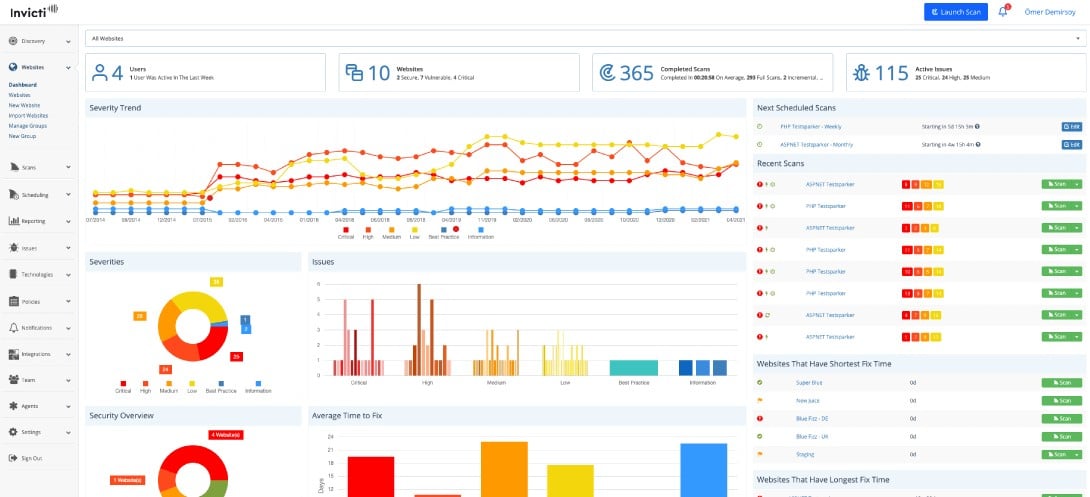
Invicti, formerly Netsparker, is a very popular DAST solution that provides in-depth vulnerability scanning for any web application. The software is sophisticated enough to detect all direct impact vulnerabilities with zero false positives. Issues that Invicti can detect include SQL Injection, Reflected XSS, Local File Inclusion, Unvalidated Redirect, Remote File Inclusion, and Old Backup Files.
Key Features:
- DAST and IAST: Dynamic application security testing and interactive application security testing
- Assesses Cohesion Weaknesses: Tests data protection between functions
- Assesses APIs and Frameworks: Runs functions with different parameters
Why do we recommend it?
Invicti is a DAST testing service and it also implements IAST. The package’s plans are all a little different in that some are only available as a SaaS platform while others can be hosted on site. You can use this tool for automated continuous testing in a CI/CD pipeline.
One of the main strengths of Invicti is its ability to scan thousands of web applications in a matter of hours. It can even automatically verify identified vulnerabilities. This means that you don’t have to waste time and money manually verifying vulnerabilities with your team.
If you’re looking for a scalable solution with unlimited capacity then Netsparker is a product you should consider. Invicti is available as a software package, online service, or on-premises solution. To view the price you will have to request a quote directly from the company.
Who is it recommended for?
This is a flexible tool so it can be used by penetration testers or it can be set up as a vulnerability scanner. You can use it to verify APIs, frameworks, and libraries for inclusion in a development. For acceptance testing and for ongoing vulnerability scanning of live web applications.
Pros:
- Continuous Testing: For CI/CD pipeline integration
- Color-Coded Reports: Helps teams prioritize remediation with color coding and automatic threat scoring
- Includes Pentesting Tools: Great for companies with internal “red” teams
Cons:
- No Free Trial: Get a demo instead
4. Acunetix
Acunetix implements DAST services in a vulnerability scanning format. This service also offers static examination of code that is written in JavaScript, PHP, and .NET framework. The system is available in three editions. While the lowest plan provides on-demand security testing, the higher two plans implement continuous, automated vulnerability scans.
Key Features:
- DAST and IAST: Dynamic application security testing and interactive application security testing
- Option for Internal Scanning: Uses the third-party tool OpenVAS
- CI/CD Testing for Development: Vulnerability scanning for live applications
Why do we recommend it?
Acunetix is very similar to Invicti but it has slightly stronger vulnerability scanning features than its main rival. This package can be used for internal vulnerability scanning of endpoints and networks by integrating it with the free OpenVAS system. The package provides IAST options as well as DAST.
The Acunetix system specializes in examining web applications. It is able to scan for the OWASP Top 10 plus 7,000 other web application exploits. The service can also provide a network vulnerability scanner that searches for more than 50,000 known weaknesses.
An implementation of Acunetix can offer development security scanning or you can use it for IT operations to keep track of the security of live websites and networked applications. The service is able to drill down through APIs to scan the vulnerabilities in their underlying modules.
The three versions of Acunetix are called Standard, Premium, and Acunetix 360. The Standard plan only offers on-demand scans but it still has full DAST capabilities. You can access Acunetix through its hosted Software-as-a-Service version or run the software on your own servers. The system will install on Windows, macOS, and Linux.
Who is it recommended for?
This package is a good choice for a vulnerability scanner because it can check on all of your IT system, not just web assets. It can also be used as a continuous tester in a CI/CD pipeline for DevSecOps. Potential buyers should compare Acunetix to Invicti before deciding.
Pros:
- Designed Specifically for Application Security: Prioritizes discovered vulnerabilities by severity
- Detects Misconfigurations: Alerts when they are discovered
- Launch Options: On-demand, scheduled, or triggered by an event
Cons:
- No Price List: You have to request a quote
Operating system: A cloud service or for installation on Windows, macOS, or Linux
5. Veracode Dynamic Analysis
Veracode Dynamic Analysis is a DAST solution that emphasizes automation and ease of use to deliver a tool that’s fast to deploy. For example, you can schedule automated scans so that you don’t need a human user to look for vulnerabilities. However, if a scan ever collides with any other development activities you can press the Pause button to stop the scan.
Key Features:
- Large Platform with Many Testing Strategies: DAST, SAST, IAST, and SCA
- API Assessment: Test supplied functions
- DevOps Usage: Use during development for module testing and in operations as a vulnerability scanner
Why do we recommend it?
Veracode Dynamic Analysis is one of the service options on the Veracode testing platform. The company also offers SAST, SCA, and container testing and they also provide the services of a penetration testing team. Most web application development businesses would probably use the SCA and SAST services as well as the DAST package.
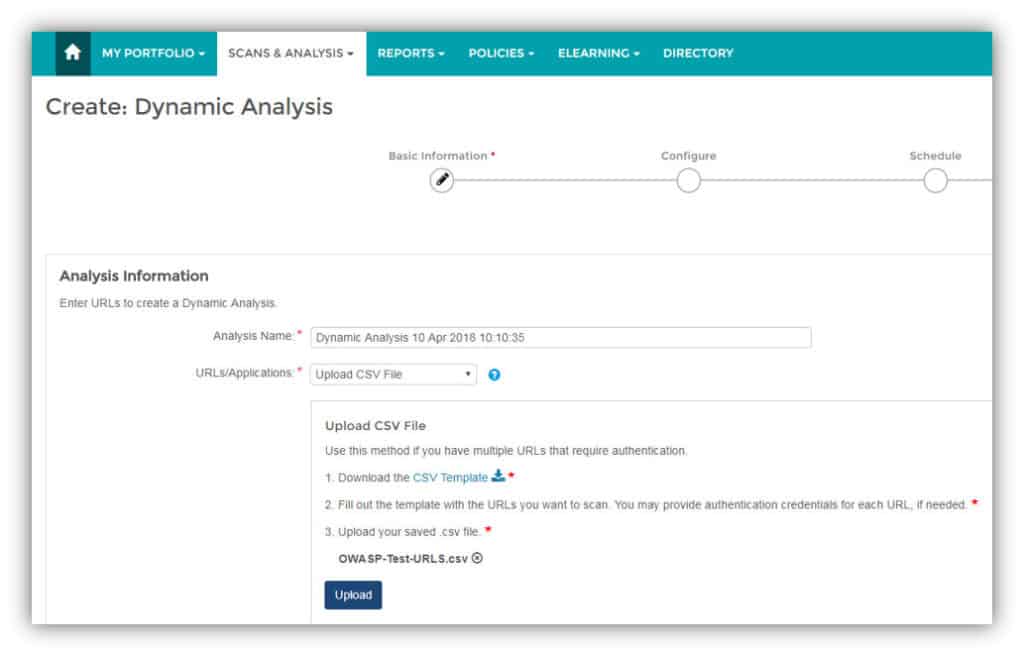
Scanning web applications is Veracode Dynamic Analysis’s specialty. There is also the option to scan web applications that sit behind login screens with the help of Dynamic Scan Engineers who will create login scripts so automated scans can take place unhindered.
The software is also highly accurate, delivering vulnerability scans with lower than a one percent false-positive rate. That means you can be sure any vulnerabilities found are legitimate.
In terms of ease of use, Veracode Dynamic analysis is second to none. You can launch a scan with a single URL. If you want to scan multiple applications then you can upload a .csv document with a list of URLs. That means you don’t have to do any complicated configuration to start scanning your infrastructure.
If you’re looking for a DAST tool that’s easy to deploy and automate, then Veracode Dynamic Analysis is highly recommended to enterprises of all sizes. However, you’ll have to contact the sales team to view a quote.
Who is it recommended for?
Veracode is a modular platform that allows buyers to select units and create a package. This tool is aimed at development teams and the platform also offers an automated remediation package. Businesses that run web apps but don’t build them would probably be more interested in the penetration testing service.
Pros:
- Assemble Your Own Testing Platform: Choose which testing methods you want
- Easy Options to Stop, Pause, and Resume Scans: Alternatively, run on a schedule
- Fully Automated: Designed to remove the complexity of vulnerability hunting
Cons:
- No Price List: No outline of what plans are available
You can request a demo.
DAST Best Practices
Many companies are hesitant to deploy DAST solutions because of their complexity and cost. While they can be costly there are a number of best practices companies can use to make the transition as productive and cost-effective as possible:
- Use DAST as early as possible
- Combine DAST with SAST
- Collaborate with DevOps teams
Use DAST as early in the SDLC as possible
The earlier you use a DAST solution in the SDLC the better. Identifying vulnerabilities in a web application early in the SDLC saves money throughout the release cycle. Employees will be able to take steps to address the issues found before the application is completely designed. It’s more cost-effective to modify an application early in production than it is after release!
Combine DAST with SAST
DAST works best when combined with SAST. Each methodology covers vulnerabilities that aren’t covered by the other. SAST will give you an under the hood source code perspective whereas DAST will give you a view of entry points from a potential attacker’s perspective. Covering a range of vulnerabilities gives you the best protection against cyber attackers.
Collaborate with DevOps Teams
Finding vulnerabilities is all well and good but if you don’t have close communication with your DevOps team you’ll struggle to address the issues. Every time you find a vulnerability make sure that you pass the information on to your developers. You can do this through the use of notifications with your DAST solution or by using a bug-tracking tool. Open communication will ensure that your time to remediation is narrow.
What is DAST: A Must For Enterprises Using Applications
DAST is vital to any organization using applications to do business. DAST tools occupy an area of application testing that not even high-tech IAST solutions can render obsolete. Being able to run penetration tests on applications outside of the source code allows you to monitor for the web application vulnerabilities and misconfigurations that attackers commonly try to exploit.
The ease with which you can deploy SAST solutions early in the SDLC increases efficiency and drives down costs. These tools are scalable and easy to use because you don’t need access to application frameworks or source code and DAST can work with any programming language.
Even with the growth of solutions like IAST and grey-box testing IAST still has a role to play in keeping modern applications safe. When used correctly on-demand dynamic testing can be a potent weapon against cyberattackers.
DAST FAQs
What does DAST stand for?
DAST stands for Dynamic Application Security Testing (DAST). This involves running a Web application with a range of input values and examining the outputs. This is a form of automated penetration testing.
What is DAST vs SAST?
DAST is “dynamic” application security testing and SAST is “static” application security testing. The difference between these two methods is that DAST runs an application to examine it, while SAST scans through the code of the application. In both of these testing strategies, the aim of the test is to identify security weaknesses.
What is DAST in SDLC?
DAST is an automated testing method and this makes it ideal for integration into a development pipeline. Completed units need to be definitively stored in the project code library and this presents an opportunity to trigger DAST. It is possible to set a DAST tool as a gatekeeper for the repository: pass and the code gets saved, fail, and it gets sent back for rework.