The widespread adoption of digital transformation and other related technologies such as cloud computing, BYOD, and IoT has significantly broadened the enterprise network attack surface and opened the door for new security risks and vulnerabilities.
In recent times, organizations are embracing a new category of security solutions that complement and even go beyond the capabilities of log analysis tools such as SIEM and endpoint detection and response (EDR) products to provide an aerial view of the suspicious activities and interactions between all devices on the network. This new category of security solutions is known as Network Detection and Response (NDR). NDR is a security strategy that enables organizations to protect their networks by analyzing their network activity without the headache of having to manage individual device software. As a result, it is rapidly emerging as a must-have capability in modern security operations.
NDR solutions primarily use non-signature-based techniques such as machine learning, deep learning, statistical and heuristic analysis, and other techniques to detect suspicious traffic on a network. When the NDR tools detect suspicious traffic patterns, they raise alarms and, where necessary, provide an automatic response. This piece will review one of the leading NDR solutions– the Vectra Cognito platform, including the ten best Vectra Cognito alternatives to consider.
Vectra Cognito Platform Review
The Vectra Cognito platform is an intelligent AI-driven NDR system for native and hybrid cloud environments. Vectra Cognito helps organizations detect, investigate, and respond to cyber-attacks or suspicious network activities across on-premises enterprise networks, cloud, and SaaS environments. The Cognito platform addresses network security challenges through three component applications: Cognito Detect, Cognito Recall, and Cognito Stream.
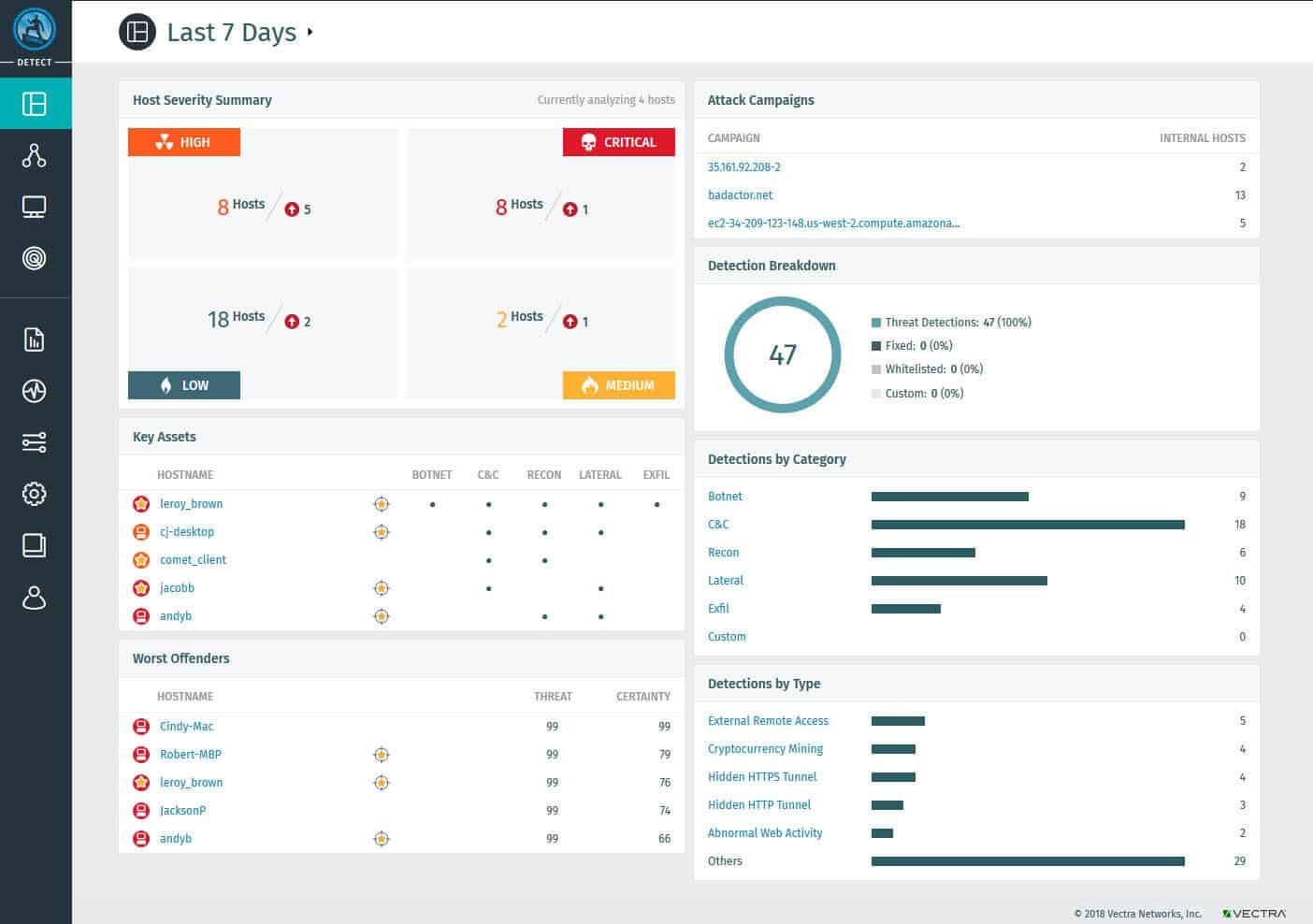
- Cognito Detect This component is designed to find threats by looking for suspicious or malicious network activities and devices and users that have already bypassed perimeter defenses. Detect tracks network devices via their MAC address, hostnames, and other non-IP-related identifiers. Even if they move to a remote location or different office, Detect can still keep track of its history, including its identity and function on the network. The detection effort is made possible by combining many detection algorithms and an AI engine. Every detection attempts to answer what was discovered, why it should be a concern, and how to mitigate the problem.
- Cognito Recall This component performs AI-driven threat hunting and investigations by correlating threat-behavior data with host devices and workloads to gain complete visibility into unseen security vulnerabilities. Cognito Recall collects and stores a vast amount of historical network traffic data and uses it to assist in deeper investigations and threat hunting. With Recall, almost nothing needs to be manually correlated. Instead, every incident in Detect has a link to launch Recall, which opens up a new dashboard where Recall pulls information related to activities that previously occurred within the network.
- Cognito Stream This component enriches network metadata with other network and host information for further analysis to improve detections, investigations, and hunting. It does not have its interface but works behind the scenes with Detect and Recall or other third-party security tools such as SIEM to enhance its capabilities. Cognito Stream can be deployed in the cloud or on-premise using StreamPlus. StreamPlus is built on your choice of hardware, whether a virtual machine or Vectra-provided hardware, and provides an on-premises data lake to collect, store, and search important network metadata.
| Product | Cognito Detect | Cognito Recall |
|---|---|---|
| Goal | Identify compromised host as an investigation starting point | 1) Manually investigate 2) Find threats that detections have missed |
| Scope | Covers "Initial detection" to "Validate detection" | Complete investigation |
| Needs | Real-time high-fidelity signal and automation | 1) 360-degree view of historical metadata 2) Efficient search |
Table 1.0 | Comparison of Cognito Detect and Recall
These products work together to analyze network data, including metadata, and provide a behavior-focused detection and response model. In addition, detect, Recall, and Stream can be purchased individually and operate independently of one another. Still, it’s much more likely that an organization may go for Detect and not Recall if they are only installing one component. However, the real power of Vectra’s Cognito platform lies in the integration of the three products to make threat hunting and detection more efficient and effective. But this comes at a cost that may be unbearable, especially for SMBs.
Key features and capabilities include:
- Collects and enriches security metadata with deep insights and context to allow analysts to stop a wide range of attack scenarios early and consistently.
- Detects prioritizes, and responds to hidden cyber threats inside a cloud, data center, IoT, and enterprise networks.
- Deliver scalable, security-enriched network metadata to feed custom detection and response tools
- Automates the manual tasks associated with Tier-1 and Tier-2 analysis to reduce the overall security operations workload.
- Accelerates response time by integrating and sharing security insights with EDR, SIEMs, and SOAR tools for the endpoint to cloud threat management and visibility.
- AI-assisted threat hunting from cloud and data center workloads to the enterprise
- Speeds-up threat detections and reduces investigation time by capturing metadata at scale across the cloud and enterprise infrastructure.
- It gives security analysts more time to proactively hunt for threats and investigate incidents with tremendous success by stopping ongoing attacks.
- Provides visibility across cloud, data center, and enterprise environments by collecting and storing rich network metadata, relevant logs, and cloud events in real-time
Cognito Vectra uses network sensors (hardware or virtualized) to collect vertical and horizontal traffic. Sensors report to the brains of the suite, which is a hardware appliance where all the AI about what is going on in the network is applied. Reports are compiled by the appliance and sent to the dashboard. Vectra Cognito pricing is based on the number of protected devices tracked by the application.
The Best Vectra Cognito Platform Alternatives
Vectra Cognito platform is not a one-size-fits-all solution for everyone. If you figure out that it is not best suited for your needs or environment and you’re considering a suitable alternative, you’ll find lots of them out there. To help you decide between the countless options out there, we’ve put together a list of the ten best Vectra Cognito platform alternatives. Hopefully, this will guide you in the process of selecting the right one that meets your needs.
1. ExtraHop Reveal(x)
ExtraHop Reveal(x) is a detailed and flexible NDR solution that helps organizations detect suspicious network behaviors, prioritize investigations according to the risk score, and automate response efforts. ExtraHop Reveal(x) is ideal for any security operations teams that need better visibility into network behavior in their environment.
ExtraHop Reveal(x) NDR licensing can be either subscription-based or perpetual. The subscription-based option offers time-based access to ExtraHop NDR software installed on purchased hardware or a virtual machine. For the endless licensing option, you are buying ExtraHop hardware and software.
2. Cisco Stealthwatch Enterprise
Cisco Stealthwatch is an agentless Network Traffic Analysis (NTA) NDR solution that uses a combination of behavioral modeling, machine learning, security analytics, and global threat intelligence to detect and respond to threats such as ransomware distributed-denial-of-service (DDoS) attacks, unknown malware, and insider threats. Stealthwatch can be deployed on-premises as a hardware appliance or a virtual machine called Stealthwatch Enterprise or cloud-delivered as a SaaS solution called Stealthwatch Cloud.
Three main components make up the core of Stealthwatch Enterprise: the Flow Rate License, Flow Collector, and Management Console. Other optional licenses and components which can be added to enhance functionality include Cisco Stealthwatch Endpoint License—to extend visibility to end-user devices, Cisco Stealthwatch Cloud—to provide visibility and threat detection within the public cloud (AWS, Azure, Google), Cisco Stealthwatch Threat Intelligence License—provides an additional layer of protection against botnets and other attacks, Flow Sensor and the UDP Director components. Stealthwatch licenses are available as a one-, three-, and five-year term subscription, depending on your need and budget.
3. Darktrace Enterprise Immune System
The Darktrace Enterprise Immune System combines real-time self-learning threat detection, automated investigation, autonomous response, and digital visualization capabilities in a single, unified system. It uses AI and unsupervised machine learning to autonomously detect and take action against cyber-threats across diverse digital environments, including cloud, virtual environments, IoT, and industrial control systems. The product can be deployed as a hardware or virtual appliance, and it’s simple enough to use because of its user-friendly GUI. The installation process is painless and takes only an hour to complete, and users can train on the system within three hours.
4. Gigamon ThreatINSIGHT
The Gigamon ThreatInsight is a cloud-native NDR solution that enables organizations to gain network visibility, discover hidden threats even in encrypted communications. In addition, it automates security investigations and responses across inbound, outbound (north/south), and internal (east/west) network communications. ThreatINSIGHT is an easy-to-install, cloud-based SaaS solution with fully managed sensors that can be easily deployed across various environments.
ThreatINSIGHT leverages machine learning algorithms and Gigamon Applied Threat Research to provide insights into hidden threats within the network. ThreatINSIGHT operates a subscription-based licensing model, and each subscription includes a designated technical account manager that ensures you get the most from the solution.
5. Datadog Cyber Monitoring
Datadog is an agent-based on-prem and cloud infrastructure and security monitoring service for cloud applications, servers, databases, tools, and services. Datadog can monitor and detect cyber threats across your applications, network, and infrastructure. With Datadog Cyber Monitoring, you can achieve end-to-end security visibility and threat detection for dynamic cloud environments in a unified platform. Datadog uses ML techniques to identify and flag anomalies in your infrastructure. A free 14-day-trial with full access to all the features is available for download. After that, the software is generally sold through monthly subscription plans based on hosts, events, or logs.
6. IronNet’s IronDefense
IronDefense is an NDR platform that provides real-time visibility and insight across the threat landscape, employs network behavioral analysis that leverages Machine Learning (ML) and Artificial Intelligence (AI) techniques to detect threats missed by traditional cybersecurity tools, and automatically responds to attacks. It is suitable for SMBs, large enterprises, and Fortune 100 companies.
IronDefense fits seamlessly within your existing security infrastructure and integrates well with security information and event management (SIEM); security orchestration, automation, and response (SOAR); endpoint detection and response (EDR); firewalls; and other network security tools. In addition, a 30-day, remote IronDefense Proof-of-Value (PoV) will give your organization insights into how IronDefense can improve your cyber defenses.
7. IBM Security QRadar XDR
QRadar XDR is an extended detection and response (XDR) solution that provides visibility, automation, and contextual insights across endpoint, network, cloud, and applications while working with your existing tools. QRadar is built with open standards and unifies endpoint detection and response (EDR), network detection and response (NDR), and security information and event management (SIEM) in one workflow.
With this tool, security analysts can automate the work of detecting cybersecurity attacks and network breaches, correlating, and investigating threats with purpose-built AI and pre-built playbooks, including automatic root cause analysis and MITRE ATT&CK mapping, view all relevant events in one place, and take action to block the attackers before any significant damage is done. A demo is available on request.
8. Lastline Defender
Lastline Defender is an agentless NDR platform that provides visibility (using lightweight Sensors) into traffic that passes through your network perimeter, uses AI-powered technologies such as network traffic analysis (NTA), intrusion detection and prevention (IDPS), file analysis, and global threat intelligence to detect threats that other network security tools miss, and automatically creates attack visualizations that help your team prioritize response. In addition, you can deploy unlimited sensors in both your on-premises and cloud environments to protect your entire network. Lastline Defender also provides a Pay-As-You-Go (PAYG) hourly pricing option—ideal for organizations that want to scale up or down quickly. A demo is available on request.
9. LogRhythm MistNet
Like Vectra Cognito, LogRhythm MistNet is an NDR solution that uses hybrid analytics that combines machine learning, rules-based detection, and threat intelligence to analyze network, user, and host activity. This holistic approach makes it possible to detect anomalous activities in real-time. In addition, it has a built-in MITRE ATT&CK Engine that eliminates blind spots and monitors your organization’s network in real-time. MistNet NDR can run in standalone SOC mode or the NextGen SIEM Platform. An online demo is available on request.
10. Attivo Networks’ ThreatDefend
The ThreatDefend platform provides comprehensive prevention and detection technology to deny, detect, and derail attackers across a wide variety of attack surfaces. This is made possible by a combination of BOTsink and ThreatDirect deception technology for threat detection, Endpoint Detection Net (EDN) suite to prevent attackers from breaking out from an infected system, and Identity Detection and Response to reduce the attack surface. An online demo is available on request.