In cybersecurity, threat modeling is a proactive approach to identifying, evaluating, and mitigating potential security risks and vulnerabilities in a system, application, or network. The goal of threat modeling is to anticipate possible cyber threats before they can exploit weaknesses, allowing organizations to strengthen their defenses and reduce the likelihood of a successful attack.
The process typically involves several key steps:
- Identify Assets: The first step is to identify and prioritize the critical assets within the system—these could be sensitive data, intellectual property, or systems that are essential for business operations. Understanding what needs to be protected is crucial to focus security efforts.
- Identify Potential Threats: Once the assets are identified, the next step is to consider all possible threats. These could include hackers, insiders, malware, natural disasters, or even accidental errors. The goal is to brainstorm what could go wrong and what malicious actors could target.
- Analyze Vulnerabilities: In this step, vulnerabilities in the system are assessed. This involves evaluating the design, architecture, and code of the system to identify weaknesses that could be exploited by the identified threats. This could include insecure coding practices, weak authentication, or inadequate network segmentation.
- Determine Impact and Likelihood: After vulnerabilities are identified, the next step is to assess the potential impact and likelihood of each threat exploiting those vulnerabilities. This helps prioritize which risks need immediate attention and which can be addressed later.
- Mitigate Risks: Finally, organizations develop strategies to mitigate the identified risks. This might involve applying security patches, implementing access controls, encrypting data, or introducing intrusion detection systems.
Threat modeling is crucial because it helps organizations anticipate and prepare for potential threats, rather than reacting after an attack has occurred.
Why is Threat Modeling Important?
The dynamic nature of cyber attacks makes threat modeling fundamental to security. The attack and defense sides of security are constantly changing. To respond appropriately to this change, organizations need to reassess and evolve their defenses continually. In addition, applications or systems must be designed to be resilient to attacks. However, establishing the appropriate security controls needed to achieve resilience poses some financial implications.
The fundamental principle underlying threat modeling is that there are always limited resources for security, making it difficult to mitigate every threat within a system. It is, therefore, necessary to determine how to use those limited resources effectively. Organizations must prioritize risks and treat them accordingly. A critical factor in determining risk is a threat. Threat modeling helps organizations systematically identify threat scenarios relevant to the system in order to implement effective countermeasures to protect them. This is why threat modeling is essential. It helps security teams understand how systems may be vulnerable and what control fixes are needed to prioritize fixes according to the severity and impact of anticipated threats.
How Threat Modelling Fits into Risk Assessment
Risk assessment identifies security risks by analyzing assets, threats, and vulnerabilities, including their severity and the likelihood of occurrence. On the other hand, threat modeling allows for greater focus on the assets and identifying potential threats and attack vectors that could exploit vulnerabilities found on those assets and their components during risk assessment. In addition, it looks at who would most likely want to attack the asset and how they could successfully do it.
Threat modeling is in fact a form of risk assessment that models aspects of the attack and defense sides of a system or its components. It augments the risk assessment process by generating contextualized threat events with a well-described sequence of actions, activities, and scenarios that the attacker may take to compromise the asset or system. This helps security teams to come up with more targeted controls and countermeasures. The diagram below shows how threat modeling and risk assessment fit together.
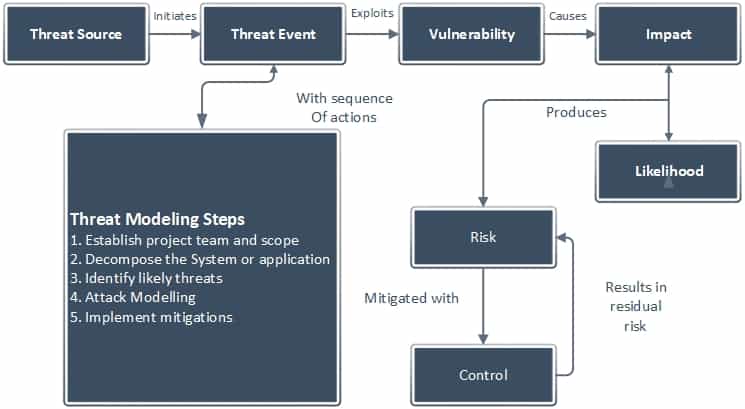
Components of a Threat Modeling Process
Different approaches or methodologies are used for threat modeling; we’ll discuss that in the next section. However, all of these methodologies have some processes or logical flow that they share in common. Let’s now examine these basic logical flow:
Establish project team and scope: The threat modeling team should be as heterogeneous as possible to guarantee a more rounded threat model. It should include key stakeholders such as C-level executives, network engineers, developers, and security managers. Next, define and describe the scope of work, including the technical scope, system architecture, system components, security perimeters, and data flows, before performing threat modeling for the target system. This involves gathering information and demarcating perimeter boundaries.
Decompose the System or application: System decomposition is breaking down a system into its different components. This involves identifying system components, drawing how data flows and dividing out trust boundaries. One of the techniques for decomposing a system is building a data flow diagram (DFD). DFDs help users gain better insights into the system by giving a visual representation that illustrates data flows in the system and the actions users can perform within a system state. Some models rely on process flow diagrams (PFDs) instead of DFDs. Once completed, the visual representation is used to identify and enumerate potential threats.
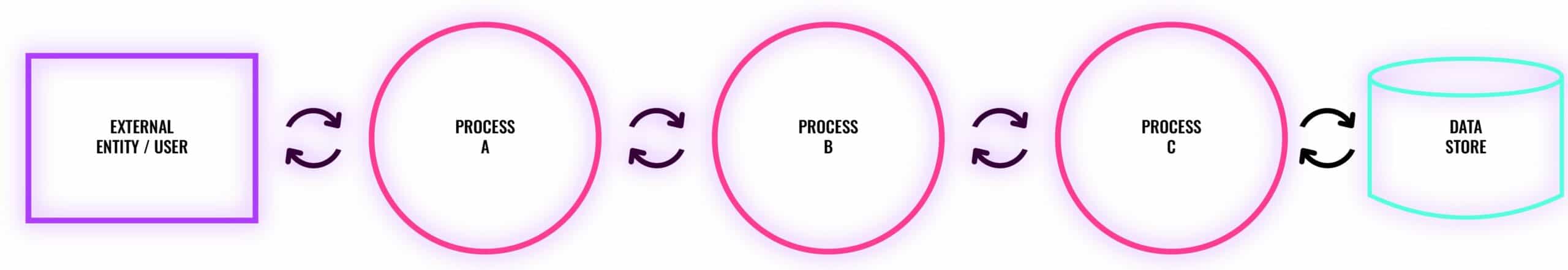
Identify likely threats: Threat Identification involves identifying and documenting threat vectors and events. Then, for all potential targets, determine where hazards exist and use threat scenarios and attack trees to identify possible vulnerabilities that could be exploited. Threat modeling tools can also be used to automate this step.
Attack Modelling: Attack modeling describes an attacker’s intrusion approach so that Users can identify mitigation controls needed to defend the system and prioritize its implementation. After placing threat events relevant to the system, tie them to a possible sequence of attacks. This involves mapping the sequence of attacks, describing tactics, techniques, and procedures, and creating threat scenarios. Attack frameworks such as MITRE ATT&CK or Lockheed Martin Kill Chain can be used to model the attack.
Implement mitigations. By understanding the attack vectors and security risks at various stages, you can apply appropriate controls and countermeasures to mitigate threats or possible attacks or minimize their impact. Develop strategies to contain these threats. This typically includes avoiding the danger, reducing the negative effect or probability of the threat, transferring all or part of the threat to another party, and even accepting some or all of the potential or actual consequences of a particular threat. The opposite of these strategies can be used to respond to opportunities.
Threat Modeling Frameworks and Methodologies
There are several available methodologies and frameworks you can use to perform threat modeling. Threat modeling methodologies can be categorized according to the focus of the approaches. These approaches include those that focus on the assets of the system being threat modeled (asset-centric), those that focus on the attackers (attack-centric threat modeling), and the approaches that focus on the software or the system (software-centric or system-centric threat modeling). Deciding which methods to deploy depends on the system or the types of threats modeled and for what purpose. Below are some of the threat modeling methodologies commonly used today:
STRIDE: Microsoft engineers developed the STRIDE methodology in 1999 to guide the discovery of threats in a system. It is used in conjunction with a model of the target system that can be constructed in parallel. This includes a full breakdown of processes, data stores, data flows, and trust boundaries. STRIDE is an acronym for the types of threats it addresses. The table below is a breakdown of the various threats managed by STRIDE and the associated properties violated:
| Type of Threat | What was Violated? | How was it Violated? |
|---|---|---|
| Spoofing | Authenticity | Pretending to be something or someone you are not |
| Tampering | Integrity | Altering data within a system to achieve a malicious goal. |
| Repudiation | Non-repudiable | Claiming not to be responsible for an action |
| Information disclosure | Confidentiality | Leaking protected information to unauthorized entities. |
| Denial of service (DoS) | Availability | Exhausting or denying access to resources needed to provide service |
| Elevation of Privilege | Authorization | Allowing someone to do something they are not authorized to do |
Table 1.0 | STRIDE threats and the associated properties violated
OCTAVE: The Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) is an asset-and operations-centric threat modeling methodology developed in 2003 at Carnegie Mellon University to help organizations assess non-technical risks that may result from a data breach. OCTAVE consist of the following phases:
- Building asset-based threat profiles—organizational evaluation.
- Identifying infrastructure vulnerabilities—information infrastructure evaluation
- Developing and planning a security strategy–evaluating risks to the organization’s critical assets and decision-making.
With OCTAVE, an organization’s information assets are identified, and the datasets contain attributes based on the type of data stored. OCTAVE is most useful when creating a risk-aware corporate culture. However, it lacks scalability.
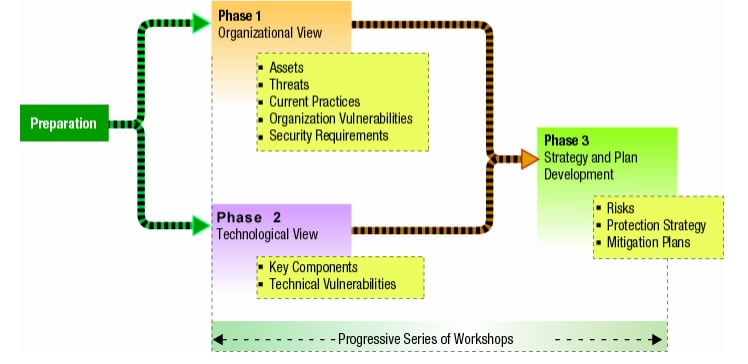
Trike: Trike is an open-source asset-centric framework for threat modeling and risk assessment.
The project began in 2006 to improve the efficiency and effectiveness of existing threat modeling methodologies. Trike is focused on satisfying the security auditing process from a cyber risk management perspective. The foundation of the Trike threat modeling methodology is a “requirements model”—which ensures the assigned level of risk for each asset is “acceptable” to the various stakeholders.
Threats are identified by iterating through a data flow diagram (DFD). Identified threats are grouped into two categories: denial of service or elevation of privilege. The implementation model is then analyzed to produce a Trike threat model.
PASTA: The Process for Attack Simulation and Threat Analysis (PASTA) is a seven-step, attack-centric methodology designed in 2015 to help organizations align technical requirements with business objectives while considering business impact analysis and compliance requirements. The goal of this methodology is to provide a dynamic threat identification, enumeration, and scoring process. PASTA is focused on guiding teams to identify, count, and prioritize threats dynamically. The overall sequence is as follows:
- Define business objectives
- Define technical scope
- Application decomposition
- Threat analysis
- Vulnerability and weaknesses analysis
- Attack enumeration and modeling
- Risk analysis and countermeasures
Once the threat model is completed, a detailed analysis of the identified threats and appropriate security controls can be developed. PASTA threat modeling is ideal for organizations that wish to align with strategic objectives because it incorporates business impact analysis as an integral part of the process.

NIST threat modeling guide: The U.S. National Institute of Standards and Technology (NIST) in 2016 published its own data-centric threat modeling methodology that focuses on protecting high-value data within systems. It models aspects of attack and defense for selected data. In this model, risk analysis is carried out using the following four significant steps:
- Identify and characterize the system and data of interest
- Identify and select the attack vectors to be included in the model
- Characterize the security controls for mitigating the attack vectors
- Analyze the threat model
The guide is targeted at security managers, security engineers/architects, system administrators, auditors, and others responsible for the security of systems and data. According to the authors, “the intent is not to replace existing methodologies, but rather to define fundamental principles that should be part of any sound data-centric system threat modeling methodology.
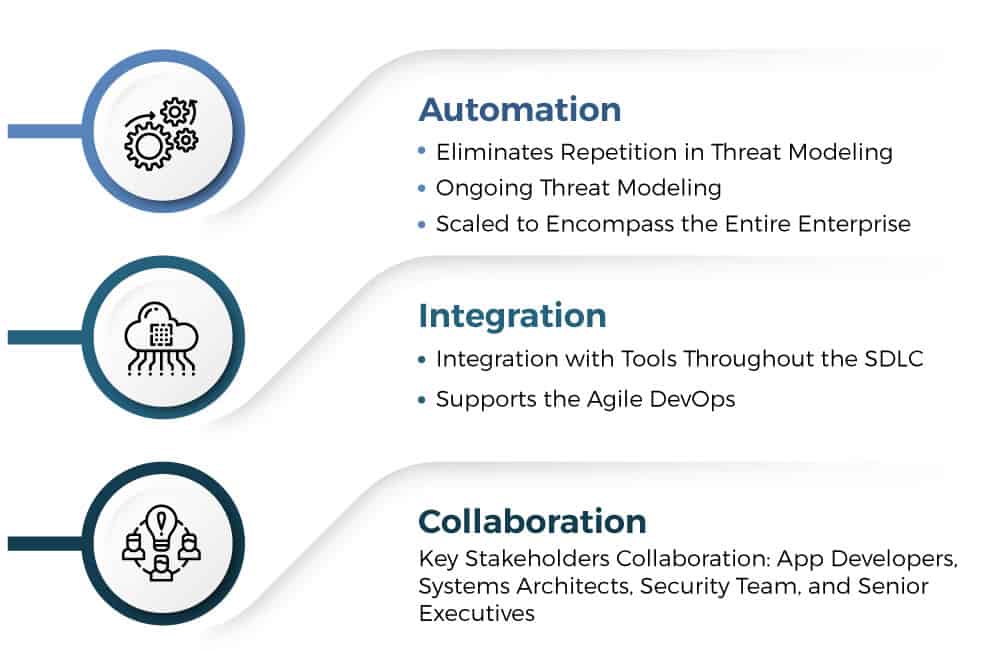
VAST: The Visual, Agile, and Simple Threat (VAST) is a highly scalable modeling methodology that uniquely addresses both developer and infrastructure team concerns. Automation, integration, and collaboration are foundational to VAST threat modeling. VAST is built around ThreatModeler—an automated threat modeling tool designed to integrate into the entire software development life cycle (SDLC). This methodology utilizes two threat models: Application threat models for development teams and operational threat models for the infrastructure teams.
Application threat models for development teams are created with process flow diagrams (PFD)—a flowchart that helps to describe the general flow of a business process and how the user would interact with the system. VAST uses PFDs instead of DFDs, to provide deeper contextual insights and a view similar to an attacker’s. On the other hand, operational threat models utilize the traditional DFDs also presented from the perspective of an attacker.
Choosing the Right Threat Modeling Methodology
With various threat modeling methodologies out there, choosing the right one for your business and environment can be challenging. Not all threat modeling methodologies are created with the same approach. Some focus on the system’s assets being threat modeled, some on the attackers, and some on the system or software being threat modeled.
While all threat modeling methodologies may identify potential threats, the number and type of threats identified will vary significantly, including the quality, consistency, and value received from those threat models. What fits perfectly from a feature and modeling approach standpoint for one organization may not fit for another. To ensure that the threat intelligence is actionable, security teams must decipher which method aligns with their specific business goals and objectives.
You need to consider a variety of factors such as the system or the type of threats being threat modeled, and for what purpose, the modeling approach (asset-centric, attack-centric, or software-centric) that best suits your needs, the desired outcome, ability to scale, capacity to generate reports, and ability to measure the effectiveness of the threat modeling, among others.
Threat Modeling Tools
Threat modeling can be a complex and time-consuming process. However, some tools can automate the process and reduce the time and cost involved. A good threat modeling tool lets users visualize, design, plan for and predict all sorts of potential threats. Microsoft Visio, Excel, and PowerPoint are among the most common tools used for threat modeling. Other commonly used commercial and open-source threat modeling tools include:
1. Microsoft Threat Modelling Tool
Microsoft’s Threat Modelling Tool was designed with non-security experts in mind and is available for free. The tool can plug into any issue-tracking system, making the threat modeling process a part of the standard development process. In addition, it provides clear guidance on creating and analyzing threat models and enables developers or software architects to:
- Communicate about the security design of their systems.
- Analyze those designs for potential security issues using a proven methodology.
- Suggest and manage mitigations for security issues.
2. OWASP Threat Dragon
OWASP Threat Dragon is an open-source threat modeling tool used to create threat models as part of a secure development lifecycle. Threat Dragon follows the values and principles of the threat modeling manifesto.
Pros:
- Completely open source and transparent platform
- Supports popular methodologies like STRIDE
- Has strong community support
- Supports a wide range of integrations
Cons:
- Better suited for non-enteprise environments
Threat Dragon supports STRIDE and other methodologies and can document possible threats and decide on their mitigations.
3. ThreatModeler
ThreatModeler is an automated modern threat modeling tool that implements the VAST methodology. The tool is designed to integrate into an agile software development environment and provide actionable outputs for developers and security teams to identify, predict, and define threats.
Pros:
- Easy-to-use threat modeling
- Can customize threat libraries on a per-project basis
- Integrates with popular tools such as JIRA or Jenkins
Cons:
- The interface can feel primitive at times
In addition, ThreatModeler delivers a holistic view of the entire attack surface, enabling enterprises to minimize their overall risk.
4. securiCAD Professional
securiCAD Professional by Foreseeti enables security teams to design virtual models of existing and future IT infrastructures. The attack simulations on a virtual model, and mitigation testing, provide detailed insights about successful attack paths and most likely kill chains.
Pros:
- Designed with security teams in mind
- Provides a variety of attack simulation options
- Offers a simple yet powerful way to access different mitigation options
Cons:
- Ideal for medium to large security teams
In addition, users can virtually assess security mitigations deployed in securiCAD to find the most effective way to eliminate cyber threats.
5. IriusRisk
Iriusrisk is a threat modeling tool that performs risk analysis and generates a threat model of a software application at the design phase with recommendations on how to address the risk.
Pros:
- Easy-to-use modeling tools
- The Enterprise version includes API access for large projects
- Includes a free version
Cons:
- Better suited for planning and threat modeling
It is a wizard-based drag-and-drop tool that you can use to generate threat maps with insights on what to look for.
6. SD Elements
SD Elements by Security Compass is an integrated risk assessment, secure coding, and threat modeling platform that allows automation of the entire security process while leveraging balanced development automation (BDA). This helps to maximize time and value.
Pros:
- Includes risk assessment tool combined with advanced threat modeling tools
- Can automate many scans, tests, and assessments
- Provides a great mix of time and value
- Best for larger environments
Cons:
- Can take time to fully explore all options and features
7. Tutamen
The Tutamen Threat Modeling Automator is a STRIDE-supported SaaS-based tool designed to enable security at the architectural stage. Their approach is simple: upload a diagram of your system (with its annotated data) in draw.io, Visio, or Excel format, and it will generate your threat model. The developed threat model will identify the elements, the data flow, and the threats and recommend mitigations.
Pros:
- Focuses heavily on threat analysis automation
- A highly flexible SaaS tool
- Can generate detailed threat models based on network diagrams
- Supports the STRIDE framework
Cons:
- Requires a fair degree of technical expertise to operate









