SpyHunter is a powerful anti-malware tool designed to detect and eliminate a wide range of cyber threats, including malware, spyware, ransomware, and other malicious software. It provides users with an effective way to safeguard their systems from harmful programs that can compromise sensitive information, slow down performance, and even cause irreparable damage. SpyHunter is widely recognized for its advanced scanning capabilities, real-time protection, and user-friendly interface, making it suitable for both novice users and experienced cybersecurity professionals.
In this review, we take an in-depth look at SpyHunter, exploring its key features, performance, pricing, and effectiveness in detecting and removing malware. SpyHunter uses a multi-layered approach to cybersecurity, combining traditional signature-based detection with heuristic and behavioral analysis to identify unknown threats. This makes it a versatile tool that can adapt to evolving cyber threats.
SpyHunter’s real-time protection continuously monitors your system for potential security risks, blocking harmful processes before they can cause any damage. Its malware removal tools are equipped to remove even the most persistent threats, including rootkits and spyware that often evade other antivirus programs. Additionally, SpyHunter offers a customizable scanning experience, allowing users to select full, quick, or custom scans depending on their needs.
Whether you’re a home user looking to protect your personal data or a business trying to secure your network, SpyHunter offers a comprehensive solution for proactive malware protection. Read on for a detailed breakdown of its features, pricing, and how it compares to other anti-malware tools on the market.
About SpyHunter
SpyHunter is the main product of Enigma Software Group (ESG). The About page on the Enigma Software site explains that the group is a collection of affiliated companies. The umbrella organization is registered as EnigmaSoft Limited, and it is based in Dublin, Ireland. The company also has offices in Kaunas, Lithuania, and Plovdiv, Bulgaria. The company also markets data protection systems under Cyclonis Ltd, which operates out of the same offices in Dublin. Both companies are private and run by Richard Scarlata and Niall Shanahan.
The company provides a feed of new malware discoveries, such as ransomware developments, on its Facebook page, and it also runs a Twitter feed.
What does SpyHunter do?
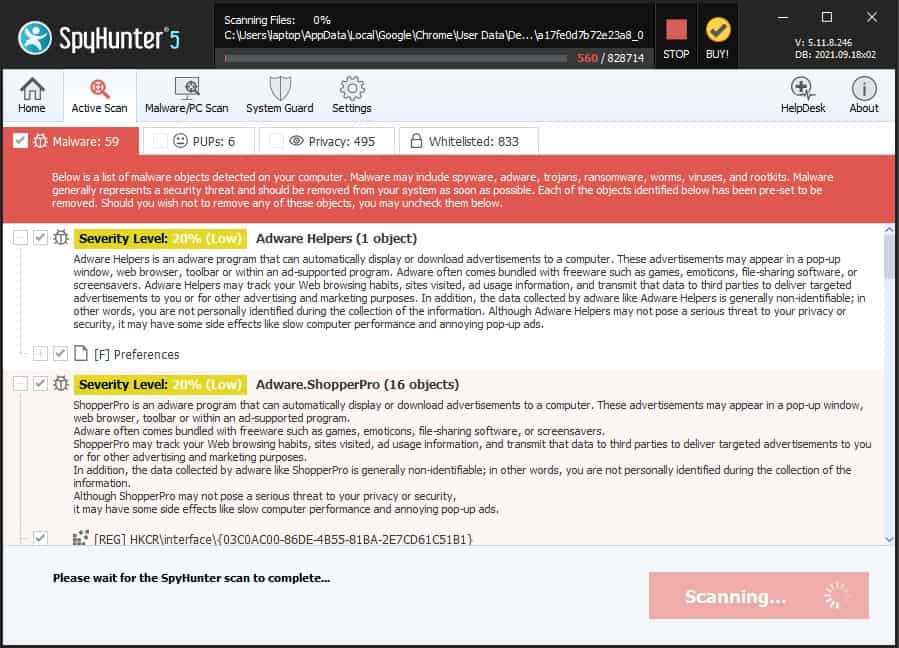
SpyHunter detects and removes malware. A free version of the tool will just detect malware but only remove it after a 48-hour delay.
The functions of SpyHunter include:
- Malware detection and removal
- Live malware monitoring and quarantining
- A vulnerability scanner
These three modules clean up a computer, harden it against future attacks, and maintain controls on new software.
Malware detection and removal
The types of malware that SpyHunter will detect include:
- Trojans
- Ransomware
- Worms
- Viruses
- Rootkits
- Adware
- Spyware
- Keyloggers
- Potentially unwanted programs (PUPs)
As well as looking at the software that runs on a computer, SpyHunter identifies the tracker libraries and cookies that get continually downloaded by websites. Many of these will compromise your privacy. SpyHunter will offer you the option of removing specific, intrusive cookies.
Live software controls
Once it has swept a device, the service remains live, triggering an alert if new malware hits the computer while quarantining that suspicious software.
The system also allows on-demand scans. A scan can be directed at specific folders or drives, and it is also possible to exclude areas of the disk or directory structure from scans.
Vulnerability scanning
The system also includes a vulnerability scanner that assesses the statuses of legitimate software for known exploits used by hackers.
SpyHunter developers have also created a heuristics system that can spot potential problems, known as zero-day threats. These work through the logical consequences of a combination of hardware and software settings that could provide a way in for hackers and malware.
Resolutions to the discoveries arising from a vulnerability scan are usually required to update software, apply an operating system patch, or change system settings. Unfortunately, these remediation steps are not automated.
User controls
All scans produce logs, and these are available for viewing. The actions were taken by the software when it encounters a malware instance can be customized. By default, the system will quarantine suspicious objects. These can be cleared manually and restored or approved for automated removal.
Some malware, such as rootkits, can get so deep into the operating system that they are almost possible to remove without reinstalling the OS. However, other malware includes persistence modules that will reinstall the code as soon as it is removed. These events require particular expertise to remove. The SpyHunter package provides access to a Help Desk that gives you the services of a cybersecurity expert who will manually identify and permanently remove the malware.
SpyHunter deployment options
SpyHunter is available in two formats. The first of these is SpyHunter 5, which runs on the Windows operating system. The second is SpyHunter for Macs, which is designed to run on macOS.
SpyHunter 5
SpyHunter 5 has the following system requirements:
Windows versions:
- Windows XP (32-bit)
- Home
- Professional
- Tablet PC
- Media Center with Service Pack 3 or later
- Windows Vista (32-bit and 64-bit)
- Starter
- Home Basic
- Home Premium
- Business
- Ultimate
- Windows 7 (32-bit and 64-bit)
- Starter
- Home Basic
- Home Premium
- Professional
- Ultimate
- Windows 8 (32-bit and 64-bit)
- Windows 8.1
- Windows 8 Pro
- Windows 10 (32-bit and 64-bit)
- Home
- Professional
- Enterprise
- Education
Minimum Hardware Requirements:
- CPU: 1 GHz CPU
- RAM: 1 GB of RAM
- Disk space: 200 MB
SpyHunter for Mac
The system requirements for SpyHunter for Mac are:
Operating system:
- macOS 10.12 and higher
Minimum Hardware Requirements:
- CPU: 1 GHz CPU
- RAM: 1 GB of RAM
- Disk space: 250 MB
SpyHunter plans and prices
SpyHunter is charged for 6-month subscription cycles. You pay every six months in advance, and the system sets up a repeat billing system, so you will be charged automatically for the next six months once your paid-for service expires.
The price for a 6-month subscription for one device is:
- SpyHunter 5: $42.00
- SpyHunter for Mac: $42.00
A license for multiple devices gets a discount, with a more significant discount for higher numbers of devices per order. The discount rates are:
- 2 – 5 devices: 42.9 percent
- 6 – 10 devices: 50 percent
- 20 – 150 devices: 57.2 percent
- All options include a 30-day money-back guarantee for the first subscription.
There is a free version of SpyHunter available.
Free SpyHunter
You can access a free version of SpyHunter from the EnigmaSoft website. Clicking on the download button for the free version, get an installer downloaded onto your computer. After clicking on the installer, you will be asked to agree to the End Under License Agreement, and then the installation begins.
Once the installation completes, the application for SpyHunter will open automatically.
The system inventory all software and services installed on the device and “whitelists” them. This effectively establishes a list of legitimate software on the device.
After scanning regular software and services, the package hunts through Web-related objects on your computer. These are trackers and cookies. You will be surprised by the number of these tracking systems that SpyHunter discovers.
The system gives a description of each malware instance that it encounters.
SpyHunter strengths and weaknesses
The SpyHunter system is very competent, although it is not the product of one of the big brands. Moreover, its combination of malware protection and vulnerability scanning gives the user a solid chance of avoiding the plague of inconveniences and threats that hackers worldwide inflict on all computer owners.
We assessed the SpyHunter system and derived these points:
Pros:
- A good combination of security functions
- Easy to install
- Includes a vulnerability scanner
- Identifies Web marketing trackers
- Recognizes legitimate software
- Employs heuristics to identify potential system weaknesses
Cons:
- Not a well-known brand
- The initial scan takes a very long time
Alternatives to SpyHunter
Although SpyHunter offers good protection, you might prefer the security of a product offered by the largest cybersecurity software providers. According to Datanyze, the market leaders in the Endpoint Protection market as of September 20201 were:
- Trend Micro Apex One: 37.94 percent
- Symantec Endpoint Protection: 14.25 percent
- McAfee Total Protection: 10.25 percent
However, size is not everything, and there are other important factors to consider when selecting an anti-malware package.
Our methodology for selecting an alternative to SpyHunter
We reviewed the market for endpoint protection systems like SpyHunter and assessed the options based on the following criteria:
- A package that combines several cybersecurity tools
- A live threat intelligence feed
- AI processes to block zero-day attacks
- Services for home use as well as business packages
- An automated system that will deal with problems as well as identify them
- A no-cost assessment opportunity through a free trial or demo system
- A service that offers value for money
As SpyHunter can be used for homes and businesses, the range of alternatives is extensive. Many brands focus on private or commercial customers, so we needed to cover both scenarios to cover replacements for SpyHunter fully.
Here is our list of the five best alternatives to SpyHunter:
- Trend Micro Apex One This is the leading AV globally. It implements AI procedures to work out what is regular activity on an endpoint and what is either malicious user actions or malware. The system doesn’t need a list of malicious processes to look out for because it looks out for potentially damaging actions, such as writing to the registry. This flexible approach is ideal for blocking zero-day attacks. If Apex One discovers a system or software weakness, it will isolate that element until a patch or solution becomes available. Then, obvious malware is killed and removed. Apex One for Business operates in the cloud but requires an agent to be installed on the endpoint. This is available for Windows and Windows Server. The Home Edition installs on Windows, macOS, iOS, Android, and ChromeOS.
- Symantec Endpoint Protection This package is available in two levels, with Endpoint Protection as the lower package and Endpoint Detection and Response as a higher plan. Symantec is a brand aimed at businesses. It has been through some significant changes lately, being taken over by Broadcom, which is gradually rebranding the Symantec stable to its own identity. Broadcom has also changed the product’s name – it is now Symantec End-user Endpoint Security, and the EDR is called Symantec Endpoint Security Complete. These systems use AI to spot anomalous behavior both in user actions and software processes rather than just looking for a list of known malware file names. This package is available for installation on Windows, Windows Server, Linux, and macOS. There is also a cloud-based version that requires an agent to be installed on-premises on Windows and Windows Server.
- McAfee Total Protection This package is aimed at home users with plans for couples and families to cover multiple devices and a straight-up single-device license. The bundle includes a Web safety service that scans Web pages for malicious code, blocks trackers, and provides a VPN service with the AV. The plans also include a password manager, a file shredder, a firewall, and PC optimization systems. The software for McAfee is available for Windows, macOS, Android, and iOS. Unfortunately, there isn’t a free trial, but McAfee offers a 30-day money-back guarantee.
- Bitdefender GravityZone This package is designed for businesses, and there is also a version for home users. It includes a long list of services, including an AV system, a backup service, a vulnerability scanner, and data privacy protection. The full service provides excellent protection against ransomware and intruders as well as traditional malware. This is a cloud-based service, but endpoints require an agent program to get enrolled in protection. Those endpoints can be running Windows, macOS, or Linux. You can get a 1-month free trial of Bitdefender GravityZone. Home users should consider Bitdefender Total Security. This includes a firewall, a system optimizer, a vulnerability scanner, a VPN, intrusion detection, anti-phishing, and anti-fraud protection, plus a data backup system. This package is available for Windows, macOS, Android, and iOS, and you can get it on a 30-day free trial. Bitdefender Free Edition is another option for Windows, macOS, and Android.
SpyHunter FAQs
Is SpyHunter safe and legit?
You might see comments on Quora or Reddit that SpyHunter is a scam. However, you shouldn’t believe every comment on a piece of software that is out there. There overwhelming assessment on all professional review sites is that SpyHunter is a safe and legitimate antimalware system and it is not a scam.
Is SpyHunter a spyware?
SpyHunter is an antimalware system and it has the ability to detect band remove spyware.