As organizations increasingly embrace cloud computing, remote work, and mobile access, traditional network security models are becoming inadequate. Well established perimeter-based defenses, such as firewalls and VPNs aren’t able to full cater to new hybrid network requirements.
The rise of sophisticated cyber threats, coupled with the growing need for seamless user access, has led to the development of Software Defined Perimeter (SDP) solutions. SDP is an innovative security framework that aims to eliminate the concept of a traditional network perimeter, replacing it with a more dynamic and hardy security model that ensures secure access to applications and resources, regardless of location or device.
At its core, SDP works by providing access only to authenticated and authorized users, effectively rendering systems invisible to unauthorized users. It creates a “black cloud” where resources are not directly accessible from the internet, drastically reducing the attack surface. This zero-trust approach, where access is granted based on user identity and device trust rather than network location, is crucial in mitigating risks from external and internal threats, especially in modern, distributed environments.
The best SDP solutions offer a combination of strong authentication, encryption, and visibility, ensuring that both users and devices are continuously verified and granted the least amount of access necessary to perform their tasks. These solutions are highly scalable, allowing businesses to maintain flexibility and agility while ensuring data security and regulatory compliance.
In this guide, we will explore the leading SDP solutions available in the market today, highlighting their features, benefits, and use cases. From small businesses to large enterprises, these solutions provide adaptable, scalable, and highly secure ways to protect sensitive resources and support an increasingly mobile, cloud-centric workforce.
Here is our list of the best SDP solutions:
- Perimeter 81 SDP EDITOR’S CHOICE Provides protection for all hardware elements on a company’s network from a cloud base. This service even marshals internal access to resources by authorized company users because it integrates with access rights management systems including LDAP and Active Directory. Access the live demo
- Twingate SDP (FREE TRIAL) Adds zero trust security to any business’s infrastructure without the need for onsite hardware changes or on-premises software. Start a 14-day free trial.
- NordLayer (GET DEMO) Internet security service that ties together sites, cloud platforms, and remote workers that can implement software-defined perimeter or a full SASE. This is a cloud-based system with device agents. Access the free demo.
- Absolute Secure Access Virtual network system that provides site-to-site VPNs and a ZTA solution.
- Appgate SDP Named a Forrester Zero Trust Wave 2020 leader, this service implements SDP onsite or in the cloud.
- Cisco Software Defined Access (SDA) Supplied by the world’s leading network device producer, this SDP is bundled together with other advanced network management facilities.
- Jamf Connect A secure access solution for a user community that uses macOS and iOS devices.
What is a Software-Defined Perimeter?
In simple terms, a Software-Defined Perimeter (SDP) solution is a security system that creates secure connections between users and the resources they need to access. It does this by individually verifying each user’s identity and granting them access only to the specific resources they are authorized to use.
SDP is a way to conceal internet-connected infrastructure (servers, routers, etc.) so that external entities cannot see it, whether it is hosted on-premises or in the cloud. Rather than focusing on traditional, network-based security, SDP takes a different approach; securing the user, the application, and the connectivity in-between. The goal of the SDP approach is to base the network perimeter on software instead of hardware. An organization that uses SDP is essentially draping a robe of invisibility over its servers and internal resources so that no one can see them from the outside; however, authorized users can still see and access the resources. They must authenticate before visibility and access to authorized services is granted.
SDP is distinct from a VPN system. While VPN is designed to allow users broad access to connect to corporate networks using simple authentication to determine user access, SDP is designed to connect users discreetly to individual resources, using a real-time contextual risk assessment to determine user access. According to Gartner, 60% of enterprises will phase out VPNs in favor of SDP by 2021. An SDP comprises of the following components:
- SDP Client—An application that runs on user devices
- SDP controller—The trust broker between the client and the backend resources
- SDP gateway—Grants users access to requested network resources
The Best Software-Defined Perimeter Software
Our methodology for selecting software-defined perimeter systems
We reviewed the market for SDP software and analyzed the options based on the following criteria:
- Cloud-hosted service with an overview of multiple sites
- Easy-to-use console that can be accessed through a browser
- Integrated access rights manager
- Connection privacy between sites and cloud platforms
- Options for Zero Trust Access (ZTA)
- Free trial, a demo, or a money-back guarantee for a no-obligation assessment opportunity
- Value for money from an SDP tool that offers a range of secure network virtualization options
1. Perimeter 81 SDP (GET DEMO)
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.perimeter81.com
Money-back guarantee: 30 DAYS
Perimeter 81 SDP platform is a scalable hardware-free solution that helps organizations provide secure access to their network infrastructure and digital assets including local and cloud resources from end-point to data-center to the cloud. It offers network visibility, resource access segmentation, and full integration with major cloud providers, giving organizations peace of mind in the cloud. The solution is ideal for SMBs, especially those looking for a modern alternative to traditional business VPN system.
Key Features:
- Integration with Identity Providers or Directory Services: SAML, LDAP, Active Directory, Touch ID, and more
- Client App: Two-factor authentication, automatic WiFi protection, and kill switch
- Authentication Per Device: Pre-screens the current user through app login
Why do we recommend it?
The Perimeter 81 SDP is one solution that you can create with the tools available on the Perimeter 81 platform. The Perimeter 81 system is based around a Zero Trust Architecture, creating secure links between sites, remote workers, and SaaS platforms. This can be interpreted into an SDP virtual network configuration.
The onboarding process is smooth and hitch free. When you sign up with Perimeter 81, you get a full management platform where you can build, manage, and secure your network. To get started, all you need to do is to sign up, invite your team, install the apps, and create user groups. By clicking on the link in the Downloads section of the platform, you can download the app on your preferred platform and follow the wizard to complete the installation. You can give network access to as many team members as possible, assign them to specific groups, and add or remove user permissions with a single click.
Perimeter 81 offers flexible payment plans with billing occurring on a yearly or monthly basis. Sign up process for all plans are commitment-free and has a 30-day money-back guarantee. The table below is a summary of the various subscription plans and associated features.
Price Plan | Cost (billed annually) | Minimum No. of Users | Features |
|---|---|---|---|
Essentials | $ 8 per user/month per gateway | 5 |
|
Premium | $12 per user/month per gateway | 10 |
|
Enterprise | Custom: + $40/month per gateway | 50 |
|
Who is it recommended for?
The Perimeter 81 system is very easy to implement and so it could be managed by the owners of small businesses without any technical skills. The minimum account size is for 10 users. Large multi-site businesses would also benefit from this easy-to-run virtual network system. Other security configurations, synch as ZTA are possible.
Pros:
- Per-User Pricing: Minimum team size of 10 members
- Cloud Firewall: Dedicated static IP address
- Device Posture Checks: Verifies that the device isn’t a security risk
Cons:
- No Free Trial: You can watch a demo instead
EDITOR'S CHOICE
Perimeter 81 SDP is our top pick for a software-defined perimeter solution because it is easy to deploy and manage. This cloud-based service manages all access to all company resources without the need for onsite changes. The Perimeter 81 service integrates with the business’s existing access rights management system to create strong zero-trust protection without blocking out legitimate system users. This tool even controls access to potentially risky wi-fi APs offsite by company assets.
Access live demo: perimeter81.com/demo
OS: Agents for Windows, macOS, Linux, iOS, and Android
2. Twingate SDP (FREE TRIAL)
Twingate SDP enables organizations to implement a more secure modern zero-trust network without changing existing infrastructure, and centrally manage user access to company digital assets, whether they are on-premises or in the cloud. Twingate is delivered as a cloud-based service, and delegates user authentication to a third-party Identity Provider (IdP).
Key Features:
- Global Server Network: 580 points of access worldwide
- Administrator Console: Set up the strategy, create user accounts, assign applications
- Access Control Strategy Options: Role-based or attribute-based
- Activity Logging: Audits of employee activities
Why do we recommend it?
Twingate SDP is a VPN-based service that creates a virtual network across the internet through VPN connections between users, sites, and SaaS platforms that run through the VPN server. Use this package to create a ZTA environment and add on a dedicated IP address to create a perimeter.
No special technical knowledge is required from end-users other than to download and install the client application and authenticate with an existing identity provider, and they’re good to go. The controller handles the rest, negotiating encrypted connections between clients and resources. Once everything is confirmed, users are routed to the appropriate resources.
A key feature of Twingate SDP is that authorization for user access is always confirmed with a second or third component depending on the sensitivity of the decision being authorized. No single component can independently make a decision to allow traffic to flow to another component or resource in your remote networks.
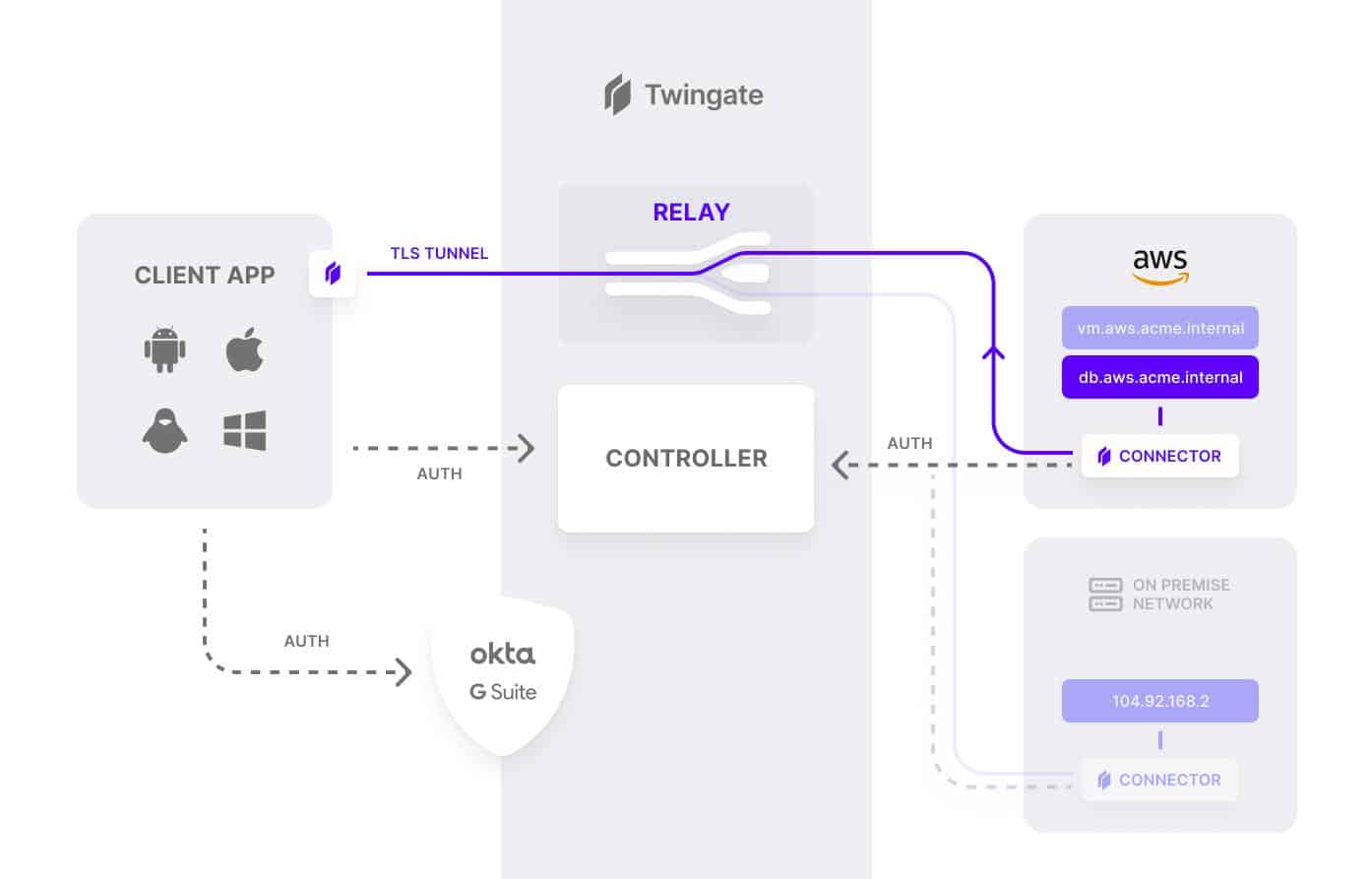
The Twingate SDP solution relies on four components; Controller, Clients, Connectors, and Relays. These components work in tandem to ensure that only authenticated users gain access to the resources that they have been authorized to access.
Twingate SDP is offered in four flexible price plans: Twingate Starter, Twingate Teams, Twingate Business, and Twingate Enterprise. The table below is a summary of the various plans and their features.
Price Plan | Cost (billed annually) | Target Market |
|---|---|---|
Starter | Free | Individuals or very small teams |
Teams | $5 / user / month | Smaller teams that need to replace a VPN for remote access |
Business | $10 / user / month | Larger teams that need more advanced access controls |
Enterprise | Custom | Companies that need comprehensive access controls, detailed auditing, and deployment automation |
Who is it recommended for?
This is a rival system to NordLayer and Perimeter 81 because it is based on VPNs. Most small business owners would be able to set this system up. The Free edition, which is a VPN service, allows up to five users. Higher functions for SDP and ZTA are offered in the paid plans.
Pros:
- Client Agents: Controls access to the system and to individual applications
- Peer-to-Peer Connections: Access is authenticated by the Twingate server but connections aren’t mediated by it
- Single Sign-On: Use Google or Okta
- Free VPN Package: For up to five users
Cons:
- Trial Period Could be Longer: The free trial only lasts 14 days
3. NordLayer (GET DEMO)
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.nordlayer.com
Money-back guarantee: 14 DAYS
NordLayer is a new service from Nord Security. This is the business behind NordVPN, which puts the provider in a great position to exploit the new market for hybrid security solutions. Although security concepts such as SDP and SASE and different from VPNs, the underlying connection security procedures are the same, so Nord Security was already halfway there and just needed to add in an identity and access management component to implement a software-defined perimeter service.
Key Features:
- Toolkit: Supports a range of secure access strategies
- Cloud-Based Access Broker: Links to device-based agents
- Zero Trust Access: Application-level access controls
- Single Sign-On Environment: Removes login fatigue
- VPNs for Connection Protection: Remote access and site-to-site
Why do we recommend it?
NordLayer is similar to the Perimeter 81 service. This provider is the company behind NordVPN and the connection security that Nordlayer uses is based around the same VPN technology. The VPN server acts as a hub between users and applications and the addition of a dedicated IP address creates a SASE.
You get a package of systems that you can choose to thread together in different ways. The idea behind this service is that each user gets an app that forges a secure link through to the NordLayer server. Up to this point, the service is exactly like a VPN.
The difference between NordLayer and NordVPN is that the NordLayer management console provides an access rights manager. This is like a cloud-based Active Directory and it lets you define user groups. This is the game-changer and it turns a VPN service into an SDP.
A full implementation of all of the utilities in a NordLayer package will give you a Secure Access Service Edge (SASE) implementation. The basic package gives you a shared IP address VPN service. To get site-to-site connectivity you need to take out the dedicated IP address service.
The NordLayer server acts as a hub. The provider offers a number of servers around the world, to which all users get access. This speeds up internet performance for international remote workers and branch offices. The VPN-style service means that your network access has a shifting IP address. This isn’t a problem for internal business traffic, in fact, it’s an advantage because it creates a moving target that complicates hacker attack strategies.
The service wouldn’t be suitable for web service hosting. However, separating internal network access from public services is a really good idea, so this restriction shouldn’t put you off.
NordLayer provides the tools to connect together users and applications no matter where those people or systems are located. The package operates a zero trust access system with access rights managed on the NordLayer server. This system allows companies to create a hybrid network, crossing sites and cloud platforms. The network connects users rather than endpoints. Access is through an app and authorized users can get onto the corporate network from any device that has the app on it, no matter where they are. The service uses VPNs to connect devices together securely and integrates an access rights management service that controls connections to applications, whether they are hosted on premises or on the cloud.
Who is it recommended for?
The NordLayer system is very easy to set up and run, so it is suitable for use by small businesses. The minimum number of users for an account with this service is five. So, if your business is too small for Perimeter 81, you should consider this package.
Pros:
- Flexible Infrastructure Planning: Virtualized network options
- All User Access to Applications Hubs: For validation through the NordLayer Server
- Per-User Pricing: Minimum of five team members
- Global Coverage: Network of access servers
- Cloud Firewall: Get a dedicated IP address
Cons:
- Not an Off-the-Peg Solution: Implement ZTA, SDP, SD-WAN, or SASE
The plans are:
Price Plan | Cost (billed annually) | Features |
|---|---|---|
Lite | $8 per user/month per gateway |
|
Core | $11 per user/month per gateway |
|
Premium | $14 per user/month per gateway |
|
Custom | As negotiated |
|
The management console for the service is cloud-based and users need an app to access the system – this is available for Windows, macOS, Linux, iOS, and Android. You can assess the NordLayer system by accessing a demo.
4. Absolute Secure Access
Absolute Secure Access is part of an endpoint management platform that provides content security, secure connections, mobile application management, and unified endpoint management. The platform is divided into two sections; Secure Access is one of those, and the other is called Secure Endpoint. You don’t have to subscribe to both categories of service.
Key Features:
- Connection Security with VPNs: Site-to-site and remote access
- Allocates Applications to Users: Each application won’t even be visible to users who aren’t authorized to use it
- Zero Trust Access: Access rights are bundled into the VPN service
Why do we recommend it?
The Absolute Secure Access Absolute Edge package is a ZTA service that provides you with a secure virtual network across the internet. This is, effectively, an SDP solution. The service will scan devices before allowing a connection, which makes it sake to allow user-owned devices to connect to corporate resources.
The Secure Access service focuses on connection security. This offers two levels of service in its two plans. The first of these is called Absolute Core, which provides a VPN service. The second option is Absolute Edge, which adds in application access rights management to create a Zero Trust Access (ZTA) service. The ZTA system is analogous to a software-defined perimeter solution. The services in the Secure Endpoint service are the types of systems that you would find in a mobile device management (MDM) package – deceive security scanning, tracking, wiping, and locking, secure content delivery, and application containerization.
Who is it recommended for?
The Absolute platform has some very large clients that prioritize network security. These include the British Army, American Airlines, and the New York Police Department. The two divisions on the platform are two separate products and you probably wouldn’t need both. The Secure Access service is less complicated than the Secure Endpoint package.
Pros:
- Access Apps for Endpoints: Windows, macOS, iOS, and Linux
- Virtual Networks: Creates a single private corporate network across sites
- Geolocation Assessment: For GDPR
Cons:
- No Access App for Linux: No app for Unix
Absolute doesn’t publish a price list, so it is difficult to assess the service’s suitability for small businesses or startups. In order to understand the Absolute Secure Access system, you should request a demo.
5. Appgate SDP
Appgate SDP solution is infrastructure agnostic and can be deployed in all environments: on-premises, multi-cloud (AWS, Azure, GPC), virtualized containerized environments, and legacy networks and infrastructure. Appgate was named a leader in the Forrester Zero Trust Wave 2020 report. The entire Appgate SDP solution is designed to be distributed and to offer high availability, and it can be deployed in physical, cloud, or virtual environments. The Appgate SDP integrates seamlessly with third-party applications such as IdPs, LDAP, MFA, SIEM, among others.
Key Features:
- Direct-Routed ZTNA Option: A peer-to-peer strategy with Appgate used as an authentication server
- Cloud-Routed ZTNA Option: All connections hub through the Appgate server
- Invisibility: Single Packet Authorization (SPA) makes your infrastructure invisible
Why do we recommend it?
The Appgate SDP creates a Zero Trust Network Access (ZTNA) solution. This is a solution to the problem of providing secure access to devices that are not directly under the control of the network administrator, such as IoT devices and user-owned devices. The platform also offers ZTA for user access controls to applications.
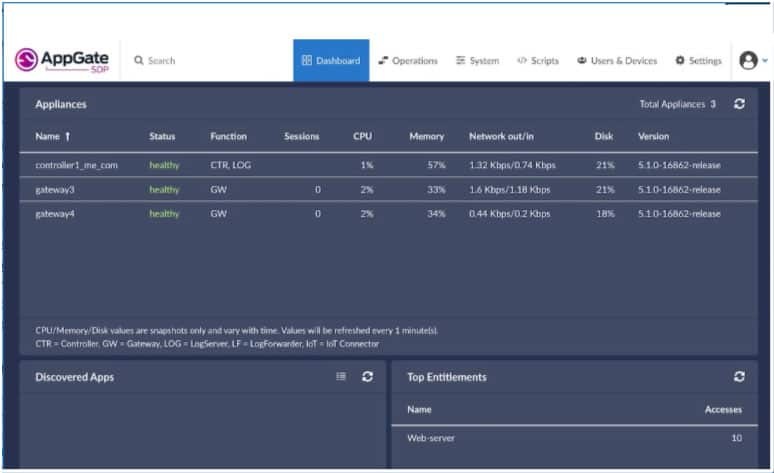
With Appgate SDP, you can control access from any location and to any enterprise resource in a unified policy engine with centralized policy management for servers, desktops, mobile devices, and cloud infrastructure among others. The Appgate SDP consists of three main components:
- Controller: The controller manages user authentication and applies access policies assigned to users based on user attributes, roles, and context, and then issues entitlement tokens listing the resources the user is permitted to access.
- Client: The Apgate SDP client is software that runs on user devices, and connects with Appgate SDP appliances to receive site-based entitlement tokens after successful authentication.
- Gateway: The gateway evaluates user entitlements and opens connections to resources accordingly.
Who is it recommended for?
This is a solution for large businesses. Appgate doesn’t publish a price list, which makes it difficult to assess its platform’s suitability for small businesses. Companies that use ‘headless devices’ and other IoT systems such as security cameras will benefit from the ZTNA solution.
Pros:
- Protects Access to Resources: They can be on your own servers or on the cloud
- Cloaks Resources: Access can only be made through a VPN
- Staged Implementation Approach: Businesses can implement the SDP in stages over time
Cons:
- More Effective for Cloud Access: Not the best choice if all of your users and apps are in the same building
The Appgate SDP is available for a test drive, and the virtual appliances and client software are also available for download.
6. Cisco Software Defined Access (SDA)
Cisco has over the years maintained its leadership position in the networking industry through innovative tools and applications. The Cisco SDA is one such innovative tools that joined the market in recent times. The Cisco SDA is a software defined perimeter solution that allows organizations to bring together users, applications, and devices and apply the right policies to each to secure the network. It is aimed at making enterprise networks more software-driven and simpler to manage.
Key Features:
- Zero Trust Access: Provides connection security and device security scanning
- Access for Headless Devices: Implements secure access for IoT devices
- Activity Logging: Compliance reporting for all application access events
Why do we recommend it?
Cisco Software Defined Access (SDA) is a robust solution from the leading network device provider. The strategy behind this service is to provide ZTNA of IoT devices, secure connections for BYOD, and controlled application access and connection protection for remote and on-site users alike.
The solution is targeted at medium to large enterprises looking to solve the following business IT challenges:
- Network segmentation without the need for MPLS network
- Flexible LAN or host mobility without additional VLANs
- Role-based access control without end-to-end TrustSec
- Common policy for wired and wireless without using multiple tools
- Consistency across WAN, cloud infrastructures, branch offices, and campuses without using multiple tools
The core components that make up the SDA solution are The Cisco DNA Center (Cisco DNA software that powers the controller appliance including a dashboard), Cisco ISE (that enables zero-trust network access), and wired/wireless network infrastructure (such as routers and switches). When you implement Cisco SDA you are essentially creating an overlay network. The DNA center creates an abstraction layer that allows the entire physical network made of switches, routers, and wireless access points to be treated as a virtual switch, which can be manipulated to create virtual networks. The virtual network makes it possible to segment the network and apply specific policies that are centrally managed.
Traditionally, creating and managing these virtual networks were made possible by technologies such as VPNs, VLANS, and segmentation rules. But to apply that consistently across LAN, WAN, and wireless networks can be daunting. Cisco SDA simplifies that whole process by creating virtual networks, which makes it easy to apply policies consistently.
If you are considering the Cisco SDA solution, the steps below will guide you in the ordering process:
- Choose the required Cisco SDA platforms
- Choose the required software licenses to enable Cisco SDA functionality in the device and ISE, available either a-la-carte or with the purchase of Cisco DNA Premier
- Choose the required appliances—Cisco DNA Center (if applicable) and Cisco ISE
- Choose Cisco SDA professional services (optional but recommended)
As with most Cisco products, the setup process is very complex and requires the services of a Cisco expert. Although the product is best suited for the Cisco environment, you don’t need to have an exclusive Cisco network to maximize value. SDA contains multi-vendor support and an API that allows integration with network equipment from other vendors.
Who is it recommended for?
This is a suitable solution for businesses that operate a virtual office, have a lot of remote and mobile users, and allow user-owned devices to connect to the office network. The underlying mechanisms of this package are similar to the straightforward systems of Perimeter 81 and NordLayer but the addition of device security for ZTNA complicates the service.
Pros:
- Device Risk Assessments: Quarantining for endpoints that display suspicious activity
- Create an Overlay Network Across Sites: Supports abstraction and network virtualization
- SD-WAN Option: Ideal for enterprises looking to sync access rules across multiple networks
Cons:
- No Price List: No free trial
7. Jamf Connect
Jamf Connect is part of a suite of tools for the management of fleet devices supplied by Apple. Those devices could be desktops running macOS or mobile devices running iOS. The Jamf Connect system expands the remit of the device management service because it allows remote users to connect with their own computers and for user-owned devices to connect within the office.
Key Features:
- Virtual Network: Part of the Jamf Apple-centric unified endpoint management plans
- Posture Management: Device security scans
- User Authentication Integration: Control of access to on-premises and SaaS applications
Why do we recommend it?
Jamf Connect supports businesses that allow telecommuting to let users running a Mac at home to connect through to corporate resources. The administrator sets up an account for a user and that person then installs an access app. That app links the user’s local credentials to the global SSO account.
As with any typical ZTA system, this tool provides connection security and authentication. The core unique feature of this system is that it allows users to link the local credentials that they use to access their device with a corporate single sign-on mechanism.
The Jamf Connect system provides three security features. These begin with connection security, which is provided by a VPN built into the access app. The second is access rights management, and the third is device security scans. So, the device is verified as secure and virus-free before it is allowed to be used by an authorized user to access a specific list of applications.
The user access app for the Jamf Connect system is available for Macs and also for iPads and iPhones. The same user will probably have different local credentials on each device, however, once each app is set up, logging in to that device will ripple through to the corporate SSO. The app verifies the validity of the local credentials for that device.
Who is it recommended for?
The per-device pricing model of Jamf Connect makes the package scaleable and suitable for businesses of all sizes. However, there is a minimum number of devices for an account, which Jamf doesn’t reveal until you are already into the sign-up process. The tool is only suitable for managing Apple devices and won’t work on Windows or Linux.
Pros:
- Access Permitted to the User: Not tied to any single device
- Will Work for BYOD as Well: Also offers a separate BYOD package
- Single Sign-On: Reduces logon fatigue
Cons:
- Only for Apple Devices: Doesn’t work on Windows or Linux
Jamf Connect is priced per device and you can assess it by accessing a demo.
Choosing the right SDP software solution for your business
With a variety of SDP products out there, choosing the right one for your business and budget can be challenging. Like most network security solutions, not all SDP solutions are created equal.
What fits perfectly from a price, feature, and functionality standpoint for one organization may not fit for another. You need to consider a variety of factors, some of which include:
- What deployment model best suits your environment—cloud or on-premises?
- How does the SDP solution implement zero-trust network access?
- Does the SDP solution integrate with your existing network infrastructure?
- Does the SDP solution require a dedicated appliance for cloud connectivity?
- Is vendor support available in your region, and to what extent?
- What is the total cost of ownership?
Hopefully, this will guide you in the process of choosing the right solution for your business.
See also: Best Access Rights Management Software