Anyone who is familiar with networking will have heard of the SNMP protocol. SNMP is a type of protocol that allows administrators to monitor the health of hardware and software. SNMP-enabled devices can be monitored remotely with network monitoring tools to keep track of performance and availability. MIBs and OIDs are some of the secret ingredients to this critical protocol.
SNMP has several components below the surface that enable performance information to be relayed back to the end-user. SNMP agents, SNMP managers, MIBs, and OIDs all work together to make these transfers possible. In this article, we will look at what MIBs and OIDs are, and what they do. However, before we do, we need to look at what SNMP is.
What is SNMP?
Simple Network Management Protocol (SNMP) is a standard protocol used for monitoring, managing, and configuring devices on a network. It enables network administrators to collect data, monitor performance, and identify issues on devices like routers, switches, servers, printers, and more.
SNMP operates on a client-server model, where the SNMP manager (client) communicates with SNMP agents (servers) installed on network devices. It uses Management Information Bases (MIBs), which are structured databases containing hierarchical information about the device’s components and their status.
Key Components:
- SNMP Manager: A central system that issues requests to gather data and control network devices.
- SNMP Agent: Software running on a managed device that responds to requests from the manager and can send alerts (traps) for specific events.
- MIB: Defines the data objects that can be managed on a device.
SNMP was first released in 1988. The standard was defined in three documents that were published by the Internet Engineering Taskforce (IETF). That organization’s specifications are known as “requests for comments” and they are serialized as “RFCs.” The first incarnation of SNMP is laid out in RFC 1065, RFC 1066, and RFC 1067. The protocol has been developed further since that date.
SNMP Versions:
- SNMPv1: The original version, offering basic functionality.
- SNMPv2: Improved performance and error-handling but lacks strong security; also known as SNMPv2c.
- SNMPv3: Adds robust security features like encryption and authentication.
SNMP uses a simple set of operations, including GET (to retrieve data), SET (to configure settings), and TRAP (to notify the manager of significant events).
Overall, SNMP is vital for maintaining network health, optimizing performance, and ensuring quick responses to network issues.
SNMP Messages
The relationship between the SNMP manager and the SNMP agent is based on messages and commands. These messages come in a range of different forms. Some of the messages exchanged by the two components are listed below:
- GET – Sent when the SNMP manager is attempting to take information from the MIB to determine the value of a variable.
- RESPONSE – The agent sends a RESPONSE to the SNMP manager when replying to a GET request. This provides the SNMP manager with the variables that were requested originally.
- GETNEXT – The SNMP manager sends this message to the agent to get information from the next OID within the MIB tree.
- GETBULK – The SNMP agent uses the GETBULK message to pull data tables by using lots of different GETNEXT commands.
- SET – SET is a message sent by the SNMP manager to the agent to change configurations and issue commands.
- TRAP – An alert sent by the SNMP agent to notify the SNMP Manager when an event happens within the device.
See also: SNMP explained
What is a SNMP MIB?
A MIB or Management Information Base is a formatted text file that resides within the SNMP manager designed to collect information and organize it into a hierarchical format. The SNMP manager uses information from the MIB to translate and interpret messages before sending them onwards to the end-user.
Resources stored within a MIB are referred to as managed objects or management variables. The simplest way to think of a MIB is as the central hub of data inside the device. The MIB contains all of the performance data that is accessed when loading up a network monitoring tool.
What is a SNMP OID?
Inside the MIB there are many different managed objects which can be identified by an OID or Object Identifier. An OID is an address that is used to differentiate between devices within the MIB hierarchy. The OID is used to refer to unique characteristics and navigate through variables on the connected device. The value of these identifiers varies from text to numbers and counters. There are two main types of Managed Objects:
- Scalar – A single object instance such as the device name determined by a vendor
- Tabular – Objects with multiple OID results for one OID
These are often depicted as a tree. An OID is formatted in a string of numbers as shown below:
1.3.6.1.4.868.2.4.1.2.1.1.1.3.3562.3
These numbers each provide you with a piece of corresponding information. For instance:
Iso (1) .org (3) .dod (6) .internet (1) .private (4) .transition (868) .products (2) .chassis (4) .card (1) .slotCps (2) .cpsSlotSummary (1) .cpsModuleTable (1) .cpsModuleEntry (1) .cpsModuleModel (3) .3562.3
OIDs almost always begin with the same sequence of numbers; 1.3.6.1.4.1. We’re going to look at what these numbers mean in further detail below:
1 iso - ISO is the name of the group that launched the OID standard .3 org - Organization specified next to this figure .6 dod - The US Department of Defense .1 internet - Determines that communication will be through the internet .4 private - States that the device is manufactured by a private company .1 enterprise - States that the manufacturer is an enterprise
Most of the time OIDs will be provided by the vendor you purchased your device from.
SNMP Get requests and SNMP Traps
Pulling data from devices with SNMP can be done one of two ways; with an SNMP Get request or an SNMP Trap. An SNMP Get Request is where the user polls the device for performance data. Once the SNMP agent receives this request it sends back OIDs that can be read by an SNMP monitoring system.
WIth SNMP traps, the SNMP agent notifies the SNMP manager automatically once a significant event occurs on the device. Traps are important because they are sent to the SNMP manager without being polled. Consequentially, traps help to keep the user updated on changes within a device.
Without SNMP traps devices could only hand over data when they are polled. SNMP traps make use of MIBs as well. These MIBs have their own alert conditions that reside within the device. The SNMP monitoring system needs to have these MIBs configured or they won’t be able to access traps sent by the device.
See also: What are SNMP Community Strings?
How to use SNMP MIBs and SNMP OIDs
As we discussed above, every SNMP-enabled network device will have its own MIB table with many different OIDs. There are so many OIDs in most MIBs that it would be next to impossible to record all of the information. Instead of doing this manually, you have to use a network monitoring tool like Paessler PRTG Network Monitor or SolarWinds Network Performance Monitor.

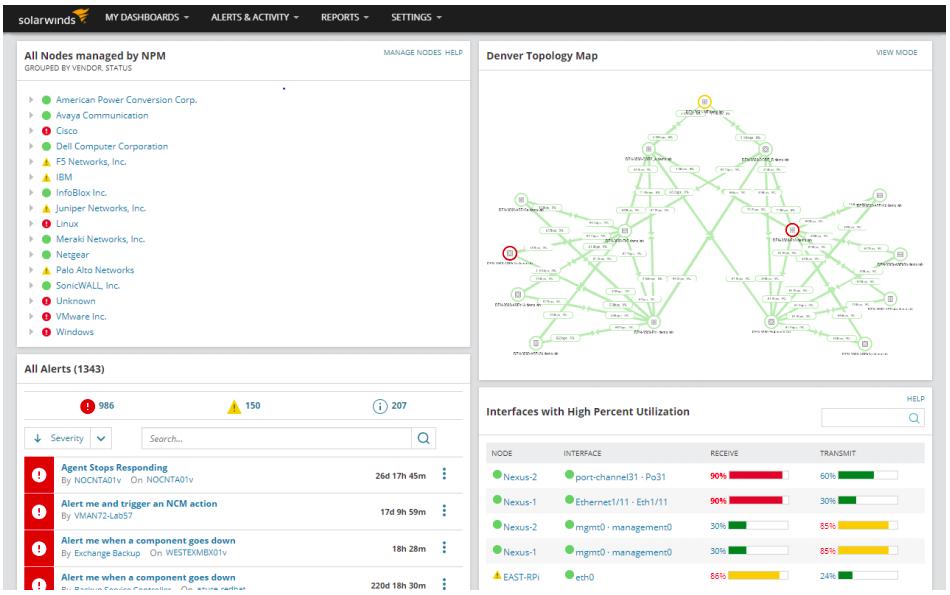
SNMP monitoring tools are designed to take data from MIBs and OIDs to present to you in a format that is easy to understand. Get requests and SNMP traps provide network monitors with raw performance data which is then converted into graphical displays, charts, and graphs. As such, MIBs and OIDs make it possible for you to monitor multiple SNMP-enabled devices from one centralized location.
MIBs and writing your own SNMP MIBs
One of the interesting things about MIBs is that you can create your own MIBs. When you purchase a new device you aren’t confined to using the MIBs that come out of the box. However, to create your own MIB you need to know which objects you want to include within it. You can write this down as a list. Once you’ve written out a list of objects you then have to determine the MIB’s place within the larger OID hierarchy.
The new MIB needs to have its own place within the tree where it won’t collide with any preexisting MIB. The best way to write a MIB is to use an existing MIB as a template. Changing the names and definitions within the MIB provides the user with a strong basis to move forward with. If you decide to go this route it is a good idea to run it through a MIB syntax checker to make sure it works.
MIBs and OIDs: Cogs in the machine
While the premise of SNMP is relatively simple, the architecture can be deceptively complex at times. The critical thing to remember is that the SNMP Manager and SNMP Agent relationship makes sure that the user can monitor multiple devices from one location.
When you load up a network monitoring tool SNMP agents are sending data from all over the network. The information you see on screen is being fed from SNMP traps and Get requests. You may be viewing this data in the form of graphs and charts but this data is actually recorded within MIBs and identified with OIDs.
Data in the MIB is identified with an OID so that network monitors can take the exact information they need. Without an ID Get Requests would be impossible because the monitoring tool wouldn’t be able to find variables within the MIB. MIBs and OIDs are an essential part of the SNMP architecture. These two components are vital for enabling you to monitor network infrastructure and run troubleshooting.
See also: A Guide to UDP (User Datagram Protocol)
SNMP MIBs & OIDs FAQs
How does a MIB browser work?
A MIB browser interprets the implied tree structure of the OID into an actual visible tree. A good MIB browser should give you the meaning of each OID code.
What Port Numbers does SNMP use?
SNMP Managers broadcast requests and receive responses on UPD port 161. Traps are sent to UDP port 162.
How do I convert MIB to OID?
MIBs are written in the OID format. In order to read a MIB, you need to load it into an MIB browser, which will make the OID structure visible.
Is an SNMP MIB OID value confidential?
SNMPv3 is encrypted. However, earlier versions travel around the network in plain text and so are not confidential.