Shape Security, a leading provider of AI-driven fraud prevention and bot mitigation solutions, was acquired by F5 in a landmark deal completed in 2020. Shape was renowned for its ability to use machine learning and behavioral analytics to detect and prevent a wide range of cyberattacks, including fraud, account takeovers, and bot-driven abuse. Its solutions were particularly effective in mitigating the impact of bot attacks that target web applications, mobile apps, and APIs, which are increasingly common in today’s threat landscape.
The acquisition by F5, a global leader in application services and delivery, was part of F5’s strategy to expand its security offerings and strengthen its position in the application protection market. With the integration of Shape’s capabilities, F5 aimed to provide more comprehensive and intelligent security solutions to businesses worldwide.
Following the acquisition, Shape’s flagship product, Shape Enterprise Defense, evolved into F5 Distributed Cloud Bot Defense. This rebranding marked a significant milestone in the integration of Shape’s AI-powered fraud and bot detection tools into F5’s larger cloud-native application security portfolio. F5 Distributed Cloud Bot Defense continues to use Shape’s machine learning models to detect and mitigate bots and fraud in real time, but now it is also part of F5’s broader cloud-native security ecosystem.
F5 Distributed Cloud Bot Defense offers businesses the ability to protect web and mobile applications from malicious bots and automated attacks, improving fraud prevention, login protection, and API security. By leveraging F5’s global infrastructure, the solution can provide fast, scalable protection against sophisticated bot attacks while minimizing false positives.
The acquisition of Shape Security by F5 and the transformation of Shape Enterprise Defense into F5 Distributed Cloud Bot Defense significantly enhanced F5’s security offerings, providing organizations with advanced bot mitigation and fraud prevention solutions designed to secure the modern web ecosystem.
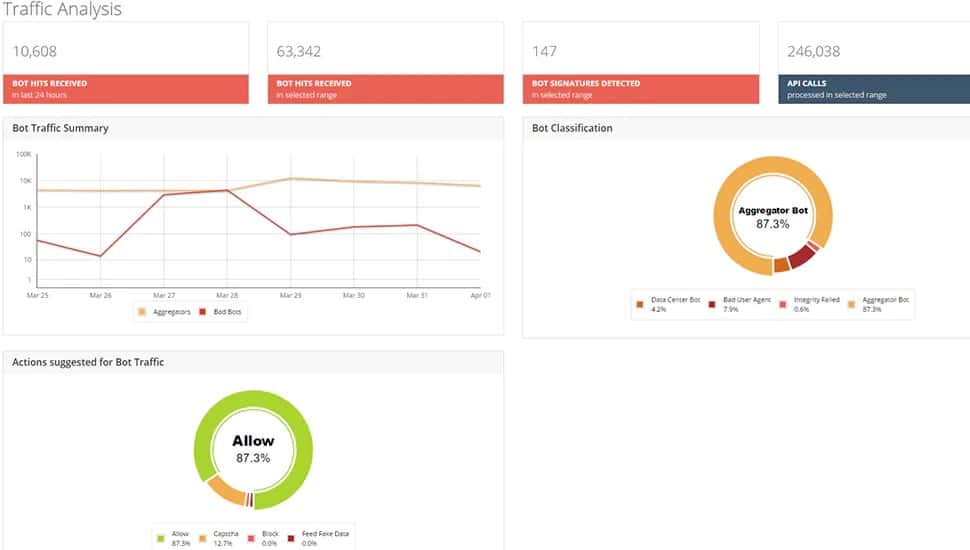
Shape Security bot management
Shape Security operates as a proxy, which assesses traffic before it gets to the protected Web server. It can protect APIs and mobile apps as well as websites.
Unlike many bot management systems, Shape Security doesn’t guard against DDoS attacks. It focuses on commercial fraud. The Shape Security system protects against:
- Fake accounts
- Account takeover attempts, such as credentials stuffing
- Card fraud
- Gift card cracking
- Marketing fraud
- Inventory hoarding
- Content scraping
These services are particularly useful to eCommerce sites, that issue accounts to buyers and has a shopping cart feature. The Shape Security system attempts to identify which transactions are being performed by automated processes rather than by humans. The system also puts actions into content, to identify malicious actions, which could also be implemented by humans.
The Shape Security system works a little differently for APIs because the traffic flow goes directly to the API, which then refers to the Secure Security proxy for transaction analysis.
The Shape Security process starts with Shape Defense Engine. This package has a database of attack vectors to look for. The first action performed by this module is to check through a blacklist. This list of known transgressors is centralized among all of Shape Security’s customers, so the system doesn’t just apply to individual accounts. Shape Security has a large number of customers and the system identifies four billion bot transactions per week.
As bots tend to operate worldwide campaigns, this blacklist is very effective. It is constantly updated and so as soon as a cyber scammer begins a campaign and hits one of the sites that Shape Security protects, all of the client community is immunized.
The efficacy of the blacklist is important because you don’t want a security system to slow down the response times of your Web services. The slightest inconvenience can make a customer give up and switch to a rival’s site.
For the next phase of the Shape Security system, the service uses machine learning to define normal human movements on a site. It then looks for deviations from that standard. Activity that misses the standard pattern gets further scrutiny and that even includes the intervention of human analysts.
Remember that Shape Security pools intelligence between customers. That means that the detection effort is distributed. As bot campaigns move through the Web and apply to many sites, scrutiny only needs to be applied once to record an attack identifier. The likelihood of each protected site being a study lab for bot detection is very slight and so the blacklist will be the main protection mechanism for most customers.
Shape Security deployment options
The primary deployment option for Shape Enterprise Defense is as a SaaS package, hosted on the Shape Security server. It is also possible to get the code installed on your site as a proxy server. This is loaded onto a network appliance or installed as a virtual appliance. The service can also be accessed as an API.
F5 operates a product line called Silverline. This is a managed service that includes technicians to run the software. Essentially, this is a Security Operations Center on contract and the managed version of Shape Enterprise Defense is called Silverline Shape Defense. You can add other F5 security systems to the package.
Shape Security prices
F5 doesn’t publish a price list for the Shape Enterprise Defense system. Your options for getting to know more about the service include:
Shape Security strengths and weaknesses
Shape Security has a good track record and an impressive client list. We have identified several good and bad points about the Shape Enterprise Defense service.
Pros:
- Easy to set up and no maintenance requirements
- Fast visitor assessments
- Protects websites, mobile apps, and APIs
- Managed service available
- Uses AI for low false-positive reporting
Cons:
- Doesn’t block DDoS attacks
Alternatives to Shape Security
You certainly should consider Shape Security for your bot protection system. However, whenever you are purchasing any kind, it is always a good idea to consider several options.
Our methodology for selecting an alternative to Shape Security
We reviewed the market for bot detection systems like Shape Enterprise Defense and analyzed the tools based on the following criteria:
- A blacklist
- Machine learning for activity baselining
- Fast activity scanning
- A reputable provider
- Managed service option
- A free trial or a demo system for a risk-free assessment
- Value for money, represented by an innovative bot detection service at a fair price
With these selection criteria in mind, we looked for systems that can identify and block bot activity and defend against automated fraud attempts on websites, mobile apps, and APIs. We were particularly interested in systems that could go one better than Shape Security and identify DDoS traffic as well.
Here is our list of the best alternatives to Shape Security:
- Cloudflare Bot Manager EDITOR’S CHOICE This cloud-based service is part of a bundle of tools for website owners that also includes a free SSL certificate, a content delivery network, and a DNS service.
- Reblaze Bot Management A remarkably fast bot blocker that operates as a proxy and can defend against DDoS attacks as well as Application-level fraud.
- DataDome A plug-in that provides bot detection with an adjustable series of 15 tests and four preset scanning routines.
- Imperva Web Application Firewall This bot protection system is offered as a SaaS platform but can also be hosted on-site or on a cloud account.
- Radware Bot Manager A plug-in bot detector that looks for DDoS traffic and automated fraud attempts.
You can read more about each of these systems in the following sections.
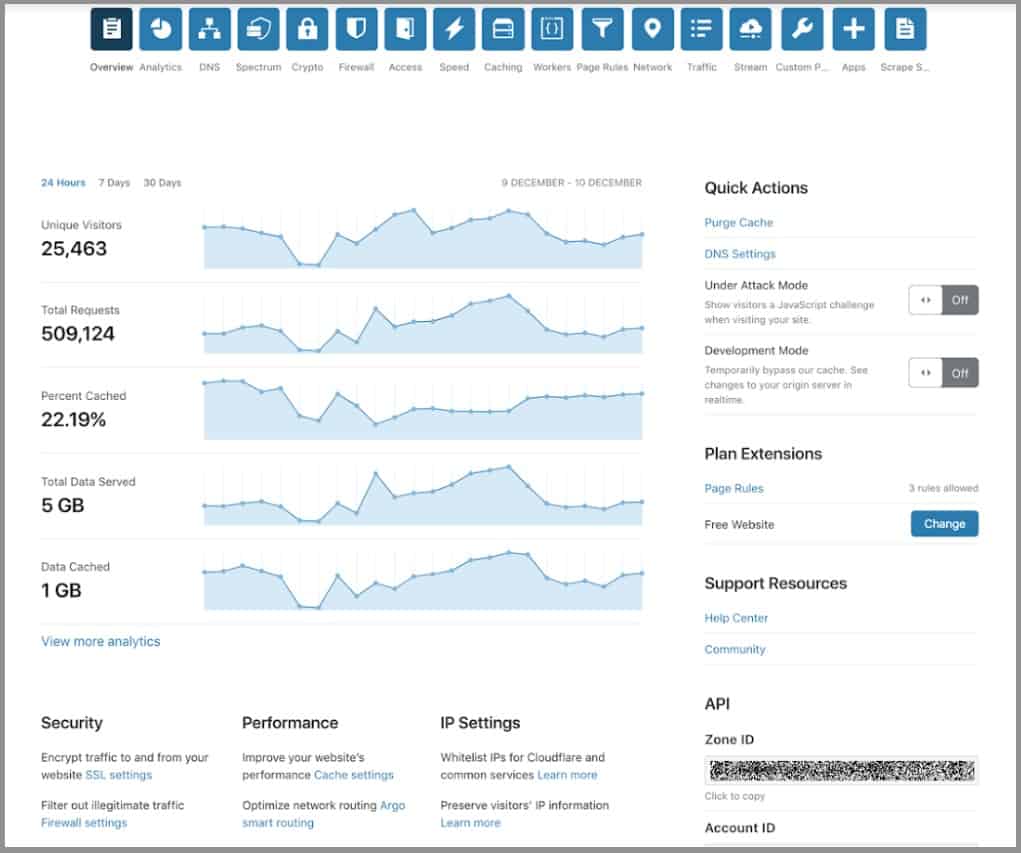
1. Cloudflare Bot Manager
Cloudflare Bot Manager is offered as part of a package called Cloudflare Application Services. Cloudflare is particularly strong on DDoS protection and it runs its DNS service. Both of these elements in the package are essential for websites. The bundle also includes a content delivery network (CDN).
Key Features:
- Service Bundle: Offers an integrated suite including CDN, DDoS protection, and DNS management.
- Always On: Ensures that your site remains accessible at all times, despite attacks.
- DDoS Defense: Effectively absorbs and mitigates DDoS attacks, protecting your website.
- Blacklisting Bots: Utilizes an extensive and constantly updated blacklist to block malicious bots.
- Rapid Scanning: Quickly identifies and blocks potential threats to maintain site integrity.
Why do we recommend it?
Cloudflare Bot Management provides a way to spot fake users without having to present a CAPTCHA challenge to every website visitor. The Cloudflare system supports millions of websites around the world and gathers data from all bot detection units to generate a bot fingerprint blacklist. Other detection methods continuously analyze traffic and blacklist new sources of bot activity.
Cloudflare processes 28 million HTTP requests per second. This is a large volume of traffic and the company operates more than 200 data centers around the globe. Customers get their websites copied and hosted at several of these locations – not all of them. The service guarantees speedy delivery and constant availability.
Incoming traffic that is part of a DDoS attack can be instantly recognized by their format. As these packets have to be received to be identified, the main strategy of Cloudflare to manage DDoS attacks is to just absorb them. Malformed connection requests just don’t get passed on to the Web server.
The next task in the bot management cycle is to check through a blacklist. This weeds out bots very quickly. The large user community of Cloudflare means that the service’s blacklist is very large and constantly updated. The first two steps in the bot detection process used by Cloudflare take care of the majority of attacks.
Detailed scans look through the remaining activity that is allowed through to the protected website. The system looks for signs of content scraping, account takeover attempts, inventory hoarding, and payment and card fraud. If malicious activity is detected, that actor gets added to the blacklist. The system uses fingerprinting that combines factors about the attacker rather than its IP address. These identifiers include operating system type and version browser brand and version, and add-on profile.
As well as bot management, a CDN, and DNS management, the Cloudflare Application Service’s bundle includes a free SSL certificate and SSL management. The package is available in four plans and the first of these is Free.
Who is it recommended for?
The Cloudflare system is accessible to all businesses. There is a basic bot detection service that is provided for free and higher plans add on more sophisticated detection services. However, as the basic plan accesses the blacklist, this should be enough for most website owners.
Pros:
- Complimentary SSL: Includes a free SSL certificate enhancing website security.
- Global Traffic Management: Leverages over 200 data centers worldwide for rapid content delivery.
- DDoS Protection: Specializes in absorbing and mitigating DDoS attacks effectively.
- Scalable Plans: Offers multiple plan options, including a free version suitable for various business sizes.
- Community-Driven Updates: Benefits from a large user community for timely updates on bot threats.
Cons:
- Scanning Delays: Intensive visitor scans may result in delays, affecting user experience.
EDITOR'S CHOICE
Cloudflare Bot Manager is our top pick for bot management because it not only provides robust DDoS protection but also offers comprehensive services such as DNS management and a content delivery network (CDN). The integration of these services enhances the overall security and performance of websites.
Additionally, its ability to handle vast volumes of HTTP requests ensures reliability and swift content delivery across its extensive network of data centers. What I particularly appreciate is the way Cloudflare handles bot management without heavily relying on CAPTCHA, making the user experience smoother while maintaining security.
Download: Access the Free Plan
Official Site: https://www.cloudflare.com/products/bot-management/
OS: Web-Based
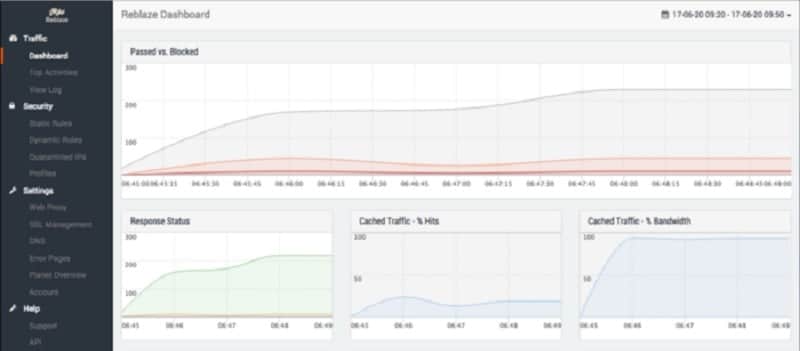
2. Reblaze Bot Management
Reblaze Bot Management is remarkable for the speed with which it processes each HTTP request – 0.5 milliseconds. This system involves a private cloud element, which is hosted on your account, and a CDN, which accelerates the delivery of websites.
Key Features:
- DDoS Protection: Blocks distributed denial of service attacks efficiently.
- Rapid Scanning: Processes each HTTP request in 0.5 milliseconds.
- Fraud Detection: Identifies various fraudulent activities.
- Account Takeover Prevention: Detects and mitigates unauthorized account access.
Why do we recommend it?
Reblaze Bot Management is part of a proxy service that filters traffic before it reaches your Web server. This is a multi-stage service that also provides a Web application firewall and DDoS protection. Reblaze also offers a content delivery network, which serves your site from other locations and keeps traffic off your Web server completely.
One of the reasons for Reblaze’s fast processing is that it can eliminate a lot of bot traffic, such as DDoS attacks straight away. It also has a large blacklist. The remaining tests of Reblaze look at the Application Layer and identify account takeover activity, click fraud, scalping, inventory hoarding, card fraud, and content scraping.
The account dashboard allows you to adjust the scanning process through options such as whitelisting. Data in the dashboard reports on all activities. It shows the traffic that was blocked and it also details the activities of permitted visitors, which is a useful tool for marketers and Web designers.
Reblaze is available for a 30-day free trial.
Who is it recommended for?
This system is competent, fast, and comprehensive. However, the company doesn’t provide a price list, which can be off-putting for many businesses. The company is also competing directly with Cloudflare, which is a difficult service to beat.
Pros:
- Comprehensive CDN: Accelerates website delivery through a content delivery network.
- Customizable Filtering: Allows blacklisting and whitelisting to refine traffic management.
- Detailed Traffic Analysis: Provides insights into both blocked and permitted traffic.
- High Availability: Ensures constant protection and uptime.
Cons:
- Pricing Transparency: The company does not publicly list its pricing.
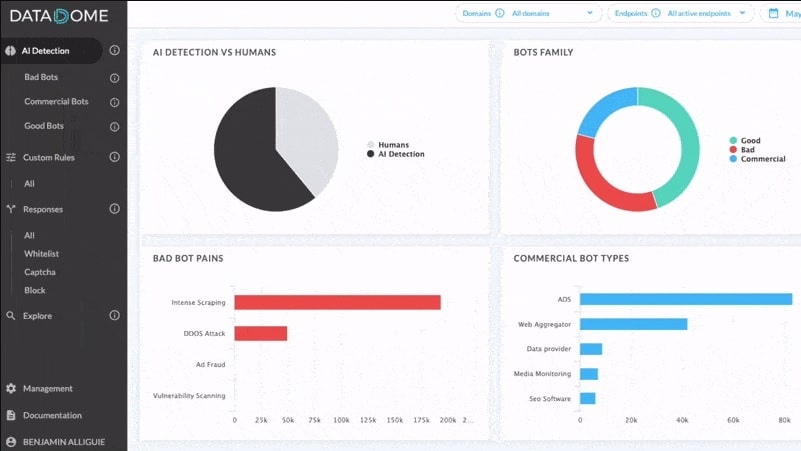
3. DataDome
DataDome is an evaluation system that operates as a plug-in. This service can protect websites, mobile apps, and APIs. You need to receive traffic into your system and call in the DataDome assessment to scan each packet so it won’t block DDoS attacks.
Key Features:
- Comprehensive Testing: Offers a suite of 15 different tests to assess and mitigate bot activity.
- Customizable Scans: Allows users to choose from preset scan combinations tailored for specific threats.
- Fraud Detection: Identifies and blocks fraudulent activities across websites, mobile apps, and APIs.
Why do we recommend it?
DataDome is a reference service instead of a proxy, so it takes a different approach to those of Reblaze and Cloudflare. All traffic goes to your Web server, which will have a plug-in from DataDome. Each arriving request gets referred to the DataDome unit, which checks back with the DataDome server. The result is a pass or fail signal.
DDoS is one of the bot activities that DataDome can detect. However, you will need to make other arrangements to prevent your Web server from being overwhelmed.
Typically, a DataDome assessment takes two milliseconds per incoming request. The tool offers a menu of 15 tests but not all of them will be implemented for every scan. You can decide which individual tests to apply or select one of four pre-set combinations that are organized to deal with specific situations.
The list of tests performed by DataDome includes a reference to a blacklist. If the source of a transaction is on that list, it can be shut down immediately, so the assessment doesn’t always need to run through all of the designated tests.
DataDome performs fraud detection and also detects scalping, inventory hoarding, account takeover, and content scraping. DataDome is available for assessment with a 30-day free trial.
Who is it recommended for?
The architecture of the DataDome system means that it can’t double up as a filter for DDoS attacks. So, you still have to find a solution to block those attack and also other attack strategies, such as cross-site scripting. DataDome also includes fraud protection for online sellers.
Pros:
- E-Commerce Security: Highly effective in protecting shopping carts and online transactions from fraud.
- Fraud Monitoring: Specializes in detecting and preventing payment and card fraud.
- Tailored Assessments: Provides flexible scanning options to suit different security needs.
Cons:
- Limited DDoS Protection: Does not provide direct DDoS attack mitigation, requiring additional measures.
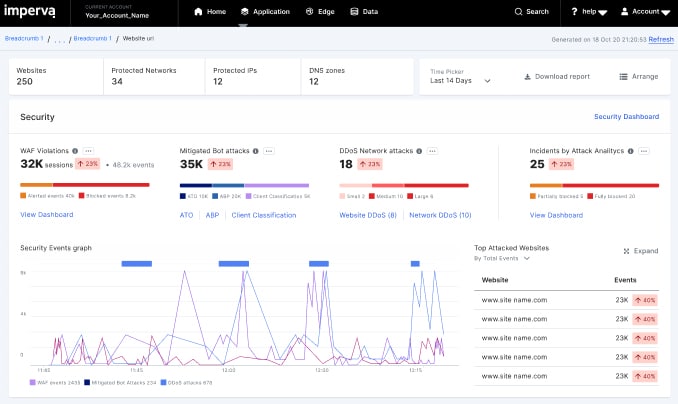
4. Imperva Web Application Firewall
Imperva Web Application Firewall includes a bot manager unit. This system can protect websites, mobile apps, and APIs. The entire firewall system is a cloud-based proxy that processes all incoming traffic before it gets to your load balancers or Web servers.
Key Features:
- DDoS Mitigation: Effectively absorbs and neutralizes DDoS attacks before they reach your infrastructure.
- Robust Blacklisting: Utilizes an updated blacklist to prevent malicious bots from accessing the system.
- Advanced Monitoring: Conducts detailed application-level observations to detect unusual activities.
Why do we recommend it?
Imperva Web Application Firewall is a package of security services for websites and mobile apps. This bundle includes bot detection as well as DDoS absorption and attack blocking. This bot manager can also be bought as part of a content delivery network. The system can also protect cloud platforms and containers.
The bot manager is called Advanced Bot Protection. This system works through a list of steps, which aim to filter out the bulk of malicious traffic as quickly as possible. Sophisticated attacks might evade early detection but should be identified by more detailed and time-consuming tests, which are kept in reserve to crack the human-like activities of fraud attempts, which can be very difficult to spot.
This service will absorb DDoS attacks in the first phase, preventing volume attacks from reaching your system. The next major test is a blacklist reference. More detailed checks occur on all remaining traffic, which has to be passed through initially. Application-level assessments need to be implemented across packets.
Application activity tests use machine learning to define the usual movements of humans through a website or mobile app. When a visitor’s activities don’t conform to this pattern, greater focus is placed on this user. The Imperva system looks for content scraping, scalping, inventory hoarding, account takeover, click fraud, payment fraud, and card fraud.
The Imperva WAF system is implemented as Imperva Cloud WAF or on-site with Imperva WAF Gateway. It is also possible to self-host the WAF in an AWS account. Imperva offers a bundle of the WAF, a CDN, and the Advanced Bot Protection system. This package is available on a 30-day free trial.
Who is it recommended for?
Imperva is a sophisticated service and is a good choice for the producers of SaaS packages, which is a field that many other bot detection systems don’t cover. The Imperva brand has a good reputation and the company maintains its own threat intelligence network, which informs the bot tracking service.
Pros:
- Integrated Security: Combines bot management with a web application firewall and content delivery network.
- Flexible Deployment: Offers options for cloud-based, on-site, or self-hosted solutions within AWS environments.
- Comprehensive Protection: Executes multiple layers of security checks to identify and block sophisticated threats.
Cons:
- Intrusive Challenges: May use reCAPTCHA, potentially disrupting the user experience for legitimate visitors.
5. Radware Bot Manager
Radware Bot Manager operates as an add-on service for the Radware CDN or WAF and it can also be used individually as a plug-in for your Web server or load balancer. The system protects websites, mobile apps, and APIs. The system examines traffic patterns to spot volume attacks. It then checks a blacklist and finally, performs a detailed analysis on the remaining traffic.
Key Features:
- Flexible Integration: Operates as both an add-on and a standalone API-type service.
- Enhanced with WAF and CDN: Can be combined with Radware’s CDN or WAF for enhanced protection.
- Versatile Deployment: Offers various deployment options to suit different infrastructure needs.
Why do we recommend it?
The Radware Bot Manager is a supplementary service that is integrated into many of the Radware Web support services. This range includes a content delivery network, a Web application firewall, and a load balancer. All of these systems are implemented on proxy servers, so they weed out excessive traffic before it reaches your Web server.
Traffic filtering is implemented very quickly but the detailed Application-level checks can take time to reach conclusions. These behavior-tracking checks use machine learning to record typical behavior and identify bot activity.
Radware Bot Manager prevents DDoS attacks, content scraping, card fraud, click fraud, and account takeover. The system is also able to encourage bots to drop a protected system’s identity from its attack list by responding with a fake connection failure report. The Bot Manager is available for a 30-day free trial.
Who is it recommended for?
As this tool isn’t a primary product, you would be more lil]kely to assess the CDN, WAF, or load balancer of Radware for suitability for your company. The bot manager is an added extra for each of these services along with DDoS protection. The company also provides this utility for its cloud platform protection package.
Pros:
- Comprehensive Blacklisting: Utilizes an up-to-date blacklist to efficiently block known threats.
- AI-Driven Detection: Employs artificial intelligence to identify and analyze anomalous activities.
- Proactive Defense: Implements strategies to mislead and deter bots by simulating connection failures.
Cons:
- Additional Setup Required: If used as an API, other measures must be in place to handle traffic surges.