Technology has become an inevitable part of our everyday life. In today’s interconnected world, businesses, consumers, and individuals literally depend on technology to carry on with day-to-day activities.
Here is our list of the best security testing solutions:
- SOOS EDITOR’S CHOICE This cloud platform offers SCA and DAST systems that can be used for continuous testing or on-demand scanning. Get a 30-day free trial.
- SonarQube (FREE TRIAL) A Static Application Security Testing (SAST) platform that is hosted on the cloud and is able to interface with CI/CD pipeline services to automate testing and error reporting. Start a 14-day free trial.
- Veracode Α cloud-based application security solution company that provides multiple security testing technologies such as DAST, SAST, IAST, SCA, and manual penetration testing, on a single platform.
- Aikido An application security testing service that focuses on scanning code with software composition analysis (SCA) and static application security testing (SAST).
- Invicti A vulnerability scanner that is suitable for use in continuous testing in a CI/CD pipeline and will also check on live Web applications. This service is offered as a SaaS platform and can also be downloaded and installed on Windows and Windows Server.
- Acunetix A flexible vulnerability scanner that can be used as an automated testing tool for penetration testing. Other versions will work as operations vulnerability scanners for Web applications and networks or for DevOps testing. This system is offered as a cloud platform or for installation on Windows, macOS, or Linux.
- SolarWinds Security Event Manager A Security Information and Event Management (SIEM) solution designed to collect and consolidate logs and events from your firewalls, servers, routers, and other devices in your network in real-time.
- Metasploit Α powerful penetration testing and an ethical hacking tool used by attackers and defenders for launching and simulating real-world attacks on a network and executing exploit code.
- Archer Α robust integrated risk management and GRC automation platform designed to help organizations automate their risk management and compliance program.
As technology embeds itself into our lives, concerns about cybersecurity continue to rise. Security attacks and breaches have grown exponentially, both in quality and impact potential. When breaches occur, businesses lose customer confidence and ultimately revenue.
In such situations, security testing provides a way for organizations to identify where they are vulnerable in order to take the necessary corrective action to fix the gaps. A growing number of organizations are adopting security testing measures as a way to ensure that their critical applications and infrastructure are shielded from security breaches. The more extensive an organization’s security testing approaches are, the better its overall security posture.
Security testing is a process intended to reveal flaws in the security mechanisms of an information system. Testing is carried out to determine the level of protection the security controls provide with a view to providing mitigations where necessary. The goal of security testing is to ensure that existing security controls are working effectively. A properly completed security testing should provide documentation outlining any security gaps, as well as measures to address the identified gaps. In this article, we will take a look at security testing, including a review of the best tools that can be used to carry out the task.
Security testing strategies and techniques
Security testing of an environment may take several forms or techniques. Tests may be blind, double-blind, or targeted. However, before carrying out security testing, a written agreement with the management of the target organization is required. This provides legal cover for the tester and ensures that there are no misunderstandings by providing in writing what the tester should—and should not—do. Below are some of the techniques and methodologies used to carry out security testing:
Black-box security testing
Black-box security testing is one in which the assessors do not have any internal knowledge of the target system or network. The goal is to determine the vulnerabilities in a system that are exploitable from outside the network and attempt to exploit them. They are not provided with any network diagrams, IP configurations, or source code that is not publicly available. It is the duty of the assessor to perform all reconnaissance to obtain the sensitive information required to penetrate the system, which places them in the role of the average hacker. This type of testing is the most realistic. However, it also requires a great deal of time to gain insights into inherent weaknesses and develop an attack plan.
Conversely, in software testing, the term is also used to refer to a method of testing the functionality of an application without knowing or examining its internal structures or workings. This testing approach focuses on the input that goes into the software, and the output that is produced. The tester is aware of what the software is supposed to do but is not aware of how it does it. The whole goal is to ensure that the user interface and user inputs and outputs are all working correctly.
White-box security testing
In white-box security testing, assessors are given full knowledge and access to the application, source code, or the network, including diagrams and other documentation. This type of assessment is more precise and targeted, as both internal and external vulnerabilities are evaluated from an “insider” point of view, which is not usually available to typical attackers. The goal is to determine and exploit the vulnerabilities in a system that are exploitable from within and without.
Similarly, in software testing, the term refers to a method of testing the internal structures or workings of an application at the level of the source code. The whole goal is to minimize errors and strengthen security.
Grey-box security testing
Gray-box security testing methodology draws partly from black-box and partly from white-box testing. The purpose of gray-box security testing is to provide a more focused and efficient assessment of a network’s security. The assessor typically has partial knowledge or access to a network’s internals, including design and architecture documentation and some lower-level access credentials to the network. In software testing, the gray-box tester may have partial knowledge of the source code or data structure, as well as the algorithms used.
Now, which of the above security testing methodology is right for your business or project? Well, it all depends on the kind of threat or security concern your organization is trying to address:
- Black-box testing is the most realistic testing method as it addresses concerns posed by an external attacker, but may require sacrificing time and efficiency.
- White-box testing is the most precise and targeted as it addresses concerns posed by insider threats, but requires detailed knowledge of the internal network.
- Gray-box testing seems to be the most effective and efficient as it strives to strike a balance between black-box and white-box testing.
Types of security testing
Different types of security testing are used by security professionals to identify potential threats, measure the likelihood of exploitation, and gauge the overall risks facing the network or application. The actionable insights from these tests are utilized to fix the gaps and minimize security risks. Below are some of the various types of security testing available:
Vulnerability assessment: Vulnerability scanning and assessment identify a broad range of vulnerabilities in a target system. Vulnerability scanning is commonly carried out through a scanning tool that scans a network or system for a list of vulnerabilities such as malware, system misconfiguration, or outdated software. No single tool can find every known vulnerability. A combination of tools may give a better picture of the flaws in your system. Vulnerability testing requires security experts with a deep security background and the highest level of trustworthiness.
The results from a vulnerability scan or assessment are just a “snapshot in time.” As the environment changes, new vulnerabilities can arise. This means that assessments should be performed regularly as changes in the network or system occur. The overall goal of the vulnerability assessment is to:
- Evaluate the true security posture of a network, system, or application.
- Identify, evaluate and prioritize as many vulnerabilities as possible.
- Test how the environment reacts to certain circumstances and attacks, to learn what the known vulnerabilities are, and ways they might be exploited.
Penetration testing
Penetration testing is the process of simulating attacks on a network using a set of procedures and tools that cybercriminals use to possibly bypass the security controls of a system. Penetration testing is usually based on the request of the asset owners, where the pen tester exploits one or more vulnerabilities to prove to the customer that a malicious actor can actually gain access to company resources whether within technologies, people, or processes.
The penetration testing team can have zero, partial or full knowledge of the target network or system before the tests are actually carried out. The main goal of penetration testing is to uncover any weaknesses within an environment, simulate how attackers would exploit those weaknesses in the real world, and measure an organization’s level of resistance to such attacks.
GRC and IT risk assessment
Governance, risk management, and compliance (GRC) is the term covering an organization’s overall approach to risk management. It also encompasses having governance policies and procedures in place along with knowing your risk areas and establishing an enterprise-wide compliance program.
A risk assessment is a method of identifying vulnerabilities and threats and the possible impacts to determine where to implement security controls. The goal of risk assessment is to ensure that security is fit-for-purpose, cost-effective, and responsive to perceived threats. Risk analysis helps companies prioritize their risks and the number of resources that should be applied to protecting against those risks. The main objectives of risk analysis are as follows:
- Identify assets and their value to the organization.
- Identify vulnerabilities and threats to those assets.
- Quantify the probability and business impact of these potential threats.
- Provide an economic balance between the impact of the threat and the cost of the countermeasure.
Security auditing
A security audit is a process of reviewing an organization’s security practices against a published standard. It also involves reviewing security audit logs within IT systems to ensure they can effectively support information security goals. Some audits are simply carried out internally for self-reporting purposes, while others may involve the use of a third party or consultant.
An organization may be audited for compliance with security standards such as PCI-DS, ISO/IEC 27002, or HIPAA. The goal is to measure an organization’s level of compliance with a particular security standard.
Application security testing
Apart from testing to evaluate the functionality of an application, application testing is increasingly focusing on finding security flaws that could expose applications to compromise. In application security testing, security attacks and penetration tests are usually carried out to uncover inherent security flaws such as buffer overflows or SQL injection vulnerabilities. When carrying out application security testing, the product interfaces should be hit with unexpected inputs and unusual user activity, denial of service (DoS) situations should be tested, and if the application crashes, appropriate security measures should be put in place to address the identified weaknesses.
There are different automated tools and approaches to software testing. These include:
- Static testing: Static Application Security Testing (SAST) is used to secure applications by reviewing the source code when it’s not running to identify vulnerabilities or evidence of known insecure practices. SAST tools employ a white-box testing strategy that scans the source code of applications and their components to identify potential security flaws. Research has shown that static analysis tools can detect an estimated 50% of existing security vulnerabilities.
- Dynamic testing: Dynamic Application Security Testing (DAST) tool communicates with applications through the front-end in order to identify potential security vulnerabilities. DAST tools do not have access to source codes; rather, they perform actual attacks using the black-box strategy in order to detect vulnerabilities. With dynamic analysis, security checks are performed while actually running or executing the code or application under review. A technique known as fuzzing is used in dynamic tests to submit random, malformed data as inputs to the application to determine if they will crash. Any application that freezes or crashes has failed the fuzz test.
- Interactive Application Security Testing (IAST): IAST combines the best of SAST and DAST. It analyzes code for security vulnerabilities while the app is run by any activity interacting with the application functionality.
- Software Composition Analysis (SCA): One of the key functions of SCA tools is to identify open-source components with known vulnerabilities. A good SCA solution will also tell you whether your code calls the affected library, and suggest a fix where possible.
- Mobile Application Security Testing (MAST): MAST solutions use behavioral analysis to observe the behavior of the applications during runtime and identify actions that could be exploited by an attacker.
Some nonprofit organizations such as Web Application Security Project (OWASP) and Web Application Security Consortium (WASC) provide security guidelines, standardized testing procedures, and best practices for secure software development.
The best security testing tools
With a variety of security testing tools out there, choosing the right one for your business, project, and budget can be challenging. What fits perfectly from a price, feature, and functionality standpoint for one project or business may not fit for another. In this section, we’re going to review some of the best security testing solutions that cover all the various types of security testing discussed above. Hopefully, this will guide you in the process of choosing the right solution for your business or project.
Our methodology for selecting security testing systems
We reviewed the market for security testing tools and analyzed the options based on the following criteria:
- Systems that can integrate into a CI/CD pipeline
- Options for DAST, SAST, and IAST
- Software composition analysis
- Facilities for testing mobile apps
- Integration with bug trackers
- Free trial or a demo option to enable an assessment before buying
- Value for money from a testing system that is offered at a fair price
1. SOOS (FREE TRIAL)
SOOS is a cloud-based testing system that offers two subscription plans. The first of these provides SCA for your Web applications and the upper plan gives you DAST as well as the SCA module.
Key Features:
- DAST and SCA: Provides Dynamic Application Security Testing and Software Composition Analysis.
- CI/CD Integration: Seamlessly integrates into CI/CD pipelines for continuous testing.
- Management System Interaction: Works with Jenkins, Jira, GitHub, Azure DevOps, and TeamCity.
- Domain Scanning: Can be run as an on-demand or scheduled domain scanner.
Why do we recommend it?
SOOS is a Web application security testing system. This is an automated tool and it focuses on systems that contribute to the processing of data for mobile apps and Web pages. Often, Web development projects rely on supporting frameworks and libraries of tools and you need to check the security of those, too.
The SOOS services are offered in a continuous testing format for integration into CI/CD pipelines. This system can be integrated into development management systems, such as Jenkins, Azure DevOps, and TeamCity and it can be used in conjunction with automated issue trackers, such as Jira, GitHub Issues, and Bitbucket.
Operations staff can use the SCA and DAST modules, too because they can be run as a domain scanner either on-demand or on a schedule.
Who is it recommended for?
This package is important for use by businesses that create web applications and those companies that rely on those developed systems as part of their business model. That is, end consumers of Web applications are probably the least likely group of stakeholders that would use the SooS system.
Pros:
- Flexible Cloud-Based Testing: Offers highly adaptable and scalable cloud-based security testing.
- User-Friendly Interface: Features an easy-to-learn and navigate interface.
- Wide System Support: Supports integration with a wide range of development and issue management systems.
- Unlimited Usage: Subscription model allows for unlimited projects and users.
Cons:
- Targeted for Larger Teams: Better suited for larger development teams due to its extensive features and integration capabilities.
The SOOS subscription model sets a price per month and that is for unlimited projects and unlimited users. You can examine SOOS with a 30-day free trial.
2. SonarQube (FREE TRIAL)
SonarQube is a cloud-based Static Application Security Testing (SAST) tool designed to help developers identify and fix vulnerabilities in their code. It integrates seamlessly with CI/CD pipelines, providing real-time feedback to ensure code quality and security.
Key Features:
- Static Application Security Testing (SAST): Detects security vulnerabilities in your code, allowing you to address them before building and testing your application.
- Security Standards Compliance: Helps ensure your code adheres to common security standards, such as OWASP Top 10 and CWE Top 25.
- CI/CD Integration: Seamlessly integrates with popular DevOps platforms like GitHub, Bitbucket Cloud, GitLab, and Azure DevOps, enabling automated code checks within your existing workflows.
- Pull Request Analysis: Provides immediate feedback on code quality and security issues directly within your pull requests, facilitating faster code reviews and issue resolution.
Why Do We Recommend It?
SonarQube is recommended for its integration with CI/CD workflows, extensive programming language support, and actionable insights that help maintain high code quality and security standards. Its real-time feedback mechanism ensures that issues are addressed promptly, making it an essential tool for modern development teams.
SonarQube stands out as a leading SAST tool due to its ability to provide detailed and actionable insights into code quality and security. It helps developers maintain clean, secure code by identifying vulnerabilities, bugs, and code smells early in the development process. Its seamless integration with popular CI/CD platforms makes it a suitable tool for any development pipeline.
Who Is It Recommended For?
SonarQube is suitable for development teams of all sizes looking to enhance their code quality and security. Unlike most vulnerability scanners, the package’s price is not excessive and it is within the reach of lower-volume coding enterprises. It’s particularly beneficial for organizations that rely on CI/CD workflows and need a tool that integrates smoothly with their existing platforms.
Pros:
- Comprehensive Vulnerability Detection: Identifies a wide range of security issues, including vulnerabilities and security hotspots, enhancing code safety.
- Built-In Security Compliance: Ensures code adheres to critical security standards like OWASP Top 10 and CWE Top 25 for industry compliance.
- Streamlined Workflow Integration: Works seamlessly with CI/CD tools such as GitHub, GitLab, Bitbucket, and Azure DevOps, ensuring automated checks during development.
- Real-Time Code Feedback: Provides immediate analysis and suggestions directly in pull requests, facilitating quicker issue resolution during code reviews.
Cons:
- Challenging Initial Setup: The extensive features can make configuration time-consuming, especially for first-time users.
- Performance Lag for Large Repositories: Analysis may be slower when working with very large codebases, impacting productivity.
The Team edition of SonarQube is available for a 14-day free trial. Individual developers and open source projects can access the Free edition, which isn’t end-dated.
3. Veracode
Veracode is a cloud-based application security solution company that provides multiple security testing technologies such as DAST, SAST, IAST, SCA, and manual penetration testing, on a single platform.
Key Features:
- Comprehensive Testing: Provides DAST, SAST, IAST, and SCA in one platform.
- Secure Coding Training: Offers online training for secure coding practices.
- CI/CD Pipeline Integration: Seamlessly integrates into CI/CD pipelines for continuous security testing.
Why do we recommend it?
Veracode is a DevSecOps tool. That is, it builds security into Web applications that businesses develop and deploy. The way the security building process is implemented is through testing. So, any piece of code needs to pass through the Veracode tester before it is released. Checks on live systems maintain that security.
Veracode provides DevOps teams with the functionality to gain actionable insights for addressing security vulnerabilities. Integrations exist for GitLab and IDEs such as Eclipse and IntelliJ, etc., helping developers to identify and remediate security vulnerabilities while they code. A personalized solution demo is available for a free trial to enable you to assess its capabilities and make sure it’s the right fit for you and your organization before purchase.
Who is it recommended for?
This package has the same audience as SOOS. Companies that develop Web applications and offer them for use by other businesses or to members of the public, such as a mobile app, should consider a system such as this. Businesses that commission Web apps from development companies should also use this system.
Pros:
- Scheduled Scans: Allows for simple scheduling of scans to ensure continuous security.
- Scan Control: Provides easy options to stop, pause, and resume scans as needed.
- Simplifies Vulnerability Hunting: Designed to reduce the complexity of identifying and addressing vulnerabilities.
- DevOps Integration: Integrates directly into the DevOps lifecycle, aiding in secure code development.
Cons:
- Pricing Transparency: Requires contacting sales for pricing information.
If you are interested in purchasing a Veracode security testing solution, you’ll have to go through a reseller partner in your area.
4. Aikido
Tested on: Cloud

Aikido offers a security testing service that provides scrutiny for web applications from their development through to their operations. Development teams get static application security testing (SAST) and software composition analysis (SCA) and operations teams get a cloud security posture management (CSPM) service from the same package.
Key Features:
- Automated Code Scanning: Continuously scans application code for security vulnerabilities.
- Risk Scoring: Assigns a risk score to each identified issue.
- Error Descriptions: Provides detailed descriptions of each discovered error.
- Fix Recommendations: Offers recommendations on how to resolve each identified problem.
- CVE Scanning: Scans for Common Vulnerabilities and Exposures (CVEs) in the code.
Why do we recommend it?
Aikido provides a range of security testing services on code. It will scan through all application code and identify open source components. These are checked against a list of known security risks. Original code is scanned for CVEs. The scan completes with a record of each discovered error, a description of why it is a risk, and an explanation of how to fix it.
The Aikido system can be set up as a continuous tester for a CI/CD pipeline. In this scenario, you register a repository in the tester and when new code is checked into the repo, the Aikido process automatically triggers. Some problems can be fixed automatically. The bulk of errors, though will be notified through your bug tracker or project management tool.
The tool recognizes that one error might repeat throughout a program. For example, if a badly planned function or third-party library is used several times, Aikido will report it as one issue with a list of the function’s locations in the program.
Who is it recommended for?
This system is designed for Web application testing and it needs access to the code, so you wouldn’t use it to scan third-party programs. The service is suitable for DevOps teams, providing the most value during the development phase. The tool is cloud-based and there is a Free edition for SMEs.
Pros:
- CI/CD Integration: Acts as an automated continuous tester for CI/CD pipelines, enhancing development efficiency.
- Software Composition Analysis: Analyzes and identifies security risks in open-source components.
- Comprehensive Scanning: Includes scanning for container images and Infrastructure-as-Code (IaC).
- Multi-Repo Support: Capable of scanning multiple repositories for a holistic security overview.
- Cloud Security Management: Offers cloud security posture management, ensuring ongoing operational security.
Cons:
- Limited to Source Code: Cannot analyze third-party functions where the source code is not accessible.
Aikido has four editions and the first of these is free. Successively higher plans offer more capacity and a few extra features. However, all editions provide SCA, SAST, IaC and container scanning, and integrations with development project management services. You can try it for free.
5. Invicti
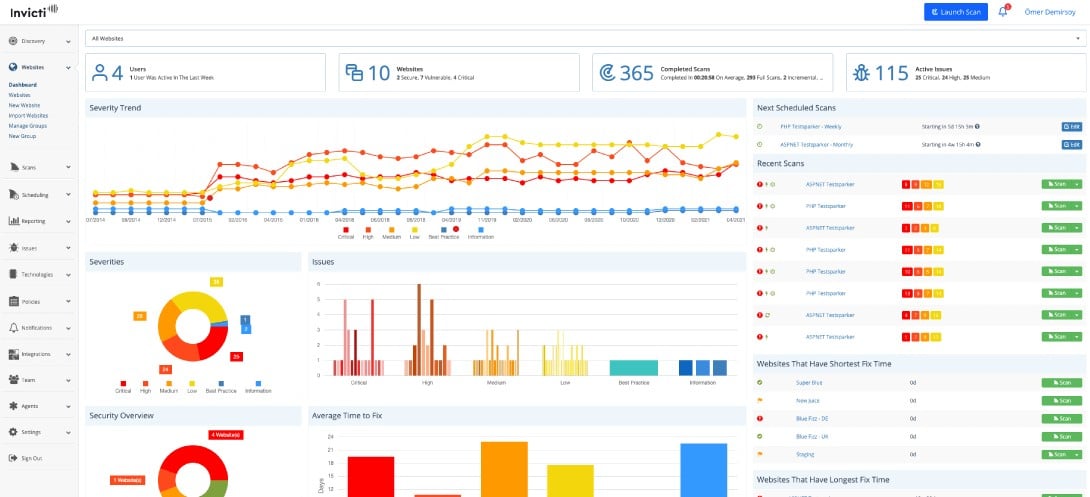
Invicti is an easy-to-use automated DAST tool that enables you to scan web applications, websites, and web services for security flaws. Invicti – formerly Netsparker – is designed for small and medium businesses and doesn’t require you to have deep IT security knowledge to use.
Key Features:
- DAST and IAST: Provides Dynamic and Interactive Application Security Testing.
- CI/CD Integration: Integrates seamlessly into CI/CD pipelines for continuous security testing.
- Heuristic Analysis: Uses heuristics to detect vulnerabilities, including zero-day threats.
- Compliance Reporting: Offers PCI DSS compliance reporting.
- Third-Party Application Scanning: Can scan and verify the security of third-party applications.
Why do we recommend it?
Invicti is another web application security testing tool. This system can be used to verify the security of third-party components before approving them for use in a development project, to assure packages after development and before they go live, and during ongoing operations. It can also be used for penetration testing.
Invicti also supports Interactive Application Security Testing (IAST); and it uses a heuristic-based approach for detecting vulnerabilities, which makes it easier to identify zero-day vulnerabilities in web applications. Invicti also uses a proprietary technology called Proof-Based Scanning to safely exploit identified vulnerabilities and automatically create a proof-of-exploit to show that it’s not a false positive. With Proof-Based Scanning technology, you can build DAST into your software development lifecycle (SDLC) to eliminate vulnerabilities before they can reach production.
Who is it recommended for?
The main market for Invicti is Web application testing. The system has a number of deployment usages, which include on-demand testing, which operates as penetration testing and vulnerability scanning tools and it can also be integrated into a CI/CD pipeline as a continuous tester.
Pros:
- Intuitive Dashboard: Features a highly intuitive and insightful admin dashboard.
- Wide Application Support: Supports any web applications, web services, or APIs, regardless of framework.
- Streamlined Reports: Provides reports with prioritized vulnerabilities and detailed remediation steps.
- Eliminates False Positives: Uses Proof-Based Scanning to safely exploit vulnerabilities and confirm their validity.
- DevOps Integration: Easily integrates into DevOps workflows, providing quick feedback to prevent future bugs.
Cons:
- Trial Availability: Would benefit from offering a trial rather than just a demo.
6. Acunetix
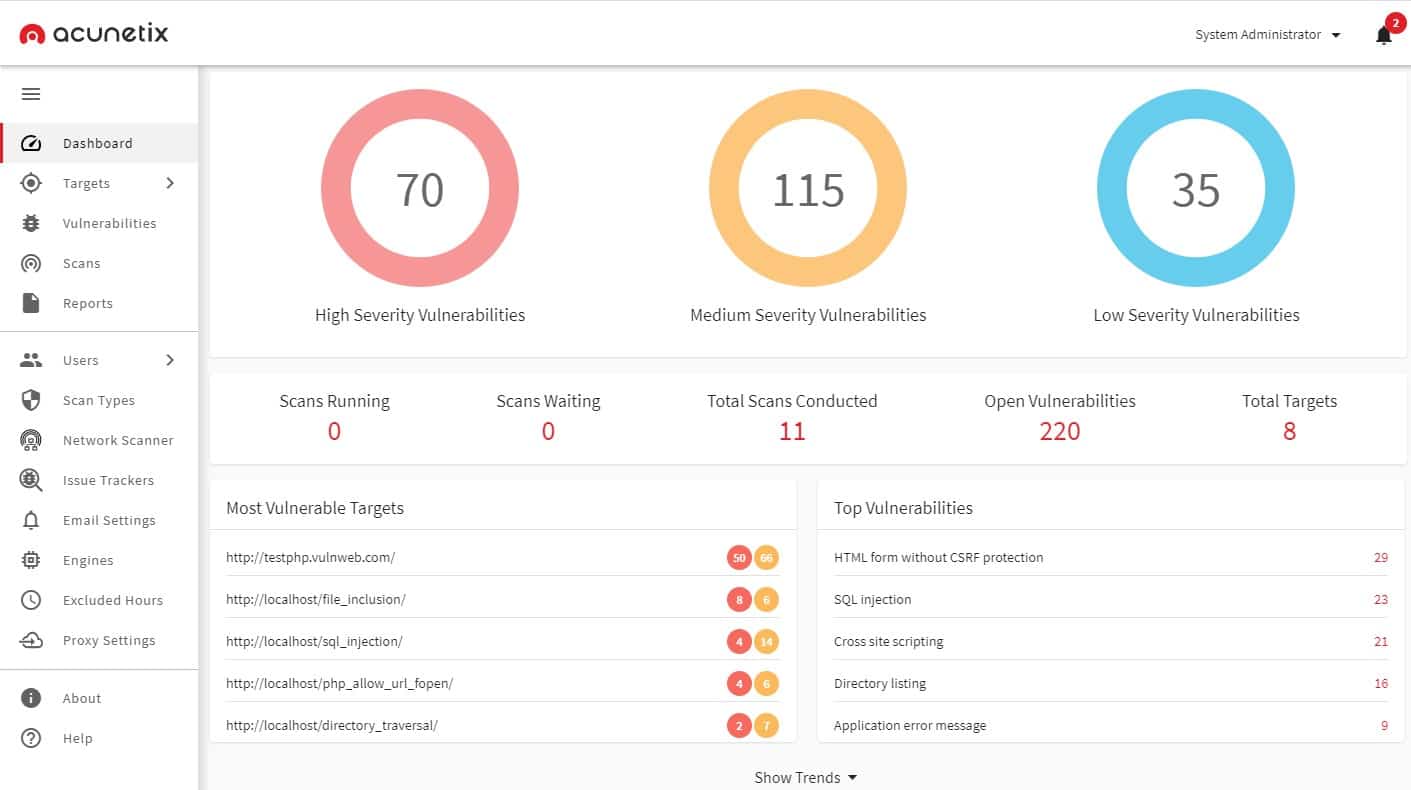
Acunetix is an automated DAST testing tool that audits your web applications by checking for exploitable vulnerabilities.
Key Features:
- DAST and IAST: Provides both Dynamic and Interactive Application Security Testing.
- CI/CD Integration: Seamlessly integrates into CI/CD pipelines for continuous testing.
- Internal Network Scanning: Uses OpenVAS for comprehensive internal network scanning.
- OWASP Top 10: Scans for vulnerabilities identified in the OWASP Top 10.
Why do we recommend it?
Acunetix is owned by the same company as Invicti and it can be put to similar uses. This system can be expanded by integrations and it will work with OpenVAS, a free vulnerability scanner to scour networks and endpoints for internal threats as well as external Web application testing.
Acunetix is made up of the following key components:
- AcuSensor technology: An optional component of Acunetix, which you can use for free with all product licenses. When you install and use AcuSensor, Acunetix becomes an IAST solution (grey-box scanner), not just a DAST scanner (black-box scanner).
- AcuMonitor: A service that allows the scanner to detect out-of-band vulnerabilities. This service is automatically used by out-of-band checks and requires no installation or configuration, only simple registration for on-premises versions.
- DeepScan Technology: Acunetix DeepScan technology enables it to crawl and scan even the most complex website or web application to find all possible entry points.
The product is available in three editions: Standard, Premium, and Acunetix 360 as shown in Table 2.0 below. All three editions can scan for the OWASP Top 10 and are particularly strong at detecting web application security issues such as cross-site scripting, SQL injection, reflected XSS, CSRF attacks, and directory traversal, among others.
Who is it recommended for?
The target market for Acunetix is very similar to that of Invicti and Veracode. However, this tool is a much stronger vulnerability manager, while still providing Web application security testing options. So, while it can be used by development teams, it will appeal more to operations teams.
Pros:
- Application Security Focus: Specifically designed for robust application security.
- Tool Integration: Integrates with a wide range of other tools, including OpenVAS.
- Misconfiguration Detection: Can detect and alert on system misconfigurations.
- Automation: Leverages automation to stop threats immediately and escalate issues based on severity.
Cons:
- Trial Availability: Would benefit from offering a trial version for testing instead of just a demo.
7. SolarWinds Security Event Manager
SolarWinds Security Event Manager is a Security Information and Event Management (SIEM) solution designed to collect and consolidate logs and events from your firewalls, servers, routers, and other devices in your network in real-time. The solution also comes with lots of pre-built connectors to gather and correlate logs and events from various sources and consolidates them in a central location to support your security auditing, incident response, and compliance reporting efforts.
Key Features:
- System-Wide Security Scans: Performs comprehensive scans across your network for real-time threat detection.
- Log Management: Collects, consolidates, and manages logs from various sources in a centralized location.
- Compliance Reporting: Provides hundreds of templates to support compliance reporting and auditing efforts.
- Automatic Threat Response: Takes automatic action against identified threats in real-time.
Why do we recommend it?
Interactive tests generate their own results to examine, however, the SolarWinds Security Event Manager provides an alternative strategy that doesn’t require active testing to generate source data. That is, gather all event data and perform searches for known attack tactics.
It not only centralizes logs, but it also provides search features to help you easily visualize and narrow in on the logs you need and even takes automatic action against threats, all in real-time. The platform also offers hundreds of compliance report templates suited to meet the needs of nearly any auditor, helping you demonstrate regulatory compliance. But don’t take my word for it—you can try it out for free yourself, to make sure it’s the right fit for you and your organization before making financial commitments.
Who is it recommended for?
Any business that needs to comply with data protection standards will need to have a SIEM in place. This tool is a SIEM, which is an automated security testing system. However, it also provides facilities for manual data searches. You also get log management, which is important for compliance auditing.
Pros:
- Wide Integration: Enterprise-focused SIEM with extensive integration options for various devices and platforms.
- User-Friendly Log Filtering: Simple log filtering capabilities without the need to learn a custom query language.
- Quick Setup: Numerous templates allow administrators to quickly start using SIEM with minimal setup.
- Historical Analysis: Includes tools for historical analysis to identify anomalous behavior and network outliers.
Cons:
- Learning Curve: As an advanced SIEM product, it requires time and effort to fully learn and utilize the platform effectively.
SolarWinds Security Event Manager installs on Windows Server and comes with a 30-day free trial.
8. Metasploit
Metasploit is a powerful penetration testing and an ethical hacking tool used by attackers and defenders for launching and simulating real-world attacks on a network and executing exploit code. As of the time of writing, Metasploit has over 2074 exploits, 592 payloads, and a suite of extensively used tools for penetration testing and exploit development. It also includes anti-forensic and evasion tools, as well as hundreds of auxiliary modules that can perform scanning, fuzzing, sniffing, and much more.
Key Features:
- Penetration Testing Tool: Provides extensive tools for launching and simulating real-world attacks on a network.
- Security Weakness Identification: Identifies vulnerabilities and security weaknesses in target systems.
- Free and Paid Versions: Available in both free (Metasploit Framework) and paid (Metasploit Pro) versions.
- Integration with Reconnaissance Tools: Integrates seamlessly with tools like Nmap and SNMP scanning.
Why do we recommend it?
Metasploit offers two versions of security testing systems and they provide different types of services. The free version, Metasploit Framework, supports manual security testing and so can be considered a penetration testing package. The paid version, Metasploit Pro has these manual testing tools and also automated testing services, making it a vulnerability scanner.
Metasploit integrates seamlessly with Nmap, SNMP scanning, Windows patch enumeration, and other reconnaissance tools used to glean information about target systems. The product is available in two editions:
- Metasploit Framework: A free and open-source edition that offers a basic set of features in a command-line-based interface for manual exploitation. This edition is recommended for developers and security researchers. A free download is available.
- Metasploit Pro: An open-core commercial edition that offers a compressive set of advanced features in a GUI-based interface for automated exploitation. This edition is recommended for penetration testers and IT security teams. A free 14-day trial is available
Who is it recommended for?
Metasploit is widely used by penetration testers, so if this is your job, you already know about it. The use of the tool is taught on cybersecurity training courses and it is one of the cornerstone tools for this discipline. Metasploit Pro is very expensive and could be used by cybersecurity agencies.
Pros:
- Widely Used Framework: One of the most popular security frameworks with a large user community for support and updates.
- Comprehensive Toolset: Offers over 2074 exploits, 592 payloads, and numerous auxiliary modules for extensive penetration testing.
- Flexible Versions: Available for both free (ideal for developers and security researchers) and commercial use (Metasploit Pro for IT security teams).
- Highly Customizable: Open-source nature allows for extensive customization and integration with other security tools.
Cons:
- Technical Learning Curve: Best suited for more technical users, which may present a steep learning curve for beginners in cybersecurity.
9. Archer
Archer is a robust integrated risk management and GRC automation platform designed to help organizations automate their risk management and compliance program. The solution encompasses audit management, compliance management, IT and security risk management, and much more. The product is mostly targeted at medium to large-scale enterprises.
Key Features:
- Risk Assessments: Conducts comprehensive risk assessments tailored to various industry sectors.
- Industry-Specific Solutions: Provides customized solutions based on specific industry requirements.
- Compliance Reporting: Facilitates detailed compliance reporting to meet legal and regulatory obligations.
Why do we recommend it?
Archer is a GRC platform, so this suite of options covers a different aspect of security assurance that extends out to working practices and awareness of legal obligations. The field of GRC is complicated and the requirements for each company depend on where they are and what business sector they are in.
With Archer IT & Security Risk Management, for example, you can determine which assets are critical to your business, compile a complete picture of security-related risks and their financial impacts, identify and remediate security deficiencies, and establish clear IT risk management best practices.
Who is it recommended for?
The complexities of GRC requirements mean that there is no single GRC solution. The Archer system offers a menu of solutions. These are all tailored to the business’s needs – you might need a bit of several units. As bespoke services, Archer’s solutions are expensive and out of the reach of small businesses.
Pros:
- User-Friendly Interface: Features a simple, easy-to-use interface with minimal configuration needed.
- Flexible Risk Management: Offers adaptable controls for managing risks effectively.
- Detailed Reporting: Includes both high-level and granular reporting for thorough risk analysis.
Cons:
- Enterprise Focus: Better suited for medium to large-scale enterprises, making it less ideal for small businesses due to cost and complexity.
Some of the key features of Archer Suite include built-in risk taxonomy, integrated industry standards, financial information database, workflow templates, on-demand risk analytics, mathematical simulations, loss tables, and much more. Pricing of this product is available on request. However, it’s important to know that this product is not cheap, which makes it less suitable for SMBs.
Choosing the best security testing tool
As technology embeds itself into our lives, concerns about cybersecurity continue to rise. Security attacks and breaches have grown exponentially, both in quality and impact potential. When breaches occur, businesses lose customer confidence and revenue.
With a variety of security testing tools out there, choosing the right one for your business, project, and budget can be challenging. What fits perfectly from a price, feature, and functionality standpoint for one project or business may not fit for another.
Security testing provides a way for organizations to identify where they are vulnerable in order to take the necessary corrective action to fix the gaps. In this article, we have explored all sources of security testing tools and have identified some very good options with Aikido being the best among them.
Security testing FAQs
What is security testing?
Security testing scans applications under development or already in use for known vulnerabilities. This form of testing is particularly prominent in the field of Web application development. Security weaknesses can make a system vulnerable to manual intrusion or automated attacks.
What are types of security testing?
There are many types of security testing methodologies:
- Vulnerability scanning – An automated process
- Penetration testing – A manual test performed by white hat hackers
- Risk assessment – Can include manual procedures and also administrative controls
- Posture assessment – A security scan of a device as part of the authentication process
- Dynamic application security testing (DAST) – A process that tests Web applications by running them and observing their behavior with a range of inputs
- Static application security testing (SAST) – Scans of the code in Web applications, looking for security weaknesses
- Interactive application security testing (IAST) – A combination of DAST and SAST
- Software Composition Analysis (SCA) – Looks for open-source components that have known security weaknesses
- Mobile application security testing (MAST) – Checks mobile applications for vulnerabilities
What are security testing tools?
Security testing tools range from utilities for use during manual system testing through to fully automated system-wide checks. Web application development needs to go through security testing before it can be released to IT operations.