Protecting your network infrastructure from threats and vulnerabilities is more critical than ever. Security Information and Event Management (SIEM) solutions play a vital role in helping organizations detect, analyze, and respond to potential security incidents. IBM’s QRadar SIEM is one of the leading solutions in the industry, offering powerful tools for collecting, analyzing, and correlating security event data from across the network.
QRadar has a strong reputation for providing extensive monitoring, real-time threat detection, and advanced analytics, but it also requires a significant investment in terms of time, resources, and expertise. Additionally, for smaller organizations or those with simpler security needs, the complexity and cost of QRadar may be overkill, leading them to explore other SIEM solutions that better align with their requirements.
This guide provides a comprehensive review of QRadar SIEM, evaluating its strengths and weaknesses, and offers insights into alternatives that might be better suited for certain businesses. While QRadar SIEM is widely used, it may not be the ideal fit for every organization due to factors like cost, scalability, or specific functionality requirements.
In this review, we explore a range of QRadar alternatives that offer comparable security capabilities with varying levels of complexity and price points. Whether you’re seeking a more affordable solution, one that provides greater ease of use, or one that integrates better with existing tools, this guide will help you evaluate the best options available in the market.
By comparing these alternatives, organizations can find the most suitable SIEM solution that fits their unique security needs and budget constraints, ultimately improving their cybersecurity posture without overextending their resources.
The facts about SIEM
SIEM systems are not the first line of defense for a business’s IT system. They are not perimeter services. Instead, a SIEM aims to flush out suspicious behavior performed by seemingly legitimate users. SIEM also looks for activities around its hardware and services that look as though someone might have hacked into them, altered their settings, or tampered with files.
SIEM systems were created to counter a hacker strategy called the “Advanced Persistent Threat” (APT). When APTs were first uncovered, the intrusions turned out not to be new. Those hacker access events had actually been occurring for years. Hackers had found a way to gain constant access at will, use the resources of the company, access data without detection, and observe business transactions.
Intruders that transfer a large amount of data out of the system are easy to spot. Those that use the victim companies gateway as a shielding proxy on a regular basis are harder to spot.
SIEM stands for Security Information and Event Management. The term is an amalgamation of two pre-existing security methodologies: SIM and SEM. SIM means Security Information Management. It checks information stored in log files for signs of intrusion. SEM stands for Security Event Management and it watches real-time events, particularly network traffic.
The problem with SEM is that it only sees a series of snapshots. It can’t spot hackers that hijack existing user accounts. The problem with SIM is that it only spots security breaches after the fact. SIEM is a second line of defense. Its philosophy is that it is better to catch intruders late than never catch them at all.
QRadar’s history
QRadar was created by Q1 Labs in the early years of this century. Initially, the tool was an anomaly detection engine, evolving into an Intrusion Detection System (IDS). SIEMs are a form of IDS. The strategy behind SIEM is to look out for unusual behavior on the system, which is called an anomaly.
By version 4 of QRadar, it had evolved into an “Intrusion Prevention System” (IPS). The distinctive feature of an IPS is that it is able to take action to block any intrusion that it detects. This is usually through interacting with a firewall and altering its rules to block specific external IP addresses. Other actions that an IPS can take include suspending user accounts in Active Directory.
In 2010, Q1 Labs restyled QRadar as a “security intelligence platform” or a “security intelligence operating system.” By this point, Q1 Labs was using the term “SIEM” to describe the main component in the security intelligence platform.
IBM bought Q1 Labs towards the end of 2011. This was a quicker and more economic way for the company to create an IBM SIEM. IBM recognized that it would take years to establish a credible space in the SIEM market and buying the highly-regarded Q1 Labs was a better plan.
IBM was so impressed by the strategy of Q1 Labs that it re-titled the company as the IBM Security Systems Division and pumped funds into it. IBM enhanced the “security intelligence platform” label and focused the marketing of QRadar as a suite of products that includes the QRadar SIEM.
QRadar SIEM features
SIEM is a multi-strategy approach to system security, so, like any SIEM, the IBM QRadar SIEM is a suite of modules. In a wider context, IBM also markets its Security Intelligence Platform, which adds on other cybersecurity features, such as automated response.
Surprisingly unlike rival SIEM systems, QRadar SIEM doesn’t include User and Entity Behavior Analysis (UEBA). In the IBM service, this is a separate module on the QRadar Security Intelligence Platform.
Asset Discovery
An autodiscovery function in QRadar SIEM tracks down all devices connected to the network and creates an inventory. This list of equipment is then available in the Assets screens of the dashboard. The screen records the activities of all equipment in a summary and enables the examination of activity on each individual device.
Vulnerability scanning
QRadar SIEM checks each device against a checklist of known vulnerabilities. The results of these vulnerability scans are shown in the Assets screens with alerts for issues that need to be resolved in order to harden the system against attack.
Log management
QRadar SIEM draws log messages from all points of an IT system. Just about every piece of software generates log messages. Part of the problem is that it is impossible to check every logfile store at a meaningful frequency.
The SIM part of QRadar SIEM acts as a log server, collecting all available log messages and storing them in a central location. All log formats are reorganized into a common structure, making it possible to search through all of them together for patterns. This is called log consolidation.
All log messages are instantly reformatted and they pass through the log server and can be viewed immediately in the QRadar dashboard. Stored records can be recalled into the dashboard viewer for analysis.
Network activity
The QRadar dashboard includes a Network Activity screen, which shows live data from traffic passing through the system. Traffic data is also scanned for anomalies, raising alerts when suspicious activity is detected. The network monitor also sends traffic data to the log server so that it can be included in historical analysis.
QRadar SIEM rules
The rule base of QRadar SIEM is the detection engine of the system. This automatically searches for patterns in the gathered log messages to identify anomalies and link together chains of events. This enables the service to identify intrusions that are made using a series of actions that would otherwise look like normal activities in the business.
Offenses
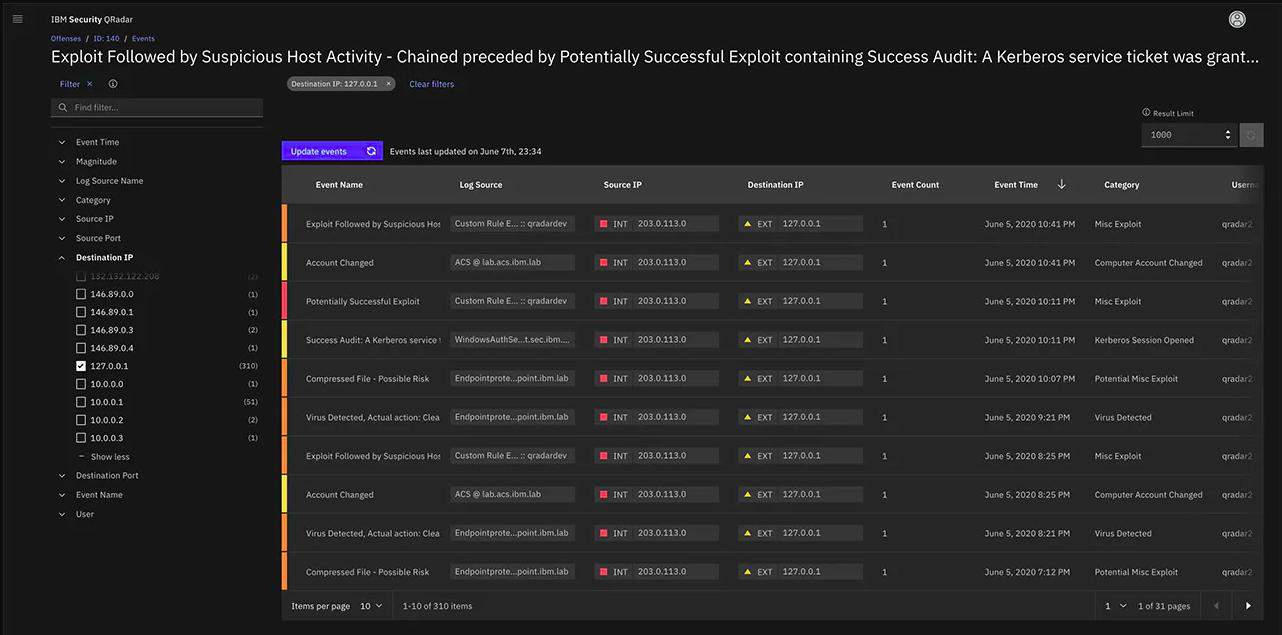
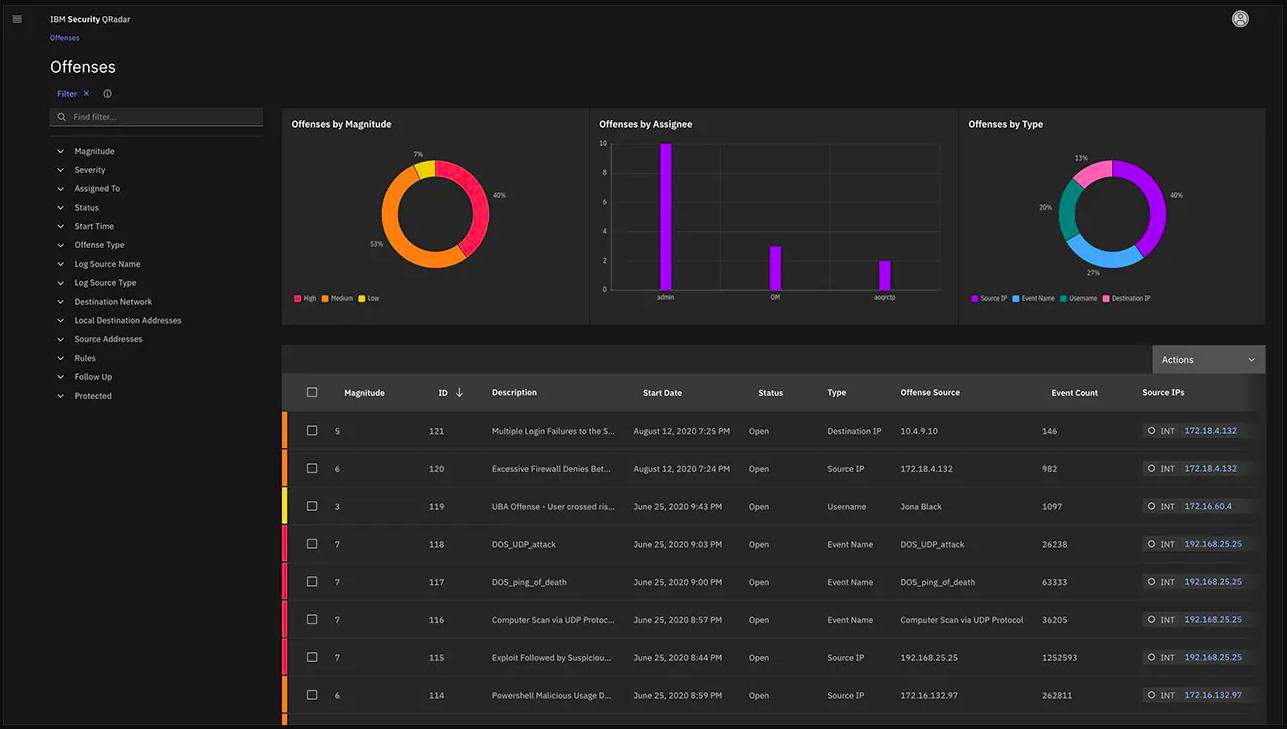
The anomalies that QRadar SIEM detects are termed “offenses.” These are shown, in the Offense Overview and Offense Details screens of the dashboard. The system links together different events found in the log files that relate to a single offense through chains of attack.
Reports
The QRadar SIEM system includes a library of pre-written report formats. However, it is also possible for customers to write their own report layouts within the system.
QRadar SIEM configuration options
QRadar is available as a cloud-based service or for installation on-premises. The on-premises version runs as a virtual appliance and it includes its own operating system so it can be installed on any server.
Dashboard
System managers access the dashboard through any standard web browser. The screens for the QRadar SIEM dashboard have a black background and white or gray text. This scheme is great for making the colored graphs in the screens stand out but it makes the text difficult to read. For example, here is a view of the Event Overview screen, which is text-intensive.
The screens can be a strain on the eyes. However, they are well organized and overview screens lead to details screens through a click on a record. Here is the Offense Overview screen.
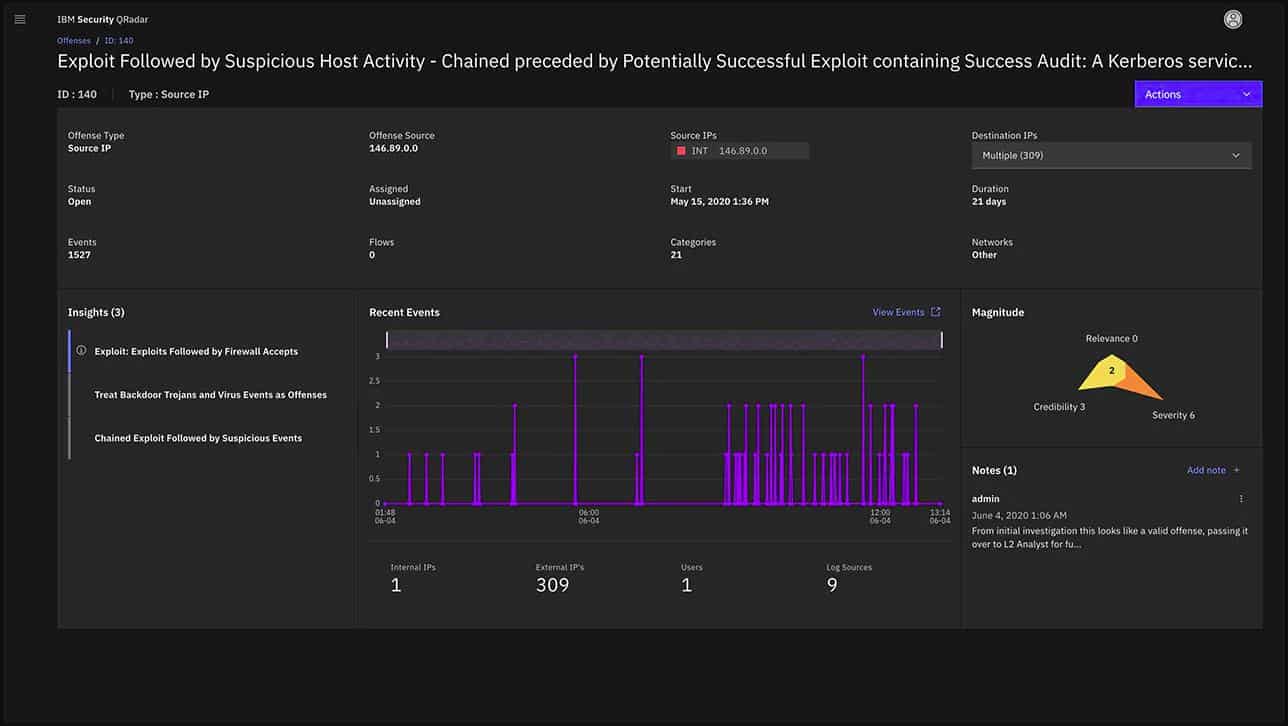
A click on one of the records in the table in the lower part of the screen leads to details about that record.
In general, the details screens are easier to read than the overview screens.
Attack mitigation
IBM offers automated attack mitigation through its SOAR system. SOAR stands for “Security Orchestration, Automation, and Response” This evolution of the QRadar’s IPS features that automatically shuts down attack paths is called IBM Resilient.
QRadar feeds detected anomalous behavior into Resilient, which implements rules to block these activities.
Compliance reporting
IBM produces content extensions that adapt the QRadar SIEM system to comply with specific data security standards. These adaptations include tailoring for PCI DSS, SOX, GDPR, and HIPAA.
The Best Alternatives to IBM QRadar
QRadar SIEM is one of the best SIEM systems available but it isn’t the only quality SIEM to consider. One of QRadar’s earliest features was its facility to enable customers to prove compliance with data management standards such as SOX and PCI DSS. Another feature at which QRadar excels is its incident response automation (now in a separate module), which evolved from the SIEM’s earlier incarnations as an IPS. There are other tools that have equal capabilities.
If you want to try out the QRadar SIEM system, you can access a 14-day free trial at the IBM website.
As with most SIEM systems, QRadar is a good log manager as well as a security system. This capability is matched by the alternatives to the IBM SIEM that appear on the following list.
To find out more about SIEM and the best systems that compete in the market, take a look at our post on the best SIEM tools. Alternatively, if you are looking to outsource the work and employ a team of SIEM experts instead, check out the best managed SIEM services post. If you don’t have time to read that guide, here are the ten best alternatives to QRadar SIEM.
Here is our list of the best alternatives to IBM QRadar:
- ManageEngine EventLog Analyzer EDITOR’S CHOICE A SIM service that is part of a suite of infrastructure monitoring tools. SEM can be provided by adding on ManageEngine OpManager. It installs on Windows and Linux. Start a 30-day free trial.
- Datadog Security Monitoring A security monitoring log manager and SIEM that is a module of a system monitoring package with alerts. Agent programs install on-site for this cloud-based system.
- McAfee Enterprise Security Manager A highly regarded SIEM that includes log management and live traffic monitoring. This system is particularly strong on Active Directory management. It installs on Windows and macOS.
- Fortinet FortiSIEM An advanced SIEM system that is delivered from the cloud. Monitored devices need agent programs installed on them to benefit from multi-vector detection strategy and automated defense responses.
- Rapid7 InsightIDR A cloud-based security service that requires device monitoring agent software to be installed on-premises. It is easy to install and includes automated threat mitigation.
- OSSEC A free, open-source IDS with a particular focus on log analysis. This is specifically a SIM but it can be expanded to be a full SIEM by feeding in live network traffic data from other monitoring packages. It installs on Windows, macOS, Linux, and Unix.
- SolarWinds Security Event Manager A SIEM tool from the market leader in IT infrastructure management tools, this security software can be calibrated to comply with many data security standards and it also includes automated incident response. This software installs on Windows Server.
- Heimdal Threat Hunting and Action Center This SIEM system is bundled into a cloud platform that gathers activity records from on-premises products that are running on a site. The platform also provides automated responses.
- LogRhythm NextGen SIEM Platform Uses AI methods for traffic and log analysis. The software package includes detailed user guides. It installs on Windows and Linux.
- AT&T Cybersecurity AlienVault Unified Security Management This is a major rival to QRadar SIEM and has a similar background – developed independently and bought out by a big multinational. It runs on Windows and macOS.
QRadar SIEM FAQs
How does QRadar SIEM use vmprotocol?
QRadar offers two types of virtualization. It is presented as a SaaS package on the cloud with an account structure that uses VMs to separate out accounts so one customer can’t break through into the account of another through the operating system. The other option is to install the QRadar software as a virtual appliance. This is IBM’s own VM protocol that contains an operating system.
How do you connect cloud service to QRadar SIEM?
You need to install an agent on the cloud service that you want QRadar to monitor, these are called Content Packs and they can be accessed from the marketplace of each platform, such as AWS and Azure. A guide for this process is available from within the QRadar platform.
What is the difference between QRadar and Splunk?
QRadar is a property of IBM and Splunk is a product of a separate company, called Splunk, Inc. These are not directly two competing products because Splunk is a data analysis tool, while QRadar only performs a SIEM function. However, Splunk can be enhanced by a paid product, called Splunk Enterprise Security. This is centered on a SIEM and it is a direct rival to QRadar.