You need to protect your USB firmware from malware and there are several proactive steps that can help mitigate the risk of infection. First, always keep the firmware of your USB devices up to date, as manufacturers often release security patches to fix vulnerabilities. Regularly check for updates on the manufacturer’s website and apply them when available.
Next, use trusted, security-focused USB devices. Opt for hardware that incorporates security features like encryption or built-in malware protection, which can prevent unauthorized modifications to the firmware.
Implementing strong endpoint security on all systems interacting with USB devices is crucial. This includes using antivirus software that specifically targets USB-related threats and ensuring the operating system is updated with the latest security patches.
Another important measure is restricting USB device usage within your network. Limit the devices that can be connected to computers, using tools like Device Control software to enforce access policies and prevent the use of unapproved USB devices.
Finally, educate users about the risks of plugging in unknown or untrusted USB devices, especially in public or unsecured locations. Raising awareness about the dangers of malware and phishing attacks can go a long way in preventing infections.
By combining these strategies, you can significantly reduce the likelihood of your USB firmware being compromised by malware. We examine these steps in greater detail in our guide.
Here is our list of the best USB firmware malware protection systems:
- ManageEngine Device Control Plus EDITOR’S CHOICE This on-premises package blocks all USB devices by default but then allows the system administrator to respectively authorize specific USB devices for use by a specific user. Runs on Windows Server. Start a 30-day free trial.
- Endpoint Protector by CoSoSys This cloud-based system can reach through agents to control all of the USB ports on your endpoints.
- Drivelock With this tool you can control USB ports and the package also includes antimalware and an encryption system. This is a cloud-based system.
You can read more about each of these systems in the following section.
What can Malicious USB Firmware Do?
By masquerading as a USB device, malicious USB firmware can perform any function that a USB device can – which is to say: effectively anything. In addition, most malicious firmware will pretend to function normally, transferring files regularly to provide a false sense of security. After all, viruses can spread faster if passed between numerous devices like a regular USB flash drive would.
One of the more common uses for malicious USB firmware is to send keypresses while masquerading as a keyboard. This ability could provide a hacker with remote control of a device via the fake keyboard, or more frequently, it will use simple macros to perform dangerous actions. For example, a macro could be set to open the command prompt, connect and download a small piece of software through cmd, run the program and even bypass the UAC prompt.
Another standard function is to infect files stored on the device. However, most smart firmware won’t contaminate the file while on the USB flash drive itself, instead choosing to attach malicious content to a file as it is transferred off the flash drive – thus avoiding incriminating the USB drive.
USB Virus Propagation
A new threat spawned by malicious USB firmware transforms regular USBs by corrupting the firmware into self-replicating virus hosts.
This threat simply transfers a virus onto a host device like a laptop PC, and then when someone connects a USB drive, it modifies the drive firmware to propagate the same virus onto any device it connects to. By reproducing the same cycle of virus-based USB firmware, it can quickly spread the malicious firmware across an entire business, then to other companies, and beyond.
This is currently the most dangerous form of malicious USB firmware despite not achieving anything on its own because the other issues listed within the article can be attached to this propagation method. This means it can spread malware between numerous, often globally-spanning networks at a rapid pace.
What can you do to Protect your USBs?
Since USB flash drives are the root of this virus propagation, securing your USB flash drives is the most straightforward approach. However, this kind of threat doesn’t need to spawn from a USB flash drive and can come from anywhere within your network – a computer might inadvertently acquire a virus that self-replicates and attaches to your USB flash drives.
This means that to be safe, and you need to approach the issue from both angles: externally protecting your company USBs and internally protecting your devices that might connect to USB flash drives.
Here are some solutions that you can do to secure your network and protect your USB firmware from this kind of threat:
- Avoid unknown USB devices
- Disable autoplay
- Secure USB flash drives
- Employ device control software on your network
We’ve broken down each of these solutions below for more information.
Avoid Unknown USB Devices
Between 2010 and 2015, a strange but surprisingly effective way of spreading malware emerged: leaving maliciously infected; USB drives out in public. Curious individuals would pick up these flash drives, take them to work or school, and plug them in, only to infect the network with whatever malicious content was installed on the firmware.
In recent years, this has stopped being a frequent issue due to educating people on the dangers of plugging in wild USB devices. However, it is still something to consider, especially with the wave of USB-centric devices dominating the market.
While this method is typically associated with USB flash drives, theoretically, any device that connects via a USB port can take advantage of this strategy. Therefore, be cautious of any unknown peripheral, and as a network administrator, be sure to inform and educate your users on the dangers of connecting random devices into their USB ports.
Disable Autoplay
Windows Autoplay is one of the most dangerous vulnerabilities that can affect the physical security of a network. Yet, all it typically does is save the 5 seconds it takes to run a connected device manually.
Malicious USB firmware can take advantage of Windows Autoplay to execute programs that can entirely cripple your network. While more advanced malware can typically bypass it somehow, it’s best to disable this Windows function across your network as a real catch-all for the majority of USB firmware-based malware.
On an individual machine, you can disable Windows Autoplay by following these steps:
- Press the Windows key and open the start menu
- Type ‘autoplay’ and open the Windows Autoplay Settings option
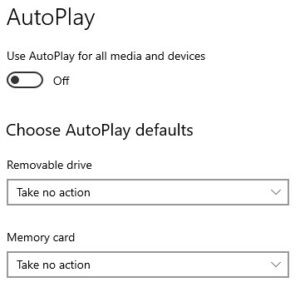
- Toggle ‘Use Autoplay for all media and devices’ to Off. Also, switch the Autoplay defaults for Removable drives and Memory cards to ‘Take no action.’
If you want to disable autoplay via Group Policy, follow these steps:
- Press the Windows key and open the start menu
- Type ‘gpedit’ into the search bar and click on the Edit group policy option
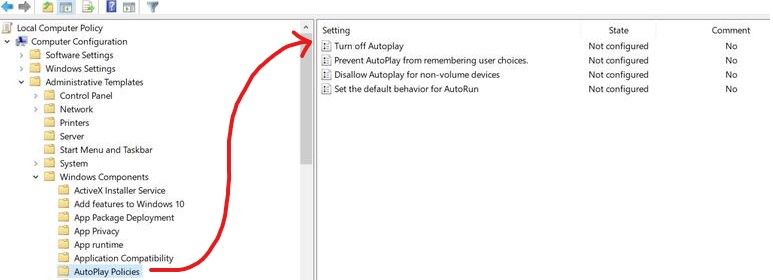
- Navigate to the following option:
Computer Configuration > Administrative Templates > Windows Components > Autoplay Policies - In the ‘Turn off Autoplay’ option, set it to Enabled on All drives – click Apply.
- In the ‘Set the default behavior for Autorun’ option, set it to Enabled and set the default Autorun behavior to ‘Do not execute any autorun commands’ – click Apply.
Secure USB Flash Drives
There are several securely built USB flash drives available on the market. However, if you find yourself frequently using a single personal flash drive, perhaps that carries portable software for net-admin purposes, then you may consider upgrading.
Encrypted flash drives such as the ones produced by Ironkey are one such solution. By encrypting access to the flash drive, you prevent both manual and automated infection of the USB’s firmware. In addition, you can also be confident that the core firmware on such a drive is designed with security in mind, making it more resistant to malicious modification from viruses.
Keypad flash drives like the Kingston Datatraveler 2000 are another example of hardware-based USB protection. By incorporating a physically entered password, this solution completely removes all possibility of software infection unless someone both knows your passcode and has physical access to your USB flash drive. Additionally, most Keypad Flash Drives also come with encryption capabilities, allowing you to double-up on your security.
Several USB Flash Drives also come with write protection, which is typically a tiny latch on the side of the flash drive. When flicked on, write protection disallows the USB drive from reporting information to or from a connected device. This allows you to browse the contents of the drive without it infecting your device. In addition, because the write protection latches are physical, they can prevent all software-based infections, much like a keypad solution.
Device Control Software
One of the absolute best solutions that you can employ across your network is device control software. This software monitors and controls any data transferred between the devices on your network and any removable storage such as USB flash drives. Device control software goes hand-in-hand with Data Loss Prevention (DLP) software, and you’ll notice that several device control solutions come as part of complete DLP software suites.
By providing a centralized point of control for all external device connections, you can use device control software to block any unauthorized USBs on your network physically that you are unauthorized. Alternatively, if you still allow flash drive connections, you can monitor whatever files are transferred and flag potentially malicious files.
Our methodology for selecting malware protection for USB firmware
We reviewed the market for USB firmware malware protection and analyzed the options based on the following criteria:
- Blocks on USB ports
- Device security posture scanning
- Centralized device control
- The option to control devices on remote sites
- Antimalware scans upon connect
- A free trial or a demo that enables an assessment of the system to be performed before purchasing
- Value for money from a service that is offered at a reasonable price with respect to the level of service that is provided
There is a wide variety of device control software on the market. We’ve looked at several solutions for you to check out below.
1. ManageEngine Device Control Plus (FREE TRIAL)
Device Control Plus by ManageEngine is a complete DLP software solution that provides the ability to monitor and block USB access across your network. By providing you the ability to monitor network traffic between your endpoints and USB flash drives, you can detect problematic malware and prevent them from accessing your sensitive data.
Key Features:
- Uninterrupted device control
- Trusted device lists for granular control
- Grant temporary access upon request
- Monitoring dashboard
- Block unauthorized USB access
Why do we recommend it?
ManageEngine Device Control Plus renders all USB devices inoperable on all of your endpoints unless the central administrator allows it. A device can be approved for use only by one user and only for one endpoint. All activity on a USB device connected to your systems is logged.
Who is it recommended for?
This package is suitable for all sizes and types of businesses. It controls endpoints running Windows and macOS, along with its USB ports. There is a Free edition available that can extend controls to multiple sites but only 25 devices. That is very appealing for small businesses. The system is a software package for Windows Server.
Pros:
- Designed to work right away, features over 200 customizable widgets to build unique dashboards and reports
- Leverages autodiscovery to find, inventory, and map new devices
- Uses intelligent alerting to reduce false positives and eliminate alert fatigue across larger networks
- Supports email, SMS, and webhook for numerous alerting channels
- Integrates well in the ManageEngine ecosystem with their other products
Cons:
- Is a feature-rich tool that will require a time investment to properly learn
The software is built with network administrators in mind, providing a simple agent rollout and an associated monitoring dashboard for your remote net-admin needs.
EDITOR'S CHOICE
ManageEngine Device Control Plus is our top pick for a USB firmware protection system because it allows you to block all USB devices and then selectively enable one only for use by an authorized user. This system is part of a data loss prevention package and it blocks malware and intruders. The Device Control Plus system is an on-premises package and it will protect all of your endpoints across the network from one central server.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/device-control/
OS: Windows Server
2. Endpoint Protector by CoSoSys
Endpoint Protector by CoSoSys has a Device Control function that ultimately secures your network from malicious USB firmware-based attacks. By providing a lightweight agent installed across your devices, you can monitor your network using the web-based interface.
Key Features:
- Uniquely identify connected USB devices
- Granular control over USB ports
- Reporting for USB activity
- Remote data encryption control
- Block unauthorized USB access
Why do we recommend it?
Endpoint Protector is a useful tool for protecting USB devices as well as for controlling their connections to corporate endpoints. A central controller can authorize a USB stick for general use anywhere, for use on a specific device and/or for use by a named user. The system creates an encrypted vault for storage on the USB, which prevents any malware from touching the firmware.
Who is it recommended for?
This is a good option for any business. All USB devices are blocked by default and a central administrator can authorize devices by serial number. The package can reach out and control ports on endpoints running Windows, macOS, and Linux. There isn’t a free edition for small businesses.
Pros:
- Custom security policies can be based on the user rather than the machine
- Automatically assesses risk based on vulnerabilities found on the endpoint
- Can alert to improper file access or insider threats (Acts as a DLP solution)
- Prevents data theft and BadUSB attacks through device control settings
Cons:
- Would like to see a trial version available for testing
Endpoint Protector also secures your network from data leakage by taking advantage of data loss prevention systems, in addition to protecting USB-propagated malware.
3. Drivelock
Another solution for your consideration is Drivelock. By utilizing both the drivelock USB restrictions and included encryption and antivirus system, you can completely secure a device from USB-based malware infection. In addition, this software allows you to determine security restrictions based on each type of removable storage beyond just USB flash drives.
Key Features:
- USB access restrictions
- Inbuilt file encryption and antivirus
- Network access reports
- Basic security monitoring
- Granular control based on file type
Why do we recommend it?
DriveLock supplies a range of security tools, including vulnerability scanners and a device control system. The scanner can reach out to attached devices, so that presents one option for protecting your USB firmware. The USB protection service creates an encrypted vault for storage that also protects the firmware from attack. The system also logs all files transferred to and from USB sticks.
Who is it recommended for?
This tool is accessible for any size of business. You can get a 30-day free trial of the tool but there isn’t a free version for small businesses. DriveLock doesn’t publish a price list for any of its products, which will deter small businesses from enquiring about the Device Control unit.
Pros:
- Combines device control with DLP and anti-malware features
- Common Criteria EAL 3+ certified
- Highly scalable – ideal for larger environments
- Offers disk encryption
Cons:
- Not ideal for a non-technical audience
Drivelock has a 30-day free trial for the software, so you can test out the functionality before committing.
In Summary
Malicious USB firmware can pose a massive threat to your network security. A single corrupted USB flash drive can infect your entire network by taking advantage of new propagation techniques.
As a net-admin, it is your responsibility to protect your network from malicious USB firmware-based attacks. So not only will you secure your network, but you’re also doing your part in cutting off potential access points for globally-reaching infection attacks.
We’ve covered several methods which you can use to secure your network and USB flash drives. At the minimum, you should educate your users on the dangers of connecting unknown USB devices, and consider deactivating Autoplay via group policy to increase your security further, you have several other available options, such as enhanced USB flash drive hardware security. You might also want to consider one of the various device control software options available, such as Device Control Plus or Endpoint Protector by CoSoSys.
USB firmware malware protection FAQs
Can firmware contain virus?
Firmware isn’t shipped with viruses in it but it can be corrupted. Viruses usually run on top of the firmware but use firmware utilities to cause damage to systems or steal data.
Can malware infect a USB?
Malware can infect a USB and from there pass onto the computers to which that USB device is connected. Malicious software can also make a USB stick appear to be a human input device (HID) and then use fake keystrokes to access accounts by activating the computer’s password locker.
Can ransomware spread through USB?
USBs are often used to spread malware. It is difficult to get targeted malware onto a specific computer and so dropping an infected USB in the car lot or lobby of a victim company is one way to get a virus or a remote access Trojan onto one of the enterprise’s endpoints.