Privileged password management refers to the secure management of login credentials for accounts that have elevated or administrative access to critical systems, applications, and infrastructure within an organization. These privileged accounts, often referred to as “privileged accounts” or “superuser accounts,” hold significant control over sensitive systems, making them prime targets for cybercriminals.
If you only have time to learn about the tools we review, here is our list of the best privileged password management tools:
- ManageEngine ADSelfService Plus EDITOR’S CHOICE This service improves the usability of Active Directory and automates password resets. Available for Windows Server, AWS, and Azure. Start a 30-day free trial.
- ManageEngine PAM360 (FREE TRIAL) This bundle of ManageEngine modules provides privileged access management, password controls, and key management. Available for Windows Server, Linux, and Azure. Access the 30-day free trial.
- KeeperPAM A cloud-based platform with advanced features to streamline access to critical resources. It can be used across any device and environment.
- N-able Passportal A cloud-based password manager combined with a document manager.
- BeyondTrust Password Safe A comprehensive password discovery, management, and session monitoring system.
- Delinea This platform includes a range of system security tools and access control tools.
- CyberArk Privileged Access Security This tool discovers and manages privileged accounts and logs session activities.
Effective privileged password management involves a range of practices and tools designed to secure, control, and monitor access to these high-level accounts to prevent unauthorized access and mitigate security risks.
At its core, privileged password management ensures that passwords for privileged accounts are stored securely and are regularly rotated. This prevents static or easily guessable passwords from being exploited by attackers.
Password vaults, which are secure repositories for storing and managing sensitive credentials, are commonly used in privileged password management systems. These vaults often include features like automatic password rotation, policy enforcement, and audit logging to ensure compliance with security best practices and regulatory requirements.
Privileged password management solutions provide granular control over who can access specific privileged accounts. This helps enforce the principle of least privilege (PoLP), ensuring that users and administrators only have access to the systems necessary for their job functions. In addition, many privileged password management systems include session recording and monitoring capabilities, allowing organizations to track and audit administrative actions for compliance and security purposes.
Controlling privileged passwords is an essential aspect of organizational cybersecurity, helping to safeguard critical systems from breaches and minimize the risks associated with compromised administrative credentials. By effectively managing privileged accounts, organizations can better protect their sensitive data, comply with regulatory frameworks, and maintain a more secure IT environment overall.
Identifying privileged accounts
Even if you are setting up a new company and creating accounts for new staff, you will still have privileged accounts on your system before you have created any new credentials. Many privileged accounts exist without the systems administrator knowing about them. IoT devices and even network equipment are shipped with default access account for managers and even firmware-enabled accounts that carry default passwords.
These embedded accounts present a serious security weakness and need to be tightened up by changing the allocated password. Finding those accounts can be difficult and an automated discovery function in the password manager is a great help.
So, stage one, when introducing a new privileged password manager is to locate all of those privileged accounts.
Password protection
All account passwords need to be stored. In most cases, the direct control over access to a resource is implemented by a controller that is related to that service. For example, Microsoft’s Active Directory governs access to a number of Microsoft products, such as Microsoft Exchange Server or SharePoint Server. Usually, a password manager sits on top of the native access rights controllers and coordinates accounts across the enterprise.
As the controlling access rights system is resident locally, storing the privileged password manager’s password vault in the same location loses an opportunity to have an off-site store that could be used for disaster recovery.
Wherever the password manager is installed, it is a good idea to have the data store associated with it in a different location. That means attaching the application to a server on a remote site or renting storage space on a cloud server.
Cloud-based privileged password management tools that are available in the cloud have a double advantage: first, they are bundled together with remote storage space and second, being charged for a subscription rather than the full fee for the software that would need to be paid upfront.
Vulnerable accounts
Abandoned accounts present opportunities for intruders and accounts that have high access privileges save hackers a lot of time and effort. Identifying those accounts and closing them is an important task for a privileged account manager. Accounts that rarely change their passwords are also vulnerable.
Privileged password managers should include enforced password changes and a system to ensure that strong passwords are used on those accounts.
Accounts previously used by staff who have left the company are easy to spot. However, the definition of abandoned accounts also applies to those accounts that were created but never used by users who are still on the payroll. Those accounts are harder to spot just by scanning through the records of HR. An activity logging system has a better chance of highlighting accounts that are not active.
Duplicate accounts
A large organization with several IT support departments on different sites has a strong possibility of creating more than one account for the same person to access the same system. Those extra, unused user accounts offer opportunities for intruders.
Centralizing the administration of passwords and maintaining an alphabetical list of employees with user accounts should reduce the incidences of duplicated accounts. Putting that list in a searchable database reduces the likelihood of creating more than one account for the same person. Privileged password managers give administrators the ability to keep tight control over the allocation of user accounts.
Account management oversight
One problem of focusing all account controls in one application in one location and giving access to those controls to a very limited number of people is that those favored administrators accumulate a lot of power. That power can be abused. The actions of administrators in charge of managing privileged accounts need to be supervised.
The oversight of password management administrators doesn’t require a company director to watch over the shoulder of IT technicians all day. Logging and auditing functions built into the privileged password management tool should take care of that.
Naturally, password manager access and the actions occurring in each session need to be analyzed. So, the company needs a cybersecurity officer who is able to deploy more tools to properly spot malicious activity. Those investigations will be greatly aided by a security information and management tool.
These auditing functions are essential if the company is implementing a data protection standard. User account controls are stipulated in many data security standards, such as HIPAA and PCI-DSS.
Password policy consistency
Even highly experienced and qualified staff sometimes make mistakes. Computers are much better at performing repetitive administration tasks faultlessly. Privileged password management systems can periodically audit password records, monitor for account login sessions, trigger alerts, write to logs, and shut down suspicious activity effortlessly.
A privileged password manager should be able to help you formulate a password policy and should also have the utility to implement those decisions through settings and automated workflows. Tight password policies, accurate policy implementation, activity tracking, and automated remediation are also essential services for system security.
Implementing privileged password management
Many system administrators still rely on spreadsheets to record user accounts and passwords. Nowadays, the risk of litigation triggered by data disclosure means that these manual systems just aren’t sufficient anymore.
Just as manual password management processes aren’t viable, manually planning the implementation of a comprehensive privileged password management system isn’t good enough. You need to choose a password management tool and use it to clear up historical account errors, such as duplicated accounts and to search the company’s IT resources for hidden, embedded privileged accounts.
A comprehensive password manager should be able to guide the administrator through the process of defining a comprehensive password policy and should also be able to implement that strategy.
Going forward, once the system has been cleaned up and policies are in place, the password manager will take care of most of the account administration tasks. It will take a lot of the strain off your technical staff and providing accountability for auditing and data protection conformance.
Here is our list of the five best-privileged password management tools.
The best privileged password management tools
There are many password management tools available and not all of them are good. It can take a lot of time to investigate all of the password managers for suitability. The following shortlist of five excellent privileged password managers will help you find the ideal system for your company in a short space of time.
Our methodology for selecting a privileged password management system
We reviewed the market for IoT update management tools and analyzed the options based on the following criteria:
- An access rights manager that can cover a range of systems
- A single sign-on (SSO) option
- User groups to segment access rights
- Permission levels to restrict the actions that each group can make
- The ability to revoke rights or set them with an end date
- A free trial or a demo package that provides an assessment opportunity without paying
- Good value for money from a reliable ARM with a reasonable price tag
Using this set of criteria, we looked for flexible access rights management tools that can implement privileged password management.
You can read more about each of these options in the following sections.
1. ManageEngine ADSelfService Plus (FREE TRIAL)
ManageEngine ADSelfService Plus runs on top of Active Directory, providing better password management functions. The system manages password complexity rules and multi-factor authentication. The service will roll out passwords to multiple AD domains be they on premises or cloud systems, such as Microsoft 365, and Google Workspaces.
Key Features:
- Creates a single sign-on environment
- Manages passwords for Active Directory
- Watches failed logins
- Enforces password strength
- User-commanded password resents
Why do we recommend it?
ManageEngine ADSelfService Plus integrates with Active Directory to improve password security policies and help manage group allocations. The tool can implement multi-factor authentication and locate local stores of AD credentials. It provides a password reset screen for all corporate users to access and reset their own passwords.
The “self-service” element in this package is a user portal that can be set up as a screen lock on a desktop or an app on a mobile device that lets the user login once and then permits access to a menu of allowed applications. The portal also includes a service that allows users to reset their accounts without recourse to technical support staff.
Who is it recommended for?
A small business that has few users and resources won’t need this package however, all other businesses would benefit from using this system as long as they have Active Directory for their access rights management system. This is a software package for Windows Server and it is also available on AWS and Azure marketplaces.
Pros:
- Tighter access rules
- User controls
- Security monitoring
- Interface for mobile apps and desktops
Cons:
- The cloud version isn’t a SaaS package
ADSelfService Plus is available for installation on Windows Server or as a service on the marketplaces of Azure and AWS. There are three editions: Free, Standard, and Professional. The top plan provides local cache management and a password policy enforcement system as well as the features of the Standard plan. The Free edition is the same as the Professional package but limited to managing 50 user accounts. You can get the Professional edition with a 30-day free trial.
EDITOR'S CHOICE
ManageEngine ADSelfService Plus is our top pick for a privileged password management solution because it tightens controls and makes passwords more complex while simultaneously making access to users simpler. Multi-factor authentication locks out password cracking and self-service reset requests make users less nervous about using original and complex passwords. This system creates a single sign-on environment and coordinates with multiple instances of Active Directory, including cloud implementations.
Download: Get a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/self-service-password/download.html
OS: Windows Server, AWS, and Azure
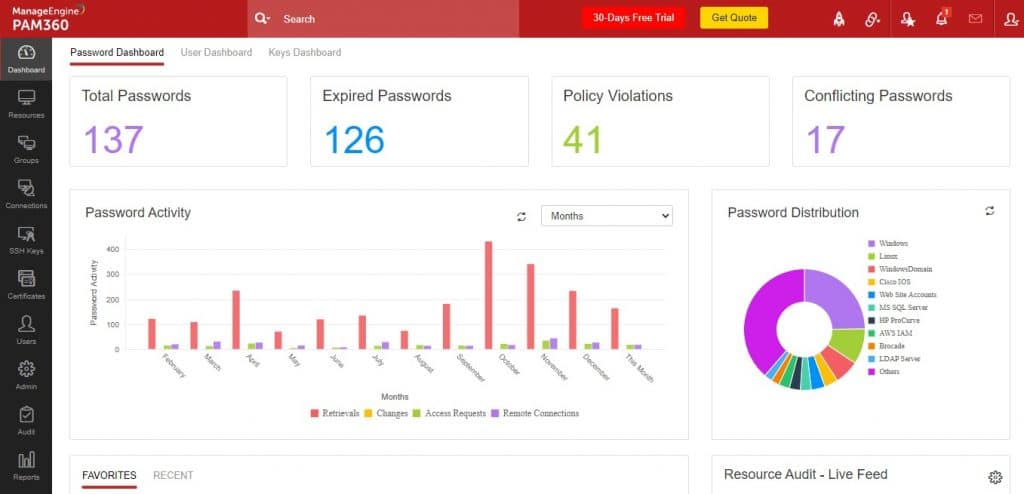
2. ManageEngine PAM360 (FREE TRIAL)
ManageEngine PAM360 is a unified package of three tools that are also available individually from the provider. These are Password Manager Pro, Access Manager Plus, and Key Manager Plus. This combination keeps user passwords confidential, providing a secure, encrypted password vault. The package also gives you management of privileged accounts and monitoring for privileged account usage.
Key Features:
- Password protection
- Remote access controls
- Privileged account activity monitoring
- Security key management
Why do we recommend it?
ManageEngine PAM360 manages access credentials for technician teams. These accounts have the ability to set up and modify user accounts and also change settings on network devices and endpoints. Thus, they need to be limited for use by just a small number of people. This tool guards all privileged account credentials in a central vault.
The PAM360 system is particularly interesting for businesses that operate a central IT support team that needs to access endpoints and resources on remote sites. The tool provides the login credentials for these remote, managed devices automatically, which removes the need for each user to be able to know and disclose the passwords. Protection of privileged accounts is extremely important because the power that this level of access provides makes them prime targets for hackers.
The account protection and SSH key management features in this package make PAM360 an essential service for businesses that need to provide compliance with HIPAA, SOX, and PCI DSS. The service can be tuned to deploy workflow pre-sets by specifying the standard that you need to follow in the setup screens of the console. The service will produce an audit trail and generate appropriate reports.
Who is it recommended for?
This package is designed for use by IT department teams. It wouldn’t be necessary for a small business with one administrator to use this system because it is designed for pooled account credentials that are shared among a team. The package will track all activity on a system when the privileged account is used.
Pros:
- Good for development teams and well as support technicians
- Ensures connection security for remote access and file movements
- SSH and SSL key management
- Privileged user activity tracking
Cons:
- Not a SaaS package
There is only one plan for PAM360, which is called the Enterprise Edition. There is no free version. The software for this package runs on Windows Server or Linux or you can take it as a service in your Azure account. ManageEngine offers PAM360 on a 30-day free trial.
3. KeeperPAM

KeeperPAM is a cloud-based tool that can secure access to every account and resource in your organization. It uses a zero-knowledge and zero-trust architecture, as a result of which, every user must be explicitly authenticated to gain access to a resource. This approach offers visibility to admins as they can know who is accessing what resource and when. More importantly, this approach can prevent unauthorized access.
Key Features:
- Compliance with CISA and other standards
- Multiple remote session protocols
- Just-in-time credentials
- Integrates well with different tools
- Single UI console
Why do we recommend it?
KeeperPAM is a simple but powerful tool for managing privileged access to resources. Its intuitive UI provides complete visibility to IT admins and they can revoke access or take other actions if needed.
A highlight of this tool is its Just In Time (JIT) provision, using which IT admins can provide access to a resource for a limited time or a session. With this feature, your organization can eliminate standing privileges, which could lead to misuse and insider attacks.
It also integrates well with all devices and platforms. KeeperPAM is also ideal for developers as it can be integrated into CI/CD pipelines, DevOps tools, custom environments, and more. You can also create end-to-end encrypted tunnels for securely sharing passwords.
Who is it recommended for?
It works well for organizations that want to improve their security through privileged access management. It is also well-suited for MSPs who need credentials to handle remote sessions.
Pros:
- Development and security teams Highly useful for dev, security, and DevOps teams.
- Password rotation Automates the process of password rotation through a zero-knowledge vault.
- Simple deployment It can be deployed through a web browser or a desktop app.
- Secure credentials Removes plaintext credentials and SSH keys from all devices.
- Limits passwords Limits passwords to specific sessions or time-frames.
Cons:
- Internet Connectivity Highly dependent on Internet connectivity.
KeeperPAM offers plans for different audiences, like Business and Enterprise, family, student, and military and medical personnel. Start a 30-day free trial.
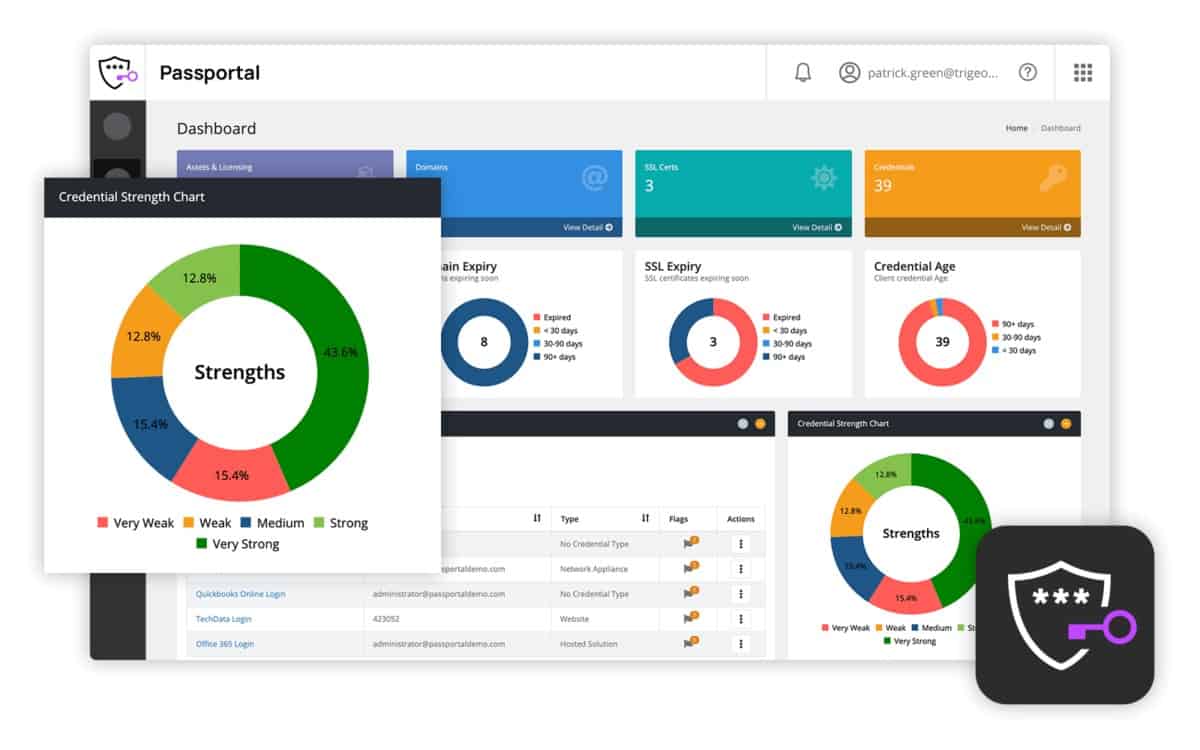
4. N-able Passportal
N-able Passportal is a cloud-based password manager, charged by subscription, that is paired with a document management tool plus secure cloud storage space. The package is covered by encryption for all communication between the client site and the Passportal servers. Storage space is also secured by encryption.
Key Features:
- Cloud-based
- Connection security
- Documentation manager
- Password generator
Why do we recommend it?
N-able Passportal is a group password manager that has a special routine for guarding privileged accounts, which tracks and logs their usage. This package is hosted in the cloud and creates one central password vault for the entire technician team. Credentials are distributed without the users being able to see the passwords.
The Passportal system includes an auto-discovery function that discovers all applications and resources on Windows-managed systems where password protection is implemented. The service then compiles its own register, referring to the local Active Directory system. Once that setup phase has been completed, you can implement your password policy in the Passportal interface and all those changes immediately get rolled out to Active Directory.
The password management system includes a password generator to create complicated passwords from random strings of characters. It can enforce password rotation and implement those changes automatically. It can also implement multi-factor authentication. The tool will also update the system tools on your network that require privileged access so that they have the new password available to them.
The service includes an auditing and reporting module, which is able to demonstrate the freshness of passwords and their usage.
Who is it recommended for?
This package is intended for use by managed service providers. However, IT departments could also use it. MSP technicians have two levels of access requirements. The first is to the systems in their own office for their own work and the second is for access to the resources of their clients.
Pros:
- Supports automatic Active Directory sync via LDAP
- Can run access audits to easily identify internal changes made during a period of time
- Supports compliance reporting to identify weak passwords and force changes based on policy
- Users generate their own encryption key, securing their cloud data from third parties, including Passportal
- Includes a document manager – great for helpdesk teams
Cons:
- Better suited for small organizations and growing MSPs
An add-on available with this password manager, called Passportal Blink is a self-service portal that enables users to reset their passwords when they forget them. That feature will drastically reduce the number of support calls that your IT team has to field. You can get a closer look with a free demo.
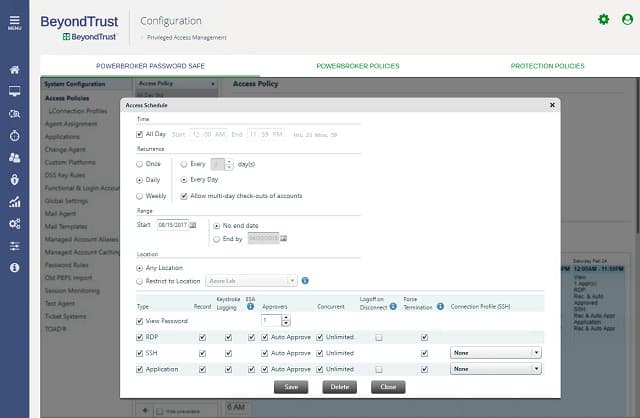
5. BeyondTrust Password Safe
Password Safe from BeyondTrust is a cloud-based password management service. This tool has an autodiscovery feature that will find all of the account-protected resources and all of the passwords issued against them. The discovered passwords get stored in an encrypted, secure password vault. That autodiscovery continues throughout the service life of the software and stems from contact with the local access rights controllers on the client’s system. The interaction with those controllers keeps them updated with any changes made in the Password Safe dashboard.
Key Features:
- Password vault
- Password strength enforcement
- Compulsory password rotation
Why do we recommend it?
BeyondTrust Password Safe provides a central enterprise password vault for passwords, keys, and other secrets. This system locates and then stores all access credentials and identifies those that get privileged access. It then tracks all user sessions, generating logs for compliance auditing and change tracking.
The password manager tracks down embedded accounts and removes them. It also enforces strong passwords and periodic password renewal. The tool can monitor resources both on the client’s site and on the cloud. This application is also a cloud resource.
Who is it recommended for?
This package is suitable for mid-sized, large, and very large businesses. The client list for the service includes the University of Utah, ServiceNow, and Wynn Resorts. The system is based in the cloud, so it is able to control access to systems on different sites and also cloud platforms through one account.
Pros:
- Uses autodiscovery to find privileged accounts for management
- Offered as a highly scalable cloud solution
- Features a great UI without sacrificing any important features
- Supports auditing for compliance and investigations
Cons:
- Must contact sales for pricing
- Would like to see a free trial for testing
Auditing and reporting functions in the tool monitor the sessions of privileged users, leaving an audit trail to help show compliance to data protection standards. The service provides all the same level of protection for non-privileged accounts. The auditing and logging features of the service feed into an analysis module that helps systems designers spot weaknesses in the security of the network.
6. Delinea
Key Features:
- Account autodiscovery
- Deployment options
- Endpoint access control
Why do we recommend it?
Delinea is a platform of security systems for privileged access management. This system was, until recently, called Thycotic and it discovers, collects, and stores access management credentials, keeping them in a central vault and distributing them confidentially. The system also includes a behavior analysis service for account takeover detection.
This tool covers network devices, security devices, software, virtualizations, and databases. It also enforces password rotation for network accounts and logs the activities of privileged accounts.
The second tool that would be of interest to privileged password management is Privilege Manager. This tool focuses on protecting privileged accounts that have access to endpoints and system applications. Privilege Manager is available for installation or can be accessed as a cloud service. The tool monitors computers that have Windows and MacOS operating systems. It controls accounts and logs account activities.
Who is it recommended for?
As with most of the tools on this list, the Delinea platform is suitable for mid-sized and large companies. The client list of the service includes Cisco Systems, BP, and ESPN. The service is suitable for controlling access to resources for development teams as well as for operations technicians.
Pros:
- Continuously discovers new accounts for credential management
- Has a wide range of policies and settings for custom password policy enforcement
- Supports Windows and macOS – great for hybrid OS environments
- Offers a suite of other security tools that integrate nicely with tool
Cons:
- Better suited for larger environments
Both Secret Server and Privilege Manager can be tested on free trials.
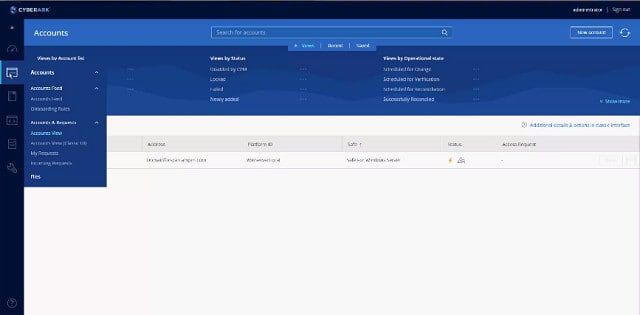
7. CyberArk Privileged Access Security
CyberArk has several password management products. The one that has the widest coverage is the Core Privileged Access Security system (PAS). This package is a bundle of CyberArk products: Enterprise Password Vault, Privileged Session Manager, and Privileged Threat Analytics. The software can be installed on-premises or accessed as a cloud service.
Key Features:
- Password vault
- Session logging
- Password policy enforcement
Why do we recommend it?
CyberArk Privileged Access Security implements a Zero Trust Access strategy in its privileged access management. Access to systems is channeled through a user portal, which enables the system to block access or monitor all activities. Account credentials are stored in a secure vault. The access portal can identify automated attacks.
The PAS system is able to scan a client’s system for resources that require access credentials and it then interfaces with the local access rights system to acquire all of the privileged account passwords and stores them in a vault.
Who is it recommended for?
This system simplifies access controls by centralizing credentials storage and the login system in one cloud platform. The tool is a good solution for businesses of all sizes but probably a single-tech small business wouldn’t need this level of service. The company doesn’t publish its price list.
Pros:
- Can manage access rights and alert to improper access by privileged users
- Autodiscovery quickly discovers resources to monitor
- Makes it easy to create and enforce custom credential policies
- Available as a SaaS or on-premise solution
Cons:
- Would like to see a full trial rather than a demo
- Pricing isn’t publically available, must contact their sales team
The service can enforce password rotation and it constantly monitors activity, logging the actions taken with each privileged account. Other features of this system are risk assessment and automated threat remediation. This tool has many features that are usually encountered in an intrusion threat prevention package.
Choosing a privileged password management tool
Protecting privileged accounts is essential for any business because failure to protect the business’s data and information held on the system about others can create legal problems. Data loss can lose your company its trade secrets, it can get you sued by the people whose information you store and it can also get you fines from authorities. Data protection is often a pre-requisite in order to be allowed to bid for work and non-compliance with data security standards can lose you customers.
The five privileged password management systems in this guide are the industry leaders. If you spent time looking at the entire selection of available software tools in this category you would waste a lot of time and end up shortlisting these same five. Check out the demos and the free trials that these service offer in order to make a decision about which to buy.
Privileged password management FAQs
What is privilege password?
Privileged passwords are really privileged accounts. A privileged account is typically used by a system administrator and it gives the user the ability to create user accounts and allocate access privileges to others. Other levels of privileged accounts include managerial responsibilities that get access to restricted data, such as customer information, accounting data, or intellectual property. User accounts with privileged access rights are the ultimate goal of data thieves because these accounts have access to data that can be sold for a high price and also allow the intruder to access all of the resources of the target company.
What is privilege management?
Privilege management is more correctly called privileged account management. The concern of these systems is to protect the credentials of user accounts that have access to high-value data and other valuable company resources. Privileged account management is conducted from an administrator account that is itself a privileged account. Tasks involved in this process include activity monitoring and account auditing. Credentials need to be protected from access even by the administrator and attempts to trick users into disclosing their credentials need to be blocked.
What is a PAM and why is IT important?
PAM stands for privileged access management. This process requires caution over the granting of privileged access rights, sticking to the principle of allowing the least access that each user needs in order to work effectively. PAM requires that the credential with elevated rights should be protected from disclosure and that disgruntled employees can’t become insider threats. Privileged accounts also need to be protected from phishing attempts and other credentials theft techniques.
Image by Peggy und Marco Lachmann-Anke from Pixabay