Detect and eliminate threats delivered to your business inboxes before they reach you with these phishing protection tools.
Here is our list of the best phishing protection tools:
- Guardz EDITOR’S CHOICE Platform of security monitoring services includes an email scanner that detects phishing attempts as well as spam, malware, and impersonation scams with automated responses, activity logging, and threat analysis utilities. Get a 14-day free trial.
- ManageEngine Browser Security Plus (FREE TRIAL) A browser security solution that enables IT admins to configure browser settings across all users in a single click, to reduce phishing risks. Get a 30-day free trial.
- Trustifi While safeguarding your email traffic from BEC attacks, Trustifi effectively identifies infections that transmit malware and ransomware and alters authorized technicians through a first-rate notification system.
- TitanHQ Anti-Phishing Protection Cloud-based service intercepts emails heading for your Exchange Server instance and assesses them for signs of phishing.
- Avanan Offers one of the most complete cloud-based email security solutions on the market thanks to its strong defense capabilities, assuring the security and compliance of your network’s whole email infrastructure.
- Abnormal Security Abnormal searches for deviations from the usual by analyzing a wide range of data and creating profiles of recognized acceptable behavior in your surroundings.
- Barracuda Sentinel By using a cutting-edge API-based architecture, Barracuda Sentinel’s AI engine can examine past emails and identify users’ unique communication preferences.
- BrandShield One of a handful of specialist security solutions that are focused on safeguarding the identity of your company and its personnel.
- Proofpoint Essentials Multi-layered anti-virus, anti-spam, and phishing detection engine from Proofpoint offer complete protection against threats sent via email.
Since you’re reading this article, you are probably at the absolute minimum, technologically savvy enough to recognize a phishing email as it hits your inbox. However, you might not be familiar with more advanced threats such as ‘spear phishing’—which is the act of using trusted senders to target your business with legitimate-seeming phishing attempts. Your end users are also likely not as technologically aware of phishing attempts, and even with education, phishing scams can still threaten your business.
One of the most insecure outlets for your entire network is your business email. It provides an almost completely open-ended chasm directly to your end users, with the capability to share malicious files and content with limited oversight. The truth remains that email is an old method of communicating information, and has all the trappings of an older technology that has been perpetually dragged along as the rest of the information technology industry moves forwards. Regardless, it’s here to stay, so you need a solution to secure your email—not just from outside threats, but it is equally important to protect your end users from themselves.
One of the best methods of securing your email infrastructure is by integrating a phishing protection tool into your environment. These tools integrate with your system typically via a pre-established setup for platforms like Office 365 or Google Workspace; or through an API with flexible integration options for your custom email system.
Phishing protection tools then employ a variety of systems to prevent your end users from falling prey to phishing scams. The most fundamental function they provide is simply scanning your inbound and outbound emails for malicious content, such as predatory URLs or malware attachments. Other features might include phishing simulations, which send fake phishing scams to your end users to test their understanding of email security—a helpful tool in educating your users on the risks posed by email communication.
Our methodology for selecting phishing protection systems
We reviewed the market for email security services and analyzed the options based on the following criteria:
- Service that can identify spoofed email addresses
- Scans for malicious URLs in emails
- AI processes to spot impersonation in BEC and spear phishing attacks
- Additional protection against malware and ransomware
- Identification of compromised accounts through behavior analysis or Dark Web scanning
- Free trial or a demo service for a cost-free assessment opportunity
- Value for money from a reliable email security package that is offered at a fair price
The best phishing protection tools
1. Guardz (FREE TRIAL)
Guardz is a cloud platform that provides security scanning and automated responses. It covers endpoints, cloud data accounts, and email systems, and also email security monitoring as part of a platform of system-wide security tools. The email security service is able to identify phishing attempts and remove them from user mailboxes to a quarantine area. The tool is also a spam blocker and it will detect impersonation attempts. Guardz also scans attachments and removes emails that are carrying malware.
Key Features:
- Email Scanner: Spam, malware, and phishing protection
- Cloud-Based: No need to host
- Microsoft 365 and Google Workspace Compatibility: Operates as a plug-in
- Phishing Simulator: User awareness training
- Dark Web Scanner: Discovers compromised credentials
Why do we recommend it?
Guardz is a fully automated service and so it is very easy to implement – the security service needs almost no manual intervention. This system is a great cost saver because it frees up technicians for other tasks. The package includes account takeover detection and Dark Web scanning – both will alert to compromised credentials.
The email scanner operates as a plug-in for Outlook and Gmail. These two systems are part of Microsoft 365 and Google Workspace. Guardz also protects the cloud drive services that are associated with those two suites: OneDrive and Google Drive. The package also protects endpoints by detecting manual intrusion and malware.
Guardz scans each email as it arrives and if malicious content is detected, that mail is moved to a quarantine area. The user never even knows about the attempted attack. The system administrator gets an alert in the management dashboard for Guardz and can go and inspect the quarantined emails and decide whether or not the algorithm correctly identified each as a threat. Incorrectly classified emails can be restored to the inboxes of their intended recipients.
The Guardz system is intended for use by managed services to operate on the email systems of their clients. The package also includes a phishing simulator for testing and all plans get access to an employee awareness training library at no extra cost.
Who is it recommended for?
This package is a nice pass-through service that managed service providers can add to their list of services. However, there is nothing to stop IT departments from buying their system for their own corporate email service. Pricing is per user. The Starter plan has no minimum user count, which makes it suitable for even the smallest businesses.
Pros:
- Pass-Through Service: MSPs can offer this to their clients
- Managed System: MSP technicians don’t need to get involved
- Protects Against BEC: Multi-level identity checks for email origin
- Extended Plans: Also protects cloud drives and endpoints
- Activity Logging: Can feed into SIEMs
Cons:
- Short Free Trial: The trial only lasts 14 days
Plans are priced per user and there is a managed security service option available. You can investigate Guardz with a 14-day free trial.
EDITOR'S CHOICE
Guardz is our top pick for phishing protection software because it also blocks spam and identifies business email compromise (BEC) attacks. The service scans attachments and quarantines malware. The remediation actions of the package kick in automatically, so the system requires very little manual intervention. There is no minimum team size for a Guardz account, so the system can cater to any type and size of business. The full Guardz package also protects endpoints and cloud drives. The plans include Dark Web scanning to detect compromised email addresses, a phishing simulator, and a library of security awareness training videos.
Download: Get a 14-day FREE Trial
Official Site: https://guardz.com/free_trial
OS: Cloud-based
2. ManageEngine Browser Security Plus (FREE TRIAL)
An advanced anti-phishing software from ManageEngine that reduces the risks of employees falling prey to phishing attacks. With Browser Security Plus, IT teams can deploy browser security configurations, protect enterprise data from phishing attacks, and ensure compliance with various standards. It also provides in-depth visibility into usage trends and detects the add-ons that can increase vulnerability to cybersecurity attacks. Its centralized interface and report generation capabilities ease the work of your IT teams.
Key Features:
- Centralized Deployment: Enables IT teams to deploy browser settings to all users across different locations through a central interface.
- Control Over Plugins and Extensions: Allows IT administrators to approve or revoke access to web apps and lockdown plugins and extensions with known vulnerabilities.
- Report Generation: Generates reports of computers that do not comply with existing security configurations.
- Security Configurations: Helps prevent phishing attacks and data leaks through strict configurations.
- Add-on Management: Provides comprehensive control to IT teams to manage and remove add-ons.
Why do we recommend it?
ManageEngine Browser Security Plus is an anti-phishing solution that protects an organization’s sensitive data from cyberattacks. It focuses on safeguarding employees from phishing attacks through browser configurations, which means you can avoid data leaks caused by human errors like clicking phishing links.
Moreover, IT teams have complete control and visibility across all browsers, and they can track usage patterns, add-ons, and more. Based on this visibility, IT admins can provide or deny permission to install specific browser plugins and extensions. Additionally, this control helps meet the compliance requirements of different standards as well.
Another aspect we like about this tool is its centralized interface. With just a few clicks, IT teams can enforce security policies across all users in the organization. Besides saving time and effort for employees, it can handle enterprise and non-enterprise sites across most popular browsers. Its reports are also detailed and provide information on the status of browser health in the organization.
Due to these reasons, Browser Security Plus is a must-have tool to control phishing attacks and data leaks through browsers.
Who is it recommended for?
It is recommended for mid-sized to large organizations that have multiple endpoints across geographies. This tool also works well for IT teams that want better control over browser usage and plugins, and to reduce the number of phishing incidents happening through browser links. It can also be handy for organizations that must meet strict compliance requirements.
Pros:
- Reduces Phishing Risks: Proactively blocks access to phishing sites and malicious content.
- Real-time Monitoring: Provides visibility into browser usage in real time.
- Support for Browsers: Supports all major browsers, including Chrome, Edge, Firefox, Ulaa, Brave, Yandex, Vivaldi, Coc Coc, Naver Whale, and Internet Explorer.
- Improves Compliance: Enables organizations to meet the compliance requirements of security standards.
- Extension Management: Allows IT teams to control the usage of browser plugins and extensions.
Cons:
- Agent Installation: An agent must be installed on every endpoint, and this can increase deployment time.
Start a 30-day free trial.
3. Trustifi
Trustifi robustly detects viruses that spread malware and ransomware, while protecting your email traffic from BEC attacks, and altering authorized technicians through an excellent notification system. The system includes options for whitelisting and blacklisting for better overall protection. General options such as integrated spam filtering, spoofing, phishing, and fraud detection, vastly improve your network security. The Inbound Shield employs specialized AI and several dynamic and comprehensive engines to safeguard your inbox against harmful links and attachments.
Key Features:
- Malware and Ransomware Detection: Automated protection with managed service option
- Email Encryption: Uses 256-bit AES
- White/Blacklisting Tools: Add to the list manually
- AI-Driven Safeguarding: Reduces inconvenient over-protection
Why do we recommend it?
Trustifi is a platform that offers a number of modules, for example, Inbound Shield focuses on phishing, spam, BEC, and malware, while Outbound Shield is a DLP system with insider threat and account takeover detection. It is most likely that any buyer will sign up for both packages.
Trustifi also includes several data-loss prevention tools such as real-time information on email delivery, opening, and reading times with tracking and certified delivery. You can enforce system-wide two-factor authentication for all of your users, or group-specific user groups to dedicate security options for better system verification. The system ensures apt cooperation with compliance standards such as HIPAA/ HITECH, PII, GDPR, FSA, FINRA, LGPD, and CCPA.
Included email encryption in addition to comprehensive DLP with an advanced rules engine to accommodate any use case means you can be certain in the protection of your internal and external email traffic. The system also includes secure mobile relays for whole-device protection, while granting you the ability to recall, block, alter, and establish customized expiration dates for emails.
There’s no trial available for the product, but you can request a demo of the platform for a better insight into the precise inner workings of the system. Trustifi is designed to easily integrate with Office 365 or Google Workspace but includes a full integration API to facilitate a variety of email systems.
Who is it recommended for?
This platform is one of the leading brands in email protection – both for phishing and inbound threats and outbound risks, such as data theft. The company doesn’t publish a price list or plan conditions, such as minimum user counts, so it is difficult to recommend this service to small businesses.
Pros:
- Compliance Assurance: Implements 10 frameworks
- Outbound Shield: Choose to add on this option for data loss prevention
- Two-Factor Authentication: Strengthens access controls for email systems
- Recall and Erase Sent Emails: Catch data exfiltration emails while they are in transit
Cons:
- No Price List: Get a quote
For pricing, you can contact Trustifi directly to get a personalized price quote based on your exact business requirements.
4. TitanHQ Anti-Phishing Protection

Anti-Phishing Protection is a new product from TitanHQ. The company used to include phishing detection in its Email Security product but not that has been split off into a separate module. Email Security is still the go-to product for spam and malware detection. Anti-Phishing Protection also provides data loss prevention services by scanning outbound emails. This system is only available for managing emails in the Microsoft 365 platform through its Exchange Server and Outlook units.
Key Features:
- AI-Driven Analysis: Utilizes artificial intelligence and machine learning algorithms to detect and block phishing attempts in real-time, enhancing email security.
- Seamless Microsoft 365 Integration: Integrates directly with Microsoft 365, providing comprehensive protection without the need for MX record changes.
- Post-Delivery Remediation: Allows administrators to remove malicious emails from user inboxes even after delivery, mitigating potential threats.
- URL Rewriting and Time-of-Click Protection: Rewrites URLs in emails and analyzes them at the time of click to prevent access to malicious websites.
- Detailed Reporting: Offers comprehensive reports on phishing threats and remediation actions, aiding in security assessments and compliance.
Why do we recommend it?
Anti-Phishing Protection provides robust, AI-driven phishing protection that seamlessly integrates with Microsoft 365, enhancing existing security measures without complex configurations. Its real-time threat detection and post-delivery remediation capabilities ensure comprehensive defense against evolving phishing attacks.
The methods implemented by the Anti-Phishing Protection system include scanning email contents for fake links and a scan for impersonation – faked colleagues. The service identifies specific text that is frequently encountered in credentials theft attempts. The system also checks on issues such as adjacent and spoofed domains. Emails can be let through with links disabled or with a warning banner. It is also possible to instruct the system to divert flagged emails to a quarantine area on the TitanHQ cloud server.
The TitanHQ system uses AI methods for both its Email Security and Anti-Phishing Protection systems. The platform deploys machine learning, which adjusts its detection rules over time. This enables the TitanHQ products to tailor their service to a specific company without needing to write custom code.
The Anti-Phishing Protection unit examines outbound emails as well as inbound mails. This provides options for data loss prevention – a service that you need to set up with your requirements in the configuration of the Anti-Phishing Protection system. You would need to link the PhishTitan service to a sensitive data discovery and classification tool to fully exploit this feature.
Who is it recommended for?
Anti-Phishing Protection is ideal for organizations using Microsoft 365 seeking to bolster their email security with advanced phishing protection. It’s particularly beneficial for businesses looking for a solution that is quick to deploy, easy to manage, and capable of adapting to sophisticated phishing threats.
Pros:
- Advanced Threat Detection: Employs multiple layers of analysis, including textual, link, and attachment scanning, to identify sophisticated phishing attacks.
- Quick Deployment: Can be set up in less than 10 minutes, allowing organizations to enhance their email security swiftly.
- User-Friendly Interface: Features an intuitive interface that simplifies management and monitoring of phishing threats.
- Enhances Existing Security Measures: Augments Microsoft 365’s built-in security features, providing an additional layer of protection against phishing attacks.
- Scalable Solution: Suitable for businesses of all sizes, offering flexible protection that grows with organizational needs.
Cons:
- Learning Curve: Some users may experience a learning curve during initial implementation, requiring time to fully leverage all features.
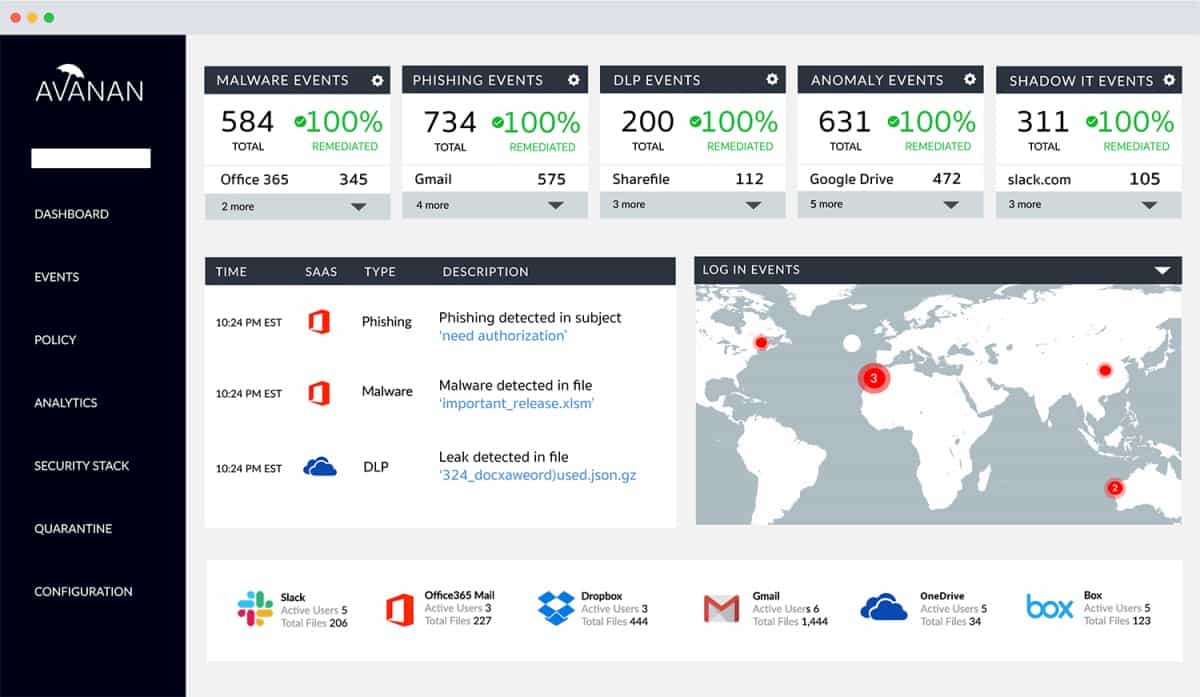
5. Avanan
With in-depth defense capabilities, the Avanan Cloud Security Platform provides one of the most comprehensive cloud-based email security solutions on the market, ensuring the safety and compliance of your network’s entire email infrastructure.
Key Features:
- Security Workflows: Covers cloud drives and collaboration apps as well as email
- Detect and Prevent System: Automated cycle
- Quarantine Mailbox: Enables manual inspection
Why do we recommend it?
Avanan offers a robust, AI-driven email security solution that integrates seamlessly with major cloud email providers, providing comprehensive protection against a wide array of cyber threats. Its user-friendly interface and advanced threat detection capabilities make it a valuable addition to any organization’s security infrastructure.
Through the detect and protect mode, deploy a cutting-edge security stack, which provides an automated policy action to quarantine malware, phishing assaults, etc. To keep any emails or attachments that are quarantined during the scanning process by policy or via human actions, you can set up a dedicated quarantine mailbox.
Three distinct workflows are offered through the system to manage malware and anti-phishing attacks entirely within the platform. After an email is delivered to the user, the ‘Detect and Prevent’ system scans it and mitigates any issues before delivery is completed. This system ensures that your end users are never exposed to potential malicious threats.
Avanan has a 14-day free trial of their services which you can use to test out the features, such as the customizable security workflows and fast deployment. The full solution is divided into three separate SaaS models with varying features and costs.
Who is it recommended for?
Avanan is ideal for organizations of all sizes seeking to enhance their email security without disrupting existing workflows. It’s particularly beneficial for businesses using cloud-based email services like Microsoft 365 and Google Workspace, offering advanced protection against phishing, malware, and data loss.
Pros:
- In-Depth Alerting: Explains the emergency
- Distinct User Policies: Allows different actions to each user group or individual
- Outbound Scanning: Data loss prevention
Cons:
- Not Available for All Email Systems: Only Outlook and Gmail
The Protect package comes with all the basic features and costs $4.30 per user/month, the Advanced Protect package comes with file sandboxing to protect from zero-day malware exploits and costs $5.50 per user/month. Finally, the Complete Protection package adds encryption and data-loss prevention, which might be necessary features for certain compliance requirements—it costs $7.20 per user/month.
6. Abnormal Security
Abnormal works by analyzing a vast array of data and builds profiles of recognized acceptable behavior in your environment to look for deviations from the norm. The system is designed to quickly and without interrupting mail flow integrate with Microsoft 365 and Google Workspace. After integration, Abnormal creates automatic profiles of your employees to create baselines and secure your business, and get you running quickly. All the vendors in your ecosystem are automatically identified by the platform so that you may determine each one’s level of risk.
Key Features:
- Behavioral Analysis: Insider threat detection
- Broad Integrations: Scans across the IT system
- API Deployment: Integrates into custom apps
Why do we recommend it?
Abnormal Security offers a robust, AI-driven email security solution that effectively detects and mitigates sophisticated threats. Its seamless integration with major cloud email platforms and automated remediation capabilities make it a valuable asset for organizations seeking to enhance their email security posture.
Abnormal can identify situations where a vendor may pose a significant risk of fraud, indicating when an email should be thoroughly checked for signs of malicious behavior. For both Microsoft and Google environments, Abnormal centralizes data, insights, actions, and the maintenance of global block lists in one location, across hundreds of tenants. Abnormal’s behavioral analysis systems can also work for its users, and as users transfer emails between folders in their mailbox, the software learns their preferences.
Abnormal is a SaaS platform built for scalability and flexible distribution, you can also integrate the solution directly through Microsoft’s Azure marketplace.
Who is it recommended for?
Abnormal Security is ideal for organizations of all sizes that utilize cloud-based email services like Microsoft 365 or Google Workspace. It’s particularly beneficial for those looking to leverage advanced AI technology to protect against evolving email threats while minimizing manual security management efforts.
Pros:
- Email Automation: AI-based inbound email scanning
- Account Takeover Protection: Spots phishing attempts and analyzes account activity
- In-Depth Reporting: Detailed threat analysis
Cons:
- Limited Email Integration: Only Outlook and Gmail
While there is no available free trial or publicly listed pricing, you can contact Abnormal directly to arrange a demo and receive a personalized quote on your business price.
7. Barracuda Sentinel
Barracuda Sentinel comes from a company that employs an innovative API-based architecture that enables its AI engine to analyze previous emails and discover users’ distinctive communication styles. Additionally, the system is designed to thwart phishing attempts that gather login information for account takeover. It discovers and deletes all fraudulent emails sent from compromised accounts after detecting aberrant email behavior and notifying IT. To uncover and stop socially engineered assaults in real-time, it can then detect irregularities in communication metadata and content.
Key Features:
- AI-Driven Behavior Analysis: Specializes in spear phishing defense
- Account Takeover Protection: Identifies changes in behavior
- Domain Fraud Protection: Scans the web for impersonator domains
Why do we recommend it?
Barracuda Sentinel is one of the email security products offered by Barracuda. The company also offers Barracuda Email Security, which doesn’t carry the Sentinel product name. This is a hosted service and it connects to your email system through a plug-in. One problem with this tool is that it is only available for Microsoft 365.
DMARC authentication is set up with the aid of Barracuda Sentinel, which provides you with the ability to see and analyze reports at a granular level to help you reduce false positives, safeguard valid emails, and stop spoofing. In the multi-layered email protection system Barracuda Total Email Protection, Sentinel offers AI-based defense against spear phishing, account takeover, and compromised corporate emails.
Who is it recommended for?
This package is a good choice for large organizations that have brand reputations to consider as well as phishing protection. The service scans for incidences of others posing as a members of a protected corporation. The package is suitable for sale by MSPs – threat data is handled directly by the Barracuda platform.
Pros:
- DMARC Authentication: Registers the origin of valid emails
- Fraud Simulation Training: User security awareness
- Threat Intelligence: Provided by the Barracuda analysis team
Cons:
- Competing Products: Barracuda confuses the market by producing its own rival package to the Sentinal product line
Barracuda Sentinel can be purchased on a license basis from any number of partnered stores. Each license costs around $3.99 per user per month, but costs will change based on where you purchase the licenses from. The solution is designed to work alongside any email solution but is specially built for Office 365 environments, and will be easily integrated into your Microsoft email suite through pre-established plugins. Other email solutions are accessible through the flexible API.
8. BrandShield
BrandShield comes equipped with several specialized security tools that are focused on protecting the identity of your business and its employees—one such tool is their robust phishing protection solution. By monitoring the Internet, including social media, to find phishing sites and pages, impersonation, and online fraud, BrandShield offers a comprehensive digital threat map. You can also access the takedown services from the system’s inbuilt threat dashboard, which can swiftly identify and eliminate threats to your business.
Key Features:
- Advanced Anti-Phishing: Protection for employees and customers
- Identity Theft Protection: Spots malicious URLs
- Social Media Protection: Scans for impersonation on the major social media platforms
Why do we recommend it?
BrandShield is much more active in preventing your company’s identity from being used to trick outsiders rather than looking for attempts to trick your own employees. Phishing protection for your team is in there – especially insider impersonation, which is used in BEC attacks. The system also looks at impersonations carried out on social media accounts.
The system provides you with the means to maintain control by providing regular updates on your enforcement actions and takedowns. Additionally, innovative tools like the website duplication detector, automated takedown notices, blacklists, and more are part of the anti-phishing solution. The platform also includes modernized systems, such as the ability to monitor popular social media sites for executive impersonation efforts and phishing scams that could expose members of your organization.
You can request a demo of the product from BrandShield directly, which also includes an online threat map of your current outward-facing business identity—this makes requesting the demo worthwhile even with no intentions of getting the product.
Who is it recommended for?
Although any business’s brand can be used to fool the public and damage a reputation, these types of campaigns are usually aimed at large corporations. This means that the BrandShield service will appeal to large businesses with valuable brands. Obscure, small companies won’t need to go to the expense of guarding against brand abuse.
Pros:
- Anti-Counterfeiting: Procedures to counter brand hijacking
- Brand Protection: Identifies impersonator domains
- Takedown Service: Swiftly impersonators
Cons:
- No Free Trial: Get a demo
For pricing on the full product, you’ll need to contact the company directly for a personalized quote on pricing.
9. Proofpoint Essentials
Proofpoint provides a multi-layered anti-virus, anti-spam, and phishing detection engine that provides a comprehensive defense against threats delivered via email. The system’s powerful AI-driven detection engines scan every one of your emails, and all known viruses are precisely and successfully captured and quarantined. Proofpoint provides reliable heuristics screening for even better defense, which identifies unknown email threats and aids in your immediate protection from them.
Key Features:
- Fully Integrated AI-Driven Solution: More accurate impersonation reporting
- URL and Attachment Scanning: Looks for malware and fake forms
- Targeted Attack Protection: BEC protection
Why do we recommend it?
The main reason that Proofpoint Essentials is recommended here is the reliability of the Proofpoint brand. Proofpoint seems to be reducing the importance of the Essentials bundle in favor of offering a mix-and-match selection of services to customers. This new approach provides more flexibility but it removes the advantage of being able to advertise a package at a fixed price.
The system provides you with a cutting-edge system interface that helps with the comprehension of your overall threat scenario. Using the system, you can also quickly access a thorough breakdown of particular threat categories and attack frequency, which equips you with all the knowledge and resources necessary to make wise security decisions. To assist safeguard your staff, the system employs targeted attack protection, with a premier email analysis solution. With the aid of this innovative technology, you may analyze URLs and attachments through sandboxing.
Proofpoint provides a 30-day trial upon request that begins with a meeting with one of their cybersecurity experts, followed by them deploying the system to your infrastructure within 24 hours.
Who is it recommended for?
By reducing the visibility of its packages, Proofpoint will lose the small business market. SMEs like to see the contents of a product and know the exact price before even getting in touch with the provider. The new consultation-based packaging and pricing will only appeal to large corporate buyers.
Pros:
- Malware Quarantine: Protects against ransomware and other automated attacks
- Simulated Phishing: User security awareness training
- Leading Brand: Combine email protection with compliance management and other security tools
Cons:
- Brand is Evolving: Proofpoint is reducing the visibility of product packages in favor of customized service selections
The Essentials package is divided into four separate tiers for the email security package, with the most basic Beginner package costing $1.65 per user per month. More advanced tiers increase the cost but exponentially add more features to their included package.