What is PCAP?
PCAP, which stands for Packet Capture, is a file format widely used in the field of networking to store data captured from network traffic. It is an essential tool for network analysis, troubleshooting, and security investigations, providing detailed insights into the behavior of a network.
A PCAP file contains the raw data of network packets, including both the headers and payloads, allowing for a thorough examination of all communication occurring over a network.
These files are typically processed using packet capture tools such as Wireshark, tcpdump, or other network monitoring software. Once captured, the data can be analyzed to diagnose connectivity issues, monitor performance, or investigate suspicious activity. PCAP files offer a granular view of network traffic, making them invaluable for identifying patterns, detecting anomalies, and understanding protocols in use.
For network administrators, PCAP files help in troubleshooting complex issues, such as packet loss, latency, or misconfigurations. Security professionals use them to investigate potential threats, including malware infections, unauthorized access, or data exfiltration. By examining the sequence of packets, they can reconstruct sessions, track unauthorized communications, and pinpoint the origin of an attack.
PCAP serves as a critical resource for anyone managing or securing a network, providing the necessary visibility to ensure efficient operation and robust defense against cyber threats.
Related post: Wireshark Vs TCPDump guide
PCAP files are widely used in network analysis and security tasks. They enable network administrators, analysts, and researchers to inspect and analyze network traffic for various purposes, including:
- Network troubleshooting: PCAP files can help diagnose network issues by examining packet-level details such as source and destination addresses, protocols, and error messages.
- Network security: PCAP files are valuable for detecting and investigating network security incidents. They allow security professionals to analyze packet payloads, identify malicious activity, and track network intrusions.
- Protocol analysis: PCAP files provide a wealth of information about network protocols. By analyzing the captured packets, researchers can gain insights into the behavior of network protocols, identify vulnerabilities, and develop mitigation strategies.
- Performance monitoring: PCAP files can be used to measure network performance, identify bottlenecks, and optimize network configurations. They provide a detailed view of network traffic, allowing administrators to analyze latency, throughput, and other performance metrics.
How Does a Packet Sniffer Work?
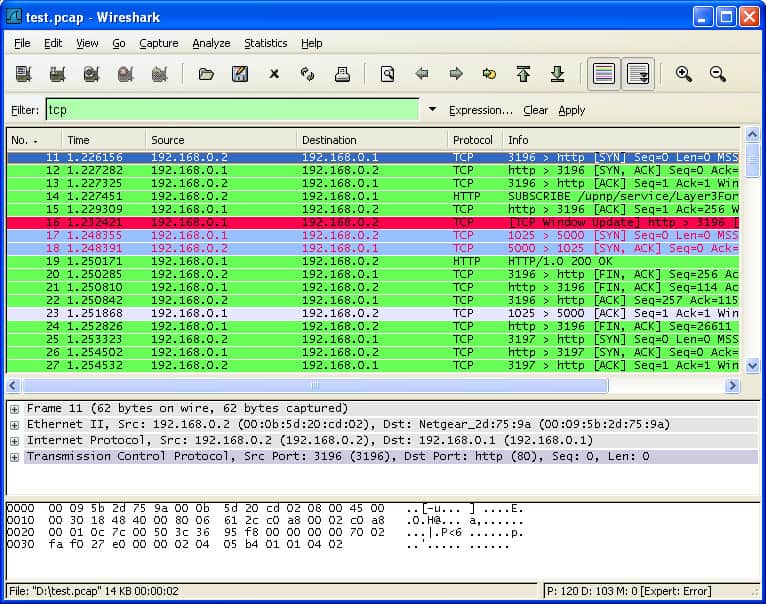
To capture PCAP files you need to use a packet sniffer. A packet sniffer captures packets and presents them in a way that’s easy to understand. When using a PCAP sniffer the first thing you need to do is identify what interface you want to sniff on. If you’re on a Linux device these could be eth0 or wlan0. You can select an interface with the ifconfig command.
Once you know what interface you wish to sniff then you can choose what type of traffic you want to monitor. For example, if you only want to monitor TCP/IP packets then you can create rules to do this. Many tools offer filters that allow you to control what traffic you collect.
Using Wireshark for PCAP file capture and analysis
For example, Wireshark allows you to filter the type of traffic you see with capture filters and display filters. Capture filters allow you to filter what traffic you capture and display filters allow you to filter what traffic you see. For example, you can filter network protocols, flows, or hosts.
Once you’ve collected the filtered traffic you can start to look for performance issues. For more targeted analysis you can also filter based on source ports and destination ports to test particular network elements. All of the captured packet information can then be used to troubleshoot network performance issues.
Versions of PCAP
As mentioned above, there are many different types of PCAP files, including:
- Libpcap
- WinPcap
- PCAPng
- Npcap
Each version has its own use cases and different types of network monitoring tools support different forms of PCAP files. For instance, Libpcap is a portable open-source c/C++ library designed for Linux and Mac OS users. Libpcap enables administrators to capture and filter packets. Packet sniffing tools like tcpdump use the Libpcap format.
For Windows users, there is the WinPcap format. WinPcap is another portable packet capture library designed for Windows devices. WinpCap can also capture and filter packets collected from the network. Tools like Wireshark, Nmap, and Snort use WinPCap to monitor devices but the protocol itself has been discontinued.
Pcapng or .pcap Next Generation Capture File Format is a more advanced version of PCAP that comes default with Wireshark. Pcapng can capture and store data. The type of data pcapng collects includes extended timestamp precision, user comments, and capture statistics to provide the user with additional information.
Tools like Wireshark are using PCAPng files because it can record more information than PCAP. However, the problem with PCAPng is that it isn’t compatible with as many tools as PCAP.
Npcap is a portable packet sniffing library for Windows produced by Nmap, one of the most well-known packet sniffing vendors. The library is faster and more secure than WinpCap. Npcap has support for Windows 10 and loopback packet capture injection so you can send and sniff loopback packets. Npcap is also supported by Wireshark.
Advantages of Packet Capturing and PCAP
The biggest advantage of packet capturing is that it grants visibility. You can use packet data to pinpoint the root cause of network problems. You can monitor traffic sources and identify the usage data of applications and devices. PCAP data gives you the real-time information you need to find and resolve performance issues to keep the network functioning after a security event.
For example, you can identify where a piece of malware breached the network by tracking the flow of malicious traffic and other malicious communications. Without PCAP and a packet capture tool, it would be more difficult to track packets and manage security risks.
As a simple file format, PCAP has the advantage of being compatible with almost any packet sniffing program you can think of, with a range of versions for Windows, Linux, and Mac OS. Packet capture can be deployed in almost any environment.
Disadvantages of Packet Capturing and PCAP
Although packet capturing is a valuable monitoring technique it does have its limitations. Packet analysis allows you to monitor network traffic but doesn’t monitor everything. Many cyberattacks aren’t launched through network traffic, so you need to have other security measures in place.
For example, some attackers use USBs and other hardware-based attacks. Consequently, PCAP file analysis should make up part of your network security strategy but it shouldn’t be your only line of defense.
Another significant obstacle to packet capturing is encryption. Many cyber attackers use encrypted communications to launch attacks on networks. Encryption stops your packet sniffer from being able to access traffic data and identify attacks. That means encrypted attacks will slip under the radar if you’re relying on PCAP.
There is also an issue with where the packet sniffer is located. If a packet sniffer is placed at the edge of the network then this will limit the amount of visibility a user has. For example, the user may fail to spot the start of a DDoS attack or malware outbreak. Furthermore, even if you are collecting data in the center of the network it is important to make sure that you are collecting entire conversations rather than summary data.
Open Source Packet Analysis Tool: How does Wireshark Use PCAP Files?
Wireshark is the most popular traffic analyzer in the world. Wireshark uses .pcap files to record packet data that has been pulled from a network scan. Packet data is recorded In files with the .pcap file extension and can be used to find performance problems and cyberattacks on the network.
In other words, the PCAP file creates a record of network data that you can view through Wireshark. You can then assess the status of the network and identify if there are any service issues that you need to respond to.
It is important to note that Wireshark isn’t the only tool that can open .pcap files. Other widely used alternatives include tcpdump and WinDump, network monitoring tools that also use PCAP to take a magnifying glass to network performance.
Proprietary Packet Analysis Tool Example
SolarWinds Network Performance Monitor (FREE TRIAL)
SolarWinds Network Performance Monitor is an example of a network monitoring tool that can capture PCAP data. You can install the software on a device and then monitor packet data pulled from the entire network. The packet data will enable you to measure the response time of the network and diagnose attacks.
Key Features:
- Uses WinPcap
- Summarizes packet data
- Identifies protocols
- Useful for VoIP testing
- Runs on Windows Server
Why do we recommend it?
PCAP viewing is just one of the utilities in the SolarWinds Network Performance Monitor – you also get device status monitoring. This tool provides extensive network monitoring and management utilities that include a high degree of automation.
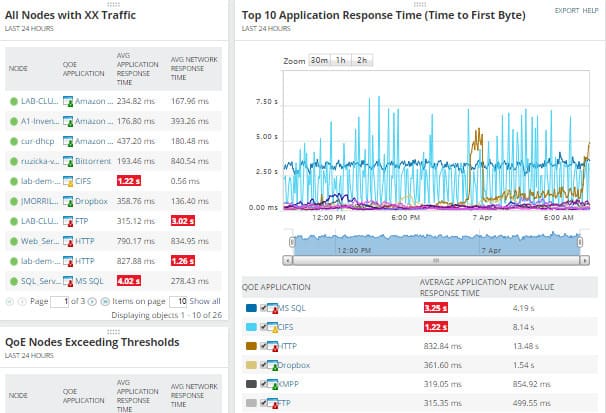
The user can view packet data through the Quality of Experience dashboard, including a summary of network performance. Graphical displays make it easier to pinpoint spikes in internet traffic or malicious traffic that could indicate a cyber attack.
You don’t need to capture and store entire packets in order to reap statistics from packet headers. Flow protocols, such as NetFlow, IPFIX, sFlow, and J-Flow can extract the operational statistics that are extracted from the headers of passing packets directly from switches and routers. You can access this data with the NetFlow Traffic Analyzer, which is a companion to the Network Performance Monitor. You can buy these two tools together with the Network Bandwidth Analyzer Pack.
Who is it recommended for?
If you just want to capture and view packets, you are probably better off with Wireshark. However, in order to fully manage your network, you are going to need to get a network monitor as well. The SolarWinds package is suitable for the managers of sizable networks who need both ongoing monitoring systems as well as analytical tools.
Pros:
- Shows packet data in lists and graphs
- Interprets packet headers for summaries
- Shows traffic statistics for well-known applications
- Shows average and longest response times
- Details Quality of Experience performance
Cons:
- Doesn’t display raw packets
The layout of the program also enables the user to differentiate applications by the amount of traffic they are processing. Factors such as Average Network Response Time, Average Application Response Time, Total Data Volume, and Total # of Transactions help the user to keep up to speed with changes to the network as they occur live. There is also a 30-day free trial available for download.
PCAP File Analysis: Catching Attacks in Network Traffic
Packet sniffing is a must for any organization that has a network. PCAP files are one of those resources that network administrators can use to take a microscope to performance and discover attacks. Capturing packets will not only help to get to the bottom of the root cause of attacks but also help to troubleshoot sluggish performance.
Open source packet capture tools like Wireshark and tcpdump give network administrators the tools to remediate poor network performance without spending a fortune. There is also a range of proprietary tools for companies that want a more advanced packet analysis experience.
Through the power of PCAP files, a user can log in to a packet sniffer collect traffic data and see where network resources are consumed. Using the right filters will also make it much easier to eliminate the white noise and hone in on the most significant data.
PCAP File Capture FAQs
How many files do I receive per day for a PCAP subscription?
PCAP isn’t a subscription service. Most PCAP tools launch packet captures on demand, however, it is possible to start and end a capture session through a script. The big issue with PCAP is not how many files you get, but the size of those files – letting a traffic capture session run for more than a brief period results in very, very large quantities of stored data.
What is the precision level for timestamping in PCAP?
The PCAP standard is able to express time down to nanoseconds – a thousand millionth of a second. All timestamps express an offset since January 1, 1970, 00:00:00 UTC.
How does Libpcap work?
Libcap is an API, which means that it can be controlled by other programs. It provides a series of services that enable the capture of network packets. Libpcap is written to operate on Unix and Unix-like systems, which includes Linux and macOS. It reads all packets on its host device’s network interface. The NIC needs to be put into “promiscuous mode” for this to be effective. That turns off the filter that reduces the NIC’s activity to just reading in packets addressed to it, so all packets circulation on the network will be processed.
What is a libpcap wrapper and how does it relate to PCAP?
Libpcap is written in C. It implements PCAP and provides a library of function calls that other programs can use in order to invoke the program code contained within each function in the library. Not all programming languages are compatible with the constructs used to call a Libpcap function. A wrapper is just a language-native function structure that exists solely to call a Libpcap function. Its purpose is to interpret data structures to make the C function calls available to the incompatible programming language. Wrappers are not provided by the libpcap library.
What should you look for in PCAP packet capture tools?
We reviewed the market for PCAP packet capture software and analyzed the options based on the following criteria:
- Support for Libpcap, WinPcap, PCAPng, Npcap
- Options for Windows, macOS, and Linux
- Packet storage file management
- Live data graphical interpretations
- Packet analysis utilities
- A free trial period for a cost-free assessment period or a free tool
- Free systems or value-for-money paid tools