Privileged Access Management (PAM) is the practice of limiting access to sensitive systems and data to only authorized users who have a specific need to access that information
Here is our list of the best PAM tools:
- Delinea Secret Server This package provides a password management system as well as privileged access management with a focus on sensitive data protection. Installs on Windows Server or offered as a cloud service.
- CyberArk PAM This access management system has compliance controls and reporting built into it and provides a Web-based authentication portal. Available as a virtual appliance or a SaaS platform.
- ARCON PAM This privileged access manager is part of a platform that specializes in authentication and access controls that make both the manual or automated revocation of access rights easy.
- KeeperPAM This PAM solution authenticates every user and device in your enterprise. It also comes with advanced features, like monitoring, threat tracking, and report generation.
- WALLIX Bastion This PAM provides a service that is best suited to businesses that are geographically spread either through multiple sites or by service remote and roaming users.
- BeyondTrust This is a platform of privileged access management tools that include password security and the distribution of credentials for technician access.
- One Identity This is a platform of access rights management services that includes privileged access management and a single sign-on environment.
This is typically done by granting privileged access only to those users who have been vetted and approved, and by implementing controls such as password management, multi-factor authentication, and monitoring and auditing of privileged access activities. The goal of PAM is to reduce the risk of unauthorized access to sensitive systems and data and to minimize the potential for data breaches and other security incidents.
Privilege management falls within the broader scope of Identity and Access Management (IAM). Together, PAM and IAM help to provide granular control and visibility over all credentials and privileges. While IAM controls provide authentication of identities to ensure that the right user has the right access at the right time, PAM layers on more granular visibility, control, and auditing over privileged identities and activities. While privilege management encompasses many strategies, a central goal is the enforcement of the principle of least privilege, in which a user or process is given the minimum levels of access or permissions needed to perform the intended job functions.
Privileged access management (PAM) is important because it helps organizations protect sensitive systems and data from unauthorized access and potential breaches. PAM controls who has access to sensitive systems and data, and ensures that only authorized individuals can access the information. This helps to reduce the risk of data breaches, unauthorized access, and other security incidents. Many regulatory requirements, such as HIPAA, PCI-DSS, and SOX, mandate that organizations implement controls to protect sensitive information and systems. PAM can help organizations meet these requirements by limiting access to sensitive data and systems only to those who have a legitimate need to access them.
Choosing the right PAM solution for your business
With a variety of PAM solutions, choosing the right one for your business and budget can be challenging. You need to consider a variety of factors, some of which include:
- Access controls Does the solution provide granular access controls, such as role-based access, and does it allow for the segregation of duties?
- Authentication What types of authentication does the solution support, such as multi-factor authentication, and does it have built-in biometric options?
- Auditing and reporting Does the solution provide detailed auditing and reporting capabilities, and can it integrate with existing security information and event management (SIEM) systems?
- Scalability Can the solution scale to meet the needs of your organization as it grows?
- Integration Does the solution integrate with other security and IT infrastructure, such as active directory, and can it be deployed in the cloud or on-premises environments?
- Support Does the vendor offer good customer support, and are they able to provide guidance and best practices for the implementation and operation of the solution?
In this article, we’re going to review the best PAM tools in the market. Hopefully, this will guide you in the process of choosing the right one for your business.
The Best Pam Tools
1. Delinea Secret Server
Secret Server is a password management and privileged access management (PAM) software developed by Delinea. It is designed to help organizations securely store, manage, and share sensitive information, such as passwords, credentials, and other confidential data.
Key Features:
- Secure Password Storage: Utilizes encryption to ensure that passwords and credentials are accessible only to authorized users.
- Role-Based Access Control: Enables administrators to assign varying access levels to users based on their roles.
- Auditing and Reporting: Generates detailed audit reports to track access and changes, aiding in regulatory compliance.
- Integration with Security Tools: Connects with Active Directory, SIEMs, and firewalls for a comprehensive security solution.
- Single Sign-On: Allows users to access multiple systems with one set of credentials, simplifying password management.
- API Access: Provides programmatic access to the system, facilitating integration with other tools and automation.
The software features an encrypted database, role-based access controls, and audit trails to track who accesses and makes changes to the stored information. Additionally, Secret Server offers integration with other security tools and systems, such as Active Directory and SIEMs, to provide a comprehensive security solution for managing privileged access.
Delinea was named a Leader in the 2022 Gartner Magic Quadrant for PAM.
Pros:
- Enhanced Security: Encryption and role-based controls provide robust protection for sensitive information.
- Regulatory Compliance: Detailed audit trails support compliance with security regulations.
- Comprehensive Integration: Integrates seamlessly with various security tools and systems.
- User-Friendly Single Sign-On: Simplifies access management by reducing the number of credentials users need to remember.
- Flexible Deployment: Offers both on-premises and cloud-hosted deployment options.
Cons:
- High Initial Cost: The on-premises version requires a significant upfront investment.
- Complex Configuration: Integration with other systems can be time-consuming and challenging.
- Learning Curve: Users may need training to effectively utilize all features.
Secret Server supports both on-premise and cloud-hosted deployment models. On-Premises license offers a perpetual license that allows users to install and run Secret Server on their own servers. Cloud Hosted license allows users to access Secret Server through the cloud, with the software hosted and maintained by Delinea. A free 30-day trial is available on request.
2. CyberArk PAM
CyberArk Privileged Access Manager (PAM) is a software solution that helps organizations secure and manage privileged access to sensitive systems and data. It provides a comprehensive and centralized approach to managing and controlling privileged access, including the ability to secure, monitor, and rotate privileged credentials.
Key Features:
- Privileged Session Management: Controls and monitors privileged sessions with recording and playback capabilities.
- Credential Management: Securely stores, manages, and rotates passwords, SSH keys, and tokens.
- Access Management: Enforces role-based access controls to manage privileges effectively.
- Auditing and Compliance: Provides detailed audit trails and reports for regulatory compliance.
- Integration: Works with existing security tools like Active Directory and SIEMs for a comprehensive solution.
- Automation: Automates privileged access management to minimize human error and boost productivity.
- Scalability: Adapts to the growing needs of organizations, making it suitable for businesses of all sizes.
CyberArk was also named a Leader in the 2022 Gartner Magic Quadrant for PAM.
Pros:
- Comprehensive Session Management: Offers robust tools for controlling and analyzing privileged sessions.
- Strong Credential Security: Securely stores and rotates credentials to prevent unauthorized access.
- Effective Access Control: Implements role-based controls to manage access to sensitive accounts.
- Regulatory Support: Detailed audit reports help meet compliance requirements.
- Seamless Integration: Works well with various security infrastructures for enhanced protection.
- Automation Efficiency: Reduces human error and increases productivity through automation.
Cons:
- Complex Deployment: Initial setup and configuration can be challenging
- Cost Considerations: Licensing options can be expensive, especially for smaller organizations.
CyberArk PAM supports on-premise, SaaS, and hybrid deployment models. The software is available under several licensing options including perpetual, subscription, capacity, and consumption-based licensing. A free demo is available on request.
3. ARCON PAM
ARCON is a globally recognized Identity-As-A-Service provider with a wealth of experience in risk management and continuous risk assessment tools. ARCON PAM is a software solution that helps organizations secure and manage privileged access to sensitive systems and data.
Key Features:
- Centralized Management: Provides a secure platform for managing and controlling privileged access to sensitive systems.
- Continuous Monitoring: Continuously monitors privileged access and alerts administrators to suspicious activities or policy violations.
- Credential Rotation: Securely rotates privileged credentials to prevent unauthorized access.
- Audit Trails: Generates detailed audit logs to help organizations comply with regulatory requirements.
- Role-Based Access Control: Enforces role-based access controls to manage user privileges effectively.
- Deployment Flexibility: Supports on-premise, SaaS, and hybrid deployment models.
ARCON provides a comprehensive and centralized approach to managing and controlling privileged access, including the ability to secure, monitor, and rotate privileged credentials. ARCON was named a Leader in the 2022 Gartner Magic Quadrant for PAM.
ARCON PAM works by providing a centralized and secure platform for managing and controlling privileged access to sensitive systems and data. It continuously monitors and manages privileged access, alerting administrators to any suspicious activity or policy violations. This allows organizations to secure their privileged access and prevent unauthorized access to sensitive systems and data.
ARCON PAM supports on-premise, SaaS, and hybrid deployment models. The licensing for ARCON PAM is typically based on the number of users or devices that need access to the protected systems and data. Some vendors also offer different levels of functionality based on the license type, such as basic or advanced features.
Pros:
- Enhanced Security: Centralized management and continuous monitoring improve overall security.
- Proactive Threat Detection: Alerts administrators to suspicious activities, allowing for quick response.
- Regulatory Compliance: Detailed audit trails assist in meeting compliance requirements.
- Flexible Deployment: Offers multiple deployment options to suit various organizational needs.
- Comprehensive Access Control: Implements role-based controls to manage user privileges efficiently.
Cons:
- Initial Setup Complexity: The initial setup can be complex and time-consuming.
- Resource Intensive: Requires substantial resources for optimal performance and monitoring.
- Costly for Small Organizations: Licensing can be expensive, especially for smaller enterprises.
4. KeeperPAM

KeeperPAM from Keeper Security is a cloud-native solution that manages access to your critical resources, like servers, web apps, databases, and more. It is based on a zero-trust and zero-knowledge architecture, which means users must prove their authentication before they can access a resource. Also, KeeperPAM comes with other security features, like an encrypted vault, automated password rotation, and monitoring of privilege sessions in real time to provide comprehensive protection against the misuse of credentials.
Key Features:
- Secure vault: Protects all users in the organization and streamlines access to the required resources.
- Remote session: Provides just-in-time access for remote sessions without exposing the credentials. This access can also be time-limited.
- Encrypted tunnels: Makes it easy to create secure tunnels to connect to localhost.
- Centralized access: Centralizes access across different environments through a single UI console.
- Multi-Factor Authentication: Supports MFA on cloud and on-prem infrastructure.
- Extensive integration: Integrates well with all identity providers and network infrastructure, making it suitable for all organizations.
- Automated password rotation: Rotates passwords and locks down accounts across cloud and on-prem environments.
Overall, KeeperPAM centralizes access to critical resources through uniform policies, MFA, password rotation, and more. Also, with its just-in-time access, it can prevent standing privileges, which could lead to potential insider attacks and misuse of credentials.
Pros:
- Zero-trust principles: This architecture ensures that no one, not even Keeper, can access your credentials.
- Unified platform: It offers multiple features like privileged password management and secure remote access, eliminating the need for multiple tools.
- Granular: Supports granular and time-bound access to critical resources.
- Monitoring: Records privileged sessions for audits and to prevent misuse.
- Quick deployment: As it is cloud-native, deployment is quick.
Cons:
- No on-prem version: It does not have an on-prem only version, though it can support hybrid environments.
KeeperPAM offers four plans – Business Starter Password Manager, Business Password Manager, Enterprise Password Manager, and Privileged Access Manager. Start a 30-day free trial.
5. WALLIX Bastion
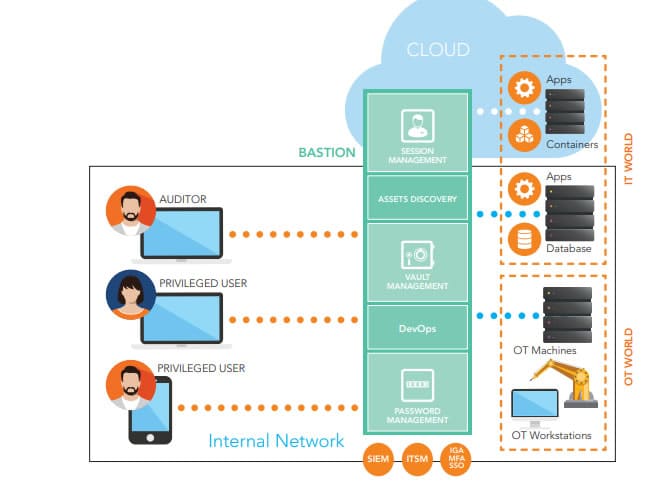
WALLIX is a leading provider of cybersecurity solutions. WALLIX Bastion is an award-winning PAM solution that delivers robust security and oversight overprivileged access to critical IT infrastructure. WALLIX was named a Leader in the 2022 Gartner Magic Quadrant for PAM.
Key Features:
- Password Management: Automates the rotation and expiration of privileged passwords to mitigate breach risks.
- Session Recording: Captures all privileged sessions, creating a complete audit trail of activities.
- Role-Based Access Control: Ensures only authorized users have access to sensitive systems with enforced role-based controls.
- User Activity Monitoring: Tracks and records user activities to detect and prevent malicious behavior.
- Compliance Reporting: Generates reports to demonstrate compliance with regulations like SOX, HIPAA, and PCI-DSS.
- Integration: Works with other security solutions such as SIEM for a comprehensive security strategy.
The Bastion solution helps organizations secure and manage privileged access to sensitive systems and data by providing secure remote access, password management, and session recording capabilities.
Pros:
- Automated Password Security: Reduces breach risks through automated password management.
- Detailed Session Logs: Provides comprehensive audit trails with session recording.
- Strict Access Controls: Ensures robust security with enforced role-based access controls.
- Proactive User Monitoring: Detects and prevents malicious activities through user activity monitoring.
- Regulatory Compliance Support: Facilitates compliance with industry regulations through detailed reporting.
- Flexible Deployment: Can be seamlessly deployed on-premise or in cloud environments.
Cons:
- Complex Integration: Initial integration with existing security systems may be challenging.
- High Resource Requirements: Needs significant system resources for optimal operation and monitoring.
- Costly Licensing: Licensing can be expensive, especially for smaller organizations.
Through your digital transformation, WALLIX Bastion can be seamlessly deployed from on-premise to private and public cloud infrastructures. WALLIX Bastion can be licensed on a perpetual or subscription basis, and pricing is typically based on the number of users or devices that need access to the protected systems and data. A free trial is available on request.
6. BeyondTrust
BeyondTrust is a cybersecurity company that provides a range of solutions for privileged access management (PAM), vulnerability management, and threat detection. BeyondTrust is recognized as a market leader in PAM solutions. It was named a Leader in the 2022 Gartner Magic Quadrant for PAM.
Key Features:
- Password Management: Secures and manages privileged credentials across the enterprise.
- Session Recording: Records and monitors privileged sessions to ensure compliance and security.
- Threat Detection: Identifies and responds to advanced threats and attacks on networks.
- Vulnerability Management: Identifies and prioritizes vulnerabilities, helping to remediate them before exploitation.
- Flexible Deployment: Supports on-premises, cloud, hybrid, and managed services deployment models.
BeyondTrust PAM solutions aim to secure and manage access to privileged credentials, such as those used by IT administrators, across the enterprise. It also provides privileged management for Windows, Mac, Linux, and Unix systems and servers. It can be used to secure access to servers, databases, applications, and cloud environments, with features such as password management, session recording, and threat detection.
They offer features such as password management, session recording, and threat detection, to help organizations secure privileged access and reduce the risk of data breaches. BeyondTrust also provides Vulnerability management solutions that help organizations to identify and prioritize vulnerabilities across their IT infrastructure, and then take action to remediate them before they can be exploited by attackers.
BeyondTrust also offers threat detection solutions that enable organizations to detect and respond to advanced threats and attacks on their networks. This can include things like endpoint detection and response (EDR), incident response, and security analytics. The goal of BeyondTrust is to help organizations improve their overall security posture and comply with regulatory requirements.
Pros:
- Comprehensive Security: Combines password management, session recording, and threat detection for robust security.
- Regulatory Compliance: Helps organizations meet compliance requirements with detailed monitoring and reporting.
- Vulnerability Management: Proactively identifies and addresses vulnerabilities across the IT infrastructure.
- Versatile Deployment Options: Offers multiple deployment models to suit different organizational needs.
- Wide Platform Support: Secures privileged access across Windows, Mac, Linux, and Unix systems.
Cons:
- Complexity: The wide range of features and options can make the system complex to configure and manage.
- Resource Intensive: Requires significant system resources for optimal performance.
- Cost: Licensing and additional modules can be expensive, particularly for smaller organizations.
BeyondTrust offers a flexible deployment model which includes an on-premises, cloud, hybrid, and managed services model. BeyondTrust offers several price plans for its privileged access management (PAM) solutions, and the pricing can vary depending on the specific solution, the deployment model, and the licensing option chosen.
The pricing for PAM solutions is generally based on the number of users, the number of sessions, and the number of assets (e.g. servers, applications) that need to be protected. Organizations can also choose to add additional features and modules to their PAM solution, which can affect the overall cost. A free trial of Privilege Management for Windows and Mac is available on request.
7. One Identity
One Identity delivers unified identity security solutions that help customers strengthen their overall cybersecurity posture. The company is recognized as a Leader in the 2022 Gartner Magic Quadrant for PAM.
Key Features:
- Privileged Session Management: Controls, monitors, and records sessions of administrators and high-risk users.
- Privileged Password Vault: Automates and secures the granting of privileged credentials with role-based access and workflows.
- Privileged Threat Analytics: Analyzes session recordings to identify high-risk privileged users.
- Least Privileged Access: Limits access to only what is necessary for administrators to perform their duties, reducing breach risks.
- UNIX Identity Consolidation: Extends Active Directory’s unified authentication and authorization to UNIX, Linux, and Mac systems.
- Privileged Access Governance: Integrates with Identity Manager to enhance governance capabilities.
One Identity PAM solution mitigates security risks by allowing you to secure, control, monitor, analyze, and govern privileged access across multiple environments and platforms. The solution is available as a SaaS or traditional on-premises offering.
One Identity PAM solution is made up of the following products:
- Privileged session management Control, monitor, and record privileged sessions of administrators, remote vendors, and other high-risk users.
- Privileged password vault Automate, control, and secure the process of granting privileged credentials with role-based access management and automated workflows.
- Privileged threat analytics Analyze privileged session recordings to identify your high-risk privileged users.
- Least privileged access Prevent security breaches by providing just the right amount of access to administrators so that they can perform their duties.
- UNIX identity consolidation Extend the unified authentication and authorization of Active Directory to UNIX, Linux, and Mac systems.
- Privileged access governance Integrate Identity Manager with Safeguard to extend its governance capabilities.
Pros:
- Comprehensive Session Control: Monitors and records privileged sessions to enhance security oversight.
- Automated Credential Management: Simplifies and secures the process of granting privileged access.
- Threat Analytics: Identifies high-risk users through session analysis, enhancing threat detection.
- Access Minimization: Reduces security breaches by limiting access to only necessary privileges.
- Cross-Platform Integration: Extends unified authentication to various systems, improving identity management.
Cons:
- Complex Setup: Initial configuration can be time-consuming and complex.
- Resource Intensive: Requires substantial resources for optimal monitoring and analytics performance.
- Cost Considerations: Can be expensive for smaller organizations due to the comprehensive feature set and licensing options.
One Identity PAM includes features such as multi-factor authentication, session management, and privilege escalation, which help to mitigate the risks associated with privileged access. The solutions also provide detailed reporting and auditing capabilities to help organizations comply with various regulatory requirements. A free trial is available on request.




