In the world of network security and administration, Nmap (Network Mapper) is a must-have tool. It’s an open-source utility designed for network discovery, security auditing, and troubleshooting. Whether you’re a system administrator, security professional, or simply someone curious about their network, Nmap provides powerful capabilities to analyze and manage network infrastructures.
At its core, Nmap helps users identify live hosts, open ports, services running on those ports, and the operating systems and software versions in use. Beyond basic scans, it can detect vulnerabilities, map complex networks, and even assist in compliance testing. Its versatility and scalability make it suitable for everything from small home networks to large enterprise environments.
This guide will introduce you to the essential Nmap command set, covering both basic and advanced usage. The Nmap command set includes powerful options for network scanning, such as host discovery, port scanning, and service detection. Advanced commands enable OS detection, vulnerability assessment, and customized scripting using the Nmap Scripting Engine (NSE), making it an essential security tool.
You’ll learn how to perform simple scans, customize your output, and leverage Nmap’s scripting engine (NSE) for deeper analysis. We’ll also explore practical use cases, such as identifying unauthorized devices, scanning for misconfigurations, and testing network defenses.
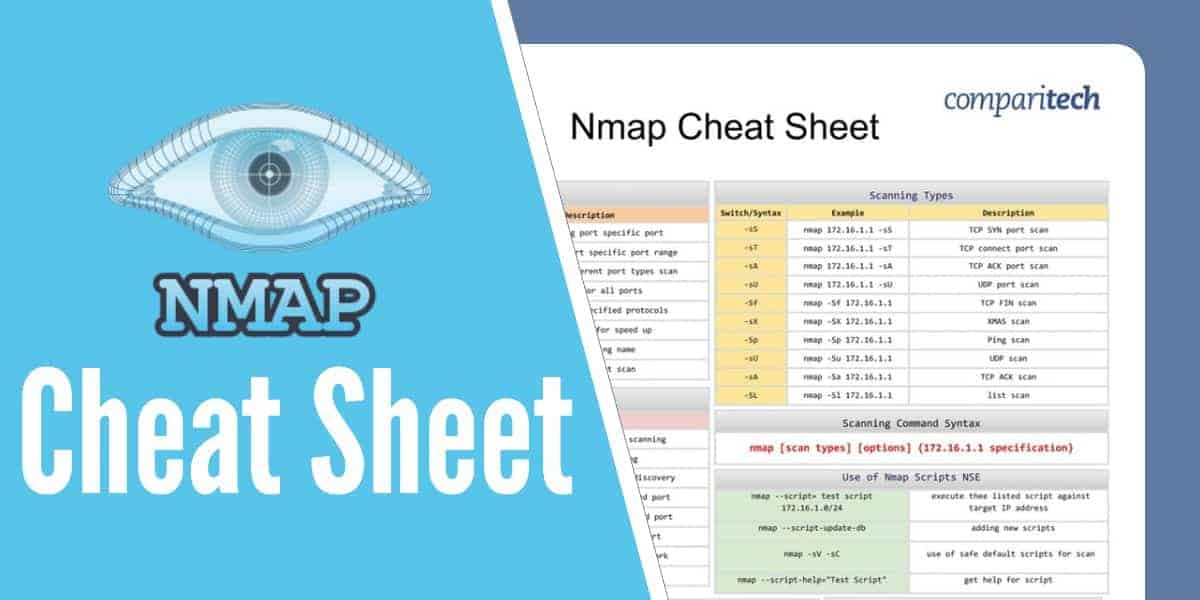
We’ve put together a comprehensive Nmap Cheat Sheet. If you also use Nessus with Nmap, keep reading. At the end of the post we have also included the Nmap + Nessus Cheat Sheet so you have all the useful commands at your fingertips.
All the tables provided in the cheat sheets are also presented in tables below which are easy to copy and paste.
The Nmap cheat sheet covers:
- Different usage options of Nmap
- Scanning command syntax
- Port Specification options
- Host /172.16.1.1 discovery
- Scanning types
- Version detection
- 172.16.1.1 specification
- Use of NMAP scripts NSE
- Firewall proofing
- NMAP output formats
- Scan options
- NMAP Timing options
- Miscellaneous commands
View or Download the cheat sheet PDF file
What’s included in the Cheat Sheet
The following categories and items have been included in the cheat sheet:
Different usage options of Nmap
| Different usage options |
|||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Port discovery and specification Host discovery and specification Vulnerability scanning Application and service version detection Software version detection against the ports Firewall / IDS Spoofing |
Scanning command syntax
Scanning Command Syntax |
|||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
nmap [scan types] [options] {172.16.1.1 specification} |
Port Specification options
Port Specification Options |
||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
Syntax | Example | Description |
||||||||
-P | nmap –p 23 172.16.1.1 | Port scanning port specific port |
||||||||
-P | nmap –p 23-100 172.16.1.1 | Port scanning port specific port range |
||||||||
-p | nmap -pU:110,T:23-25,443 172.16.1.1 | U-UDP,T-TCP different port types scan |
||||||||
-p- | nmap -p- 172.16.1.1 | Port scan for all ports |
||||||||
-p | nmap -smtp,https 172.16.1.1 | Port scan from specified protocols |
||||||||
-F | nmap –F 172.16.1.1 | Fast port scan for speed up |
||||||||
-P "*" | namp -p "*" ftp 172.16.1.1 | Port scan using name |
||||||||
-r | nmap -r 172.16.1.1 | Sequential port scan |
||||||||
Host /172.16.1.1 discovery
Host /172.16.1.1 Discovery |
||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
Switch/Syntax | Example | Description |
||||||||
-sL | nmap 172.16.1.1-5 -sL | List 172.16.1.1 without scanning |
||||||||
-sn | nmap 172.16.1.1/8 -sn | Disable port scanning |
||||||||
-Pn | nmap 172.16.1.1-8 -Pn | Port scans only and no host discovery |
||||||||
-PS | nmap 172.16.1.185 -PS22-25,80 | TCP SYN discovery on specified port |
||||||||
-PA | nmap 172.16.1.185 -PA22-25,80 | TCP ACK discovery on specified port |
||||||||
-PU | nmap 172.16.1.1-8 -PU53 | UDP discovery on specified port |
||||||||
-PR | nmap 172.16.1.1-1/8 -PR | ARP discovery within local network |
||||||||
-n | nmap 172.16.1.1 -n | no DNS resolution |
||||||||
Scanning types
Scanning Types |
||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
Switch/Syntax | Example | Description |
||||||||
-sS | nmap 172.16.1.1 -sS | TCP SYN port scan |
||||||||
-sT | nmap 172.16.1.1 -sT | TCP connect port scan |
||||||||
-sA | nmap 172.16.1.1 -sA | TCP ACK port scan |
||||||||
-sU | nmap 172.16.1.1 -sU | UDP port scan |
||||||||
-Sf | nmap -Sf 172.16.1.1 | TCP FIN scan |
||||||||
-sX | nmap -SX 172.16.1.1 | XMAS scan |
||||||||
-Sp | nmap -Sp 172.16.1.1 | Ping scan |
||||||||
-sU | nmap -Su 172.16.1.1 | UDP scan |
||||||||
-sA | nmap -Sa 172.16.1.1 | TCP ACK scan |
||||||||
-SL | nmap -Sl 172.16.1.1 | list scan |
||||||||
Version detection
Version Detection |
||
|---|---|---|
Switch/Syntax | Example | Description |
-sV | nmap 172.16.1.1 -sV | Try to find the version of the service running on port |
-sV --version-intensity | nmap 172.16.1.1 -sV --version-intensity 6 | Intensity level range 0 to 9. |
-sV --version-all | nmap 172.16.1.1 -sV --version-all | Set intensity level to 9 |
-sV --version-light | nmap 172.16.1.1 -sV --version-light | Enable light mode |
-A | nmap 172.16.1.1 -A | Enables OS detection, version detection, script scanning, and traceroute |
-O | nmap 172.16.1.1 -O | Remote OS detection |
172.16.1.1 specification
172.16.1.1 Specification |
|
|---|---|
nmap 172.16.1.1 | single IP scan |
nmap 172.16.1.1 172.16.100.1 | scan specific IPs |
nmap 172.16.1.1-254 | scan a range of IPs |
nmap xyz.org | scan a domain |
nmap 10.1.1.0/8 | scan using CIDR notation |
nmap -iL scan.txt | scan 172.16.1.1s from a file |
nmap --exclude 172.16.1.1 | specified IP s exclude from scan |
Use of NMAP scripts NSE
Use of Nmap Scripts NSE |
|
|---|---|
nmap --script= test script 172.16.1.0/24 | execute thee listed script against target IP address |
nmap --script-update-db | adding new scripts |
nmap -sV -sC | use of safe default scripts for scan |
nmap --script-help="Test Script" | get help for script |
Firewall proofing
Firewall Proofing |
|
|---|---|
nmap -f [172.16.1.1] | scan fragment packets |
nmap –mtu [MTU] [172.16.1.1] | specify MTU |
nmap -sI [zombie] [172.16.1.1] | scan idle zoombie |
nmap –source-port [port] [172.16.1.1] | manual source port - specify |
nmap –data-length [size] [172.16.1.1] | randomly append data |
nmap –randomize-hosts [172.16.1.1] | 172.16.1.1 scan order randomization |
nmap –badsum [172.16.1.1] | bad checksum |
NMAP output formats
Nmap output Formats |
|
|---|---|
Default/normal output | nmap -oN scan.txt 172.16.1.1 |
XML | nmap -oX scanr.xml 172.16.1.1 |
Grepable format | snmap -oG grep.txt 172.16.1.1 |
All formats | nmap -oA 172.16.1.1 |
Scan options
Scan Options |
|
|---|---|
Syntax | Description |
nmap -sP 172.16.1.1 | Ping scan only |
nmap -PU 172.16.1.1 | UDP ping scan |
nmap -PE 172.16.1.1 | ICMP echo ping |
nmap -PO 172.16.1.1 | IP protocol ping |
nmap -PR 172.16.1.1 | ARP ping |
nmap -Pn 172.16.1.1 | Scan without pinging |
nmap –traceroute 172.16.1.1 | Traceroute |
NMAP Timing options
Nmap Timing Options |
|
|---|---|
Syntax | Description |
nmap -T0 172.16.1.1 | Slowest scan |
nmap -T1 172.16.1.1 | Tricky scan to avoid IDS |
nmap -T2 172.16.1.1 | Timely scan |
nmap -T3 172.16.1.1 | Default scan timer |
nmap -T4 172.16.1.1 | Aggressive scan |
nmap -T5 172.16.1.1 | Very aggressive scan |
Miscellaneous commands
Miscellaneous Commands |
|
|---|---|
nmap -6 | scan IPV6 targets |
nmap –proxies proxy 1 URL, proxy 2 URL | Run in targets with proxies |
nmap –open | Show open ports only |
Nmap + Nessus Cheat Sheet PDF
If you also use Nessus with Nmap, download this cheat sheet instead has all the tables included in the Nmap cheat sheet plus three extra Nessus tables.
Nessus install and use
Nessus Installation and Usage |
|
|---|---|
Installation | # apt-get install nessus |
Add administrator for the application | # nessus-adduser |
Update components | # nessus-update-plugins |
Start nessus | # /etc/init.d/nessusd start |
Check nessus port | # netstat -luntp or # netstat –landtp |
Nessuscli
Nessuscli |
|
|---|---|
nessus –h | Display help |
nessus –q | Run in batch mode |
nessus --list-policies | List policies included in .nessus configuration file |
nessus --list-reports | List report names included in .nessus configuration file |
nessus –p | List available plugins in the server |
nessus --policy-name (policy name) | Specify policy to use when a scan initiate in command line |
nessus -T (format) | Specify output report format (html, text, nbe, nessus) |
nessus --target-file (file name) | Use scan targets specified in the file instead of default .nessus file |
nessus –x | Do not check for SSL certificates |
Nessus server commands
Nessus Server Commands |
|
|---|---|
nessus-service -a ( ip address ) | Listens to specified IP address only |
nessus-service -c (Config file name ) | Set to use server side configuration file instead of default configuration file |
nessus-service -D | Set server mode to background run |
nessus-service -h | List summary of nessus commands |
nessus-service --ipv4-only | Listen to IPV4 only |
nessus-service --ipv6-only | Listen to IPV6 only |
nessus-service -K | Configure master password for nessus scanner |
nessus-service -p | Set server to listen to client specified port rather than default port 1241 |
nessus-service -q | Run in quiet mode |
Related: Nmap Scanning Tutorial






thank you so much for making the commands available for easy learning, including the video.