Nikto is one of the most popular open-source web server scanners, used for identifying potential security vulnerabilities in web applications and servers. As cyber threats become more sophisticated, it’s essential for security professionals and system administrators to regularly scan their web servers to uncover vulnerabilities that could be exploited by attackers. Nikto simplifies this process by automating the scanning of web servers for over 6,000 known security issues, making it a valuable tool for network and application security assessments.
In this Nikto cheat sheet, we provide a handy reference to help you quickly leverage Nikto’s capabilities for effective web server scanning and vulnerability detection. Whether you’re a seasoned penetration tester or a system administrator looking to bolster your server security, this cheat sheet will guide you through the most common Nikto commands, options, and use cases.
Nikto’s open-source nature, combined with its extensive set of scanning features, allows it to be used for a wide range of security testing purposes. It can detect a variety of vulnerabilities, including misconfigured web servers, outdated software versions, security flaws in web applications, and even potential SQL injection points. It can also uncover information disclosure vulnerabilities and various other security weaknesses that might otherwise be overlooked.
This cheat sheet is designed to streamline your workflow by providing concise explanations and examples for using Nikto to its full potential. From basic scanning commands to advanced configuration options, you’ll learn how to use Nikto to identify security risks and generate reports. You will be able to integrate Nikto into your broader security testing or vulnerability management strategy.
Whether you are assessing a single server or conducting routine web application security assessments, this cheat sheet will be an indispensable tool in your security toolkit.
All the tables provided in the cheat sheets are also presented in tables below which are easy to copy and paste.
The Nikto cheat sheet covers:
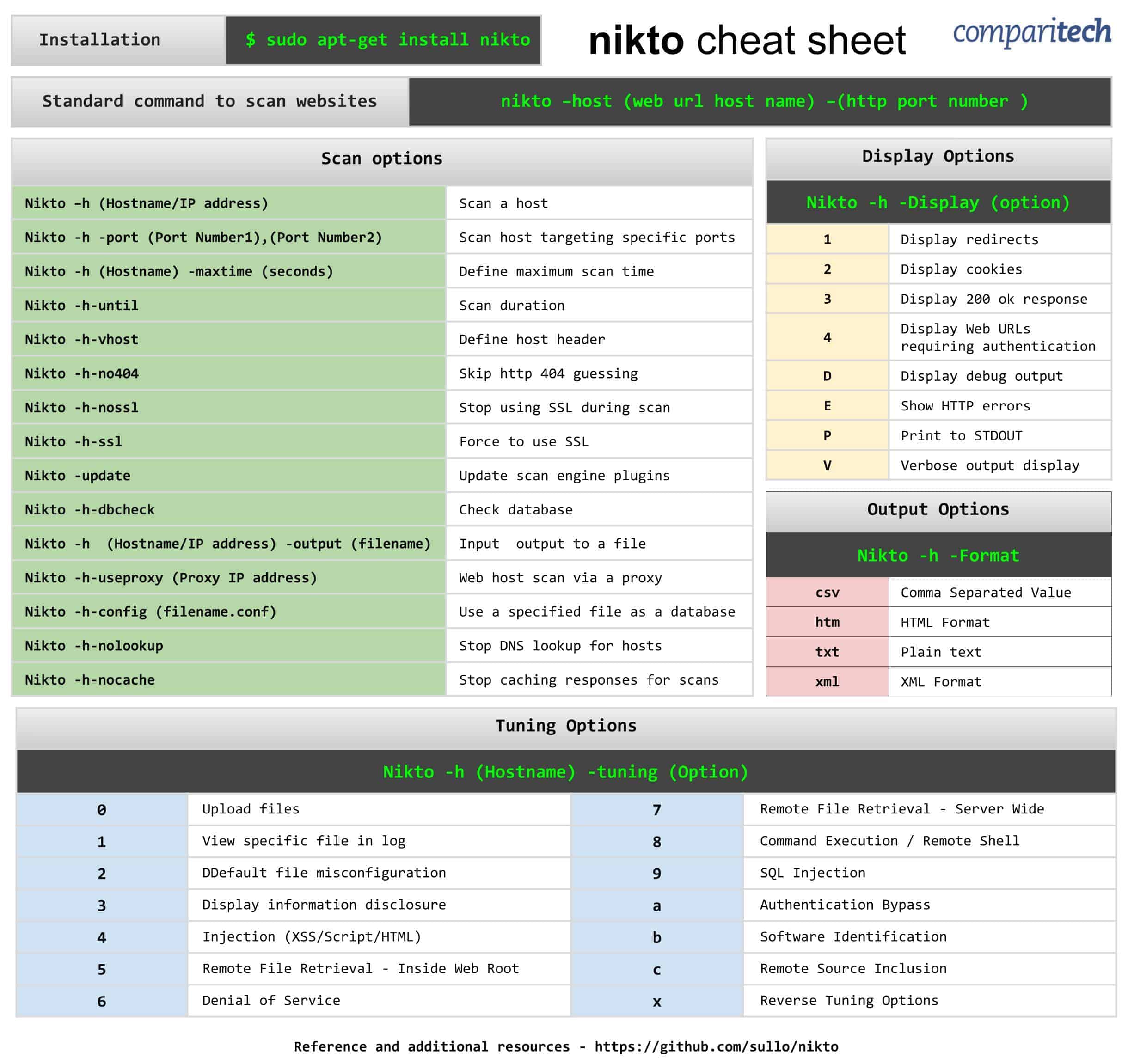
- Installation
- Standard command to scan websites
- Scan options
- Display options
- Output options
- Tuning options
View or Download the Cheat Sheet JPG image
Right-click on the image below to save the JPG file ( 2427 width x 2302 height in pixels), or click here and open it in a new browser tab. Once the image opens in a new window, you may need to click on the image to zoom in and view the full-sized jpeg.
View or Download the cheat sheet PDF file
You can download the cheat sheet PDF file here. If it opens in a new browser tab, simply right click on the PDF and navigate to the download selection.
What’s included in the Cheat Sheet
The following categories and items have been included in the cheat sheet:
Installation
Installation | $ sudo apt-get install nikto |
|---|
Standard command to scan websites
Standard command to scan websites | nikto –host (web url host name) –(http port number ) |
|---|
Scan options
Scan options |
|
|---|---|
Nikto –h (Hostname/IP address) | Scan a host |
Nikto -h -port (Port Number1),(Port Number2) | Scan host targeting specific ports |
Nikto -h (Hostname) -maxtime (seconds) | Define maximum scan time |
Nikto -h-until | Scan duration |
Nikto -h-vhost | Define host header |
Nikto -h-no404 | Skip http 404 guessing |
Nikto -h-nossl | Stop using SSL during scan |
Nikto -h-ssl | Force to use SSL |
Nikto -update | Update scan engine plugins |
Nikto -h-dbcheck | Check database |
Nikto -h (Hostname/IP address) -output (filename) | Input output to a file |
Nikto -h-useproxy (Proxy IP address) | Web host scan via a proxy |
Nikto -h-config (filename.conf) | Use a specified file as a database |
Nikto -h-nolookup | Stop DNS lookup for hosts |
Nikto -h-nocache | Stop caching responses for scans |
Display options
Display Options |
|
|---|---|
Nikto -h -Display (option) |
|
1 | Display redirects |
2 | Display cookies |
3 | Display 200 ok response |
4 | Display Web URLs requiring authentication |
D | Display debug output |
E | Show HTTP errors |
P | Print to STDOUT |
V | Verbose output display |
Output options
Output Options |
|
|---|---|
Nikto -h -Format |
|
csv | Comma Separated Value |
htm | HTML Format |
txt | Plain text |
xml | XML Format |
Tuning options
Tuning Options |
|||
|---|---|---|---|
Nikto -h (Hostname) -tuning (Option) |
|||
0 | Upload files | 7 | Remote File Retrieval - Server Wide |
1 | View specific file in log | 8 | Command Execution / Remote Shell |
2 | Default file misconfiguration | 9 | SQL Injection |
3 | Display information disclosure | a | Authentication Bypass |
4 | Injection (XSS/Script/HTML) | b | Software Identification |
5 | Remote File Retrieval - Inside Web Root | c | Remote Source Inclusion |
6 | Denial of Service | x | Reverse Tuning Options |
Reference and additional resources: https://github.com/sullo/nikto
Nikto FAQs
What does Nikto command do?
Nikto is a vulnerability scanner for Web servers. This provides lists of weaknesses that can be filtered to specific vulnerability types. The scanner looks for thousands of weaknesses, which means that its output can be overwhelming if you don’t properly target each scan and categorize the results into groups of weaknesses that can be closed down with a single action.
What is tuning in Nikto?
Tuning is the term used by Nikto for its search settings. Tuning a scan to a specific type of weakness limits the actions of the vulnerability scanner. Tuning is the core step in using Nikto because its breadth is so great that you will receive too much information to deal with if you don’t target each run.
How long does a Nikto scan take?
A full Nikto scan can take 45 minutes to run. To get an idea of the extensive nature of each investigative run, the Nikto system has a list of 6,700 files to look for. The important skill to deploy when using Nikto is learning how to limit each scan to make it quicker to complete and so that the results give you just enough remediation tasks that can be meaningfully handled.