Penetration testing requires cybersecurity consultants to think like hackers. Known as “white hat hackers”, penetration testers need to use the same tools that hackers deploy to break into networks. Automated tools save time and perform repetitive tasks, such a brute force password cracking, that couldn’t be performed manually in a reasonable length of time.
Here is our list of the best network penetration testing tools:
- Zenmap A graphical user interface for Nmap, which is a widely used hacker tool for documenting networks. Both tools are free and run on Windows, Linux, BSD Unix, and macOS.
- Burp Suite is a potent hacker tool with a graphical front end that offers various research and attack utilities. This system is available in free and paid versions and will run on Windows, macOS, and Linux.
- Acunetix This security system can be used as a vulnerability scanner or penetration testing tool. Options include external scanning and exploit detection from within the network.
- Intruder This cloud-based cybersecurity platform offers automated vulnerability scanning to identify security weaknesses in IT systems.
- Vonahi Security vPenTest This SaaS platform provides automated network penetration testing tools that can also be implemented as a continuous testing system.
- Invicti This vulnerability scanner can spot entry points in Web applications, such as cross-site scripting and SQL injection opportunities. This is a cloud-based service that can also be installed on Windows and Windows Server.
- Ettercap is a free hacker tool that is reliable and widely used. This tool researches networks and implements different attack scenarios. Available for Linux, Unix, Mac OS X, and Windows 7 and 8.
- Metasploit is a highly respected penetration testing tool that is available in free and paid versions. Rapid7 provides the paid edition. It runs on Windows, Windows Server, macOS, RHEL, and Ubuntu.
Penetration testing tools are closely connected to vulnerability managers. However, there is a fine line between automated network pen-testing tools and vulnerability scanners.
As a rule of thumb, a vulnerability scanner will work programmatically down a list of known exploits and check the system for the presence of that fault. A penetration tester will look for the same weaknesses and then launch an attack appropriate to the specific loophole to break into the system.
Typical hacker tools for penetration testing
While vulnerability scanners don’t need any skills to run, some on-demand scanners can be an excellent overall system run-through that indicates to the hacker which attacks strategy to use. So, in some cases, on-demand vulnerability scanners can be counted as penetration testing tools.
At the other end of the spectrum, the typical hacker toolkit includes some old, tried, and tested tools that are free to use and are widely known to be the mainstays of any hacker toolkit. Penetration testers need to use those same tools.
So, there is a wide range of tools to consider when you are kitting out to perform penetration testing.
Network penetration testing tools
Penetration testing falls into two broad categories:
- Endpoint penetration testing
- Network penetration testing
While endpoint penetration testing looks at weaknesses in operating systems and software, network penetration testing aims for communications weaknesses, such as open ports. Although the ultimate goal is to get onto an endpoint, every type of hacker attack needs to pass through a network to reach a target.
Even after an endpoint has been breached, network attacks don’t stop. Many common network attacks can only be performed from within the network. These secondary network attacks are aimed at moving across a network to search or infect other endpoints.
So, the category of network penetration testing tools includes systems to get you into a network and systems to document the network and investigate ways into endpoints.
The Best Network Penetration Tools
As the range of helpful network penetration testing tools includes older, accessible, and quick services to complete system scanning services that cost a lot of money, you can balance your budget by mixing your toolkit with utilities from across the price spectrum.
Our methodology for selecting a network penetration tool
We reviewed the market for pen testing tools for networks and analyzed the options based on the following criteria:
- A good mix of options from quick utilities through to complex system scanners
- Tools that combine system research and attack implementation
- Systems for external attacks to get into the network and internal attacks to cross the network
- Utilities that document all of their findings
- Attack recording for later analysis
- A free tool or an opportunity to assess a paid tool for free
- A reasonable price for each paid tool that fits the capabilities of the utility.
- We made sure to include tools for each of the major operating systems.
You can read more about each of these systems in the following sections.
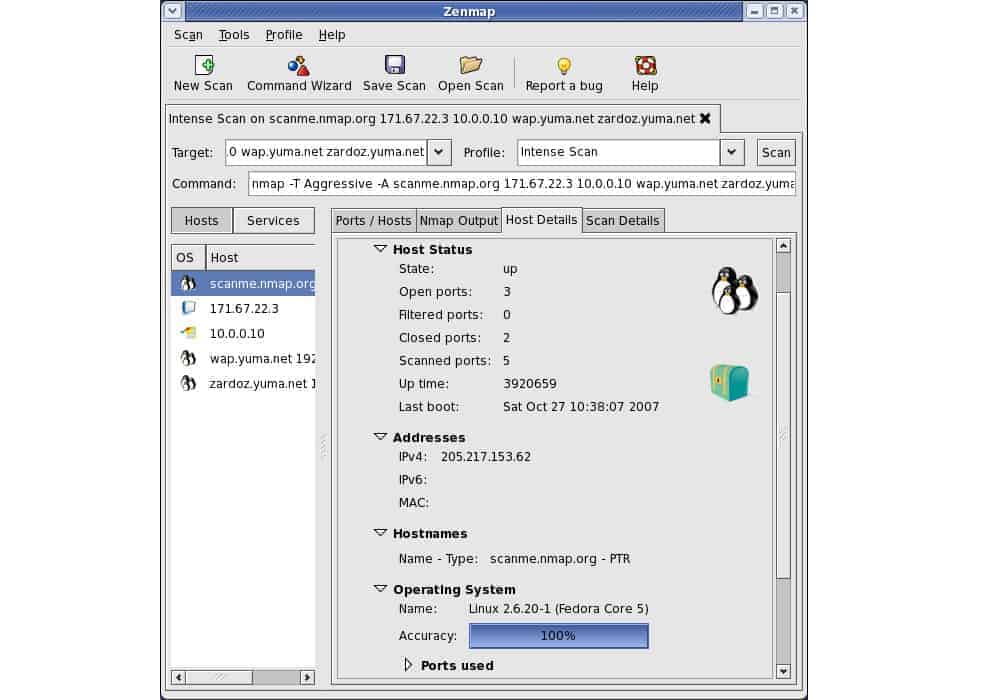
1. Zenmap
Zenmap is a front end for Nmap. While hackers love to use Nmap, a command-line utility, The displays and graphical representations on Zenmap are easier to work with for testing and analysis. Nmap is also called Network Mapper. It scans a network and discovers all devices and endpoints, probing each for all available information. This is essential information for hackers who want to break into other endpoints once they have already established a foothold on one device on the network.
Key Features:
- Network Scanning and Mapping: Provides capabilities for scanning networks and creating visual maps of network topology.
- Network Discovery: Zenmap facilitates network discovery by scanning the network to identify active hosts, services, and open ports.
- Graphical Interface: Offers a graphical user interface (GUI) for easier navigation and visualization of scan results, enhancing user experience.
- Port Scanning: Performs port scanning to identify open ports and services running on target hosts, enabling users to assess the security posture of their network.
- Host Enumeration: Enumerates hosts and services to gather information about operating systems, versions, and configurations, aiding in vulnerability assessment and penetration testing.
Why do we recommend it?
Zenmap is a free tool and it provides a graphical front-end for Nmap. The Nmap system is a staple of any penetration tester’s toolkit. The benefit of that command line tool is that it can be set up to run in scripts. Zenmap doesn’t offer that level of automation but its results are easier to read.
Nmap derives all network information by capturing packets and scanning their headers. This packet capture feature is also available in Zenmap. You can use it to look for information about device settings and endpoint identities manually.
Zenmap and Nmap are free to use and run on Windows, Linux, BSD Unix, and macOS.
Who is it recommended for?
Zenmap could be used on the side by penetration testers as a way to better understand the results of Nmap. However, Nmap is a more likely tool for penetration tests. A casual investigator who doesn’t have the skills of regular testers would probably prefer Zenmap.
Pros:
- Cross-Platform Compatibility: Zenmap is available for multiple operating systems, ensuring compatibility and flexibility in deployment across different environments.
- Output Formats: Provides multiple output formats for scan results, including interactive GUI displays, plain text, XML, and grep-able formats, facilitating analysis and reporting.
- User-Friendly Interface: Zenmap features an intuitive graphical interface that simplifies the process of network scanning and result interpretation, making it accessible to users of all levels of expertise.
- Scripting Support: Provides scripting support with Nmap Scripting Engine (NSE), enabling users to extend functionality, automate tasks, and develop custom scripts.
Cons:
- Resource Intensive: Zenmap’s scanning operations can be resource-intensive, especially when performing intensive scans on large networks or with aggressive timing options.
- No Attack Support: Lacks support for conducting attacks or penetration testing; primarily focused on scanning and packet capture.
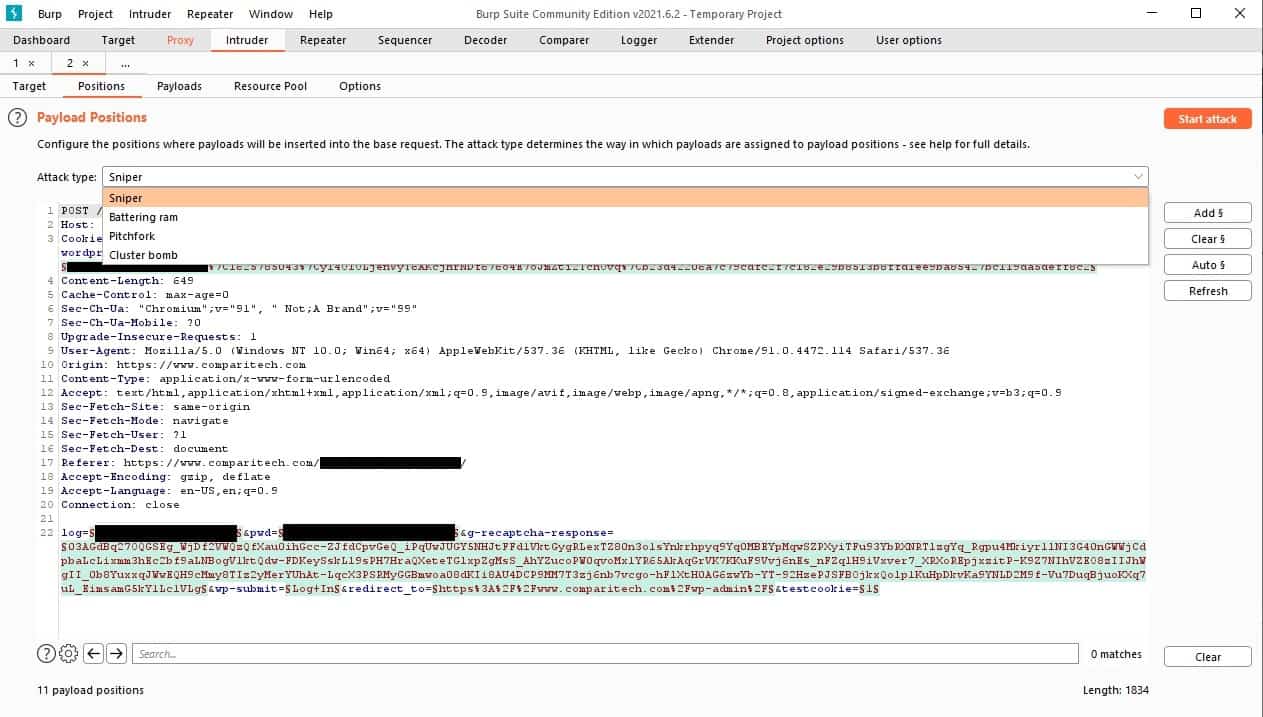
2. Burp Suite
Burp Suite is a tool that offs both research and attack utilities to pen testers. PortSwigger produces this package of hacker tools. The system includes both a graphical user interface and a command-line utility. There are three versions of Burp Suite: the Community Edition, accessible, the Professional Edition, and the Enterprise Edition. Both versions use the same interface, but many functions are disabled in the free system.
Key Features:
- Web Application Scanning: Burp Suite offers powerful web application scanning capabilities to identify security vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms.
- Proxy Tool: Features a proxy tool that allows users to intercept and modify HTTP and HTTPS traffic between the browser and the web server, facilitating manual testing and analysis of web applications.
- Automated Scanning: Provides automated scanning functionality to discover common web application vulnerabilities, reducing manual effort and enabling efficient vulnerability assessment.
- Vulnerability Detection: Detects vulnerabilities in web applications through a combination of active and passive scanning techniques, providing comprehensive coverage of security issues.
Why do we recommend it?
Burp Suite offers both automated scanning and manual tools. There is a free version of this package, which is the same package as the paid service but with the advanced features disabled. The great feature of the manual tool is that you can perform research in investigative tools and the discovered values will automatically copy over to the attack tools.
One of the main functions that free users don’t get is an automated vulnerability scanner. That shouldn’t be a problem for penetration testers because they need to run individual tests. The Enterprise Edition is a full vulnerability scanner.
The outstanding feature of Burp Suite is that other tabs in the interface cater for different stages in a test, so you can keep your tasks separate and well organized. However, the system also facilitates copying data from one screen to another, so you can research in one tab and then copy over the results into an attack screen.
The Burp Suite service works on a combination of methods, including packet capture and system hijacking. As a result, attacks conducted with Burp Suite can be undetectable to the victim. It is also possible to set up test data in a file, which is a significant advantage for tasks like credentials cracking. For example, you can feed in the output of a password generation tool or a credentials dictionary.
Burp Suite runs on Windows, macOS, and Linux. Download the Community edition for free or request a free trial of the Professional edition.
Who is it recommended for?
One problem that many potential customers will have with Burp Suite is that the paid system is very expensive. While corporate consultancies could probably afford that, independent pen testers would go for the free version. The free edition is better for penetration testing while the paid version is more of a vulnerability scanner.
Pros:
- GUI Interface and Command-Line Utility: Offers both a graphical user interface (GUI) and a command-line utility for flexibility in usage.
- Extensibility: Provides a platform for creating custom scanning rules, scripts, and extensions, allowing users to enhance functionality and adapt the tool to their specific testing requirements.
- Active Community: Benefits from an active user community and extensive documentation, tutorials, and resources for support, knowledge sharing, and collaboration.
Cons:
- Report Formats: Lacks presentable report formats, which could improve the user experience for reporting vulnerabilities and findings.
- Cost: Burp Suite is a commercial product, and the licensing costs may be prohibitive, especially for smaller businesses or independent security professionals.
3. Acunetix
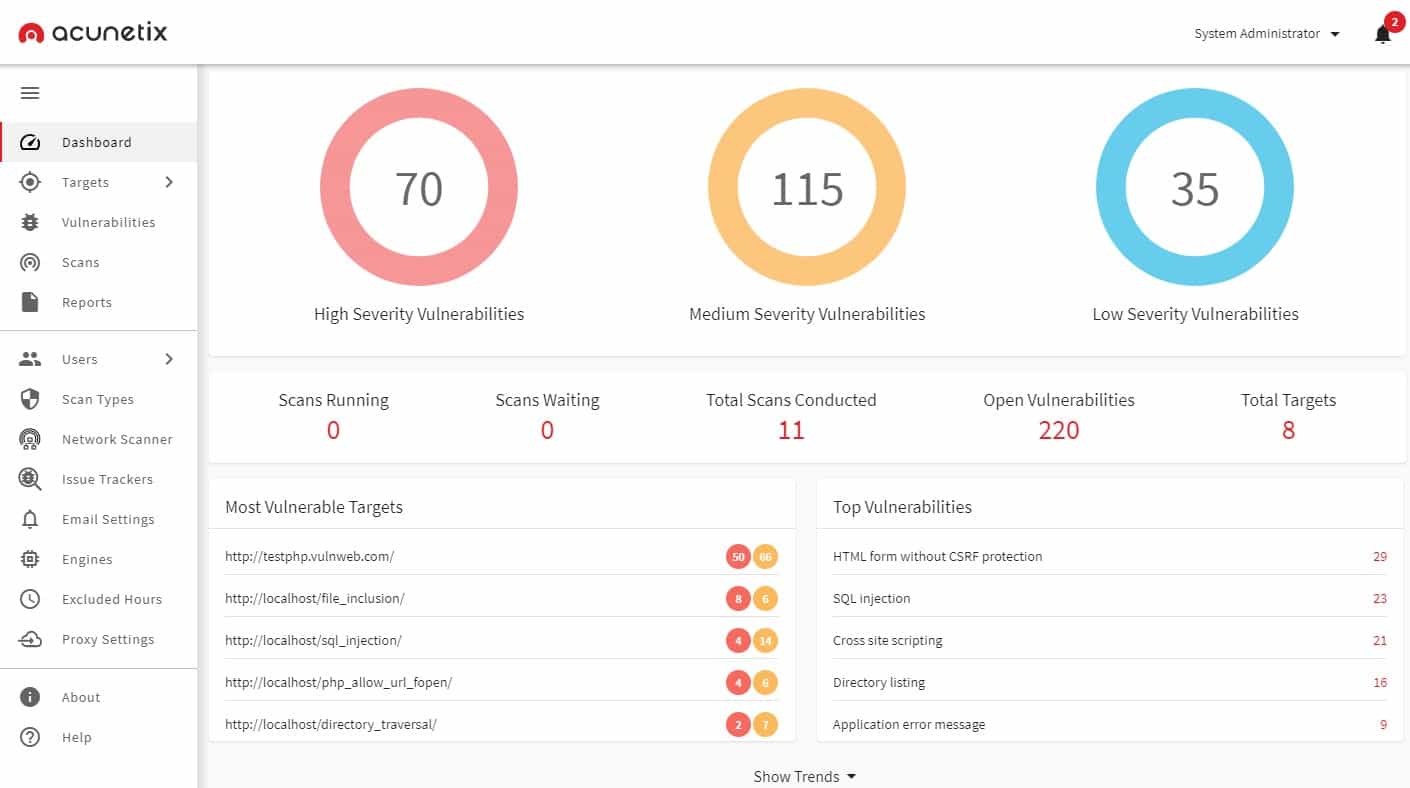
Acunetix can be used in many different ways. It is available in three editions, and that increases its flexibility. This is a vulnerability scanner, but it can also be used for on-demand scans during penetration testing. Options include scans from outside the network to check on Web application weaknesses and the external profile of a network. The tool can also scan a network from within to spot opportunities for moving onto different endpoints.
Key Features:
- Web Vulnerability Scanning: Acunetix offers comprehensive web vulnerability scanning to identify security flaws such as SQL injection, XSS, and vulnerable server configurations.
- Deep Scan Technology: Utilizes advanced crawling and scanning algorithms to comprehensively scan and identify vulnerabilities in web applications, APIs, and web services.
- OWASP Top 10 Coverage: Provides coverage for vulnerabilities listed in the OWASP Top 10, ensuring that critical security issues are identified and addressed.
- DAST, SAST, and IAST Services: Offers DAST, SAST, and IAST capabilities for real-time testing of web applications during runtime, allowing for more accurate detection of vulnerabilities and reduced false positives.
Why do we recommend it?
Acunetix provides a great deal of automation in scanning for weaknesses, which makes it a good vulnerability manager. However, it can also prove to be a time-saver for penetration testing. You would use Acunetix for a general scan to identify issues that need to be tested and confirmed manually.
The external scanner of Acunetix has a list of more than 7,000 potential weaknesses, including the OWASP Top 10 Web application vulnerabilities. The internal network scanner check for more than 50,000 exploits.
The Acunetix system can also be used as a Dynamic Application Security Testing (DAST) system. In addition, it can also perform Interactive Application Security Testing (IAST) and Static Application Security Testing (SAST). These tools are suitable for a DevOps operation because they can be integrated into software development project management systems.
Once you subscribe to an Acunetix package, what you use it for is up to you. So, you can use it for penetration testing, vulnerability scanning, and testing in a CI/CD pipeline.
There are three editions of Acunetix called Standard, Premium, and Acunetix 360. Of these three, the most suitable for network penetration testing is the Premium plan. This is the only one of the three editions that include internal network testing.
Who is it recommended for?
Being so highly automated, this package is more suitable as a vulnerability manager for automated security scanning. The tool can also be used as a continuous tester in a CI/CD pipeline. The tool performs external scans but can be enhanced by the addition of OpenVAS for network vulnerability scanning.
Pros:
- Integration with DevOps Tools: Integrates seamlessly with development tools and issue tracking systems, enabling integration into the DevOps workflow and facilitating collaboration between development and security teams.
- Continuous Monitoring: Supports continuous monitoring of web applications for new vulnerabilities and emerging threats, ensuring proactive detection and mitigation of security risks.
- User-Friendly Interface: Features an intuitive and user-friendly interface that streamlines the scanning process, making it accessible to both experienced security professionals and beginners.
- Deployment Options: Offers the option for a SaaS platform or on-premises software deployment.
Cons:
- No Attack Capabilities: Lacks features for conducting attacks or simulations, focusing solely on vulnerability scanning and testing.
- Cost: Acunetix is a commercial product, and the licensing costs may be prohibitive for some individuals or organizations.
Acunetix is offered as a hosted Software-as-a-Service platform. However, you can opt to download the software and run the system in-house. The package will run on Windows, macOS, and Linux.
4. Intruder
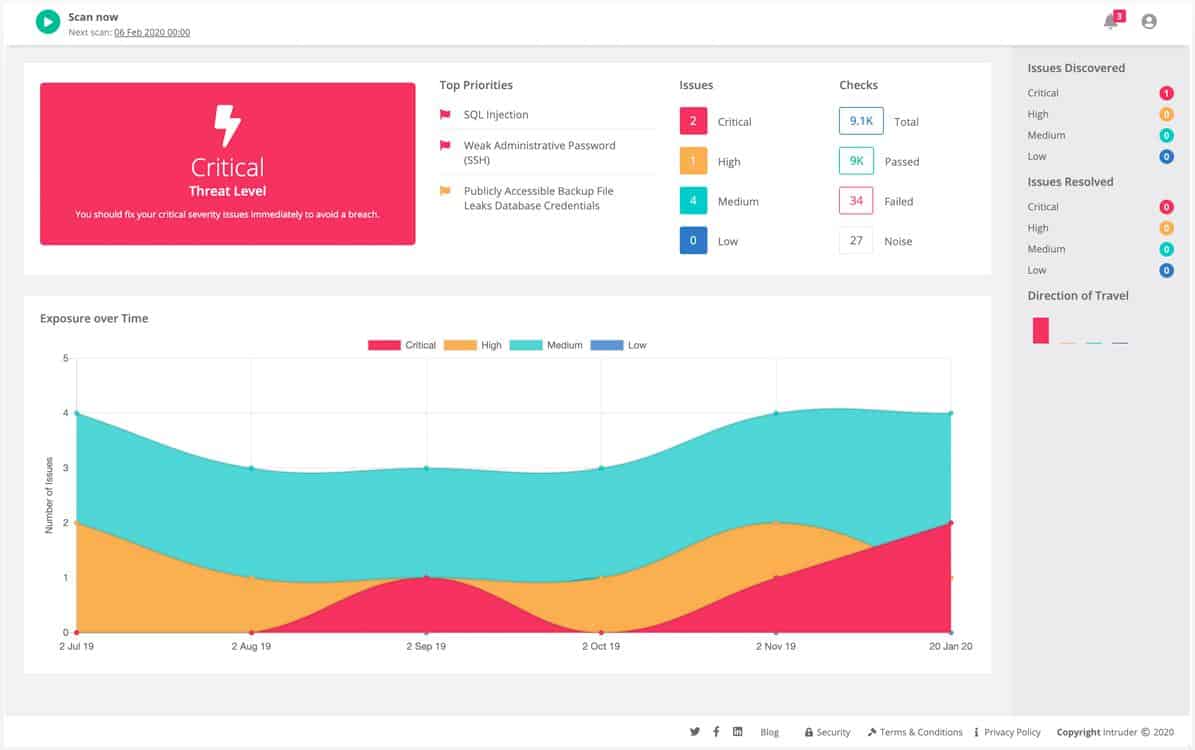
Intruder is a vulnerability scanner that can provide attack surface monitoring that is useful for penetration testing. You would use this system to look for security loopholes and then try an attack to confirm its potential as an exploit.
Key Features:
- Vulnerability Scanning: Offers vulnerability scanning to identify potential weaknesses in network infrastructure, web applications, and cloud services.
- Asset Discovery: Automatically discovers and catalogs assets within the organization’s infrastructure, providing visibility into the attack surface and potential points of entry for attackers.
- Compliance Monitoring: Offers compliance monitoring capabilities to assess the organization’s adherence to industry standards and regulatory requirements, such as PCI DSS and GDPR.
- Threat Intelligence Integration: Integrates with threat intelligence feeds to enrich scan results with additional context and prioritize remediation efforts based on known threats and vulnerabilities.
Why do we recommend it?
Intruder can be used as an automated penetration testing tool, although it is actually a vulnerability scanner. There are two versions of this system that offer tools for black box and white box scanning. You can get just external scanning, which also covers Web applications or you can get both external and internal scanning.
The intruder can be used for continuous testing in a development environment or as attack surface monitoring in the production environment. The developers of the intruder cloud platform are a penetration testing team and you can hire them to check your system on a consultancy basis. So, the intruder.io service offers a range of options for businesses that don’t have the size or budget to enable them to run an in-house cybersecurity team.

Intruder can save a lot of time with its on-demand full system sweep. The package provides external scans in all plans, and you can choose an edition that gives you network scans as well. The system will implement automated scans at a different frequency according to the plan that you choose. That’s great for system managers and it can highlight problems that require further investigation. So, penetration testers are provided with a starting point for weaknesses to probe.
Who is it recommended for?
This system is useful for businesses that don’t want the expense of hiring a penetration tester. Alternatively, it can be used by a penetration tester to perform research and then manually confirm any weakness that the scanner reveals. The service is constantly updated with new attack discoveries and rescans all clients whenever one emerges.
Pros:
- Continuous Monitoring: Provides continuous monitoring for new vulnerabilities and emerging threats, ensuring organizations stay ahead of evolving cybersecurity risks.
- Ease of Use: Features an intuitive user interface and streamlined setup process, making it accessible to users of all levels of expertise.
- Remediation Guidance: Offers actionable remediation guidance and recommendations to help organizations prioritize and address identified vulnerabilities effectively.
Cons:
- Limited Coverage: May have limitations in coverage compared to some other vulnerability management solutions, particularly in specialized areas or niche technologies.
- False Positives: Like any vulnerability scanning tool, Intruder may generate false positive results, requiring manual validation and verification by security professionals.
As the Intruder system is a cloud service, there is no need to download or install software, you just sign up for the service at its website. You can experience the system with a 14-day free trial.
5. Vonahi Security vPenTest

vPenTest is a SaaS platform designed to assist IT service providers in performing automated network penetration tests for their clients. The platform was created by a team with extensive background in cybersecurity, consulting, managed services, and product development. It offers a comprehensive network penetration test that goes beyond what a typical vulnerability scanner can provide, encompassing both internal and external assessments.
Key Features:
- Continuous real-time testing: Live results in the dashboard
- Good for managed service providers: Multi-tenant and white-label capable
- Compliance management: For PCI DSS, HIPAA, and SOC2
- Automated expertise: Solidifies the techniques used by a penetration testing team
- Test launch options: Run it continuously, on a schedule, or on demand
Why do we recommend it?
Vonahi Security vPenTest is a rare tool that sits between the definition of vulnerability manager and penetration tester. While vulnerability scanners are thought to be automated penetration testing systems, they don’t quite embody the ingenuity of a human penetration testing team. Vonahi Security designed this system to fully model their methods for penetration testing.
vPenTest is designed to enhance the speed and efficiency of network security assessments. It provides real-time results, quickly scanning large networks and reducing the time required for manual testing. This helps to ensure that the results are accurate and consistent, as the same tests are performed in a repeatable manner, reducing the chances of human error.

vPenTest is also designed to be scalable, accommodating larger networks and freeing up resources for other tasks. This combined with its comprehensive testing capabilities, including vulnerability scanning, penetration testing, and configuration deficiency checks, provides a more complete assessment of network security.
Who is it recommended for?
This package is marketed to managed service providers. It isn’t intended as a protection service for the MSP but is a sell-through product for the provider to offer to their clients. So, vPenTest will secure the clients of MSPs. Vonahi essentially uses MSPs as its sales force and provides a markup opportunity.
Pros:
- Attack surface testing: Scans from an external location
- Income generator: Provides MSPs with an extra income stream without any investment
- Automated reporting: Provides both summaries and detailed remediation guidance
- Network penetration testing: Both external and internal
- System hardening validation: Verification of network security measures
Cons:
- No web application security testing: Also no testing for APIs
Vonahi Security vPenTest is hosted in the cloud and has a much better interface than most penetration testing tools. You don’t have to be a qualified penetration tester to use this package. The administrator can choose the frequency of scan and it is also possible to just run it on demand. The system produces detailed explanations of each discovered weakness. The SaaS platform is designed for use by managed service provides in order to scan the networks of their clients.
The solution is cost-effective, built for MSPs with flexible pricing models to help secure their clients and generate new revenue streams. Additionally, vPenTest automatically generates several reports, including executive summaries and technical reports, providing easy-to-understand information for all stakeholders. You can register for the demo and access the free trial to explore how vPenTest works.
6. Invicti
Invicti is a vulnerability scanner like Acunetix, and just like Acunetix, this system can also be used as a penetration testing tool. However, Invicti doesn’t have the internal network testing features of Acunetix, which is why this tool is our number two pick. The scans that this system offers mainly focuses on Web application vulnerabilities.
Key Features:
- Advanced Tools: Offers advanced tools and techniques for web application security testing, including crawling, scanning, and attack payloads, to provide comprehensive coverage of security issues.
- Reporting and Analysis: Generates detailed reports and analysis of scan results, including vulnerability severity, impact, and remediation recommendations.
- SaaS Package: Available as a Software-as-a-Service (SaaS) package for easy deployment and management.
- External Scanning Viewpoint: Provides an external scanning viewpoint, enabling thorough security assessments.
- CI/CD Testing: Supports Continuous Integration/Continuous Deployment (CI/CD) testing processes.
Why do we recommend it?
Invicti is a Web vulnerability scanner that provides an AI-based inference system to spot illogical connections and configurations, which create security weaknesses. This insight identifies security loopholes that would not be spotted by traditional vulnerability lists and provides opportunities for investigations by penetration testers.
The Invicti scan can be run constantly and automatically. However, for penetration testing, you would launch scans on demand. Invicti operates a browser-based crawler that tests for a known list of Web application vulnerabilities and then reports on them. This, therefore, is a research tool that a penetration tester would use to establish which types of attacks would be fruitful. Then, the actual attack would be implemented with another tool.
Although this is an automated scanning system, each run can be customized. It is possible to limit the tests performed in a session, thus shortening the tool’s runtime. You can also set up specific parameters for each probe, which brings you closer to implementing an actual attack. Failed scans are good news and offer proof of system resilience. These reports can be used as part of data privacy standard compliance reporting.
Who is it recommended for?
This system is very similar to Acunetix and has the same use cases. You would use this system as a vulnerability scanner for live systems or as a continuous tester for Web applications under development. The tool can be used to provide pointers for deeper investigation by penetration testers.
Pros:
- Integration: Integrates seamlessly with third-party tools and services, enabling customization and integration into existing workflows and systems.
- Fast Scanner for Web Application Vulnerabilities: Offers a fast scanning process for detecting web application vulnerabilities.
- Option for Manual Runs and Continuous Automated Scans: Provides flexibility with both manual and automated scanning options.
Cons:
- Can’t Implement Attacks: Lacks features for implementing attacks or simulations, focusing solely on vulnerability scanning.
- No Internal Network Scanning Features: Does not include features for scanning internal network infrastructure, limiting its scope to external assessments.
Invicti is a SaaS platform that can be used for system testing during Web app development and vulnerability scanning and penetration testing. It is possible to opt for the package as on-premises software that will run on Windows and Windows Server.
7. Ettercap
Ettercap intercepts network traffic; it doesn’t block that traffic. It also facilitates masquerading and packet injection, so it can be used to hijack all of the routings on communications for all of the endpoints on a network or just one.
Key Features:
- Network Sniffing: Ettercap facilitates network sniffing to capture and analyze packets transmitted over a local network, providing visibility into network traffic.
- Man-in-the-Middle Attacks: Supports man-in-the-middle (MITM) attacks to intercept, modify, or redirect network communications between two parties, allowing for various security assessments and penetration testing scenarios.
- Protocol Analysis: Provides protocol analysis capabilities to dissect and interpret various network protocols, including HTTP, FTP, SSH, and more, enabling detailed inspection and manipulation of network traffic.
- ARP Spoofing: Supports ARP spoofing attacks to manipulate the Address Resolution Protocol (ARP) cache of target devices, redirecting traffic through the attacker’s machine.
Why do we recommend it?
Ettercap is an impressive tool but its interface is a little clunky. This tool is quite old and it hasn’t been updated for a while. However, it is free and that makes it attractive to most penetration testers. The system provides traffic interception opportunities, which can be used to trick and also test configurations.
The Ettercap interface is not very good. It is just a bespoke Terminal / Command Prompt screen. The whole Ettercap system is getting a little out of date and could do with a significant overhaul. However, the attack capabilities of this tool are compelling, which is why it is worth putting up with the feeble interface.
Ettercap works by hijacking the addressing system of the network in traffic sent to a specific endpoint. That means you need to already be inside the network before you can use this tool. The system Ettercap uses to divert traffic is called ARP poisoning. The tool can also be used for Denial of Service attacks, man-in-the-middle attacks, and DNS hijacking.
Ettercap is free forever, and it installs on Linux, Unix, Mac OS X, and Windows 7 and 8. Unfortunately, it doesn’t work on macOS or Windows 10.
Who is it recommended for?
Ettercap is definitely a penetration testing tool. It can also be used by real-world hackers. There isn’t any automation in this package, so it isn’t a vulnerability scanner or a continuous tester. You need to already be inside the network to use this system. It will now work on Windows 10.
Pros:
- Plugin Support: Offers plugin support for extending functionality and adding custom features, allowing users to customize and enhance the tool according to their specific requirements.
- Cross-Platform Compatibility: Ettercap is cross-platform and runs on various operating systems, ensuring flexibility and compatibility with diverse environments and setups.
- Control over Network Traffic: Enables users to control network traffic for one or multiple endpoints, enhancing attack customization.
- Network Sniffing Capabilities: Offers powerful network sniffing capabilities for capturing and analyzing network traffic, providing insights into network communications and potential security vulnerabilities.
Cons:
- Legal and Ethical Concerns: Performing MITM attacks and network sniffing activities using Ettercap may raise legal and ethical concerns. Users should ensure they have appropriate authorization and consent before conducting security testing with Ettercap.
- Limited GUI Support: While Ettercap offers some GUI features, its primary interface is command-line-based, which may be less user-friendly for some users who prefer GUI-based tools.
- Limited Platform Support: Does not have versions available for macOS or Windows 10, limiting its compatibility with modern operating systems.
8. Metasploit
Metasploit offers both automated scans and individual manual attack tools. The service is available in free and paid versions, with much more automation in the paid version. The free version is called Metasploit Framework, and this was the original open-source service.
Key Features:
- Exploitation Framework: Metasploit provides a comprehensive exploitation framework with a vast database of known vulnerabilities and exploits, enabling security professionals to assess and exploit security weaknesses in target systems.
- Vulnerability Scanning: Offers vulnerability scanning capabilities to identify potential security flaws and misconfigurations in networked systems and applications.
- Penetration Testing: Facilitates penetration testing activities, including reconnaissance, exploitation, post-exploitation, and reporting, allowing users to simulate real-world attacks and assess the effectiveness of security defenses.
- Payload Generation: Supports payload generation for delivering exploits to target systems, including reverse shells, meterpreter sessions, and other payloads for remote command execution.
- Post-Exploitation Modules: Includes post-exploitation modules for maintaining access to compromised systems, gathering additional information, and escalating privileges, enabling advanced exploitation scenarios.
Why do we recommend it?
Metasploit is a must-have penetration testing tool. The free version of the system is called Metasploit Framework. Its interface is not so hot because it just provides a command line window. Despite that interface problem, the free version is much more popular with penetration testers than the paid Metasploit Pro.
The project is now fully funded by Rapid7, which bought the right to create the paid version on top of Metasploit Framework. That paid version is called Metasploit Pro. In truth, there aren’t many facilities in Metasploit Framework, and you will probably want to go for Metasploit Pro. However, it is costly.
Both versions of Metasploit include a vulnerability scanner that searches for more than 1,500 vulnerabilities. Both versions also have a command-line option, which is accessed through a bespoke Terminal / Command Prompt screen, called Metasploit Console. Only Metasploit Pro offers a graphical user interface, which is browser-based.
Manual tools in the Framework version allow you to create a brute-force password-cracking attempt. However, that task is easier to perform with the automated brute force system in the Pro version. The paid version also includes system auditing and reporting services, which are great for compliance reporting.
Both tools are excellent for launching attacks from within networks. However, a handy Network Discovery feature is only available in Metasploit Pro. The Pro version is also equipped for Web application scanning.
Who is it recommended for?
A successful penetration testing consultancy might be attracted to the Metasploit Pro system. However, it is very expensive. Universities and penetration testing training courses all explain to students how to use Metasploit Framework, which partly explains why that free tool is so widely used in the industry.
Pros:
- Active Community: Benefits from an active and vibrant community of users, developers, and contributors who continuously contribute new exploits, modules, and improvements to the framework.
- Versatility: Metasploit is versatile and can be used for various security testing activities, including penetration testing, vulnerability assessment, and post-exploitation activities.
- Flexibility: Provides flexibility through its modular architecture, allowing users to customize and extend the framework with their own modules, scripts, and plugins to suit their specific requirements and use cases.
- Choice of Free and Paid Versions: Provides options for both free and paid versions, catering to different user needs.
Cons:
- Incomplete Toolset in Each Edition: Both the free and paid versions may not have a complete set of tools, requiring users to choose based on their specific requirements.
- Legal and Ethical Concerns: Using Metasploit for security testing and penetration testing activities may raise legal and ethical concerns. Users should ensure they have appropriate authorization before using Metasploit in security assessments.
Download Metasploit Framework for free onto Windows, Windows Server, macOS, RHEL, CentOS, Debian, and Ubuntu Linux. The free tool is bundled into Kali Linux. In addition, check out a free tool called Armitage if you want to use Metasploit Framework. The Armitage system provides a front end for Metasploit and creates connectivity between research and attacks.
Metasploit Pro is available for a 14-day free trial.
Network penetration testing tools FAQs
What is network penetration testing?
Ordinarily, you would expect network penetration testing to be carried out from within the network. The purpose of this exercise would be it identify methods that can be applied by hackers and intruders once they had gained access to a network. This would model the opportunities for traffic interception, lateral movement between endpoints, and the implementation of communication hijacking methods, such as ARP poisoning.
What does SAST and DAST stands for?
SAST stands for Static Application Security Testing and DAST stands for Dynamic Application Security Testing. Usually, these two types of tools are automated and would be used for the testing of Web-based systems before they are moved from development to production. However, they can also be used during the manual processes of penetration testing. SAST examines the code, while DAST runs a program and tests its results given a range of inputs. Both look for security weaknesses in modules.
Is Owasp SAST or DAST?
OWASP is the Open Web Application Security Project. It is the definitive organization for defining vulnerabilities in Web applications. OWASP defines a list of security weaknesses to look out for, which is called the OWASP Top 10. It also offers a free testing tool, called the Zed Attack Proxy (ZAP). This runs Web applications in an automated testing sequence and that action defines ZAP as a DAST.