A basic network inventory is just a list of all of the network devices that you own and operate. A network inventory should also detail important information about each device such as its make, model, and firmware version.
Here is our list of the best network inventory tools:
- Site24x7 Network Monitor EDITOR’S CHOICE A combination of network device monitoring and traffic analysis that is delivered from the cloud. You can start with a 30-day free trial.
- ManageEngine Network Configuration Manager (FREE TRIAL) This package scans the network and creates an inventory, repeating the process to keep records up to date. Runs on Windows server, Linux, and AWS. Get a 30-day free trial.
- Paessler PRTG An infrastructure monitoring service that automatically logs all equipment in an asset inventory. It installs on Windows Server.
- SolarWinds Network Configuration Manager This tool automatically discovers every device on your network and creates an asset list that is constantly updated.
- Faddom A system discovery and documentation service that creates a network inventory and map for security monitoring and capacity planning.
- Datadog Infrastructure A cloud-based IT infrastructure monitoring system that includes an inventory management service.
More sophisticated inventory management databases show the location of each device and the physical links it has to other devices. This level of detail provides all of the information needed to create a network topology map and start monitoring traffic flows as data is moved from device to device.
Network inventory management
The network inventory is the basis for network monitoring. However, network inventory management is a goal in itself. Network devices are fixed assets that need to be amortized in the company accounts. Each device has an expected service life and the cost of acquiring it is allocated to the accounts over a number of years.
The standard accounting practices of fixed asset management give the network manager an expected service life for each device. This factor needs to be recorded in the network device inventory and provides a goal for the efficient operations of the device. That is, you are expected to keep that device in service for a specified number of years, so if it breaks before it’s expected life is up, you either need to get it repaired or justify its replacement.
Inventory management can be eased through leases instead of purchases and maintenance contracts that cover the expected service life of each device. All of these contracts and expectations need to be recorded as part of network inventory management. You also need to put in place plans for replacements to existing devices. A large business can establish a supply agreement with one vendor, gaining discounts and simplifying management by having a single firmware to deal with.
Network inventory maintenance
Once you have a record of the make, model, and location of each device on your network, you are in a better position to watch over your infrastructure and keep it available and efficient.
Device security is another network inventory maintenance issue. Your network won’t be any use if a device gets crippled by inefficient settings. So, you need to optimize the configuration of each device and then ensure that no one can alter those settings. So, network device configuration management becomes an important part of network inventory management.
The best network inventory tools
When looking for the best inventory tools, we focused on those utilities that perform all inventory management tasks or do an excellent job of covering one aspect of the discipline. In all cases, you will need to be able to extract data from the utility for use by other departments and also feed data from other sources.
Our methodology for selecting network inventory software
We reviewed the market for network inventory tools and analyzed the options based on the following criteria:
- A service that can automatically discover all assets connected to the network
- Scans to gather system data from each device
- A live monitor of device statuses and availability
- Controls to prevent unauthorized changes to device settings
- Options for monitoring across a network or over the internet
- A no-cost assessment period offered by a free trial or demo system
- A service that offers value for money by giving good controls at a fair price
We kept these selection criteria in mind while looking for good network asset management systems and also made sure to include systems that run on Windows and Linux or are offered as SaaS platforms.
1. Site24x7 Network Monitor (FREE TRIAL)
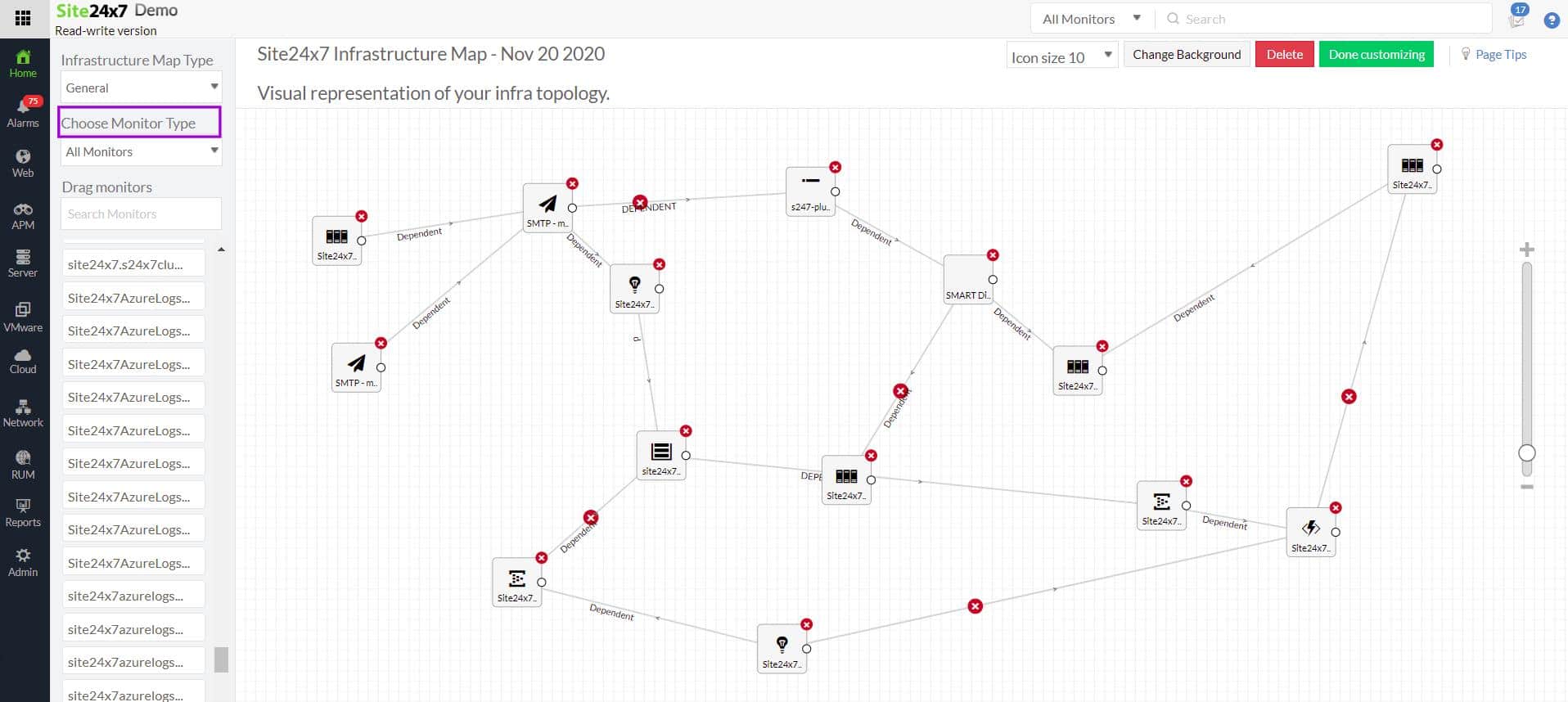
Site24x7 Network Monitor is part of a cloud platform of system monitoring tools. This network monitoring service is not offered as a standalone package but forms part of all of the Site24x7 plans. It combines network performance monitoring with traffic analysis.
Key Features:
- SaaS Platform: Includes cloud storage for statistics
- Autodiscovery: Cycles repeatedly
- Logs all Connected Devices: Creates an inventory with capacity information
- Lifecycle Management: Tracks device age and service life
Why do we recommend it?
Site24x7 Network Monitor offers both device status monitoring and traffic analysis from its cloud base. The tool starts its service by scanning with SNMP and this service continues to form the device status monitoring mechanism. The SNMP data is compiled into a network inventory and topology map.
The network performance monitoring service of this tool uses SNMP procedures to broadcast requests for status reports from network devices. All network devices are shipped with an SNMP agent pre-installed. This constantly checks the device it runs on and compiles a Management Information Base (MIB) and sends it out whenever requested.
Apart from delivering important status information, the MIBs that the Site24x7 monitor receives back in response to its request tell Site24x7 exactly what devices are out there on the network and how they connect together. The MIB contains a large amount of attribute data about each device and the Site24x7 Network Monitor extracts this to compile a network inventory.
The Site24x7 Network Monitor console includes a network topology mapper. This generates a new map of the network, based on information from the network inventory, every time that it is accessed.
If devices are added to the network, moved, or removed, the MIBs that the Network Monitor receives back will be different. It notices this and updates the network inventory accordingly. That means that the next time the Network Topology Map is accessed it will show the new layout of the network.
Who is it recommended for?
This service is suitable for businesses of all sizes. Site24x7 is a subscription service with different plans that combine the many modules on the platform. All of the packages include network monitoring functions that provide the inventory creation service. Plan prices are at a level to suit small businesses with capacity expansions for larger companies.
Pros:
- Full-Stack Monitoring Packages: Includes network, website, cloud, server, and software monitoring
- Builds Network and Application Maps: Helps to visualize how assets interact
- Rogue Device Identification: Lists all devices, revealing those that shouldn’t be there
- Network Configuration Management: Stores and restores network device settings
Cons:
- The Platform Offers Plans that Combine all of its Modules: You can’t subscribe to one module
Site24x7 offers subscription plans. These are: Website Monitoring, Site24x7 Infrastructure, Application Performance Monitor, All-in-one, and MSP. All of these are available for a 30-day free trial and they all include the network monitor. For example, you can try out Site24x7 free for 30-days and test the Network Monitor’s automatic inventory service for yourself.
EDITOR'S CHOICE
Site24x7 Network Monitor is the best network inventory tool on our list. This cloud-based service automatically discovers all the assets in your network and gathers information about them to provide comprehensive insights for your team. Also, it offers support during the entire lifecycle of the devices by tracking its age and service life and sending relevant alerts about their status changes. All this means, your team can always be on top of the components in your network. Due to these features and the ease of use, this tool is our editor’s top choice.
Download: Get a 30-day FREE trial
Official Site: https://www.site24x7.com/network-monitoring.html
OS: Cloud-based
2. ManageEngine Network Configuration Manager (FREE TRIAL)
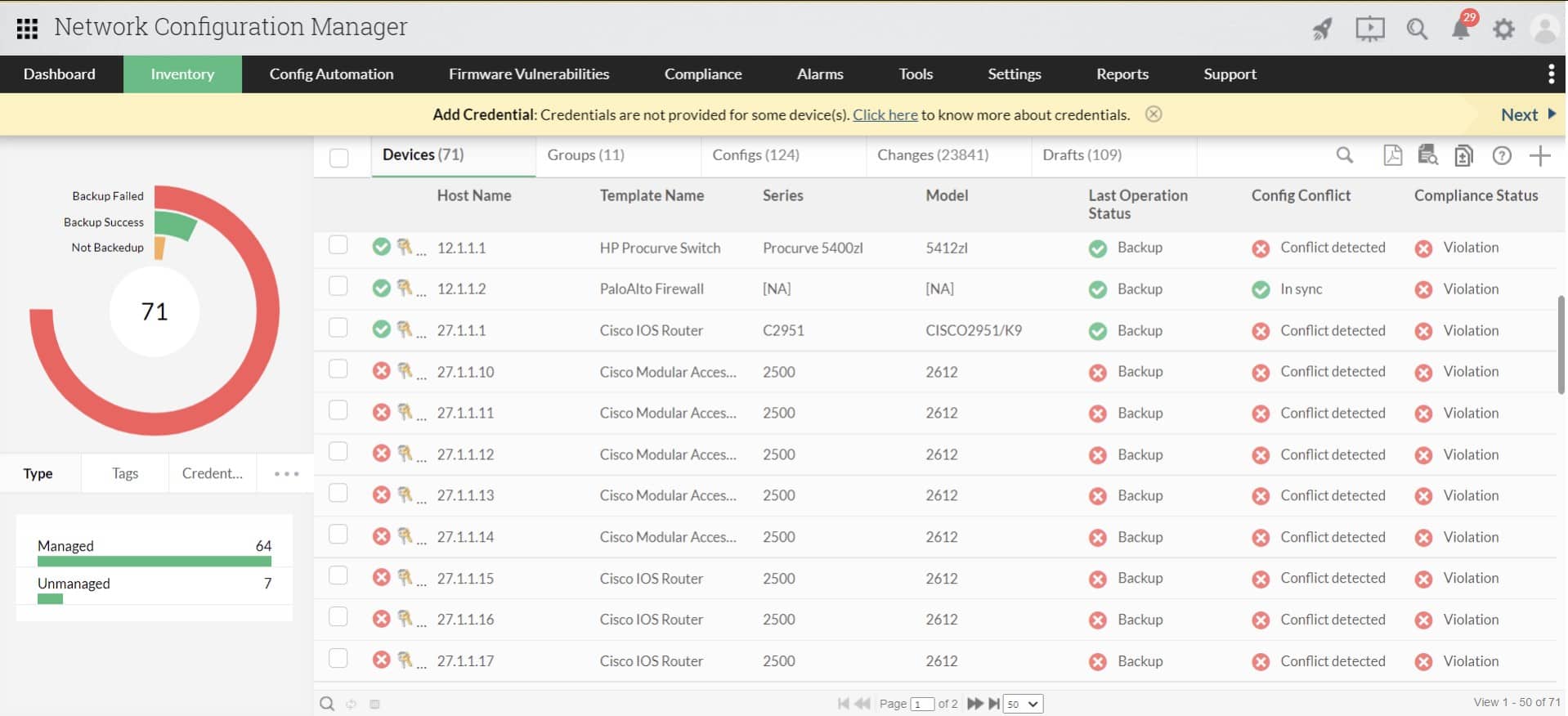
ManageEngine Network Configuration Manager includes an autodiscovery feature. This scans the network and logs each discovered device in an inventory. Each entry provides details of the hardware and it also records how the device is set up, namely which ports are in use and which device it is connected to.
Key Features:
- Autodiscovery: Creates a network device inventory
- Searchable Records: Enables examination and analysis of each device
- Backup and Restore: Repair damaged or tampered configurations
Why do we recommend it?
ManageEngine Network Configuration Manager is designed to lock down the configurations of network devices. That involves storing an image of each device’s configuration in a library and then checking for any changes. If any are made, the system reapplies the stored settings. The tool also generates a list of devices and their details.
The discovery service repeats constantly. This process enables the inventory to be kept up to date. The service takes an image of each configuration and stores it. If a change is detected on the next sweep, the Network Configuration Manager will restore the official settings. This process can be turned off temporarily to allow an administrator to update settings.
The configuration of a switch or router includes detailed security settings, such as the password for privileged access and the encryption scheme to protect it. There are many other features that are held in the configuration, such as access control lists (ACLs), which provide blocks on certain routes and define zones of trust. If a hacker can get to these features, the security measures implemented on the network will be compromised.
Any network device’s operating system provides a backup option that can export an image of the device’s settings and store it. It is also possible to import and apply a stored image at the device’s command line. So, the Network Configuration Manager automates the backup tasks that a network administrator would probably perform anyway. However, the constant checking for unauthorized changes is an important security service that no network manager would have time to perform with such frequency and accuracy.
Who is it recommended for?
This tool is a great time saver for any network manager. However, the larger the network, the more benefits the company will get from this system. So, the system would be particularly useful for a large company. ManageEngine offers a Free edition of the package but that is limited to managing two devices.
Pros:
- Constantly Updates a Network Inventory: The discovery process repeats
- Backup Library: Provides a store for network configuration images
- Network Compliance Management: Blocks intruders
Cons:
- Free Edition Only Manages Two Devices: The smallest paid package covers 10 devices
The software for the Network Configuration Manager installs on Windows Server or Linux. You can opt to get it as a service on AWS Marketplace. ManageEngine offers the system on a 30-day free trial.
3. Paessler PRTG
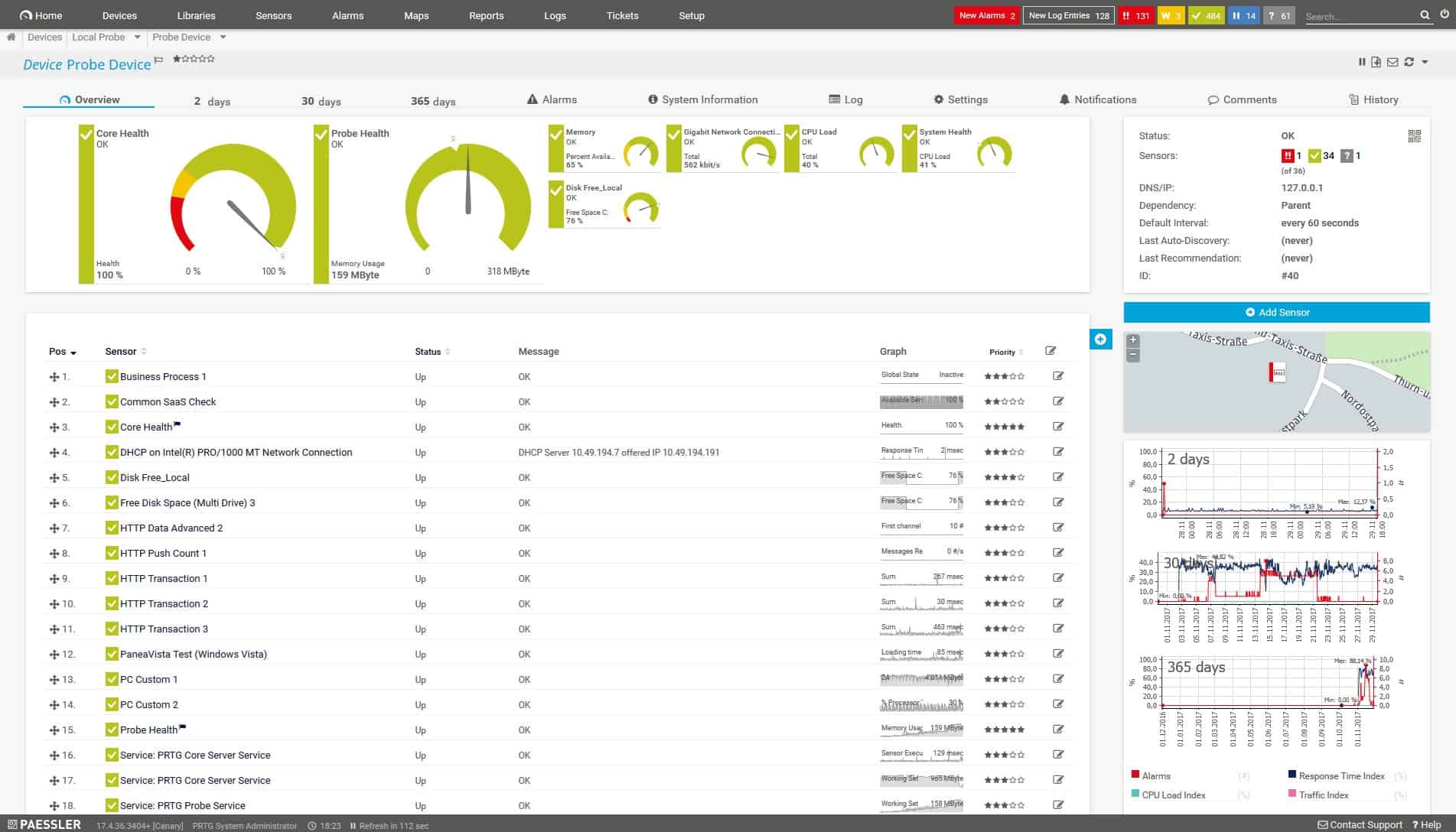
Paessler PRTG is a complete infrastructure monitoring tool because it covers networks, servers, and applications. The system includes an autodiscovery tool, which creates a network inventory of all devices currently active on the network.
Key Features:
- Full-Stack Observability: Monitors network servers, and applications
- Includes a Constant Autodiscovery Service: Creates a network inventory and map
- Tracks Device Performance: Uses the Simple Network Management Protocol
Why do we recommend it?
Paessler PRTG is a flexible package that allows each buyer to decide which functions to activate. The more monitors you turn on, the more you pay for the package. However, there is a core service that all customers get and that is the network discovery and inventory creation facility.
PRTG uses the network inventory as the basis for a network topology diagram. This service is dynamic, as is the asset logging routine. Both the network inventory and topology map get updated automatically when any infrastructure changes occur.
One big weakness in the PRTG system is that is purely a monitoring system and does not include network management functions, such as configuration management.
The dashboard of PRTG is customizable, so each network manager can collect all asset information that is important on one screen. The tool is able to track devices over several sites, enabling the centralization of asset management.
Who is it recommended for?
Each buyer pays for an allowance of sensors. You calculate how many of the systems in the bundle you need and pay accordingly. Small businesses that only activate 100 sensors never have to pay for the package. Host the software on Windows Server or access it as a SaaS platform.
Pros:
- Multiple Monitoring Methods: A combination of packet sniffing, WMI, and SNMP
- Constantly Updated System Documentation: SNMP polling repeats
- Performance Alerts: Sent as notifications by SMS, email, and Slack
Cons:
- No Version for Linux: Available for Windows Server or as a SaaS platform
PRTG installs on Windows Server and Paessler makes it available on a 30-day free trial.
4. SolarWinds Network Configuration Manager
SolarWinds produces a number of monitoring tools that create a network inventory. However, the Network Configuration Manager provides the most comprehensive inventory management functions of the entire SolarWinds’ stable.
Key Features:
- Automatic Device Discovery: Generates a device inventory
- Takes an Image of Device Settings: A snapshot of all the configuration
- Provides an Interface to Create a Standard Configuration: Create a standard for each device make and model
Why do we recommend it?
SolarWinds Network Configuration Manager identifies all network devices and then logs them in an inventory. The service manages device settings. It locks down the configuration by taking an image to store as a backup. The tool scans all devices and reapplies the authorized settings if unexpected changes are detected.
The Network Configuration Manager includes an autodiscovery feature. This searches the network for all connected devices and logs them into a database. This gives you the network inventory that you need.
The network configuration manager is particularly needed to standardize the settings of all network devices, so the creation of the device inventory is just the first phase of this tool’s activities. The autodiscovery function is not a one-off task because the process runs recursively and will spot and document any changes in the network’s infrastructure.
A big security feature of the Network Configuration Manager is that it keeps track of each device and spots changes to its settings. When this occurs, the tool immediately restores the authorized settings. Reasons for unexpected changes are accidental alterations or hacker activity that seeks to weaken the defenses of the network. The Network Configuration Manager raises an alert whenever an unauthorized change occurs. This allows the network manager to investigate the source of the alteration and launch a search for an intruder.
Reports from the Network Configuration Manager help you to keep other departments, such as the company accountant, informed of the asset inventory. These reports can extract data in a digital format and also in a CSV layout that is easy to import into a spreadsheet.
Details recorded in the inventory include the device’s physical location and its connections through to other devices. Service life expectancy can be loaded into the Network Configuration Manager, which takes care of all of the capacity planning and inventory tracking tasks of a network manager.
Who is it recommended for?
This tool is important for large networks. The configurations of switches and routers are used by security software to protect the network and so one trick that intruders perform is to try to get into those settings and change them in their favor. Large networks with many devices cannot be supervised manually.
Pros:
- Features Designed to Streamline Troubleshooting: Improves TTR and overall productivity
- Automatically Discovers New Devices on the Network: Scans each new device and produces a health report
- Configuration Management: Quickly backs up and restores changes that may have impacted performance
Cons:
- Only Available for Windows Server: No version for Linux
SolarWinds builds its key tools on a common platform, called Orion. This makes the interaction between modules much easier. The software installs on Windows Server and SolarWinds offers the Network Configuration Manager for a 30-day free trial.
5. Faddom

Faddom is an IT asset management system for networks and applications. The network discovery process repeats continuously and thus forms a security service, spotting rogue devices.
Key Features:
- Network discovery: System documentation, including a network map
- Rogue device detection Provides security scanning
- Network capacity planning: Supports network expansion
- Intruder detection: Identifies unusual network activity
- Segmentation support: Plan zones of trust
Why do we recommend it?
Faddom provides a network inventory in the form of a network map. The map shows the capacity of each link and identifiers for each network device. The map is created from a discovery routine. This repeats and updates the map if it discovers any changes to the network layout.
The system provides details of each device and can also assist with addressing issues, such as subnetting. The package is useful for implementing segmentation, which enables network security to be enhanced through the creation of zones of trust.
The Faddom package also provides an application discovery service. This process creates an application dependency map. This shows the relationships between software and also between software and server resources. The package can be used for server capacity planning. Another benefit of this system is that it can be used to plan for cloud migration.
Who is it recommended for?
Faddom is an on-premises software package and it is suitable for large organizations. The platform is available in three plan levels with the first providing discovery and documentation. The top two plans also provide security features with the top edition being a custom service.
Pros:
- Application discovery: scans servers and lists running processes
- Generates an application dependency map: detects the links between software packages
- Server capacity planning: Estimates resource requirements
- Cloud migration planning: Identifies which software packages need to be ported together
- On-premises package: Alternatively, it is available as a service on AWS
Cons:
- No SaaS package: You have to host it yourself
Faddom is an on-premises software package but it is also available as a service on AWS. On your site, the system runs on a VM, which is provided with the software. Faddom is available for a free trial.
6. Datadog Infrastructure
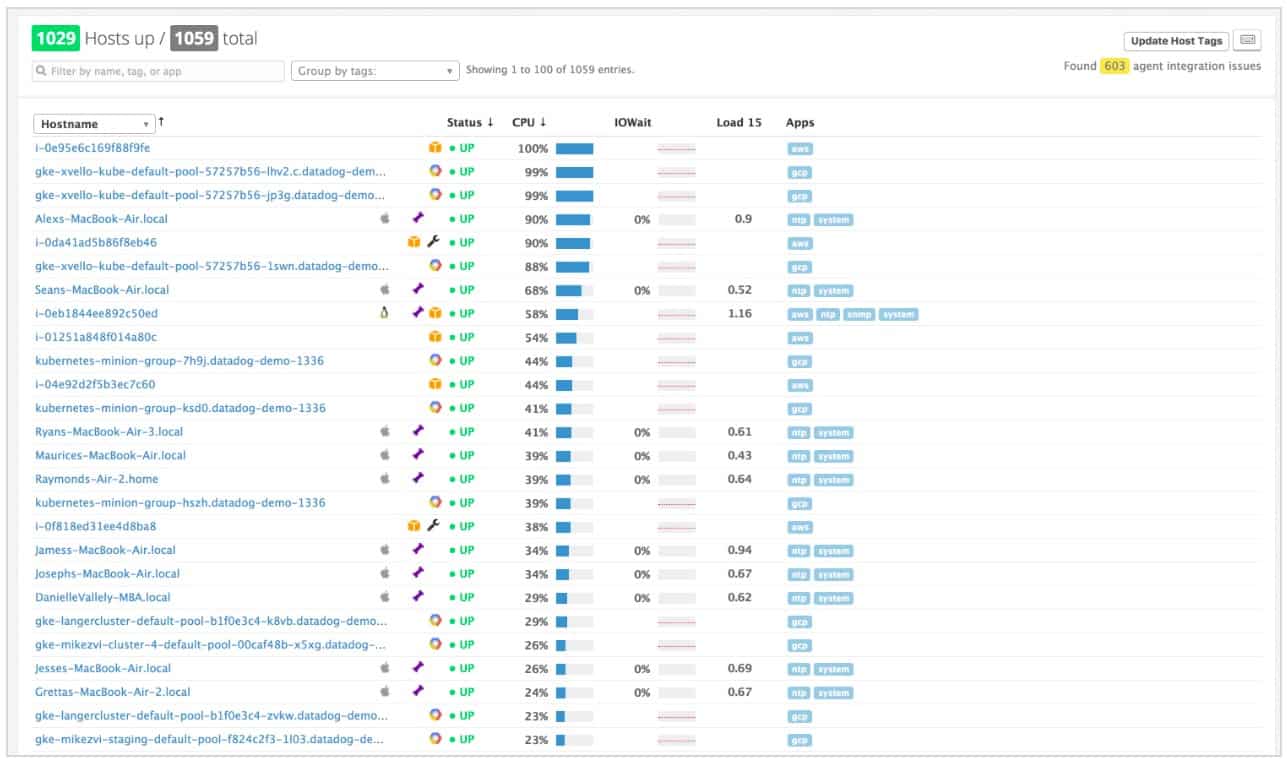
Datadog is a cloud-based IT support service that includes monitoring and management modules for networks, servers, and applications. The Datadog Infrastructure service watches over all of the physical assets run by an IT department.
Key Features:
- Discovers Devices: Creates a network inventory and map
- Hybrid Monitoring: Covers networks and cloud services
- Plugins: The system is expandable to monitor specific technologies
Why do we recommend it?
Datadog Infrastructure is a module on the Datadog cloud platform. You pay for each module individually, however, to get full network discovery, inventory creation and mapping, you need to combine this tool with the Network Performance Monitoring service. Both the Network Device Monitoring and the Network Performance Monitoring packages require a subscription to the Infrastructure plan.
As it is a remote-based service, Datadog isn’t limited to one location and can unify the management of infrastructure on many sites. The system requires an agent to be installed on each site for network monitoring. This agent will detect all network devices and other equipment connected to the network and create an asset inventory from those discoveries. The inventory is updated automatically and it also provides the basis for a network topology map.
Who is it recommended for?
Datadog provides a Free edition of the Infrastructure plan for up to five hosts but no free option for either of the Network Monitoring units. However, both of those network plans are affordable for small businesses. Larger businesses can scale up to either of the two paid plans of Datadog Infrastructure. The network monitoring plans are priced per device.
Pros:
- Cloud-Based SaaS Product: Allows monitoring with no server deployments or onboarding costs
- Web-Based Console: Can be accessed through any standard Web browser
- Live Device Status Monitoring: Uses SNMP
Cons:
- Free Trial Lasts 14 days: Would like to see a longer trial period for testing
Datadog Infrastructure is a subscription service and is charged per host per month. There is a Free version of the system and two paid plans called Pro and Enterprise. The paid services include more features than the free versions, although all versions include network discovery. You can get a 14-day free trial of the Pro and Enterprise plans.
Choosing a network inventory tool
You need to get a list of all the devices running your network, you need to know what each is, who supplied it and what firmware version it has. You also need to make sure it is optimized and secure and you need to plan for its replacement at the end of its service life.
There are very few tools available that cover every aspect of network inventory management. You might choose to use several tools to get the best service for each aspect of inventory management. The task certainly requires input from other departments, such as accounting and purchasing managers in your business.
Network inventory tools FAQs
What are the two common tools to create a hardware inventories?
Hardware inventories can be created manually or automatically. If you are running the IT services of a small business, you will probably be more likely to keep a manual hardware inventory, which can be held in any tool, such as a spreadsheet or an Access database. Although this sounds like an unsophisticated route, it has the advantage of making the system administrator walk around the office and check out each device. Large businesses are to spread out for such a tour, so they need to use automated tools. These are often built into network monitoring systems and they scan the network, compiling a network inventory from the responses that they get from SNMP requests. These tools usually also provide network topology maps.
What is network inventory system?
A network inventory system stores a list of all of the devices that you have connected to your network. In some cases, this might only list the network devices, such as switches, routers, and hardware firewalls. However, some network inventory systems will also list endpoints. The asset inventory should detail the make and model of the device and also the age of the device and its operating system with a version number. The information in the asset inventory will form the basis for status monitoring and will also help the company accountant to calculate depreciation.
What are two benefits of network inventory management?
The two main benefits of a network inventory management system for a system administrator are that it forms the basis for monitoring and also enables capacity planning. It is impossible to monitor your network without first finding out what devices you have running the network. It is also impossible to know what devices are available for users and what capacity of traffic your network can rise to without examining the details of each device.