A network firewall is a critical security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Positioned at the perimeter of a network or within an internal network, firewalls act as a barrier between trusted internal networks and untrusted external networks like the Internet.
Firewalls come in various forms, including hardware-based appliances, software solutions, or a combination of both, and they are essential in ensuring the security of digital communication. They inspect packets of data and allow or block them based on criteria such as IP addresses, port numbers, protocols, and the contents of the data packet itself.
Network firewalls use various methods of filtering traffic, such as packet filtering, stateful inspection, and deep packet inspection (DPI). Packet filtering looks at headers of data packets to decide whether to allow or block traffic, while stateful inspection keeps track of the state of active connections to make more informed decisions.
DPI goes a step further by examining the content of packets to detect malicious activity. By filtering out harmful traffic, firewalls prevent unauthorized access to sensitive systems and data, providing a critical first line of defense against cyber threats.
Why Does a Company Need a Network Firewall?
A network firewall is an essential security tool for any organization, as it helps protect the network from unauthorized access and malicious activities. With increasing cyber threats such as hacking, data breaches, and denial-of-service (DoS) attacks, businesses need to secure their digital infrastructure from external and internal threats. A properly configured firewall acts as a gatekeeper, filtering out harmful traffic while allowing legitimate communication to pass through.
Firewalls protect against a variety of attacks, including cybercriminals attempting unauthorized access to sensitive systems, malware infections, and DoS attacks designed to overload network resources. They also help prevent unauthorized data exfiltration by blocking certain types of outbound traffic.
Firewalls can be configured to enforce access control policies, ensuring that only authorized users and devices can access specific parts of the network. By blocking harmful traffic, such as virus-laden emails, malicious websites, and botnet traffic, firewalls serve as an effective deterrent against a wide range of network-based threats. Cybercrime continues to rise, so having a firewall in place is vital to ensure business continuity and safeguard data, systems, and reputations from devastating attacks.
How does a firewall protect a network?
Corporations often have very complex firewalls in place to protect their large networks. On the inbound side, firewalls can be programmed to prevent certain IP addresses outside the network from accessing computers inside the network or prevent access to prohibited websites and web applications. On the outbound side, the firewall configuration can be done in a way that prevents employees from sending sensitive data or certain types of emails outside of the network.
When your computer has firewall protection enabled, everything that goes in and out of it is monitored. Firewalls carefully analyze and filter incoming and outgoing traffic at the entry and exit points based on predefined rules to keep the network protected from malicious traffic. The firewall allows traffic it deems legitimate but blocks the ones it deems malicious from gaining access to the network. Now you may be wondering, “how does the firewall know what traffic is legitimate or malicious?” The firewall has an Access Control List (ACL) which sets up some guidelines that allow or prevent access to a specific computer or network. This list can be customized to suit the needs of any computer, network, or organization. Modern firewalls also carry out deep packet inspection to further analyze the traffic contained in each packet and data stream.
Firewalls use one or a combination of the following three key technologies to control traffic flowing in and out of the network:
- Packet filtering Packets that make it through the filtering systems are forwarded to the requesting network device, and those that don’t make it are discarded.
- Proxy service Acts as an intermediary between a trusted and untrusted network to inspect and intercept traffic going in and out of the network.
- Stateful inspection Keeps track of the state of network connections passing through it and constantly checks if they are valid. If the comparison yields a positive match the information is allowed through, otherwise, it is denied.
Although various firewall products can provide a mix of these technologies and work at different layers of the OSI model, it is important you understand the basic definitions and functionalities of these firewall technologies and types. We will now discuss them in detail in the following text.
Related post: OSI Model Explained
What are the different types of firewalls?
There are many different types of firewalls available for diverse environments, requirements, and security goals. The following sections describe the various types of firewalls in use today:
1. Packet filtering (stateless inspection)
Packet filtering is a first-generation firewall technology that operates on the network layer of the OSI model and makes access decisions based on network-level protocol header values. The packet-filtering firewall is configured with ACLs, which dictate the type of traffic that is allowed into and out of specific networks. When a packet passes through a packet-filtering firewall, its source and destination address, protocol, and destination port number are inspected. Any packet that does not comply with the firewall set rules is automatically dropped.
The ACL filtering rules are enforced at the network interface of the device, which is the doorway into or out of a network. Packet filtering is also known as stateless inspection because the device does not understand the context that the packets are working with; rather, it makes decisions based on the data contained in that individual packet.
The advantages to using packet filtering firewalls are that they are scalable, application-independent, and have high performance because they do not carry out extensive processing on the packets. They are commonly used as the first line of defense to weed off malicious or unwelcomed network traffic for a specific network.
However, the lack of sophistication in packet filtering means that an organization should not solely depend upon this type of firewall to protect its network infrastructure. In addition, packet-filtering firewalls are vulnerable to IP spoofing and packet fragmentation attacks and have largely been replaced by stateful inspection firewalls.
2. Proxy firewalls
A proxy firewall is a second-generation firewall technology that acts as an intermediary server. Proxy firewalls stand between a trusted and untrusted network and make each filtering decision on the basis of a single packet. There is no way to refer to past packets to make current decisions. It inspects and intercepts traffic entering or leaving a network for malicious content, and when it figures out that the traffic is safe, it passes it on to the intended recipients. A proxy firewall ensures that there is no direct connection between the two communicating devices.
Suppose you need to board an airplane that will take you on a trip to another city; you couldn’t just walk into the airport and head straight to board the airplane. Instead, you would have to go through the “check-in” process in order to make sure that you and your luggage is thoroughly inspected to ensure nothing dangerous finds its way in. This is what a proxy firewall does.
A proxy firewall can work at different layers of a network stack. A proxy-based firewall that works at the session layer of the OSI model is referred to as a circuit-level proxy—access decisions are based on available protocol header and session information—no deep-packet inspection. A proxy-based firewall that works at the application layer is called an application-level proxy—access decisions are based on deep-packet inspection.
There’s also another kind of proxy-based firewall system that is even faster than application layer proxy firewalls. It is called a kernel proxy firewall. A kernel proxy firewall function on the application layer to analyze packets through a virtual network. When a packet arrives at a kernel proxy firewall, a new virtual network stack is created to examine the packet. Because it solely relies on the processing power of the kernel, information is processed faster.
3. Stateful firewalls
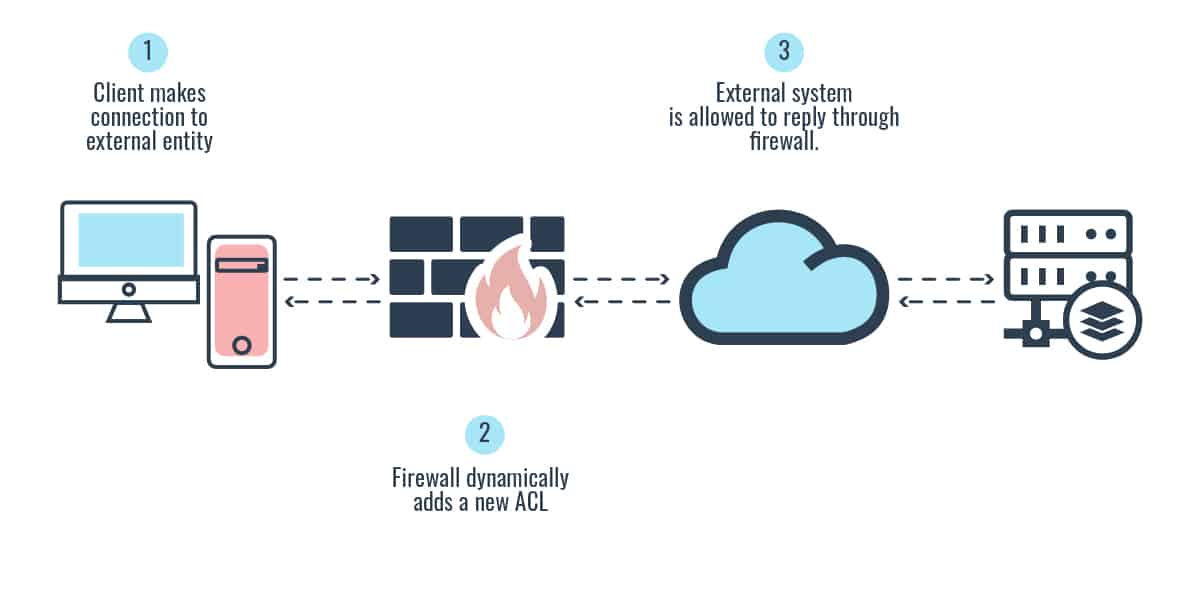
Stateful firewall is a third-generation firewall technology that monitors incoming and outgoing packets over the long term. Stateful firewalls have a state table that allows the firewall to compare current packets to previous ones. It remembers and keeps track of the whereabouts of packets until each particular connection is closed. When new packets arrive, it compares information in the packet header to the state table and determines whether the packet is part of an established connection. If it is, the packet is let through without further analysis. If the packet does not match an existing connection, it is evaluated according to the rule set for new connections.
A stateful firewall is like a security guard that likes to listen in on the conversations of people in the neighborhood. He keeps track of almost everyone, including suspicious and anomalous movements in and around the neighborhood. Because the security guard knows virtually everything going on in the neighborhood, he’s in the best position to know and detect when something unusual happens. Stateful firewalls are slower than packet filters but are far more secure.
4. Next-Generation Firewalls (NGFW) and UTM
Next-Generation Firewalls (NGFW) combine the functions of a traditional firewall (packet filtering, stateful inspection, NAT, etc) with other network security functions such as an application firewall using in-line deep packet inspection (DPI), intrusion prevention system (IPS), and a host of others.
NGFW emerged as a response to enterprises that wanted to combine traditional port and protocol filtering with IDS/IPS functionality and the ability to detect application-layer traffic; over time they added more features like deep-packet inspection and malware detection. The goal of NGFW is to include more layers of the OSI model and improve the filtering of network traffic that is dependent on the packet contents. NGFWs perform even deeper inspection than stateful firewalls, and offer administrators a deeper awareness and control over individual applications.
Unified Threat Management (UTM) firewalls are similar to NGFW in terms of the underlying technology. However, UTM addresses a different market—small and midsize businesses. UTM firewalls incorporate much more security functionalities such as gateway anti-virus, business VPN, DLP, anti-spam, and web content filtering, including cloud management features. UTM are typically rated with lower firewall throughput and management capabilities than their NGFW counterparts, as such, they are tailored mostly to SMBs.
5. Virtualized firewall
A virtual firewall is basically a virtual appliance deployed in a private cloud (VMware ESXi, Microsoft Hyper-V, KVM) or public cloud (AWS, Azure, Google, Oracle) to monitor and protect traffic in virtual infrastructure environments.
A virtual firewall is necessitated by the need to protect today’s fluid network perimeter that extends to the cloud—SaaS, IaaS, and PaaS-based infrastructure, with many points of entry. There is also an increasing number of devices that fall under categories such as BYOD and remote access workers that will continue to grow internal to the network.
The popularity of these modern fluid infrastructures brings to bear the inadequacies of the traditional fixed perimeter firewall model. In fact, the future of network security is gradually moving towards Software-Defined Perimeter (SDP) and Zero Trust Network Access (ZTNA) technology. A virtual firewall is often a key component in a Software-Defined Perimeter (SDP).
| Firewall Type | OSI Layer | Characteristics | Advantages | Disadvantages |
|---|---|---|---|---|
| Packet Filtering | Network Layer | Looks at destination and source addresses, ports, and services requested | High performance, scalable and application independent | Vulnerable to spoofing and fragmentation attacks |
| Stateful Firewall | Network Layer | Looks at the state and context of packets. Keeps track of each conversation using a state table | More secure; can block DOS attacks and protocol vulnerability exploitation | High processing overhead makes it slower |
| Circuit-Level Proxy | Session Layer | Looks only at the header packet information | Relatively inexpensive | Not ideal for content filtering |
| Application-Level Proxy | Application Layer | Looks deep into packets and makes granular access control decisions | Can detect and block attacks not visible at Layer 3 and Layer 4 | Creates performance issues. Not ideal for high-bandwidth applications |
| Kernel Proxy | Application Layer | One network stack is created for each packet | Information is processed faster | Not compatible with all network protocols |
| NGFW and UTM | Multiple OSI layers | Incorporates multiple security functions, and targets two distinct markets | Ease of management from a central point. Deeper packet inspection | Single point of failure. Experts required. It may not need all the functionality |
| Virtual Firewall | Multiple OSI layers | Virtual appliance | Ease of mgt. and lower TCO | Relatively low firewall throughput rating. Internet bandwidth dependent |
Table 1.0 Comparison of different types of firewalls
Network firewall architecture designs
Firewalls can be placed at different areas on a network depending on the security threat that needs to be addressed. Firewall network designs have evolved over the years, from the old-fashioned flat designs such as dual-homed host and screened host, to the modern layered designs such as the screened subnet. The following are some of the commonly used firewall architecture:
Bastion host architecture
A bastion host is any Internet-facing host (it does not have to be a firewall) that is not protected by another device (such as a firewall). A system is considered a bastion host if it is highly exposed, and is most likely to be targeted by attackers. Bastion hosts must be hardened enough to withstand attack.
Dual-homed host architecture
A dual-homed host has two network interfaces (NIC). One interface is connected to a trusted network (LAN), and the other connected to an untrusted network (Internet). For this setup to be effective, you must disable a computer’s forwarding and routing functionality so the two networks are truly segregated. Most modern network firewalls today are multihomed—having several NICs that connect to different networks. Multihomed devices are commonly used to host firewall software applications.
Screened host architecture
Screened host firewall architecture is an older flat network design using one router to filter (screen via ACL) traffic before it is passed to the firewall. In a network with only a screened host, a failure of the firewall puts the entire trusted network at risk. if an attacker successfully breaks through the firewall, nothing else prevents the attacker from gaining full access to the LAN. Screened subnet architecture evolved to mitigate this risk.
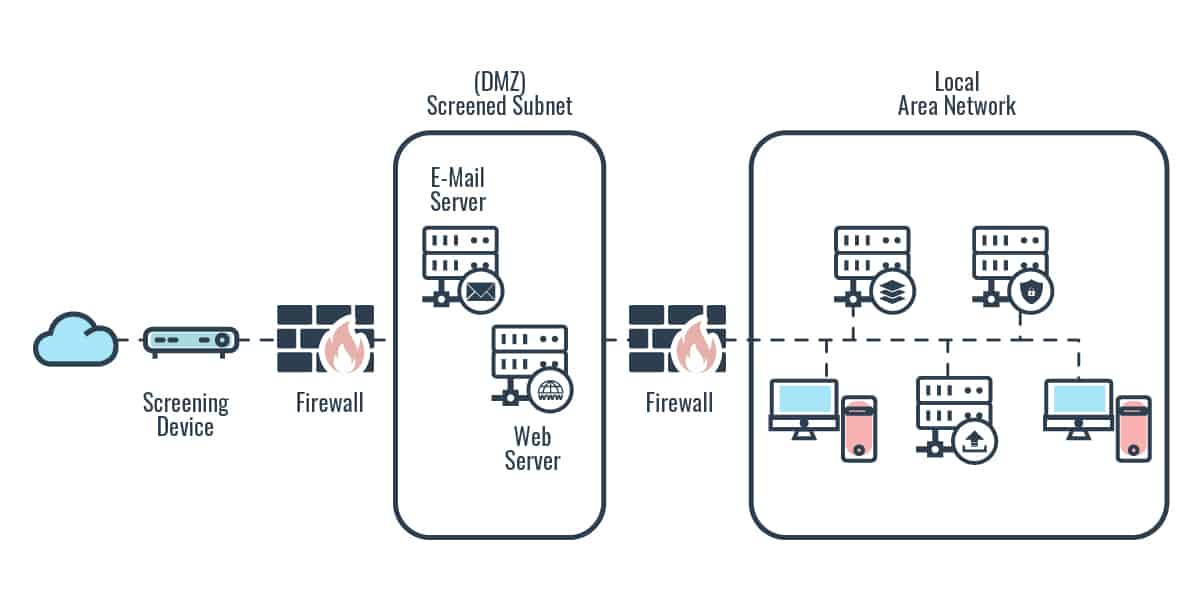
DMZ networks and screened subnet architecture
A screened-subnet architecture adds another layer of security to the screened-host architecture. An external router filters (screens) traffic before it enters the subnet. Traffic headed toward the internal network then goes through two firewalls. The use of these two firewalls creates a DMZ. The exterior firewall screens the traffic entering the DMZ network, while the interior firewall filters the traffic going to the internal network. In an environment using a screened subnet, an attacker would have to break through two firewalls to gain access.

Choosing the right firewall for your business
Before you set out to procure a network firewall for your business, you first need to be clear about your network security strategy and policy and highlight your specific security concerns. When evaluating a network firewall product, you need to ensure that the underlying technology and the device’s different functionalities address your security risks and policy requirements.
With such a huge range of firewall products and appliances available, choosing the right one for your business and budget can be challenging. You don’t want to get caught up in the sales and marketing hype that tends to surround most security products. Like most network security solutions, not all firewall solutions are created equal. What fits perfectly from a price, feature, and functionality standpoint for one organization may not fit for another.
There are key questions you need to consider, such as: What security problem are you trying to solve? Is a particular type of firewall right for your organization? What security features are most important? Do you require the firewall to support geographically dispersed branch locations and remote workers? What is the infrastructure bandwidth for your environment, and how many users, devices and networks does the organization need to support today and in the future? Is it easy to deploy, manage and maintain? Other factors to consider include performance, scalability, vendor support, and of course, cost.
For most small businesses with little or no in-house firewall expertise, it makes sense to consider a cloud-based firewall solution that can protect every device on the network. If you are concerned with data leaving your network in addition to other inbound security threats, consider investing in a two-way firewall instead of a one-way firewall. If you cannot tolerate low performance or processing slowdowns, you may want to consider an on-premises vs cloud-based firewall. A company that deals with sensitive information, such as health care or financial data, should invest in the best NGFW or UTM solution depending on the size of the network. For those that are mostly concerned with the security of their fluid or virtual network infrastructure; consider investing in virtual firewalls, or cloud-based NGFW or UTM solutions.
We’re here to make the decision-making process much easier. As a starting point, we’ve selected the best network firewall security software and hardware firewall options for small businesses. If you’re just looking for a quick list, below’s a brief rundown of our top picks:
Here is the list of our top picks for the best network firewall security software for small businesses:
- CrowdStrike Falcon Firewall Management The Falcon suite of cybersecurity services includes endpoint protection as well as a firewall protection system.
- Zscaler Cloud Firewall Cloud-based next-generation firewall that has SSL inspection, granular firewall policies, and real-time monitoring.
- Barracuda CloudGen Firewall Cloud-based firewall that can detect zero-day threats, with network activity monitoring and VPN load balancing.
- SolarWinds Security Event Manager A SIEM solution with real-time firewall management and automated change management.
- GFI Languard Kerio Control Network firewall with an Intrusion Prevention System, deep packet inspection, configurable traffic policies, and usage reports.
- pFSense Open-source firewall that can be installed on any hardware and comes with a web-based GUI with add-ons.
- IPFire Open-source firewall with an Intrusion Prevention System, alerts, Stateful Packet Inspection, and add-ons.
- SophosXG Firewall Next-generation firewall with a dashboard, automatic threat response, sandboxing, and SSL inspection.
Here is the list of our top picks for the best network firewall security hardware for small and mid-size businesses:
- SonicWall TZ400 Security Firewall A customizable, versatile solution for small businesses with possible expansion goals.
- Ubiquiti UniFi Security Gateway This budget option is easy to install and manage.
- WatchGuard Firebox T35 Ideal for businesses with up to 20 employees, the T35 comes with optional built-in wifi.
- Protectli Vault – 4 Port A robust firewall hardware for use with open source firewall distributions.
- Cisco Meraki MX68 This all-in-one router and firewall is backed by advanced cloud-managed security.
- Sophos XG 86 A next-generation firewall with optional wifi and centralized management.
Firewall FAQs
What kind of network traffic can you filter with the Windows Firewall with Advanced Security?
The Advanced Security feature on Windows Firewall allows you to filter application traffic. This includes system services. The settings allow specific types of activity in the nominated applications to be distinguished, so some of that traffic will still get through.
Why is it important that a firewall provide a centralized security checkpoint for a network?
A centralized security checkpoint, provided by a firewall, is important because it removes the need for automated security software, such as a SIEM, or a network administrator to monitor many different locations in order to enforce security policies.
In a typical firewall configuration, what is the central host in an organization’s network security?
Although you might have many hosts behind your firewall, the central host for network security is called a “Bastion.” The bastion host act as a dense wall and can form part of the firewall. Its purpose is to be resistant to attack.




