Multi-factor authentication (MFA) is one of the most effective ways to secure online accounts and systems against unauthorized access. By requiring multiple forms of verification, MFA significantly reduces the risk of data breaches and cyberattacks, even if a user’s password is compromised. As cybersecurity threats become more sophisticated, implementing MFA has become a critical step for organizations aiming to safeguard sensitive data, comply with regulations, and enhance overall security.
Here is our list of the best multi-factor authentication tools:
- ManageEngine ADSelfService Plus EDITOR’S CHOICE This package is designed to reduce the volume of calls to Help Desk support technicians and includes facilities to implement single sign-on and multi-factor authentication. This is a software package for Windows Server. Get a 30-day free trial.
- LastPass (FREE TRIAL) A cloud-based service that distributes user passwords or shared credentials confidentially, reaching out across multiple devices per user. Get a 14-day free trial.
- Auth0 This cloud-based system is able to manage a single sign-on system for cloud-based applications, focusing on application-level protection.
- OneLogin A cloud-based authentication service that operates like a combined VPN and ARMand limits the visibility of applications to authorized users.
- Authy This package includes cloud backup space as well as user-centered authentication that uses mobile devices for multi-factor authentication.
- RSA SecurID A multi-factor authentication solution that includes the option for a physical device to provide an access code.
- Okta The leading single sign-on brand that includes a multi-factor authentication service.
- Google Authenticator A free user app for Android that provides a seamless authentication method for multiple, unrelated applications.
This guide explains the best tools available for implementing MFA across an organization. The guide outlines the importance of MFA in today’s security landscape, explaining how it adds an additional layer of protection by requiring users to provide multiple forms of identification. This can be something they know (password), something they have (a smartphone or token), or something they are (biometric data). This multi-layered approach ensures that even if one factor is compromised, unauthorized access is still blocked.
The guide reviews and compares various MFA tools, highlighting features such as ease of integration, user experience, cost-effectiveness, and support for a variety of authentication methods, including SMS-based, app-based, and hardware token-based MFA. It also examines how these tools can be used in conjunction with existing identity management systems like Active Directory or LDAP.
We provide insights into best practices for implementing MFA, such as enforcing MFA for critical applications, selecting appropriate authentication methods based on user needs, and ensuring scalability to accommodate growing user bases.
By leveraging the MFA solutions discussed in this guide, businesses can strengthen their security posture, reduce the likelihood of account takeovers, and ensure compliance with regulatory standards that mandate strong access controls.
What are the different methods of multi-factor authentication?
Multi-factor authentication (MFA) employs several methods to verify a user’s identity, enhancing security. The most common methods include:
- Something you know This method involves knowledge-based authentication, typically using passwords or PINs. While familiar and easy to implement, these are vulnerable to attacks like phishing and brute force. For example, many online banking systems require users to enter a password before accessing their accounts. Despite its common usage, relying solely on something you know is not sufficient for robust security.
- Something you have This method uses physical devices such as smartphones, hardware tokens, or smart cards. These devices often generate time-based one-time passwords (TOTP) or receive push notifications for access approval. For instance, Google Authenticator generates a TOTP that users must enter along with their password to access their Google accounts. This method adds a layer of security by requiring possession of a physical device.
- Something you are Biometric verification methods include fingerprint scanning, facial recognition, and iris scanning. These are highly secure as they rely on unique biological characteristics. A common example is Apple’s Face ID, which uses facial recognition to unlock iPhones and authenticate purchases. Biometrics are hard to replicate, making them a reliable method for securing sensitive information.
- Somewhere you are Geographic location-based authentication uses the user’s location, determined by GPS or IP address. Access can be restricted or granted based on specific locations. For example, some corporate networks only allow access to employees within the office premises. This method helps prevent unauthorized access from remote locations.
- Something you do Behavioral biometrics analyze unique patterns in the user’s interactions with devices, such as typing rhythms or mouse movements. For instance, some advanced security systems monitor keystroke dynamics to verify the user’s identity continuously. This method is gaining traction for its ability to provide ongoing authentication without interrupting the user experience.
How to pick an MFA tool for your organization
Choosing the right multi-factor authentication (MFA) tool for your organization is critical to ensuring robust security without compromising user experience.
Consider the following factors when selecting an MFA tool:
- Compatibility Ensure the MFA tool integrates seamlessly with your existing systems and applications. Compatibility with various platforms such as Windows, macOS, iOS, and Android, as well as with critical applications like email, VPNs, and cloud services is essential. An MFA solution that fits well into your current infrastructure minimizes disruptions and streamlines the implementation process.
- Usability The MFA tool should be user-friendly and not overly cumbersome for employees. Look for solutions that offer intuitive interfaces and straightforward setup processes. For instance, tools that support biometric authentication or push notifications can enhance user convenience while maintaining security. Ensuring a positive user experience is crucial for high adoption rates.
- Security features Evaluate the MFA tool’s security features. These include support for multiple authentication methods such as TOTP, biometrics, and smart cards, compliance with industry standards, and robust encryption protocols. Additionally, consider tools that provide continuous monitoring and threat detection capabilities to stay ahead of emerging security threats.
- Scalability Choose an MFA solution that can scale with your organization’s growth. Whether you are a small business or a large enterprise, the tool should support an increasing number of users and devices without compromising performance or security. A scalable solution ensures long-term viability as your organization expands.
- Cost Assess the total cost of ownership, including licensing fees, implementation costs, and ongoing maintenance. Compare different vendors to find a solution that offers the best value for your budget without sacrificing essential features. Balancing cost and functionality is key to making a smart investment in security.
- Support and maintenance Reliable customer support and regular updates are essential for maintaining the effectiveness of your MFA tool. Choose a vendor known for providing excellent technical support and timely software updates to address new security threats. Strong support and maintenance services ensure your MFA system remains robust and up-to-date.
Our methodology for selecting the best multi-factor authentication tools
We’ve broken down our analysis for you based on these key criteria:
- Security Features: Evaluating the strength and variety of security measures offered.
- User Experience: Considering the ease of use and accessibility for end-users.
- Integration: Assessing compatibility with existing systems and applications.
- Customization: The ability to tailor the tool to specific business needs.
- Support and Updates: Availability of customer support and frequency of software updates.
The Best Multi-Factor Authentication Tools
1. ManageEngine ADSelfService Plus (FREE TRIAL)
Key Features:
- Multi-Factor Authentication: Enhances security by requiring multiple forms of verification.
- Self-Service Password Reset: Allows users to reset their passwords without IT assistance.
- Single Sign-On: Provides users with one-click access to multiple applications.
- Real-Time Alerts: Sends instant notifications for suspicious activities.
- Customizable Policies: Tailors security settings to meet specific organizational requirements.
Why do we recommend it?
ManageEngine ADSelfService Plus is highly recommended for its robust security features and seamless integration with various systems. Its user-friendly interface and customizable policies make it a versatile choice for businesses of all sizes.
Who is it recommended for?
This tool is ideal for organizations looking to enhance their security protocols without compromising on user convenience. It’s particularly suitable for businesses that require a customizable and scalable authentication solution.
Pros:
- Enhanced Security: Various multi-factor authentication options significantly boost protection against unauthorized access.
- User-Friendly Interface: The platform is easy to navigate, making it accessible for all users.
- Integration Capabilities: Seamlessly integrates with a variety of existing systems and applications.
- Customizable Options: Security policies can be tailored to specific business needs.
- Real-Time Alerts: Immediate notifications help in quick response to security threats.
Cons:
- Learning Curve: Some users may need time to fully understand and utilize all features.
Download ADSelfService Plus for a 30-day free trial.
EDITOR'S CHOICE
ManageEngine ADSelfService Plus is our top multi-factor authentication tool because of its comprehensive security features and ease of integration with existing systems. Its user-friendly interface simplifies the authentication process, making it accessible for all levels of users. The customization options allow businesses to tailor the tool to their specific security needs. I particularly appreciated the robust support and frequent updates, as well as the simple options for users to reset their own credentials, which cut down on the number of tickets our helpdesk has received. Overall, ADSelfService Plus stands out for its balance of security, usability, and adaptability.
Download: Access a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/self-service-password/sem/active-directory-multi-factor-authentication.html
2. LastPass
LastPass is a powerful password manager designed to securely store and manage your passwords. It offers a password vault, multi-factor authentication, and auto-fill capabilities to streamline and enhance your online security. The tool generates strong, unique passwords, ensuring your accounts are well-protected. Accessible across multiple devices, LastPass provides a seamless user experience while maintaining robust security.
Key Features:
- Password Vault: Stores and encrypts passwords securely.
- Multi-Factor Authentication: Adds an extra layer of security with multiple verification methods.
- Auto-Fill: Automatically fills in login credentials on websites and apps.
- Password Generator: Creates strong, unique passwords to enhance security.
- Cross-Platform Access: Accessible on multiple devices and operating systems.
Why do we recommend it?
LastPass is recommended for its comprehensive security features and ease of use. Its ability to securely store and manage passwords, coupled with multi-factor authentication, makes it an essential tool for maintaining robust security.
Who is it recommended for?
This tool is perfect for individuals and businesses seeking a reliable and user-friendly password management solution. It’s particularly beneficial for those who need secure access to their passwords across multiple devices.
Pros:
- Secure Password Storage: Keeps all passwords encrypted and protected in one place.
- Ease of Use: User-friendly interface makes it easy to manage and retrieve passwords.
- Auto-Fill Feature: Saves time by automatically filling in login credentials.
- Strong Password Generation: Helps users create and maintain secure passwords.
- Multi-Device Access: Provides flexibility by allowing access from various devices and platforms.
Cons:
- Subscription Cost: Full functionality requires a paid subscription.
- Occasional Sync Issues: Some users experience delays in syncing passwords across devices.
- Dependence on Internet: Needs an internet connection for optimal performance.
3. Auth0
Auth0 is a versatile identity management platform designed to provide secure and seamless authentication solutions for applications. It offers a range of features including multi-factor authentication, single sign-on, and advanced user management. Auth0’s flexibility and extensive integration capabilities make it a valuable tool for developers looking to implement robust security measures. With its user-friendly interface and comprehensive security options, Auth0 ensures both ease of use and strong protection.
Key Features:
- Multi-Factor Authentication: Enhances security with multiple verification methods.
- Single Sign-On: Provides a unified login experience across multiple applications.
- Advanced User Management: Allows detailed control and management of user profiles.
- Extensive Integrations: Integrates seamlessly with a wide variety of applications and platforms.
- Customizable Login: Offers tailored login experiences to match your brand.
Why do we recommend it?
Auth0 is recommended for its extensive integration capabilities and strong security features. Its flexibility and ease of implementation make it an excellent choice for developers and businesses aiming to enhance their authentication processes.
Who is it recommended for?
This tool is ideal for developers and organizations needing a secure, customizable, and scalable authentication solution. It’s especially useful for businesses that require advanced user management and seamless integration with various applications.
Pros:
- Strong Security: Multi-factor authentication and single sign-on ensure robust protection.
- User-Friendly Interface: Simplifies the implementation and management of authentication processes.
- Integration Flexibility: Easily integrates with numerous applications and platforms.
- Advanced User Control: Provides detailed management options for user profiles and access.
- Customizable Login Experience: Allows businesses to tailor the login interface to their branding needs.
Cons:
- Pricing Structure: The cost can escalate with extensive usage and advanced features.
- Learning Curve: New users may require time to fully understand and utilize all features.
- Support Response Time: Some users have reported slower response times from customer support.
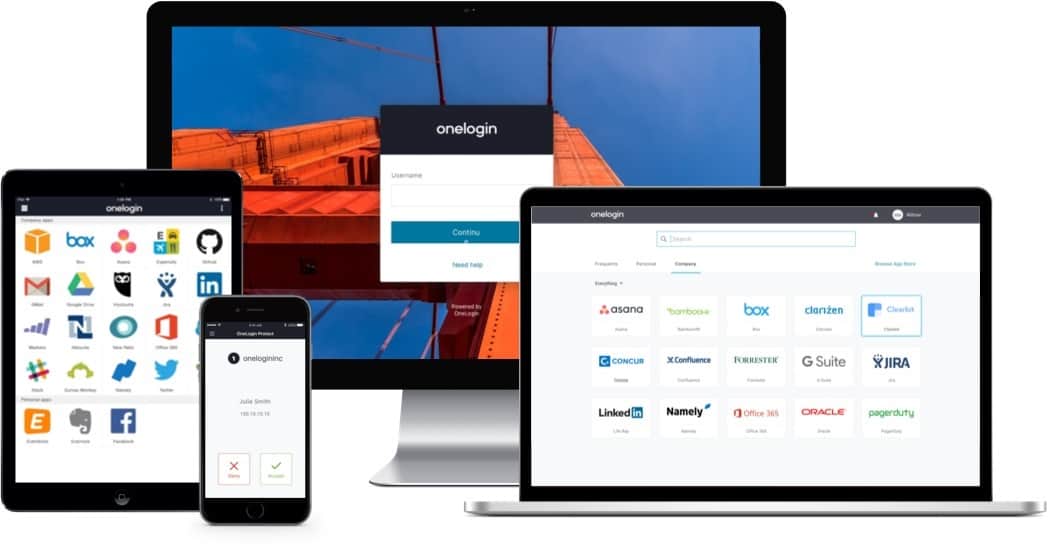
4. OneLogin
OneLogin is a comprehensive identity and access management platform designed to simplify and secure user access to applications and data. It features multi-factor authentication, single sign-on, and advanced user provisioning, ensuring robust security and efficient user management. OneLogin’s intuitive interface and extensive integration capabilities make it a reliable choice for organizations of all sizes. By streamlining the authentication process, OneLogin enhances both security and user convenience.
Key Features:
- Multi-Factor Authentication: Adds an extra layer of security with multiple verification steps.
- Single Sign-On: Simplifies access by allowing users to log in once and access multiple applications.
- User Provisioning: Automates the process of managing user access and permissions.
- Extensive Integrations: Connects seamlessly with a wide range of applications and systems.
- Centralized Dashboard: Provides a single interface to manage all identity and access controls.
Why do we recommend it?
OneLogin is recommended for its robust security features and ease of integration with various systems. Its user-friendly interface and comprehensive access management capabilities make it an excellent choice for enhancing organizational security.
Who is it recommended for?
This tool is ideal for organizations seeking a reliable and secure solution for managing user identities and access. It’s particularly suitable for businesses that require seamless integration with multiple applications and efficient user provisioning.
Pros:
- Enhanced Security: Multi-factor authentication ensures strong protection against unauthorized access.
- Ease of Use: The platform’s intuitive interface makes it easy to manage and navigate.
- Streamlined Access: Single sign-on simplifies user access to multiple applications.
- Automated User Management: User provisioning automates access and permission controls, saving time and reducing errors.
- Comprehensive Integration: Connects effortlessly with a wide array of applications and systems.
Cons:
- Cost: The pricing can be high for smaller organizations or those with extensive usage needs.
- Initial Setup Complexity: Setting up the system can be complex and time-consuming.
- Support Availability: Some users have experienced delays in receiving customer support assistance.
5. Authy
Authy is a reliable and user-friendly multi-factor authentication app designed to enhance the security of your online accounts. It offers secure cloud backup, multi-device synchronization, and seamless integration with various applications. Authy’s intuitive interface and robust security features make it an excellent choice for both individuals and businesses. By providing an additional layer of authentication, Authy ensures that your accounts remain protected against unauthorized access.
Key Features:
- Multi-Factor Authentication: Provides an extra layer of security with multiple verification steps.
- Secure Cloud Backup: Ensures your authentication data is safely backed up in the cloud.
- Multi-Device Sync: Allows you to access your authentication tokens from multiple devices.
- App Integration: Easily integrates with numerous applications and services.
- User-Friendly Interface: Simplifies the process of managing and accessing authentication tokens.
Why do we recommend it?
Authy is recommended for its strong security features and user-friendly design. It provides secure cloud backup and multi-device synchronization, making it a convenient and reliable choice for enhancing account security.
Who is it recommended for?
This tool is perfect for individuals and businesses looking for a secure and easy-to-use multi-factor authentication solution. It is especially beneficial for users who need access to authentication tokens across multiple devices.
Pros:
- Enhanced Security: Multi-factor authentication significantly strengthens account protection.
- Convenient Cloud Backup: Secure cloud backup ensures your data is always accessible and safe.
- Multi-Device Access: Syncs authentication tokens across various devices for added convenience.
- Ease of Use: The intuitive interface makes managing authentication tokens straightforward.
- Seamless Integration: Integrates effortlessly with a wide range of applications and services.
Cons:
- Reliance on Internet: Requires an internet connection for cloud backup and synchronization.
- Limited Customization: Offers fewer customization options compared to some competitors.
- Occasional Sync Delays: Some users experience delays in token synchronization across devices.
6. RSA SecurID
RSA SecurID is a leading multi-factor authentication solution designed to provide strong security for accessing critical systems and data. It offers robust features such as hardware and software tokens, risk-based authentication, and extensive integration capabilities. RSA SecurID is renowned for its reliability and high-security standards, making it a preferred choice for organizations needing stringent access controls. By combining various authentication methods, RSA SecurID ensures that only authorized users can access sensitive information.
Key Features:
- Multi-Factor Authentication: Strengthens security with multiple layers of verification.
- Hardware and Software Tokens: Provides flexible authentication options with both physical and digital tokens.
- Risk-Based Authentication: Adjusts security requirements based on user behavior and risk levels.
- Extensive Integration: Connects seamlessly with a wide range of applications and systems.
- Centralized Management: Offers a unified platform to manage all authentication controls.
Why do we recommend it?
RSA SecurID is recommended for its robust security features and flexible authentication options. Its comprehensive approach to multi-factor authentication makes it an ideal solution for organizations requiring high levels of security.
Who is it recommended for?
This tool is perfect for enterprises and organizations that require stringent access control and reliable authentication solutions. It is particularly suitable for businesses handling sensitive data and requiring compliance with strict security standards.
Pros:
- Strong Security: Multi-factor authentication provides robust protection against unauthorized access.
- Flexible Token Options: Offers both hardware and software tokens for versatile authentication methods.
- Risk-Based Authentication: Enhances security by adjusting requirements based on user behavior and risk.
- Seamless Integration: Integrates effortlessly with numerous applications and systems.
- Centralized Management: Simplifies administration with a unified platform for managing authentication controls.
Cons:
- Complex Setup: Initial configuration can be time-consuming and complex.
- Higher Cost: The solution can be expensive, particularly for smaller organizations.
- User Training Required: Users may need training to effectively utilize all features and tokens.
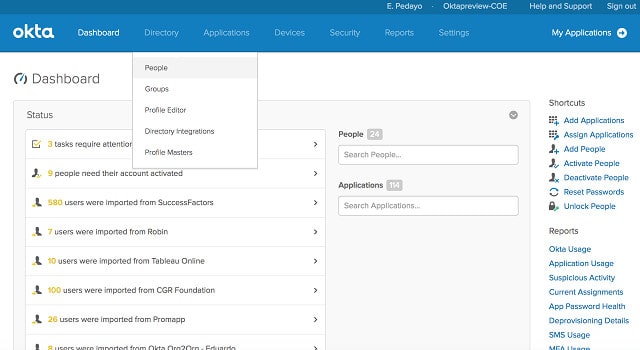
7. Okta
Okta is a powerful identity and access management platform designed to streamline and secure user authentication across applications and devices. It features multi-factor authentication, single sign-on, and advanced user provisioning to enhance security and user management. Okta’s robust integration capabilities and user-friendly interface make it an excellent choice for organizations seeking comprehensive identity solutions. By simplifying the authentication process, Okta ensures strong security while improving user convenience.
Key Features:
- Multi-Factor Authentication: Strengthens security with multiple verification methods.
- Single Sign-On: Provides seamless access to multiple applications with one login.
- User Provisioning: Automates the creation and management of user accounts.
- Extensive Integrations: Connects with a wide range of applications and systems.
- Centralized Management: Offers a single platform to manage all identity and access controls.
Why do we recommend it?
Okta is recommended for its comprehensive security features and seamless integration with various applications. Its robust user management and intuitive interface make it a top choice for enhancing organizational security and efficiency.
Who is it recommended for?
This tool is ideal for organizations of all sizes looking for a reliable and scalable identity and access management solution. It’s particularly suitable for businesses that need advanced user provisioning and extensive integration capabilities.
Pros:
- Robust Security: Multi-factor authentication provides strong protection against unauthorized access.
- Ease of Use: The intuitive interface simplifies user management and navigation.
- Streamlined Access: Single sign-on simplifies user access to multiple applications.
- Automated User Management: User provisioning automates account creation and management, saving time and reducing errors.
- Comprehensive Integration: Integrates effortlessly with numerous applications and systems.
Cons:
- Pricing: Can be expensive, particularly for smaller organizations.
- Initial Setup Complexity: The setup process can be complex and time-consuming.
- Learning Curve: Users may require time to fully understand and utilize all features.
8. Google Authenticator
Google Authenticator is a simple yet effective multi-factor authentication app designed to enhance the security of your online accounts. It generates time-based one-time passwords (TOTP) that provide an additional layer of security. The app is easy to set up and use, making it accessible for a wide range of users. With its straightforward interface and reliable performance, Google Authenticator is a popular choice for those seeking to bolster their account protection.
Key Features:
- Time-Based One-Time Passwords: Generates unique codes that change every 30 seconds.
- Offline Functionality: Works without an internet connection once set up.
- Easy Setup: Simple QR code scanning to add new accounts.
- Cross-Platform Compatibility: Available on both Android and iOS devices.
- Lightweight and Fast: Minimalistic design ensures quick and efficient performance.
Why do we recommend it?
Google Authenticator is recommended for its simplicity, reliability, and ease of use. It provides a robust second layer of security for your accounts with minimal setup and maintenance required.
Who is it recommended for?
This tool is ideal for individuals and small businesses seeking an easy-to-use, no-frills multi-factor authentication solution. It’s especially suitable for users who need a quick and reliable way to enhance their account security.
Pros:
- Enhanced Security: Provides an extra layer of protection with time-based one-time passwords.
- No Internet Required: Functions offline once initial setup is complete, enhancing reliability.
- Quick Setup: Adding new accounts is fast and straightforward using QR code scanning.
- Cross-Platform Access: Available on both Android and iOS, ensuring wide compatibility.
- Lightweight App: The app is fast and efficient, without unnecessary features.
Cons:
- No Cloud Backup: Lacks cloud backup, so losing your device can result in losing access to your codes.
- Limited Features: Offers fewer advanced features compared to some other authentication tools.
- Manual Transfer: Transferring accounts to a new device requires manual reconfiguration.
My Final Thoughts
After evaluating various multi-factor authentication tools, I personally prefer ManageEngine ADSelfService Plus. Its comprehensive security features and seamless integration capabilities truly stand out. I found its user-friendly interface and customizable policies particularly impressive, allowing for tailored security solutions without compromising on usability.
Overall, ADSelfService Plus strikes the perfect balance between robust protection and convenience, making it my top choice for any size organization looking to implement MFA across their network.