Metasploit is a handy tool and is one of the critical systems used by hackers – including the white hat hacker who performs penetration testing. There are two versions of Metasploit. These are Metasploit Framework and Metasploit Pro
Penetration testers can use Metasploit to gather information on a system, look for its security weaknesses, and then launch an attack to test whether real hackers could get into the system.
The history of Metasploit
Metasploit was first created in 2003 by H D Moore. It was made into an open-source project. Open-source systems make the source code of the software available to everyone. The main package is kept in storage, but those who copy it can change it and use it for free. Others can just use it for free. Some of the people who make changes send their new version back to the core project manager. A committee assesses the changes and, in many cases, brings them into the core system. Thus, members of the public end up becoming unpaid developers for the project.
The problem with many open-source projects is that they lack the funds to manage the system properly. As a result, the software can get attacked by hackers who discover exploits. A software house will quickly produce an update in those events, but unfunded projects can’t organize a quick response, and thus, open-source systems rapidly become unusable.
Metasploit avoided being abandoned as outdated and insecure software by being adopted by the cybersecurity firm, Rapid7. The match between Metasploit and Rapid7 is a good one. The company is a leading innovator in the cybersecurity field.
An Overview of Metasploit: Framework vs. Pro
The Metasploit Project has evolved significantly since its acquisition by Rapid7 in 2009. Leveraging Rapid7’s expertise in professional project management and its financial backing, the tool has grown into one of the most widely used platforms for penetration testing and vulnerability exploitation.
Metasploit Framework
Metasploit Framework is the original, open-source version of the tool, which remains a cornerstone of the cybersecurity community. Maintained and enhanced by a global network of contributors, it is freely available and highly adaptable. The Framework is ideal for security professionals, researchers, and ethical hackers seeking a powerful and customizable tool for testing network defenses and exploiting vulnerabilities. Despite being free, it is feature-rich and frequently updated, allowing users to work with cutting-edge security tools and methodologies.
Metasploit Pro
Metasploit Pro, on the other hand, is Rapid7’s commercial iteration of the Framework. While built on the same foundation, it is subjected to rigorous testing for stability and reliability before release. Rapid7 then integrates advanced features, making it a more comprehensive solution for enterprise-level security operations. These additional capabilities, such as automation, enhanced reporting, and broader exploit libraries, make Metasploit Pro a premium choice for businesses seeking reliable, scalable security testing tools.
Key Differences
The primary distinction between Metasploit Framework and Pro lies in functionality and user accessibility. The Framework, while versatile and free, requires a deeper technical understanding and lacks some of the enhanced features available in Pro. This makes it an excellent entry point for users who may later opt for the paid version to access advanced tools.
Metasploit’s dual offerings provide flexibility, allowing individuals and organizations to choose a version that aligns with their technical expertise and operational requirements.
| Feature | Pro | Framework |
|---|---|---|
| De-facto standard for penetration testing with more than 1,500 exploits | Yes | Yes |
| Import of network data scan | Yes | Yes |
| Network discovery | Yes | |
| Basic exploitation | Yes | |
| MetaModules for discrete tasks such as network segmentation testing | Yes | |
| Integrations via Remote API | Yes | |
| Simple web interface | Yes | |
| Smart Exploitation | Yes | |
| Automated credentials brute forcing | Yes | |
| Baseline penetration testing reports | Yes | |
| Wizards for standard baseline audits | Yes | |
| Task chains for automated custom workflows | Yes | |
| Closed-Loop vulnerability validation to prioritize remediation | Yes | |
| Basic command-line interface | Yes | |
| Manual exploitation | Yes | |
| Manual credentials brute forcing | Yes | |
| Dynamic payloads to evade leading anti-virus solutions | Yes | |
| Phishing awareness management and spear phishing | Yes | |
| Web app testing for OWASP Top 10 vulnerabilities | Yes | |
| Choice of advance command-line (Pro Console) and web interface | Yes |
As you can see from the features comparison, Metasploit Framework includes the same automated vulnerability scanner as Metasploit Pro but not much other automation.
Metasploit operating system compatibility
Metasploit requires 64-bit processors with the following operating systems:
- Microsoft Windows: 7 SP1+, 8.1, 10
- Windows Server: 208 R2, 2012 R2, 2016, 2019
- Linux: RHEL 5.10 or later, Ubuntu 14.04 LTS or later
The download page for Metasploit Framework includes instructions for downloading to macOS and also includes CentOS, Fedora, and Debian Linux. However, these operating systems are not mentioned on the Systems Requirements page of the Metasploit section of the Rapid7 website.
Metasploit Framework is pre-installed on all versions of Kali Linux.
Metasploit Pros & Cons
Pros:
- One of the most popular security frameworks in use today
- Has over of the largest communities – great for continuous support and up-to-date additions
- Available for free and commercial use
- Highly customizable with many open-source applications
Cons:
- Metasploit caters to more technical users, which increases the learning curve for beginners in the security space
How to install Metasploit Framework
To get to know Metasploit Framework, you should download it and install it. The installation on Linux and macOS is straightforward, but the process is difficult on Windows.
If you are running Windows, turn off Windows Security first because otherwise, it will go crazy during the installation of Metasploit and block all of the threat files that it wants to copy onto the computer.
- Open File Explorer and create the directory c:\metasploit-framework.
- Open the Start menu.
- Click on the Settings cog.
- Select Update and Security.
- In the Update and Security windows, Click on Windows Security in the left-hand menu.
- Click on Virus & threat protection.
- Click on Manage settings.
- Slide the Real-time protection switch to Off.
- Scroll down to the Exclusions heading and click on Add or remove exclusions.
- Click on the Add an exclusion button and select Folder in the dropdown list. A Select Folder window will appear.
- Enter c:\metasploit-framework in the folder name field and press the Select Folder button.
You can now install Metasploit.
- Go to the download page for Metasploit Framework.
- Click on the link for the installer for your operating system.
- Click on the downloaded
- file to run the installer.
- Accept the End-User Licensing Agreement and cycle through the Installation Wizard by pressing the Next button on each screen.
- Press the Install button and wait for the progress bar to fill up.
- If you are installing Windows, during the installation process, a User Account Control pop-up will appear. Press Yes.
Wait for the installer to complete and then access the Metasploit Console.
How to install Metasploit Pro
Metasploit Framework and Metasploit Pro don’t install to the same directory, so it is possible to run both. This is mainly a good idea if you want to have the option of manually performing a brute force attack – a utility that isn’t included in Metasploit Pro.
You can access a 14-day free trial of Metasploit Pro. Go to the Metasploit Pro download page and fill out the form for the free trial.
The email address you enter must be on a company domain and not one of the free email systems, such as yahoo.com or mail.com. However, it needs to be a valid email address to which you have access because the Metasploit system sends an activation code to that account, and Metasploit Pro won’t work without it.
Before downloading the installer, crate the directory c:\metasploit. Go through the anti-virus disabling steps shown above if you are installing on Windows. Then, add in an exclusion for c:\metasploit. You will have less trouble installing on Linux. However, if you have an anti-virus system, you need to set up Metasploit as an exception to prevent your AV from blocking the installation.
Follow these steps after adjusting your AV:
- Click on the download link for your operating system on the page that follows the free trial form. This link is written as 64-Bit.
- Click on the downloaded file to run the installer.
- Accept the License Agreement.
- Cycle through the installer steps by clicking on the Next button.
- Note down the SSL port that you select for Metasploit activity. The default that is shown in the installation wizard is 3790.
- At the end of the installation process, press the Finish button. The application will open in a browser, and your system will present an option in which you select your preferred browser.
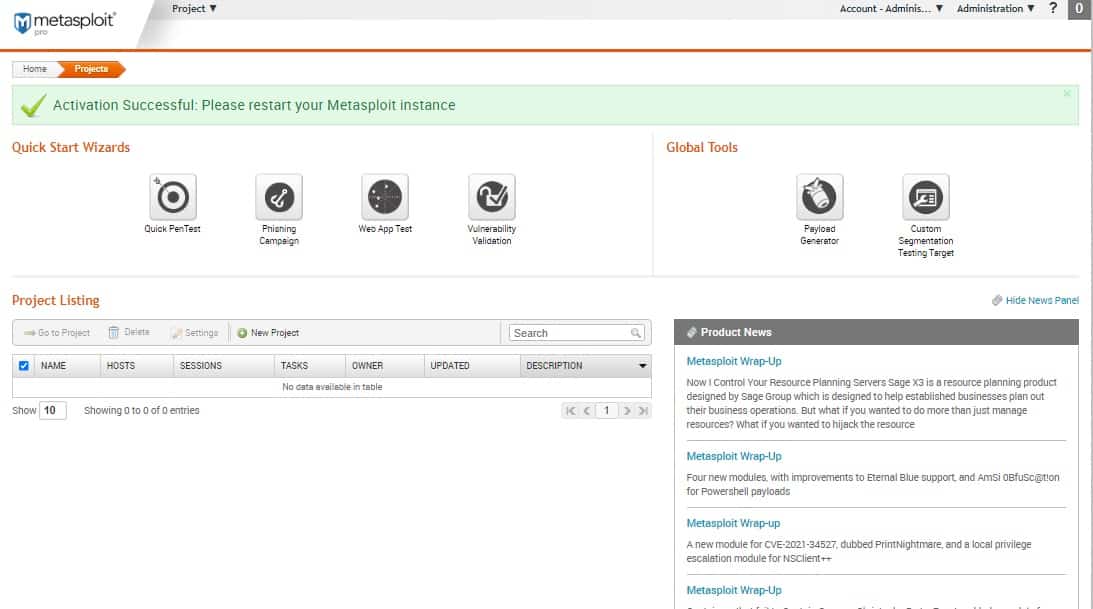
Using Metasploit Pro
The first time that you run Metasploit Pro, you will need to use the Metasploit Web UI. When this opens, you can set up an account for yourself.
The first account that you create is the Administrator account. You need to ensure that you choose a strong password because if a hacker ever got into this account, they could cause havoc on your entire system. The password must be a mix of letters and numbers and should include at least one unique character. It should not have the username that you are setting up and should not be easy to guess.
Next, look at the Inbox for the email address you gave when applying for the free trial. Copy the Product Key shown in the email and paste this into the screen that appears after entering the account details.
You can now use the Metasploit system through the Web interface.
If you want to use Metasploit at the command line, go to the Start menu and look for the Metasploit menu item. Then, expand that and click on Metasploit Console.
The Metasploit Console is, basically, just a Command Prompt/Terminal window. Once you open up the window, the Metasploit system takes a long time to start up.
Types exit at the prompt to close down the Metasploit Console.
If you opt for the Metasploit Framework, you just get the Console version.
How much does Metasploit Pro cost?
Rapid7 sells Metasploit Pro through distributors. Those businesses make their own decisions on the sales price, deciding how far they want to squeeze their margins to win business from rival software retailers.
The current price for Metasploit Pro is around $15,000 per year. The package price ranges from $14,267.99 to $15,329.99.
Alternatives to Metasploit
The option of both a free version and a fully-armed paid version gives Metasploit a broad appeal. The alternatives to Metasploit need to include both free utilities that compete with Metasploit Framework and paid systems that present Metasploit Pro alternatives. It is also helpful to consider vulnerability scanners, which can provide excellent alternative strategies to identifying system weaknesses.
1. Invicti (ACCESS FREE DEMO)
This web vulnerability scanner is particularly useful for development testing and it is able to identify weaknesses in any APIs that the project might intend to use. In addition to looking for known vulnerabilities, this scanner uses its own process of heuristics that can spot weak security in modules and recommend fixes to tighten up any potential exploits.
Pros:
- Features a highly intuitive and insightful admin dashboard
- Supports any web applications, web service, or API, regardless of framework
- Provides streamlined reports with prioritized vulnerabilities and remediation steps
- Eliminates false positives by safely exploiting vulnerabilities via read-only methods
- Integrates into dev ops easily providing quick feedback to prevent future bugs
Cons:
- Would like to see a trial rather than a demo
Offered as a SaaS platform or for installation on Windows and Windows Server.
2. Acunetix (ACCESS FREE DEMO)
This is a vulnerability scanner. The system is offered in three editions, and the lowest plan, called Standard, provides on-demand vulnerability scans that search for more than 7,000 vulnerabilities. The middle package, called Professional, includes a network scanner that can spot more than 50,000 known exploits. The external scanner will look at the internet-facing profile of a network and scan through websites and Web applications. In addition, it can monitor the operations of APIs and assess the security weaknesses of the modules that support them.
Pros:
- Designed specifically for application security
- Integrates with a large number of other tools such as OpenVAS
- Can detect and alert when misconfigurations are discovered
- Leverages automation to immediately stop threats and escalate issues based on the severity
Cons:
- Would like to see a trial version for testing
Acunetix is provided as a hosted SaaS platform. However, it is also possible to download the software package and install it on Windows, macOS, or Linux.
3. Armitage
This package is not so much an alternative to Metasploit; this free tool enhances Metasploit Framework and makes it a better rival to Metasploit Pro. Armitage works as a front end to Metasploit Framework. It enables the user to use Metasploit to probe systems, gathering information, and identifying possible entry points. It stores the findings of research and feeds them into attack strategies.
Pros:
- Designed to enhance the Metasploit framework
- Enables users to probe systems, gather information, and more
- Can store information and pair that information with attack strategies
- Native to Kai Linux
Cons:
- Can take time to fully explore all features and tools
This tool is available for Windows, macOS, and Linux. It is pre-loaded into Kali Linux.
4. Burp Suite
Finally, this package from PortSwigger, is a very close match to Metasploit because it is available in a free Community Edition and a paid version, called the Professional Edition. There is also an Enterprise Edition, which is a fully automated vulnerability scanner. Both the free and paid versions have the same interface. However, many of the functions within that app are disable for Community Edition users. Those paid-for services include automated vulnerability scans. A significant benefit of the Burp Suite interface is that the user can select data from the research utility and get it sent directly into the attack services. Burp Suite runs on Windows, macOS, and Linux.
Pros:
- A collection of security tools designed specifically for security professionals
- The Community Edition is free – great for small businesses
- Available cross-platform for Windows, Linux, and Mac operating systems
Cons:
- Takes time to explore all the tools available in the suite
You can download the Community edition for free or request a free trial of the Professional edition.
5. Sqlmap
This command-line utility offers just one command, but it has hundreds of options, which changes the function that gets run. This utility documents database and also launch attacks. The service includes valuable processes, such as password cracking and injection attacks. Some of the episodes can be conducted without leaving any trace, while others are intended to alter data in the database under attack.
Pros:
- Completely free
- Open source transparent project
- Specifically caters to identifying SQL attacks
- Available for Windows, Linux, Mac OS, Free BSD
Cons:
- Is slightly outdated when compared to other VAPT tools
Sqlmap is free to use and installs on Windows, macOS, and Linux.
6. Ettercap
This packet capture utility is also an attack facility because it can inject traffic into a stream. This is a command-line utility that has an extensive library of commands. The attacks of this utility are based on the man-in-the-middle strategy. Its methods rely on the utility being run from within a network. The Ettercap package offers a user interface. However, like the Metasploit Console, this is just a customized Command Prompt/Terminal window. Ettercap can also be used for password capture, DNS spoofing, and Denial of Service.
Pros:
- Open source security platform
- Specifically for identifyting man in the middle attacks
- Well documented with a large community
- Completely free
Cons:
- Is more of a specialized tool than a complete solution
This utility is free to use and runs on Linux, Unix, Mac OS X, Windows 7, and 8. Unfortunately, it will not work on macOS or Windows 10.
Metasploit FAQs
What is Metasploit used for?
Metasploit framework is a package of tools that researches the security of IT systems and uses that information to launch attacks. This tool can be used by hackers and it is also widely used by penetration testers.
Can I hack with Metasploit?
Metasploit was made for hacking. Its big advantage is that it includes methods to identify weaknesses in an IT system and other tools to try to break into them. The system is a good tool for penetration testers as well.
Is Metasploit still free?
Metasploit Framework is a free, open-source system. There is a better version, called Metasploit Pro, which is the Metasploit Framework with extra features added on by Rapid7. Metasploit Pro is not free.








Ettercap doesn’t belong on the comparison list at ALL. If the goal was to describe alternatives this missed the mark badly. These things that are listed are mostly web auditing tools. The only two alternatives aren’t even listed here.