Managed SIEM services offer organizations a powerful solution for detecting, analyzing, and responding to security threats in real-time, without the complexity of managing the underlying infrastructure and software. Security Information and Event Management (SIEM) systems are essential for businesses looking to enhance their security posture, providing centralized logging, threat detection, and compliance reporting.
Many organizations struggle to implement and maintain these systems due to the required expertise, resources, and ongoing management. This is where managed SIEM services come into play. By outsourcing the management of SIEM solutions to specialized providers, organizations can benefit from expert-level security monitoring, advanced threat detection, and incident response, all while reducing the burden on internal IT teams.
Managed SIEM services offer a comprehensive approach to cybersecurity, ensuring continuous monitoring, proactive threat hunting, and swift identification of vulnerabilities or breaches. These services typically include features such as 24/7 monitoring, automated log collection, incident detection, and real-time alerts. This combination of services is designed to mitigate risks and help businesses comply with industry regulations.
These managed security services provide actionable insights, enabling organizations to identify patterns of suspicious activity and respond to potential threats quickly, reducing the likelihood of a successful cyberattack. They often integrate with existing IT infrastructure, enhancing services such as managing a complex network environment, ensuring compliance with GDPR or HIPAA, or defending against advanced persistent threats.
In this guide, we explore the top managed SIEM services, examining their features, benefits, and what to consider when choosing a service provider. With expert-managed services, businesses can ensure their networks remain secure, compliant, and resilient to cyber threats.
Here is our list of the best Managed SIEM services:
- UnderDefense EDITOR’S CHOICE A SIEM service backed by a proficient Security Operations Center and cybersecurity consultancy, offering options for fully managed SIEM, on-premises software, or a co-managed SIEM to best suit your needs. Get the first month free.
- Ideal Smart Managed Cybersecurity An impressive Security Operation Center that can protect IT resources anywhere in the world.
- Nomios Managed SIEM System security services from a fully certified Security Operations Center.
- Bulletproof Managed SIEM A Security Operations Center that runs a SIEM service and also offers vulnerability scanning and penetration testing.
- ArmorPoint A SIEM system that can be bought as software to install on-premises or subscribed to as a managed service.
- Redscan Managed SIEM A SIEM service that includes around-the-clock vigilance from experts who are good at rooting out false positives.
Who needs a Managed SIEM Solution?
SIEM stands for Security Information and Event Management. It is a category of cybersecurity software that looks in many different places around the IT system for evidence of intrusion or malicious behavior.
Most SIEM systems are tools for experts to use in order to find intruders or insider threats and they point to possible problems so that a member of staff can make further investigations and make a decision on what to do about the menace.
Small businesses, startups, and businesses that outsource their IT management won’t have any in-house IT team to assess the results shown by a SIEM system. Fortunately, this is another area of IT support that can be outsourced. Managed SIEM system bundle in the SIEM tools and cloud server resources with a team of technicians to carry out that risk analysis, root cause investigation, and mitigation actions that on-premises experts are expected to perform.
Note: If need to purchase your SIEM software individually, consider checking out our post on the Best SIEM tools for Businesses
How does SIEM work?
SIEM is an evolution of traditional antimalware systems. Hackers don’t always use software and automated processes to attack a private IT system. They also have manual methods for exploiting networks and endpoints. A hacker might enter into a network looking for data that can be sold or ways to command a funds transfer to steal money from the business.
Even bland and boring businesses are interesting to hackers. This is because the IT resources of a victimized company provide free equipment that a hacker can use. Hackers drag down the performance of servers by secretly installing cryptocurrency mining systems on them. A hacker can also use the gateway of business to channel attacks on other businesses, thus hiding the real location of the attacker and evading detection.
Most network defenses are there to block access by unauthorized users so hackers use phishing emails to trick employees into divulging their login credentials. Another way that genuine user accounts can be acquired by hackers is through guessing passwords. Legitimate users of a company system can also perform malicious acts. This could be because they were tricked by a hacker impersonating a superior or because that employee is angry with a boss, the owner, or the business in general because of a perceived slight.
When valid user accounts get used for attacks, there is little that boundary defenses can do to spot them. SIEM systems look through log files and watch traffic patterns to look for unexpected activities. For example, the user account of an employee in the sales department probably shouldn’t be trying to access the business’s purchasing records and a worker sitting in the offices in the USA couldn’t possibly be logging in from the Philippines.
SIEM uses two sources of information and combines two older security strategies. SIM is Security Information Management, which gathers log files from all over the business, consolidates them into a common format, and searches through them for significant patterns of activities, called “indicators of compromise.” The second methodology that feeds into SIEM is called Security Event Management (SEM), which scans network traffic for anomalous behavior.
While SEM is quick, SIM is more accurate. SIM can spot malicious behavior by linking together apparently normal events that collectively indicate unauthorized actions. Combining SIM and SEM into SIEM produces a fast and accurate system protection strategy.
About Managed SIEM services
If you are just starting up a business or if you haven’t automated many processes in a traditional business that you have been running for a long time, you should investigate managed services.
It is possible now to run an entire business empire without employing anyone directly or having any premises. You can hire home-based freelancers and get cloud services, so all of your IT systems is focused on the Internet. It is even possible to get together a bunch of people all working individually as one company by getting a VoIP telephone number for your business. You can then subscribe to a cloud switchboard to channel calls through to the mobile devices and home phone numbers of your workers.
However, even if you don’t have any on-premises equipment at all, your business is still under threat from hackers. Web-based eCommerce businesses are particularly vulnerable. Any business that has an Internet connection is at risk of attack. So, they all need cybersecurity systems for protection.
A Managed Service Provider (MSP) takes care of all of the IT functions that a traditional office would. Whether your enterprise has premises or works as a virtual office, an MSP takes all of the worries of running IT infrastructure off your shoulders. A managed SIEM service gives you the full attention of the top-drawer cybersecurity experts that even the most prosperous corporations can’t hire because they are so rare.
The best Managed SIEM services
Placing the control of your IT infrastructure’s defense in the hands of a separate company seems to be a big risk. No matter where your company’s data is held or who secures it, ultimately, you have the legal responsibility for it. However, managed SIEM providers know that. They are only in business because they are good at what they do and better at looking after system security than the people who are available for hire.
A major priority for many companies is to prove compliance with data security standards. In many fields of business, it isn’t possible to win clients or get associate agreements without having accreditation to some standard or another. Managed SIEM service providers know all about those standards. They will help you tighten up your system, so it qualifies for an accreditation certificate, providing all of the necessary documentation for that aim.
Our methodology for selecting a managed SIEM service for your company
We reviewed the market for managed SIEM systems and analyzed the available packages based on the following criteria:
- Around-the-clock system management team
- Expert security analysts to interpret anomaly reports
- A service that can manage the security for multiple sites
- Options to choose the SIEM software that will be used
- A trustworthy and traceable service provider
- A free trial or a demo service that lets you assess the credibility of the security team
- Value for money represented by a high degree of security expertise at a reasonable subscription rate
With these selection criteria in mind, we looked for managed service providers that have good reputations in the field of system security and have a list of satisfied clients.
We have surveyed the marketplace to identify outstanding managed SIEM providers that not only protect IT systems competently but can also assist with data security standards compliance
1. UnderDefense (FREE TRIAL)
UnderDefense is a long-standing cybersecurity consultancy that runs a Security Operations Center. However, the reason this company is on our list is that it also offers a managed SIEM service. The service is ideal for companies that don’t have in-house IT staff with security expertise.
Key Features:
- Remote Security Operations Center: SIEM deployment in minutes
- Technicians Manage Everything: All sensors, log collectors, and visibility testing provided
- Constant Support: 24/7 SOC team monitoring
- Regulation Conformance: Automated compliance reports
- Security System Adjustments: Garbage data filtering and performance tuning
Why do we recommend it?
UnderDefense’s Managed SIEM service is designed to get your new SIEM operational within 20 minutes, fully prepared for log ingestion in your specific geo-location. This service is available in three levels of participation, catering to your specific needs, whether you host the SIEM software on your servers or opt for a cloud-based SIEM. UnderDefense doesn’t host the SIEM software itself.
A unique offering from UnderDefense is its co-managed SIEM service, ideal for businesses with an IT department and the necessary equipment to host the SIEM software. While your in-house staff maintains the software, UnderDefense’s team of cybersecurity experts are on-call to interpret the results, identify compromised system elements, and recommend necessary actions.
The co-managed service is a support package with cybersecurity experts on-call. These experts check on the alarms raised by the SIEM software and perform further analysis through the stored records of the SIEM to identify all of the compromised elements of the system. As a result, UnderDefense experts are able to recommend actions that need to be taken.
Who is it recommended for?
The three levels of service include the fully managed SIEM service, where UnderDefense installs, maintains, and provides cybersecurity advice; the co-managed SIEM service, offering security advice and support; and the SIEM technical support option, assisting you in maintaining the SIEM software.
Pros:
- Full Range of Cybersecurity Software: Vulnerability management, SIEM, and compliance management
- Scaleable Prices: Pay-as-you-go pricing model
- Customization Options: The client can choose from 1000+ correlation rules tailored to your needs
- Proactive Hunting for Anomalies: Real-time correlation of hosts, risks, vulnerabilities, and threats
- Actionable Context for Threat Severity: Allows immediate reaction to threats
Cons:
- Wide Range of Cybersecurity Service in One Package: Best suited for enterprises and large networks
You can get your first month for free.
EDITOR'S CHOICE
UnderDefense is our top choice for a managed SIEM service because of its unique co-managed solution. The ability to pool expert advice 24/7 that is constantly exposed to identifying and dealing with threats instead of relying on an internal team makes UnderDefense a natural choice for organizations that lack budgets to run in-house security teams.
Download: Try it for Free
Official Site: https://underdefense.com/services/underdefense-siem/
OS: Cloud-based
2. Ideal Smart Managed Cybersecurity
Ideal is a consultancy that provides advice and plans for the implementation of IT in smart buildings. The company also runs a Security Operations Center from which it operates as a managed security service provider (MSSP). The company recommends using Microsoft security products.
Key Features:
- Remote SOC: Fully staffed with cybersecurity experts
- Customizable Plans: Tailored service
- Constant Vigilance: SOC active 24/7
- Compliance Reporting: Automatically generated
Why do we recommend it?
The Ideal Smart Managed Cybersecurity service is a bespoke SOC service that is designed to support smart building systems, which include IoT and OT devices along with traditional computers and networks. The company designs these networks as well and helps provides security advice during the creation of a smart building.
The Ideal Smart Managed Cybersecurity takes all of the security tasks from its customers. The typical customer of Ideal Smart Managed Cybersecurity is a company that has an IT department but doesn’t have any cybersecurity expertise on staff. The service is manned around the clock to ensure that there are no times of the day when intrusion could be made easier. The consultants of Ideal assist their customers in creating security that complies with any data protection standard. The technicians will also assist compliance auditors and provide all of the necessary documentation to prove security or declare any breaches.
Who is it recommended for?
Businesses that hire Ideal to help them set up a smart building are the most likely candidates for the company’s managed security service. Smart buildings involve a lot of sensors, which often have weak security and so need to be bolstered with Zero Trust Network Access routines and constant monitoring.
Pros:
- Great Fit for Organizations with Little to No In-House IT Staff: In places where there are few cybersecurity experts or those that have high wages
- Provides Cybersecurity Monitoring: Also IoT and smart building management
- Ad-Hoc Consultancy: Techs offer compliance assistance and assistance managing breaches
- Also Offers Other Services: Network consultancy, cloud and data center consultancy
Cons:
- No Co-Managed Option: No price list
The Ideal Smart Managed Cybersecurity service is a tailored solution and so there is no fixed price. The fee is set after a consultation that assesses the exact security needs of the new customer.
3. Nomios Managed SIEM
As with most of the managed SIEM solution on this list, the Nomios Managed SIEM is a service that grew out of a cybersecurity consultancy. The business has been in operation since 2005 and specializes in security advice for multinational, telecom services, and managed service providers. The company’s staff includes more than 170 certified engineers.
Key Features:
- Custom Plans: Tailored cybersecurity service
- Consultancy Available: Services of security experts
- Support for Purchases: Cloud-based solution or the SIEM software of choice
Why do we recommend it?
Nomios Managed SIEM is one of the security options you can choose from the Nomios MSSP. This company will provide technicians to run your SIEM or XDR and can also advise on software purchases. However, as with the UnderDefense service, the security software is not included in the deal.
Nomios advises businesses on cybersecurity strategies and software purchases. The MSP division of Nomios offers managed SD-WAN, managed firewalls, managed detection and response, and vulnerability and compliance management services as well as the managed SIEM system.
Nomios is based in Basingstoke in the UK but it supports customers all over the world through offices in seven countries. The service’s customer base is spread across 50 countries. The SIEM service doesn’t have a fixed price because it is a tailored service that is assembled from different specialist services.
Who is it recommended for?
This is a good choice if you have already had advice on which type of security you need but you either can’t find the staff to run it or don’t want the burden of cybersecurity experts on your payroll. If you don’t have any security software as yet, Nomios can help you decide what to buy.
Pros:
- Highly Qualified Technicians: Staff includes over 170 certified engineers
- Not Just Cybersecurity: Offers managed SD-WAN, intrusion detection, and vulnerability management
- Through Selling: Offers services that cater to MSP environments
Cons:
- No Co-Managed Option: Just consultancy and managed security services
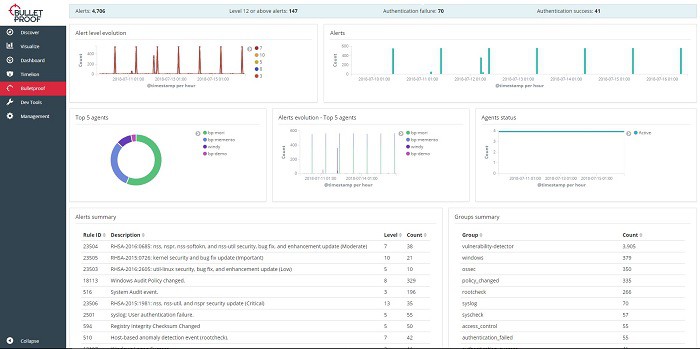
4. Bulletproof Managed SIEM
Bulletproof is a cybersecurity consultancy that offers vulnerability assessments, penetration testing, and a managed SIEM service. While many MSPs use cloud servers provided by the likes of AWS, Google, or Digital Ocean, Bulletproof owns all of its own infrastructure. The company uses its own cyber threat defense skills to ensure its own servers are free from intrusion.
Key Features:
- Scalable Pricing: Choose your services
- Fully Owned Infrastructure: Doesn’t rely on third-party cloud platforms
- Proprietary SIEM Software: Also offers penetration testing and vulnerability manager
Why do we recommend it?
Bulletproof Managed SIEM comes from an outstanding brand in cybersecurity – the company is also a certified trainer in the most important cybersecurity industry qualifications. Bulletproof runs its own SIEM and by subscribing to it, you get cybersecurity consultancy bundled in with it. Your security will be handled off site.
The Bulletproof SIEM platform is a proprietary system that includes user and entity behavior analysis. This is an AI-based process that uses machine learning to establish a baseline of normal behavior for each user account. UEBA is useful for preventing false-positive reporting that could target and lock out legitimate users. It is able to spot accounts that have been hijacked and also identifies dormant accounts that are vulnerable to takeover.
Bulletproof consultants examine the results of alerts raised by the SIEM software and perform root cause analysis to investigate whether an unusual event really does indicate malicious activity. They are then able to take action to block off the intruder and prevent data loss.
The service also supports the data standards compliance needs of its customers, providing assistance to compliance auditors and furnishing all necessary documentation for reporting.
The Bulletproof tariff is charge by subscription per protected node per month.
Who is it recommended for?
The Bulletproof solution is like paying for a cloud-based SIEM that includes a server to run the security software vans storage space for gathered logs, except in this case, you also get a team to run the system, analyze alerts, and implement threat remediation.
Pros:
- AI Efficiency: Leverages machine learning to monitor each environment for threats
- Data Governance: Supports compliance management and auditing
- Immediate Resolution Solutions: The platform provides root cause analysis
Cons:
- Requires a Long-Term Commitment: Geared towards enterprise clients
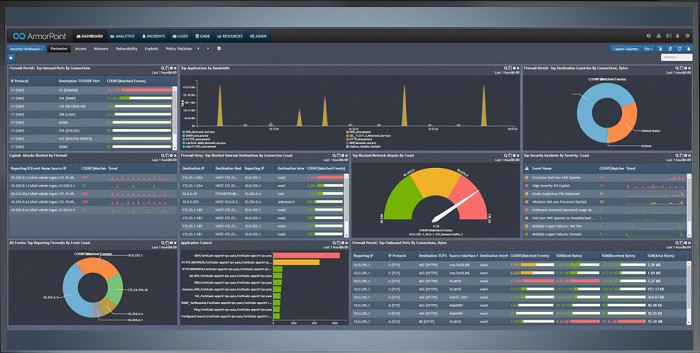
5. ArmorPoint
ArmorPoint Managed SIEM service also includes system performance monitoring. The technicians for the service include IT incident management routines, so they can back up and restore data to ensure service continuity. The service begins with an asset discovery phase, which is a great feature to help disorganized businesses get on top of their asset inventory. This record of equipment gets updated automatically whenever the IT resources of the customer change.
Key Features:
- Security Monitoring: System performance monitoring included
- Requirements Assessments: Cybersecurity consultancy included
- Alert Management: Technician assessments focus on the more important warnings
Why do we recommend it?
ArmorPoint offers a cloud-based SIEM, which you can subscribe to. The next level up is its Managed SIEM option, which provides a cybersecurity team to run your ArmorPoint SIEM instance for you. The team will analyze the messages of the SIEM tool and implement or recommend actions for threat remediation.
The security system offered by ArmorPoint includes event log management, event correlation, threat detection and response, automated mitigation procedures, and standard compliance reporting. The service uses machine learning processes in user and entity behavior analysis to refine the accuracy of the SIEM’s alerts.
Customers get access to the SIEM dashboard for informational purposes. The system console is attractive and includes data visualizations, such as graphs and charts. This can be useful for internal reporting and team goal discussions. However, none of the staff of a client of ArmorPoint need to intervene in the security process. All human expertise is provided in with the ArmorPoint Managed SIEM package.
The Managed SIEM service is offered in three plan levels and each is available for a free trial. The ArmorPoint SIEM services are also available on a SaaS basis for those businesses that want to manage their security themselves. All plans are priced by monthly subscription.
Who is it recommended for?
This is a good option if you know you need a SIEM but you don’t have anyone on staff to set it up or run it. The ArmorPoint technicians work at the service’s Security Operations Center, so you will never see any of them on your site.
Pros:
- Clients Get Activity Views: Displays SIEM information through an informative dashboard
- Uses Machine Learning and Data Science: Pinpoints threats and prevent attacks
- Deployment Options: Offers both managed and SaaS options
Cons:
- No Fixed Plans: Need a consultation to arrive at a quote
6. Redscan Managed SIEM
Redscan Managed SIEM includes a hosted SIEM system, human experts to analyze findings and a threat intelligence feed. The service operates 24/7 from the Redscan Security Operations Center. Redscan is able to support clients all over the world and will monitor single-site networks, cloud services, hybrid systems, and multi-site infrastructure.
Key Features:
- Fully Managed Service: Includes the SIEM software hosted on the cloud
- Constant Manned Monitoring: 24/7 activity
- Compliance Support: A tailored package
Why do we recommend it?
Redscan Managed SIEM is a co-managed SIEM solution. Businesses that need to buy a SIEM can contract Redscan to assess the company’s system, recommend which SIEM to buy, and then assist in analyzing its output. Companies that already have a SIEM can get advice on how to get the best out of it.
Redscan also offers alternative managed cybersecurity services. These include a managed intrusion detection system, a managed endpoint detection and response service, managed behavioral monitoring, and vulnerability management. The company can also perform one-off penetration testing and vulnerability assessments of any client system.
Redscan is an experience managed security service provider that has a SOC that is operational around the clock and always has cybersecurity experts on-site to assess SIEM results and recommend mitigation actions. The service is fully compliant with PCI DSS and GDPR and the support team is able to provide all of the documentation that clients need for compliance reporting.
Who is it recommended for?
A customer of the Redscan Managed SIEM would already have security staff in its IT department but perhaps, not enough of them, and possibly their knowledge isn’t quite deep enough to cope with all of the alerts that come out of the SIEM. Redscan provides that added expertise.
Pros:
- Manual Services: Penetration testing and Web application testing
- Provides Compliance Services: For PCI, DSS, and HIPAA
- Machine Learning: Provides behavioral monitoring baselining
Cons:
- No Co-Managed Option: Only available as a fully managed solution
Choosing a Managed SIEM Service provider
Small businesses and startups that don’t have the office space or work volume to justify having an in-house cybersecurity team should certainly opt for a managed SIEM service.
Cyberattacks have removed the ease of doing business on the Internet. An attack can ruin an enterprise that is dependent on connectivity for the success of its business plan. A managed SIEM service evens the score and removes the threat of ruinous attacks.
Best Managed SIEM Services FAQS
What is a managed SIEM service?
SIEM stands for Security Information and Event Management. It is a security package that checks through log files for signs of malicious activity and also watches over network traffic. The system produces warnings about possible security breaches. You need a security analyst on staff to look through the SIEM output and work out whether warnings represent serious threats and then decide what to do about it. You can subscribe to cloud-based SIENMs, which means you don’t have to host the software for the package. A managed SIEM goes one step further because not only is the software hosted, with maintenance technicians provided, but you also get the services of security specialists to assess the SIEM’s alerts.
Which is better SIEM or soar?
SIEM is a security package that gathers data from network traffic monitoring and system logs. SOAR is Security Orchestration, Automation, and Response. A SOAR system coordinates the activities of existing security services, such as access rights managers and firewalls. SOAR is a newer system than SIEM and it includes automated responses, such as blocking traffic from suspicious IP addresses or suspending compromised user accounts. SIEM services don’t necessarily include any response mechanisms – although some SIEM producers include these. The relative superiority of SIEM or SOAR comes down to the competence of the individual package. While SOAR is more comprehensive than SIEM, some SIEM systems and extensive and a lot better than many SOARs on the market.
Will XDR replace SIEM?
XDR Is very similar to a SIEM. THE XDR system focuses on collecting data from endpoints and adds in data collected from system security services, such as firewalls and access rights manager. Effectively, the two systems perform the same task. While an XDR usually includes an agent installed on every endpoint, a SIEM only requires one agent connected to the network to gather information from all devices on the network. A very comprehensive XDR endpoint agent can implement device security measures even when the device is disconnected from the network. An XDR with a very slim device agent has almost identical capabilities to a SIEM.