Rapid7 insightIDR uses innovative techniques to spot network intrusion and insider threats. By using all of the insights that the multi-pronged SIEM approach can offer, insightIDR speeds up the detection process and shuts the attack down.
The SIEM strategy
SIEM is a composite term. It combines SEM and SIM. SEM stands for Security Event Management; SEM systems gather activity data in real-time. SIM stands for Security Information Management, which involves scanning through log files for signs of suspicious activities. SIEM combines these two strategies into Security Information and Event Management.
Traditional intrusion detection systems (IDSs) capture traffic data and examine the headers of packets to analyze activity. An IDS monitor quickly categorizes all traffic by source and destination IP addresses and port numbers. These two identifiers can then be referenced to specific devices and even specific users. The port number reference can explain the protocols and applications that each transmission relates to. This is the SEM strategy.
SEM is great for spotting surges of outgoing data that could represent data theft. However, it can’t tell whether an outbound file is a list of customer credit cards or a sales pitch going out to a potential customer. When contents are encrypted, SEM systems have even less of a chance of telling whether a transmission is legitimate. Identifying unauthorized actions is even harder if an authorized user of the network is behind the data theft.
An SEM strategy is appealing because it is immediate but speed is not always a winning formula. SIM offers stealth. It involves processing both event and log messages from many different points around the system. It looks for known combinations of actions that indicate malicious activities. SIM is better at identifying insider threats and advanced persistent threats because it can spot when an authorized user account displays unexpected behavior. So, it can identify data breaches and system attacks by user account, leading to a focus on whether that account has been hijacked or if the user of that account has been coerced into cooperation. SIEM offers a combination of speed and stealth.
About Rapid7
Rapid7 has been working in the field of cyber defense for 20 years. The company operates a consultancy to help businesses harden their systems against attacks and it also responds to emergency calls from organizations under attack.
As well as testing systems and cleaning up after hackers, the company produces security software and offers a managed security service.
Key Features:
- User Behavior Analysis: Leverages machine learning to distinguish between legitimate user activities and potential security threats.
- Attacker Behavior Analytics: Utilizes historical data on hacker groups to predict and neutralize subsequent stages of an attack.
- Endpoint Defense: Employs the Insight Agent on each device for continuous protection and data collection, even when offline.
- Network Traffic Monitoring: Analyzes network data in real-time and for log consolidation, aiding in intrusion detection and response.
- Centralized Log Management: Gathers and standardizes log data across the network, storing it securely for up to 13 months.
- File Integrity Monitoring: Ensures critical files and logs remain untampered, complying with major data security standards.
Rapid7 operates a research lab that scours the world for new attack strategies and formulates defenses. The lab uses the companies’ own tools to examine exploits and work out how to close them down. The most famous tool in Rapid7’s armory is Metasploit. This is an open-source project that produces penetration testing tools. When Rapid7 assesses a client’s system for vulnerabilities, it sends a report demonstrating how the consultancies staff managed to break that system.
Pros:
- Advanced Threat Detection: Uses behavioral analytics to identify threats that traditional, signature-based methods might miss.
- Comprehensive Threat Intelligence: Integrates various data sources for a nuanced threat analysis approach.
- Proactive Remediation Strategies: Facilitates prompt automated responses to identified security threats.
Cons:
- Premium Pricing: The cost is on the higher side compared to similar cybersecurity tools.
- Additional Costs for Features: Some functionalities may require further investment in paid add-ons.
insightIDR is part of the menu of system defense software that Rapid7 developed from its insights into hacker strategies. Rapid7 offers a free trial.
insightIDR Features
InsightIDR is an intrusion detection and response system, hosted on the cloud. The intrusion detection part of the tool’s capabilities uses SIEM strategies. The log that consolidations parts of the system also perform log management tasks. The tool even extends beyond typical SIEM boundaries by implementing actions to shut down intrusions rather than just identifying them.
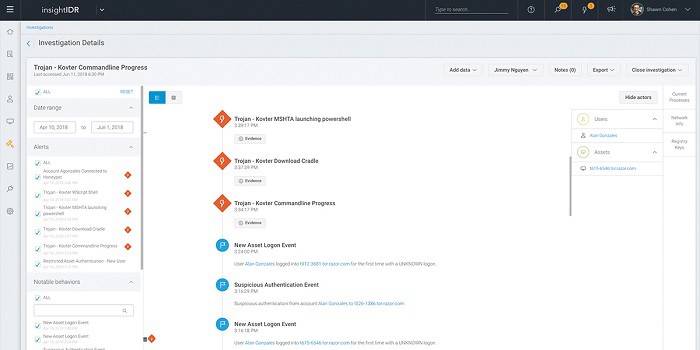
Mechanisms in insightIDR reduce the incidences of false reporting. With so many different data collection points and detection algorithms, a network administrator can get swamped by a diligent SIEM tool’s alerts. Information is combined and linked events are grouped into one alert in the management dashboard. insightIDR reduces the amount of time that an administrator needs to spend on monitoring the reports of the system defense tool.
Here are some of the main elements of insightIDR.
User Behavior Analytics
A big problem with security software is the false positive detection rate. Many intrusion protection systems guarantee to block unauthorized activity but simultaneously block everyone in the business from doing their work.
The only solution to false positives is to calibrate the defense system to distinguish between legitimate activities and malicious intent. The User Behavior Analytics module of insightIDR aims to do just that. This module creates a baseline of normal activity per user and/or user group. If patterns of behavior suddenly change, the dense system needs to examine the suspicious accounts. They may have been hijacked.
Observing every user simultaneously cannot be a manual task. However, it is necessary in order to spot and shut down both typical and innovative hacker account manipulation strategies. This task can only be performed by an automated process. It requires sophisticated methodologies, such as machine learning, to prevent the system from blocking legitimate users.
Attacker Behavior Analytics
Attacker Behavior Analytics (ABA) is the ace up Rapid7’s sleeve. This feature is the product of the service’s years of research and consultancy work. Rapid7 analysts work every day to map attacks to their sources, identifying pools of strategies and patterns of behavior that each hacker group likes to use.
The research of Rapid7’s analysts gets mapped into “chains of attack”. If Hacker Group A got in and did X, you’re probably going to get hit by Y and then Z because that’s what Hacker Group A always does. So, Attacker Behavior Analytics generates warnings. As soon as X occurs, the team can harden the system against Y and Z while also shutting down X.
Endpoint Protection
The analytical functions of insightIDR are all performed on the Rapid7 server. This is great for lightening the load on the infrastructure of client sites, but it introduces a potential weakness. Not all devices can be contacted across the internet all of the time. If all of the detection routines are remotely based, a savvy hacker just needs to cut or intercept and tamper with that connection.
To combat this weakness, insightIDR includes the Insight Agent. This is a piece of software that needs to be installed on every monitored endpoint. The Insight Agent is able to function independently and upload data or download updates whenever a connection becomes available. While the monitored device is offline, the agent keeps working.
In the SIEM model, the Insight Agent’s activities amount to the collection of event and log messages and also the generation of original log records through real-time monitoring. While a connection is maintained, the Insight Agent streams all of this log data up to the Rapid7 server for correlation and analysis. However, the agent is also capable of raising alerts locally and taking action to shut down detected attacks.
Endpoints are the ideal location for examining user behavior with each agent having only one user to focus on. Insights gleaned from this monitoring process is centralized, enabling the Rapid7 analytical engine to identify conversations, habits, and unexpected connections. User monitoring is a requirement of NIST FIPS.
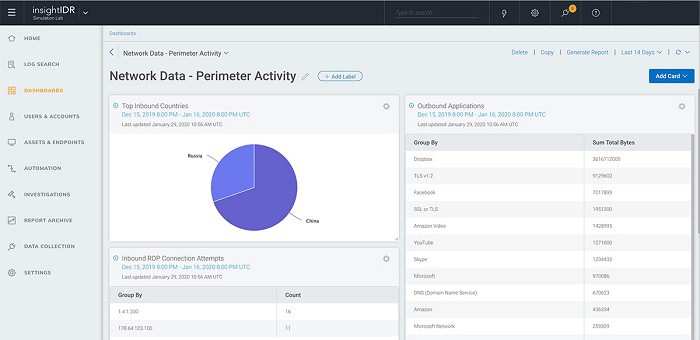
Network Traffic Analysis
The SEM part of SIEM relies heavily on network traffic monitoring. The Network Traffic Analysis module of insightIDR is a core part of the SEM sections of the system.
The data sourced from network monitoring is useful in real-time for tracking the movements of intruders and extracts also contribute to log analysis procedures. So, network data is part of both SEM and SIM procedures in Rapid7 insightIDR.
Centralized Log Management
SIM methods require an intense analysis of the log files. In order to complete this work, log messages need to be centralized, so all the event and syslog messages, plus activity data generated by the SEM modules, get uploaded to the Rapid7 server. SIM requires log records to be reorganized into a standard format. So, as a bonus, insightIDR acts as a log server and consolidator.
insightIDR stores log data for 13 months. For the first three months, the logs are immediately accessible for analysis. For the remaining 10 months, log data is archived but can be recalled. Data is protected by encryption while in storage, so this solution enables you to comply with a range of data security standards, including SOX and PCI DSS.
File Integrity Monitoring (FIM)
File Integrity Monitoring (FIM) is a well-known strategy for system defense. It is particularly important to protect log files from tampering because intruders covering their tracks will just go in and remove incriminating records.
Several data security standards require file integrity monitoring. These include PCI DSS, HIPAA, and GDPR. So, the FIM module in insightIDR is another bonus for those businesses required to follow one of those standards. They won’t need to buy separate FIM systems.
This function is performed by the Insight Agent installed on each device. The console of insightIDR allows the system manager to nominate specific directories, files, or file types for protection. Pre-written templates recommend specific data sources according to a particular data security standard.
Protecting files from tampering averts a lot of work that would be needed to recover from a detected intruder. Companies don’t just have to worry about data loss events. Data security standards allow for some incidents. However, your company will require compliance auditing by an external consultancy and if an unreported breach gets detected, your company will be in real trouble.
Deception Technology
SIEM systems usually just identify possible intrusion or data theft events; there aren’t many systems that implement responses. Rapid7 insightIDR is one of the very few SIEM systems that deploy shrewd technology to trap intruders. Deception Technology is the insightIDR module that implements advanced protection for systems.
The Detection Technology strategy of insightIDR creates honeypots to attract intruders away from the real repositories of valuable data by creating seemingly easy ways into the system. These false trails lead to dead ends and immediately trip alerts. The techniques used in this module were developed by the Metasploit Project and also the Heisenberg Project and Project Sonar. These are ongoing projects, so the defense systems of insightIDR are constantly evolving to account for hacker caution over previous experience with honeypots.
Automation
IDR stands for “incident detection and response”. Task automation implements the “R” in IDR. The response elements in insightIDR qualify the tool to be categorized as an intrusion prevention system. Typically, IPSs interact with firewalls and access rights systems to immediately block access to the system to suspicious accounts and IP addresses.
Other account monitoring functions include vulnerability scanning to spot and suspend abandoned user accounts. Rapid7 insightIDR deploys defense automation in advance of any attack in order to harden the protected system and also implements automated processes to shut down detected incidents.
Alternatives to Rapid7 insightIDR
insightIDR is a comprehensive and innovative SIEM system. However, it isn’t the only cutting edge SIEM on the market. To learn more about SIEM systems, take a look at our post on the best SIEM tools.
If you don’t have time to read a detailed list of SIEM tool reviews, here is a quick list of the main competitors to Rapid7 InsightIDR.
- SolarWinds Security Event Manager (FREE TRIAL) A SIEM tool from SolarWinds that includes real-time incident response. This software installs on Windows Server and includes compliance monitoring and reporting out of the box. Start a 30-day free trial.
- ManageEngine EventLog Analyzer (FREE TRIAL) Provides SIM functions and can be paired with Log360 for SEM services. It installs on Windows and Linux. Start a 30-day free trial.
- Datadog Security Monitoring A cloud-based SIEM system integrated into a network monitoring tool.
- McAfee Enterprise Security Manager A SIEM tool that focuses on managing and querying Active Directory. It installs on Windows and Mac OS.
- Fortinet FortiSIEM A close competitor to insightIDR that includes a range of detection tactics plus automated defense responses.
- Splunk Enterprise Security A well-known network scanner that includes analysis functions and log management capabilities. It installs on Windows and Linux.
- OSSEC A free open-source IDS with strong log analysis routines. It installs on Windows, Mac OS, Linux, and Unix.
- LogRhythm NextGen SIEM Platform It uses AI techniques in traffic and log analysis. It installs on Windows and Linux.
- AT&T Cybersecurity AlienVault Unified Security Management A strong IDS that implements a range of detection strategies including SIEM. It installs on Windows and macOS.
InsightIDR FAQs
What is InsightIDR?
Insight IDR is a cloud-based SIEM system that collects log messages and live network activity information and then searches through that data for signs of malicious activity.
Is InsightIDR a SIEM?
Yes. InsightIDR is a SIEM. It is delivered as a SaaS system.
What is Rapid7 insight agent used for?
Rapid7 operates a SaaS platform of cyber security services, called Rapid7 Insight, that, being cloud-based, requires a data collector on the system that is being protected. This collector is called the Insight Agent. If the company subscribes to several Rapid7 Insight products, the Insight Agent serves all of them.
Does Rapid7 have a SIEM?
Rapid7 offers a range of cyber security systems from its Insight platform. Of these tools, InsightIDR operates as a SIEM.