Many organizations understand they need network protection from threats outside of their networks. But what happens when the threat comes from inside? In this article, we’ll dive into some of the best insider threat detection tools you can use to protect your assets from rogue internal threats.
Here’s our list of the best insider threat detection tools:
- ManageEngine Endpoint DLP Plus (FREE TRIAL) This data loss prevention system tracks user access to sensitive data in order to spot insider threats on all endpoints. Runs on Windows Server. Get a 30-day free trial.
- ManageEngine Log360 (FREE TRIAL) This software package provides a threat-hunting SIEM that looks for unexpected behavior by software and by user accounts, which is ideal for spotting insider threats. Runs on Windows Server. Start 30-day free trial.
- ESET Protect (FREE TRIAL) A hybrid threat detection and response solution. Runs on Windows, macOS, Linux, iOS, and Android. Start a 30-day free trial.
- UnderDefense MAXI Platform This Security-as-a-Service deal provides a support team to manage your security software for you with a scaleable package that is suitable for businesses of all sizes.
- SolarWinds Security Event Manager Gives the best combination of insider threat control and flexibility.
- SentinelOne Singularity Platform This cloud-based system is an XDR, which gathers activity data from endpoints and security systems for insider threat detection and malware scanning.
- Datadog Security Monitoring Provides excellent pre-configured rules for fast deployment.
- PRTG Monitor Uses a specialized sensor to track user behavior.
- Splunk Uses peer group analytics to track both groups and individuals.
- ActivTrak Offers extensive threat detection paired with efficiency insights.
- Code42 Allows for extensive intellectual property protection and data monitoring.
The best Insider Threat Detection tools
Our methodology for selecting an insider threat detection tool
We reviewed the market for insider threat detection systems and analyzed tools based on the following criteria:
- A system that uses machine learning to establish a baseline of normal activity
- A package that looks for secondary indicators of a threat before fully flagging an intrusion
- A service that includes alerts to draw the attention of technicians
- Recommendations for access rights management tightening
- Options to feed data through to analysis tools
- A free trial or a demo system for a cost-free assessment
- Good value for money from a tool that offers full-features intrusion detection at a sensible price
With these selection criteria in mind, we identified some affordable and effective insider threat detection tools.
1. ManageEngine Endpoint DLP Plus (FREE TRIAL)
ManageEngine Endpoint DLP Plus implements insider threat detection that focuses its user activity tracking on access to sensitive data. Many insider threat identification systems deploy AI-based user and entity behavior analytics (UEBA) for all user activity, but the ManageEngine package’s strategy is more lightweight because it is limited to file activity.
Key Features:
- On-Premises Software Pack: Runs on Windows Server
- Data Risk Management: Scans for sensitive data, records its location, and categorizes it
- Protection Mechanisms: Based on access rights and activity tracking
Why do we recommend it?
ManageEngine Endpoint DLP Plus is a data protection and compliance management package that extends to user activity tracking or insider threat detection. The system identifies sensitive data and then constructs strategies to protect it. The biggest threats these data locations will face are from the users of authorized accounts.
The Endpoint DLP Plus software package needs to be installed on one server. All of the other endpoints in the system are monitored over the network. This configuration creates one central console for the entire business. An extension to the standard package can reach out to remote sites, thus allowing a security operations center to track activity at all locations.
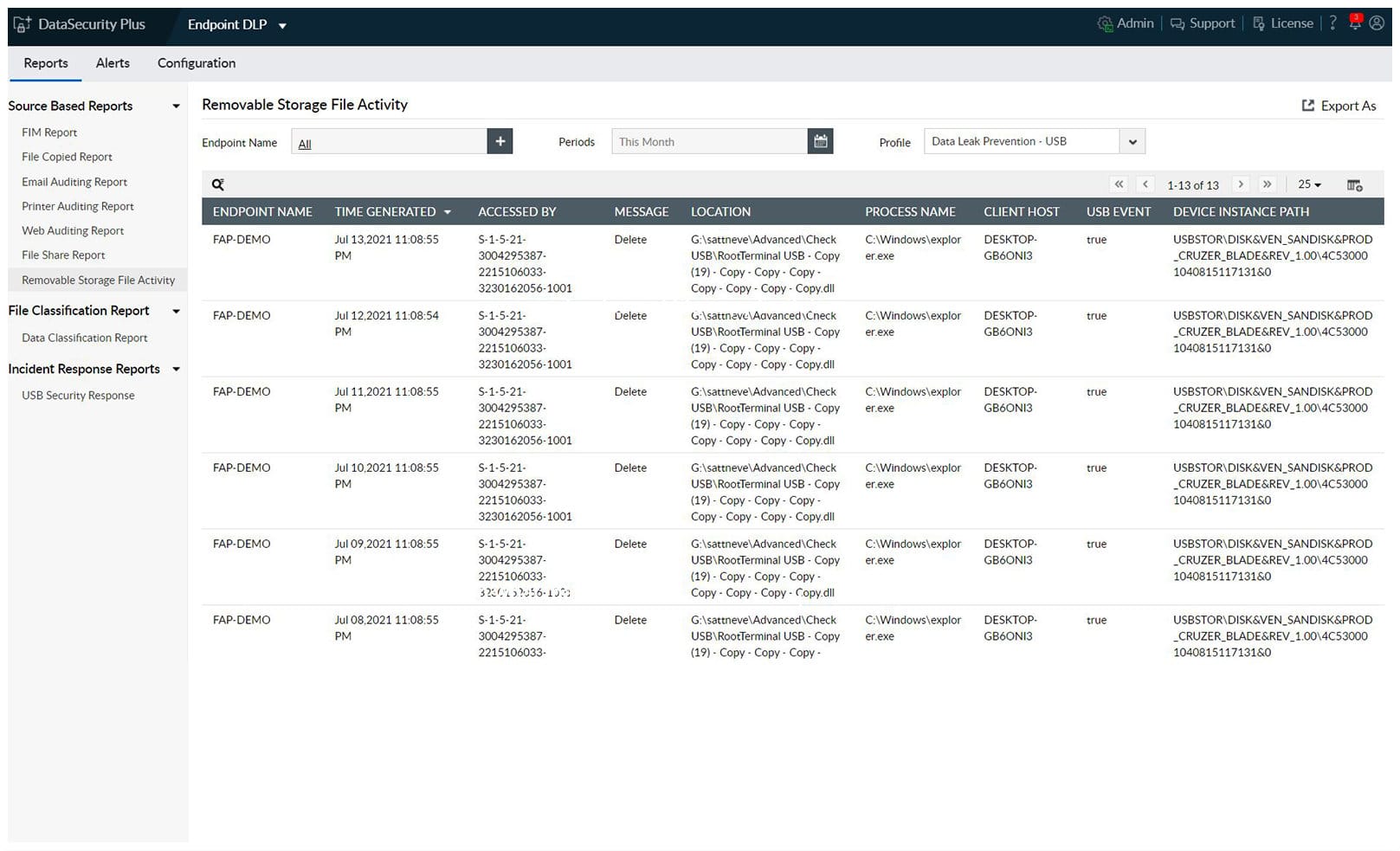
The important setup task with any data security system is to create a definition of what is considered to be “sensitive” data. The dashboard of Endpoint DLP Plus includes a library of policy templates that provide preset definitions and controls. There are templates for all of the major data protection standards and it is also possible to create your own.
Applying a template creates a security policy that sets down rules over which user groups can access, modify, or delete different types of sensitive data. These controls extend to the supervision of USB storage devices, email systems, and file transfer services to cloud platforms.
The ManageEngine service performed a sweep of all endpoints to identify sensitive data stores. The tool is able to process document images with OCR and it can spot collections of fields, which, by their proximity, create a composite sensitive data record. The DLP then categorizes each instance of data that was identified.
The categorization of sensitive data into different types allows for a filer detail of control by allowing some actions to be performed on one category that could be blocked on another. The system also allows you to define trusted applications that generate or process sensitive data. The service will block exports of data from these privileged software packages to unauthorized applications.
The DLP system will raise an alert if suspicious activity has been identified. You can set up rules to let the package automatically deal with these events or leave responses to manual processes.
Who is it recommended for?
ManageEngine provides a Free edition of the Endpoint DLP Plus system. This is ideal for small businesses because it will supervise up to 25 endpoints. The system is reasonably priced for larger enterprises and it can manage data on multiple sites from one control panel.
Pros:
- Application Whitelisting: Designates a limited number of software packages that can access data
- Containerization: Protect files with encryption
- Data Movement Controls: Memory sticks, email, cloud uploads
Cons:
- No SaaS Option: Only available for Windows Server
The software for ManageEngine Endpoint DLP Plus installs on Windows Server. There are two editions available: Free and Professional. The Free option is limited to monitoring data on 25 endpoints. The paid version is called the Professional Edition. You can assess the Professional plan on a 30-day free trial.
2. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 is a collection of security systems that is centered on a SIEM. This threat detection system relies on log files for source data and so the package also includes a log manager. The threat hunting service is anomaly based and it deploys user and entity behavior analytics (UEBA) to establish a pattern of regular behavior per user account and per device. Typical insider threats suddenly change their pattern of activity and this would raise a flag in the Log360 system.
Key Features:
- Super Pack of Tools: A bundle of seven ManageEngine modules
- A SIEM Service: Automated threat detection
- Compliance Management: For PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA
Why do we recommend it?
ManageEngine Log360 tracks user activities both on-premises and on cloud platforms. The tool includes a SIEM service that spots all types of threats. A CASB in the bundle provides access controls for cloud services and feeds activity logs to the SIEM. The tool examines user activity and identifies unusual behavior that could indicate an account takeover.
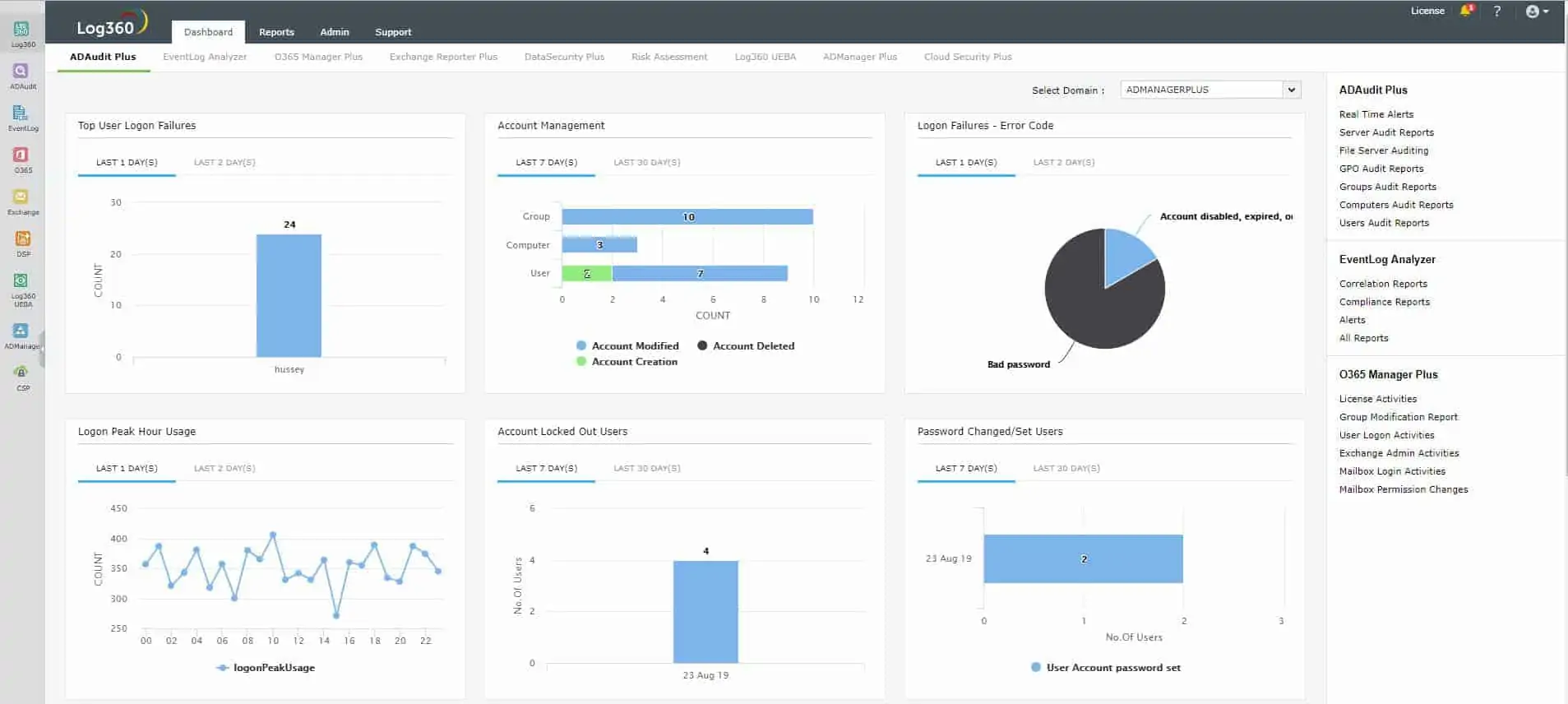
The log collector gathers activity data from operating systems, network devices, applications, software packages, and third-party security tools. The SIEM builds a profile of each user account, which examines which endpoints, software packages, and data servers each account regularly uses. This creates a profile of the resources that the employee needs to access in order to perform authorized duties.
If a user intends to steal or sabotage, there needs to be a change in activity, such as moving or deleting data or trying to bypass system access controls. It is this type of new activity that the anomaly-based SIEM spots.
The Log360 system also includes a SOAR system. This means “security orchestration, automation, and response.” This unit coordinates the capabilities of all of the units in the Log360 package and also accesses the services of third-party tools. This coordination is performed to automate responses to detected threats.
Examples of automated responses include instructing a firewall to block communications from and to a specific IP address or suspending a user account in the access rights manager – which is usually Active Directory. The suspension of an account is the most likely action to deal with an insider threat. While performing this task, Log360 will also send a notification to the technician team. This can be implemented as a ticket sent into a Help Desk system, such as ManageEngine Service Desk Plus.
Other measures in the Log360 include file access logging and Active Directory auditing. The assessment of AD is important to block account takeover, which can be implemented by capturing an abandoned account or by getting the user to disclose access credentials. An account takeover event can be dealt with by prompting all users to change passwords and the risk can be reduced by forcing users to regularly alter credentials.
Log360’s user access controls and activity logging extends to cloud services. The full system provides auditing and reporting functions for standards compliance. These are suitable for businesses that need to comply with PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA.
Who is it recommended for?
This package is suitable for use by a large organization. In fact, it provides all of the systems that a central, corporate Security Operations Center (SOC) would need. The bundle also provides data loss prevention, user activity tracking, file integrity monitoring, and Active Directory auditing.
Pros:
- Log Management: Collects, consolidates, and files log messages
- Insider Threat Detection: User behavior analytics
- Automated Responses: Sends instructions to third-party tools
Cons:
- No Cloud Version: Only available for Windows Server
ManageEngine Log360 is delivered as a software package for Windows Server. You can assess the package with a 30-day free trial.
3. Eset Protect (FREE TRIAL)
ESET Protect is a cybersecurity package that offers a hybrid solution to threat detection with on-device elements and a cloud-based coordinator. This service looks for automated threats, such as malware, and human threats, which include intruders and malicious or duped insiders.
Key Features:
- Endpoint Protection: Centered on an antivirus package
- User Activity Tracking: Insider threat detection
- Automated Responses: Threat remediation is included in higher plans
Why do we recommend it?
The ESET Protect system searches for all types of threats, not just insider threats. Not all categories of attacks can be pigeonholed into an insider threat, an intrusion, or malware because many attack strategies involve all three elements. By looking for unusual activity, this service implements stronger protection.
ESET produces four plan levels of the Protect range and the first of these is an on-device software package that scans locally for threats and deals with them. That software is available for Windows, macOS, Linux, iOS, and Android.
All editions of ESET Protect include a cloud console, which receives activity reports from those endpoint units. In the lowest plan, which is called ESET Protect Entry, that console only reports on wheat the endpoint units have been doing.
The cloud system gets more interesting in the ESET Protect Advanced edition. This plan gives you a unified threat hunting service that mines uploaded activity reports for signs of threats. This system supplements the local threat hunting of the on-device unit. It can take a company-wide view of threats and this is particularly important for those user account-based attacks that can be implemented with an account takeover. The system can spot attempts to move from one endpoint to another and it can also identify illogical account activity, such as the same account being used for multiple simultaneous sessions.
The Advanced plan provides threat defense in the form of a cloud-based sandboxing service. This enables suspicious software to be tested without any risk to the protected endpoints. The next plan up has far more defense services. This is ESET Protect Complete and it provides a vulnerability manager and a patch manager for system hardening.
The Complete plan also gives you protection for cloud packages, such as Microsoft 365 and it will scan your email systems both on-premises and on the cloud. This service sends its response instructions to the ESET on-device units. The ESET Protect Elite option extends those response actions to third-party systems. This is particularly necessary for insider threats because the obvious solution to a detected malicious insider action is to reach into your access rights manager and suspect that user’s account.
All ESET Protect editions are available in a multi-tenanted architecture for managed service providers. ESET acts as a managed security service provider itself with its ESET Protect MDR, which is a Managed Detection and Response package.
Who is it recommended for?
The ESET Protect system has editions for all sizes and types of businesses. Small businesses don’t have many endpoints and so don’t need extensive cloud-based threat hunting; on-device threat detection is enough. Large corporations need much more complex solutions for their hybrid systems, which ESET provides with its highest plans.
Pros:
- Extends to Mobile Devices: Security protection covers workstations, servers, and mobile devices
- Anomaly-Based Detection: Looks for unusual activity
- Dual-Level Threat Detection: Threat hunting on each device and on a central server
Cons:
- Doesn’t Cover Network Security: Entirely focused on endpoints
Most ESET Protect plans require a minimum of five devices; the Elite edition starts with a minimum of 26 devices. ESET Protect is available for a 30-day free trial.
4. UnderDefense MAXI Platform
The UnderDefense MAXI Platform provides a team of cybersecurity experts to support the security software of your choice. This service is ideal for businesses that just can’t have security staff on the payroll.
Key Features:
- Security-as-a-Service: This is a remote system management team
- Security Software Acquisition: The team will help you identify and buy the right software
- System Configuration: Get all of your security software set up and calibrated
- Security Management: The team forms a Security Operations Center
- Assesses Security Alerts: The team looks through log files to examine the reasons for security alerts
Why do we recommend it?
UnderDefense MAXI Platform is a service rather than a package. This system gives subscribers access to a team of cybersecurity experts who will monitor your security monitoring software for you. The team can access any network anywhere in the world over the internet and the company provides shifts so support is active 24/7.
The Under Defense team doesn’t lock you into a specific security package. You can subscribe to this service if you already have your threat detection and response software in place. If you don’t, the UnderDefense team will advise you on the best systems to buy.
The team can install your security software or you and keep it up to date. However, this is the extent of the remote software management services of UnderDefense because it doesn’t provide a general system maintenance plan. The technicians only watch over your security monitoring systems.
Many security packages will implement responses automatically on the detection of a threat. However, there are always borderline cases that need human attention and the UnderDefense team is there for those events. So, your staff doesn’t need to spend time on threat detection or response because it is all taken care of.
The UnderDefense technicians don’t need to come to your site in order to run your security system. In fact, they can remotely manage many sites for you. You don’t need to allocate office space to a cybersecurity team because they are all based elsewhere.
UnderDefense MAXI Platform is a Security-as-a-Service package that gives you the technical experts to manage your system security for you. In this case, you buy and host the security software and the UnderDefense team will set it up and manage it for you. This is a good option for companies that want to control which security systems they use but just can’t get the staff to look after it. This scenario is becoming extremely common nowadays because cybersecurity experts are difficult to find and in areas that have talent available, high demand makes their salaries very high. So, the use of an external team works out as a much more efficient choice.
Who do we recommend it for?
There are many reasons that a company won’t have its own cybersecurity team. Some companies are too small to justify specialists on the payroll. Other businesses might be located in a town that doesn’t have any local skills base in the cybersecurity field and other city locations cost so much to live in that the wages for rare talent become too expensive.
Pros:
- Outsourced Service: The MSSP caters to multiple clients simultaneously to bring costs down
- Remote Office: No need to meet any of the technicians working on your system from their offices
- User Behavior Analytics: Spots anomalous user activity
Cons:
- Package Doesn’t Include Software: This package only provides the expertise
As it is a bespoke service, there is no free trial or even a list of software that you could look at. You can start your investigation by booking a demo.
5. SolarWinds Security Event Manager
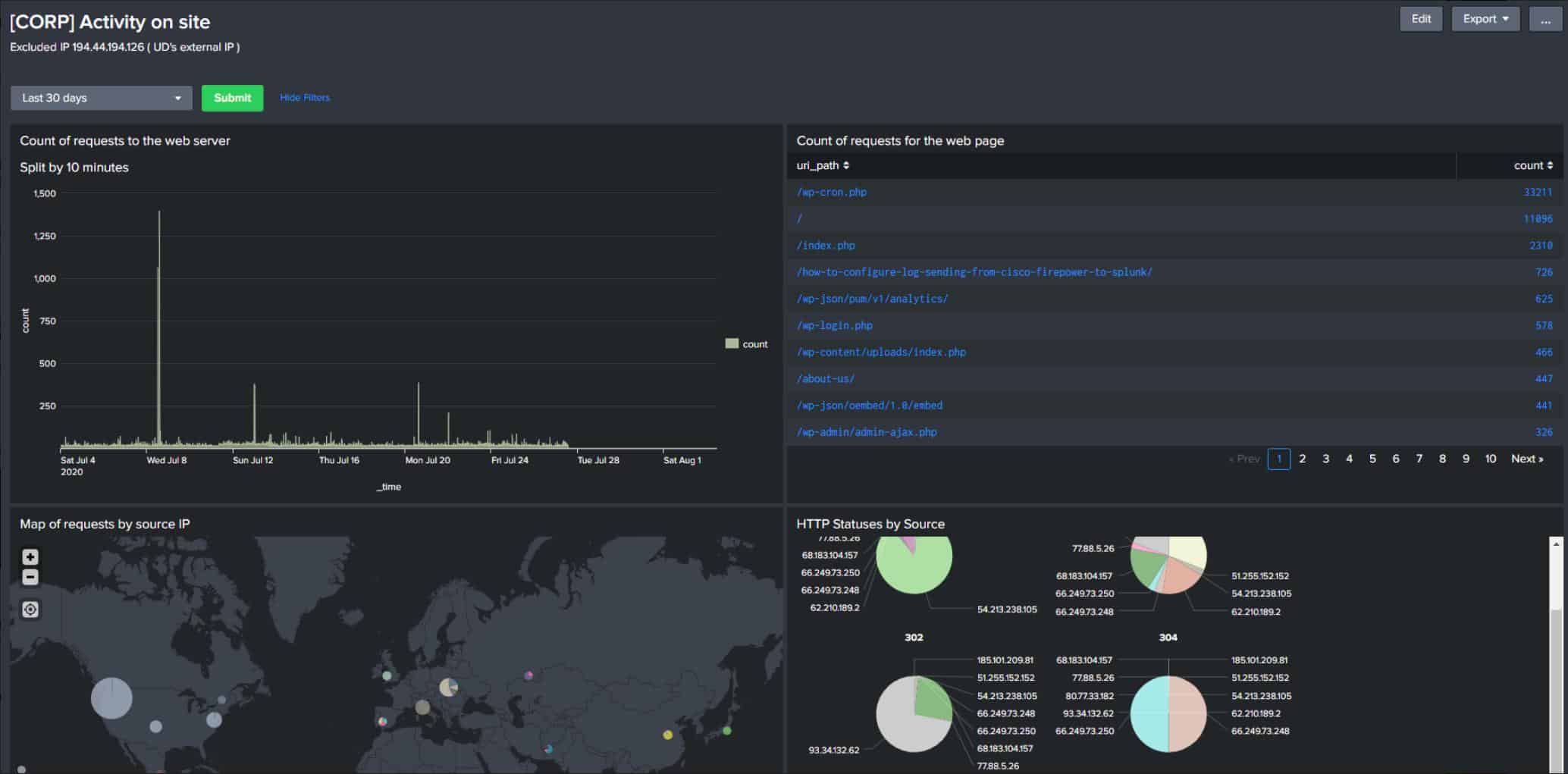
SolarWinds Security Event Manager (SEM) is a Windows-based centralized security application that can identify and prevent threats both internally and externally. SEM works by monitoring event logs and pulls that information into its own system for analysis, alerting, and correlation.
Key Features:
- On-Premises Software Package: Runs on Windows Server
- Log Management: Collects and consolidates log messages
- Automated Analysis: Includes pre-written threat hunting searches
- Manual Analysis: A data viewer provides tool for manual analysis
Why do we recommend it?
SolarWinds Security Event Manager is a software package that implements security scanning on log messages. The package includes a log manager to gather, consolidate and file logs, making them available for viewing and manual analysis. The automated analysis service in the bundle implements detection for insider threats, intrusion, malware.
The platform features over 700 built-in correlation rules combined with hundreds of automated responses administrators can use to build their own custom security rules. For example, SEM can detect events such as account lockouts, after-hours-logins, and detect when specific files are accessed. These events can be matched with an action such as disable a user account, send an email notification, or quarantine a workstation.
SolarWinds SEM also features activity monitoring and access logging, making it a great tool for insider threat management. Inside you’ll be able to quickly identify user accounts and visualize their permissions within your network. This makes tracking inheritable permissions and access control much easier, especially for larger organizations.
Rather than digging through log files, the access logging feature can highlight who has a privileged account and display an audit of exactly how that account was used within the network. Access can be filtered either by the user, time, or endpoint. This helps you quickly determine if an attack is coming from inside, or outside of your organization.
Through the threat intelligence feed, you can view both live and historical activity logs to identify anomalies or aid in a forensic investigation. Through this trove of data, you can stop threats of access violations, and then create correlation rules to stop these insider attacks from occurring again.
Outside of just reactionary tools, SolarWinds Security Event Manager makes it easy to search through your active directory environment and find inactive accounts, historical access rights, and permission information. This drastically cuts down on the time it takes to run a manual audit on your domain controller and helps close any potential internal weaknesses before they are exploited.
Who is it recommended for?
This system can gather data from multiple sites, remote endpoints, and cloud platforms. It has a high processing capacity and is built to serve large organizations. The log manager by itself is great for compliance management and is a good choice for businesses that need to follow PCI DSS, HIPAA, and SOX.
Pros:
- Spots Automated Attacks: Scans activity on networks and on endpoints
- Identifies Malicious Human Activity: Both external intruders and insider threats
- Compliance Management: Log storage enables compliance auditing
Cons:
- No Cloud Option: Only available for Windows Server
SolarWinds Security Event Manager operates on Windows 10 and later, Windows Server 2012 and later, Cloud-based: Hypervisor, AWS and MS Azure, and can be tested completely free through a 30-day trial.
6. SentinelOne Singularity Platform
The SentinelOne Singularity Platform is a cloud-based package that gathers activity data from endpoints for threat hunting. The system is able to ingest data from other security tools and the highest plan also includes information from network devices.
Key Features:
- An XDR: Gathjers activity data from endpoints for central threat hunting
- Spots All Types of Threats: Identifies malware activity, insider threats, and intrusion
- Interfaces with Third-Party Security Tools: Implements automated responses
Why do we recommend it?
While endpoint detection and response (EDR) systems operate as malware and intrusion detection services, extended detection and response (XDR) tools go a little further by pulling in logs from other security software. Thus, having the SentinelOne Singularity XDR package in operation in addition to other systems is not a waste of money.
The operating procedures of this platform sound a lot like a SIEM. This is because the standard ensign of an XDR is very similar to a SIEM to the point that a number of threat hunting systems define themselves as both. The difference between these two categories of security systems is that a SIEM takes data from endpoints and networks, while XDRs focus only on endpoints. The top plan of the SentinelOne Singularity Platform includes network data, so that edition could easily be defined as a SIEM.
SentinelOne includes a next-gen anti-virus unit, which runs on each endpoint, gathers activity data, and uploads it to the SentinelOne cloud server for analysis. If intrusion, account takeover, an insider threat, or malware is detected, instructions on how to shut down the discovered threat are sent back to the endpoint. These responses could involve suspending a user account in the case of an insider threat or an account takeover.
As it is an XDR, the SentinelOne system is more than a next-gen AV. The tool doesn’t just gather activity information from the operating system. It is also able to collect data from other security systems and it merges data from multiple endpoints into one data lake. This strategy enables the package to identify attacks on multiple endpoints and also track the movement of an attack from one endpoint to another.
The multiple endpoint view of the system is able to record illogical activity by a user and access that goes outside of that user’s normal business duties. For example, if a sales user tries to access the finance system, an alert would be raised.
The package is able to collect data from cloud platforms as well as on-premises systems and it reads through both incoming and outgoing emails as well. The precise set of functions that you get from the SentinelOne Singularity Platform depends on the plan that you choose.
The lowest plan on the platform is just a next-gen AV and successively higher plans add on more functions. This is very similar to the CrowdStrike Falcon product range, in that the onsite agent for the cloud-hosted threat hunter doubles up as a local malware and intrusion detector.
Who is it recommended for?
This is a suitable package for a large organization for whom a simple local anti-malware service is just not good enough. Small businesses are catered for in the lower packages. However, the price of the system doesn’t compete well against the other options for small businesses, which include free AVs.
Pros:
- A Cloud-Based System: installs agents on endpoints
- Focused on Endpoints: Doesn’t collect network activity data
- AI-Based Detection: Reduces also positives and blends scans of activity on many endpoints
Cons:
- Requires a Constant Internet Connection: If access to the SentinelOne server is blocked, the system breaks down
The SentinelOne Singularity platform is available in five plans with the lowest operating as an on-device anti-virus package. All of the higher plans include that AV unit and add on extensive cloud-based analytical tools that include automated threat hunting and opportunities for manual analysis. The minimum order quantity for the lowest plan is a pack that covers five endpoints. There isn’t a free trial for the SentinelOne Singularity Platform, but you an get to know the system by accessing a demo.
7. Datadog Security Monitoring
Datadog Security Monitoring aims to be a holistic approach to network security by ingesting data from every part of your network both internally and externally. The platform is extremely flexible allowing you to hunt threats manually and leverage automation to stop insider threats in their tracks.
Key Features:
- Includes a Cloud SIEM: Threat hunting for on-premises systems
- Pre-Written Activity Searches: Looks for manual and automated threats
- Cloud-Based System: Installs data collection agents on the site
Why do we recommend it?
Datadog Security Monitoring is a new service from the Datadog cloud platform. The security system is split into three modules: Cloud SIEM, Cloud Security Management, and Application Security Management. The Cloud SIEM collects activity data from your premises and cloud accounts and searches for intruders, insider threats, and account takeovers.
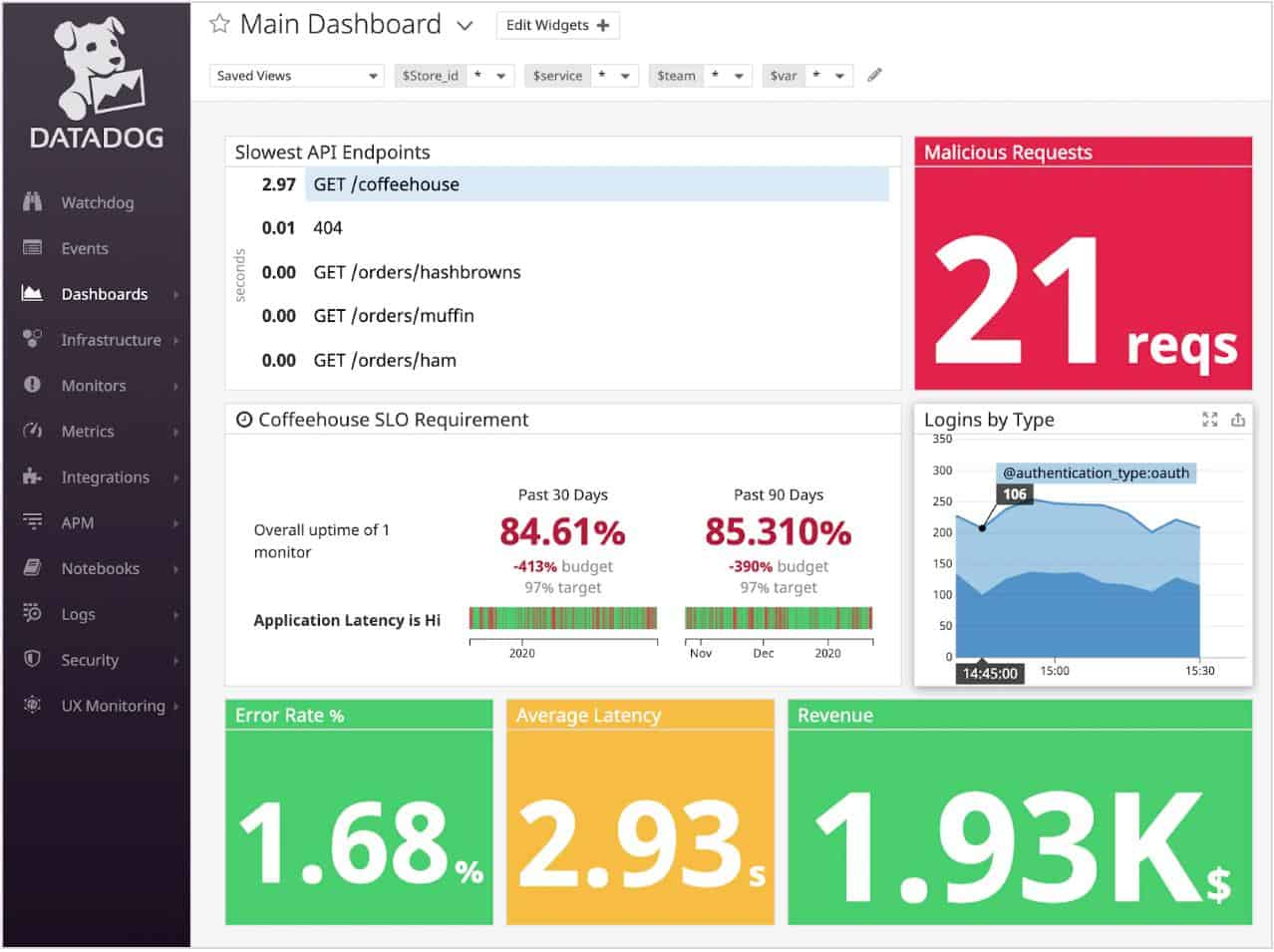
While this may sound complex, Datadog does an impressive job at keeping the interface clean and user-friendly. Through a single pane of glass, you can identify and sift through security events across dynamic environments, whether that be in the cloud, on-premises, or a mix of both.
This real-time threat detection combined with Datadog’s out-of-the-box features makes deploying your insider threat management strategy much quicker than most platforms. Dozens of pre-configured detection rules start working immediately, meaning you can start seeing instant insights on attacks, misconfigurations, and potential attacks starting from behind your firewall.
With over 500+ vendor-supported integrations, Datadog has some of the most flexible logging and monitoring abilities of any threat detection tool. For example, you can have integrations for AWS and G Suite, while also having on-premises Windows server and endpoint monitors pushing data to one centralized location.
Partner integrations allow you to pivot and add additional capabilities into new and existing tools. For more incident response features a CrowdStrike integration can be installed to help direct how internal threats are dealt with and give you more control over how a team handles incident responses.
When a possible insider threat is found, a manual investigation can begin to determine its validity and scope. Datadog drastically decreases the time an investigation takes by integrating directly with communication tools as well as assigning events their own severity score.
Assigning an event to a technician or a team can be done through automation or manually. Datadog allows you to quickly share security information dubbed “Signals” with your team. Events can be shared via email, push notification, or through third-party apps like Slack or PagerDuty.
Who is it recommended for?
The Cloud SIEM is charged for by data processing volume. This is a very scaleable service and is accessible to businesses of all sizes. Once you have the SIEM security in place for threat detection, you can expand to security protection with the Cloud Security and Application Security tools.
Pros:
- Manual Threat Analysis: A data viewer with analysis tools
- Long-Term Log Retention: Can store logs for up to 15 months
- Automated Responses: Response playbooks
Cons:
- Relies on Datadog Log Management: You have to subscribe to the Log Management unit additionally
Datadog Security Monitoring starts at $0.20 (£0.15) per gigabyte of analyzed log data per month. To access the out-of-the-box detection rules and enable 15-month log retention the price goes up to $0.30 (£0.22) per gigabyte of ingested data.
You can try hunting insider threats with Datadog for free through a 14-day trial.
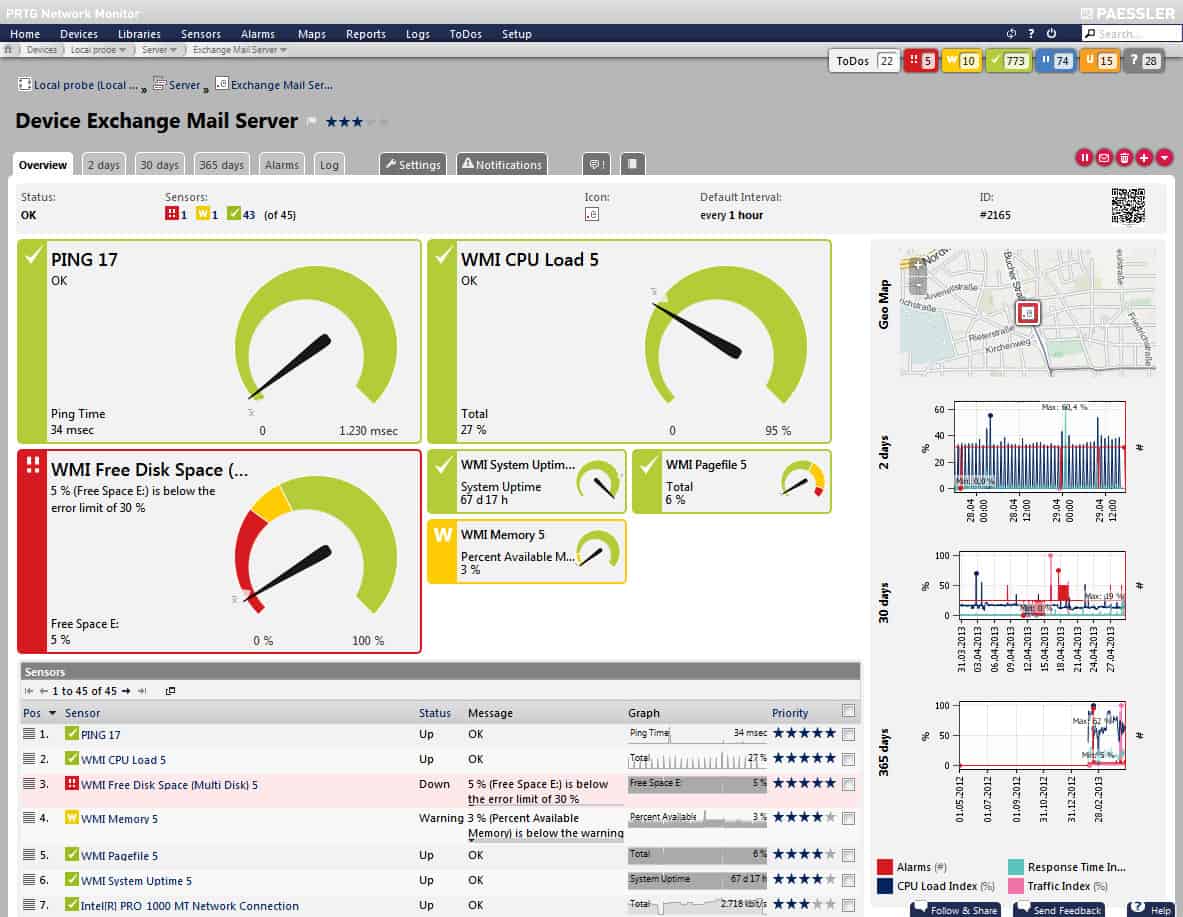
8. Paessler PRTG Monitor
PRTG Network Monitor has been known for its robust and flexible sensor-based monitoring, but it has now expanded into insider threat detection. Paessler and Flowmon Networks have recently partnered up to expand the capabilities of PRTG Monitor to include insider threat detection, in-depth flow analysis, and behavioral analytics.
Key Features:
- Combination of Two Packages: Needs Flowmon as well as PRTG
- Network-Based Monitoring: Focuses on network traffic data
- Scans for Threats: Looks for anomalous network activity
Why do we recommend it?
Paessler PRTG is a system monitoring package. All buyers of PRTG receive the same software bundle. This includes a large number of sensors and among them are a series of activity monitoring tools that can be used to assess user account traffic. There is also a SaaS version of PRTG.
This addition makes the PRTG platform considerably more flexible, especially for companies who are looking for a combination of insider threat detection and network monitoring.
Like all PRTG monitors, insider threat detection works by combining two custom sensors, an SNMP sensor, and a Python script sensor. The SNMP sensor is used to monitor the Flowmon appliance while the Python script allows that data to be displayed from Flowmon into the PRTG dashboard.
Together these sensors give both deep insights into the network status of a device, as well as contextual security information that can be processed by machine learning. Once processed these security events are grouped together and then assigned a priority depending on their severity before being displayed on the PRTG monitoring dashboard.
The live dashboard puts your entire network into perspective through a series of key insights, charts, and live network maps. All of your key insider threat management information and network monitoring can be displayed and customized through over 300 different graphic objects and visualizations.
On the backend, PRTG allows for flexible alerting based on a combination of conditions, thresholds, and quotas. All alerts are highly configurable which allows you to reduce the number of total alerts your operations center receives. You can choose to be alerted via email, HTTP request, push notification, or from PRTG’s Android and iPhone apps.
Technicians can quickly toggle from PRTG to Flowmon while troubleshooting an event to apply root causes analysis; they can search through other related security events to get a clearer picture of what may be an insider threat. By combining your insider threat management with your network monitoring you simplify the workflow and increase the speed at which IT staff and the network security team can identify and solve issues.
Who is it recommended for?
PRTG is suitable for businesses of all sizes because it is a very flexible package. The tool is priced according to the number of sensors that you want to activate, so smaller companies can save money because they won’t have such a large technology spread as large organizations.
Pros:
- Spots Network Movements: Lateral movement of malware, insider threats, and intrusion
- Sees Rogue Devices: Detects all devices that are connected to the network, including those that shouldn’t be there
- Root Cause Analysis: Compare activity from different data sources
Cons:
- Requires Work to Set Up: You need to coordinate two packages from different suppliers
PTRG Monitor is highly flexible and designed to fit virtually any sized company. Pricing is based on the number of sensors you have deployed. You can test out the full version of PRTG and its insider threat detection system for free through a 30-day trial.
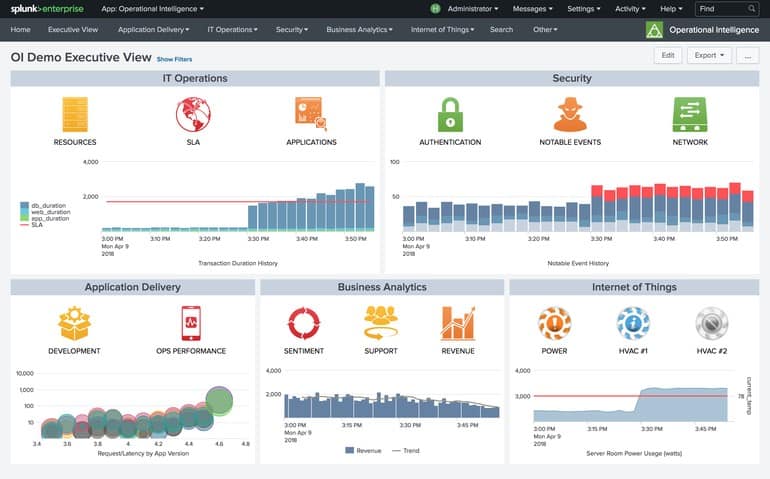
9. Splunk
Splunk markets itself as the “data to everything” platform, making it an extremely flexible tool for threat detection, monitoring, and even business intelligence. For now, we’ll focus on how Splunk can specifically be used for insider threat management.
Key Features:
- Data Analysis Tool: Can be used to analyze any type of data
- Pre-Written Security Scanning: A SIEM package
- A SOAR Option: Choose a package that coordinates signals from third-party tools and implements automated responses with other systems
Why do we recommend it?
Splunk is a data analysis tool and it can be put to many uses. The Splunk organization has produced a pre-set package of security monitoring services called Splunk Enterprise Security, which implements insider threat, intrusion, and account takeover detection. The security modules can be assembled into your ideal security package.
Like many of these platforms, Splunk harnesses its power by collecting signals through event logs pulled from endpoints, servers, and applications. These events are brought into the Splunk ecosystem and displayed in a single dashboard. Machine learning and behavioral analysis help highlight key security events a manual review may have missed and even can apply automatic remediation via scripts.
Splunk excels in insider threat detection primarily through its User Behavior Analytics (UBA) system. This is a form of continuous threat monitoring that combines rules you define with how a user regularly behaves. If a rule is broken, or if suspicious behavior is detected, immediate action can be taken to stop the threat.
This combination of behavior baselining and peer group analytics gives a clear window into not just the actions of an internal account, but the intent behind a user’s action. For example, the actions of a compromised account will look much different than an employee who is manually attempting to access parts of the network they are not authorized to.
The data Splunk can process gives you a granular look at these events and puts the tools to deal with them at your disposal. Outside of just unusual account activity, Splunk has the ability to detect data exfiltration, privilege escalation, and privileged account abuse.
Through constant network monitoring the Splunk platform can automatically prevent and alert to data theft. Private or sensitive information can be tagged as confidential, allowing Splunk to stop it from leaving through unsecured channels as well as audit the history of its access.
Who is it recommended for?
Splunk Enterprise Security is not cheap. You could save money by just buying the Splunk system and then constructing your own SIEM. However, you will need to know what you are doing and you will also need a lot of time. Therefore, the Splunk Enterprise Security system saves you time and money.
Pros:
- Platform Options: Available as a cloud-based SaaS platform and as an on-premises software package
- Also Provides Performance Monitoring: Infrastructure and application monitoring
- Multiple Data Sources: Acquires both log messages and network data
Cons:
- Complicated Setup: Requires work to create data feeds into the package
Splunk has three pricing tiers, starting with a free version allowing for 500MB of daily indexing. Monitoring and alerts are only available through their Standard and Premium versions, but your monthly cost will be closely tied to how much data Splunk processes.
You can test out Splunk through a free download.
See also: Network Security Auditing
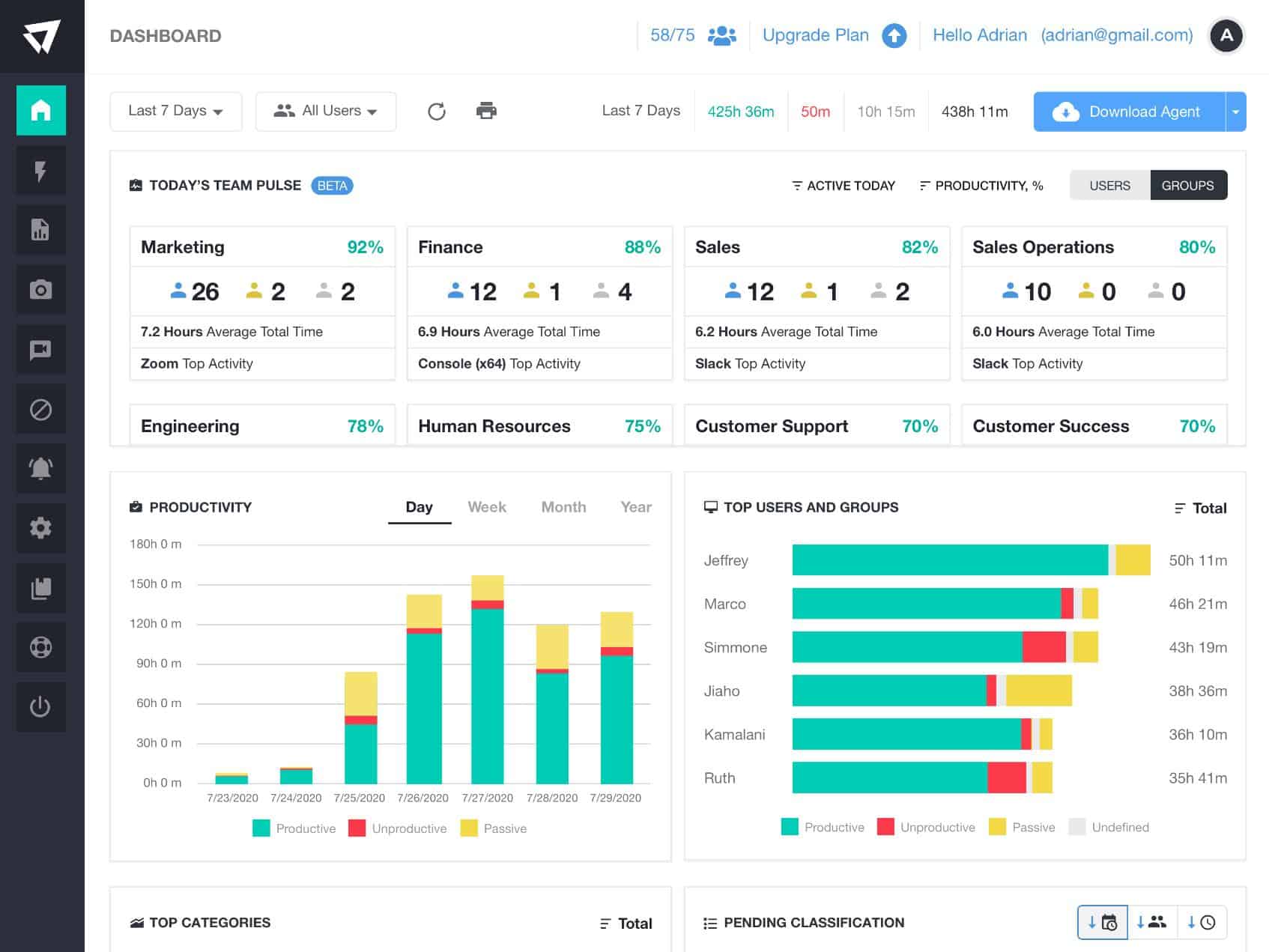
10. ActivTrak
ActivTrak is a dedicated platform for employee monitoring, operational efficiency, and security management. Since ActivTrak collects so much information around end-user behavior, it can easily identify insider threats and play a key role as an insider threat management tool.
Key Features:
- Employee Activity Monitoring: The base package is used to make sure that workers are not slacking
- Insider Threat Monitoring: All plans provide user activity reports
- Free Edition: Tracks the users
Why do we recommend it?
ActivTrak is an employee activity tracker. The main purpose of this system is to assess productivity. However, all of those activity records also provide insider threat detection. Access rights managers are central to user tracking and can weaken security f not properly maintained. So, the ActivTrak system includes an Active Directory auditor.
Through a series of lightweight sensors living on endpoint devices, ActivTrak can immediately stop insider threats as well as provide an overview of the threat scope on a company-wide level. These sensors can not only identify insider threats but read into the context of the security event on a deeper level.
For example, an employee accidentally opening a malicious email is much different from employees actively installing hacking tools on their machines. Understanding this difference helps shape a custom response that is both appropriate and impactful.
Through these insights, you can view both individuals and specific departments or groups who are engaging in high-risk behavior. Viewing this information on such a high level helps larger organizations track their security posture by department, and even uncover opportunities for further security education or policy changes.
In combination with this high-level behavioral overview, ActivTrak also provides basic malware protection, website restrictions, and automated data redaction.
Outside of security, ActivTrak offers additional features such as application usage tracking, employee productivity reports, and workflow monitoring for identifying unbalanced workloads and peak work hours.
Who is it recommended for?
This package presents an innovative angle to employee management because you can spot slackers as well as belligerent workers. The AD management tool locks down your user accounts and reduces the threat of account takeovers. A Free edition can track three employees. Three paid editions cater to larger businesses.
Pros:
- Website Blocking: Create a website blacklist
- File Transfer Detection: Through USB devices, file transfer systems, and email
- Activity Alerts: Automated notifications and responses
Cons:
- Free Edition Has No Support: Professional support is not included
ActivTrak is considered a Freemium software that offers some of its most basic features completely free. To get access to features such as customized alerts, detailed automation, and remote deployment you’ll need the Advanced plan starting at $7.20 (£5.39) per user per month.
You can view the full pricing chart on the ActivTrak pricing page.
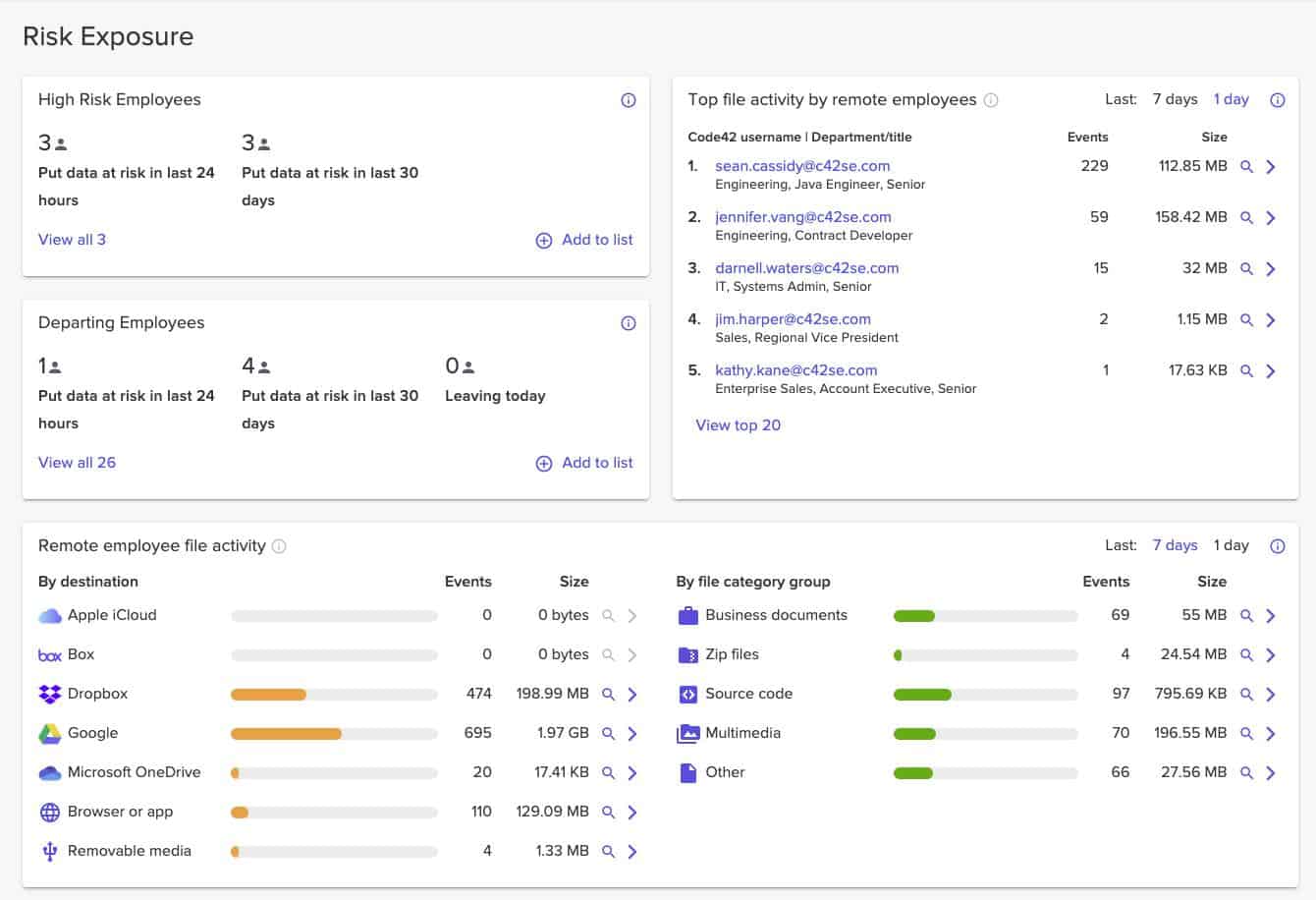
11. Code42
Code42 is a SaaS that focuses almost entirely on stopping and preventing insider threats for any sized network. Whether you’re protecting intellectual property or stopping a rogue employee, Code42 uses a combination of detection, investigation, and response to put an end to malicious activities.
Key Features:
- Focused on Insider Threats: User activity tracking
- Controls for Departing Employees: Stops leavers taking business data to their next job
- Stops Data Movements: Examines USB sticks and file transfer systems
Why do we recommend it?
Code42 has two packages – Incydr, which is an insider threat detection service, and Instructor, which is an insider risk education service. Incydr is also available in a version tailored to US government agencies. The Incydr package focuses on data movement control for data loss prevention.
The Code42 platform takes a granular look at data protection and applies custom solutions for each scenario. For example, the system uses separate techniques to secure data from a cloud platform, such as Google Drive, than it does when an employee unexpectedly leaves the company.
By monitoring virtually all file activity, Code42 can get a pulse on violations and identify what should or shouldn’t be considered acceptable by a security policy. This technique can fill the gap where single solutions such as Data Loss Prevention (DLP) or User Activity Monitoring (UAM) fall short.
By seeing security events at such a level your company is able to identify big-picture security flaws such as data exposure, most high-risk users, and most vulnerable third-party platforms.
Using this broad coverage Code42 allows you to quickly take action against threats through both manual review and automated remediation. Administrators can view a pre-prioritized dashboard that highlights the most pressing security matters so they can get to work on what matters most.
There is an entire section dedicated to Security Orchestration Automation and Response (SOAR) which gives security teams the power to create rules based on conditions or thresholds and apply customized responses to each event.
Lastly, Code42 can dive deep into the context and change in an individual user’s activity. The platform works to monitor privileged accounts and can monitor those users more closely who show signs of becoming more of an insider threat.
For example, users who fail phishing tests, have expressed job dissatisfaction, or have worked on unsecured networks all will have a higher level of scrutiny applied to their user accounts.
Who is it recommended for?
The Icydr threat detection and data loss prevention system is attractive for businesses of all sizes. Code42 doesn’t publish a price list, so it isn’t possible to say whether this package is suitable for small businesses. However, it is certainly attractive to large businesses – Code42 has Okta, CrowdStrike, Rakuten, and Snowflake on its client list.
Pros:
- Government Version Available: FedRAMP-compliant edition for US government agencies
- Scans Endpoints and Cloud Platforms: Agents for Windows, macOS, Linux, and cloud drives
- A Cloud-Based System: This is a SaaS package
Cons:
- No Price List: You have to contact the sales department for rates
Code42 comes in two pricing structures, Basic and Advanced. The Advanced tier gives you more in-depth investigation tools, file deletion detection, and cloud file monitoring. Pricing is not publicly available, however, a free 30-day trial is offered.
Choosing an Insider Threat Detection Tool
We’ve narrowed down the best insider threat detection tools, but which is right for you?
If you’re a mid to large-sized organization SolarWinds Security Event Manager provides broad coverage against insider threats at a fair price. SolarWinds SEM allows for insider threat management paired with the ability to scale and monitor other aspects of network security in one easy-to-use platform.
Both Paessler PRTG and Datadog are close runners up, with their pre-made rule-sets, intuitive dashboards, and scalable monitoring solutions.
Insider threat detection FAQs:
How do you monitor insider threats?
Monitor insider threats by looking for actions performed by user account holders that are out of the norm. The baseline of standard behavior needs to be established per user.
What are the insider threat indicators?
Security software works on “indicators of compromise” to identify malicious activity. These are known as IoCs and there are specific signatures of behavior relating to insider threats.
What are 4 methods of threat detection?
There are four threat detection strategies:
- Configuration Analysis – communication occurs that doesn’t fit in with the planned architecture of the system
- Modeling – Establish a baseline of normal activity per user and look for deviations from this
- Indicator – System changes (indicators of compromise) that are known to indicate malicious behavior
- Threat Behavior – Known patterns of activity that can chain through to a damaging event
Do you have a method for tracking insider threats? Be sure to tell us about your insider threat experiences in the comments below.