For smart administrators to troubleshoot, and then resolve, network failure issues quickly, they need to assess the stability of the network and find out where the disruption has occurred. And yet, an even a smarter administrator would conduct a network stability test before a failure to evaluate the connection strength and spot any errors or weak spots before they cause a crash.
The definition of a network stability test can, therefore, be given as:
The process of using programs and commands to make sure every router and other devices being used to connect an intranet to the Internet – be they behind or beyond the territorial firewall – is up and running. It also involves making sure all the authorized data on the network is safe – both in motion and in resting states.
How can you test network stability?
Testing network stability is essential to ensure consistent performance and reliability, especially in environments where uptime is critical. There are several methods to test network stability:
- Ping Test: This is the simplest way to test if devices on the network can communicate. By sending ICMP echo requests (ping) to various endpoints, you can check for packet loss, latency, and response times. A high rate of packet loss or high latency indicates instability.
- Traceroute: This tool helps identify the path data takes from one device to another, showing where delays or packet loss occur along the route. It’s useful for detecting network bottlenecks or failing network hops.
- Bandwidth Test: Using tools like iPerf or Speedtest, you can measure the available bandwidth between devices on the network. Variability in bandwidth or sudden drops can indicate congestion or instability.
- Network Monitoring Tools: Tools like Site24x7, PRTG, or Nagios continuously monitor network health, alerting you to issues like high traffic, spikes in latency, or downtime.
- Stress Testing: Simulating heavy traffic or large-scale data transfers can reveal how the network behaves under load, helping to identify potential points of failure during high-demand periods.
- Packet Sniffing: Using tools like Wireshark, you can capture and analyze traffic to detect anomalies, errors, or signs of interference that might affect stability.
By combining these methods, you can obtain a comprehensive view of network performance and pinpoint areas of weakness. In this guide, we outline a strategy to follow.
Several steps need to be taken when testing a network’s stability. They include:
Checking network connectivity
Network connectivity should never be lost; period. Apart from being up, it should also be fast and not prone to dropping packets. This can be done using three methods:
- There are tools out there that help administrators keep track of their networks. One such tool is the Paessler PRTG Network Monitor (FREE TRIAL). This is an all-in-one network monitoring suite of programs that keep a constant eye on the connectivity between a host network and a test server like Google, for example, which aren’t expected to be down – ever.
- If you have a grasp of even the basics of networking, you can conduct the test yourself using free tools like Ping and Tracert. If you don’t, keep on reading and we will show you how it is done.
- Finally, connectivity and health testing can be done using third-party websites like Internet Health Test or Ping Can Be Useful. While these are the easiest way to go, they really don’t give in-depth information about network connectivity issues – at least not for free.
Monitoring network data
Only the right type of data should be transported on a network and not, for example, spam data from an attacker on the outside. In another scenario, servers shouldn’t be backed up during peak processing hours when they could hog the bandwidth.
Administrators should, therefore, keep track of what data packet is passing through their networks. They can use numerous deep packet inspection and network analysis tools found on the market which can be used to keep an eye on traffic and filter it as required.
For an example of a suitable tool for the task of traffic monitoring, you could look at Site24x7. This cloud-based package provides autodiscovery, network mapping, device health monitoring, and also traffic analysis. The system has the ability to communicate with a wide range of network device brands because it is loaded with the statistics protocol languages that they use: NetFlow, IPFIX, and J-Flow are three examples.
Any of the statistics that Site24x7 gathers can have alert rules placed against them. If one of those conditions is breached, Site24x7 will post an alert in the system console. It will forward those alerts to specific technicians as notifications by SMS or email. This feature automates the system monitoring task and support staff can assume that everything on the network is working well unless they are notified otherwise.
Related posts:
Maintaining packet speeds across the connection
There shouldn’t be any attrition or loss of data speeds. Packets shouldn’t be dropped because the network is too congested, an access point is not up or performing as well as it should be, or because the specific packets have been blocked by mistake.
Administrators should have a plan as to how much bandwidth is allocated to every aspect of your data transportation – give more to VoIP and less to email traffic, for example, so audio communication doesn’t lag.
Here too, administrators can take certain defensive steps and corrective measures to remedy this particular issue.
Network performance testing
Monitoring the different metrics in your network can help you better understand the performance and stability of your network. It can also provide information about potential issues, so you can proactively fix them before they impact the wider organization.
That said, it’s important to have a plan and a defined approach to resolve these bottlenecks. There are five broad steps involved:
- Identify the precise location of the issue.
- Analyze the parameters to identify the root cause at the location identified in the earlier step.
- Fix the issue at the earliest.
- Audit and track if all the issues are fixed. Generate reports as needed for internal evaluation.
- Set up automation actions to reduce the need for human interference.
To implement the above approach, you need a tool like ManageEngine OpManager. Using this tool, you can automate the testing of different parameters. It monitors more than 3000 parameters in real time across physical and virtual servers, switches, routers, firewalls, and other devices. Also, it offers support for over 53,000 vendors and uses more than 10,000 device templates for monitoring critical parameters.
With such comprehensive support, you are always on top of your network’s performance and can resolve issues as they occur. You can register with ManageEngine for a 30-day free trial.
Ensuring network protection
Network administrators also need to make sure there are no breaches or unauthorized usage of the network, connected devices, and the data on it.
The ideal toolset to use here would be Network Intrusion Detection Systems (NIDS).
Related posts:
Tools for Network Security and Stability
Finally, administrators know that their networks will only be stable as long as people who aren’t supposed to be on them are kept away. If outsiders keep meddling with data, configurations, and authorizations they will soon be able to hijack the network. They can then use it as a springboard for further attacks, hack the devices connected on it, or simply crash it.
Network security can be assured using tools like firewalls, anti-viruses, antimalware, and IDS/IPS tools.
Ok, now that that is clear let us get into the technical part of PING and TRACERT.
What does PING do?
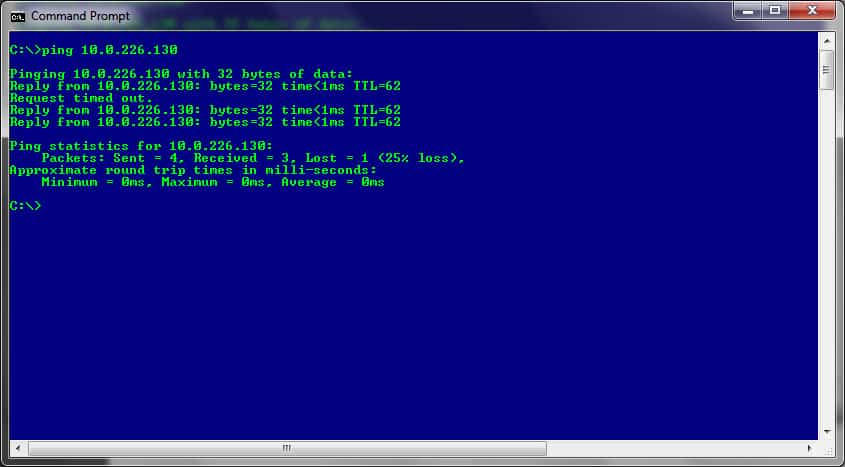
PING is a tool that sends packets to a target server and listens for a reply. A successful reply of all (100%) the packets delivered means the target is up and running and there are no connectivity issues. On the other hand, any dropped packets indicate that there is a network problem somewhere along the way, as is the case in the image below:
If the PING results in 100% loss, it could mean any (or all) of the connecting devices between the host machine and the target server are down.
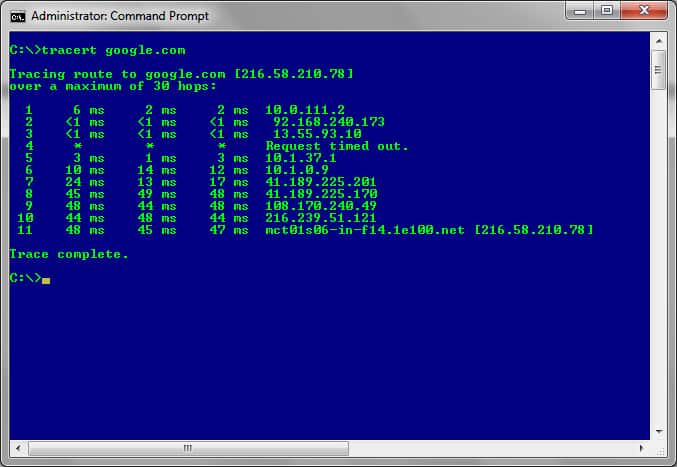
What does TRACERT do?
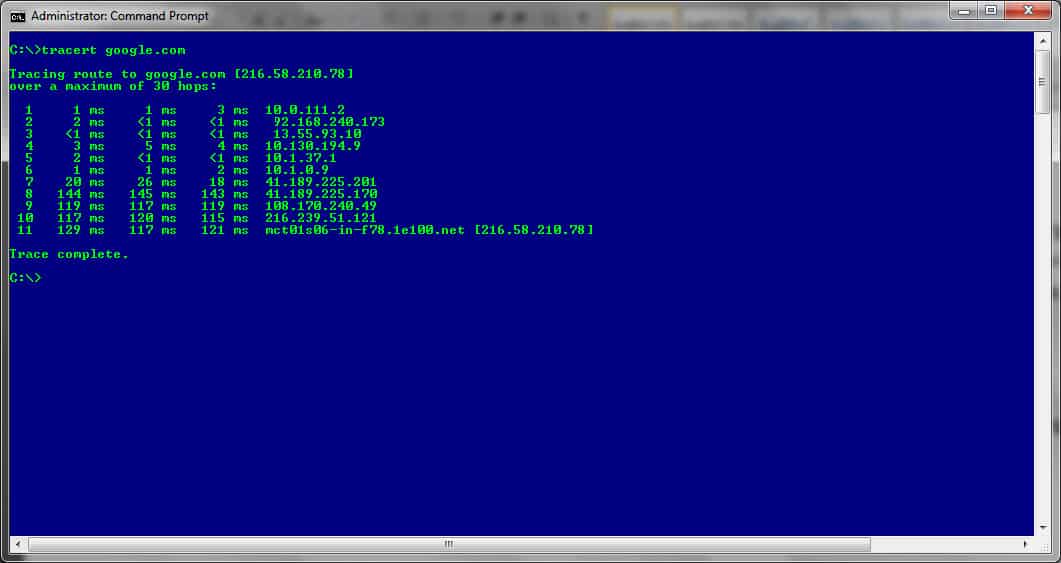
TRACERT is a tool that sends packets to every single router that lies between the host machine and the target server.
In this case, though, the packets sent out will hop to every single router that is en-route to the target server and send a reply back to the host machine. Apart from confirming connectivity, each reply also includes the information of the next router in line so the subsequent packets have an address to target in the queue.
How to use PING to test for network connectivity
PING is a versatile tool that can be run from the command-line interfaces (CLI) of operating systems like Windows, Linux, and macOS.
The steps involved [in Windows OS] are:
- Go to RUN -> Type CMD (or COMMAND) -> Then, type PING XXX.XXX.XXX.XXX (the target IP address) or PING ACME-Company.com (the domain name of the target network) in the CLI.
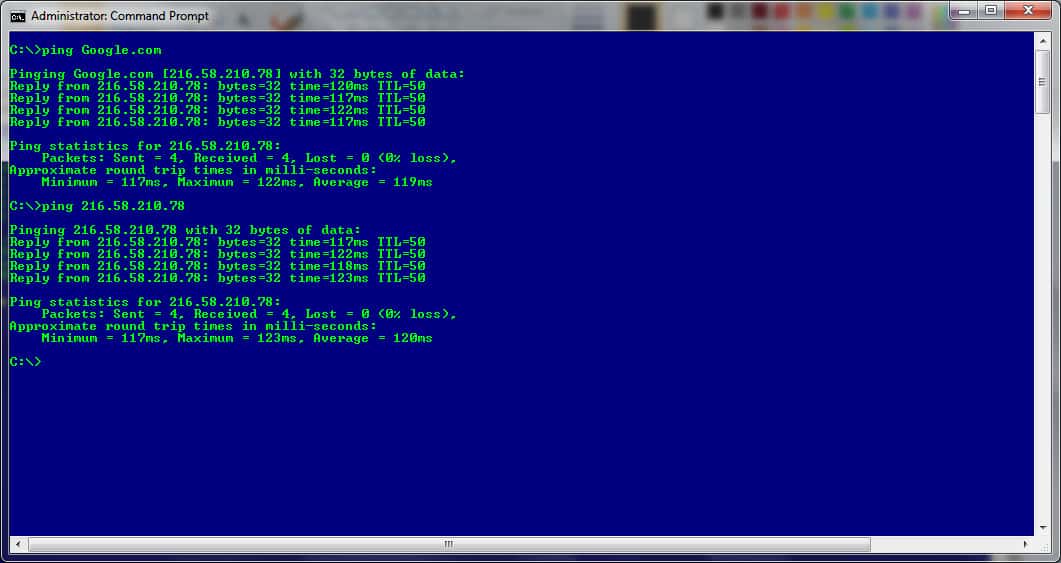
- “-t” is used to continuously ping a target when, for example, a remedy is being put in place and you want to keep monitoring to see if the issue has been resolved
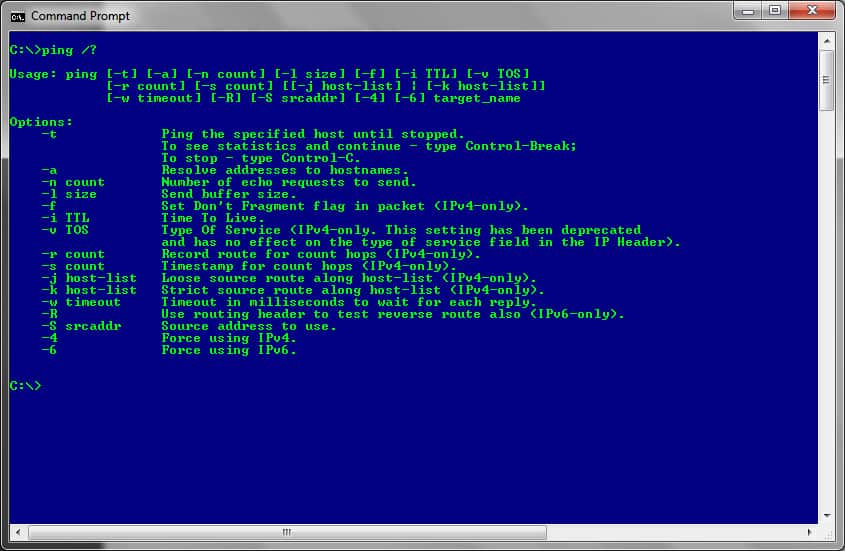
For a full list of all the arguments that can be used, simply type PING /? at the prompt.
How to use TRACERT to check for network or internet connectivity
TRACERT is another command-line tool that helps with resolving network connectivity issues. As mentioned, and in comparison to PING, this tool doesn’t just test the connection speed between two points. It also checks all the routers that are found along the route as the packets that are sent hopping to and from each of them.
Any interruption in the connection becomes evident when the packet ceases to return with a reply from the device. This indicates that the silent device is the one to check out.
Once executed from the CLI, the command sends a UDP packet to all the routers that lie between the origin and target address and then waits for a reply – again, if there is one, that is.
The basic syntax of the TRACERT command looks like:
TRACERT XXX.XXX.XXX.XXX or TRACERT domain-name.com (the target IP address or domain name)
- “-h” is used to set the number of hops that can be used to reach the target device
For a full list of all the arguments that can be used simply type TRACERT /? at the prompt.
Conducting network and internet stability tests
Well, we have just seen all the tools you will need to conduct a network stability test. For those of us that don’t really want to be bothered with command-line interfaces, we have also seen there is a collection of tools you can use to achieve each objective of a network stability test.
Depending on your choice of tools and the frequency required, you can schedule or run them to see the status of your network’s stability at any given time.
Are there any tools you prefer to use or think would do the job better? Let us know in the comments section below.
Network Stability Test FAQs
How do you test network quality?
Network quality is assessed by latency, packet loss, and jitter. All of these indicators can be identified through Ping. The roundtrip time given in the Ping summary is the time to the destination and back. Latency is the speed of delivery in one direction. So, divide the roundtrip time by two to get latency. The jitter is the variance in delivery time. The Ping results show the minimum, maximum, and average RTT. The wider the min and max are, the higher the jitter. The first line of the Ping statistics report shows the number of lost packets in th4e test batch run.
How do I trace network latency?
Use Pathping to get a report on the latency on each hop from your computer to another node on the network. The command can be executed from the command prompt and it takes the IP address of another node on the network as a parameter, eg., pathping 192.168.0.10.
Why is my jitter so high?
The biggest cause of jitter on a network is excessive traffic. Traffic-shaping measures, such as prioritized queuing on network devices can improve performance for some applications while making jitter worse for others. For example, latency and jitter are very important for VoIP. So, many network administrators prioritize that traffic. However, VoIP traffic occurs in bursts, so the traffic of other applications will go fast, slow, fast, slow, creating a wide variation in transfer times as some of its packets get temporarily parked to make way for bursts of VoIP traffic.
How to find out round-trip time?
The roundtrip time (RTT) is a standard statistic given by both Ping and Pathping.
How do I fix network stability?
Network stability is an issue of load on the hardware of the network. The goal of network stability is to get all packets traveling from source to destination at a regular speed. Don’t confuse the goals of network stability and high network speeds. In order to get a steady flow of traffic you would need to drop high speeds as a goal. Once you have a regular traffic flow at an achievable speed, you can then address speed issues and you will find that you can provide more capacity for urgent traffic, such as video conferencing or VoIP, at the expense of less time-critical systems, such as email.
What causes poor network conditions?
Poor network conditions are caused by faulty or overloaded network devices. Lost packets occur when a network device, such as a switch or a router is fully occupied. Extra traffic just doesn’t get passed on and ceases to exist. You can fix this problem by increasing switch and router capacity or by implementing queuing. Network device faults can be headed off by implementing network performance monitoring.
Related post: What is Network Jitter?