Graylog and Splunk are two of the leading SIEM platforms and each grew out of a generic data processing tool. These two systems have a lot in common and have progressed through log management into security scanning via the SIEM methodology. However, despite their shared purpose, Graylog and Splunk differ in several key areas. So, businesses need to understand the nuances between the two before selecting the right solution.
Graylog is an open-source log management platform that is known for its flexibility, ease of use, and cost-effectiveness. It allows organizations to aggregate, search, and analyze log data in real time, while providing powerful tools for visualizing and troubleshooting operational issues. The open-source nature of Graylog also enables greater customization, making it an appealing choice for businesses with specific needs or those operating in environments that require more tailored solutions.
On the other hand, Splunk is a commercial platform renowned for its scalability, advanced analytics capabilities, and enterprise-grade features. It offers a comprehensive suite of tools designed to handle everything from log aggregation to sophisticated data analysis, security monitoring, and incident response. While Splunk offers more advanced features, it comes with a higher price point, which may be a deciding factor for smaller businesses or organizations on a tight budget.
In this guide, we will compare Graylog and Splunk in terms of features, pricing, scalability, and use cases. By the end, you will have a clearer understanding of which platform best aligns with your organization’s needs and resources for log management and analysis.
Graylog vs Splunk: Similarities
From a top-down perspective both Graylog and Splunk act as aggregates of both structured and unstructured data. While basic tools restrict your data into isolated silo structures, both Graylog and Splunk can pull information from multiple sources and provide a single point of analysis for all data across your organization.
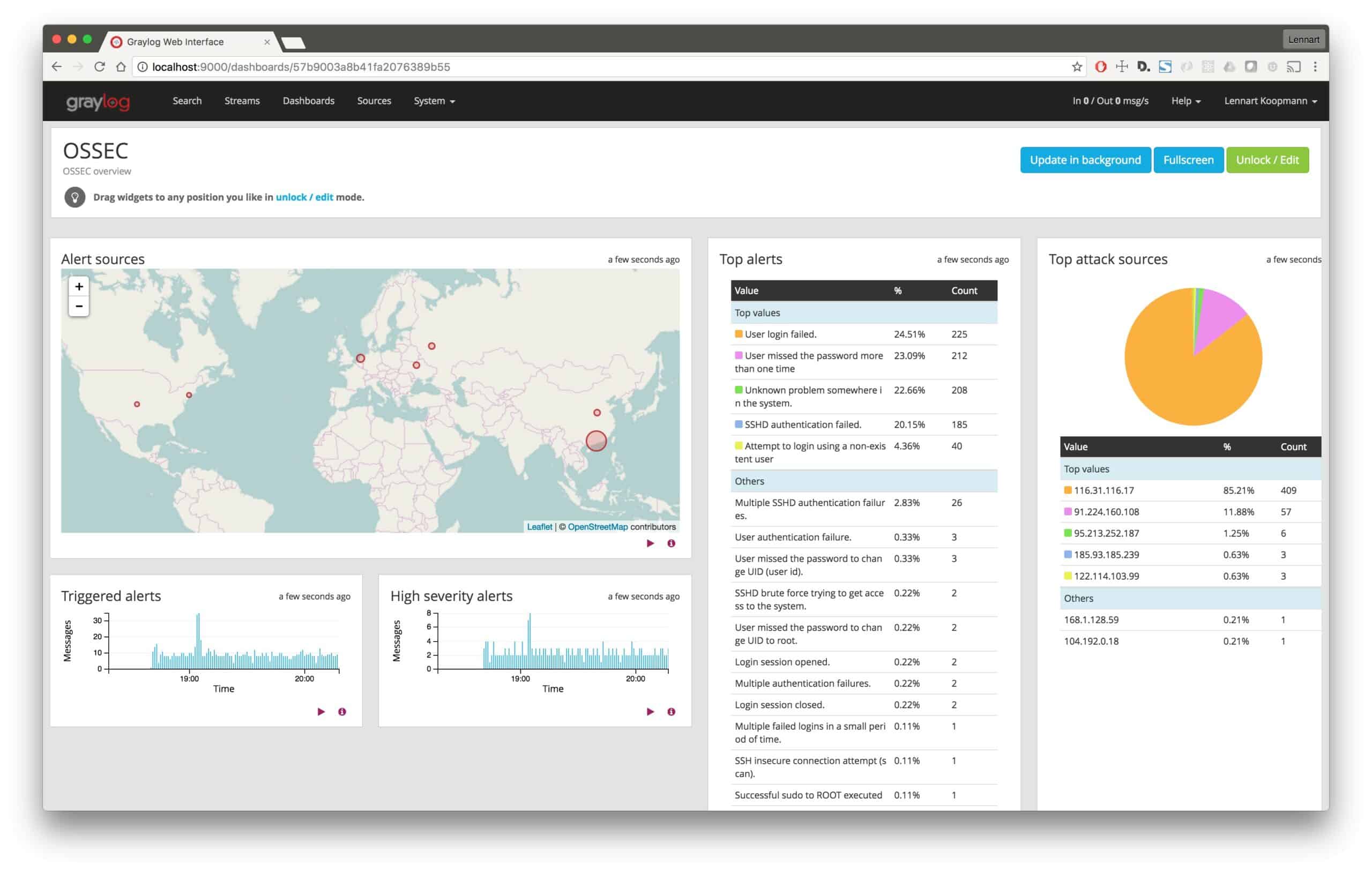
Splunk and Graylog are built to collect this data and store it both for long-term use as well as send alerts if specific events are detected. There might be a time when you need to sort through your data in a forensic manner to uncover a data breach or audit your systems. Graylog and Splunk provide an adequate platform to collect and sort through that data.
Both systems utilize advanced search functions to query and analyze data, both in real-time and through historic logs. While the types of search engines Graylog and Splunk use are different, they perform fairly equally when compared against each other in terms of functionality.
Looking at the level of support you’ll receive, both Splunk and Graylog offer onboarding assistance, phone and email support during normal business hours, and access to extensive knowledge bases. Splunk has a larger more granular support plan where you can purchase additional priority support for 24/7 availability and 30-minute response times.
Graylog
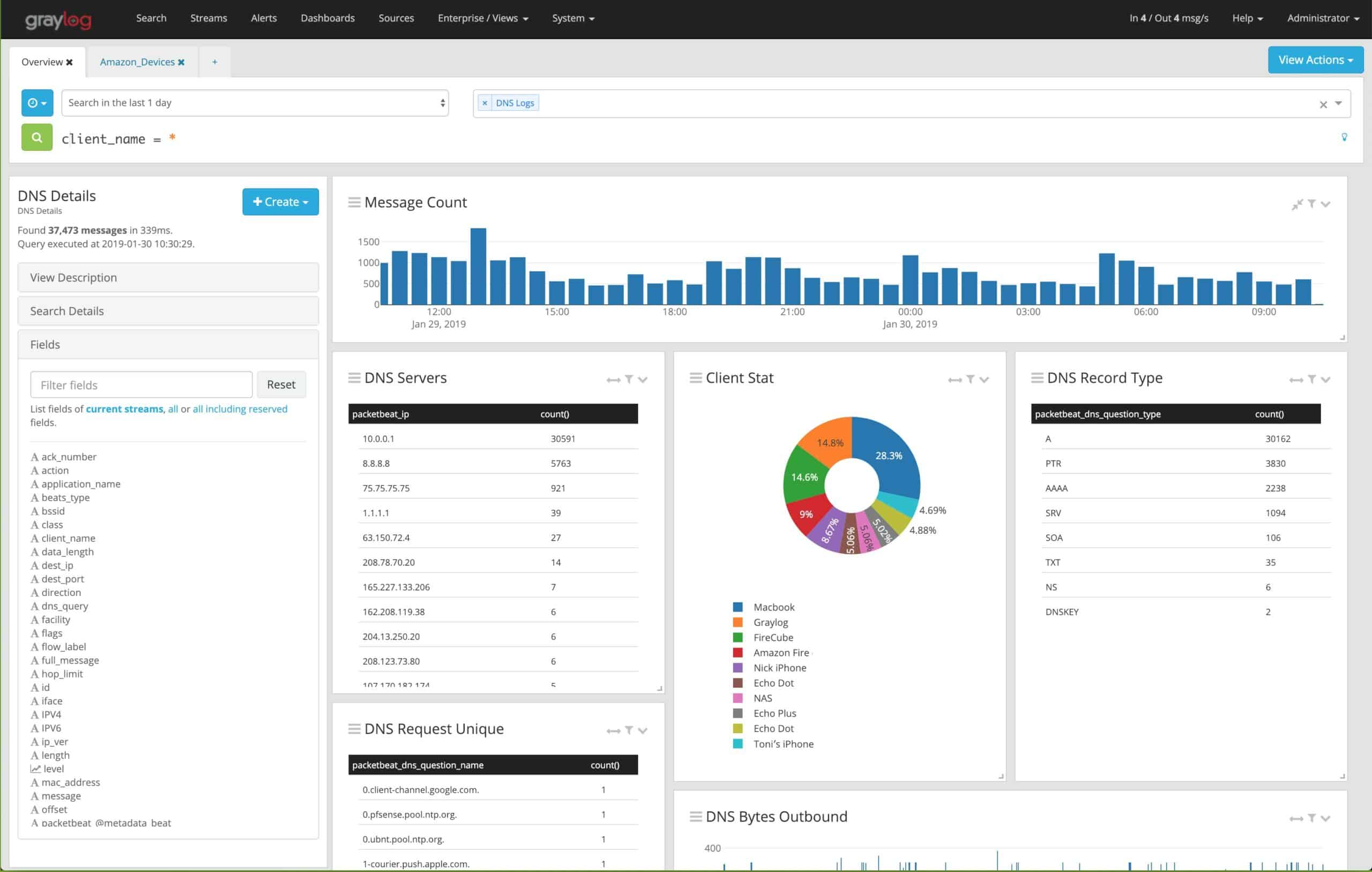
The platform relies on Elasticsearch and MongoDB to generate searches and operate. Deploying Graylog requires an agent to pull log data from multiple sources across your network and aggregate them into a single system. You’ll need at least one agent per server. Once data reaches Graylog’s central server the data can be searched and sorted to create actionable insights and increase business intelligence.
Key Features:
- Log collector and consolidator
- Creates and manages log files
- Data viewer
- Query Builder
- Free version
Why do we recommend it?
Graylog is a log analysis tool that can be used for IT system performance monitoring or security analysis. There is also a free edition, called Graylog Open. The free system is adaptable and you can create your own data analysis tools with it. The two paid versions are Graylog Operations and Graylog Security.
Rather than a free trial, Graylog offers its open-source edition to anyone who would like to start using its log management in a limited fashion. This allows Graylogs’ customers to get familiar with the product in their environment for longer than a typical trial would allow for. The open-source version is incredibly generous and provides 10 of the 18 core features completely for free. As you’re setting up Graylog, advanced search and queries can be executed right away even while Graylog is still pulling in data. While understanding and crafting your own insights from raw data might take time, a feature called Content Packs helps streamline this process as quickly as possible.
Content Packs allow you to import a template of combined sets of inputs, data streams, alerts, and dashboards. Common content packs could range from authentication monitoring to DNS reliability reports. These templates allow you to plug in your current data streams and get value quickly without having to start from the ground up.
Graylog has an entire community-driven marketplace that exchanges different config files and Content Packs with other Graylog users. You can even create your own Content Packs from existing configurations through a simple wizard in the Content Packs section of Graylog.
The way Graylog was built allows the product to be a powerful log management tool whether you’re a small dev team or Fortune 500 company. Features like Sidecar allow you to replicate your data streams across multiple clients or networks while still staying consistent. Sidecar works by utilizing a tagging feature for each and every config file an agent uses to pull data. This means no matter how many servers you pull logs from, you’ll be confident the data is consistent for every environment.
At the heart of Graylog’s features is the correlation engine. This feature gives you the building blocks to correlate multiple sources of information into big-picture business intelligence. Creating in-depth correlations across data will definitely require the work of a professional. Simpler tasks such as monitoring uptime or detecting a brute-force login attack can be done by following an intuitive ruleset builder in the correlation engine dashboard.
If you’re using Graylog Open Source, you’ll be on your own when it comes to support. There is extensive documentation as well as a large community that can help answer your questions. For the Enterprise version of Graylog support is available Monday through Friday, 9 AM UTC/3:00 AM EST 2 AM UTC/to 8:00 PM EST. Support can be accessed via email or phone and has no limitation to the number of tickets you can enter with them. Graylog also provides custom onboarding support for their new enterprise customers.
While Graylog has plenty of upsides, it’s not without its issues. In order to expand Graylogs functionality, you’ll need to utilize other tools that may have issues and learning curves of their own. For example, expanding the graph functionality would require a tool such as Grafana to integrate into Graylog.
Graylog is excellent at what it does but would prove to be frustrating for someone who needs multiple features that fall outside of its scope.
Who is it recommended for?
Graylog is evolving the same way as Splunk did previously. In fact, it looks as though Graylog is following Splunk’s strategy of adding value with pre-written system performance and security monitoring packages. Like Splunk, Graylog is available as a SaaS package or for on-premises installation on Linux
Pros:
- Was built to un-silo and ingest large amounts of data
- Uses simple widgets to create custom reports, dashboards, and monitors
- Offers Content Packs, which act as add-ons to help interpret data faster
- Additional features can be found on the user-powered community marketplace
Cons:
- The open-source version isn’t the best option for large enterprises
Graylog Open Source is completely free, while Graylog Operations and Garlog Security are priced per server at $1,250 for Operations and $1,500 per server. Pricing from this point will increase depending on your data usage needs per day.
See also: Graylog Review
Splunk
Splunk defines itself as a “data to everything platform” that allows you to gain insight from both structured and unstructured data types from data generated and from practically anywhere. Splunk is a large company and currently serves 92 of the Fortune 100 companies, which gives it proven experience with enterprise levels of information. While Splunk does not have an open-source version, it does offer a free trial.
Key Features:
- Flexible data management tool
- Log manager option
- Highly customizable
- SIEM option
- Machine learning module
Why do we recommend it?
Splunk is a leader in the data analysis field. Without any add-ons, it is an excellent, flexible tool that allows anyone to build an application based on input time-series data such as the information from log messages. Splunk now has many units, including Splunk Enterprise Security and Splunk Observability.
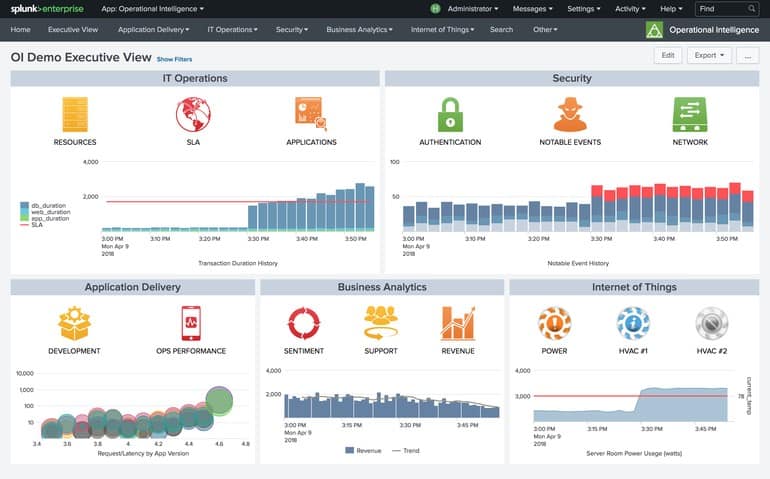
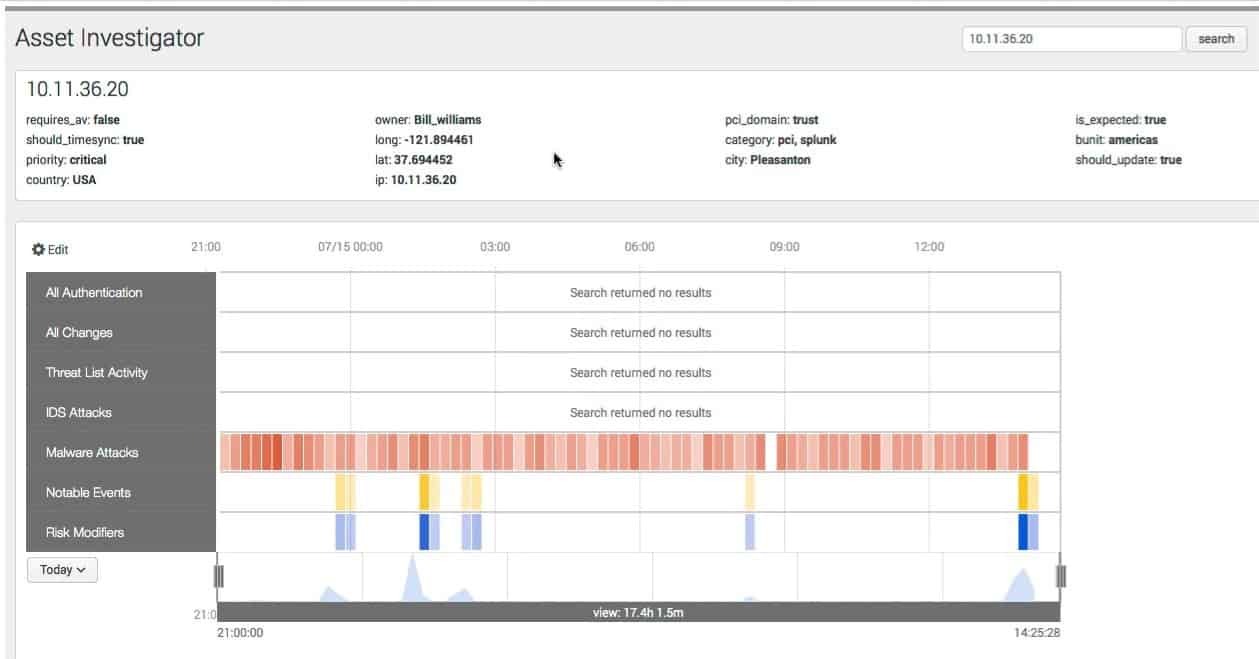
The Splunk platform focuses on providing a simplistic dashboard overview of key insights and alerts while doing the heavy lifting on the back end. Splunk leverages Artificial Intelligence (AI) and root causes analysis to comb through your logs and data streams to keep you alerted to critical events and helps you make data-driven business divisions while on the fly.
The dashboard section has a complete internal integration to allow for SLAs and KPIs to be compared against the current status of the service. This helps you identify both critical alerts as well as whether or not goals are being met. A similar dashboard called Glass Table gives you an alternate look into your data through the lens of financial and operational performance. Metrics like average order values, customer satisfaction, and uptime can all be viewed to allow you to see directly how outages or issues impact the bottom line.
All data views and dashboards can be customized based on roles and departments to ensure that key team members have access to the information and insights that are relevant to their responsibilities. Analyzing data is a bit more intuitive than Graylog and allows you to drag and drop information-rich graphics into swimlanes or charts for manual comparison.
Splunk has shown that it’s consistently working to improve not just how data is gathered, but how it is experienced and interpreted. Dashboards and data can be accessed through the Splunk Mobile app as well as through Splunk TV, which was designed to allow network operation centers and large departments access to critical data in large open areas.
Impressively, Splunk Augmented Reality (AR) allows you to scan a QR code or NFC tag to ‘see’ your data and where it’s being generated in physical space. While some might see AR data as a gimmick, in reality, it provides on-site technicians with real-time information without having to sort through dashboards or spend time correlating virtual graphics with physical machines in the field. Splunk AR proves to be particularly useful to field technicians and industries such as manufacturing and energy.
Unlike Graylog, machine learning can be applied to data streams right from inside of Splunk without programming or even any general directive. As Splunk AI monitors your data it can help you create baselines that help you detect anomalies, catch concept drift, and get an accurate reading on how your average performance is over time.
Splunk also offers a library of preconfigured modules that allows you to get fast insights from your raw data. This is similar to how Graylog utilizes Concept Packs. Modules are a collection of key metrics, dashboards, and alerts that are designed to give you the most commonly requested insights as an out-of-box solution. The key difference here is that all modules are created by the Splunk team, and not built by the community.
Who is it recommended for?
Graylog and Splunk have the same market. They are both good at sorting through large volumes of data so the full capabilities of their expensive paid packages would be wasted on a small company. Splunk no longer has a free version, which means it loses out to Graylog in the small business market.
Pros:
- Uses excellent visuals to display collected data and insights
- Supports a multitude of environments for data collection
- Uses machine learning to identify new data sources and monitor behavior
- Caters to enterprises with excellent support and a wide range of integrations
Cons:
- Many features and services cater to large enterprise networks
Splunk pricing varies depending on multiple factors such as data usage and infrastructure. You can expect pricing for Splunk Enterprise to start at $2000.00 per year at the 1GB/day data plan.
See also: Splunk Review
Key Differences Between Graylog vs Splunk
While both Graylog and Splunk can provide excellent log management and intelligence, there are some key differences between the two which are important to consider if you’re working on narrowing down your decision.
- Graylog and Splunk use different software architecture. Graylog utilizes the REST architecture for API integrations and connections to other services, whereas Splunk supports CLI, REST, or SOAP.
- Graylog has the power of an open-source community. While Splunk may be larger in size, Graylog has a community of dedicated users who help share information, create templates, and troubleshoot issues amongst each other.
- Splunk has more built-in solutions. If you’re looking to use less third-party tools while increasing functionality in your data, Splunk has many different AI, machine learning, and graphical analysis tools that are already part of the Splunk platform. Graylog requires integrations into other services which might make operations more complex.
So which solution is right for you? While both are great products, smaller businesses with more time to experiment and set up their log management will likely find Graylog to be a better fit. Graylog is a great choice if you don’t need to see the need to expand on features that already exist, or apply artificial intelligence to your data streams.
For larger companies or those who need to move quickly, Splunk has perfected the art of creating out of box insights on an enterprise level. Splunk has multiple log management solutions as well as other data services that can help you scale, and leverage the power of AI and machine learning.
What should you look for in an alternative to Graylog and Splunk?
Our methodology for selecting log management systems like Graylog and Splunk
We reviewed the market for log management systems like Graylog and Splunk and analyzed tools based on the following criteria:
- Log collector and consolidator
- Log file management
- Prewritten SIEM system
- Option to create applications based on data queries
- Data analysis tool
- A free trial or a demo that provides a no-risk assessment opportunity
- Value for money, represented by a log management system that is offered at a good price or a free tool that is worth using
With these selection criteria in mind, we have identified log management tools similar to Graylog and Splunk.
Graylog and Splunk Alternatives
To get a complete list of the best SIEM tools, be sure to check our breakdown of the best SIEM tools post. If you’re still searching for the right log management solution?
Check out our shortlist of alternatives for Graylog and Splunk:
- Datadog Leverages real-time and historical data to provide actionable insights, automated remediation, and alerting across your cloud or on-premises environment.
- ELK Open-source tool dedicated to free log management and incorporates tools such as Elasticsearch, Logstash, and Kibana for extended functionality.
- LogStash Developed by Elastic, LogStash makes data management affordable for almost any business with its flexible monthly service plans.
- SumoLogic Combines data across all sources to develop operational, security, and business intelligence with a pricing structure that utilizes a credits system based on usage.
- Sentry.io Provides logging solutions primarily focused on serving software development teams and the DevOps industry.
Graylog and Splunk FAQs
Is Graylog a SIEM?
Graylog is a log management package. That in itself is not a SIEM. However, SIEMs are security systems that search through log files and Graylog offers Graylog Security, which performs that function. So, Graylog is not a SIEM but it offers one as an extra service.
Is Splunk a SIEM or soar?
Splunk is a data analysis tool, so it can be used to search through and format any type of data collection – that includes log files. Splunk offers an add-on package, called Splunk Enterprise Security, which is a SIEM. It also offers a data processing and gathering service that performs SOAR – this is called Splunk SOAR.
Can we automate Splunk?
Processing data through Splunk can be automated. You can achieve this either through mechanisms offered within the Splunk environment, such as Splunk SOAR, which coordinates data exchanges with other tools, or you integrate Splunk into other system data management packages. A third option is to use a task automation tool that is able to launch Splunk from within its batch scripts.