The FortiSIEM system is a Security Information and Event Management (SIEM) package. SIEM is a combination of two security protection methodologies: Security Information Management (SIM) and Security Event Management (SEM).
What is SIEM?
SIM systems examine log records to look for patterns that indicate suspicious activity. SEM methods watch real-time events, such as network traffic patterns and user activities.
Each method has its weaknesses. For example, SIM detects intrusion or insider threats after the fact. This security strategy is very effective at spotting malicious activity, such as data theft, but only after the damage has already been done. SEM is instant, and so has a better chance of blocking the damaging activities of miscreants before it is too late. However, instant data monitored in one location often doesn’t spot stealthy attackers. It is only when information on several seemingly unrelated events in different locations are linked together that the intrusion is revealed.
The combination of SIM and SEM into SIEM creates a much stronger protection strategy – the strengths of SIM make up for the weaknesses in SEM and vice versa.
About FortiSIEM
Fortinet has a strong track record in cybersecurity and system defense, so, naturally, the company should launch a SIEM product. FortiSIEM has all of the guile of the combined approach of SIEM backed with all of the expertise of Fortinet.
FortiSIEM started life as AccelOps, a SIEM solution produced by a company of the same name. The company engaged in security threat analysis and research, offering intelligence and consultancy as well as the SIEM software. Fortinet bought AccelOps in June 2016. The expertise of AccelOps integrated well with the Fortinet team, and the new subsidiary’s main product was relaunched as FortiSIEM.
Related post: The best Fortinet analyzers
FortiSIEM features overview
As a SIEM system, FortiSIEM implements a range of threat detection strategies simultaneously. Here are some of the key actions of the security framework.
Combined security and network operation monitoring
As well as examining logs for notifications of transactions when looking for unusual activity, FortiSIEM harnesses information from data sources. These data sources are typically used for network performance monitoring, namely alerts from the Simple Network Management Protocol (SNMP traps).
To implement the SEM part of SIEM, FortiSIEM needs to keep an eye on the traffic circulating on the network, looking for suspicious activity. Effectively, this shadows the functions of any standard network monitoring system.
Monitoring of device and software configuration changes
Network equipment needs to be hardened against attack vulnerabilities. Hackers know this and regularly probe ways to alter device configurations to make undetected access to the network easier. FortiSIEM detects and reverses those changes.
Deployment of AI machine learning techniques
Security software rarely gets the perfect template of typical user behavior out of the box. FortiSIEM begins operations with a standard profile of expected user behavior but adjusts this over time through a machine learning process. This establishes a baseline of reasonable activity. Divergence from that standard is then flagged as unusual – this is called User and Entity Behavior Analytics (UEBA).
Risk scoring
The breach of some devices would be more catastrophic than the breach of others. FortiSIEM accounts for this fact through risk scoring, enabling monitoring to be heightened for critical pieces of network equipment. The same prioritization also takes place for user accounts and user roles.
Real-time distributed event correlation
An effective SIEM system needs to compile event data drawn from many different locations on the network. Typically, this task is performed on data drawn from log files, which offer retrospective information. A stealthy intruder can erode system security through a series of seemingly innocuous actions.
An elaborate list of detection rules helps identify typical combinations of actions that indicate a threat. Unlike most SIEM services, FortiSIEM is able to work its activity combination rules – termed “event correlations” – in real-time rather than waiting for records to be written into log files.
Autodiscovery and configuration management database
FortiSIEM operates a network discovery system that seeks out all devices connected to the protected network, compiling an asset inventory from its findings. This inventory is maintained in real-time, so any changes to the equipment inventory are automatically noted.
This service will particularly please businesses that are following the ITIL standards because it automatically creates a configuration management database (CMDB). The CMDB is central to the Configuration Management process of ITIL asset management.
User identity mapping
Thanks to DHCP, identifying users by an IP address is not straightforward. Systems that admit external users, such as customers or remote workers also have difficulties when trying to identify individuals. Add in the variations in IP addresses that VPNs and IP switchers create and it can be really difficult to tie together all of the actions of a single user.
Even user accounts and system authentication can be duped sometimes and pre-authenticated guests are able to wreak havoc without logging in. FortiSIEM uses MAC address tracing and other fingerprinting techniques to remove the reliance on the IP address as the sole identifier of each user or visitor.
Log parsing
Log parsing is the central SEM strategy of any SIEM system but the quality of SIEM software can be seriously impaired by inefficient and slow text searches. Fortinet beefed up its log search methodology for FortiSIEM with a patented log analysis system.
Threat intelligence feeds
Fortinet runs FortiGuard Labs, which researches new cyber attacks and viruses. The threat intelligence produced by FortiGuard is fed into all running instances of FortiSIEM around the world.
Fortinet also compiles “indicators of compromise,” which link together attacks produced by the same hacker groups, leading to the knowledge of attacks that could follow on from an initial intrusion or infection attempt.
Key Features:
- Real-Time Event Correlation: Continuously monitors and analyzes incoming security data to detect threats as they happen.
- Log Management: Collects, stores, and analyzes log data from various sources.
- Combined SOC and NOC Analytics: Integrates Security Operations Center (SOC) and Network Operations Center (NOC) analytics with a Configuration Management Database (CMDB).
- Highly Scalable Architecture: Can handle large volumes of data and scale as needed.
- Unified Interface: Provides a single, easy-to-use interface for managing security operations.
FortiSIEM configuration options
FortiSIEM is available in three configurations:
- A network device
- On-premises software
- Cloud service
Each option has its benefits and detractions.
FortiSIEM appliance
The Network device is similar to a hardware firewall. It just plugs into the network like any other device. As a participant in the network, it is able to sample all passing traffic, similar to a packet sniffer.
The advantage of using the hardware option is that the device includes memory and processors, so it doesn’t put any load on any existing servers, and it doesn’t require any extra disc space. However, this is the most expensive of the three FortiSIEM options.
There are three models of the FortiSIEM device:
- FortiSIEM 500F – 5,000 events per second, 3 TB storage
- FortiSIEM 2000F – 15,000 events per second, 36 TB storage
- FortiSIEM 3500F – 30,000 events per second, 72 TB storage
Clearly, the larger the model is the higher its price. It is important to get a clear estimation of your network traffic throughput before ordering one of these devices. This is so that you do not overpay for unneeded capacity, nor do you under provide for your network traffic to be fully analyzed.
On-premises software
The software option isn’t as straightforward as just installing a download on the server. The FortiSIEM service requires that a hypervisor is present to support it. The system will run on top of VMWare vSphere, KVM, Microsoft Hyper-V, and OpenStack.
If you already have one of these systems installed and operating, the software option is very attractive because it has very little extra requirements for in-house skills in order to operate it. If you don’t have any virtualization on your servers at present, getting a hypervisor operating will be an extra task in which you might not be prepared to invest.
Cloud service
The hosted cloud-based option is the easiest route to go down – it doesn’t require any specialized hardware, and you don’t need dedicated technicians in order to use it. However, some businesses are still wary about outsourcing hardware and software under the Software as a Service (SaaS) model because it seems that allowing data about the system to leave the building will inevitably weaken security.
Transmission security is covered by encryption, so hackers are blocked from intercepting communications between your site and the Fortinet cloud server where analysis takes place.
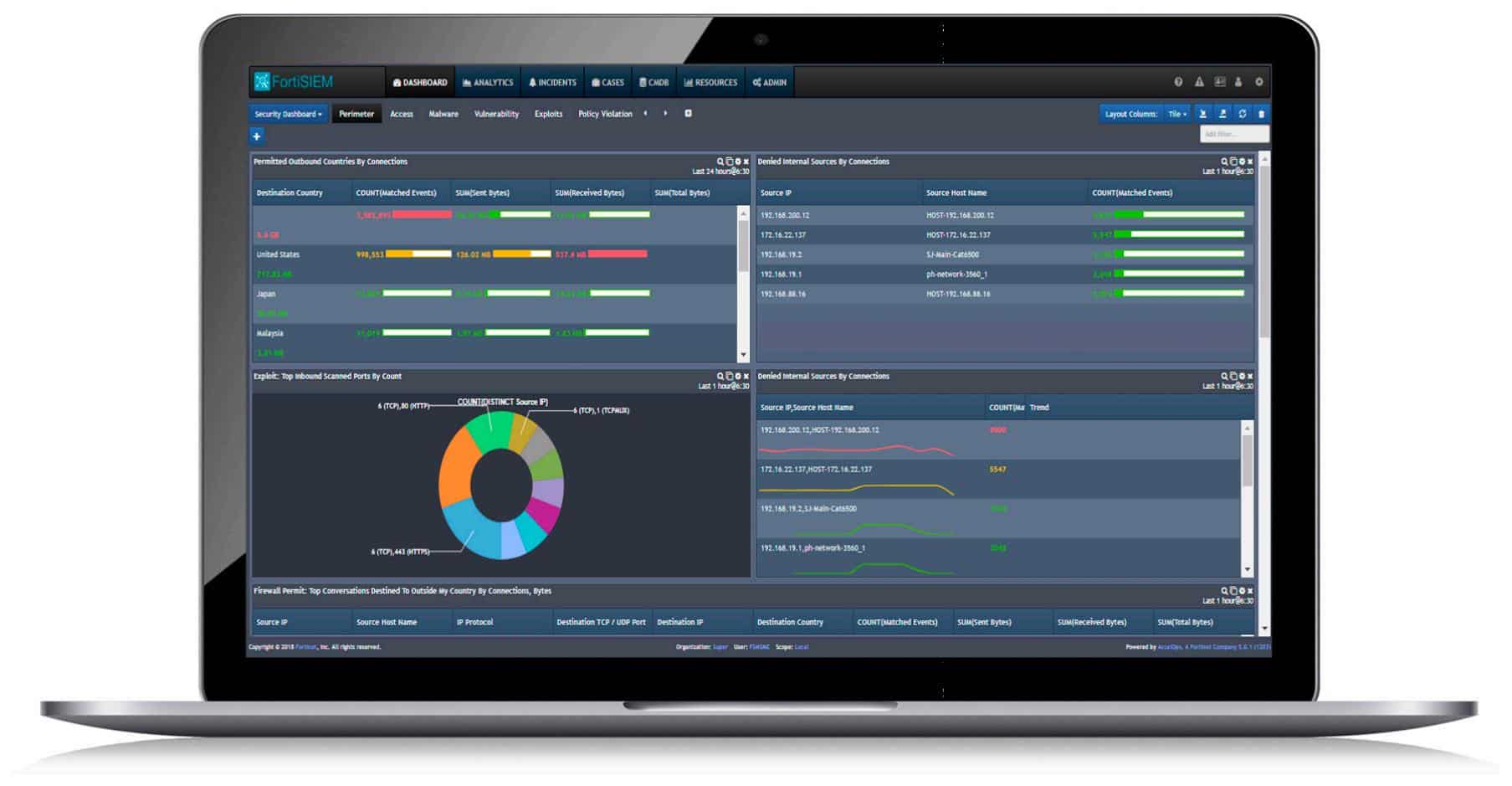
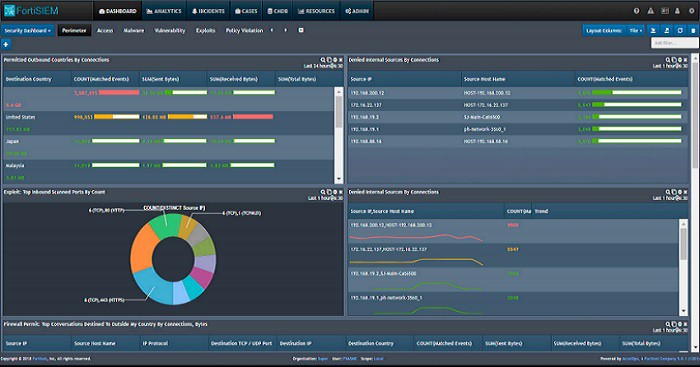
Dashboard
The user console of the FortiSIEM system combines standard “out of the box screens” and opportunities for customized screens.
Standard screens
The main screens that any network manager is going to look at on a day-to-day basis are the summary screens. These show live data statistics concerning the performance of the company’s infrastructure.
There is a screen for the network, and one for servers, which can be switched to focus on each server. There are also screens for virtualizations; this section is particularly important for those businesses that run the FortiSIEM software on-premises. This is because the SIEM service relies on this VM for its operating system.
Apart from the overall system monitoring screens, there are individual screens that examine the activities of specific applications and services. Those will only be activated if the autodiscovery sweep of FortiSIEM detects the presence of those systems. Examples of such features include Office 365 and Amazon Web Services.
Summary screens give drill-down access to detail screens. All of the standard screens of the service represent data in a spreadsheet format. Data can be sorted by each column in the display and also extracted to analysis utilities.
Customizable screens
The parts of the FortiSIEM dashboard that can be customized are called the “widget screens.” A widget is a data representation panel. The user can decide which piece of information is going to be shown in a panel and how it will be represented. This could be a list, a graph, or a chart.
The layout of a widget screen is more attractive and allows for mixed sources of information. As network managers become more comfortable with the different administration screens of the FortiSIEM system, they will begin to assemble widget screens and use those instead of the standard screens.
Attack mitigation
FortiSIEM doesn’t just detect suspicious activities; it can also take automatic action to block those movements. The service is able to interact with several utilities on a network, such as firewalls and access rights systems to block an IP address from accessing the network or shut down a user account. The SIEM system can communicate directly with individual devices to restore configurations and protect log files from tampering.
Pros:
- User Entity and Behavior Analytics (UEBA): Detects anomalies in user behavior to identify potential security threats.
- Extensive Reporting: Offers customizable and compliance-focused reporting, including hundreds of built-in reports.
- Threat Intelligence: Integrates commercial, open-source, and FortiGuard threat intelligence.
- Integration: Seamlessly integrates with Fortinet products and other third-party solutions like Cisco and Palo Alto.
- Comprehensive Reporting: Includes built-in reports and customizable options for compliance.
Cons:
- Complex Configuration: Can be challenging to set up and configure.
Compliance reporting
The FortiSIEM package includes report formats that are necessary to prove compliance with PCI-DSS, HIPAA, SOX, NERC, FISMA, ISO, GLBA, GPG13, SANS Critical Controls, COBIT, ITIL, ISO 27001, NERC, NIST800-53, NIST800-171, and NESA. You can find more details on the datasheet.
The best FortiSIEM Alternatives
FortiSIEM is by no means the only SIEM system available on the market today. For more detailed information about how SIEM systems work, please see our post on the Best SIEM Tools.
Here is our list of the best alternatives to FortiSIEM:
- ManageEngine EventLog Analyzer (FREE TRIAL) Log file analysis that provides SIM; add to OpManager for SEM. It installs on Windows, Windows Server, and Linux. Access the 30-day free trial.
- Datadog Security Monitoring A cloud-based network monitoring system with integrated SIEM function.
- Splunk Enterprise Security Network monitoring with log management plus analysis tool. It installs on Windows and Linux.
- OSSEC A free open-source intrusion detection system that focuses on log analysis. It runs on Windows, Mac OS, Linux, and Unix.
- LogRhythm NextGen SIEM Platform AI-based traffic and log analysis tool. It installs on Windows and Linux.
- SolarWinds Security Event Manager A SIEM tool from SolarWinds, which is the leading infrastructure management tool provider. This tool integrates with SolarWinds network monitoring tools and runs on Windows Server.
- AT&T Cybersecurity AlienVault Unified Security Management Multi-strategy IDS and SIEM. It runs on Mac OS as well as Windows.
- RSA NetWitness Network traffic analysis for SIEM aimed at large businesses. It runs on a VM.
- IBM QRadar A SIEM tool with risk assessment and attack modeling. It runs on Windows Server.
- McAfee Enterprise Security Manager A SIEM tool that interfaces with Active Directory. It runs on Mac OS as well as Windows.
FortiSIEM FAQs
How does FortiSIEM support multi tenancy?
FortiSIEM supports multi-tenancy in a Service Provider implementation. The account holder has to activate this setting and then identify data sources. During this process, the FortiSIEM system installs data collection agents on the sites allocated to the client account. This information is only loaded into the client sub-account in the user dashboard.
How do I add a device to FortiSIEM?
It shouldn’t be necessary to add a device to FortiSIEM manually because the service runs a discovery routine that automatically detects all devices. This function repeats periodically, so if you don’t see the new device immediately, wait until the next system sweep for it to appear. If, for some reason, you still need to manually add a device, you can do this by going to the Supervisor dashboard. Click on CMDB, look in the Device View section, and click on Devices. Look at the device category that relates to your new equipment and click on Nw. This brings up a form for you to fill in with the device’s details.
How do I add FortiGate to FortiSIEM?
First, check that FortiGate is set up to gather the information types that FortiSIEM needs. Then move on to the FortiSIEM setup:
- Log into FortiGate as Administrator and go to Network on the System menu.
- Edit the interface that you will use for FortiSIEM. Under Administrative Access, ensure that SSH and SNMP are selected. Click OK.
- Go to Config on the System menu and select SNMP v1/v2c.
- Click Create New to enable the public community.
Switch to FortiSIEM. When the Discovery process runs, it should identify the FortiGate device and use it as a data source.