Fortinet and Palo Alto Networks are both innovators of firewalls and leaders in the market for them. Now the network security industry is moving into Zero Trust Access and Fortinet and Palo Alto Networks are both vying for leadership in this new area of security.
What is Zero Trust Access?
Zero Trust Access (ZTA) is a modern cybersecurity framework designed to enhance data security and reduce the risk of breaches by eliminating implicit trust within a network. Unlike traditional perimeter-based security models that assume devices and users inside the network are trustworthy, Zero Trust operates on the principle of “never trust, always verify.” This approach ensures that every user, device, and application attempting to access resources is continuously authenticated and authorized, regardless of their location—inside or outside the network perimeter.
At its core, ZTA emphasizes strict identity verification, least-privilege access, and continuous monitoring. It requires users and devices to prove their identity and security posture before being granted access to specific resources. This granular access control minimizes exposure by ensuring that users only have access to the data and systems necessary for their roles.
Key components of Zero Trust Access include:
- Identity and Access Management (IAM): Tools like multifactor authentication (MFA) and single sign-on (SSO) ensure secure identity verification.
- Endpoint Security: Ensuring that devices meet security requirements, such as having updated antivirus software or specific configurations.
- Microsegmentation: Dividing the network into smaller segments to limit lateral movement in case of a breach.
- Continuous Monitoring: Using analytics and AI to detect and respond to anomalies in real-time.
The Zero Trust model is particularly effective in today’s environments where remote work, cloud services, and IoT devices blur the traditional network boundary. By verifying every access request dynamically, ZTA reduces the attack surface, protects sensitive data, and enhances compliance with security regulations. Organizations adopting Zero Trust Access benefit from a proactive and resilient security posture that adapts to evolving cyber threats.
You can read more about Zero Trust Access in our guide, Zero Trust Architecture Explained.
About Fortinet
Fortinet is based in Sunnyvale, California and until recently, its main product was a hardware firewall, called FortiGate. The company has moved into edge services, which center on a cloud-based firewall, which took it one step closer to ZTA.
The business began operations in 2000. It was started and is still run by two brothers, Ken and Michael Xie. The business has 9,700 employees and its revenue in 2021 was $3.342 billion.
The company’s marketing advantage came from its design for the FortiGate network appliance. This has a custom-designed architecture that speeds up data processing. The entire family of products from this provider slot together into what the company calls the Fortinet Security Fabric.
The edge services offered by Fortinet include a Firewall-as-a-Service, a secure web gateway, A SASE system, network access control (NAC), a secure SD-WAN, DDoS protection, a cloud access security broker (CASB), cloud workload security (CWP), cloud security posture management (CSPM), email security, a SIEM, and load balancing. These services can be implemented on the cloud or a FortiGate appliance. They all combine well because they involve processing data as it passes across the boundary of a network. The ZTA system of Fortinet is created through a combination of services.
About Palo Alto Networks
Palo Alto Networks was started by Nir Zuk in 2005. Zuk is credited with creating the first stateful firewall while working for Check Point. The company is based in Santa Clara, California, and has a total of 11,098 employees worldwide. In 2021, the business’s revenue was $4.256 billion.
Palo Alto Networks uses the cloud for its main delivery model. However, it also offers its firewall software as a virtual appliance and as a physical network device. The firewall is still the main product of Palo Alto Networks. However, the company has branched out to offer edge services that can be offered in combination with the firewall.
The product list of Palo Alto Networks includes a SASE, an SD-WAN system, and a Firewall-as-a-Service package. The company also offers a secure web gateway, cloud workload protection, cloud security posture management, and a cloud access security broker. The company has so many modules available that several different package combinations will assemble a ZTA strategy.
Fortinet Zero Trust Access
Fortinet’s ZTA solution is an add-on for the FortiGate firewall. The group of services that make up the ZTA solution includes:
- FortiSASE Secure access service edge system that provides a secure web gateway
- FortiClient Endpoint agent that provides secure connections and controlled access to the Fabric
- Fortinet ZTNA Controls access to applications
- FortiAuthenticator An identity and access management service that creates a single sign-on environment within the Fabric
- FortiNAC Network access control system that protects communications with IoT devices and can also be used to secure BYOD access.
The way these services slot together is that the FortiClient locks the remote devices of WFH employees into the FortiSASE system. Essentially, this is a VPN.
The FortiSASE brokers access to resources in and out of the network, referencing FortiAuthenticator for access permissions. FortiSASE can send traffic into the network through the FortiGate firewall or off to another site over a secure connection to that location’s FortiGate appliance. If the requested service is a SaaS system, the FortiSASE service mediates traffic to that package, implementing an autologin.
Meanwhile, BYOD and IoT devices get secure access to your network with FortiNAC, which acts like a containerization service.
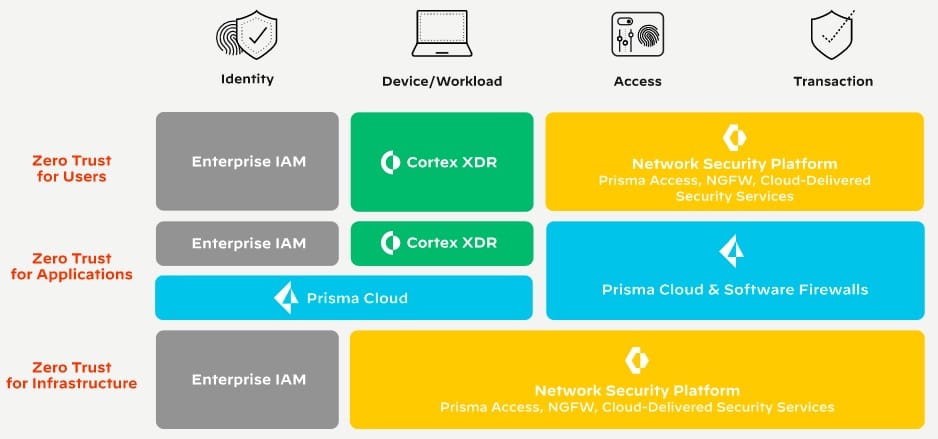
Palo Alto Zero Trust Enterprise
Palo Alto Networks groups its ZTA systems under the umbrella, Zero Trust Enterprise. Each of those products is available individually. The Palo Alto list of services is much longer than that of Fortinet and there is a degree of overlap between its products. This means that there are several paths to assembling a Zero Trust system with Palo Alto products.
As the diagram below demonstrates, Palo Alto recommends different combinations of products depending on what type of system you want to protect.
The paths available are:
- Zero Trust for Users.
- Zero Trust for Applications.
- Zero Trust for Infrastructure.
This is confusing because, typically, a business will need all three. To bring the Palo Alto solution closer to the Fortinet system, you could boil this proposal down to two services:
- Prisma Access SASE system that connects sites, integrates remote devices, and can also be used to protect IoT and BYOD devices
- Enterprise IAM Not delivered by Palo Alto but is your existing access rights manager, either Active Directory or Open LDAP.
Prisma Access combines the following services:
- An SD-WAN for inter-site and site-to-cloud connection protection
- A cloud-based firewall to protect traffic outside the WAN
- A secure web gateway to manage the inclusion of remote computers of WFH employees plus IoT and BYOD devices into the network
- A next-gen CASB to provide authentication services into SaaS systems
Fortinet vs Palo Alto: Head-to-head
Fortinet and Palo Alto Networks are two very similar businesses. Both began as firewall providers and both created innovations in firewall technology to create market interest. Both offer firewalls as virtual or physical devices and also cloud-based firewall solutions. Fortinet is prouder of its network devices than any of its other products and while Palo Alto also has physical appliances, it pushes its cloud solutions more.
Neither company specifically offers a ZTA product. However, as you can see from the analysis above, it is very easy to assemble one from the product list of each provider.
With Fortinet, you would order a FortiGate network appliance and add on FortiSASE, Fortinet ZTNA, FortiNAC, and FortiAuthenticator – FortiClient is a free download that you get access to with the FortiSASE. The FortiGate device will be delivered with all of the ordered products pre-loaded.
Palo Alto Network can coordinate with your existing access rights management system to manage access control and enhances that for SaaS access through the CASB element in Prisma Access. Although Palo Alto presents a range of solutions, just getting the Prisma Access system will provide you with a ZTA service. You can choose to buy the Prisma Access system pre-loaded onto a PA-series network appliance or just subscribe to the cloud-hosted version.
Fortinet and Palo Alto ZTA solutions pricing
Neither Fortinet nor Palo Alto Network publishes prices for any of their products. Fortinet doesn’t offer a demo of its ZTA system because it is a combination of products, which needs to be put together, and so isn’t available off the shelf. The way to start an investigation into the Fortinet Zero Trust Access solution is to contact the Sales Department.
Palo Alto Networks can fulfill a Zero Trust Access system with one product – the Prisma Access system. That service is available for a demo.
Fortinet vs Palo Alto: The verdict
Overall, once you have waded through all of the options, Prisma Access delivered from the cloud is the simplest ZTA solution available from either of these two providers.
Although Fortinet’s products are respectably secure, Palo Alto Networks has an equal reputation for its security products and the Prisma Access tool is very thorough, providing all of the access security systems that you need.
The one big hole in the Prisma Access solution is its lack of an integrated access rights manager. However, unless you are provisioning your system from scratch, you probably already have an identity and access manager, such as Active Directory. The CASB module within Prisma Access extends your ARM to include access to cloud services. That means you don’t have to scrap your existing system and start again to get a single sign-on environment for your Zero Trust Access implementation.
As you saw from the Palo Alto diagram of how its services fit together, you can add on the Cortex XDR to get extra endpoint protection. This creates a complete and integrated security plan for your entire enterprise.