Firewall as a Service (FWaaS) is a cloud solution that protects networks from malicious traffic and viruses.
The purpose of a firewall is to protect a system. However, new tricks by hackers can make a firewall’s processes outdated very quickly. The databases and procedures of firewalls have to be updated very frequently in order to keep them proficient and that creates maintenance tasks.
Firewall maintenance can be time consuming and requires technicians to acquire special knowledge about how the firewall software works, and about cybersecurity in general. Cloud-based firewalls are easier to manage because the hardware configuration decisions and software maintenance tasks are taken care of. The people who understand each firewall best are the teams that developed them.
Here is our list of the best FWaaS systems:
- Check Point’s SASE FWaaS EDITOR’S CHOICE Cloud-based attack blocker able to protect multiple sites and also remote workers and cloud platforms. This is an advancement on traditional network-based firewalls that only protect one LAN.
- NordLayer (FREE DEMO) Package of connection and application security systems includes a cloud firewall to protect your entire virtual network. Operates on the cloud.
- CrowdStrike Falcon Firewall Management Cloud-based firewall that integrates into the Falcon Suite of enterprise security tools.
- Zscaler Cloud Firewall Flexible cloud-based firewall system that protects team member devices wherever they are located.
- SecurityHQ Managed Firewall Cloud-based firewall that includes the services of cybersecurity experts to manage the system for you.
- Aryaka Managed SASE Full virtual network with a cloud firewall included, so it provides a fully secure and private network across the internet and supplies the technicians to run it as well.
- Cato Networks SASE Comprehensive edge services platform that includes Security as a Service features, such as its FWaaS.
FWaaS packages
When users of firewalls have difficulty setting them up properly, they call the help desk of the system providers. Support call solutions can even involve the help desk technician accessing the customer’s system to fix the problem.
In an FWaaS scenario, rather than buying the software and installing it on-site, the customer subscribes to a firewall service. This includes the software, the server to run it on, storage space for log files, and the staff needed to fine-tune and maintain the system. Some FWaaS products are part of a managed firewall solution. That concept changes the perception of a firewall from a software package into a security service. A firewall element is just a tool used by cybersecurity experts who are contracted to protect a business’s IT system.
Firewall configuration options
Every firewall vendor would like to think that their system is impregnable and every firewall buyer would like to believe them. However, total confidence is a delusion. There is always the possibility that hackers will find a way around the security system.
In medieval Europe, communities defended themselves from attack by building high, thick walls around their towns. However, a new attack strategy invented by clever raiders literally undermined these defenses. They dug a tunnel beneath the walls, filled it full of wood, and set fire to it, causing the mortar in the foundations to disintegrate, leading to the collapse of the wall.
Modern hackers would like to do exactly the same thing to ruin the strength of a firewall – get under its foundations. The key vulnerability of any piece of software lies in the operating system that it depends on.
Firewall providers would have to create a very comprehensive series of checks and controls in order to monitor the system that supports its software. Ultimately, protecting the system on which the firewall is resident becomes a bigger task than protecting the network.
In order to reduce the risks of a hacker getting into the operating system and just passing beneath the firewall software, it is advisable to run the firewall software on a separate physical device.
Where firewalls are resident on servers that are shared with other applications, the firewall package includes its own operating system and is run as a virtual machine – making it impossible for any process to break out of the container and interfere with other running programs.
Onsite firewall solutions have three configurations:
- Appliance that hosts all necessary security software and controls the gateway to the network
- Dedicated Server
- Virtual Appliance
Cloud hosts offer a fourth option. Logically, if it is safer to run a firewall on a separate device as far out on the edge of the protected system as possible, it is even safer to run it on a server in an entirely separate building and operated by a separate company.
FWaaS is a category of a system that is termed an edge service. It is out beyond the boundary of the protected system. A firewall is supposed to protect a network by examining all traffic between it and the internet, so filtering all traffic somewhere else in a faraway place still creates a vulnerability. The clean traffic still has to travel over the internet to its intended destination.
Does an FWaaS customer need a second firewall to re-examine traffic coming in from the FWaaS? Having a firewall in a remote location could give hackers an easy opportunity to bypass the firewall service entirely and go directly to the unprotected network. FWaaS providers close down that option by establishing a VPN link between its servers and the protected network. The internet interface of the network is controlled by the VPN client, which will only accept traffic coming in from the FWaaS server. All transmissions are protected by encryption, making it impossible for hackers to break in and tamper with it.
FWaaS benefits
Cloud firewall providers can go all-out in their strategy to protect the firewall from attack. Serving many customers gives them the cost base that allows them to invest in clusters of servers with failover backup hardware, technicians working in shifts around the clock, and a worldwide perspective to cybersecurity.
If a new attack vector arises, the firewall provider has to come up with a solution very quickly and roll that out to all of its customers. An FWaaS provider does the same thing but rather than sending out updates to its customers all over the world, it just needs to update the software on its own servers and every customer is instantly protected by the adjustment.
The distributed software strategy of traditional onsite firewalls opens up the risk of a customer blocking automatic updates, neglecting to install a patch, failing to read a security warning notice, or just not securing their systems properly. Letting the firewall provider host the security system removes all of those weaknesses.
The best FWaaS providers
There are many firewall providers in the world and a large number of them have opened up FWaaS divisions. It can take a long time to investigate all options, so we have created this review to focus on the best providers in the field.
Our methodology for selecting an FWaaS package
We reviewed the market for Firewall as a Service platforms and analyzed the options based on the following criteria:
- Easy to set up and use
- Automated responses on threat detection
- Full event logging
- Alerts sent by SMS or email
- Integration with other edge services
- Free trial or a demo system that provides an opportunity for a no-cost assessment
- Value for money offered by strong protection provided for a fair price
Using this set of criteria, we looked for FWaaS edge services that provide constant protection.
Features Comparison Table
| Features/FWaaS Providers | Perimeter 81 | NordLayer | CrowdStrike Falcon Firewall Management | Zscaler Cloud Firewall | SecurityHQ Managed Firewall | Aryaka Managed SASE | Cato Networks SASE |
|---|---|---|---|---|---|---|---|
| Threat Intelligence Integration | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Cloud-Native Architecture | Yes | Yes | Yes | Yes | No | Yes | Yes |
| Real-Time Monitoring & Alerts | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| SD-WAN Integration | Yes | Yes | No | No | No | Yes | Yes |
| Policy Management | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Data Loss Prevention (DLP) | Yes | Yes | Yes | Yes | No | No | Yes |
| Zero Trust Network Access (ZTNA) | Yes | Yes | No | No | No | Yes | Yes |
| Multi-Cloud Support | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
1. Check Point’s SASE FWaaS (ACCESS FREE DEMO)
Check Point’s SASE, formerly Perimeter 81, is an edge service platform and its Firewall-as-a-Service is its central product. Unlike traditional firewalls, the Perimeter 81 system isn’t limited to guarding a single network. Instead, it can be used to control access to all of the resources of an enterprise. This includes the workstations of remote home workers and cloud platforms as well as all of the LANs that a multi-site business might operate.
Key Features:
- Covers Multiple Sites: Connects sites together with VPNs
- Protects the Devices of Remote Workers: Remote access VPNs
- Scalable Pricing: A per-user rate
- Offers a Single IP Address: Fronts for the company’s virtual network
Why do we recommend it?
The Check Point’s SASE FWaaS is part of a package of connection security and application access management tools. This package can create a Zero Trust Access strategy or a virtual network over the internet. The FWaaS is implemented as a dedicated IP address for incoming traffic, making Check Point’s SASE the company’s gateway.
Although this is a great security system for large, multi-site operations, that doesn’t mean that Check Point’s SASE isn’t suitable for small businesses. On the contrary. The pricing structure of the FWaaS from Check Point’s SASE favors small enterprises because it offers all of the features that big businesses get but at a rate per user per month. Also, you don’t need to employ cybersecurity experts or even have a big server to host the software. The Check Point’s SASE configuration is particularly useful for businesses that don’t invest in premises but operate virtual offices.
There are no installation fees, no minimum subscription period, and no upfront cost to using the Check Point’s SASE service. The system is very flexible because if you expand your workforce, you just increase the capacity of your subscription packager. The minimum number of users for the lowest package of Check Point’s SASE, which includes the FWaaS, is five.
Check Point’s SASE FWaaS fronts your organization, while providing connection security behind it to protect all of the communications between your own equipment that cross the internet. The FWaaS ties all of your sites together because it offers you one public-facing IP address for all of your sites. It is not difficult to use this system to unite the address space of all of your sites and remote devices into one centrally-managed network.
The entire Check Point’s SASE package offers a range of protection strategies against attacks inside your network and for internet connections through the firewall. You can choose to protect access to specific applications, which you can host yourself or subscribe to on the cloud. You also get protection from DNS-based spoofing attempts because the Check Point’s SASE package gives you a private, protected DNS system.
Who is it recommended for?
This system is suitable for businesses that have a lot of remote or roaming staff. It is able to create a company network with connection privacy across the internet. The addition of the dedicated IP address service means that all outsiders have to communicate with staff through the Check Point’s SASE cloud server, thus creating a firewall.
Pros:
- Multi-Site Management: Makes this system viable for MSPs
- Wide Variety of Integrations: Includes LDAP systems and SAML
- Protected DNS: Blocks snoopers and sinkholing
- Easy-to-Use Object-Based Configurations: Plan your own security system
Cons:
- No Free Trial: Only a demo is offered
You can examine the Check Point’s SASE system, including its Firewall-as-a-Service with a demo. All plans are covered by a 30-day money-back guarantee.
EDITOR'S CHOICE
Check Point’s SASE FWaaS is our top pick for a Firewall-as-a-Service because it offers internal network security as well as protection against attacks from the outside world. You can link all of your resources together into a unified network and monitor it centrally with this package. Your enterprise might be scattered across the globe, but Check Point’s SASE makes it seem contiguous. All of this technology that protects your network is fronted by a cloud-host firewall. You can let Check Point’s SASE technicians look after your security systems and get on with your core activities.
Download: Access FREE Demo
Official Site: https://www.sase.checkpoint.com/demo
OS: Cloud-based
2. NordLayer (ACCESS FREE DEMO)
NordLayer is a strong competitor to the Perimeter 81 package. The package includes a bundle of services that can be used to create Zero Trust Access, an SD-WAN, or a SASE. The difference between the SD-WAN and SASE configurations lies with whether you choose a dedicated IP address to front your virtual network.
Key Features:
- Inbound Traffic Scanning: Entry point of external traffic is through the NordLayer server
- Four Levels of Service: Also a deal for managed service providers
- Virtual Network: Creates a protected network across the internet
- Application Access Controls: User’s app only shows the services to which that person has been granted access
- Based on VPNs: Remote workers, sites, and cloud apps are connected together through VPNs
Why do we recommend it?
NordLayer is easy to implement and it provides equal access security for all of your users whether they are on your site or working remotely, Similarly, the service treats access controls for all applications in the same way, whether you host those systems or get them as SaaS packages. The cloud firewall can be a simple block on incoming connection requests or a full malware scanning service.
With this service, you expand on a VPN system to connect sites together and securely include remote workers in your home network. All workers get an app that grants access to the network, whether they are in the office or elsewhere.
The app includes a menu of services that the user has been given permission to use. Clicking on an option takes the user through to that application and automatically logs in. This is a single sign-on service that reduces the burden of having to log in again and again to use every resource.
The services that each user can access might be on your site or they might be cloud SaaS applications, such as Word on Microsoft 365. Each connection between a user and a service is protected with a VPN. The NordLayer server acts as a hub, authenticating users and only allowing forward connections to be made after authorization.
The combination of VPNs effectively creates a virtual network that includes both the site network and the internet. All traffic has to pass through the NordLayer server. That includes traffic traveling out of the virtual network to external sites. Traffic traveling in has to pass through the NordLayer server because that is the host of the dedicated IP address that your company gets with a NordLayer subscription.
The dedicated IP address provides one level of cloud firewall service because it masks the true IP addresses of your sites and remote users. The two higher plans of NordLayer also offer extra malware scanning services to provide a full cloud firewall.
This package provides VPN connections between remote workers, sites, and cloud services. The access app for each user integrates a menu of services, which limits the visibility of the applications that an organization uses so only those users who are assigned accounts on those services can see them. By taking a plan that includes a dedicated IP address, a company gets a cloud-based firewall-as-a-service. This is because all external devices connect to the company through that IP address, which is hosted on the NordLayer server. The NordLayer system strips out traffic floods and malicious traffic before passing clean traffic on to its destination over a secure connection.
Who is it recommended for?
This system is ideal for small and mid-sized enterprises. Even owner-managers with few technical skills will be able to set up and manage a sophisticated access control service with a cloud firewall in the NordLayer administrator’s console. There is a five-user minimum for any NordLayer plan.
Pros:
- Device Posture Security: Each device is scanned for security threats before it is allowed to connect
- Simple On-Device App: Combines access controls for the connection and for all applications
- Access Controls: System has an integrated access rights manager in the console
- Single External Identity: Dedicated IP address provides a single gateway between all company locations and the outside world
- Single Sign-On: Login for the access app flows through to all application access
Cons:
- No Free Trial: Get a 14-day money-back guarantee
The subscription rate for NordLayer is per user and it doesn’t matter whether they are all on one site, spread over several offices, or working from home. The system has four plans and the lowest, Lite, doesn’t include a firewall. You get the basic firewall that blocks incoming connection requests with the second plan, which is called Core. The Premium plan includes the full malware scanning firewall and the Custom plan’s components are up to you. NordLayer doesn’t offer a free trial but you can get a demo.
3. CrowdStrike Falcon Firewall Management
CrowdStrike Falcon is an enterprise security suite that delivers next-gen AV and endpoint protection. The Falcon system includes a number of modules and the Firewall Management component is an optional extra.
Key Features:
- Firewall Coordinator: Provides a central location for firewall rule planning
- Interacts with On-Site Firewalls: Gathers activity data
- Enhances Third-Party Firewalls: Implements standardized security policies
Why do we recommend it?
The CrowdStrike Falcon Firewall Management package augments your existing on-premises firewalls rather than replacing them. This is a cloud console that interacts with your existing firewalls to interpret your preferred security policies into firewall rules. The system also gathers notifications from those firewalls and coordinates them into a unified protection system.
As with the endpoint protection system from CrowdStrike, the Falcon Firewall Management module is resident in the cloud and also relies on an installed agent onsite to gather data and implement workflows. The tool protects the network and each endpoint, creating a two-phase protection service.
The CrowdStrike Falcon dashboard is delivered from the CrowdStrike server and accessed through any standard browser. That means that it is available anywhere and the administrator does not need to be in the same location as the protected system. It also means that remote workers and different sites can all be protected and managed from one central console.
Even though it is a distributed system, the central Firewall Management console enables administrators to impose the same rules and policies on all protected devices. This unifies the firewall, making it operate as a single entity.
Although there are onsite elements to the CrowdStrike Falcon system, the bulk of processing, such as threat hunting and traffic scanning, is carried out on the cloud servers. This greatly reduces the hardware requirements of the business using the service. It also means that network administrators don’t need to worry about keeping the system updated or providing failover hardware because all of those issues are dealt with by the CrowdStrike staff.
Who is it recommended for?
This service works best when combined with other CrowdStrike products to create a multi-level XDR service. The core product of the CrowdStrike Falcon system is an anti-virus package that needs to be installed on each device, called CrowdStrike Falcon Prevent. However, the Firewall Management service will also work as a standalone product.
Pros:
- Dual Level Operations: Combines FaaS and endpoint protection through a single platform
- Machine Learning: Tracks and alerts anomalous behavior over time, improves the longer it monitors the network
- Lightweight Agents: Won’t slow down servers or end-user devices
Cons:
- 15-Day Trial: Would like to see a longer trial period
Falcon is available in four editions; Falcon Pro, Falcon Enterprise, Falcon Premium, and Falcon Complete. None of those plans include the Firewall Management module automatically – it has to be added on. The Falcon Complete option is a bespoke plan that includes a managed security service and a Breach Prevention Warranty. Potential customers can get a 15-day free trial of the Falcon security suite.
CrowdStrike Falcon Firewall Management is a great FWaaS because it provides a nice blend of network and endpoint protection. The service is charged for by subscription, so there are no upfront hardware or software costs with this security system. Thanks to the cloud architecture of CrowdStrike Falcon Firewall Management, administrators can include protection for remote workers and other sites into the home network protection plan.
Get a 15-day free trial: go.crowdstrike.com/try-falcon-prevent.html
OS: Cloud-based
4. Zscaler Cloud Firewall
Zscaler built its FWaaS system with virtual offices in mind. The company noted that traditional business practices that involve crowding all workers into an office space is no longer valid. This system offers a solution that allows remote workers to safely connect to the business network and enjoy protection from the corporate firewall while working.
Key Features:
- Unifies Multiple Sites: Connects with VPNs hubbed through the Zscaler server
- Covers User-Owned Devices: Access is through an app
- Intranet Connection Security: All app access goes through the Zscaler authenticator
Why do we recommend it?
The Zscaler Cloud Firewall is part of a package of tools that provides connection security and application access controls that build up to create a Zero Trust Access solution. The packages are flexible and you can also use them to build a virtual network. There are now many plans offered by Zscaler.
The software for the firewall service doesn’t need to be resident on the protected computer. Instead, the service just protects the connection, checking all traffic to make sure that the worker’s device doesn’t pass viruses over to the main system.
The Zscaler solution is a great idea for businesses that deploy a BYOD strategy as well as those that regularly deal with home-based workers. Whether the protected device is owned by the company or the user, the firewall service doesn’t touch the device. This means that there are no heavy background processes to drag down the performance of the device. It will even protect communications via mobile equipment.
The remote inclusion service sounds like a VPN. However, Zscaler points out that its system doesn’t just protect the privacy of connections, it implements firewall policies within the secure connection. So, it could be seen as a VPN+. It is certainly a proxy service as all traffic needs to flow through the Zscaler server, which acts as an edge system between the company’s network and the wider internet.
Who is it recommended for?
The cloud firewall is included in some Zscaler packages; it isn’t a standalone service. The system will also provide a data loss prevention function. Although the large number of Zscaler editions makes the purchasing journey complicated, implementing security with the system is relatively easy.
Pros:
- Operates in the Cloud: No compliance onboarding or infrastructure expense
- Customize Bandwidth Allocation on a Percent Basis: Good for larger networks and more granular control
- Cloud-Based Console: Access it from anywhere through any standard web browser
Cons:
- No Price List: Must contact sales for pricing
Zscaler is coy about its pricing for the Cloud Firewall and it doesn’t offer a free trial. However, it is possible to get a demo of the firewall service.
5. SecurityHQ Managed Firewall
SecurityHQ goes one step further than just hosting a firewall service, it also offers the management of the firewall. This is a great option for businesses that don’t have their own IT team or those that do but don’t have specific cybersecurity skills onsite.
Key Features:
- Managed Service: Includes the services of technicians
- Compliance Management: PCI DSS, NERC, CIP, HIPAA and SOX
- Defence Against Malicious and Anomalous Activity: Malware and human threats
Why do we recommend it?
SecurityHQ Managed Firewall is an interesting package that includes the services of system technicians and security consultants to manage your firewall for you. This is in addition to the supply of a cloud-based firewall system. The team is able to tune the performance of the firewall to specific data protection standards requirements.
IT specialists with cybersecurity expertise are hard to find and, as in any market with a shortage, their wage levels are high and constantly rising. Even if you manage to hire an expert to manage your firewall, it won’t be long before another business outbids you, leaving you with the need to go through the hiring process again.
Managed services plug the skills gap. This is a particularly useful option for small businesses that just don’t have the volume of traffic that would justify the expense of a dedicated cybersecurity expert on their staff. The other option that small businesses usually go for is to dump the responsibility for the firewall’s installation and management on an unskilled manager.
The SecurityHQ service is staffed around the clock and is hosted on a cluster of servers, which guarantees persistence. The system is run along with ITIL standards and it enables businesses to be fully compliant with PCI DSS, HIPAA, SOX, NERC, and CIP.
Who is it recommended for?
As a managed service, this proposal works out cheaper than subscribing to a FWaaS and paying for your own in-house cybersecurity specialists on the payroll. However, you will need security experts and technicians to watch over other aspects of your system, so if you have already budgeted for that staff, giving them responsibility for a firewall won’t cost much.
Pros:
- Offers FWaaS as a Managed Solution: Great for companies lacking technical expertise
- Firewall Optimization: The team will create your security policies
- Coordinates On-Device and Network Firewalls: Creates a unified protection system
Cons:
- No Price List: Ask for a consultation
SecurityHQ’s Managed Firewall is a bespoke service. There is no price list or plan schedule. You need to contact the company and ask for a free security audit in order to get a quote.
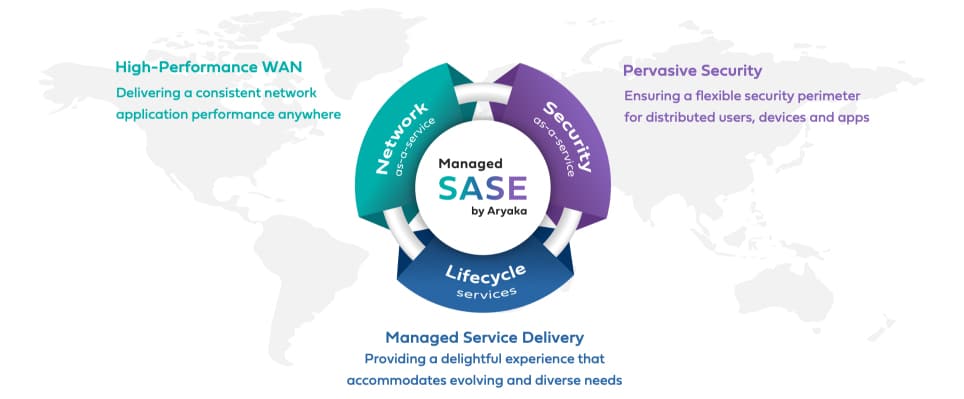
6. Aryaka Managed SASE
Ayaka Managed SASE is a secure virtual network that provides you a single network for multiple sites. This strategy integrates internet links between sites and treats them as though they were private. If you know about VPNs, you know how this can be done. The final element of the SASE is a cloud-based firewall, which acts as a secure gateway between the virtual network and the outside world.
Key Features:
- Cloud Firewall: Receives all of your traffic before it gets to your site
- Secure Private Network: Secure Access Service Edge (SASE) package
- Connects Sites: Create a software-defined WAN (SD-WAN)
Why do we recommend it?
The Aryaka Managed SASE provides an easy way that a multi-site business can merge all of its networks into one. The IP address space is unified and the stretches of internet between sites are hidden by the representation of the network. Outsiders are blocked by VPN protection and can only get in through the cloud firewall.
To understand how the SASE concept works, you first need to know about software-defined wide-area networks (SD-WANs). This is an overlay network that presents a virtual view of a big network and you don’t see that, in fact, underneath, it is a collection of different networks and internet links. Adding a cloud firewall as a gateway to the internet that isn’t included in the virtual network makes an SD-WAN a SASE, which stands for Secure Access Service Edge.
So the FWaaS is an essential element of the SASE, which is why this package is on our FWaaS list. However, Aryaka doesn’t offer its cloud-based firewall as a standalone service – you have to take the whole virtual network system and the management technicians as well.
Who is it recommended for?
SASE is difficult to conceptualize and you need a special network management package to create one. These concepts and tools require specialized staff to manage them and those experts are hard to find. Aryaka provides its own team for remote management of your new virtual network.
Pros:
- Advanced Methods for Threat Detection: Leverages machine learning and AI
- Alert Verification: Reduces false positives and improve anomaly detection
- Secure Private Network: Protects traffic through it’s own VPN tunnel
Cons:
- No Self-Hosted Solutions: This is a proxy service
Many companies might benefit from implementing a SASE. This is a relatively new concept and not many business managers would know about the possibility. You can explore the concept by contacting Aryaka for a demo.
7. Cato Networks SASE
Cato Networks has developed a cloud-based security platform, called SASE, which stands for Secure Access Service Edge. This system offers a range of edge services including an FWaaS. This strategy makes sense because there are a number of services that a proxy service can offer to businesses and they can all be performed simultaneously.
Key Features:
- Complete Connection Security: Scans site-to-site and network traffic as well as inbound traffic
- VPN-Based System: Provides a private corporate network over the internet
- Deep Packet Inspection: Identifies threats
Why do we recommend it?
Cato Network SASE gives you a SASE option that you can manage yourself. Cato Networks also offers a managed Security-as-a-Service package, called SSE (Secure Service Edge) 360, a package that includes a firewall. This system protects access to your cloud systems and multiple sites across a virtual network.
Other edge services in the SASE system include an SD-WAN, WAN optimization, a content delivery network, and a DNS service. This is supplied by a network of servers in many locations rather than just one data center. The system also includes a secure remote access system for home-based workers so that they can connect to the company network and be protected by the FWaSS while on company business. This system will also include mobile devices in the network.
The FWaaS is part of a bundle of security services offered by SASE, which also include a next-gen anti-virus, a managed threat detection and response, and a managed intrusion prevention system.
The Cato Networks SASE system is very comprehensive and so it takes some time to fully understand. It deals with all communications issues that any business connected to the internet could have. The FWaaS deploys deep packet inspection to examine all incoming and outgoing traffic, enabling businesses to block access to certain websites and it also implements data loss prevention strategies. The firewall checks on the protocol of each transmission and adapts its control standards accordingly.
The Cato Network SASE is a very good option both for very large businesses that want to centralize the security measures that cover many sites and it is also appropriate for small businesses that use freelance workers and have most of their staff out on-site or that operate a virtual office.
Who is it recommended for?
This service and all of the other Cato systems are aimed at large businesses. Rapidly growing mid-sized companies might also consider it. The package gives you a private network across the internet with security that blocks all break-in attempts, keeping transmissions confidential.
Pros:
- Aids System Comprehension: Offers excellent graphing, reporting, and dashboard visuals
- Offers Remote Access System Feature: Great for secure WFH solutions
- SASE Includes a Bundle of Other Security Features: IPS, antivirus, and threat detection
Cons:
- Not Ideal for Small Businesses: Better suited for larger organizations
Firewall as a Service FAQs
What are the 3 types of firewalls?
There are three types of firewall:
- Packet Filters – Check the header of each packet for suspicious identifiers
- Stateful Inspection – Accumulate information across packets
- Proxy Server Firewalls – Pre-filter traffic before it reaches the network
Does PaaS need a firewall?
PaaS providers don’t hold any responsibility for the programs that you run on the platform or the data that you store there. That responsibility lies entirely with your company. Therefore, you need to ensure that the contents of your accounts are secure. Using a cloud-based firewall, such as a FWaaS, will give your cloud resources access protection against malware and hacker attacks.
What is firewall in ISP?
Your internet service provider might offer a firewall service. However, this is not believed to be a core element of an ISP’s product and therefore, any firewall system could be charged for as an extra service. An ISP might decide to team up with a cloud-based firewall provider and offer clients discounts on the service, gaining commission for each new subscriber.