Digital Guardian DLP and CoSoSys Endpoint Protector are two competing data loss prevention (DLP) systems. You might be in the market for a DLP, or you might need one but no what it is. In this guide, we look at why you should buy a DLP and how to evaluate these two.
What is data loss prevention?
Data loss prevention is mainly concerned with preventing the data on your system from being stolen. Although any data theft can be damaging, disclosing personally identifiable information (PII) can be catastrophic. PII describes the information you hold about private individuals. In many parts of the world, the security of PII is governed by legislation and industry standards. If data thieves get hold of the PII system, your company can be fined by the authorities and sued by the individuals to whom that stolen PII relates.
Not only will your get penalized directly, but a PII disclosure event can cause long-term damage to your company’s reputation. If you aren’t able to protect PII, your company becomes a risk, and that means you will lose supply contracts, and you won’t win any new customers – your company will be barred from bidding for work. The loss of data can also lead to your company being blackmailed by thieves. Those data thieves expect to make money off PII, and they can do that by selling it on to hackers or by ransoming it back to you.
In addition to PII, you will probably also want to protect your trade secrets. As well, intellectual property, such as designs and bills of material, your client list, and supplier information, could also be of use to a rival business.
There are several ways that sensitive data can leave your system. Either a hacker can break in, which is called an intrusion, or one of your system’s authorized users could steal the data they have access to – that’s an insider threat.
An insider might steal data because of a perceived slight or simply to make money. Whistleblowers are another type of insider threat who disclose secrets because of a need for justice. Other employees might accidentally send out data or be duped by a confidence trickster to pass on sensitive data.
Data can be “exfiltrated” by email attachment, file transfer, fax, or copied onto a removable storage device, such as a USB memory stick. It can also be printed, with the thieve walking out with it in a bag or sending it out as a letter. All of these exit points need to be controlled by a data loss prevention system.
Digital Guardian DLP – Highlights
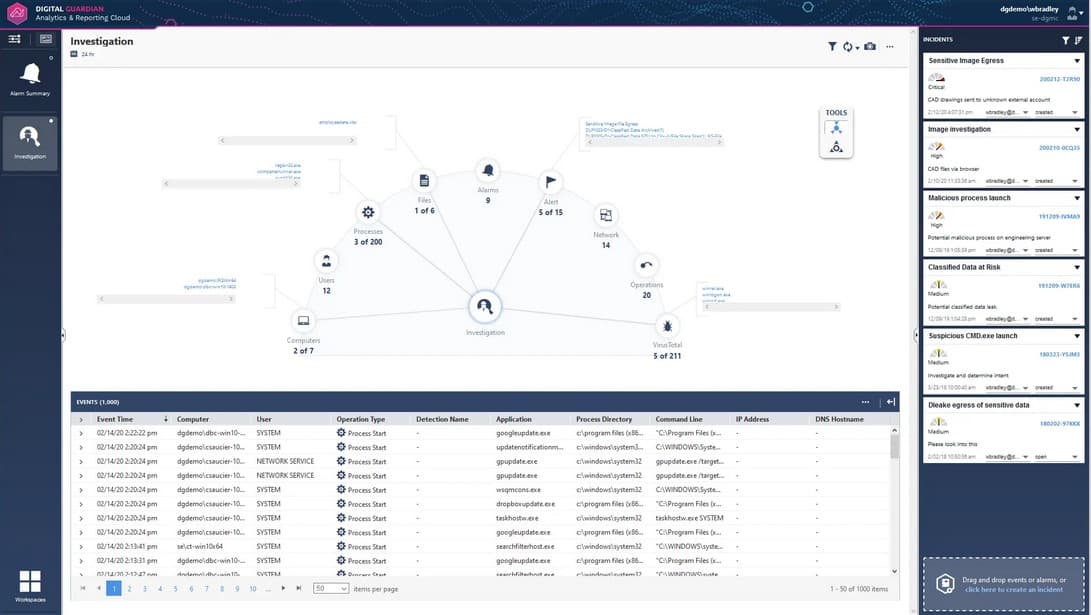
Digital Guardian is the name of a product and the company that supplies it. The software was created in 2003 by Verdasys at the start of the company’s operations. The DLP has been the main product of the company since that date. The company changed its name to Digital Guardian in 2014.
Key Features:
- SaaS Platform: Hosted on AWS servers for reliable and scalable performance.
- Endpoint and Network Protection: Implements DLP on endpoints and networks for comprehensive security.
- Advanced Threat Detection: Integrates FireEye malware detection for enhanced protection.
- Cloud Data Protection: Supports data security for AWS, Google Cloud Platform, and Azure.
Digital Guardian has been through many changes throughout the years and became a Software-as-a-Service platform in 2012. The company has invested a lot in the evolution of the DLP system. It holds 20 patents that cover the innovations embedded in the data loss prevention tool. In addition, FireEye malware detection was integrated into the service in 2013. The Digital Guardian system is one of the most significant DLPs globally and is administrated from the company’s HQ in Waltham, Massachusetts.
Key Information
- The Digital Guardian DLP SaaS platform is hosted on AWS servers
- Seven of the world’s ten largest brands use Digital Guardian
- Digital Guardian is a private company; its revenue was $63.55 million in 2019
- Digital Guardian implements DLP on endpoints and networks
Pros:
- Extensive Coverage: Protects data across endpoints, networks, and cloud environments.
- Integration with Major Platforms: Offers compatibility with Microsoft Office, SharePoint Online, and OneDrive.
- Advanced Threat Detection: Includes FireEye malware detection for robust security.
- Enterprise Proven: Trusted by seven of the world’s ten largest brands.
Cons:
- Limited Deployment Options: Fewer deployment options compared to competitors.
- Higher Cost: Can be more expensive due to advanced features and enterprise focus.
CoSoSys Endpoint Protector – Highlights
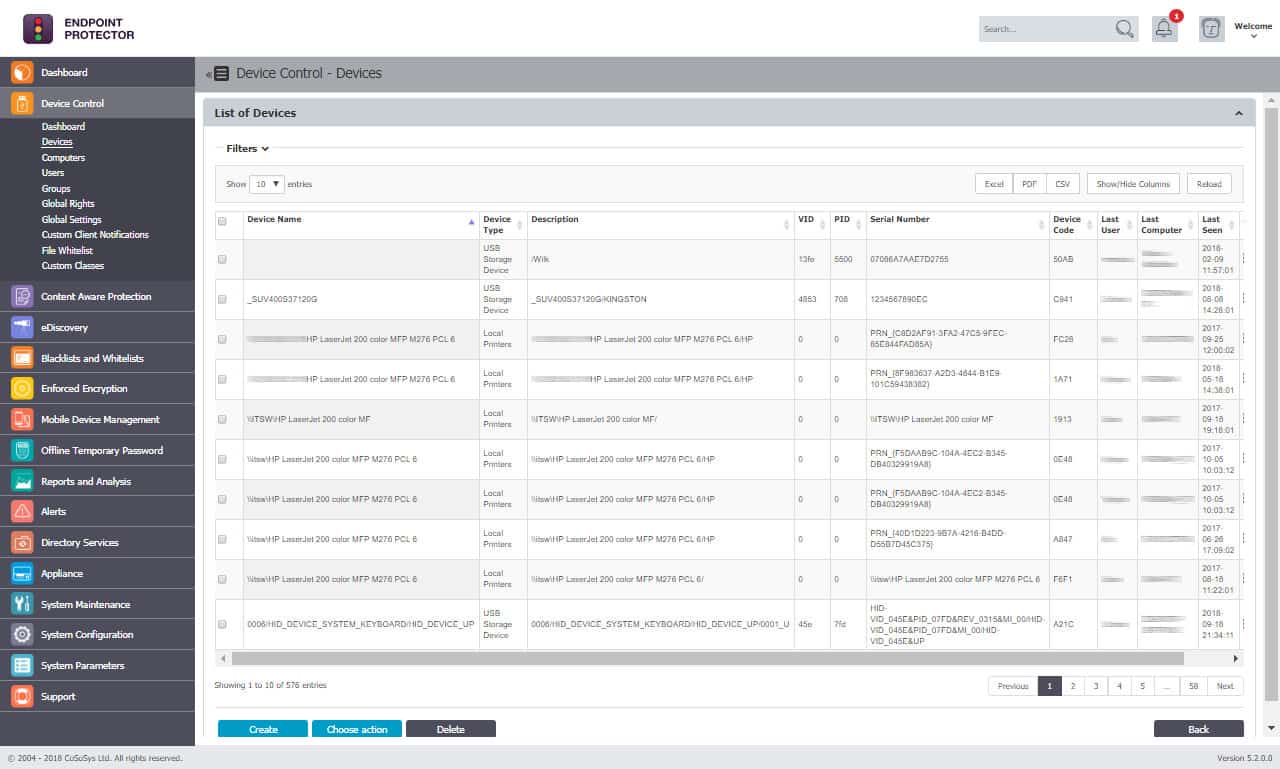
CoSoSys was founded in 2004. The name of the company is a contraction of Controller Software Systems. The company focuses on one product: Endpoint Protector. The Endpoint Protector system is offered as a SaaS platform by CoSoSys, but it is also available in other formats.
Key Features:
- Multiple Deployment Options: Available as SaaS, on-premises, or through major cloud platforms like AWS, Google Cloud Platform, and Azure.
- Comprehensive Endpoint Protection: Scans and monitors Windows, macOS, and Linux endpoints.
- Collaboration Tools Monitoring: Monitors data activity on Microsoft Outlook, Skype, and other collaboration tools.
- Flexible Integration: Supports multiple languages and integrates with various cloud services.
The company is headquartered in Cluj-Napoca, the capital of the Transylvania region of Romania. CoSoSys also has strategic offices in Friedrichshafen, Germany, Raleigh, North Carolina in the USA, and Seoul, South Korea. In India, the business partners with RAH Infotech for representation.
Key Information
- 11 million companies around the world use CoSoSys Endpoint Protector
- CoSoSys is a private company; its revenue was $5.6 million in 2019
- Endpoint Protector is available in 11 languages
- Endpoint Protector’s customer base includes eBay, Sony, and Philips
Pros:
- Versatile Deployment: Offers more deployment options, including virtual machine installations.
- Wide Compatibility: Protects data on various operating systems and collaboration tools.
- Language Support: Available in 11 languages, making it suitable for global businesses.
- High Adoption Rate: Used by 11 million companies worldwide, including major brands like eBay and Sony.
Cons:
- Limited Advanced Threat Detection: Does not include integrated malware detection like Digital Guardian.
- Potentially Lower Support Levels: Consultancy services and advanced support are paid extras.
Digital Guardian DLP vs. CoSoSys Endpoint Protector head-to-head
Both Digital Guardian DLP and CoSoSys Endpoint Protector have excellent reputations within the industry. Both are award-winning services and looking at the industry buzz about data loss prevention providers, and it is difficult to say which of these two systems has the best reputation. So, let’s take a look at each attribute of a DLP and see how our two subjects compare.
Deployment options
Both Digital Guardian DLP and CoSoSys Endpoint Protector are offered as SaaS platforms. Digital Guardian also offers its DLP system as a managed service. That plan includes the expert staff needed to watch over the live data shown in the system’s dashboard and take decisions on how to respond.
The Endpoint Protector system is available in the Marketplace of the three major cloud platforms: AWS, Google Cloud Platform, and Azure. This means that you can choose to add the software to your preferred cloud service account and run it from there. CoSoSys also makes the software package available for download. In this scenario, you need to run the package on a virtual machine.
The CoSoSys service offers more deployment options than Digital Guardian’s DLP.
Endpoints protected
Endpoint Protector scans endpoints running Windows, macOS, and Linux. It also monitors data-related activity on Microsoft Outlook, Skype, and Microsoft Outlook. Digital Guardian extends scanning and data protection to devices running Windows, macOS, and Linux. The Digital Guardian DLP also protects data held on Microsoft Office, SharePoint Online, and OneDrive servers. In addition, the Digital Guardian Cloud Data Protection module offers full coverage for data stored on AWS, Google Cloud Platform, and Azure servers.
Risk assessment
In DLP terminology, risk assessment refers to the discovery and classification of data. This is an automated process that identifies all of your data stores and then works through all data instances deciding whether they are classified as sensitive or not. Then, you need to apply extra security measures to that sensitive data.
Both Digital Guardian DLP and Endpoint Protector include this service. What constitutes sensitive data is personally identifiable information (PII) and intellectual property (IP) with both Endpoint Protector and Digital Guardian. In both cases, that identification of data can be further tailored to fit the requirements of specific data protection standards. Both services use context-awareness. This technique uses fingerprinting to identify groups of data fields that, in isolation, cannot identify an individual but can in combination.
Access rights management
Your access rights management system needs to be fine-tuned to use a DLP system. For example, DLP services allow different actions n sensitive data to other user groups, so you need to define many more user groups than you already have. You might also have lax security in your permissions structure.
Both of these DLPs use Active Directory for their data access controls. However, neither provides AD auditing out-of-the-box. Instead, customers of the Digital Guardian Managed Security Program get their AD structures sorted out for them.
Security policy creation
Security policies are the instruction manual for DLP systems. They specify which types of users can perform which actions on which categories of data. Many DLP systems offer libraries of templates, and both Digital Guardian and Endpoint are in this category. Templates offer pre-sets, and it is possible to apply whole sets of them that implement specific data privacy standards. These settings can be adjusted to create customized rules.
Remediation automation or orchestration
Endpoint Protector enforces encryption for data at rest when it is held on Windows or macOS endpoints. The management of this encryption is dynamic and is closely tied to access rights and security policies. Those users who have the permission to access specific data instances will gain that access seamlessly, not noticing that the data is encrypted. Endpoint Protector also monitors activity on Google Drive, Slack, and Skype to prevent sensitive data from moving through those channels.
Digital Guardian enforces encryption for sensitive data when it is moved rather than when it is at rest. This means that the system will encrypt files as they pass onto an authorized USB memory stick or moved with a file transfer system.
Both of these tools report all data-related activity. This means successful access events or blocked illegal access. The reports are displayed in the form of alerts in the system console for each DLP. Both also write those events to log files.
Exfiltration points covered
Removable storage devices, such as USB memory sticks, represent the main focus of control activities performed by both Digital Guardian DLP and Endpoint Protector. In both cases, the DLP doesn’t merely block all USB devices from attaching to the computer. Instead, certain types of data can be moved by specific user groups. Peripheral ports, disk drives, and CD and DVD drives are also scanned.
Endpoint Protector watches over network connections to printers and fax machines and tracks activity on Bluetooth connections and wired links to mobile devices. Digital Guardian DLP also monitors physical ports and connections and networked links through printers and fax machines. However, it doesn’t extend its controls to communications with mobile devices.
Governance, compliance, and reporting
Digital Guardian DLP can be preset for GDPR, ITAR, PCI-DSS, and HIPAA. In addition, endpoint Protector customizes GDPR, SOX, HIPAA, PCI DSS, NIST, GLBA, and CCPA.
Support
Endpoint Protector offers a Knowledge Base at its website for self-service support. CoSoSys also runs a fully manned Help Desk, which can be contacted through a ticket system or a chat window, both available at the Endpoint Protector website. However, some businesses want assistance in setting up the Endpoint Protector service. This could be because they need advice on choosing security policies or what staff needs to be dedicated to monitoring the system. In these cases, CoSoSys offers a consultancy service, which is a paid extra.
The most comprehensive support service offered by Digital Guardian is its Managed Detection and Response package, which includes constant attendance by trained Digital Guardian staff. In addition, subscribers to the regular Digital Guardian DLP service get support on-demand included in the price. This is available instantly through a chat facility at the Digital Guardian website. The site’s self-service portal also offers pre-written guidance in a searchable database, and customers can raise a support ticket within this system.
Price
Neither Digital Guardian nor CoSoSys publishes a price list for their data loss prevention systems. Instead, you need to contact CoSoSys or Digital Guardian to discuss solutions.
The start of the buyer’s journey is implemented by requesting a demo of each DLP for both products. CoSoSys offers a demo account for Endpoint Protector, and there is also a demo available for Digital Guardian DLP.
Digital Guardian DLP vs. CoSoSys Endpoint Protector: The verdict
Both Digital Guardian DLP and CoSoSys Endpoint Protector are leading data loss prevention systems. Both have won awards and are usually counted in the top four designs in the world each year. Unfortunately, it is challenging to choose between them. There is no replacement for experience, so you will only truly make your mind up once you have experienced each system yourself by accessing the demo services.
Perhaps, the broader range of deployment options and the ability to control communications with mobile devices gives CoSoSys Endpoint Protector the edge over Digital Guardian DLP.