Here is our list of the best data loss prevention (DLP) software & tools:
- Fortra Digital Guardian EDITOR’S CHOICE This cloud-based DLP protects data on computers running Windows, macOS, and Linux and also on cloud systems. This package is also available as a managed service. Access a free demo.
- Guardz (FREE TRIAL) This cloud-based platform scans email systems, endpoints, and cloud data storage accounts to block manual and automated attempts to steal or corrupt data. Get a 14-day free trial.
- CoSoSys Endpoint Protector (ACCESS DEMO) A choice of onsite or cloud-based data loss prevention systems that protect devices running Windows, macOS, and Linux plus attached storage devices. Get a free demo.
- ManageEngine Device Control Plus (FREE TRIAL) This system blocks unauthorized data transfers onto peripheral devices by creating a matrix of allowable devices, actions, and users. Runs on Windows and Windows Server.
- Acronis Cyber Protect Cloud (FREE TRIAL) A SaaS platform of backup and system security protection services that is designed for use by managed service providers.
- ManageEngine Endpoint DLP Plus (FREE TRIAL) This package of on-premises data protection software discovers, tracks, and protects sensitive data. Available for Windows Server.
- SolarWinds Data Loss Prevention with ARM Access rights manager can be set up to help shield against accidental or malicious data loss. Can automate user access and activities through policy, respond to suspicious activity and investigate user events that could potentially compromise your systems.
- Symantec Data Loss Prevention This system offers data protection solutions for endpoints, networks, cloud resources, and file servers from a central console. Installs on Windows Server and Linux
- Vembu BDR Suite This backup and disaster recovery package saves data from destruction or accidental loss. Available for Windows Server and Linux or as a SaaS platform.
- Trustifi Outbound Shield This cloud-based service integrates into your email system to provide transmission protection and sensitive data management. Integrates with a plug-in.
- Trellix XDR Platform This system-wide security package scans endpoints and networks to identify threats before they get a chance to steal or damage data.
- Check Point Data Loss Prevention A suite of security products for different system services that implement DLP as part of a broader protection strategy. This is a SaaS platform.
- Cyberhaven This SaaS package is a data discovery and classification service that examines data flows rather than files and databases and then blocks movements.
- ThreatLocker This cloud platform of security services has a combination of modules that helps to protect data against theft. Data corruption is also guarded against.
- SpinOne This platform of SaaS data protection services offers risk assessment, ransomware protection, DLP, and compliance auditing from its cloud platform.
- CrowdStrike Falcon Device Control This specialized monitor for removable devices is an add-on to the endpoint detection and response systems offered by CrowdStrike. This is a cloud-based system and coordinates with endpoint agents for Windows, macOS, and Linux.
- Teramind DLP This package focuses on user activity profiling to spot changes in behavior that could indicate malicious activity as well as sensitive data discovery. Offered as a SaaS package or a virtual appliance.
- Digital Guardian Endpoint DLP The data protection solution covers devices running Windows, macOS, and Linux. A central coordinating server operates from the cloud.
- Code42 Incydr This cloud-based service specializes in spotting insider threats and includes system preparation processes to recover from loss and destruction.
- Comodo MyDLP This DLP observes activities on the web, mail, printers, removable devices to block all system exits. Runs over Hyper-V or VMWare as a virtual appliance.
What is data loss prevention?
Data Loss Prevention (DLP) is a set of strategies, tools, and practices designed to prevent unauthorized access, leakage, or loss of sensitive data from an organization’s network, endpoints, or storage systems. The goal of DLP is to protect confidential and critical information from being exposed, stolen, or compromised, whether intentionally or accidentally. This is especially important for businesses that handle sensitive data such as customer information, intellectual property, financial records, and personally identifiable information (PII).
DLP solutions typically use a combination of content inspection, contextual analysis, and predefined rules to monitor and control data movement within an organization. They can be implemented across various channels, including email, cloud storage, file transfers, and endpoints like laptops and mobile devices. By inspecting the content of files and communications in real time, DLP tools can identify sensitive data, such as credit card numbers, social security numbers, or proprietary company information.
There are three primary types of DLP strategies:
- Network-based DLP: Monitors and filters data in transit across the network, such as email or cloud services, to prevent unauthorized sharing or transfer of sensitive data.
- Endpoint-based DLP: Protects data stored on endpoints (computers, smartphones, and other devices) by enforcing policies to prevent data from being copied, shared, or accessed inappropriately.
- Storage-based DLP: Protects sensitive data stored on servers, databases, and file systems by monitoring and enforcing access control and encryption policies.
Effective DLP systems provide automated responses to policy violations, such as blocking the transfer of sensitive files, alerting administrators, or encrypting data before it leaves the network. As cyber threats and data breaches increase, DLP plays a crucial role in safeguarding an organization’s reputation, ensuring compliance with privacy regulations, and reducing the risk of financial and legal consequences.
When you come to tighten up your system protection, you will find that you don’t need one of each of these because just one will take care of many tasks, including blocking access to the system and protecting data simultaneously. With the correct policy and systems in place, you will be able to reduce or eliminate data loss incidents across your business.
You might want to allow staff to copy files onto removable media, such as USB memory sticks. However, this is one of the main ways that employees can steal data. This situation presents a dilemma. You want to keep the system secure without blocking normal and acceptable working practices.
The Best Data Loss Prevention Software Tools
You likely won’t get all of your data loss prevention needs fulfilled by the one tool. However, many software providers produce suites of tools that fit together. There is a lot of overlap between data loss prevention, standard compliance, and data backup. You will need all of these to successfully protect and manage your company’s data.
What should you look for in data loss prevention software?
We reviewed the market for data loss protection tools and analyzed the options based on the following criteria:
- A detection system that can interact with access rights managers and firewall to shut down data theft
- Email attachment scanning and logging
- Suitability for use for HIPAA, GDPR, SOX, and PCI DSS
- Variable controls to offer tighter scrutiny of PII usage
- Endpoint identification for both source and destination of data movements
- A free trial or money-back guarantee for a risk-free assessment
- Value for money represented by a trade-off between delivered functions and price
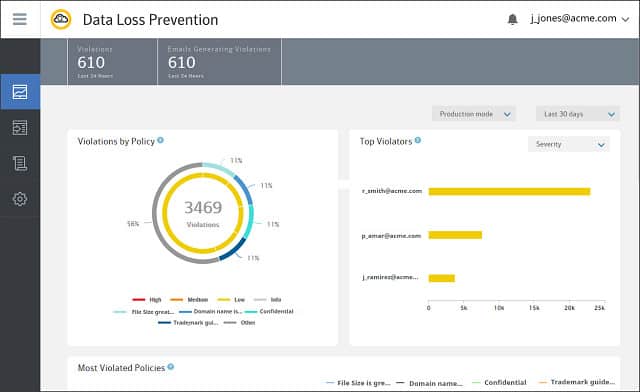
1. Fortra Digital Guardian (GET DEMO)
Fortra Digital Guardian is a SaaS package that is hosted on AWS. This tool will protect sensitive data on-premises, on cloud platforms, and in SaaS packages.
Key Features:
- Data Discovery & Classification: Automates the identification and categorization of sensitive information across systems.
- Compliance Standards: Ensures adherence to HIPAA, PCI DSS, and GDPR for data protection.
- Multi-Platform Endpoint Protection: Offers comprehensive security for Windows, macOS, and Linux devices.
- SaaS Protection: Secures data within Google Workspace and Microsoft 365 environments.
- Cloud Flexibility: Operates seamlessly on AWS, GCP, and Azure, providing versatile cloud security.
Why do we recommend it?
Fortra Digital Guardian is a cloud-based system and it can simultaneously protect data on premises and on cloud systems. This is a well-established package that has a service history protecting PII and intellectual property. The system is able to implement HIPAA, PCI DSS, and GDPR among other data security standards.
The package uses Active Directory for its access rights manager, so you need to make sure that you have your user groups correctly set up before you implement Digital Guardian. The service controls file movements as well as file access and on cloud editors, it will manage which users can be given permission to share a sensitive document.
The tool implements sensitive data discovery and classification. This process is tailored towards the requirements of a specific data security standard, such as PCI DSS, HIPAA, or GDPR. The scanner implements data fingerprinting to create context-aware field groupings that collectively denote personally identifiable information.
Who is it recommended for?
This SaaS platform is a good choice for businesses that have both on-premises and cloud systems in operation. The service can protect data in Microsoft 365 and Google Workspace as well as data held on AWS, GCP, and Azure. On-premises data can be protected if it is held on computers running Windows, macOS, or Linux.
Pros:
- Integrated Access Rights Management: Utilizes Active Directory for streamlined access control and management.
- Detailed Activity Logging: Maintains comprehensive records of data discoveries and security actions.
- Compliance Reporting: Generates reports to assist in meeting compliance requirements for various standards.
- Data Encryption in Transit: Encrypts data as it moves between systems, enhancing security during data transfer.
- Robust Malware Defense: Offers effective protection against malware threats, safeguarding sensitive data.
Cons:
- Pricing Inquiry Required: Specific pricing information is unavailable upfront and must be requested.
- No Free Trial: While a free demo is offered, there is no direct free trial available for hands-on evaluation.
There isn’t a free trial of Fortra Fortra Digital Guardian, however, you can examine the system by requesting a free demo.
EDITOR'S CHOICE
Fortra Digital Guardian is our top pick for data loss prevention software because includes a sensitive data discovery and classification system as well as a data protection service. The Digital Guardian package is hosted in the cloud on AWS servers and it will protect data held on the major cloud platform, SaaS productivity suites, and on premises. The package is a good choice for companies that operate a hybrid environment. Fortra offers a managed service version of Digital Guardian, which is ideal for companies that don’t have their own cybersecurity experts on staff.
Download: Access FREE Demo
Official Site: https://www.digitalguardian.com/demo
OS: Cloud-based
2. Guardz (FREE TRIAL)
Guardz is a package of IT system protection measures that is delivered from the cloud. The service shields data from attack and it operates on endpoints and cloud data accounts. The package is particularly strong at protecting the OneDrive and Google Drive services. The system scans emails coming into Exchange Server/Outlook and Gmail system to identify threats that can lead to data theft.
Key Features:
- Email Scanning: Identifies and blocks email threats before they can compromise systems.
- Cloud Data Protection: Safeguards data stored in cloud services like OneDrive and Google Drive.
- Endpoint Security Monitoring: Monitors devices for signs of intrusion or malware activity.
Why do we recommend it?
Guardz protects endpoints by scanning for intrusion and malware. It also guards cloud data stores. The package is particularly strong at blocking the email-based methods that hackers use to trick their way into the system. It addresses account takeover attempts that are usually implemented through phishing and also scans attachments for malware.
Account takeover represents a major threat to data security and it is usually implemented through credentials theft, which occurs in phishing emails. The Guardz platform includes a number of tools to protect email accounts against phishing. The first is its malicious email detection system and the second is a Dark Web scanner that looks for signs that company email account details are up for sale on hacker forums.
The package also includes a phishing simulator that can be used for system testing and user education. There is a much bigger employee awareness training resource in the Guardz plans, however. This is a library of courses that are implemented as a series of videos that explain to users how to spot fake emails and what do do about them.
Who is it recommended for?
This system is delivered as a subscription package with a rate per user per month. There is no minimum team size for an account and so the service is suitable for all sizes of businesses. Guardz insists that its service should be administered by a managed service provider. However, companies that don’t have an MSP partner can take out a managed service plan, which will be run by Guardz itself.
Pros:
- Comprehensive Hacker Defense: Effectively blocks access attempts by hackers, securing systems against unauthorized entry.
- Malicious Behavior Detection: Scans both endpoints and cloud data services for signs of malicious activities, ensuring comprehensive protection.
- Phishing Protection: Includes tools for email security, reducing the risk of account takeover through education and detection.
- User Education Resources: Offers a vast library of training materials to help users recognize and respond to phishing attempts.
- Flexibility in Service Management: Provides options for self-management or fully managed services by Guardz, catering to different business needs.
Cons:
- Managed Service Provider Required: To fully utilize the service, a partnership with a managed service provider is necessary.
- Cloud-Based Limitations: Being cloud-based, there might be concerns for businesses with strict data residency or security requirements not covered by cloud services.
As it is based in the cloud, the Guardz service is not constrained by the boundaries of one network. It can monitor endpoints on multiple sites and even those used by remote workers. You can examine the Guardz package with a 14-day free trial.
3. CoSoSys Endpoint Protector (GET DEMO)
CoSoSys offers Endpoint Protector as an onsite solution, as a cloud-based service, and as a standalone software package. The onsite version will protect computers running Windows, Mac OS, and Linux. A central Endpoint Protector Server appliance communicates across the network with client software installed on each endpoint. The Server will also protect attached devices, such as digital cameras and USB sticks. The Endpoint protector system is also available as software that implements a virtual appliance on your own server.
Key Features:
- Versatile Deployment: Available as an on-site solution, a cloud service, or standalone software, catering to diverse business needs.
- Comprehensive Device Protection: Secures endpoints and attached devices across Windows, macOS, and Linux platforms.
- Regulatory Compliance: Meets standards for HIPAA, PCI DSS, and GDPR, ensuring data protection across various jurisdictions.
- Enforced Encryption: Implements strict encryption protocols for data at rest and in transit.
Why do we recommend it?
CoSoSys Endpoint Protector operates like an XDR because it operates on each device and then centralizes local intelligence in one server as well. Interactions between these two detection levels spread track actions that could spread around the network while also being able to reach down to physical interfaces on reach computer to block unauthorized data transfers.
The full Endpoint Protector system includes content protection, device control, enforced encryption, network discovery and mobile device management. A standalone version is available to protect just one endpoint per install. This is Endpoint Protector Basic and it includes the content and device protector modules of the Server version.
Those who prefer to subscribe to “software as a service” packages instead of running their own hosts and software can opt for My Endpoint Protector. This includes content protection, device control, and mobile device management. In all implementations, the system is HIPAA, PCI DSS, and GDPR compliant.
The content protection system in Endpoint Protector manages file transfers according to the policies you set. All file transfers can be blocked for specific user groups or sensitive files can be allowed to be moved as long as they meet certain criteria. Similarly, the device control system can either completely block devices from attaching to a protected endpoint or can be allowed for file transfers under specified conditions.
Who is it recommended for?
CoSoSys appeals to a broad audience because it has covered just about every deployment strategy that any business could want. The cloud-based SaaS option will appeal to businesses with multiple sites and remote users, while the on-premises option is good for businesses that don’t want to interact with external systems to protect a LAN.
Pros:
- Multi-Platform Support: Offers robust protection for a wide range of operating systems, ensuring comprehensive security.
- Granular Data Monitoring: Capable of detailed monitoring at both the file and device level for precise control.
- Compliance Ready: Pre-configured for major regulatory standards, simplifying the compliance process.
- Customizable Control: Allows for easy implementation of custom rulesets to meet specific organizational needs.
Cons:
- Limited Trial Option: Offers only a demo for evaluation, which may not provide a full understanding of the system’s capabilities.
The online version can be accessed for evaluation on a free demo.
4. ManageEngine Device Control Plus (FREE TRIAL)
ManageEngine Device Control Plus offers strong protection against the use of peripheral devices such as USB memory sticks as a conduit for malware. The tool also allows you to integrate the control of data movements onto peripheral devices as part o the implementation of your security policy if you have located and defined stores of sensitive data.
Key Features:
- Peripheral Device Whitelisting: Enables control over which devices can connect to the network, enhancing security.
- Data Transfer Management: Allows for variable control based on data type, supporting compliance and security policies.
- Compliance Support: Aids in maintaining compliance with standards like HIPAA and PCI DSS through stringent data handling policies.
Why do we recommend it?
The solution to managing the use of peripheral devices for data carriage is to control the access of devices rather than disable them entirely. ManageEngine Device Control Plus offers a way to implement a range of security devices for peripheral devices.
This device management system lets you define a security policy and then it translates those requirements into manageable controls. For example, you can allow a list of approved devices to attach to endpoints and you can also set a file size limit, or a total data transfer limit, to account for acceptable office use of peripheral devices. It is also possible to block the copying of data from some sources while allowing other types of data to be transferred to memory sticks. If you follow data security standards, such as HIPAA or PCI DSS, you need to pay particular attention to personally identifiable information (PII).
The Device Control Plus system is very easy to use and it includes guidance points to assist those who are not security experts. The system also logs all data access events and copying attempts, which is a necessary feature for those following data security standards. 
Who is it recommended for?
This tool is a useful block on malware movements from peripheral devices. It can be used as part of a data loss prevention system if you have a sensitive data discovery system in place – in the ManageEngine menu of services, you would need Data Security Plus for that function.
Pros:
- Intuitive User Interface: Features an easy-to-navigate dashboard that balances visuals and insights for effective management.
- Removable Media Control: Offers hardware lockdown options to restrict the use of removable media, minimizing malware risk.
- Customizable Security Policies: Simplifies the creation of security policies tailored to organizational needs, including PHI scanning capabilities.
- Event Logging: Keeps detailed logs of data access and copying attempts, critical for compliance and security audits.
Cons:
- Limited Evaluation Option: Provides a demo for initial assessment, which may not fully showcase the tool’s capabilities compared to a full-featured trial.
Device Control Plus installs on Windows and Windows Server. ManageEngine offers the system on a 30-day free trial.
5. Acronis Cyber Protect Cloud (FREE TRIAL)
Acronis Cyber Protect Cloud is a package of system protection measures that includes extensive data protection systems. The Acronis system is tailored for use by managed service providers (MSPs) and is delivered from a hosted SaaS platform. The Acronis Cyber Protect Cloud service offers a list of services that can be added to an MSP’s client account. Thus, these are sell-through services that provide extra income streams.
Acronis supplies marketing material and training guides to help MSPs sell the services in the package to their clients. Screens can also be white-labeled and the package includes consultancy and analysis tools to increase earning opportunities.
Acronis Cyber Protect Cloud isn’t an RMM package. It specifically focuses on security services and Acronis has organized integrations with the major RMM and PSA systems so it can be delivered seamlessly from an MSP’s existing operating consoles.
Key Features:
- Comprehensive Backup and Recovery: Ensures data integrity with file-level and full disk backup options, tailored for various recovery scenarios.
- Antimalware Protection: Delivers endpoint and system-wide application protection, integrating with email and data transfer services for holistic security.
- Data Loss Prevention: Offers a suite of tools for preventing data leaks, including file integrity monitoring and user behavior analysis.
Why do we recommend it?
Acronis Cyber Protect Cloud is a comprehensive bundle of cybersecurity tools. The core of this package is Acronis Cyber Protect, which is produced in a number of flavors that cater to businesses, home workers, private individuals, and service providers. This bundle includes malware scanning, data backup, file integrity monitoring, threat intelligence, and user behavior analysis.
Services in the Acronis Cyber Protect Cloud package include a backup and recovery service that can operate on both a file-level basis and as a full disk backup option. This allows MSPs to structure custom solutions for their clients, including cloud storage space.
The package offers antimalware that operates on endpoints and also attaches to specific system-wide applications, such as email and data transfer services. The antimalware system also extends to a synching and file sharing service that is built into the Acronis package of services. File infection scans are integrated into both data uploads for backup and data recovery procedures.
Threat detection is organized through an AI-based baselining system for behavior anomaly tracking. Acronis also provides an in-house threat intelligence feed and includes an internal attack logging and tracking system for each account. Event remediation such as recovery from ransomware can be triggered automatically and run as a series of operations through playbooks, which include data recovery.
The intelligence and analysis features in the Acronis platform are useful for security analysts and human threat support technicians. There is also a system security auditing toolbox in the service that enables MSPs to offer high-value services to clients. The package is suitable for use by Security Operations Centers as well as regular system support MSPs.
Who is it recommended for?
The Acronis Cyber Protect Cloud version of Acronis Cyber Protect is specifically designed for use by managed service providers. It contains all of the elements of the base Cyber Protect package but delivered in a SaaS format that has a multi-tenant architecture, suitable for MSPs that are protecting the sites of their clients.
Pros:
- Cloud-Based Flexibility: A SaaS solution that includes cloud storage, catering to the needs of managed service providers (MSPs) and their clients.
- Multi-Tenant Architecture: Designed for MSPs, allowing for the management of multiple client sites through a single, streamlined platform.
- Integrated Recovery and Malware Remediation: Automates backup and recovery processes, seamlessly integrating them with antimalware efforts for efficient threat response.
- Customizable Security Services: Provides MSPs with the ability to tailor security services to their clients’ needs, adding value and potential revenue streams.
Cons:
- Not a Comprehensive RMM Solution: Focuses primarily on security and backup services, lacking the broader range of tools included in a full Remote Monitoring and Management (RMM) package.
Acronis Cyber Protect Cloud can be assessed with a 30-day free trial.
6. ManageEngine Endpoint DLP Plus (FREE TRIAL)
ManageEngine Endpoint DLP Plus is a complete data protection package that identifies the locations of sensitive data, classifies it, tracks access to it, and blocks its movement. This is a networked service, so you install it on one endpoint and it will reach out to the other computers on the network. The system can also be used to protect multiple sites.
Key Features:
- Comprehensive Data Protection: Integrates data discovery, classification, access tracking, and movement blocking to secure sensitive information.
- Multi-Site Support: Designed to protect data across multiple locations, offering a network-wide security solution.
- Insider Threat Mitigation: Implements measures to prevent unauthorized access and misuse of sensitive data by insiders.
Why do we recommend it?
ManageEngine Endpoint DLP Plus is a package of data security tools that operate on workstations, servers, and cloud platforms. It includes data store scanning to discover sensitive data, which can be automatically tuned to specific data protection standards. Those discovered data instances are then categorized and from these definitions, the implementations of your security policies can commence. These controls extend to the monitoring of movements of sensitive data between files, between computers, onto peripheral devices, or out on emails.
Sensitive data discovery is guided by templates. The setup for a DLP can be quite laborious because you need to specify details about the type of data that needs to be tracked and who can do what to each category of data. The template library simplifies that process by tuning the system to conform to a particular data security standard.
Data detection and classification uses a number of identification techniques, including fingerprinting, which can spot combinations of data fields that, individually have no significance, but have importance when stored in proximity.
The insider threat prevention system in the Endpoint DLP Plus package tracks users who access sensitive data stores and logs their activity. Analysis of these records will enable you to spot where access rights are too lax and point to how that should be tightened. The data movement prevention extends to email content scanning and attachment controls plus connected device management and monitors that watch the movements of data between sites and cloud services.
The DLP package includes an interesting approach to data-handling applications. This assesses the risk of each system on an endpoint and its use of sensitive data. The administrator can then nominate specific software for data access and it will then prevent data from being exported from these trusted applications out to unauthorized systems.
The ManageEngine system includes solutions for BYOD because it containerizes data that passes onto user-owned devices. This means that corporate data does not get stored on externally-managed devices and access to it is blocked once the device leaves the company network.
Who is it recommended for?
This package is a bundle of other ManageEngine tools including Device Control Plus (above) and Data Security Plus. This option provides a more complete data protection service than buying individual elements. Any business that needs to implement DLP for standards compliance but has no element already in place should opt for this package. Small businesses can benefit from the Free edition of Endpoint DLP Plus, which will manage data protection on 25 endpoints. One problem with this system is that it is only able to scan endpoints running Windows or Windows Server – it cannot operate on devices running Linux or macOS.
Pros:
- Email and Domain Controls: Implements restrictions on email communications, including blocking messages to unauthorized or blacklisted domains.
- BYOD Data Containerization: Ensures corporate data does not reside on personal devices, maintaining control over sensitive information.
- Trusted Application Safeguarding: Identifies and authorizes specific applications for data access, preventing data export to unapproved software.
Cons:
- Limited Operating System Compatibility: Focused on Windows and Windows Server platforms, lacking direct support for Linux and macOS endpoints.
- On-Premises Only: No cloud-based version available, potentially limiting flexibility for some organizations.
ManageEngine Endpoint DLP Plus is an on-premises package for Windows Server. It is available in two versions: Free and Professional. The Free package is limited to monitoring 25 endpoints. The Professional version will cover an entire network and it can be extended to monitor multiple sites from one location. The Professional edition is offered for a 30-day free trial.
7. SolarWinds Data Loss Prevention with ARM
Tested on: Windows Server 2008 R2 or higher & AD domain
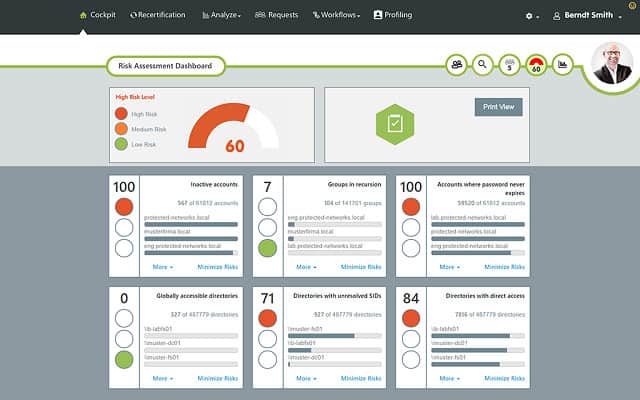
SolarWinds is a leading producer of IT infrastructure monitoring tools and its DLP security solution is part of its Access Rights Manager.
Key Features:
- Access Rights Management: Streamlines permissions and access control to sensitive data.
- Suspicious Activity Monitoring: Keeps an eye on user behavior to identify potential security threats.
- Automated Responses: Takes immediate action on detected threats, reducing potential damage.
- Compliance Auditing: Facilitates adherence to data protection standards with comprehensive auditing features.
Why do we recommend it?
The SolarWinds Access Rights Manager focuses on the fact that you probably already have access to your sensitive data protected by credentials, so the biggest for data abuse lies with the inappropriate use of valid accounts. Tighten up your AD entries and then watch how each account is used with this package.
A key starting point in your data loss prevention strategy is to set a company policy on data access control. The SolarWinds Access Rights Manager supports this task by giving you clear reports on current access permissions. You then have an opportunity to set better controls, which can be implemented through the Access Rights Manager.
Ongoing monitoring keeps a constant check on data access and generates alerts whenever copies are made or data is transferred. The manager unifies user monitoring for Active Directory, Windows File Share, SharePoint, and Microsoft Exchange. This enables you to monitor the activities of a user who has displayed unusual or suspicious behavior across many communication channels.
Overall, SolarWinds Access Rights Manager assists you to tighten up Active Directory instances and create more finely tuned device access controls and user permissions. Once you have improved the security provided by AD, you can use the tool to monitor the behavior of each user and spot changes in activity that could signify an account takeover or a newly dissatisfied employee. Alerts and automation features draw your attention to suspicious users and implement account suspension.
Who is it recommended for?
SolarWinds Access Rights Manager is a comprehensive tool that is aimed at businesses that have a large number of users and devices. Such organizations are susceptible to intrusion because of the large volume of turnover of accounts and there might be insecure abandoned accounts in Active Directory that provide a good way in for data thieves.
Pros:
- Seamless AD Integration: Enhances existing Active Directory environments for improved security and management.
- Visual Permission Insights: Provides clear visualizations of permission structures, making management more straightforward.
- Behavioral Analysis: Utilizes behavior analysis to detect insider threats and policy violations effectively.
- Automation Capabilities: Automates responses to threats, saving time and potentially avoiding data breaches.
- Comprehensive Compliance Support: Aids in maintaining compliance with various standards, ensuring a secure data environment.
Cons:
- Complexity for Non-Sysadmins: The depth and breadth of features may be overwhelming for those not familiar with system administration.
- Enterprise Focus: Primarily designed for larger networks, which may not be as accessible or necessary for smaller organizations.
The auditing and reporting function of the Access Rights Manager supports GDPR, HIPAA, and PCI DSS compliance. The interface of the tool is very easy to use, making user access management a much simpler task. The software installs on Windows Server and you can get it on a 30-day free trial.
Related post: File Activity Monitoring Software
8. Symantec Data Loss Prevention
The Symantec Data Loss Prevention solution from Broadcom is a module platform with protection services that you assemble to get the complete protection service for your system. Whichever of these elements, you choose, you end up with a single console to manage and monitor the security system.
The four elements to the DLP system are:
- Symantec DLP for Endpoint
- Symantec DLP for Network
- Symantec DLP for Storage
- Symantec DLP Cloud Services
Symantec’s DLP solution combines user activity tracking with data risk controls. It can monitor data held on servers, desktops, mobile devices, and in cloud storage. An initial sweep on installation identifies all locations that hold sensitive data and gives you the option to remove it all to a central management server, secure data repository or secure it in place. You receive templates and workflows for compliance with HIPAA, GDPR, and PCI DSS standards.
Key Features:
- Broad Coverage: Protects data across endpoints, networks, storage, and the cloud for comprehensive security.
- Sensitive Data Management: Identifies, classifies, and secures sensitive data throughout the organization.
- Compliance Readiness: Offers templates and workflows for HIPAA, GDPR, and PCI DSS, simplifying compliance processes.
Why do we recommend it?
Symantec Data Loss Prevention from Broadcom is a well-established DLP system by a strong brand. The service is split into two products. The first of these is Symantec Data Loss Prevention Core Solution for on-premises systems. The second is Symantec Data Loss Prevention Cloud Solution, which operates more like a Zero Trust Access service for cloud-based applications. The on-premises system provides data discovery and classification and also file integrity monitoring and data movement tracking and blocking. That movement tracking involves controls on peripheral devices and emails.
The tool logs all access to sensitive data and tracks those accounts that have raised alerts. Sensitive documents are encrypted and can only be seen by authorized users. The tool also makes sure that discarded copies and retired documents are completely destroyed, leaving no recoverable versions in memory. All copies are tracked and kept secure even when sent out to remote locations or onto user-owned mobile devices.
The Symantec DLP contains documents with sensitive data by using encryption and it identifies the intended recipients by fingerprinting every copy. This encryption and access identification are paired with data movement and copy restrictions. This enables you to block files and data from being attached to emails or transferred over the network or the internet.
The Symantec DLP system is part of its endpoint protection system. This searches for intrusion and malicious software, which could compromise your data privacy. This system includes the monitoring of software that is not authorized by the business but is installed on the same device as sensitive data – a situation that is particularly common in the case of the use of user-owned devices for access to company data.
Who is it recommended for?
Symantec Data Loss Prevention Core Solution is almost identical to ManageEngine Endpoint DLP Plus. However, while the ManageEngine service only operates on endpoints running Windows, the Symantec system is able to manage sensitive data on Windows, macOS, and Linux. The Cloud Solution should be considered more as a SASE or ZTA package and compared with those categories of tools rather than the DLP systems on this list.
Pros:
- Unified Monitoring: Integrates user activity tracking with data risk management for enhanced oversight.
- Advanced Encryption: Utilizes encryption to secure sensitive documents, with access limited to authorized users.
- Automatic Data Mapping: Scans and identifies sensitive data locations automatically, facilitating efficient data protection.
- File Integrity Assurance: Employs fingerprinting to monitor and maintain file integrity, preventing unauthorized changes.
Cons:
- Integration Opportunities: Could offer better integration with other Broadcom/Symantec solutions for a more cohesive security strategy.
The software for the Symantec DLP suite’s server installs on Windows Server, CentOS, and Oracle Linux. Endpoint agents are available for Windows, macOS, and Linux.
Related post: Symantec Endpoint Protection: Full Review & Rival Comparison
9. Vembu BDR Suite
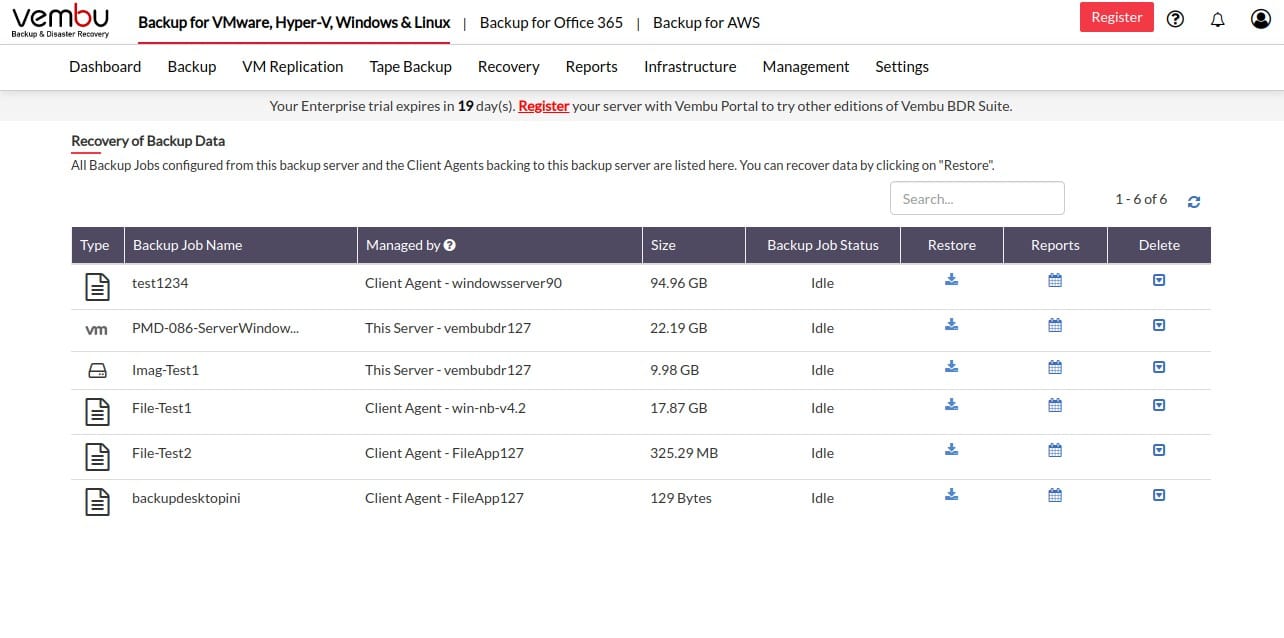
Vembu BDR Suite is a backup and disaster recovery service – that’s what BDR stands for. This platform offers disk imaging, file backup, and application data protection. So, this service isn’t a theft or disclosure prevention system, but a data recovery service. The platform offers different editions for different technologies. You pay for each of the types of system that you want to back up.
The choice of services from Vembu are VM backup, Server backup, Endpoint backup, Cloud productivity Suite backup, Cloud VM backup, and Applications backup. All of these packages except for the Server and Apliciatons editions offer a free tier that protects 10 assets.
Key Features:
- Versatile Backup Solutions: Offers disk imaging, file-level backups, and application data protection across a range of technologies.
- Incremental Backup Capability: Reduces storage needs and speeds up the backup process by only capturing changes since the last backup.
- Flexible Storage Options: Supports backups to both local devices and various cloud storage platforms.
Why do we recommend it?
While data loss prevention often refers to systems that block the disclosure of data, the corruption or destruction of data also has to be prevented and that process requires preparation. Taking a backup of all sensitive data with Vembu BDR Suite means that unauthorized changes and deletions can be reversed easily.
The Server edition of the package will back up computers running Windows or Linux and the Endpoint edition will back up computers with those operating systems plus macOS. You can take a disk image and store that or opt for file-level backups. The VM edition works with Hyper-V and VMware and the Cloud VM edition backs up AWS or Azure. The cloud application package backs up data on Microsoft 265 and Google Workspace and the Applications edition will back up data from Active Directory, SharePoint, Exchange Server, SQL Server, and MySQL. This edition also takes the log files for those applications.
The BDR Suite packages don’t include cloud storage space for repositories, so you have to provide that yourself. The classic backup strategy is to have a local store for quick recovery and a second, remote location for security against site disasters. You can backup locally to SAN, NAS, or tape and the cloud repositories can be on AWS S3, Azure Blob Storage, Google Cloud, or Wasabi.
Who is it recommended for?
This package is priced per asset, so per host for the Server and Endpoints edition and per VM for the VM edition. This makes the system affordable for businesses of all sizes. You aren’t limited to buying just one edition. You can group together a number of editions that match the technologies that you use.
Pros:
- Customizable Storage: Allows organizations to choose their preferred storage locations, offering flexibility in backup strategies.
- Comprehensive Cloud Backup: Includes cloud-to-cloud backup options for Microsoft 365 and Google Workspace, ensuring data in cloud productivity suites is protected.
- Migration and Replication Tools: Facilitates easy data migration and replication, adding value for businesses looking to move or duplicate data securely.
Cons:
- Excludes Storage Space: Does not include cloud storage space as part of the service, requiring additional arrangements for data repository locations.
You can download the software for Vembu onto Windows Server or Linux and there is also a SaaS option. You can buy the on-premises software outright or choose a subscription plan for the software package or the SaaS platform. Access Vembu BDR with a 30-day free trial.
10. Trustifi Outbound Shield
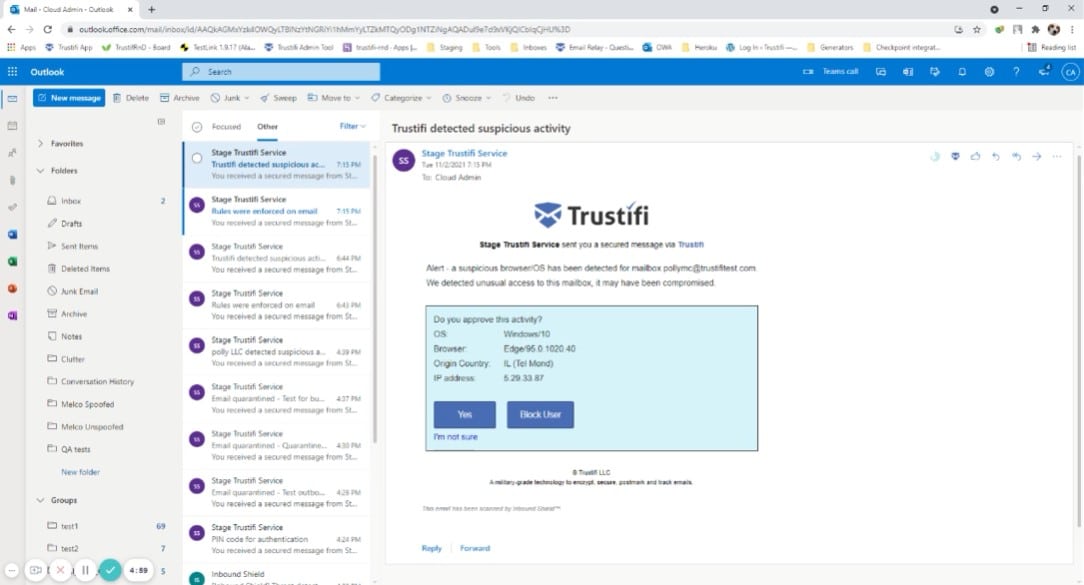
Trustifi Outbound Shield is a secure, hosted file service that focuses on protecting email content. When a user wants to send a secure message, the contents of that message are uploaded to the Trustifi sever. All that gets sent in the email body is a link to access the message. Within the Trustifi environment, recipients get the opportunity to reply and that text is also kept on the Trustifi server. This is like a chat system where responses are all grouped together in a conversation.
Key Features:
- Secure Email Storage: Hosts sensitive email content on a secure server, sending recipients a link to access the information.
- Sensitive Data Identification: Scans emails for sensitive data, applying protection based on predefined or custom policies.
Why do we recommend it?
Trustifi Outbound Shield is a proxy service that sites in the cloud and examines all outgoing emails for evidence of data transfers, either in the body of an email or as an attachment. The service provides an optional secure email system that holds the email text on its server and sends a link for access to that content to the recipient instead.
The Trustifi software doesn’t automatically secure all emails – only those that have sensitive data in them. The Trustifi system scans each email before it is sent and identifies sensitive data.
In order to get the system working for your business, you need to configure your Trustifi account, specifying your security policies. These are available as templates to implement specific data protection rules, such as those designated by PCI DSS, HIPAA, or GDPR. There are also templates where you can specify protection for specific types of data without needing to name a data protection standard. It is also possible to define your own protection rules. The Trustifi system is able to protect intellectual property as well as third-party information.
Access controls for email contents can be set by the administrator for sensitive data categories or by the sender per email. These can block the recipient from copying or saving the data. It is also possible to prevent recipients from forwarding emails that contain sensitive data. Access to specific emails can also be revoked for specified recipients.
Administrator tools in the Trustifi platform include a risk analysis feature that shows which user accounts handle more sensitive data than others and also spots users who display risky behavior in data sharing.
Who is it recommended for?
The Trustifi platform offers a number of security services for emails that include Inbound Shield, which scans incoming emails for phishing and impersonation attempts, among other checks. It makes sense to take out subscriptions to both the Inbound Shield and Outbound Shield services because they are both hosted on the same cloud server and require all of your emails in both directions to be channeled through that proxy service.
Pros:
- Selective Email Protection: Automatically secures emails containing sensitive data, ensuring targeted protection.
- Configurable Security Policies: Offers a variety of templates for common data protection standards and allows for custom rule creation.
- Advanced Recipient Controls: Enables administrators or senders to set specific access and action restrictions for email recipients.
- Risk Analysis Tools: Provides insights into user behavior and data handling, highlighting potential security risks.
Cons:
- Lack of Free Trial: Absence of a free trial option may limit initial evaluation and testing opportunities for prospective users.
If Trustifi’s email data loss prevention strategy interests you, contact the company to get a quote and access the free demo.
11. Trellix XDR Platform
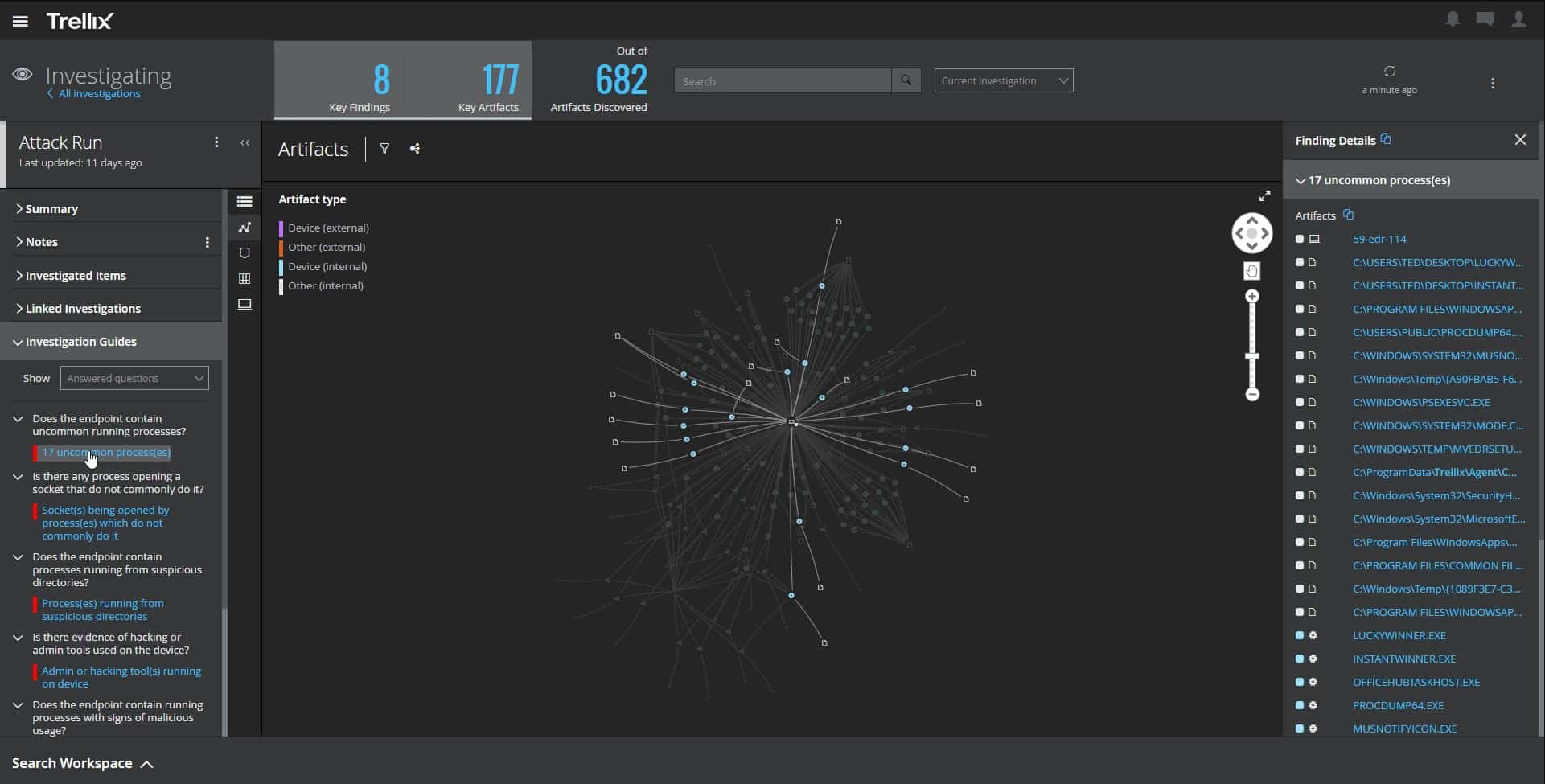
Trellix XDR Platform provides scanning for threats on endpoints and networks. This means that the tool can identify malware, such as ransomware, kill it, and remove it before it damages data. It can also spot insider threats and account takeovers that might target your data. This system is delivered from the cloud and provides constant system-wide security.
Key Features:
- Advanced Threat Detection: Scans for malware, ransomware, insider threats, and account takeovers across endpoints and networks.
- Cloud-Based Delivery: Ensures constant, system-wide security from a cloud platform.
- Automated Threat Response: Immediately neutralizes identified threats, preventing data damage.
Why do we recommend it?
The Trellix XDR Platform is an intrusion prevention system and an endpoint protection platform that also scans cloud systems. This means that it also prevents data theft. The package works with anomaly detection, which involves tracking the regular activity of each user account and flagging accounts that suddenly implement different behavior.
A change in user behavior could indicate that an intruder has got hold of the account and the Trellix system will shut it down to prevent data loss. Similarly, software that starts to process data files will be killed immediately before it tries to encrypt or move data.
The Trellix system isn’t a typical DLP because it doesn’t scan emails for data movements. However, it is just as effective because it removes the threat of outsiders getting onto the system and trying to gain access to data.
The logic behind this approach is that, if outsiders can get to sensitive data, they can’t steal it. Similarly, a disgruntled employee would be blocked from accessing data that isn’t normally needed for work. Even if a user regularly access specific data stores, attempts to transfer those files elsewhere would trigger an alert and the movement would be blocked.
This system provides data loss prevention as a consequence of its service that blocks intrusion and malware. The system can also prevent other activities often implemented by intruders, such as using the company network as a proxy system to mask illegal activities on other networks or resource consumption through crypto-mining.
Who is it recommended for?
The Trellix system is suitable for mid-sized businesses and large companies. It is particularly useful for businesses that need to prove compliance to a specific data protection standard because Trellix records its discoveries and the actions taken to block intruders and malware. This documentation forms a part of compliance reporting. The package is a little too expensive for small businesses.
Pros:
- Preventative Security Measures: Actively blocks data thieves and prevents unauthorized access or transfer of sensitive data.
- Comprehensive Protection: Offers system-wide defense against a broad spectrum of threats, ensuring robust security.
- Compliance Support: Generates detailed documentation of security incidents and responses, aiding in compliance reporting.
Cons:
- Cost Prohibitive for Small Businesses: The platform’s pricing structure may not be feasible for smaller enterprises looking for cost-effective solutions.
The Trellix system isn’t available for a free trial. However you can investigate the Trellix XDR Platform further by requesting a demo.
12. Check Point Data Loss Prevention Software Blade
Check Point is a major provider of cybersecurity systems and it integragtes data loss prevention into its firewall and edge services products. These are:
- Quantum Network Security – a range of hardware appliances
- CloudGuard Cloud Network Security – a cloud-based firewall service to protect sites and cloud resources
- Harmony Connect – a secure access service edge (SASE) that creates a protected virtual network
These three options mean that you don’t install the DLP service as a software package on your server. Instead, it runs on a network appliance or on the Check Point servers.
Key Features:
- Flexible Deployment Options: Available on hardware appliances, as a cloud service, or through a SASE solution.
- Integrated Security: Works in tandem with other Check Point cybersecurity solutions for comprehensive protection.
- Data Movement Monitoring: Tracks and controls data transfer across various channels to prevent unauthorized leaks.
Why do we recommend it?
Check Point Data Loss Prevention takes a unique attitude towards notifying about data breaches. While such events are blocked and logged, rather than notifying the security operations center (SOC), the software notifies the user that tried to send the data. This is a form of user education. In the case of an account takeover, it informs the hackers that they are wasting their time trying to steal from this business.
Having an external, network-based viewpoint, the Check Point service doesn’t examine activity on endpoints. Instead, its strategy is to examine every channel for data movement, which includes file transfer systems, chat and messaging service, email, and other Web utilities.
On discovering a potential data leak, the Check Point DLP doesn’t notify the IT Operations team but sends an alert to the user involved in the event. This approach assumes that the user accidentally disclosed the data or that a user account has been hijacked. The ethos here is to educate users to be responsible for their actions. It also makes the system more accessible to smaller businesses that don’t have an IT department.
Who is it recommended for?
As the DLP is either based on a hardware device or in a cloud SaaS package, the notification going to the user instead of a SOC means that this is a good package for businesses that don’t have a SOC. That makes the service attractive to small businesses, cost-conscious MSPs, and large businesses with overloaded IT support departments.
Pros:
- User Education Approach: Directly notifies users attempting unauthorized data actions, serving as an immediate educational tool.
- Automated Email Control: Scans and automatically blocks potentially risky emails, reinforcing data security.
- Compliance Standard Support: Comes pre-loaded with policies tailored to major compliance standards, simplifying the implementation process.
Cons:
- User Notification System: The decision to alert users rather than IT may not align with all organizational policies or preferences.
- Policy Customization Complexity: While the system offers a broad policy library, customization can be challenging for users seeking specific adjustments.
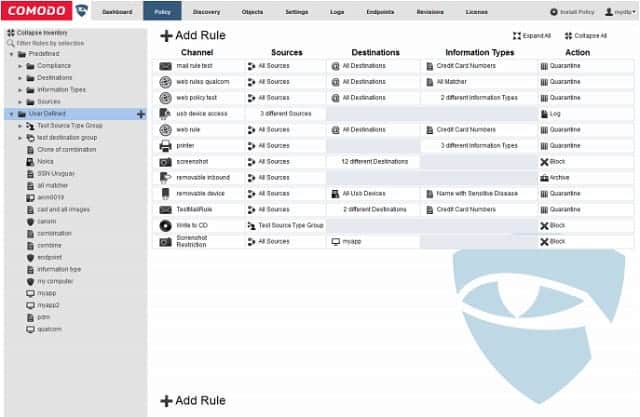
Like most DLP systems, the enforcement rules in this service are called “policies.” These are specifications that identify the types of data that are to be classified as “sensitive” and specifies which users can have access to those data points. Check Point’s DLP tool is shipped with a library of policies, which you can adapt. It is also possible to create your own policies. However, the library is organixzed into sets that categorize data according to the major data protection standards, such as HIPAA, SOX, and PCI DSS.
Your buyer’s journey for the Check Point DLP depends on which Check Point service you think would be most appropriate for your needs because the DLP isn’t sold as a standalone service. You can get a look at how the DLP works with a live demo.
13. Cyberhaven
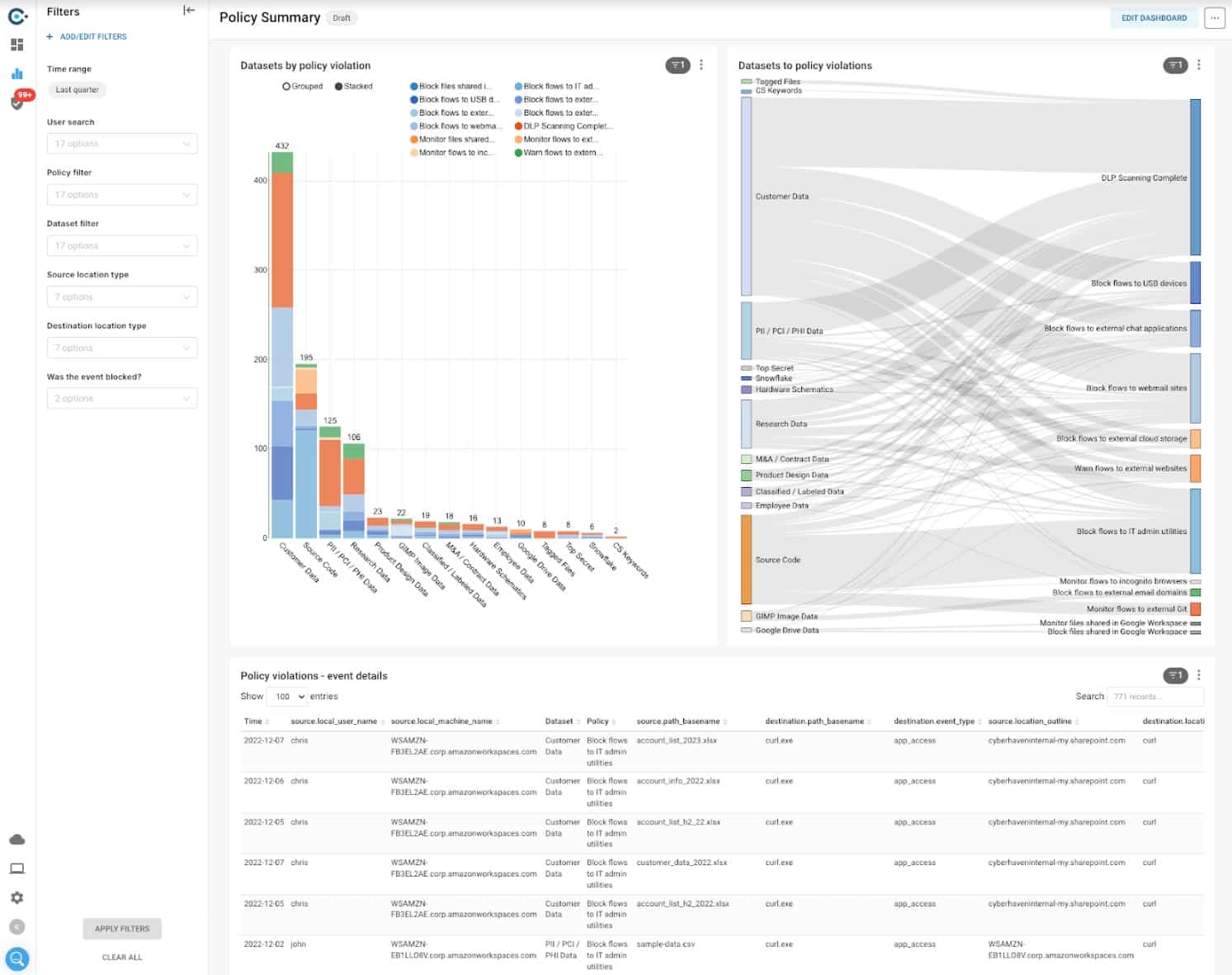
Cyberhaven starts with the fact that all system access, applications that store data, and file servers all require user credentials for access, so data loss is only going to be implemented by authorized users. Ultimately, that means insider threats or account takeover. So, there isn’t any point in protecting data stores, it is unusual account activity that indicates an attack.
Key Features:
- Data Movement Monitoring: Keeps a vigilant watch on data transfers to identify unauthorized movements.
- Quick Data Classification: Rapidly categorizes data, enhancing protection efficiency.
- Movement-Based Blocks: Blocks unauthorized data transfers, focusing on preventing insider threats and data leaks.
Why do we recommend it?
Cyberhaven relies on your user accounts being secure and granular. It focuses on looking for anomalous behavior in data movement activity. This reveals an insider threat or an account takeover and the system blocks those transfers. The strategy is innovative and might worry some administrators who want to protect files instead.
You already have a list of users that are allowed to access specific types of sensitive data. For example, the accounts department staff can’t access HR records and vice versa. So, when you set up Cyberhaven, it knows who is allowed to access what types of data and where they are allowed to send it.
Cyberhaven watches data movements to and from your on-site applications and cloud SaaS accounts and scans for sensitive data. The system is able to detect a wide range of sensitive data formats and if an authorized user suddenly starts to do unauthorized things with one of those types, the system blocks the data transmission.
The Cyberhaven system doesn’t completely block data movements. For example, if one authorized user transfers data to another authorized user, that’s OK. Even if a user transfers data outside of the organization, that could still be allowed. An example of this scenario would be a response to a data subject access request (DSAR). However, a client list or an internal research paper being emailed to a rival business would trigger a blocking action.
The idea of not protecting data stores directly is a little confusing because data usually travels one way or another from a data store to an application or to a user through browser access in order to be viewed or selected for forwarding. So, Cyberhaven does also monitor file and database access.
Who is it recommended for?
The Cyberhaven system is an option for any business that holds sensitive data in digital formats. This doesn’t only relate to the protection of PII but also trade secrets. Although the company’s talk of watching transfers rather than stores might worry you, you should check out the demo before making up your mind.
Pros:
- Sensitive Data Tracking: Effectively tracks the movement of sensitive data, offering targeted protection.
- Access Needs Assessment: Analyzes each user’s legitimate access needs, reducing the risk of inappropriate data handling.
- List-Based Transfer Comparisons: Compares data movement destinations to approved lists, ensuring compliance with policy.
Cons:
- Unconventional Strategy: The focus on monitoring data movement rather than storing may cause concern for some administrators, requiring a shift in traditional security paradigms.
The Cyberhaven system takes a new approach to sensitive data detection and categorization but it actually doesn’t move very far from the traditional approach of scanning files. Access a demo to assess the strategy.
14. ThreatLockaer

ThreatLocker is a cloud platform of system security tools that help you to implement Zero Trust Access (ZTA). This strategy involves moving access controls to applications and this strategy also helps to guard data. The ThreatLocker system builds boundaries around resources so that access to them can be controlled individually.
Key Features:
- Application Protection: Ensures only approved applications can access data, providing a robust defense mechanism.
- Access Control: Offers granular control over who can access specific resources, enhancing security.
- Comprehensive Logging: Maintains detailed logs of all activity, aiding in compliance and security monitoring.
Why do we recommend it?
The ThreatLocker system blocks access to files so that they can only be accessed through approved applications. No other application is allowed to run, so you get to control access to both software and data with this system. The applications and data can be hosted anywhere, which is a useful feature for businesses that run hybrid systems.
With ThreatLocker, you start your data loss prevention journey by defining the services to protect. So, the file server where you keep sensitive data should be first on the list. You then block access to files on the server or specific directories. Access to these files can only be implemented through approved applications.
The applications that you allow to access data stores should require credentials for access and log access events. Access to files by the application can also be logged. These data access logs are suitable for use in compliance auditing and reporting for HIPAA, PCI DSS, and GDPR.
You can also block all USB ports on every endpoint on your system. Those endpoints don’t need to be on an office network. They can be in the homes of remote workers or on multiple sites. Endpoints become part of your network when you install the ThreatLocker agent on them.
The Storage Control unit of the ThreatLocker toolset can allow USB memory sticks to attach to a computer for use by a specific user on request. This access, however, should be granted with care and revoked quickly. While a USB device is active, all file movements on or off that device are logged.
Who is it recommended for?
Any business would benefit from the deployment of ThreatLocker’s security tools. However, companies that have many sites and remote workers plus extensive use of cloud-based services, such as Google Drive or Microsoft 365, would particularly need this package.
Pros:
- Extensive Activity Monitoring: Generates detailed logs for every file access and application usage, facilitating compliance and auditing.
- USB Control Flexibility: Provides strict controls over USB device usage, with the ability to log all data transfers and temporarily allow access for specific devices.
- Network-Wide Implementation: Capable of securing endpoints across multiple locations and remote work environments, ensuring consistent security policies.
Cons:
- Lacks Data Classification: Does not include a tool for discovering and classifying Personally Identifiable Information (PII), which may necessitate additional solutions.
It’s worth noting that the ThreatLocker system doesn’t include a PII definition service. In order to know exactly which data files need to be protected, you would have to pair up ThreatLocker with a sensitive data manager tool. You can assess ThreatLocker by booking a demo.
15. SpinOne
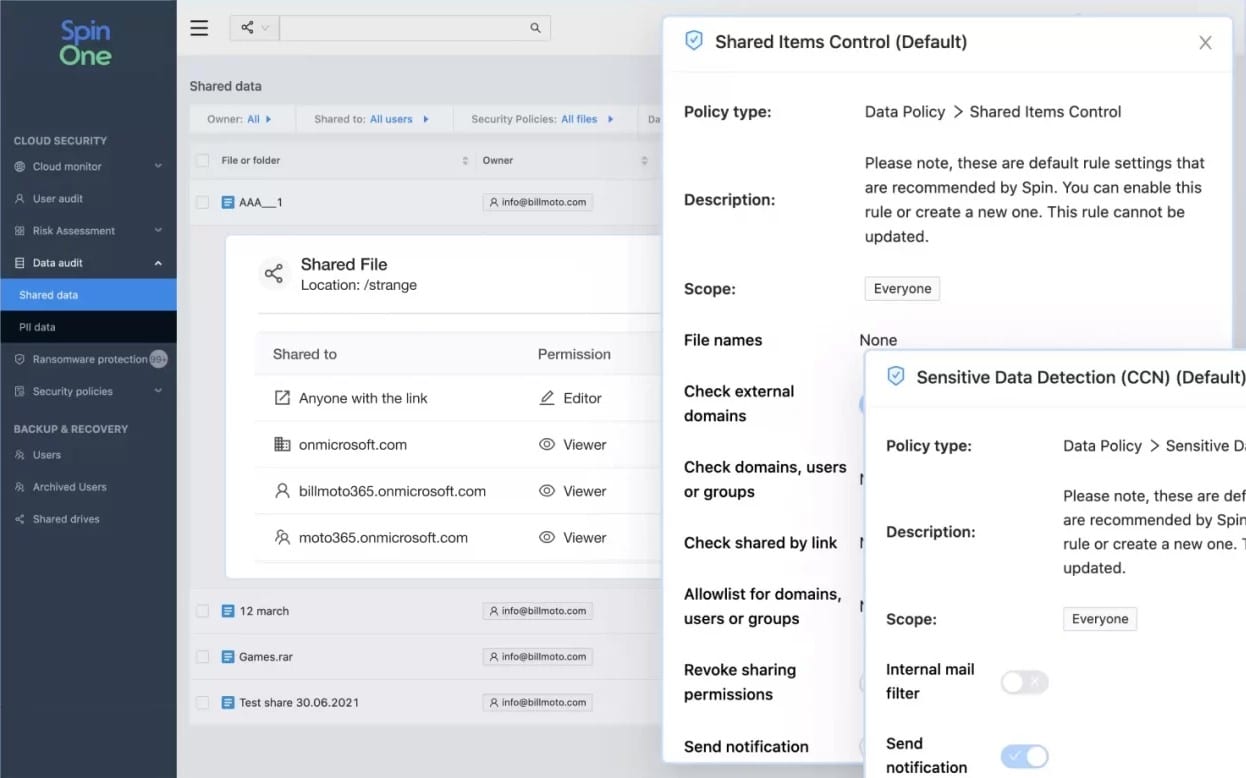
SpinOne from Spin.ai is a SaaS service that integrates with three widely-used SaaS business services – Microsoft 365, Google G Suite (Google Workspace), and Salesforce. The tool’s main aim is to provide for SaaS platforms the EDR protection that on-premises resources enjoy. The SpinOne service is offered in editions, each specialized in one of those three productivity platforms.
Key Features:
- SaaS Data Protection: Specializes in securing widely-used cloud platforms like Microsoft 365, Google Workspace, and Salesforce.
- Advanced Ransomware Defense: Offers protection against ransomware, including data backup for recovery.
- Risk Assessment: Evaluates risks associated with third-party app integrations, enhancing overall security posture.
Why do we recommend it?
SpinOne from Spin.AI is a data loss prevention system to protect SaaS packages. If your business operates entirely with cloud-based services, such as Google Workspace, Dropbox, Microsoft 365, and Salesforce, you would need to protect sensitive data within these systems and that is the specialization of SpinOne.
The SpinOne strategy offers three strands of data protection. The first of these is data backup to enable recovery from accidental or intentional destruction of data. The second is sensitive data protection, which tracks user activities around specific files and folders that contain sensitive data, and the third is a risk assessment service that checks on application dependencies, monitoring which third part software attaches to the platform for data access.
The need for data loss protection is particularly important because of the existence of data privacy standards. The SpinOne platform includes compliance auditing and reporting systems so that you can get regulatory benefits from this service.
SpinOne integrates AI-based machine learning techniques in its activity anomaly detection services. The tool watches over access to sensitive data stores and builds up profiles of typical activity for each user account. This baseline of acceptable behavior provides a reference for the anomaly detection system. This enables SpinOne to identify insider threats and account takeover incidences.
The SpinOne detection and response service is intelligent enough to control access to productivity suites and their related data stores without hindering users or generating excessive warnings. The constant AI-based fine-tuning of warning thresholds means that the service gets increasingly accurate during its service life and provides better performance than a system that uses out-of-the-box detection rules.
Who is it recommended for?
SpinOne doesn’t have any components to protect data held on your on-premises servers, so if you use a combination of on-premises and cloud-based systems in a hybrid environment, you would only get partial protection from SpinOne. If you are all SaaS, SpinOne is ideal for your business.
Pros:
- AI-Driven Behavior Analysis: Utilizes AI to monitor user behavior and detect anomalies, helping to prevent insider threats and account takeovers.
- Comprehensive Data Backup: Provides data backup and recovery solutions, ensuring business continuity in the event of data loss.
- Regulatory Compliance Support: Includes tools for compliance auditing and reporting, aiding organizations in meeting data protection standards.
Cons:
- Limited Cloud Platform Coverage: Focuses protection on specific SaaS platforms, which may not cater to businesses using a broader range of cloud services.
Spin.ai doesn’t publish a price list for its SpinOne editions. However, you can begin your contact with the service by accessing a 15-day free trial of SpinOne for G Suite, SpinOne for Microsoft 365, or SpinOne for Salesforce.
16. CrowdStrike Falcon Device Control
CrowdStrike Falcon Device Control is a cloud-based service that is an add-on to Falcon Prevent or Falcon Insight. Falcon Prevent is a device-resident endpoint detection and response (EDR) service that can be installed on Windows, macOS, and Linux. Falcon Insight is an enterprise-wide coordinator for Falcon Prevent instances.
Key Features:
- Peripheral Device Management: Offers detailed control over data transfer via USB and other removable storage devices.
- Policy-Based Security: Enables customizable security settings based on organizational policies for data protection.
- Integrated Ecosystem: Works seamlessly with Falcon Prevent and Falcon Insight for comprehensive endpoint and network security.
Why do we recommend it?
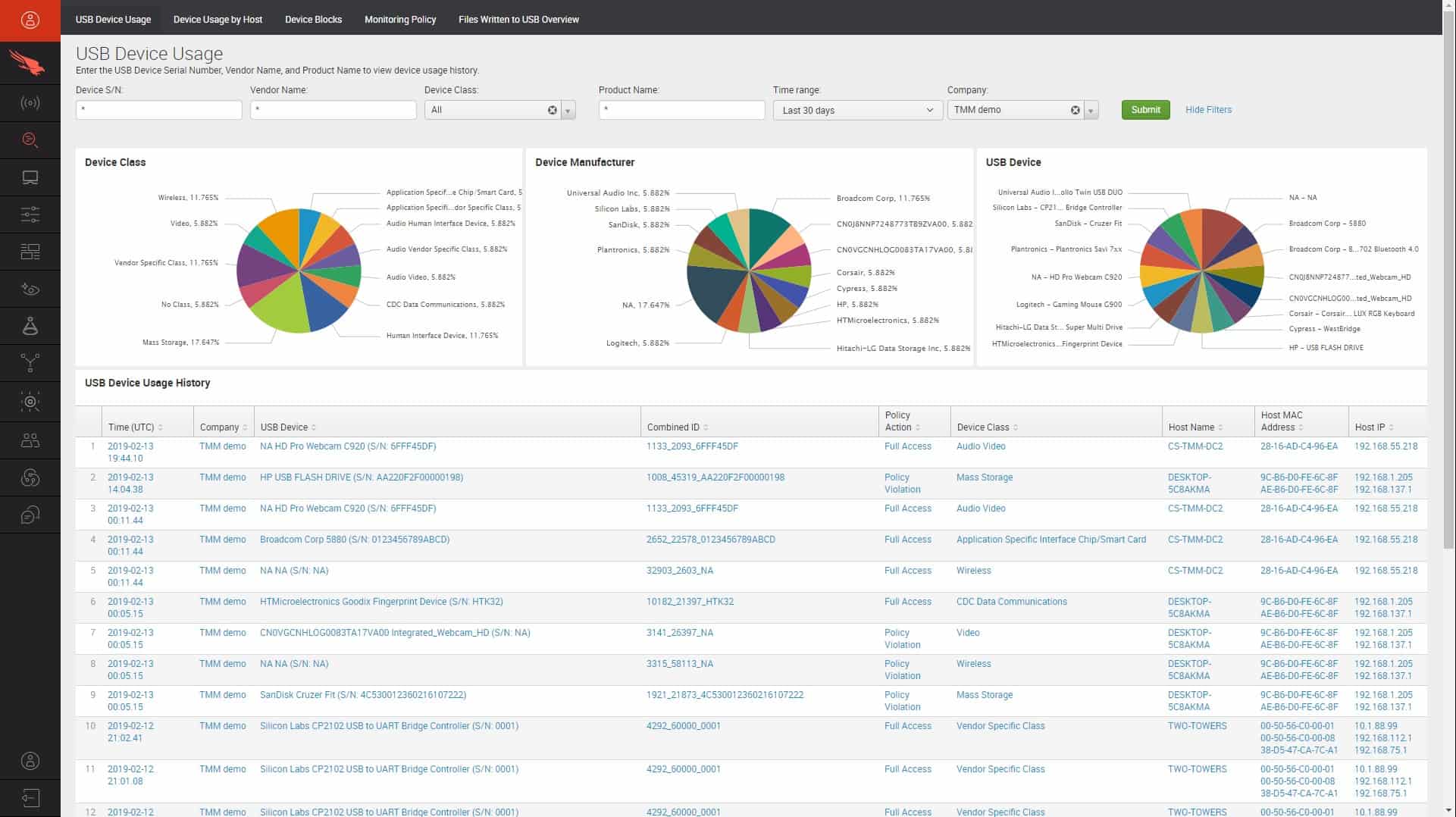
CrowdStrike Falcon Device Control is an add-on module for any of the CrowdStrike Falcon bundles. The core unit in CrowdStrike Falcon is an on-device antivirus system, called Falcon Prevent. Coordinating these instances on a site with a central threat hunter creates Falcon Insight XDR. The Device Control add-on enables the security policies defined in the XDR to extend to the monitoring of data movements on peripheral devices.
When you pair Falcon Device Control with Falcon Prevent, the endpoint-resident Prevent communicates with the Device Control service in the cloud. When Falcon Device Control is deployed alongside Falcon Insight, both cloud services communicate with the on-device Prevent modules. In either configuration, the Device Control system reaches through the endpoint to implement data exfiltration controls on peripheral devices.
It is very easy to disable USB ports entirely. However, this approach is not always suitable. For example, USB ports can be used for many features, not just for removable storage. You might want to keep USB ports active but just control what data passes over them.
The question of data movement is not an all-or-nothing decision either. You could allow certain types of data to be moved onto USB devices while blocking more important data collections from being moved. So, the control of USB devices needs to be finely tuned.
With Falcon Device Control you get to specify which types of devices can be connected or, more easily, define which device types are banned. The control extend to user access controls, so you can allow some users or user groups to use USB devices while blocking all others.
The software for Falcon Device Control is able to identify and document all devices as they are connected to a USB port on an endpoint. You can install this software on all of your endpoints and nominate one device to host the server. Thus, you get all activity reports for all devices forwarded to one dashboard for consolidated reporting.
Who is it recommended for?
Any business that handles sensitive data has intellectual property, or needs to protect trade secrets would benefit from the use of CrowdStrike Falcon Device Control. Keep in mind that this module does not operate as a standalone product, so you can only consider this product in connection with the consideration of a CrowdStrike Falcon bundle.
Pros:
- Flexible Device Control: Allows for nuanced control over which types of devices can connect, enhancing security without completely disabling functionality.
- Centralized Monitoring: Provides a unified dashboard for monitoring device usage and data movement across the network.
- Access Rights Integration: Enables integration with access rights management systems, ensuring only authorized users can transfer data.
- Rapid Response Capabilities: Offers fast, localized control over data access and transfer on all monitored endpoints.
Cons:
- Limited to Device Control: Focuses on peripheral devices and does not extend to other data exfiltration channels, like email.
CrowdStrike Falcon Device Control is an extra service that can be added to a subscription to the Falcon Pro, Falcon Enterprise, Falcon Premium, and Falcon Complete packages. The endpoint agents for this solution install on Windows, macOS, and Linux. You can get a 15-day free trial of the software.
17. Teramind DLP
Teramind DLP will help you to be compliant with GDPR, HIPAA, ISO 27001, and PCI DSS. The tool starts off by searching your entire system for sensitive data. The search follows typical data formats, such as Social Security or credit card numbers. It also uses OCR and natural language processing to scan all documents. It then prioritizes those that contain personally identifiable information, personal financial data, and personal health information. Scans to spot new instances of these data categories continue during the software’s service life.
Key Features:
- Comprehensive Data Protection: Identifies sensitive data across the system to ensure compliance with GDPR, HIPAA, ISO 27001, and PCI DSS.
- Dynamic Risk Assessment: Continuously evaluates the system for new instances of sensitive data and potential risks.
- Advanced User Activity Monitoring: Tracks user activities, including web, application, and email interactions, for detailed oversight.
Why do we recommend it?
Teramind DLP provides sensitive data identification with selective redaction that can be applied in the viewer without altering the underlying content. It is also very strong on user activity tracking and has a file integrity monitor. Lower plans of the platform are available without sensitive data management and data governance for businesses that are only interested in user activity tracking and account takeover detection.
The package includes templates for data security policies that will help you set your DLP strategy. This tool has two focuses: insider threats and data security. The user tracking functions cover activities on websites, applications, and on the network. It monitors emails and also includes a keystroke logger for special scrutiny.
Overall system activity is measured to establish a baseline of normal behavior. This is a typical strategy of intrusion detection systems so it will identify external as well as internal threats.
Data protection measures include clipboard monitoring and blocking. A fingerprinting system for files will enable you to trace who leaked a file.
The console for the software includes a Risk Dashboard, which centralizes notifications of all threats and vulnerabilities that require investigation.
Who is it recommended for?
This tool is a good choice for businesses that need to qualify for data protection standards. The platform is offered in several levels and the DLP plan is the third edition up, with two cheaper options and one more expensive plan that adds on stronger security.
Pros:
- Selective Data Redaction: Allows for the redaction of sensitive information in viewer mode without altering original documents.
- Robust Policy Templates: Includes pre-defined templates for data security policies, facilitating easier compliance with various standards.
- Integrated Risk Dashboard: Centralizes threat and vulnerability notifications for streamlined risk management.
- Versatile Monitoring Tools: Extends beyond DLP to include user monitoring and behavior analysis for comprehensive security coverage.
Cons:
- Complexity and Learning Curve: The platform’s broad capabilities may be overwhelming, particularly for users focused solely on DLP.
- Potential Privacy Concerns: Features like keystroke logging could raise privacy issues, requiring careful policy implementation.
Termaind DLP is delivered as a SaaS platform. It is also possible to get a software package if you prefer to host the system yourself. The system runs on a hypervisor created by VMWare ESXi or Microsotf Hyper-V. The cloud version requires an agent to be installed on your site. This is available for Windows, Windows Server, macOS, Citrix XenApp, and VMWare Horizon.
18. Digital Guardian Endpoint DLP
The Digital Guardian Endpoint DLP starts its service life by searching through-out your system for sensitive data. The tool logs those locations and tracks all events that occur at them. It is able to communicate with the Windows, Mac OS, and Linux operating systems and its tracking capabilities extend out to cloud resources. This package focuses on endpoint security. Digital Guardian produces a companion tool that hardens networks against data loss events.
Key Features:
- Multi-Platform Support: Compatible with Windows, macOS, and Linux, offering comprehensive endpoint protection.
- Sensitive Data Identification: Discovers and categorizes sensitive information across endpoints and cloud environments.
- Dynamic Data Protection: Implements access and movement controls to safeguard sensitive data from unauthorized actions.
Why do we recommend it?
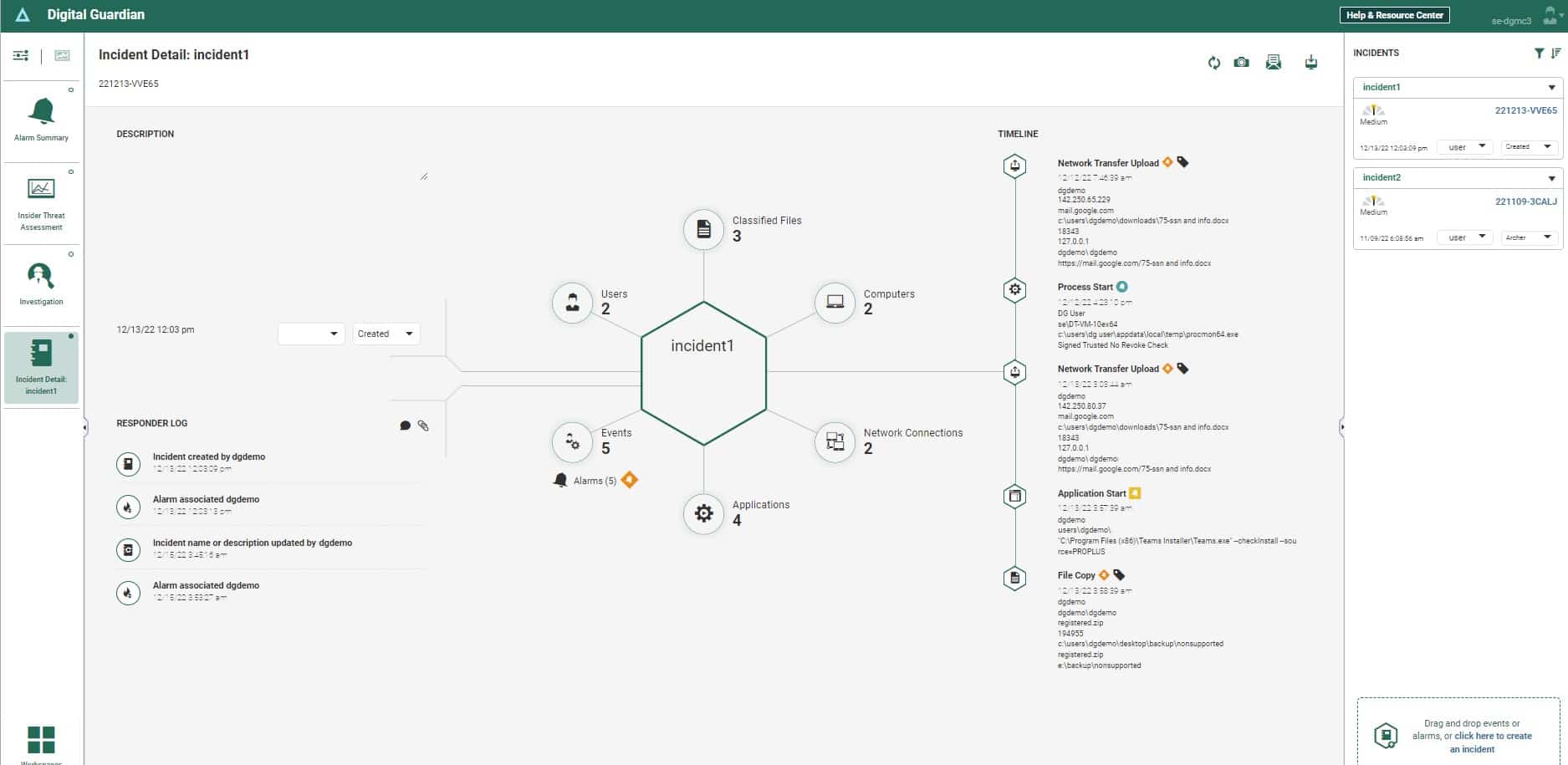
Digital Guardian Endpoint DLP is able to discover and categorize sensitive data that is resident on Windows, macOS, Linux, and cloud platforms. The tool then implements data access and movement controls through file integrity monitoring and change tracking, email and peripheral device data movements, and file transfer controls.
The endpoint data protection system can block activities on offline computers as well as monitoring devices over the network. It will automatically block unauthorized user actions, such as the destruction, alteration, copying, or transferring of protected data. This equally prevents both insider and outsider activities.
This system is suitable for the protection of intellectual property as well as personal information. It requires the network administrator to define categories of data and assign specific protection policies to each. Enhancements to the DLP give you the option of adding encryption to data storage and transmissions.
Who is it recommended for?
This is a sensitive data protection package that can be tuned to compliance with data privacy standards or set to protect trade secrets and intellectual property. The tool is able to work with all the major operating systems, which makes it a suitable DLP tool for any organization.
Pros:
- Offline Protection Capabilities: Ensures data protection measures are effective even when devices are not connected to the network.
- Flexible Data Categorization: Allows for customized data protection policies, catering to both compliance requirements and intellectual property protection.
- Encryption Enhancements: Offers options for encrypting data in storage and during transmission, enhancing data security.
Cons:
- Plugin Compatibility Issues: Some users may experience difficulties with email plugins, affecting functionality.
- False Positive Concerns: Initial setup may result in a higher rate of false positives, necessitating fine-tuning over time.
You can assess Digital Guardian Endpoint DLP by requesting a demo.
19. Code42
You will notice from the descriptions of the other tools here that corporate data protection strategies are implemented within the DLP tool by rule bases, called “policies.” Code42 has a different system and doesn’t use policies. Despite not operating on policies, the tool does link detected problems with remediation actions.
Key Features:
- File Integrity Monitoring: Logs activities and reverses unauthorized changes, ensuring data integrity.
- Comprehensive User Activity Tracking: Monitors data access and file movements across operating systems and cloud services.
- Advanced Analysis Tools: Utilizes event data for exposure analysis, identifying potential internal and external threats.
Why do we recommend it?
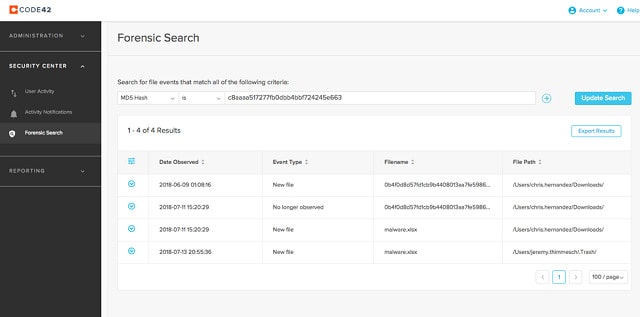
Code42 Incydr offers file integrity monitoring that performs activity logging and change reversal. It doesn’t include a sensitive data discovery module. This system is able to monitor data stores on Windows, macOS, and Linux and it will watch over file movements on cloud-based email systems and SaaS applications.
Code42 works on data files the way a SIEM tool behaves with log files. It monitors data files, backing them up and restoring the original version should any changes be made. It also tracks every access to those data files and blocks any copy or transfer actions.
All actions on files, including those performed by Code42 are recorded, which generates the audit trail that you need for data security standards. The tool includes an analysis utility that uses event information to present exposure of internal misdeeds or intrusion threats.
Who is it recommended for?
The absence of sensitive data classifications makes this tool a little weak for compliance auditing. However, it includes strong user activity tracking, so it is good for identifying insider threats and account takeovers.
Pros:
- Automatic Restoration: Capable of restoring files to their original state, providing an effective defense against data tampering.
- SIEM-like Capabilities: Offers robust monitoring and analysis, akin to Security Information and Event Management (SIEM) tools, for detailed oversight.
- Audit and Analysis: Generates detailed audit trails for compliance and security analysis, aiding in threat identification and response.
Cons:
- Resource Intensity: May require significant system resources, impacting device performance.
- Complexity and Cost: Features a steep learning curve and comes with a high cost, potentially making it less accessible for some organizations.
There are two opportunities to scope out Code42 Incydr because you can get a demo of the system or access a 4-week free trial.
20. Comodo MyDLP
You receive a license for your entire organization that covers all of your endpoints and sites. This tool will also protect data held on cloud servers. MyDLP will discover all of the sensitive data held by your company, log it, and protect it. Comodo MyDLP is a site-based data protection system that can be tailored to enforce data protection standards compliance.
Key Features:
- Comprehensive Endpoint Monitoring: Tracks and logs endpoint activity throughout the network to ensure data security.
- Cloud Platform Activity Tracking: Monitors actions and data movements on cloud services, extending protection beyond physical premises.
- Focused File Protection: Employs a targeted approach to safeguarding sensitive data, based on specific data formats.
Why do we recommend it?
Comodo MyDLP will perform sensitive data discovery and classification. However, it operates in a different way than most data protection compliance systems. With most of these sensitive data systems, you can select a data standard from a dropdown list in the settings screen to calibrate the search engine for specific types of data to look for. In the case of MyDLP, you select a template for a specific data format, such as credit card numbers or social security numbers. The system will then protect those data locations and block their movements by users without specific high-privilege accounts.
This system focuses on a user permissions service. It lists who can have access to which data and what actions each person is allowed to perform on each bit of data. The data it protects might be trade secrets, development plans, engineering drawings, accounts, or the personal data of employees and customers. It is able to monitor devices running any operating system and the software can be installed on premises or accessed online as a cloud-based service.
Who is it recommended for?
You would have to map any data protection standard to specific data types and then set up MyDLP to work with those specific data formats. So, this is probably not the easiest compliance tool available. However, its data movement controls extend to email systems, peripherals, and even printers.
Pros:
- Scalable Enterprise Solution: Offers features that effectively scale to meet the needs of large organizations, covering all endpoints and sites.
- Sensitive Data Discovery: Capable of automatically identifying sensitive data or being configured to monitor designated areas and data types.
- Flexible Deployment Options: Available as both an on-premise solution and a cloud service, offering versatility in data protection strategies.
Cons:
- Integration Limitations: Lacks seamless integration with other tools in the Comodo suite, potentially complicating ecosystem synergy.
- Complex Setup: Presents a steeper learning curve compared to similar DLP solutions, requiring more effort for effective implementation.
MyDLP installs on a hypervisor and it will operate over VMWare or Hyper-V. You can assess the system by requesting a demo.
Priorities for DLP
The first and most obvious topic to deal with when trying to prevent the data your business stores is to control access to it. However, this is not your only task. In order to prove compliance with data security standards, you are going to need some evidence. So, constant transaction logging is needed, and you are going to need to store those logs for years so that they can be available for spot audits. Constant self-auditing is also necessary to ensure that security procedures are sufficiently strong.
Although failure to protect data is a setback, any leakage should not be covered up. Non-disclosure of data leakage is a big mistake. It will cause you to lose your accreditation. Data protection standards all include protocols for data loss notification and they should be followed.
Surprisingly, most organizations don’t properly track all of the locations on the system where data is stored. Staff might keep notes in documents on their desktop computers and forget to delete them; other local stores, such as contact databases can sometimes be overlooked. It is important to centralize the data storage and track access to it.
The data held by your company is a potential money earner for hackers. So, you have to properly defend your network against intrusion. However, authorized users also present a security risk. They might be tricked into passing on data to outsiders or might be motivated through resentment or greed to steal the company’s data. Preventing the copying of data onto portable devices, or printout, or sending data out through email, or a chat app is another important requirement of your DLP system.
Compliance to a data security standard is also important in order to win contracts. The public sector is very strong about protecting personal data and they ripple that priority through all of the services that they buy. So, if you don’t implement effective data loss prevention you will be locked out of the opportunity for new contracts. The need to comply with the standards of the public sector continues through the supply chain. So, even if you don’t bid for public sector contracts, your ability to do deals with businesses that do work for the public sector will be reduced.
Conclusion
Data loss events were once seen as an unfortunate risk. The IT industry and the legal systems of most advanced economies recognize that no IT system can ever be 100 percent secure. However, the requirements for companies to take all possible steps to prevent data disclosure have become far stricter in recent years.
Many businesses are unable to fully identify all of the locations of data storage and fixing that issue is the first step to a comprehensive data loss prevention strategy. Getting the right DLP tools is very important and you won’t be able to fully comply with the law or data security standards without them. Without standards accreditation, you will be barred from bidding for many contracts and without full data loss protection systems you run the risk of a disclosure event, which could lead to destructive prosecutions.
You run a great risk of your business being destroyed if you don’t have a data protection strategy. Data loss prevention software is no longer optional.
Data Loss Prevention Software FAQs
How can cloud computing prevent data loss?
The data loss risk is no different in cloud computing than it is with onsite infrastructure with the exception of the communication channel between your site and the cloud host.
- Locate all sensitive data
- Categorize data according to security standards requirements
- Track all access to categorized data
- Track changes to device configurations
- Monitor log file records for unexpected user behavior or unauthorized traffic
- Install all updates and patches to firmware, operating systems, and software
- Secure all access channels across the internet
What is a data loss prevention policy?
A data loss prevention policy is a set of rules and workflows laid down by your business to define how to allow access to data and protect the information that you hold. This strategy applies to working procedures, access rights management, activity monitoring procedures, reporting requirements, and disaster recovery measures.
What is a DLP alert?
A DLP alert is a system-generated message. A DLP tool monitors activities, such as data storage access and network traffic. The software will raise an alert if an activity lies outside registered acceptable behavior. The alert does not necessarily mean that a data loss event has occurred. It could identify a potential risk or a system weakness that the actions of intruders have exposed without successfully touching the target data. An alert should instigate an investigation into the necessity of adjusting security standards or taking some other preventative measures or it could indicate a security breach in progress.