Credential Management Systems (CMS) are available both on an individual level and as an enterprise-wide service. A key feature of CMSs is that they can distribute credentials in a closed-loop system, removing the need for operators to know the passwords being used.
This is particularly important for organizations that manage systems on behalf of other businesses. A CMS increases confidentiality by removing the risk of insider threats.
Here is our list of the best credential management systems for IT professionals and MSPs:
- N-able Passportal EDITOR’S CHOICE A cloud-based credential management system that automatically discovers all user accounts on a system lists them for management, and synchs all changes with onside AD and LSAP implementations.
- NinjaOne Credential Exchange A credentials manager that is integrated into the cloud-based NinjaOne RMM remote monitoring and management system.
- ManageEngine Endpoint Central A unified endpoint management system that includes its own credential management system.
- Dashlane Business A cloud-based credentials manager that allows employees to use the service for personal use as well as for work logins.
- Zoho Vault A cloud-based credential management service that coordinates on-premises and cloud-based access rights systems and also includes secure document storage space.
- LastPass Enterprise A cloud-based credentials manager that creates a single-sign-on account for a long list of business applications.
Credential management components
A central feature of the CMS architecture is password management. The CMS should also be able to generate complex passwords and store them in an encrypted format without disclosing them to administrators running the CMS software.
The second main element of a typical CMS is a password distribution mechanism. Operators that need to access a protected system don’t need to log in to that computer or network. Instead, the facilitating utility requests the credentials from the CMS without human intervention. The CMS then delivers the credentials which feed to an automatic login routine in the system access software.
The credentials distribution process is more than just a messaging system. It integrates encryption and authentication procedures to ensure that the requestor for the credentials is not an intruder and also to protect the transmission of sensitive information from wiretappers.
Most CMSs use a public key encryption system that enables the requestor to prove its identity and also protects transmission without needing to distribute encryption keys. This is very similar to the security procedures used by Transport Layer Security (TLS), the authentication system deployed by HTTPS to protect web traffic.
Another important feature of CMS software is that it can log every credentials request. This enables a business to know exactly which service had access to a resource and at what time. Should a data breach occur, tracing all possible culprits is an essential task, and activity logging provides that information.
CMS services offer extra security features, such as two-factor authentication (2FA) and automatic password rotation. Setting up initial credentials requires an interface to a business’s access rights system. Once a resource’s allowed user accounts have been set up in the CMS, further communications with access rights systems are required whenever passwords are replaced.
The best credential management systems
The need to keep passwords secure and free from disclosure is important in any organization. In the past, IT departments created a weak point in system security because support technicians needed to know system passwords in order to log into a resource and fix a problem.
The creation of credential management systems removed the need for technicians to know passwords in order to carry out their tasks. The automated credentials request procedures built into system access software also removes the need for an operator to get involved with system or user passwords.
Managed Service Providers (MSPs) have an even higher priority for password security. Their technicians not only risk the security of the MSP’s system if they have to acquire credentials, but they also could compromise the security of every client of the MSP. An MSP would find it difficult to win new business if its technicians had to get direct access to the passwords of all users. The implementation of a CMS enables the MSP to demonstrate to potential customers that there is no way any of the staff of the service provider could find out access credentials.
Our methodology for selecting a credential management system
We reviewed the market for credential management tools and analyzed the options based on the following criteria:
- Password distribution without users getting visible access
- Login screen autofill
- Secure password locker
- Activity logging
- Permissions levels
- A free trial or a demo service that allows an assessment to be made before paying
- Value for money, provided by an affordable but comprehensive package
Using this set of criteria, we looked for credentials management services that can be used throughout the organization for support access.
You can read more about each of these options in the following sections.
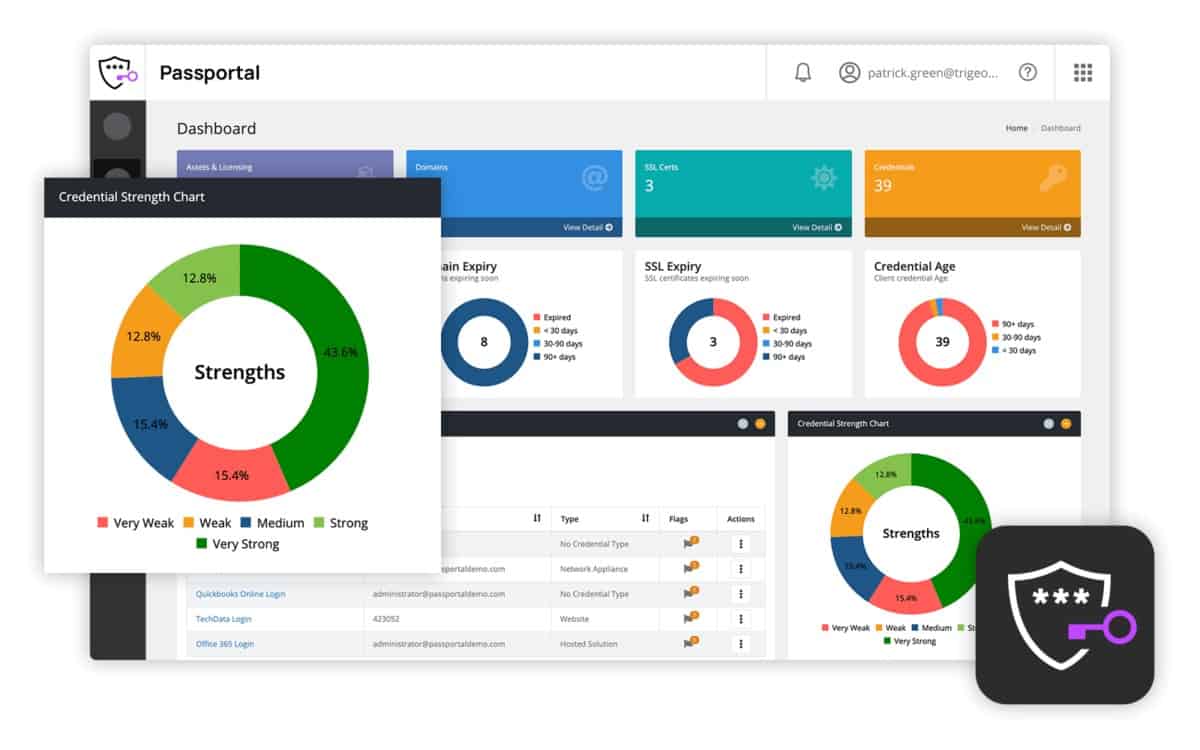
1. N-able Passportal
Passportal is a cloud-based credential management system. It centralizes the controls of identity management and access management in one console. The system is able to manage access rights to resources on many sites, so it is a good tool for centralized IT departments. It is also built to enable an MSP to support credential management for multiple clients.
Key Features:
- MSP-Oriented Design: Tailored for managed service providers to centralize credential management.
- Active Directory Integration: Seamlessly connects with AD and LDAP for streamlined access management.
- Cross-Environment Access: Manages credentials for both on-premises and cloud services efficiently.
- Temporary Account Creation: Generates short-term access accounts for secure, temporary access.
- Automated Password Management: Includes a password generator and enforces policy-based password changes.
Why do we recommend it?
N-able Passportal combines password management with document security. The encrypted vault stores all your corporate passwords and also sensitive documents. Credential distribution is implemented behind the scenes without the user seeing passwords. Documents can only be accessed by specific users. The console also acts as a front end for Active Directory.
The Passportal system supports Microsoft-produced access rights systems based on Active Directory and LDAP. It is able to manage credentials for access to a network, endpoints, email, file servers, and cloud-based services, such as Azure and Office 365.
When beginning service, Passportal searches for all AD-controlled services and software and compiles its own user account list to enable credential management to be driven within its own console. The system administrator then works with user accounts listed in Passportal with the ability to add, alter, and delete accounts. All changes made within Passportal get synched to local AD instances.
Passportal is able to create temporary access accounts to allow the technician access to a system without having to use permanent credentials that could be disclosed. The creation of each technician account is recorded and the temporary account gets deleted once the technician’s task is complete.
The password management features of Passportal include a password generator and the enforcement of password rotation. Passwords for each user are held in a personal vault and can be distributed automatically for autofill functions in many applications. The credentials manager integrates with-able Take Control, N-central, and RMM, ConnectWise Manage, Automate, and Control, Datto Autotask, NinjaOne, and Kaseya VSA and BMS. When dealing with these integrated services, all credentials get exchanged behind the scenes, so the user never needs to know what they are.
Who is it recommended for?
This system was specifically designed for use by managed service providers. The credentials that it stores relate to access for MSP systems and also access to the assets of clients. The N-able platform includes an RMM package and Passportal integrates with that. It can also manage passwords for a list of other RMM systems.
Pros:
- Comprehensive Audits: Facilitates access and change audits.
- Custom Encryption Keys: Allows users to generate their own encryption keys.
- Policy-Driven Security: Enforces strong password policies and rotations
- Integration Capabilities: Integrates with various Remote Monitoring and Management (RMM) and Professional Services Automation (PSA) tools.
- Comprehensive Documentation: Includes IT documentation management features, allowing for better organization and retrieval of information.
Cons:
- Not Ideal for Small Networks: Features are targeted at MSPs and larger enterprises, which may be excessive for smaller setups.
Passportal is charged for by subscription, paid monthly in advance. There is no contract, deposit, or minimum service period. You can schedule a demo.
N-able Passportal is our top pick for a credential management package because it offers a comprehensive, secure, and user-friendly solution tailored for IT professionals and managed service providers (MSPs). With its robust features designed to streamline the management and protection of sensitive credentials, Passportal ensures that your organization’s login information is securely stored, easily accessible, and compliant with industry standards. One of the most important services of Passportal is its integration with other N-able tools, allowing for a seamless, centralized management experience. This integration ensures that credentials can be accessed quickly across various platforms, improving workflow efficiency without compromising security. Passportal also supports single sign-on (SSO) capabilities, reducing the burden of remembering multiple passwords and enhancing user convenience while maintaining security. Security is a top priority with N-able Passportal. It uses encryption standards, including AES-256, to protect sensitive credentials from unauthorized access. Such features as role-based access controls, multi-factor authentication (MFA), and secure password sharing ensure that only authorized users can access critical information. The platform’s auditing and reporting capabilities allow businesses to track user activity and ensure compliance with security policies. Passportal is an excellent solution for businesses of any size. It eases onboarding and user account management, even for organizations with limited IT resources. OS: Cloud basedEDITOR'S CHOICE
2. NinjaOne Credential Exchange
NinjaOne is a remote monitoring and management system, which can manage several sites from one central location. This makes it a good tool for IT professionals operating a central IT department. Multi-tenant features in the system also make NinjaOne an ideal software platform for Managed Service Providers.
Key Features:
- Client System Access Management: Streamlines access to client systems with secure credential distribution.
- Patch Management Integration: Works in tandem with patch management for efficient system updates.
- Detailed Activity Logging: Captures all credential use and technician activity for audit purposes.
Why do we recommend it?
NinjaOne is a rival to the RMM packages offered by N-able. It has its own integrated credential management tool – this is the NinjaRMM Credentials Exchange. This tool specifically operates for technician access to the devices on client sites. It stores passwords for endpoints running Windows and macOS.
Credential Exchange is a credential management system that is built into NinjaOne. It is specifically designed to enable technicians to run scripts behind the scenes on endpoints. The system is able to manage access to computers running Winds and macOS and those scripts will be run without requiring the device’s user to log off. The user won’t even realize that troubleshooting and maintenance tasks are going on.
The Credential Exchange service integrates with NijnaRMM’s patch manager and software management functions. It enables automated and manual software updates to be implemented in bulk or individually on any of the managed endpoints running Windows or macOS. It also facilitates access to endpoints using the NinjaOne remote desktop utility.
Credential usage events are logged for an audit trail along with all technician activity logs that are built into other utilities in NinjaOne.
Who is it recommended for?
The NinjaOne platform was designed for use by managed service providers and it is now also being marketed to corporate IT support departments. The credentials exchange is a part of the NinjaOne RMM package – remote access for technicians won’t work without this tool. The credential manager is also relied upon for remote task automation.
Pros:
- Extensive Integration: Offers over 120 integrations, enhancing compatibility with existing IT ecosystems.
- Customizable Interface: Tailors monitoring and device management to specific organizational needs.
- Remote Troubleshooting: Enables technicians to execute remote commands without full session initiation.
- Adaptable Pricing: Provides flexible pricing options to accommodate various organizational sizes.
Cons:
- Limited Trial Period: A longer evaluation period is desired for thorough testing of its capabilities.
NinjaOne is a cloud-based service and is charged for by subscription. The RMM is available as a total package and includes Credential Exchange. It is available on a 30-day free trial.
3. ManageEngine Endpoint Central
ManageEngine Endpoint Central – formerly Desktop Central – enables a central IT department to manage endpoints and servers on multiple remote sites. The functions of this system also extend to mobile devices, making it a unified endpoint management system. None of the functions of Endpoint Central would be possible without being able to access the operating systems of all of the devices that it serves. For this purpose, the Endpoint Central system has its own Credential Manager.
Key Features:
- Technician Remote Access: Manages credentials specifically for technician remote access and system interventions.
- Secure Distribution: Ensures secure credential handling for system and device access.
- On-Premises Deployment: Offers a software solution that can be hosted internally for full control.
Why do we recommend it?
ManageEngine Endpoint Central is an RMM package that is designed for use by IT support departments. This tool includes remote access for automated processes and also for manual troubleshooting and maintenance tasks. The Endpoint Central package includes a password locker to facilitate these operations without technicians needing to see passwords.
The Endpoint Central system automates many IT department tasks. It includes patch management, software management, mobile device management, configuration management, IT asset management, and endpoint security functions.
Endpoint Central allows multiple access accounts for access to the dashboard with a superuser status for system administrators. So, each technician using the system has an individual account.
The Credentials Manager operates on two levels – a secure anonymized central credentials store and a local user-accessible credentials system. The system administrator is able to manage a pool of credentials for automated access to remote devices. These account details are not visible to other users of Desktop Central. Each technician can access a personal section of the Credential Manager to organized allocated access accounts.
The Endpoint Central dashboard includes a remote access console and remote desktop system for use by technicians engaged in troubleshooting. The entry into remote devices through this system can be made possible either through administrator credentials or through a personal account of the technician. In either case, the credentials are communicated to the remote access console automatically without visibility or the need for manual input.
Who is it recommended for?
This package is for in-house use – Endpoint Central MSP is offered to managed service providers. The full package has a Free edition for 25 endpoints, which includes the credential manager. The software for the bundle installs on Windows Server, Azure, and AWS and there is also a SaaS version.
Pros:
- Supports Various Platforms: Compatible with a wide range of operating systems, including Windows and Linux.
- Comprehensive Reporting: Delivers in-depth reporting features suitable for both MSPs and enterprise use.
- Unified Management: Combines endpoint and credential management for streamlined operations.
Cons:
- Geared Towards Larger Entities: Best suited for MSPs and organizations managing multiple sites, possibly overkill for smaller teams.
Endpoint Central is on-premises software that installs on Windows Server and Linux. Credential Manager gives access to devices running Windows, Linux, macOS, iOS, Android, and Windows Mobile. The system is available for a 30-day free trial.
4. Dashlane Business
Dashlane Business is a credential manager based in the cloud. Dashlane also offers a password manager for personal use. All user account information is stored in a secure, encrypted vault that is held on the Dashlane cloud server, so it can be accessed from any device in any location in the world that has Internet access.
Key Features:
- Cloud-Based Solution: Provides a secure, accessible-anywhere password management system.
- Encrypted Vault: Stores passwords and credentials in a highly secure, encrypted online vault.
- Password Generation: Automates the creation of strong, unique passwords to enhance security.
Why do we recommend it?
Dashlane Business offers a combined identity protection system that includes secure password storage and distribution and a Dark Web scanner that identifies password disclosure. Users don’t get to see passwords, which is a good block against insider threats and the risks presented by departing employees.
Each user registered in the system gets a personal vault space and there is also a company-wide credentials management system included with a Dashlane Business account. Employees are able to use their Dashlane service for personal use as well as getting their business passwords managed by the system. The Dashlane service includes a password generator, which creates impossible-to-remember passwords. A Dashlane app on the protected device communicates securely with the Dashlane server to autofill all login screens. The Dashlane app is available for Windows, macOS, iOS, and Android.
Communications between the Dashlane server and protected devices are protected by encryption and access to the dashboard is facilitated through any browser and protected by TLS encryption and authentication. Two-factor authentication is also available but this needs to be activated by the system administrator.
Dashlane Business includes a web protection system that scans any requested web page for malware and blocks it from loading into protected browsers if any hacker tricks are detected.
Who is it recommended for?
Small businesses can get the reasonably priced Starter pack, which provides protection for 10-user accounts. Higher plans have per-user pricing, which makes the package very scaleable. The two top plans, called Teams and Business include extra features, such as a VPN for WiFi protection and a single sign-on mechanism.
Pros:
- Cross-Platform Accessibility: Ensures access across all major platforms for seamless integration.
- Convenient Autofill: Simplifies login processes with secure password autofill capabilities.
- Enhanced Security Features: Includes a password generator and dark web monitoring for comprehensive protection.
Cons:
- Browser Extension Limitations: Some features may not perform optimally due to frequent updates from browser developers.
Dashlane Business is a subscription service with a rate per user per month. You can access the service on a 30-day free trial.
5. Zoho Vault
Zoho Vault is a cloud-based secure storage system that includes a credentials management service and a secure document storage space. Zoho Vault includes a multi-account bundling feature that gives each user a personal space while also creating a group-wide credential management service for system administrators. This means that employees can use their account for personal use as well as for work.
Key Features:
- Encrypted Storage: Provides a secure, encrypted vault for both credentials and documents.
- Versatile Credential Management: Handles passwords for both on-premises and cloud resources.
- Shared Access: Enables controlled sharing of credentials among team members.
Why do we recommend it?
Zoho Vault is an online package that is very easy and quick to set up. The tool is able to manage passwords for on-premises systems as well as for other cloud platforms. The package stores credentials in an encrypted vault and distributes them unseen. You can also store important documents in the vault.
The Zoho Vault is protected by uncrackable 256-bit key AES encryption. The system is accessed through any standard browser and the internet data transfers for console traffic is protected by HTTPS. Zoho also produces an app for access from iOS and Android devices.
The management dashboard syncs with many on-premises or cloud-based access right systems including Active Directory, Azure AD, Google Cloud Platform, and Office 365. This means that Zoho Vault will become your central credentials management dashboard and you won’t need to visit each access rights system because changes made in Zoho Vault get rolled out automatically.
Permissions can be set up per group and you can allocate each user account to a group to automatically set a list of permission per account. Individual permission level settings are also possible.
Each user gets login screens filled in automatically. This means that the complex passwords generated within the management console don’t need to be remembered, and they are not even seen by the end-users. End-user facilities include the ability to grant access to files or directories to other team members registered in the Zoho Vault team account.
A team account of Zoho Vault logs all of the credential-related activities of team members, creating an audit trail that is useful for data security standards compliance and can also be used to investigate data breaches.
Who is it recommended for?
There are three versions of Zoho Vault: Individual, Teams, and Enterprise. Businesses need to look at the Enterprise system to get full features, such as on-site controls as well as website password storage. This plan gives you coordination with your Active Directory instances and includes a single sign-on system.
Pros:
- Simplified Organization: Categorizes passwords by service for easy retrieval by all users.
- Cloud Accessibility: Offers the convenience of accessing credentials from anywhere, on any device.
- Flexible Access Control: Supports granular permissions for individuals or groups, enhancing security for diverse environments.
- Personal Use Option: Available for free for individual users, promoting wide accessibility.
Cons:
- Trial Duration: A more extended trial period could better showcase its full capabilities.
Zoho Vault is a subscription service and it is available in three editions for business: Standard, Professional, and Enterprise. The business plans are charged at a rate per user per month. There are no setup fees or minimum service periods. All paid versions are available for a 15-day free trial.
6. LastPass Enterprise
LastPass offers a free credential management service for individuals and has a paid package for business, called LastPass Enterprise. This is a cloud-based service that is able to coordinate with other access rights management systems based on-premises and in the cloud.
Key Features:
- Single Sign-On (SSO) Management: Simplifies access across applications with SSO capabilities.
- Secure Password Sharing: Facilitates the safe distribution of passwords within the organization.
- Enhanced Security: Implements multi-factor authentication to bolster access security.
Why do we recommend it?
LastPass Enterprise is a business plan from one of the most widely-used password managers in the world. This system provides each employee with a personal vault and links it into the browser’s user account. This means that as long as the user is logged in, passwords can be accessed from any device.
The LastPass Enterprise system offers a central dashboard to system administrators where Single Sign-On accounts can be set up for all users. The credential management system is able to integrate with a long list of applications and communicate account credentials without the user getting any sight of passwords. This makes it ideal for use by IT departments and MSPs for technician access.
Among the long list of systems that LastPass Enterprise can manage credentials for are AWS, Salesforce, Datadog, GitHub, Evernote, Google Cloud Platform, Dropbox, and Office 365. Once an application is linked to the LastPass system, all user accounts can be managed centrally through the LastPass system because they will be replicated in the local authorization systems of those other systems.
There are three other LastPass plans for businesses, which are called Teams, MFA, and Identity. However, the Enterprise system is the best of all editions because it includes procedures for multi-factor authentication as well as team credential management services.
Who is it recommended for?
The Enterprise plan is the top plan of the Business division of LastPass. There are two lower plans available for those who don’t need all of the features. One problem with this system is that it only stores passwords for online services, not for on-premises software.
Pros:
- User-Friendly Interface: Offers an intuitive admin console and user experience.
- Comprehensive Auditing: Provides detailed logs of login activities for security and compliance.
- Flexible Password Management: Allows for secure password sharing and private storage within individual vaults.
- Global Accessibility: Enables password access from anywhere, backed by secure cloud storage.
Cons:
- Trial Limitations: A longer evaluation period is desirable for a thorough assessment.
LastPass Enterprise is a subscription service with a charge per user per month. You can test the system on a 14-day free trial.
Credential Management Software FAQs
What is credential management software?
A credential management system (CMS) is a password locker. This service is available for individuals and will automatically instantiate login values from the stored data. Team versions transmit passwords to application login screens across a network. Transmissions are usually protected by a public key encryption system.
Why is credential management important?
Credentials management enables the use of unique, complex passwords, which can be created by a password generator. Credentials management systems (CMSs) often include a password generator along with secure storage space for all passwords. When used for teams that access the systems of external businesses or individuals, such as support technicians, the automatic population of password fields means that the employee never gets to discover the login and so cannot access the protected system outside of the controlled and monitored work environment.
Does Microsoft have a password manager?
The Microsoft Edge Web browser has a password manager built into it. This can generate complex passwords and store them securely. The tool will automatically populate remembered login screens when they are accessed.