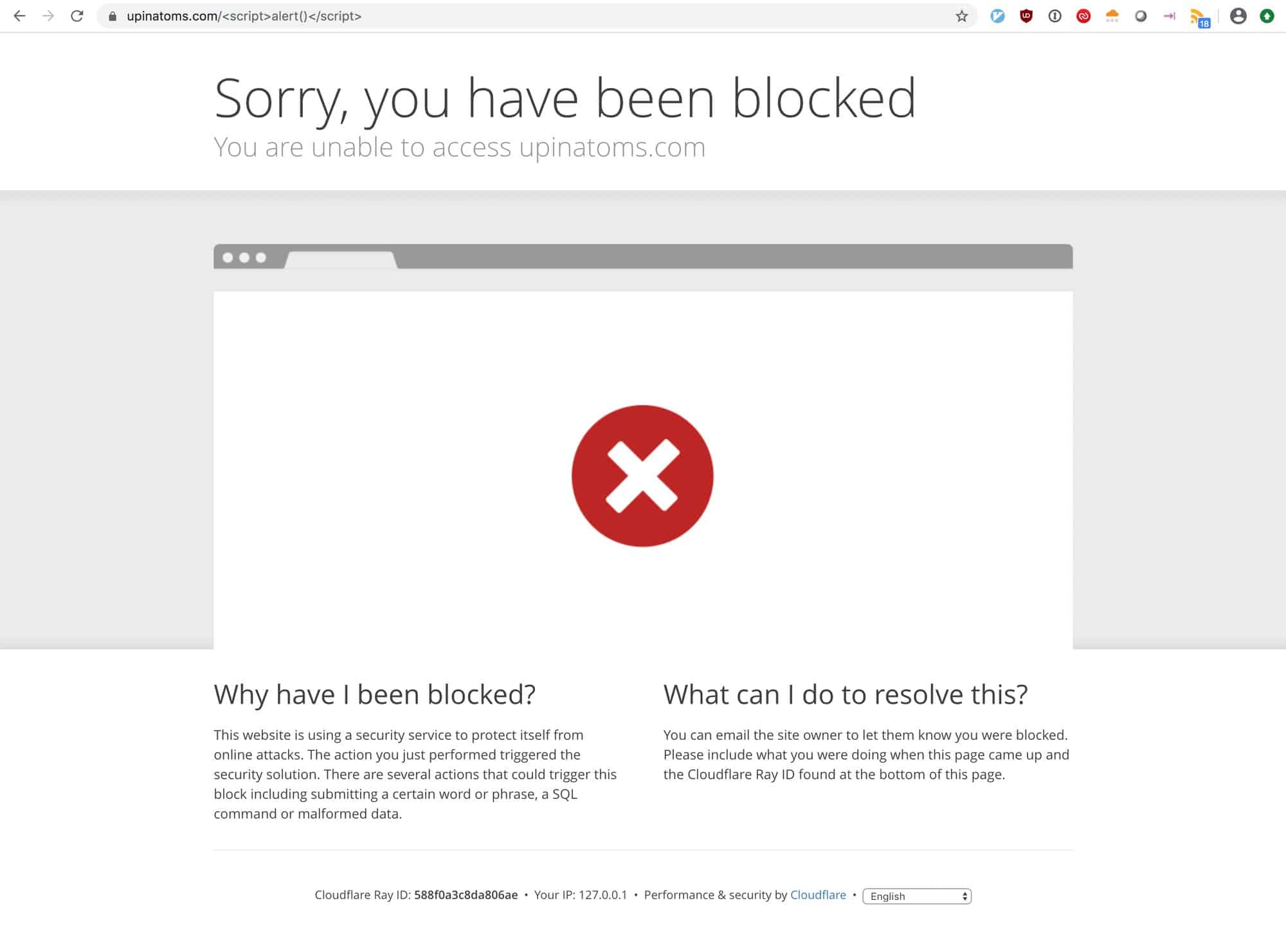
Cloudflare WAF is a cloud-based security solution that focuses on protecting your online services and applications through the creation of rules, policies, and restrictions.
Cloudflare, founded in 2009, has grown to become one of the most prominent names in web performance and security. Initially focused on providing content delivery network (CDN) services, Cloudflare has expanded its offerings to include a wide range of security solutions aimed at protecting websites, applications, and networks from various cyber threats.
One of the cornerstone products in the brand’s security portfolio is Cloudflare Web Application Firewall (WAF). This is a tool designed to protect websites from attacks such as SQL injection, cross-site scripting (XSS), and other common web vulnerabilities.
The Cloudflare WAF was introduced in 2014 as part of the company’s broader suite of security products. Since then, it has become an essential feature for businesses looking to safeguard their online presence from malicious traffic and cyberattacks. The WAF provides real-time protection by inspecting incoming traffic and filtering out harmful requests before they can reach the web server. This helps prevent potential breaches, reducing the risk of data loss, downtime, and reputational damage.
Cloudflare’s WAF is highly customizable, enabling users to tailor security rules to their specific needs. It integrates with other Cloudflare services, including DDoS protection and bot mitigation, providing a comprehensive security solution. The WAF also benefits from Cloudflare’s global network, ensuring low-latency protection across a vast number of data centers worldwide.
As of recent reports, Cloudflare generates a significant portion of its income from its security products, including the WAF. While the exact percentage fluctuates, it is estimated that around 40% of Cloudflare’s overall revenue comes from its suite of security services, which includes the Web Application Firewall.
The importance of security tool to the Cloudflare bottom line highlights the growing demand for web security solutions as cyber threats continue to evolve. Security awareness is solidifying Cloudflare WAF’s position as a critical tool for enterprises seeking robust protection against online vulnerabilities.
How Does Cloudflare WAF Work?
Implementing this type of WAF is beneficial, as you don’t need to make any existing changes to your application or environment. Rule-sets and policies created inside of Cloudflare WAF are designed to protect against attacks such as SQL injection, cross-site scripting, and file inclusion.
You can choose to select a pre-built rule-set or build your own custom set of policies that dictate how traffic interacts with your applications. Cloudflare leverages a distributed network that analyzes over one billion IP addresses and threat signatures across the globe.
The threat intelligence is categorized and assigned a threat score. This collection of threat information is shared among Cloudflare WAF users. This same data is used to increase the accuracy of managed rule-sets and share newly discovered zero-day vulnerabilities quickly with other engineers.
Everything you configure inside of Cloudflare WAF will either be a rule or a rule group. Depending on your needs and the complexity of your environment you can establish a hierarchy of rules and rule groups. This allows certain rule groups to always take priority over other rules.
Unlike open-source WAF solutions, Cloudflare has analytics and reporting built right into the platform and does not require further integrations or third-party tools. From the analytics dashboard, you’ll receive an overview of threats blocked, as well as a real-time and historical account of security events across your WAF.
Now that we’ve explored how Cloudflare WAF works, let’s dive into the setup process.
Setting Up Cloudflare WAF
I was pleasantly surprised at how well the activation and configuration process was streamlined. While similar cloud-based WAF tools can take hours to set up, activation and configuration only took about 30 minutes.
You start by creating a Cloudflare account and selecting your plan. Currently, there are four plans to choose from, and one of them is completely free. After your account has been created you’ll need to update your DNS to allow Cloudflare to manage it. This is a simple process that only requires the creation of a new MX and TXT record.
Optionally, you can transfer your domain to Cloudflare through Cloudflare Registrar, but if you’re happy with your current registrar there’s really no need to do this. A helpful wizard walks you through best practices and guides you through optional configuration settings that improve security and performance.
There are several security options that are pre-enabled that start protecting your services immediately.
DDoS Protection – Cloudflare works on the application layer to defend your domain against five of the most common attack types. This includes protection from HTTP, UPD, SYN, ACK, and QUIC flood attacks.
HTTPS Rewrites – Automatic rewrites help secure your site when there is a mix of secure and unsecured content. This service automatically rewrites HTTP content and links as an HTTPS source.
Email Address Obfuscation – Cloudflare deploys a service called Scrape Shield that automatically protects your email and domain from spammers. This hides elements on your site that scrapers and bots use to steal information and harvest your email address.
Settings such as enabling DNSSEC and turning on Hotlink Protection are two examples of how Cloudflare WAF aims to help improve your security, as much as your application performance. After you’ve navigated through about half a dozen configurations, you’ll be prompted to run a health check.
This health check tests your configuration and settings by scanning your domain and alerting you to problems. If something was missed, or misconfigured, the health checker will provide actionable steps to get those issues resolved.
Ease Of Use
Functionally you’ll find Cloudflare WAF to be one of the more intuitive and easy to use application firewall products. From the simple setup to the clean user interface, Cloudflare WAF feels responsive and less complicated than most alternatives.
Navigating through the WAF is simple. Large blue buttons at the top of the webpage allow you to toggle between DNS settings, speed insights, and security configurations. There is no complicated nesting of settings or buried menus.
When you select a section you want to work in, you can easily see what settings are enabled or disabled by glancing at large on/off slider buttons. This allows you to quickly glance across your rule groups or settings and see what is enabled. If something isn’t as it should be, you can simply turn that feature back on, or drill down into the configuration of that feature to make more detailed changes.
Pre-configured DDoS protection and other out-of-the-box security settings make implementation more streamlined and ultimately save you time on fewer settings you have to configure. Managed rule sets give you an excellent starting point for your WAF that immediately apply best practices developed by OWASP and Cloudflare.
Visualizing attempted attacks and security events can all be done from the Cloudflare dashboard and doesn’t require any additional add-ins like many open-source WAF products. Through the analytics dashboard, you can view security events in real-time and look back as far as 30 days.
While the dashboard isn’t modular, you can still filter your view by specific time ranges and firewall events. Below the main chart, you can view metrics such as top countries, most popular paths, and most frequently connected IP addresses.
This view helps you understand some similarities between threats and where they originate. At a glance, you can determine if you need to further tune a firewall rule to block a specific country, IP address, or service.
If your business utilizes other online platforms, Cloudflare WAF can integrate with a number of companies such as Google Cloud, Rackspace, Acquia, Microsoft Azure, and IBM. Depending on the platform you’re trying to integrate, you may be able to take advantage of Cloudflare’s extensive API.
Features
Let’s look into some of the key features that Cloudflare WAF has to offer. We’ll primarily focus on its security and firewall capabilities.
At the heart of Cloudflare’s security filtering are its managed and custom rule-sets. You can choose to utilize both managed and custom rule-sets at the same time if you wish. Although managed rule-sets are already configured, you still have the option to modify specific rules inside of those rule-sets.
When a rule is broken, a specific action is taken. Under managed rules, you can change this default action to disable, simulate, block, or challenge. Disable simply turns that rule off, while simulate allows that request through and logs it. Lastly setting a rule to challenge presents the user with a CAPTCHA.
This is something other WAF services such as AWS WAF do not allow you to do. This allows you a little bit more freedom when combining best practices alongside some of your own custom rules you need to implement. Cloudflare currently has around a dozen different rule-sets catering to multiple CMS systems such as WordPress, Magento, and Drupal.
The OWASP managed rule set operates a bit differently and works by assigning each event its own threat score. When a threat score number breaches a custom threshold, you can choose how your WAF interacts with that traffic.
You can choose the rule-set’s sensitivity and specify whether you want it set to high, medium, low, or just off completely. The OWASP rule-set will also have an action it defaults to when that threshold is broken; this too can be customized to your liking.
While managed rule-sets aren’t nearly as granular as configuring a custom set of rules, Cloudflare does an excellent job of giving you pre-configured options to choose from without feeling completely restricted. Let’s review how custom rules are set up with Cloudflare WAF.
Specifying your own custom rule is simple, especially if you’ve worked with object-based firewalls before. Under the Firewall Rule section, you’ll choose a field such as IP address from a drop-down list, specify an operator, and then input a value. As you build your rule through the interface the written expression is previewed directly below it.
Once your expression is written, you can choose an action, such as block or challenge. A feature I really enjoyed was the option to test the rule against events that have already occurred. This ensures that your rule is working against the event you’re looking to remediate before you hit publish.
Alternatively, you can run the rule in Log Mode and view how that rule would impact your traffic over time. After ensuring that no false positives occurred you can publish your rule change live.
Pricing
The four-tier pricing model makes Cloudflare WAF affordable for nearly all dev teams and businesses. Currently, Cloudflare has Free, Pro, Business, and Enterprise base packages that you can choose from. Their pricing combines base core features along with optional add-ons that increase your monthly cost by either a flat amount or by usage.
Some add-ons will cost more or less depending on what your base package is, and if that feature bills by usage. You’ll want to review what your WAF needs are to make sure you’re selecting the right base package.
It’s entirely possible that you may only need features covered in the Pro plan, with one or two a la carte features added on. Currently, the Pro plan starts at $20.00 (£15.19) per month and includes 20 firewall rules, CAPTCHA challenge, analytics, and API access.
When you compare Cloudflare WAF to similar products you’ll find that Cloudflare not only provides a completely free version for use but is also very competitive with its base package offerings and data usage fees.
Why Choose Cloudflare WAF?
Cloudflare provides a streamlined and flexible approach to securing your applications and services behind a cloud-based WAF. From setup to manual configuration Cloudflare WAF uses simple user design to make the entire process as smooth as possible.
While Cloudflare lacks a rule-set marketplace, it makes up for this with a wide variety of its own rules that you can be confident have been thoroughly tested by experts at Cloudflare. The ability to modify or turn off some managed rules within a rule set is a welcomed feature, as some WAFs don’t allow this level of flexibility.
Simple pricing that combines base packages and add-on features means you don’t have to spend hours calculating all of your usage metrics, and a free plan lets you get started completely commitment-free.
If you’re looking for your first WAF implementation, or have been frustrated by the limitations or complexity found with other firewall products, I’d highly suggest trying out Cloudflare WAF to test for yourself.
If you’re still in research mode, let’s take a look at a few alternatives to Cloudflare WAF and see how they stack up.
Cloudflare WAF Alternatives
If you’re still on the hunt for WAF products, we’ve got you covered. Be sure to check out our list of the best WAFs.
- AppTrana Managed Web Application Firewall (FREE TRIAL) This WAF solution comes with its own fully managed security team and features customized security policies, contractual SLAs, and 24×7 support. Start a 14-day free trial.
- F5 Advanced Web Application Firewall Utilizes proactive botnet defenses, behavioral analytics, and application-layer encryption to defend your services against threats, and secure communications between your ancillary systems.
- Barracuda Web Application Firewall Barracuda has three WAF offerings that provide adequate protection from threats and a host of automated remediation. Solutions include on-premises, cloud-based, and as a managed service.
- NGINX App Protect WAF Leverages automation to reduce costs and unclog bottlenecks that are commonly found in workflow rules. It features a suite of non-disruptive security controllers developers can use in DevOps environments.
Cloudflare WAF FAQs
What ports does Cloudflare WAF use?
Cloudflare uses the following HTTP ports:
- 80
- 8080
- 8880
- 2052
- 2082
- 2086
- 2095
And the following HTTPS ports:
- 443
- 2053
- 2083
- 2087
- 2096
- 8443
Is Cloudflare a CDN or WAF?
Cloudflare offers both a content delivery network (CDN) and a Web application firewall (WAF).
What does Cloudflare WAF protect against?
Cloudflare WAF protects against SQL injection attacks, cross-site scripting, cross-site forgery requests, DDoS attacks, HTTP vulnerabilities, and email spammers.