Businesses increasingly rely on cloud computing to store, manage, and process their data, ensuring the security of these systems has become paramount. Cloud environments offer unparalleled scalability, flexibility, and cost-efficiency, but they also come with unique security challenges. From protecting sensitive data against unauthorized access to mitigating threats like data breaches, misconfigurations, and cyberattacks, robust cloud security is no longer optional, it is a necessity.
Cloud security tools are designed to address these challenges, providing businesses with the ability to secure their infrastructure, data, and applications hosted on cloud platforms. These tools encompass a wide range of capabilities, including vulnerability management, threat detection, compliance monitoring, encryption, and access control. They are crucial for safeguarding assets in public, private, and hybrid cloud environments while also ensuring adherence to regulatory standards such as GDPR, HIPAA, or PCI DSS.
Choosing the right cloud security tools can be daunting, especially given the vast number of options available. Different tools cater to various needs, from securing multi-cloud environments to providing real-time alerts for potential threats. Some focus on automating compliance checks, while others specialize in protecting data through advanced encryption techniques.
In this guide, we delve into the best cloud security tools currently available, highlighting their key features, benefits, and use cases. Whether you’re a small business looking for straightforward solutions or a large enterprise managing complex, multi-cloud operations, this comprehensive overview will help you find the tools that fit your needs. With the right strategies and technologies, you can mitigate risks, protect critical assets, and confidently navigate the dynamic world of cloud computing.
Here’s our list of the best cloud security tools:
- Intruder EDITOR’S CHOICE An online vulnerability management solution that turns scanning into a continuous process for ongoing security monitoring and can cover cloud assets as well as on-premises systems. Get a 14-day free trial.
- ManageEngine Log360 Cloud (FREE TRIAL) This SaaS version of the on-premises Log360 is a SIEM that collects logs from on-premises systems and cloud services and analyzes them for threats. Access a 30-day free trial.
- Barracuda CloudGen Firewall Next-gen SaaS security system ideal for protecting complex distributed network architectures; identifies and protects against email, phishing, and policy non-compliance and also offers backup.
- Cloudflare Web Application Firewall Popular online protection service that keeps millions of websites safe and effectively connected; also protects networks by acting like a reverse-proxy, effectively preventing DDoS attacks.
- Cyscale This SaaS platform maps all cloud assets and provides both cost and security assessments, implementing better protection policies for processes and data.
- Datadog Cloud Security Management This SaaS package implements configuration checks on cloud assets. This is a like a vulnerability manager for cloud systems and it checks on other SaaS packages as well as platforms.
- PingSafe This CNAPP platform offers robust protection against potential cloud threats, effectively addressing challenges in multi-cloud infrastructures. It intelligently detects and prioritizes issues, automating their resolution to safeguard your cloud infrastructure from attackers.
- Hornetsecurity Spam and Malware Protection This package is a cloud-resident proxy for email traffic that scans text in email bodies for spam and masquerading as well as detecting malware in attachments.
- Vicarius Cloud security tool that collects data on assets and analyzes it to find threats and rank them according to their severity; applies Patchless Protection and in-memory protection to defend a network.
- Trend Cloud One – Workload Security Cloud-based defense system to protect workloads, network layers, and storage services; also serves as an antivirus, Intrusion Detection System (IDS), and vulnerability management system.
- Rubrik Ideal for complex network architectures this tool uses backups that are searchable for pin-pointed restoration as a way to protect data; it saves the backups securely so that even if it is breached, it is of no use to the intruders.
- Orca Security An agentless SaaS security tool for popular public cloud platforms (AWS, GCP, etc.); immediate discovery of assets across complex networks supporting multi-operating systems that are quickly assessed for ambiguities and, in case of issues, flagged for resolution.
- Splunk Enterprise Security Machine data analysis software platform that helps admins collect, analyze, and visualize data from digital assets in any network; can be further enhanced with modules for advanced detection and investigation of abnormal activity.
- Zscaler Suite of cloud-based security tools ideal for protecting users of on-demand software; can work as a gateway as well as a tunnel for private usage (better than a VPN), for an enhanced UX.
The evolution of cloud security
The cloud presents an opportunity for security system providers to cut costs by hosting their software and providing it to customers on the SaaS model. However, as more system creators make the same switch, security scanning becomes more complicated. A security tool no longer has the boundaries of a network to work within.
The first phase of cloud security development was to create tools that can monitor both on-premises and cloud-based systems. This strategy suits most businesses that now have to work with packages in both areas. So, there are now cloud-based SIEMs and XDRs that monitor on-premises systems and cloud packages. User access controls can be implemented by a Zero Trust Architecture (ZTA) and Cloud Infrastructure Entitlement Management (CIEM).
The proliferation of SaaS systems, mobile apps, and online services in websites means that there is now a large market for cloud security tools that provide protection for those systems. That is, security that is marketed to the owners of those cloud and Web systems rather than to their customers. This has created a new field of tools, which include Cloud Security Posture Management (CSPM), which is a cloud version of a vulnerability scanner, and Cloud Workload Protection Platforms, which provide anti-virus and intrusion detection for cloud systems. A bundle of these services is called a Cloud-Native Application Protection Platform (CNAPP).
Developers and operators of framework,s APIs, and other Web services needs Application Security Testing systems, commonly implemented as Static Application Security Testers (SAST) and Dynamic Application Security Testers (DAST).
The best Cloud Security Tools
Our methodology for selecting a cloud security system
We reviewed the market for cloud security tools and analyzed the options based on the following criteria:
- Cloud-based services that can cover hybrid systems
- Cloud workload protection services for virtual servers
- Cloud security posture management services for system hardening
- Multiple systems that are delivered from a common edge platform
- Alerts for security problems
- A free trial or a demo package for an assessment opportunity without risk
- Value for money, represented by an efficient edge service that is available at a fair price
Using this set of criteria, we looked for edge services that provide system protection for cloud-based and on-premises assets.
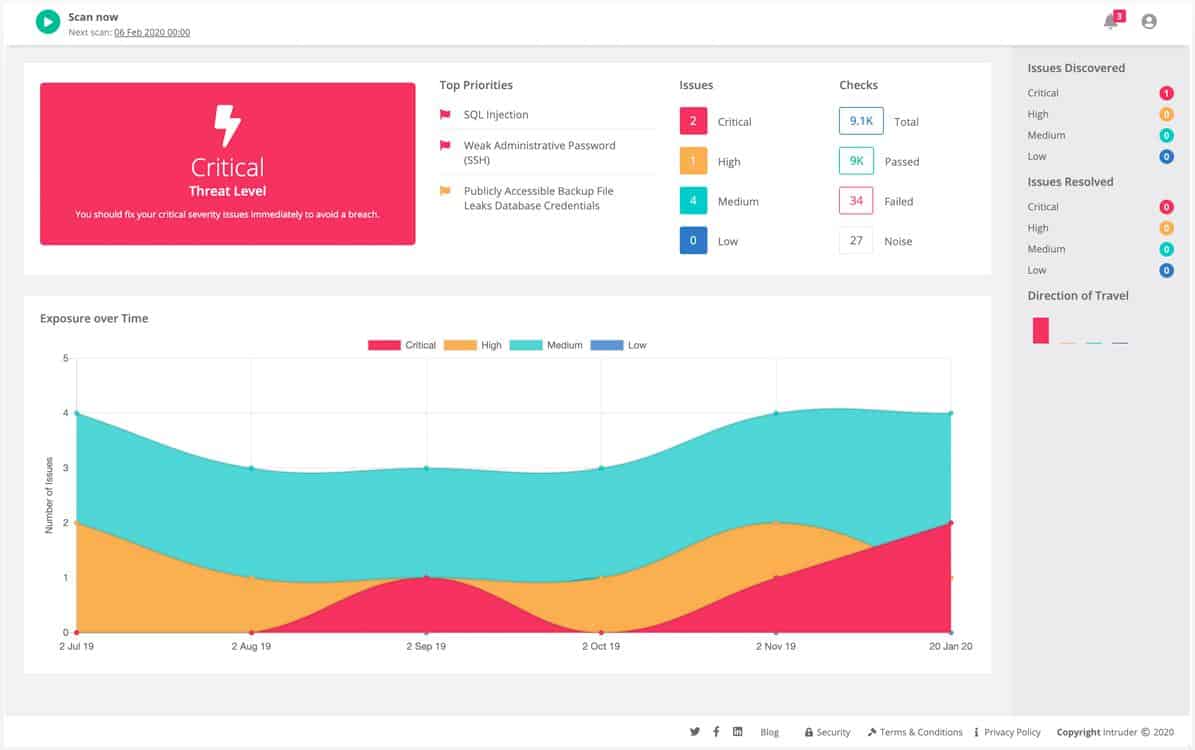
1. Intruder (FREE TRIAL)
Intruder is a cloud-based vulnerability scanner that can run continuously to provide ongoing security scanning. This service is able to scan cloud assets as well as networks. The system is offered in three levels of service and external scanning is included in all plans.
Key Features:
- Vulnerability Scanning: A hosted security system
- Attack Surface Scanning: Examines weaknesses from an external viewpoint
- Internal scanning: Available in higher plans
- Based on OpenVAS or Tenable Nessus: The underlying system depends on the chosen plan
- Seeks Known Vulnerabilities: Searches for the OWASP Top 10
Why do we recommend it?
Intruder provides vulnerability scanning for on-premises systems and cloud services from its own cloud-located server. This system extends the traditional system hardening mechanism for on-site assets to include cloud accounts as well. This vulnerability manager’s plans give you the option of external attack surface scanning or internal network vulnerability scanning.
Intruder leverages trusted third-party tools to enhance their vulnerability scanning capabilities. In the Essential plan, they utilize the powerful OpenVAS vulnerability scanner, while the Pro and Premium plans include the robust Tenable Nessus. These tools are seamlessly integrated into their service, allowing them to deliver advanced security measures. It’s worth mentioning that access to all their enhanced features is available in the top-tier plan.
As a comprehensive vulnerability management service, Intruder incorporates the expertise of experienced penetration testers in their package. While the scanning process is largely automated, the results are carefully curated by their dedicated team. With the Premium plan, customers benefit from increased involvement and support from the human pen testing team.
The scanning service provided by Intruder is designed to schedule scans for all registered assets. Additionally, users have the flexibility to manually launch scans according to their needs. Even with the Essential plan, unlimited manual scans are allowed. The Essential package includes scheduled scans once a month, while the Pro and Premium editions offer the option to schedule scans as frequently as desired, including continuous scanning.
Who is it recommended for?
This package is for use by businesses that are consumers of cloud services. While some cloud security systems, such as the Datadog service, are limited to securing cloud assets. The Intruder package covers both on-premises and cloud systems. This package examines how the users of software set up their configurations rather than how the producers of those systems design them.
Pros:
- Choice of Scan Frequency: Monthly or daily according to the plan
- Ad Hoc Scanning: Included in all plans
- Web Application Scanning: An add-on to any plan
- Cyber Hygiene Score: Summarizes security status
- Integrations: Slack, Gitlab, Github, and others
Cons:
- Monthly External Scans Might not be Sufficient: OpenVAS is also available for free
Intruder has a transparent pricing structure which is refreshing to see in comparison to some of its peers. If needed, their higher tier plans provide access to a team of pentesters, and their Essential and Pro tiers are fully automated and self-serve. You can assess Intruder with a 14-day free trial.
EDITOR'S CHOICE
Intruder stands out as our top pick for small business firewalls due to its comprehensive, cloud-based vulnerability scanning capabilities. This service offers continuous security scanning, which is crucial for ongoing protection. Intruder’s ability to scan both cloud assets and networks makes it highly versatile. The three-tiered service structure, including external scanning in all plans, provides scalability for businesses of varying sizes. What makes Intruder particularly appealing is its integration of trusted third-party tools like OpenVAS and Tenable Nessus, enhancing its scanning efficiency. This combination of automated scanning with expert oversight from experienced penetration testers ensures thorough vulnerability management. The flexibility in scheduling scans, including the option for unlimited manual scans even in the basic plan, adds to its user-friendliness and effectiveness.
Download: Get a 14-day free trial
Official Site: https://portal.intruder.io/free_trial
OS: Cloud-based
2. ManageEngine Log360 Cloud (FREE TRIAL)
ManageEngine Log360 Cloud is a cloud-based SIEM. This system can collect logs from assets on your site and also on cloud platforms. So, the tool will protect cloud systems with its threat detection service.
Key Features:
- Hybrid security monitoring: Tracks activity on your site and on the cloud systems that you use
- Shadow IT discovery: Lists the cloud systems that your users access
- Compliance management: Suitable for PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001
Why do we recommend it?
ManageEngine Log360 Cloud is a SIEM that is hosted on the cloud. This package is able to collect event logs from systems on your site and from cloud services. The package looks at the traffic leaving your site and discovers what cloud platform and SaaS packages your users are accessing.
This SIEM includes a log manager. This receives logs from active systems, including firewalls and gateways. So, it is able to record all of the connections that on-premises users make to cloud systems. The service provides administrators with a data analyzer that accesses the pool of activity data that is drawn from log messages.
The system’s log manager files log messages in meaningful directories and rotates files daily, making specific records easy to find. This is important for compliance auditing. The plans for Log360 Cloud include storage space for those log files.
Pros:
- Threat detection: The package includes pre-written searches for indicators of compromise
- User behavior analytics: Looks for insider threats
- Log file storage space included: More space with higher, more expensive plans
Cons:
- No extension for retention period: The log retention period for each plan is fixed
Each plan has a storage allowance and a retention period for logs. The storage capacity can be increased but the retention period can’t. You will need to organize a second cloud storage account and set up a routine to archive logs after this period. There is a Free edition that includes 50 GB of storage and a 15-day retention period. You can get a 30-day free trial to test the system.
3. Barracuda CloudGen Firewall
Barracuda CloudGen Firewall is a cloud-based, SaaS cloud security system. As a matter of fact, it is a next-generation collection of physical, virtual, and cloud-based appliances that protect and enhance the performance of a dispersed network infrastructure.
Key Features:
- Other Deployment Options: The Barracuda firewall is also available as a physical or virtual appliance
- Protection for Hybrid Systems: Covers on-premises and cloud-based assets
- Advanced Threat Protection: Blocks zero-day attacks, intrusion attempts, and malware
Why do we recommend it?
Barracuda CloudGen Firewall provides an intrusion detection system as well as a traffic scanner to block incoming malware. The service is hosted in the cloud and can be combined with other edge services from Barracuda. Traffic management and WAN optimization are among the other functions of this system.
It is a solution that can be used to optimize the performance of a distributed network; it is easy to scale across any device combination or distributed network infrastructure. It can also easily be administered from a single-window – regardless of the asset types on the network – where admins can configure their own sets of rules and policies, manage software patches and upgrades.
Barracuda offers many other products which means CloudGen can be integrated with them to extend the security cover and offer all-around protection of both software and hardware assets: email protection, secure backup, and AI-based protection from phishing attacks. There’s even a cloud scanner to check for security policy compliance.
Who is it recommended for?
This package is suitable for use by businesses that have a hybrid environment to protect. sites in front of your multiple networks and cloud services. This is a solution for large businesses and particularly those that need to field incoming requests for Web servers.
Pros:
- Network Access Controls: Implement microsegmentation
- Application Controls: Block specific applications per user or group
- SSL Offloading: Acts as an endpoint for encryption and so can scan packet contents in plan text
Cons:
- No Price List: you have to contact the Sales Department
This is a great cloud security tool for larger businesses that need to stay on top of the safety and connectivity of complex and dispersed network infrastructures.
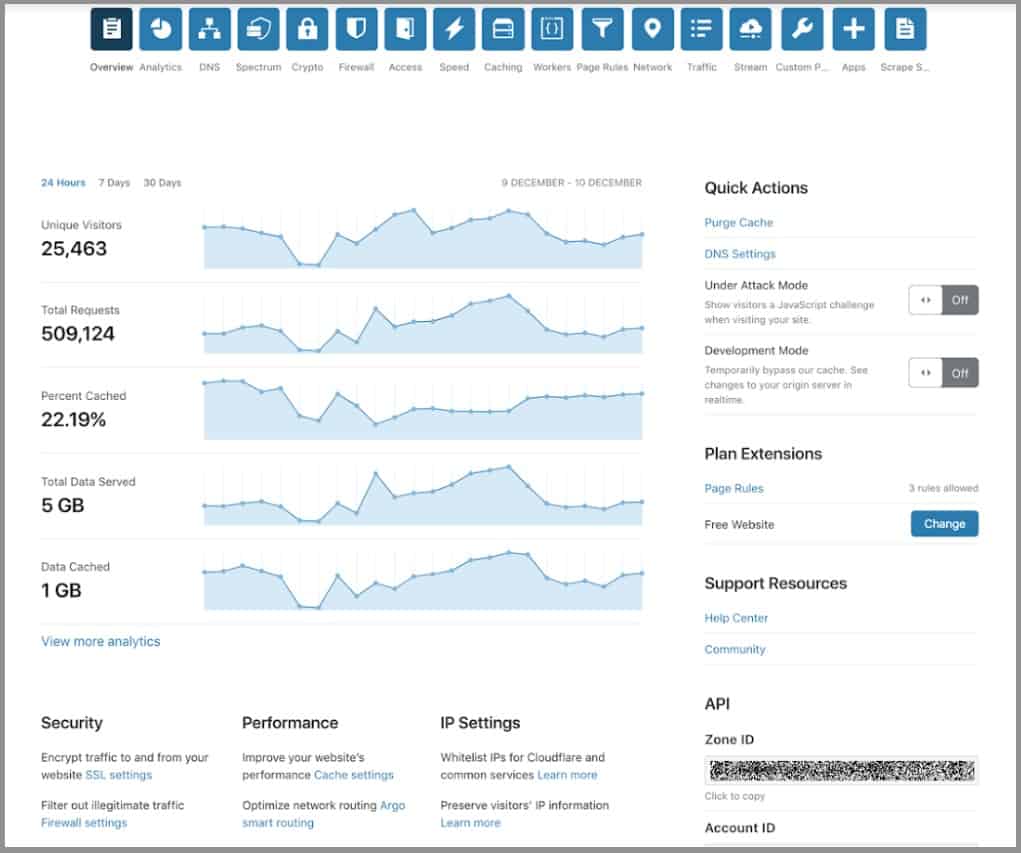
4. Cloudflare
Cloudflare is another company that offers popular and reliable cloud security tools that speed up and protect millions of websites, APIs, SaaS services, and devices connected to the Internet.
Key Features:
- DDoS Protection: All traffic passes through the Cloudflare server
- Malware Blocking: Also blocks ads and trackers
- Threat Intelligence Feed: Records know malicious websites
Why do we recommend it?
The Cloudflare system grew from a DDoS protection package. Now Cloudflare offers a range of services, which include a Web application firewall. The service operates as a vulnerability scanner for cloud-based assets as well as protecting them from malicious incoming traffic. Several edge services can be combined into one package.
It is a multi-purpose company that has been relied on to provide protection on anything from the cloud server and services to domain names and CMS installations.
Cloudflare’s Web Application Firewall (WAF) helps keep your websites and applications secure from OWASP Top Ten CMS vulnerabilities. It has more than 145 rules to protect from almost all types of web application attacks.
This is just one tool from the Cloudflare arsenal that helps protect whole infrastructures. The company runs one of the world’s largest networks – of more than 100 data centers, in 200 cities all over the world – that powers over 10 trillion requests a month. This is approximately 10 percent of all Internet requests, affecting more than 2.5 billion people globally.
Apart from security, Cloudflare helps accelerate the connection between online devices. It also secures and ensures the reliability of public-facing resources like websites, APIs, and cloud applications.
Who is it recommended for?
This service is accessible to businesses of all sizes. In fact, because of its marketing deals with Web hosting services, a very large number of startups and low-volume websites use the tool. The combination of CDN services, traffic optimization, DDoS protection, and WAF is also available for free.
Pros:
- Free Tier: Ideal for small businesses
- Content Delivery Network: Speeds up Web delivery
- DNS Filtering: Customizable URL blocking
Cons:
- The Presentation of Plans is Confusing: Pages of options
In the case of cloud infrastructures, Cloudflare increases connection security and reliability with features like a reverse proxy that performs load balancing, offers firewall capabilities, and provides protection from DDoS attacks.
Finally, Cloudflare also offers more services like CDN and DNS for free.
5. Cyscale
Cyscale maps cloud assets and provides assessments for their configurations and procedural security. This is a SaaS platform and it assesses other cloud platforms and SaaS systems as well as virtualization, databases, microservices, APIs, and frameworks.
Key Features:
- Easy to Set Up: Presents a console of controls
- Cloud Asset Discovery: Also creates a dependency map
- Cloud Security Posture Management (CSPM): Protection for cloud systems
- Data Security Dashboard: Measures data exposure risk
Why do we recommend it?
Cyscale offers a range of security tools to protect cloud-based systems that begin with an asset discovery routine that generates an inventory. Assets might extend to supplied, SaaS systems or APIs. These services include data loss prevention and configuration vulnerability scanning. The system provides remediation actions, constant attack monitoring, and compliance reporting features.
The Cyscale discovery process generates a Security Knowledge Graph. This accounts for security weaknesses that can occur between cloud assets not just within them. The Knowledge Graph exposes all of the subscriptions that a company has and identifies their utilization. This can reveal forgotten services that are no longer used and can be canceled. It also enables a business to save money by reducing reserve cloud capacity down to actual needs.
The security assessment service in Cyscale is based on a library of templates. There are more than 500 of these and they provide best practices for each type of cloud asset. The assessment scan produces a report of how the configuration of each asset deviates from the relevant standard of security. These checks can also be adapted to apply the requirements of specific data protection standards. The Cyscale system also locates data stores and provides recommendations for their protection.
The system provides a recommendation for each change that is needed to tighten security. Some of the assets that the system scans might be provided by a third-party. In these cases, security improvements will need to be implemented by negotiation with the provider or the replacement of a risky service with one that offers better security.
Who is it recommended for?
This package is particularly concerned with resolving the security weaknesses in cloud platforms, APIs, and Web assets. The service’s price is based on the volume of assets that need to be protected. This makes the service accessible to businesses of all sizes. It is particularly useful for compliance reporting.
Pros:
- Multiple Cloud Platforms: AWS, Google Cloud, Azure, and Alibaba Cloud
- Compliance Reporting: For GDPR, PCI DSS, HIPAA, NIST, and SOC 2
- Policy Enforcement: Calibrate system for compliance
- Option for MSSPs: Multi-tenant architecture
Cons:
- No Free Trial: A demo is available
The subscription for a Cyscale account is levied as an allowance of assets to be scanned. You can get derive an asset count by taking out the 14-day free trial of Cyscale.
6. Datadog Cloud Security Management
Datadog Cloud Security Management is a package of two units: the Cloud Security Posture Management service and the Cloud Workload Security system. The first of these is a preventative security system that looks for possible weaknesses in the configuration of your cloud assets. This is like a cloud version of vulnerability management. Once you subscribe to this service and list your cloud systems, it will continuously scan your services for weaknesses.
Key Features:
- Cloud Security Posture Management: Detects configuration weaknesses for system hardening
- Cloud Workload Protection Platform: Live security monitoring for cloud assets
- Compliance Auditing: Calibrates controls to specific standards
Why do we recommend it?
Datadog Cloud Security Management is at the cutting edge of the rapidly developing field of cloud security. It offers the main cloud system protection tools of Cloud Security Posture Management (CSPM) for exploit detection and system hardening, and a Cloud Workload Protection Platform (CWPP) for constant vigilance against malware and manual attacks.
The tool explores all of the cloud services that you register in the monitoring system and looks for components and related subscriptions. This generates a dependency map and then the system checks each of these units individually and as a group. The system looks at how these modules connect and exchange data, which could identify a point of security weakness.
The Cloud Workload Security module is the other package in the Cloud Security Management service. This option is a live security service, similar to an anti-malware package on a computer. So, you have two options – scan for vulnerabilities and look out for attacks.
The two packages of Cloud Security Management are not mutually exclusive – you can subscribe to both. Cloud platforms might serve different business departments and even have separate support times looking after them. The Datadog platform allows the administrator to set up multiple user accounts, so a collaborative effort can be facilitated to resolve security problems and threats.
Who is it recommended for?
Like any cloud security system, this package is of interest to businesses that manage SaaS platforms and services to other cloud system owners, such as frameworks and APIs. The system is useful for DevOps teams and particularly so if combined with the code profiling and distributed tracing functions of the Datadog APM package.
Pros:
- Cloud Infrastructure Entitlement Management (CIEM): An integrated access rights manager for cloud systems
- Kubernetes Security Posture Management: Protects containers
- Prioritized Notifications: Provides a list of problems that need to be fixed
Cons:
- Doesn’t Protect on Premises Systems: You will need to buy separate security products for your on-premises systems
The Datadog platform keeps evolving and adding on more services. The provider also offers a Cloud SIEM and it also has an Application Security Management Module that identifies threats to Web applications. You can try any and all of the Datadog services with a free trial.
7. PingSafe
PingSafe is a Cloud-native Application Protection Platform (CNAPP) that offers a comprehensive range of protection strategies within a unified package.
Key Features:
- Cloud System Hardening: Discovers misconfigurations
- Vulnerability Management: Continuous scanning
- Container and Kubernetes Security: Checks on application delivery mechanisms
Why do we recommend it?
PingSafe’s advanced secret scanning engine specializes in identifying over 800 types of secrets and cloud credentials in code repositories, ensuring comprehensive protection against data breaches and leakage.
The agentless nature of PingSafe enables a straightforward and immediate onboarding process, requiring only read-only access. This approach eliminates additional cloud costs and minimizes vulnerabilities associated with agent-based approaches.
PingSafe seamlessly integrates with various applications like Slack, Jira, Webhooks, PagerDuty, Splunk, and Sumo Logic, streamlining threat detection, reporting, and response automation. Users can receive real-time alerts via Slack or PagerDuty and analyze log records in Splunk for deeper insights.
Upon vulnerability detection, PingSafe generates detailed records in its cloud-based console, providing insights into the affected assets, identified weaknesses, and recommended remediation steps. While some vulnerabilities can be automatically remediated, others may require manual actions or policy changes.
Who do we recommend it for?
While many cloud security platforms are adaptable to Web application security testing, the PingSafe team doesn’t detail that option, so this isn’t a DevOps tool. Instead, with its cloud-agnostic and agentless approach, PingSafe caters to the security needs of organizations using AWS, GCP, Azure, and Digital Ocean, effectively addressing potential threats across multi-cloud infrastructure.
Pros:
- Infrastructure as Code Scanning: Ensure IaC has no security weaknesses
- Hacker Graph: A visual representation of system weaknesses
- Content Disarm and Reconstruction: Strips out suspicious elements in discovered documents, such as PDFs
Cons:
- No Price List: Also no free trial, but you can get a demo
For a more in-depth understanding of PingSafe’s capabilities, interested users can register for a free demo to explore the possibilities of this innovative Cloud-Native Application Protection Platform.
8. Hornetsecurity Spam and Malware Protection
Your email is a critical part of your corporate cloud system and Hornetsecurity Spam and Malware Protection is the perfect tool to keep your messaging system safe.
Key Features:
- Email Protection: Spots spam and phishing attempts
- DDoS Absorption: Protects mail servers against volumetric attacks
- Link Tracking: Scans target sites for infection and malware
Why do we recommend it?
Hornetsecurity Spam and Malware Protection is a cloud-based system that operates as a proxy for email traffic. This system pre-filters your incoming email traffic before it reaches your mail server. The system doesn’t just scan packets because it operates on text as well. This enables it to detect scams and spam as well as malware hidden in attachments.
Hornetsecurity Spam and Malware Protection, a tool created for small-to-medium businesses, is a cloud-based email security tool that offers protection that harnesses AI-powered filtering technology allowing it to act both as an antivirus as well as an anti-spam solution. Some of the threats that it can tackle include ransomware, zero-days, Business Email Compromise (BEC), spear phishing, and more.
Who is it recommended for?
Hornetsecurity markets the Spam and Malware Protection service for small and mid-sized businesses. An account is very easy to set up and doesn’t require any technical skills, so even owner-managed businesses that have no technical expertise on the staff can use this tool. Although it includes an outbound email filter, it doesn’t perform data loss prevention.
Pros:
- A Proxy Service: All email passes through the Hornetsecurity server for analysis
- Secure Connection: Validated emails are passed on over a VPN
- Outbound Email Scanning: Spots malware
Cons:
- No Price List: No free trial
Although it is highly effective in preventing attacks, it is also simple to use. And with it being a SaaS, there is nothing to install or update. Client’s just need to change their MX records and they are automatically protected; software updates and system support are handled by the engineers at Hornetsecurity Spam and Malware Protection.
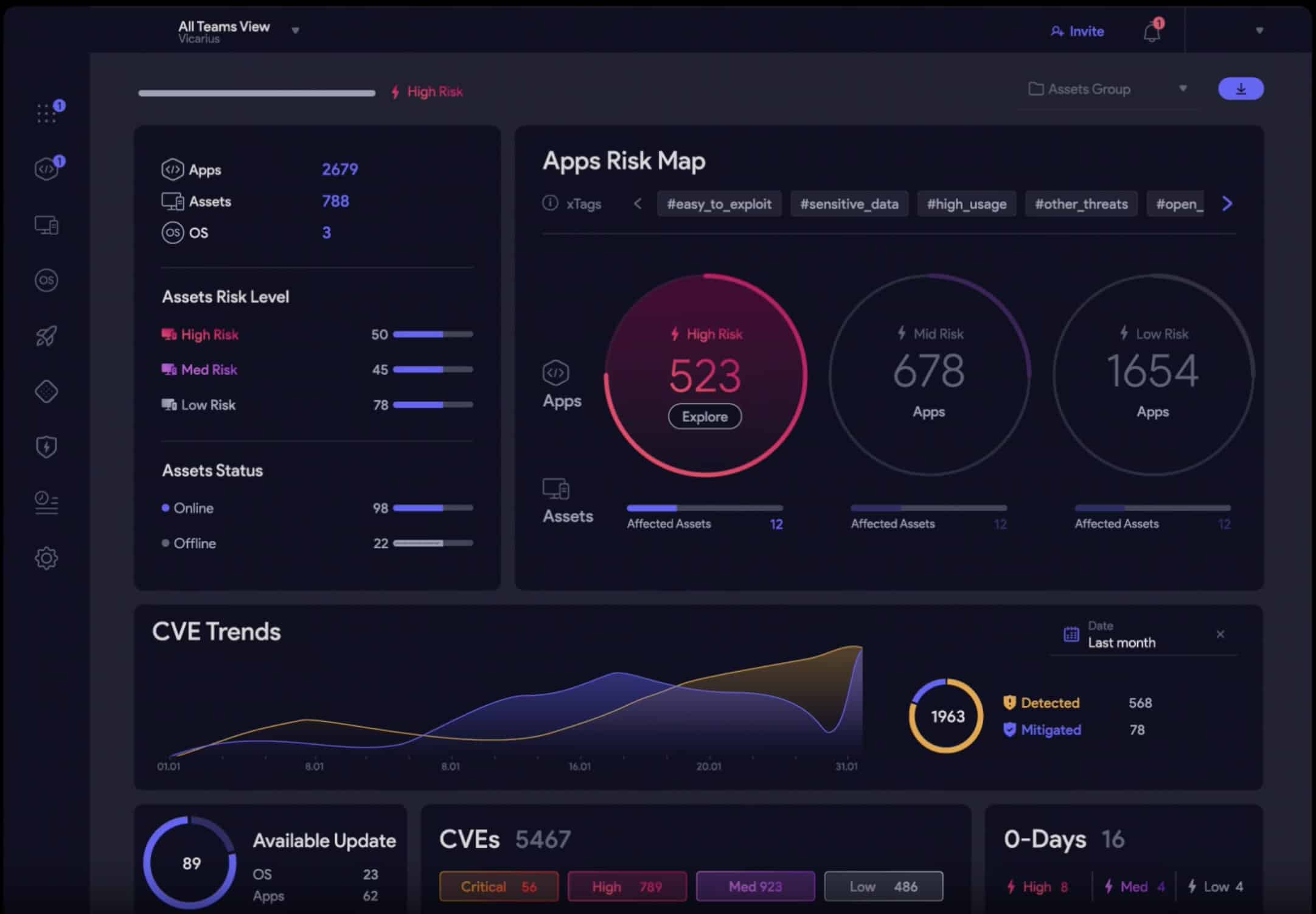
9. Vicarius
Vicarius is another innovative cloud security system that collects data across a digital infrastructure to recognize and mitigate vulnerabilities before they become threats. Businesses can use this vulnerability management software to detect, analyze, and remedy cybersecurity threats.
Key Features:
- A Vulnerability Scanner: Identifies security weaknesses
- Threat Analysis: Looks for hacker inroads
- Auto Remediation: Shuts down security loophole
Why do we recommend it?
Vicarius has an attractive and well-laid-out console, which makes this an easy-to-use and appealing security tool. The service is delivered from the cloud and there is also an option to get the software and host it on your own cloud account. The system includes an autodiscovery of on-premises and cloud assets and it then performs vulnerability scans.
Vicarius helps admins apply a consistent, comprehensive, and clear approach to identifying and resolving security threats and risks. The tool’s threat analyzer helps to show a business’ assets’ threat levels and then offers recommendations for treating or handling the most critical of them.
This tool also offers real-time patch management to make sure your tech environment is current and up-to-date. In case there are no patches, Vicarius’ Patchless Protection takes care of the assets on the network by surrounding it in a defensive dome over the most vulnerable assets with the help of in-memory protection.
Add to this the fact that Vicarius has an amazing GUI which offers a pleasant user experience (UX) means that, apart from practicality, it is a pleasure to work with as admins can easily see any threats and effectively respond to them. They can control their whole domain, in real-time, and have a comprehensive inventory of all the active workstations and servers at their disposal.
Admins can, therefore, focus on reducing vulnerabilities with the help of real-time contextual app vulnerability and asset-risk analysis combinations. These map the whole digital infrastructure for easier prediction, detection, prioritization, and handling of issues.
Who is it recommended for?
This package is a good choice for mid-sized and large organizations that operate hybrid environments. There is also a free tool that integrates with the free Nmap tool. The Nmap system is well-known as a site network discovery package, so this edition isn’t suitable as a cloud security tool.
Pros:
- Virtual Patching: Protects vulnerable software for which patches are not available
- Script Library: You can also add your own
- Hybrid Protection: Also protects on-premises systems
Cons:
- Not All Editions Cover Cloud Assets: The free edition is for network protection
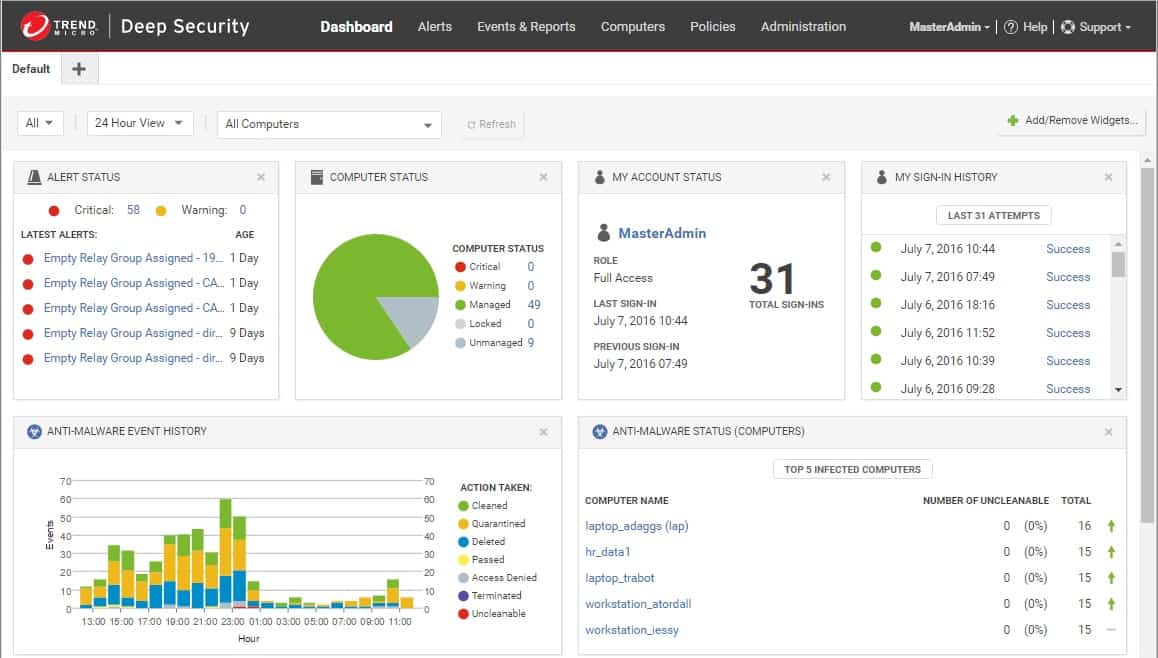
10. Trend Cloud One – Workload Security
Trend Cloud One – Workload Security formerly Deep Security, the new name for Deep Security, is a cloud-based threat defense system against vulnerabilities, malware, and unauthorized access.
Key Features:
- Hybrid Protection: Security for on-premises servers as well as cloud platforms
- Vulnerability Scanning: Spots weaknesses before attacks happen
- Firewall Functions: Scans traffic coming into the network
Why do we recommend it?
Trend Cloud One provides workload security, which is a vulnerability manager for cloud systems. This service is a cloud platform of modules that examine the security of different types of cloud assets, such as storage, containers, and applications. It is also possible to add on network security to and through your site and endpoint security.
This all-inclusive security service offers protection features like runtime security for workloads (physical, virtual, cloud, and containers), cloud network layer security, serverless security, and security for cloud file and object storage services.
This is all done from a single dashboard that combines capabilities with full visibility into popular environments like Google Cloud, Azure, IBM Cloud, VMware, and AWS.
Workload Security lowers the cost and complexity of securing workloads across multiple environments and virtually shields servers from the latest advanced threats like ransomware and network-based vulnerabilities.
It can actually protect systems from previously unknown threats thanks to its machine learning and virtual patching capabilities.
Now, although this is a tool with advanced capabilities, it is still a cloud-based SaaS which means it has a small digital footprint – all that is needed to get things rolling is to install a single smart agent. That is all it takes to start protecting the architecture against vulnerabilities or ensuring policy compliance.
Other features protect against threats by acting as an Intrusion Detection System (IDS), antivirus, and vulnerability management system.
Who is it recommended for?
This package is suitable for hybrid systems. A certain volume of usage for each module is free each month, so small businesses could get away without paying anything for the service. You don’t have to subscribe to the entire platform. Instead, you chose each module, which has its own charge rate.
Pros:
- Scans for Unexpected Configuration Changes: Alerts on possible hacker activity
- A Threat Intelligence Feed: Produces a blacklist of domains and IP addresses
- Zero Day Detection: Looks for anomalous behavior
Cons:
- Provides Value to Companies with Multiple Cloud Services: Small businesses that access one cloud platform wouldn’t get the most value from the package
11. Rubrik
Sometimes, no matter how hard you try to protect your data, you will find that it just isn’t enough. And sometimes, disaster does strike and you lose your data.
But, that doesn’t mean you have to close shop and slink away into oblivion. On the contrary, you should have a backup and restore system that you can rely on to protect your data and have you back on your feet again in the shortest amount of time – regardless of the amount of data lost.
Key Features:
- Cloud Security Posture Management: Discovers security weaknesses before hackers do
- Backup and Recovery: Protection for cloud-stored data
- Mirrored Backup Repositories: Immutable storage
Why do we recommend it?
Rubrik is a cloud platform that offers a range of services to protect other cloud systems. The backup and recovery services is just one of the options on this evolving platform that also enables the implementation of Zero Trust Architecture, sensitive data protection, and threat detection.
Rubrik offers such a solution: it backs up and recovers data center and cloud data and features automatic recovery from failure. It has in-depth reporting capabilities and it is also highly scalable.
With the help of this tool, businesses can manage their backup, have access to on-demand restoration, and guarantee a secure data storage system – everything they need to ensure business continuity.
Administrators can search and recover the precise data that is needed, instead of having to restore the whole database. There is no need to be concerned about data loss or theft because Rubrik protects the data from ransomware attacks – even after it has been stored in backup – with the help of immutable storage.
Rubrik also makes it easy for backup and recovery processes in a hybrid cloud environment. In fact, it can be used to get rid of complex, legacy backup/restore processes – that don’t even guarantee recovery. Instead, this tool replaces them with a software solution that bridges legacy and next-gen applications.
Who is it recommended for?
This platform is rapidly evolving and keeps adding new services. This makes the system difficult to keep up with and it is becoming too complicated for small businesses to manage. You need an experienced cybersecurity expert to fully implement a data protection system with this system or, at least, a well-schooled system administrator.
Pros:
- Options for Backing up On-Premises Data: Look at the Enterprise Data Protection service
- Data Threat Analysis: Identifies risks to data
- Threat Hunting: Live security monitoring with anomaly detection
Cons:
- No Price List: You have to contact the Sales Department to find out how much this service costs
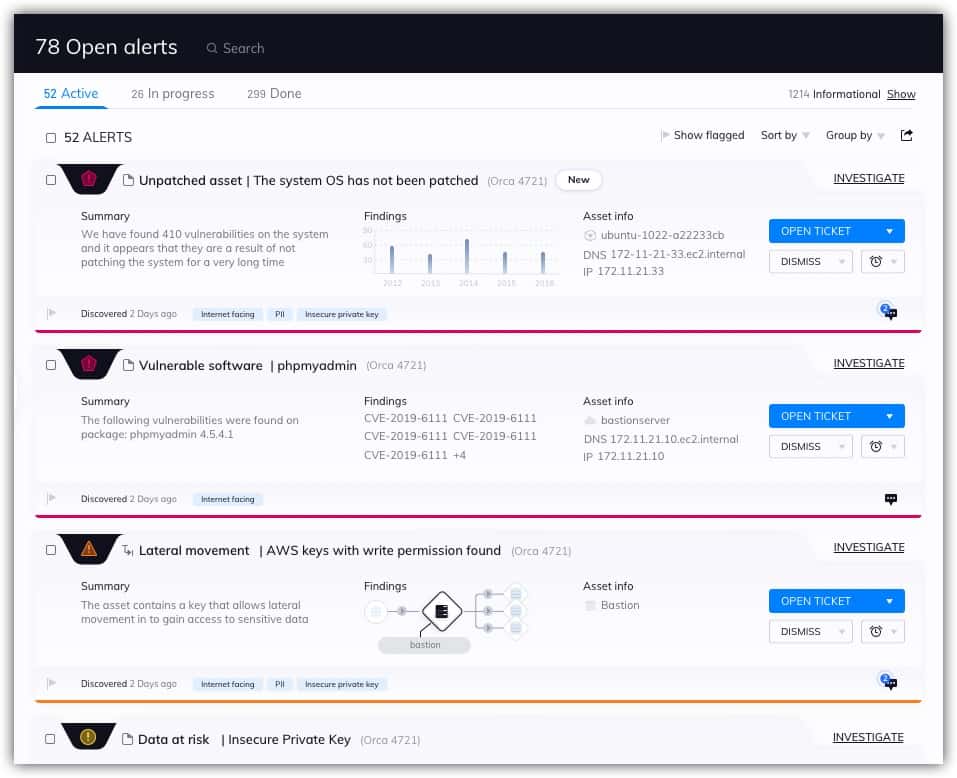
12. Orca Security
Orca Security is a SaaS tool that delivers in-depth visibility into AWS, Azure, and GCP. It replaces legacy vulnerability assessment tools, Cloud Security Posture Management (CSPM), and Cloud Workload Protection Platforms (CWPP).
Key Features:
- Protection for Cloud Platforms: AWS, Azure, Alibaba Cloud, and Google Cloud Platform
- Sensitive Data Protection: Discovers, categorizes, and maps personally identifiable information
- Cloud Security Posture Management (CSPM): Preventative security scanning
Why do we recommend it?
Orca Cloud Security Platform provides vulnerability scanning for cloud systems provided by AWS, Azure, Alibaba Cloud, and Google Cloud Platform. It can also scan Kubernetes containers. The service isn’t an occasional on-demand scanner – it handles the alerts that your cloud services emit and organizes them into a prioritized list.
This is a completely agentless tool and requires no installation. It involves a simple three-step process to connect and account and start discovery, monitoring, and assessing all cloud assets, regardless of platform, network, or operating system. Even paused or stopped machines are discovered.
Once connected, Orca scans a read-only view of cloud assets that includes cloud configuration, operating systems, applications, and data. The tool then detects vulnerabilities, malware, misconfigurations, lateral movement risk, weak (or leaked) passwords, and high-risk data such as Personally Identifiable Information (PII). Once the vulnerability information is compiled it is then prioritized based on the risk it poses.
This tool is an ideal tool for large enterprises as well as “born in the cloud” companies in industries such as SaaS, FinTech, Internet, media, ad tech, and pure-cloud service delivery.
Orca treats a cloud network as an interconnected web of assets. Should it find any ambiguities or errors, it can be configured to push informative alerts to Slack (or any other third-party collaboration platform where the admins hang out) and include each alert’s precise path or triggering point to help with a quick resolution.
Who is it recommended for?
This service doesn’t cover all cloud platforms. For example, there is no mention of Oracle Cloud or SaaS systems, such as Salesforce or Microsoft 365. The platform offers a number of modules and you will need to understand cybersecurity terminology in order to pick the right services for your business.
Pros:
- Integrations: Okta, Datadog, Slack, and others
- Live Security Monitoring: Looks for anomalous behavior on cloud platforms
- Insider Threat Detection: Analyzes data access by account holders
Cons:
- No Price List: You have to contact the Sales Department
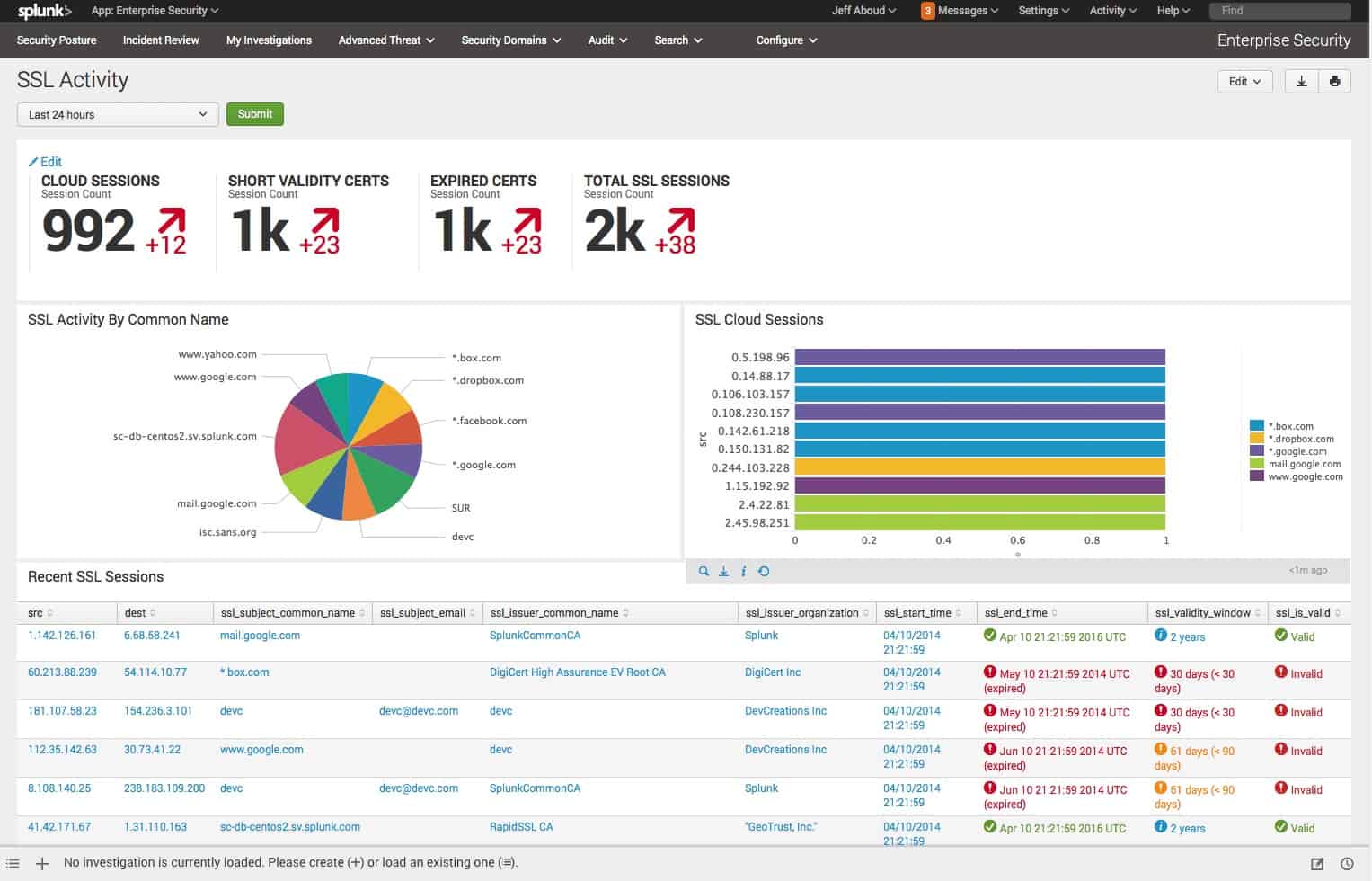
13. Splunk Enterprise Security
Splunk Enterprise Security is a software platform for machine data analysis that enables customers to gather real-time Operational Intelligence on their digital investment.
Key Features:
- On-Premises Software: A cloud-based version is also available
- A SIEM Service: Reads through activity logs
- False-Positive Alerting Reduction: Risk-based alerting
Why do we recommend it?
Splunk Enterprise Security is a SIEM tool and is one module in a platform of security systems that can be hosted on your server or accessed on a cloud platform. This package collects log messages from all of your assets and searches through them for threats. The service can extract status logs from cloud platforms.
This security tool enables admins to search, analyze, and visualize the data gathered from all components of an IT infrastructure including data from websites, applications, sensors, devices, and more which it then stores in a searchable format.
Splunk is an analytics-driven Security Incident and Event Management (SIEM) solution that uses actionable intelligence and advanced analytics to combat threats. It detects, investigates, and responds to these threats in real-time allowing for secure and no-risk operations.
Splunk Enterprise Security consists of a group of security modules known as the Splunk Security Operations Suite which includes two other packages – Splunk User Behavior Analytics, which draws on user and entity behavior analytics to stop as-of-yet unknown threats and Splunk Phantom, a tool to automate and coordinate the subsequent responses to them.
Splunk is the security platform that enables admins to perfect their security operations and reduce associated risks. From this platform, they can streamline their entire security stack, minimize unplanned downtime, and explore and visualize business processes for increased transparency.
The information that is gathered includes machine data from multi-cloud or on-premises installations that are displayed in one unified view for a quicker response. Admins can then quickly and effectively resolve the issues.
An interesting feature from Splunk is the Advanced Threat Investigation which uses advanced detection and investigative controls to detect and investigate abnormal activity that is usually associated with compromised systems.
Who is it recommended for?
This package is one option for businesses that are looking for SIEM solutions. There are other SIMs on the market and you should assess the Splunk option alongside other candidates. One of the signature features of the Splunk service is that is able to process large volumes of data very quickly.
Pros:
- User and Entity Behavior Analytics: Looks for unusual behavior per user account and per endpoint
- Options for Customization: Add to the rules base with your own detection rules
- Opportunities for Automated Remediation: Set up playbooks to shut down suspicious accounts
Cons:
- Complicated Pricing: You have to contact the Sales Department for a quote
14. Zscaler
With Zscaler we have a comprehensive suite of security services that are also delivered from the cloud. It is the ideal tool for protecting users who use cloud applications as would be the case in clients of an On-Demand Software service provider.
Key Features:
- A Menu of Edge Services: All modules operate from the cloud
- Creates a Virtual WAN: Secures connections between users and cloud services
- Firewall Service: Block malware and intruders from getting cloud to your cloud assets
Why do we recommend it?
Zscaler provides a toolkit of security measures that can be assembled in different combinations to provide different security strategies. It hottest option at the moment is the creation of a Zero Trust Access system. You can also implement SASE with this service.
Businesses that use this tool can protect their users by routing Internet traffic through the Zscaler Security Cloud, which is distributed across more than 100 data centers worldwide. The company’s direct-to-cloud architecture connects users to the nearest data center for an overall faster UX.
This method also cuts costs for their clients because they don’t need to purchase and manage their own network security software or devices.
One of the company’s two main services is Zscaler Internet Access (ZIA), which acts as a gateway between users and the Internet. ZIA securely connects users to externally managed applications – be they applications or Internet hosts, and regardless of device, location, or network.
The ZIA service also inspects encrypted and unencrypted Internet traffic in-line, looking for malware and advanced threats while also helping prevent corporate data leakage.
The other service, Zscaler Private Access (ZPA), offers authorized users with fast and secure access to internally managed applications hosted in enterprise data centers or in the cloud. Unlike a Virtual Private Network (VPN), which is used to connect users to a corporate network, ZPA connects a user to an application without involving the network, resulting in more secure connectivity.
Who is it recommended for?
Zscaler is affordable and accessible for any size of business. However, it doesn’t provide a single out-of-the-box security solution and you have to know a thing or two about cybersecurity and networking in order to get the most out of the platform.
Pros:
- Access Rights Management: System access accounts flow through to application access
- SSL Offloading: Enables the firewall to unpack and inspect packet contents
- Traffic Management: Offers WAN optimization
Cons:
- A Complicated Solution: This package is best suited for multi-site hybrid networks that also have remorse workers
Choosing a cloud security tool
While keeping the security of a cloud computing architecture can be done using several applications to take care of endpoints, servers, and networks, we can all agree the best solution would be one that covered the entire setup from end to end.
With that in mind, we can say Trend Cloud One – Workload Security is the best of the best cloud security tool with Splunk Enterprise Security and Orca Security following close behind.
Cloud security tools FAQs
What are security issues related to using cloud-based file management tools?
There are two main security issues when working with cloud-based file management tools: protection for data at rest and protection for data in motion. The files held on your cloud server didn’t originate there. Even if your cloud service includes productivity tools to create the files, there will still be a transfer of characters from the creator’s computer to the cloud server. So, if a user types the contents of the file, the connection between the user’s device and the cloud server needs to be encrypted and remote access to the server needs thorough authentication. If the file is created locally and then transferred to the cloud server, the same level of protection also needs to be applied. The files stored on the cloud server need to be protected with encryption to control access and the people allowed access should be identifiable with secure credentials.
What are the four areas of cloud security?
One definition of cloud security defines four areas to consider — other theorists define three or even five categories. The four areas are:
- Visibility and compliance – Know where everything is and what its value or sensitivity is
- Compute-based security – This is provided by vulnerability management and a SIEM
- Network protection – Firewall-as-a-Service, Secure Access Service Edge (SASE), or Zero Trust Access
- Identity security – Identity and access management (IAM)