Burp Suite is one of the most popular and powerful tools for web application security testing, used by security professionals, penetration testers, and developers to identify vulnerabilities and weaknesses in web applications. Known for its versatility and rich feature set, Burp Suite offers a comprehensive suite of tools designed to assist in various aspects of security testing, from web application scanning to manual inspection and exploitation of vulnerabilities.
Whether you’re assessing a website for potential risks or actively working to secure your application, Burp Suite provides everything you need to conduct thorough security assessments. One of the key advantages of Burp Suite is its user-friendly interface, which simplifies complex security testing tasks. The suite integrates tools such as a web spider, intruder, repeater, and a vulnerability scanner to provide complete control over web application testing.
Burp Suite is widely used to discover common vulnerabilities such as cross-site scripting (XSS), SQL injection, security misconfigurations, and more.
There are three editions for Burp Suite: Enterprise, Professional, and Community. The Community Edition is completely free to use.
While the Community Edition offers a more limited set of features compared to the Professional version, it is still a highly capable tool for smaller-scale web security testing. It includes core features like the proxy, repeater, and intruder, allowing users to perform manual testing, intercept requests, and exploit vulnerabilities. This makes it an ideal starting point for individuals or small teams who want to explore web application security without the need for a paid license.
In this guide, we’ll walk you through the key features of Burp Suite, focusing on the Community edition, and provide instructions on how to use the tool effectively for web application security testing. Whether you are a beginner or an experienced security tester, this guide will help you get the most out of Burp Suite for identifying and mitigating web application vulnerabilities.
In this guide, we will be looking at the free tools in the Community Edition and how you can use them to check on the security of your websites. There are many attacks on businesses that hackers can implement by infecting websites. There are also several backdoors into your Web server that can allow hackers in. The aim of Burp Suite Community Edition tools is to enable you to act like a hacker and try to damage your system. By this strategy, you can identify security weaknesses and eradicate them before hackers spot them and compromise your system.
Penetration Testing
The difference between penetration testing and vulnerability scanning is that penetration testing is performed manually, whereas vulnerability scanning is automated. However, the two security testing strategies look for the same problems. So, if you don’t have the time to perform penetration testing, you might be better off opting for a vulnerability scanner.
In-house penetration testing can be ineffective. This is because the owners or managers of websites aren’t usually prepared to go as far as real-life hackers in damaging their systems. The guiding strategy behind penetration testing is that it should emulate the actions of a real hacker. A hacker is prepared to go to any lengths to break a target, but proprietors are more likely to shy away from heavy tactics, preferring to excuse weaknesses rather than expose them.
Penetration testing is more effective if performed by external, experienced consultants. However, those professional pen-testers are expensive, and few businesses can afford their services regularly. Frequent checks on potential security weaknesses are cost-effective if they are performed in-house. However, periodic external tests are worth investing in to check whether your sts actually caught all vulnerabilities.
Burp Suite Community Edition
There aren’t many tools included in the Community Edition. However, there are enough there for you to get familiar with the concept of penetration testing. Once you have established a testing strategy, you might want to move up to the Professional Edition, which provides many more tools for manual testing and also some testing automation systems.
Burp Suite includes a Web browser, which is already set up for testing. This is easier to use than a regular browser. However, if you don’t want to switch to the included browser, it is possible to use any other. The browser offers a WebSockets proxy, and it retains test history. The Community Edition package consists of a repeater, a sequencer, a decoder, and a comparer. There is also a demo version of Burp Intruder in the pack.
Burp Suite Community Edition system requirements
The Burp Suite system for all editions will install on Windows, macOS, and Linux. The critical issue is that the host computer needs to have Java Runtime Environment (JRE) 1.7 or later (64-bit edition).
The computer needs at least 4 GB of memory, but it is recommended that it should have 8 GB, mainly if you think you might end up upgrading to the Professional Edition. The computer also needs two CPU cores. Finally, the installation takes up 286 MB of disk space.
Install Burp Suite Community Edition
To get Burp Suite Community Edition running on your computer, follow these steps:
- Go to the Burp Suite Community Edition download page and click on the Download button. This takes you to another page.
- Select your operating system and click on the Download button.
- Click on the downloaded file to run the installer.
- Follow the instructions in the download wizard, cycling through each page by pressing the Next button.
Running Burp Suite Community Edition
The installation ends by creating an entry in your Start menu and an icon on the Desktop. Click on either to open the program. You will be presented with a Terms and Conditions statement. Click I Accept to open the application.
The running of tests is called a project in Burp Suite. You can only save a test plan and open it through the Burp Suite interface with the Professional edition. With the Community Edition, you just run a test from scratch. However, as you are still learning about the “projects” concept, you are unlikely to have any test plans saved anyway. Therefore, your only option in the opening screen is the Temporary project. Press the Next button to get started.
The next screen allows you to set a configuration for the test. This feature is tricky with the Community Edition because it will only load settings related to a project, and you can’t restore a project from a file. So, it is better to just stick with the option to Use Burp defaults. Then, press the Start Burp button to begin testing.
The system runs a range of tests and then opens up the Burp Suite Dashboard, showing test results. The Issue activity side of the Dashboard is just a demo. You can’t direct this utility to one of your sites. It just shows issues with sample sites that Burp Suite set up for demonstration purposes. In short, the Issue activity feature isn’t of any use to those running the Community Edition. As that is the main feature of the Dashboard tab, you won’t get much helpful information out of this part of the interface.
View Web traffic with Burp Suite
The Proxy tab in the Burp Suite interface is the main engine for activities using the Community Edition. It lets you see all of the traffic that passes between your Web browser and the servers for your visit sites.
There are options to narrow down the sites that are reported on. However, this is only an issue if you use your regular Web browser for tests. If you use the built-in browser, you will only get reports on traffic to that browser. Any activity you perform in your particular regular browser simultaneously won’t get reported in Burp Suite. This strategy drastically simplifies your management of information in Burp Suite.
The Proxy tab includes four sub-tabs. These are:
- Intercept
- HTTP history
- WebSocket history
- Options
These are the areas where you capture traffic used in other sections of the Burp Suite service.
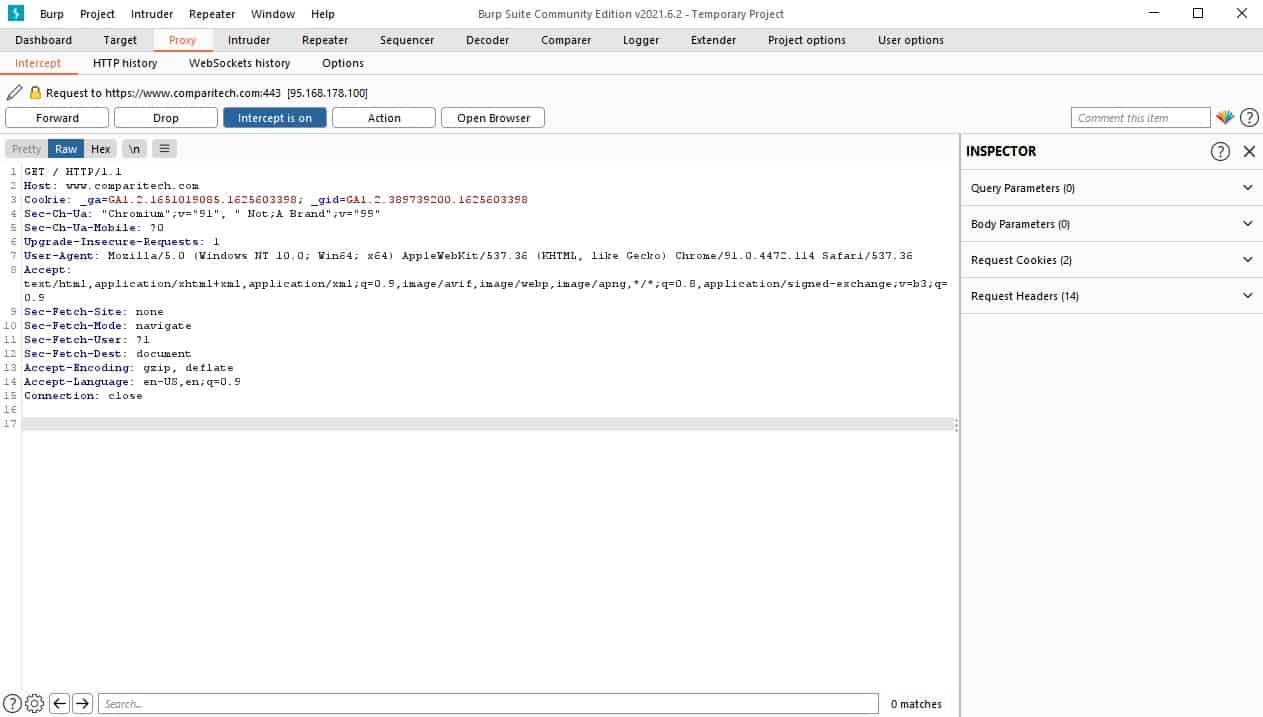
The Intercept service
When you click on the Intercept sub-tab, you will see four buttons. These are:
- Forward
- Drop
- Intercept is on
- Action
- Open Browser
The body of this screen shows several information panels. The first of these encourage you to open the built-in browser. As the purpose of this screen is to show traffic between the browser and a Web server, you aren’t going to get anything useful in it until you open a browser and access a Web page. Click on one of the two Open Browser buttons on the screen.
The Burp Suite Browser will open in a new window, but the Intercept screen in the console won’t change. You need to go to a Web page to get things to happen. We can use the Comparitech website as an example. This is at comparitech.com.
Enter compritech.com in the browser’s search bar – use the address of your website if you prefer.
You won’t see any movement in the web browser. The “working” indicator will just circle slowly. The Intercept system blocks the request and response conversations that go into building up a Web page in a browser. You have to step through these requests.
Go back to the Burp Suite console, and you will see that it has changed. The information panels have gone, and instead, you will see the request that the test browser sent to the Web server. The next step is jammed to enable you to examine this information.
There are actions that you can perform at this point with the request information shown on the screen. To see the complete list, click on the Action button. You will know that you can copy the details of this request into other functions in the Burp Suite service. However, hold off on that right now because you will get the opportunity to see both the request and the response in another section of the Proxy tab. Right now, you are just looking at each request live as it goes to the Web server. These steps are also saved, and you can see them all in a table later.
Avoid using the Open Browser button again – this will open another instance in another window rather than taking you to the browser you already have open. If you want to switch back to the browser you are working with, use the functions of your computer, such as Alt-TAB, instead.
To advance the page request process, press the Forward button. This allows the next step to progress. Switching back to the browser, you will see the requested Web page load as you continue to step through the requests with the Forward button.
When the Web page is fully loaded, the main panel of the Intercept screen will be blank. This is because you have captured all of the traffic passed back and forth between the browser and the Web server to access the page. Further actions that you perform on the page loaded into the browser will be reflected in the Intercept screen.
HTTP history
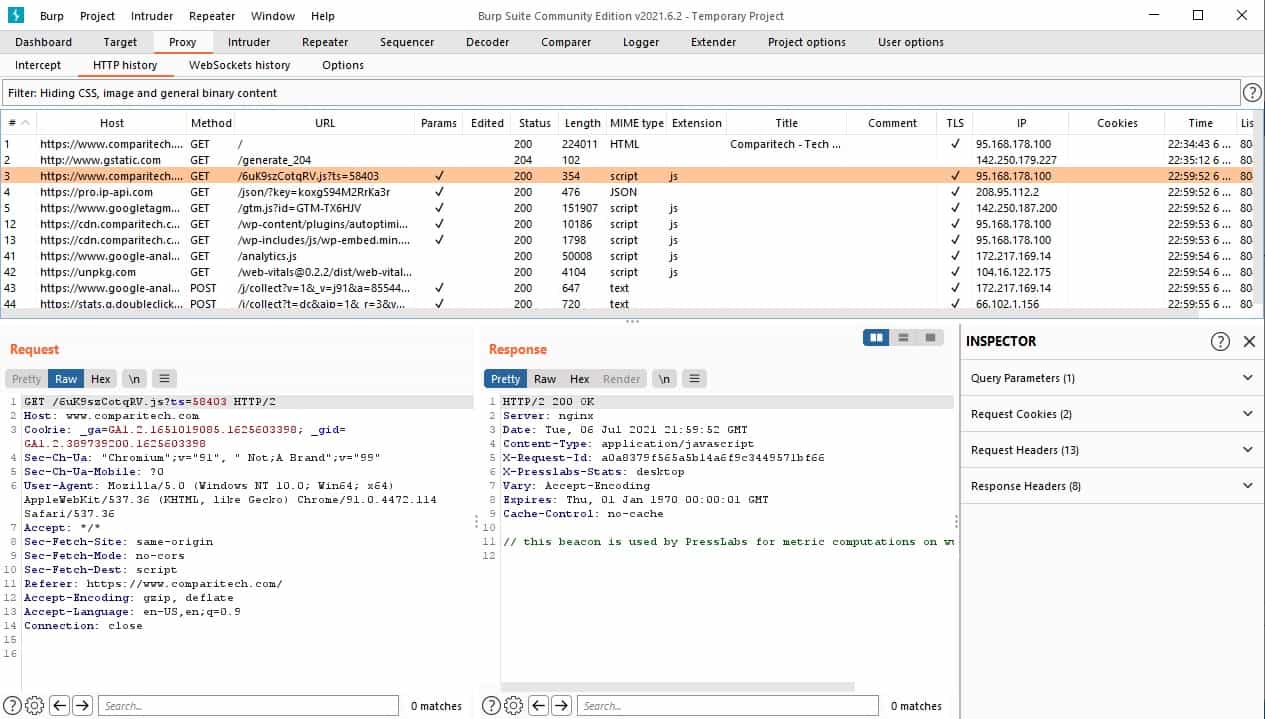
The second sub-tab under the Proxy tab is HTTP history. This is where you can look back at those transactions that you stepped through in the Intercept sub-tab.
Click on the HTTP history sub-tab. All of the transactions are listed in a table at the top of the screen. Click on any line to see details.
The most exciting Request/Response pair you could find in these records is those that pass user account credentials. If you find such a line, you can start to act like a hacker and launch your penetration testing attacks.
Launching an attack
Right-click on a line in the HTTP history list that has a login post in it. The context menu should appear, and you can click on Send to Intruder to get this data transferred over to one of the attack tools.
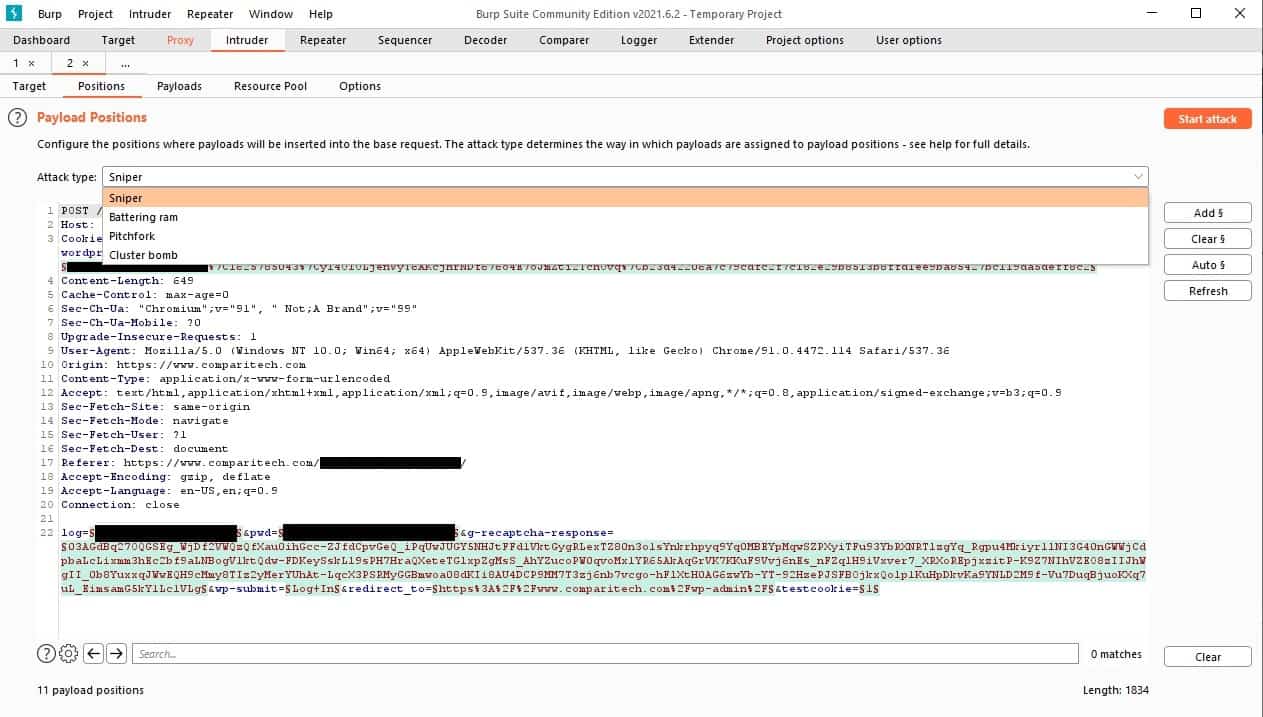
As soon as you send data to the Intruder, the Intruder tab in the top menu strap will turn red. Click on this tab. The data from the request that you selected in the HTTP history screen will already be there in the Positions sub-tab. The Intruder will highlight pertinent data in green. These will become the payload of the attack, and the sections highlighted are the “positions” or tracts of information to use in the attempts. The contents of the request are in plain text and not encrypted, so if you captured a log-in action, the process of breaking in like a hacker should be pretty straightforward. It should be noted, however, that penetration testing is rarely that easy.
The Intruder offers four attack strategies:
- Sniper – Uses one set of payloads and inserts each value into each position in turn. This is used for fuzzing, such as, you know a particular matter is needed but not which field it should go in.
- Battering ram – Duplicates each payload, places the same value in all positions at once, and then tries the next value. This is used where the exact value is expected to coordinate in several places in a form, such as a username being required for several inputs and expected to conform.
- Pitchfork – Uses multiple payloads and lets you decide which set of values to use per position. Useful for cycling through corresponding candidate values for a range of input fields simultaneously.
- Cluster bomb – Uses multiple payload sets with one set assigned to each input field and using every permutation of combinations of values for all sets. A large number of sets and a large number of values in each set can result in this attack taking a long time to complete.
The Cluster bomb attack is probably the best strategy for guessing access credentials. For example, set the Attack type field to Cluster bomb and clear the Burp Suite positions marked out. Next, look through your data and find a user name field. Highlight it and click the Add button. Next, look for the password field, highlight it and press the Add button.
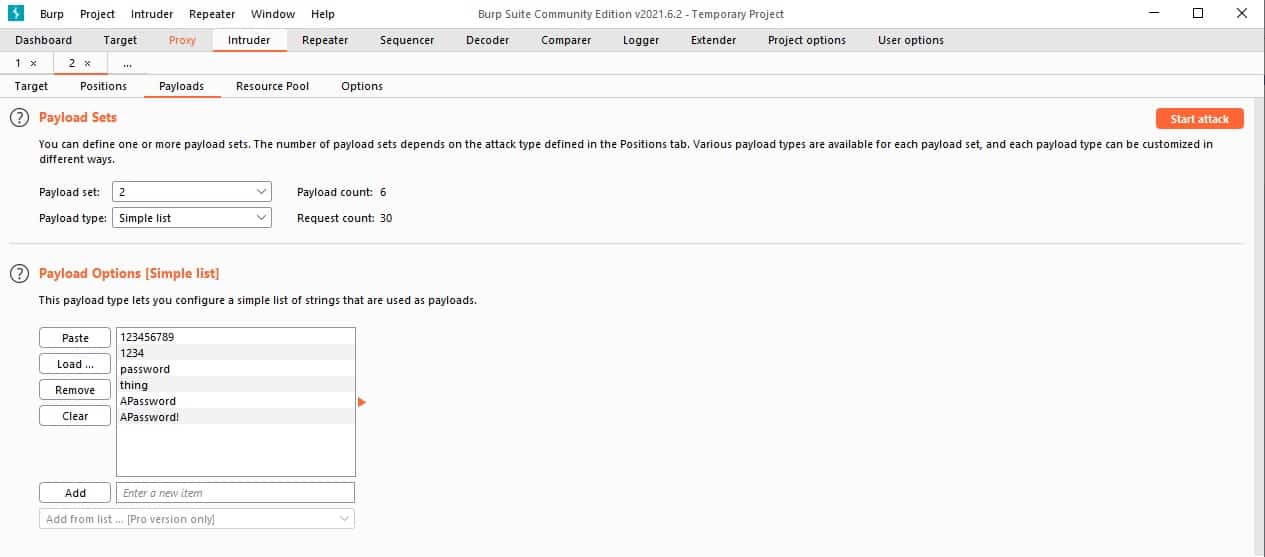
Switch to the Payloads sub-tab. Select 1 for the Payload set – this refers to the username field. The Payload Type field has many options—select Simple list.
In the data entry field at the bottom of the Payloads Options panel. Type in a typical user name, such as admin or guest. Press the Add button next to the field. Repeat this until you have about six possible values in your list.
Go back to the Payload set drop-down list and select 2. Then, enter a list of possible passwords in the Payload Options list.
Don’t put too many values in each set for each run. There will be many possible user names and passwords that you might want to try. However, it is better to execute combinations in sections so that you can get results quicker.
Press the Start attack button.
The system will work through all possible combinations of the values in the two lists. You can watch each attempt in the Results window that opens up. You will know if one of the combinations is correct by looking at the Length field.
The length referred to in this field is the number of bytes in the response. Each system has a different message for login success or failure. However, you can be sure that most of your attempts will fail and have the same number in the Length field. That tells you the number of bytes in the failed login attempt message. If one of the attempts has a different value in the Length field, that will be the correct username and password combination.
Explore Burp Suite
The capabilities of the Community Edition of Burp Suite are limited. For example, to get any value out of the vulnerability scanning capabilities of the Dashboard tab, you need to upgrade to the Professional Edition. However, there are several manual attack strategies that you can implement with the Community Edition.
If you decide to upgrade to the Professional Edition, you can get it on a 30-day free trial.
Burp Suite FAQs
What is Burp Suite for?
Burp Suite is a penetration testing tool. The package is delivered through a GUI app that provides a section on system research and another that launches attacks. The interface will copy over data from a research probe directly into an attack tool. A higher plan of Burp suite is fully automated, which makes it a vulnerability scanner.
Do hackers use Burp Suite?
Burp Suite was designed as a penetration testing framework. It enables testers to break into systems. Naturally, these services are also attractive to real hackers. The use of Burp Suite by hackers shows that it remains a sharp tool that is beneficial for ethical hackers. If hackers didn’t use it, that would indicate that there are better tools that penetration testers should use instead of Burp Suite.
Is Burp an open-source?
Burp Suite is a proprietary system and it is not an open-source project. There is a free version of the tool as well as the full, paid edition.