XDR stands for Extended Detection and Response. It is an advanced version of endpoint detection and response (EDR) that pulls in other security tools and coordinates everything from the cloud.
Here is our list of the best XDR tools:
- Barracuda Managed XDR EDITOR’S CHOICE This cloud-based system remotely monitors your sites for security threats and constitutes a full Security Operations Center (SOC) with 24-hour attendance by cybersecurity experts. Access a demo.
- ESET Protect MDR This is a Managed Detection and Response service that provides a SaaS XDR and also the staff to run the system and take appropriate action.
- Palo Alto Cortex XDR The definitive XDR system from the company that coined the phrase.
- LogRhythm SIEM A NextGen SIEM combined with UEBA and SOAR is a largely cloud-based system.
- CrowdStrike Falcon Combines onsite modules and SaaS systems in a unified security platform.
- UnderDefense MAXI Platform This platform is a security operations center that companies without their own cybersecurity experts can contract in to run security software for them.
- Rapid7 Insight Platform A combination of on-site and cloud-based tools that compose an XDR.
- TrendMicro XDR A cloud-based SIEM that coordinates with on-site security services from that same vendor, including email security.
- Exabeam A SaaS SIEM system that interfaces to on-site agents.
- ImmuniWeb A cloud-based vulnerability management suite that blends together to form an XDR.
- Cynet XDR Platform This platform uses AI routines and provides a high degree of threat resolution automation in its cloud-based services.
While system coordination occurs on the cloud, detection and remediation actions need to be implemented by on-site modules. The extent to which research gets refined before it is sent to the cloud depends on the design decisions made by each vendor of XDR systems.
The interplay between detection speed and processing efficiency influences how much of an XDR is based onsite and how much is centralized in the cloud. Competing businesses need to offer attractive prices and centralized SaaS-based components bring costs down. However, a remote system that can be cut off from networks under attack is no use to anyone, no matter how cheap it is. So, XDRs are never entirely cloud-based.
Elements of an XDR
An XDR is a platform – it is composed of a range of modules that work together. These are:
- Data collection which could be adapted from an EDR.
- Threat hunting which could be a SIEM, a vulnerability manager, or both.
- User and Entity Behavior Analytics (UEBA) to rule out false-positive reporting.
- Security Orchestration, Automation, and Response (SOAR) for threat mitigation.
Some providers offer these modules as individual products as well as bundled services
The best XDR platforms
Our methodology for selecting XDR systems
We reviewed the market for XDR tools and analyzed the options based on the following criteria:
- A cloud-based system that can monitor multiple sites
- Options to include remote work-from-home devices in monitoring
- User and entity behavior analytics for activity baselining
- Detection of anomalous activity
- Automated threat remediation functions
- A free trial or a demo to enable a no-obligation assessment before buying
- Value for money from a system that provides full security monitoring at a reasonable price
All of these products are SaaS-based, which is one of the defining characteristics of an XDR system. You can read more about these tools in the following sections.
1. Barracuda Managed XDR (ACCESS DEMO)
Barracuda Managed XDR is a managed security service opportunity for MSPs. This service delivers a team of security experts as well as SaaS-based XDR software. This is a managed service for managed service providers.
Key Features:
- Includes All Security Software: The team also manages that software for you
- Includes Hardware to Run Security Systems: Both processors and storage space
- Secure Connections: Both for data collection and dashboard access
- 24-Hour Monitoring: Based at a remote location
- Cybersecurity Experts: Included in the price
Why do we recommend it?
Barracuda Managed XDR extends the XDR platform by adding on the security staff to run the system and analyze security alerts. Barracuda runs its own Security Operations Center and subscribing businesses get coverage for their entire site added to the duty roster of this team.
The Security Operation Center (SOC) of Barracuda MSP will implement threat detection for your enrolled clients, allowing you to add a new product to your service menu without needing to source hard-to-find security experts. The system provides MSPs with a dashboard that allows you full visibility into your customers’ environments. Otherwise, all security-related support is supplied by Barracuda.
The system is a SIEM tool with automated responses. When one of your clients signs up for the Barracuda service, they are enrolled into the self-service dashboard. This guides the installation of data collectors that will upload log files to the Barracuda platform. The Barracuda system consolidates those logs while making them available to the AI-based SIEM system for security scanning.
The SIEM operates on a speedy triage basis, looking for anomalous behavior and then locking in tracking for the accounts and devices that were involved in that event. The service won’t raise a threat alert right away. Instead, it continues to scan incoming logs, looking for the next expected action that would mark out an intrusion.
This system uses generic rules, so it isn’t reliant on a signature database or even a set pattern of indicators of compromise. This makes the Barracuda XDR able to spot zero-day attacks.
Not all attacks are easy to spot and insider threats are particularly difficult to define. This is why an effective threat detection system needs the occasional input of human analysts. While many threats are clear, tricky hackers can sometimes evade detection and so the human eye is called in for borderline threat identification. Similarly, automated responses can be fine-tuned to prevent legitimate user activity from being shut down.
Who is it recommended for?
This package is marketed only to managed service providers. In this case, MSPs act as agents for Barracuda because the SOC is not intended to manage the XDR for the MSP but for its clients. So, MSPs can market security services and then let Barracuda deliver them.
Pros:
- Designed with Managed Service Providers in Mind: Protects subscribing MSP clients
- Includes a Self Service Portal: Will reduce the number of support tickets that you get
- Highly Visual: Displays data at scale well
- Adjustable Settings: Includes various alert and reporting templates
- Best Suited for MSPs and Enterprise Companies: Particularly those in locations with few cybersecurity experts available
Cons:
- No Price List: Request a quote
You can access a demo to find out more about the XDR.
EDITOR'S CHOICE
Barracuda Managed XDR is the perfect security solution for businesses that can’t locate sufficiently qualified staff to run their security monitoring systems. The right people to solve problems for businesses that don’t have their own qualified IT staff are managed service providers and the Barracuda system is part of a suite of systems aimed at MSPs. This managed SOC can be offered by the MSP to their clients as a pass-through service. IT could also be a useful service for use by MSPs to guard their own systems because a security breach at an MSP’s facilities would be very damaging to that service’s business prospects.
Download: Access a demo
Official Site: https://www.barracudamsp.com/products/xdr/managed-xdr-demo
OS: Cloud based
2. ESET Protect MDR
ESET Protect MDR is a managed security service that provides an account with the ESET Protect SaaS cybersecurity system plus the technicians to run the service for you. You still get to see the console for the security package and you can extract data for other purposes, such as capacity planning.
Key Features:
- Managed Service: Provides cybersecurity technicians
- On-Device Protection: A local scanner
- Central Threat Hunting: Run from a remote location
Why do we recommend it?
The ESET Protect MDR is a managed security service that provides system hardening services as well as ongoing security protection. This is a complete security operation service that protects endpoints, networks, and system services, synch as email. The package also protects cloud-based applications.
ESET offers its Protect range in a number of editions. The base package gives you an anti-virus system that needs to be installed on each device. This software is available for Windows, Linux, macOS, iOS, and Android. Each instance sends activity reports to a cloud-based controller. Higher plans use that uploaded data for threat detection and the top plan will automatically send response instructions to all equipment on the site.
The ESET Protect Complete plan gives you an XDR that covers on-site systems and cloud services. This system sends response instructions to ESET units. The top plan, ESET Protect Elite can send automated response instructions to third-party systems as well.
Even though you might buy a cybersecurity package that automatically shuts down threats, you still need a cybersecurity expert to manage it. If you don’t have such a person, you are the ideal customer for the ESET Protect MDR system.
The top plans of ESET Protect don’t just detect threats, they also scan for system vulnerabilities. The package will fix some of those weaknesses with a patch manager or issue guidance on what system changes need to be made. You need experts to implement these changes and those tasks form part of the duties of the ESET Protect MDR staff.
Who is it recommended for?
This cloud-based service covers on-premises and cloud services, so it is ideal for businesses that run hybrid systems. The package includes cybersecurity technicians to run the security software, so the deal is particularly interesting for businesses that are in locations where security specialists are hard to find.
Pros:
- Security Operations Center for Hire: Great for companies that can’t find security staff to hire
- XDR and Vulnerability Management Software: Included in the package
- Cloud Host and Storage: Priced in with the service
Cons:
- No Free Trial for the MDR Add-On: You can get a free trial for the ESET Protect software
The MDR system is a technician add-on service to your choice of ESET Protect plan, so there isn’t a free trial for this system. You need to contact ESET to discuss your requirements.
3. Palo Alto Cortex XDR
The term “XDR” was defined by Palo Alto Networks in 2018. As the inventor of the industry, Palo Alto can certainly be assumed to have got the right combination of tools to compose the definitive XDR service.
Key Features:
- A Cloud-Based System: Includes hosting and storage
- UEBA: Looks for insider threats
- Threat Intelligence: Focuses threat detection
Why do we recommend it?
Palo Alto Cortex XDR follows the typical XDR format of gathering activity data from local cybersecurity tools and consolidating that data in the cloud for threat hunting. The service will implement automated responses by sending instructions to those on-site tools. The Cortex system will work with third-party cybersecurity packages, so the local systems don’t have to be from Palo Alto.
Each security software provider arrived at the XDR target from a different starting point. The Palo Alto journey to XDR started with evolved onsite security products, such as an EDR to replace endpoint antivirus and a Next-Generation Firewall to protect the network. Palo Alto also offers a virtual firewall – which is a SaaS service, based in the cloud, effectively creating a virtual network. This can protect your own cloud-based services, such as virtual servers provided by the likes of AWS or Azure.
Palo Alto Networks created its Cortex XDR to tie each of these services together into a coordinated cybersecurity service. This is the essence of XDR, a SaaS console that presents an overview of security elements and, behind the scenes, unites the information feed from each to provide a consolidated data lake for threat hunting.
The threat detection system that is the core service provided by Cortex uses UEBA and triage to cut through to pertinent data. As it operates on the servers, of the Palo Alto Networks servers, this system gets instant threat intelligence feeds and also benefits from the zero-day experiences of security processes operating for other Cortex customers.
Cortex speeds up threat mitigation through SOAR, lightening the code base on-site by interfacing to services that are already present on-site, such as Active Directory (AD) and the firewall.
The elements of the XDR platform, such as the next-generation firewall, can all be deployed independently, so getting the XDR plan is a matter of buying a service bundle.
Who is it recommended for?
This is a solution for large businesses that will get extra value from their existing security software. The Palo Alto brand is top-of-the-line and is priced accordingly. The company doesn’t provide a price list and there is no free erosion and those two factors mean that it won’t appeal to small businesses.
Pros:
- Great User Interface: Easy-to-use reporting features
- Manages Coordinated Cybersec: Provided as a SaaS platform
- SOAR Functions: Reduces mitigation time
Cons:
- Too Much for Smaller Businesses: Better suited for enterprises
Palo Alto Cortex XDR is a leading pick for an XDR solution because the XDR term was invented to describe it. This system has all of the indicators of a classic XDR. It is a SaaS coordinator of onsite protection measures and it uses already installed services to direct responses to attack. The cloud module pools attack experience from all customers and injects threat intelligence developed at the same data center. UEBA and AI processes complete the combination of services that thread together into a coordinated defense platform.
4. LogRhythm SIEM
LogRhythm SIEM operates as an XDR because it gathers log messages from third-party on-site systems through an agent. This data is standardized into a common pool of records on the LogRhythm cloud server and forms the source material for threat detection.
Key Features:
- A SaaS Package: Pay a subscription
- Log Management and a Network Activity Feed: Blends HIDS and NIDS methods
- UEBA: Identifies insider threats
Why do we recommend it?
LogRhythm SIEM provides a core package with extra units that you can choose to add on. The extra modules include network detection and response, user and entity behavior analytics, and security orchestration, automation, and response (SOAR). Although this tool is entitled a SIEM, its activities also define it as an XDR.
The SIEM will implement threat detection and response. Those functions can be enhanced by add-on modules. The first of these is the LogRhythm UEBA, which records user activity and transactions per endpoint or remote identity. The tool uses ML to establish a baseline of regular activity and then alerts when it identifies deviations from that standard.
LogRhythm NDR stands for Network Detection and Response. This adds network activity data to the threat-hunting data pool and also interacts with on-site network security systems, such as firewalls to block suspicious activity.
The LogRhythm Axon system is a security analytics tool that refines the intelligence identified by the SIEM. this is a little like a vulnerability manager because it will identify weak points in your IT system and provide guides on how to fix them.
The final element that you can add to the SIEM is the LogRhythm SOAR. This provides extensive interactions with third-party tools and will let you thread together otherwise incompatible cybersecurity tools from different providers.
Who is it recommended for?
This is another solution for large organizations. The system will particularly interest businesses that have already invested a lot of money in on-premises security tools and find that they are so siloed that they cannot provide a unified approach to security. This service ties all of your current security tools together.
Pros:
- Guided Onboarding: Provides simple wizards
- Leverages Artificial Intelligence: Machine learning for behavior analysis
- Live Data Processing: Scans log messages and network activity feeds
Cons:
- UEBA and Network Traffic Monitoring are Add-Ons: They cost extra
LogRhythm SIEM is a cloud-based system and its data collector can install on Windows, Windows Server, and Linux. There is no free trial for the package but you can schedule a demo.
5. CrowdStrike Falcon Insight

CrowdStrike Falcon Insight is a brand of cybersecurity tools. CrowdStrike has created a series of products within the Falcon product range that cover all aspects of system security. It markets these tools individually and in bundles.
Key Features:
- Strong Endpoint Unit: Can operate independently
- Multi-Level Threat Hunting: Local protection and central coordination
- Automated Responses: Automation levels can be adjusted
Why do we recommend it?
CrowdStrike Falcon Insight is a cloud-based coordinator for on-premises CrowdStrike tools. The main requirement for the XDR is the presence of the Falcon Prevent unit, which needs to be installed on each protected endpoint on the network. The XDR coordinates the protection of the Prevent anti-virus system and creates a central threat detection and response service.
The full complement of the Falcon range creates an XDR. CrowdStrike offers an EDR solution, which is installed on each endpoint, providing constant defense even when the device is offline. It provides a management console for its EDR system, which coordinates data collection and threat response. That central coordinator is cloud-based and that service, called Falcon Insight, is the core of a classic XDR.
The Falcon Insight system can be augmented by other modules to create a stronger XDR system. Those other services are Falcon Intelligence, which is a threat intelligence feed, Falcon Overwatch, which is a threat hunting service, and Falcon Discover, which is a vulnerability manager. Other add-ons are a firewall management system and USB device management.
CrowdStrike produces a next-generation antivirus system, called Falcon Prevent. This is installed on each endpoint. However, customers of Falcon Insight don’t need to buy this separately because it is bundled in with that coordinated service. In fact, Falcon Insight is really a coordinator that communicates with Falcon Prevent instances.
Features of the CrowdStrike Insight service include UEBA for detection triage and SOAR for threat response. It is included in the Falcon Enterprise, Falcon Premium, and Falcon Complete bundles. Falcon Complete is actually a custom-built package. CrowdStrike also offers a managed cybersecurity service.
Who is it recommended for?
This system enhances the on-device Prevent module but it can also gather data from other CrowdStrike tools on a site and the more that you have, the better the Insightr service gets. This tool can work with Falcon Fusion SOAR to communicate responses to third-party security systems.
Pros:
- Excels in Hybrid Environments: Protects Windows, Linux, Cloud, and BYOD
- Intuitive Cloud-Based Admin Console: Access it through any standard Web browser
- Long-Term Anomaly Detection: Improves the longer it monitors the system
Cons:
- Short Trial: Would benefit from a longer trial period
CrowdStrike offers customers a 15-day free trial, although this actually gets you Falcon Prevent, not the fully-coordinated Falcon Insight service.
6. UnderDefense MAXI Platform
UnderDefense MAXI Platform is a managed security service and it gives you a team of technicians and cybersecurity consultants so that you don’t need to hire those skills onto your payroll. This is a cost saver and provides continuity because you don’t need to worry about replacing leavers.
Key Features:
- Cybersecurity Support Team: A good option if you can’t find the right people to hire in-house
- 24/7 Support: A SOC that operates around the clock
- Incident Analysis: Strategize to improve protection
Why do we recommend it?
The UnderDefense MAXI Platform combines security monitoring and compliance reporting. The system offers value for money through efficiency by eliminating the need to buy a separate compliance management service. This system also integrates with your SIM and other third-party security tools to provide automated responses.
This system is a cybersecurity technical support team and not an XDR package. This gives you the flexibility to choose your own software. With most managed security services, you assess the software on offer and not the quality of the staff in the security operations center. In this case, the staff is the product.
The UnderDefense team will assess your cybersecurity software and report on its suitability. There might be gaps in coverage or you might need to install updates to your existing software. If you don’t already have a cybersecurity package in place, UnderDefense will recommend the appropriate purchases to protect your system.
On starting its service, the UnderDefense team will recalibrate your cybersecurity software to provide the minimum protection. The team also combs through log files, looking for indicators of threats that the automated threat detection system you deploy has missed.
Discoveries will result in an adjustment to the configuration of your security system, changes to your network access controls, or recommendations for extra software to improve coverage.
The typical customer of UnderDefense is a business that struggles to hire expert cybersecurity staff either because of their budget or their location. Even corporations that can afford and find suitable experts will find that contracting this outsourced SOC saves them money and HR issues
Who is it recommended for?
The UnderDefense system is designed for businesses that hold sensitive data. It is particularly interesting for larger businesses. The company doesn’t provide a price list, which will put off small businesses that are usually price-sensitive. The company also offers a Managed Detection and Response (MDR) service for businesses that don’t have their own cybersecurity staff.
Pros:
- Cybersecurity Software Calibration: Preventative system hardening
- Options to Monitor Multiple Sites: All managed from a remote location
- Customizable Support Package: No fixed price
Cons:
- No Free Trial: Get a demo
The UnderDefense MAXI Platform is a custom service and the price will vary according to the level of service that you require. The team won’t provide monitoring or management of your non-security systems. As it is a bespoke service, there is no free trial for this package but you can request a demo of the MAXI Platform.
7. Rapid7 Insight Platform
Rapid7 has assembled an XDR platform called Insight. This is a collection of security products, mostly based in the cloud, that coordinate to provide a full XDR.
Key Features:
- A SIEM System: Also termed an XDR
- Attack Analysis: Looks for indicators of compromise
- UEBA: Identifies insider threats
Why do we recommend it?
Rapid7 Insight Platform is a cloud-based system with a core SIEM that can be enhanced by extra modules. The service can also be enhanced by the addition of a threat intelligence feed and a vulnerability manager. The system requires agents to be installed on the protected site.
The main component of the Insight system is called InsightIDR. This is a SIEM system that performs most of its tasks on the cloud and offers a browser-based console to customers. This tool is not all cloud-based, however, because it includes onsite agents that gather data and upload them to the Rapid7 server over an encrypted connection. InsightIDR uses UEBA for activity baselining that reduces false-positive reporting.
The InsightIDR service implements threat detection by searching through unified log records for “chains of attack.” This is the threat intelligence base of the InsightIDR system, which is termed Attack Behavior Analytics (ABA). This service identifies the typical behavior of active hacker groups and can spot the opening attacks of each. This enables the system to jump ahead of the attackers and shut down the avenues that they typically use to get into a system and wreak havoc.
IDR stands for Incident Detection and Response. As that term explains, InsightIDR includes response mechanisms that are implemented through the onsite agent modules and also involve interfacing with other security products in a typical SOAR strategy. That SOAR system is called Insight Connect.
Who is it recommended for?
The full Insight platform provides all of the tools that any Security Operations Center (SOC) could need. As such, this is a solution for large, multi-site organizations with centralized cybersecurity services. The package is probably a little too much even for mid-sized businesses.
Pros:
- Leverages Anomaly Analysis: Detect threats that bypass signature-based detection
- Uses Multiple Data Streams: Spots attacks from different viewpoints
- Allows for Robust Automated Remediation: Set the level of automation yourself
Cons:
- Pricing is Higher than Similar Tools on the Market: Doesn’t compete on price
Other modules in the Insight Platform include InsightVM, which is a vulnerability manager that operates through both cloud and on-site components. Cloud services are protected by the DivvyCloud service. Rapid7 offers an Insight module specifically for DevOps environments concerned with Web applications. This is called Insight AppSec.
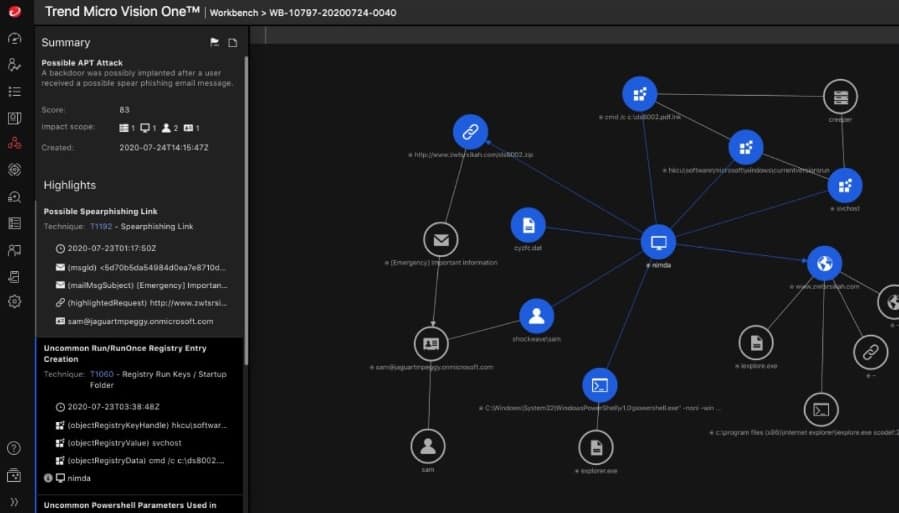
8. TrendMicro XDR
TrendMicro implements its XDR solution by coordinating its onsite security products through a cloud-based SIEM system. Those onsite tools include endpoint protection, network security, server protection, and email security products. There is also a cloud security system that can feed into the TrendMicro XDR service.
Key Features:
- Endpoint Security: Also tracks cloud platforms
- User and Identity Security: Examines failed login attempts
- Automated Responses: Can involve third-party tools
Why do we recommend it?
TrendMicro produces one of the most widely used AVs in the world and the XDR builds a cloud layer on top of that on-device protection system. This tool provides a secondary threat detection system in addition to the on-device anomaly detection. This enables the service to take a business-wide view of threats.
The various security products that are busy protecting specific aspects of IT infrastructure gather log messages and also generate their own monitoring notes. These get sent to the TrendMicro server for consolidations. That unified pool of live event records is then searched through by a threat detection module, which is essentially a SIEM system. Any worrying events generate system alerts and instructions to the relevant onsite module for deeper vigilance.
Confirmation of malicious activity triggers automated response actions that are performed directly by the onsite tools or relayed through them to system utilities. This is the classic SOAR strategy.
Who is it recommended for?
TrendMicro is strong at supporting mid-sized business sector and jockeys for the lead in this market with Sophos. As with many of the other packages on this list, the XDR relies on the company’s AV unit being installed on every endpoint. However, the TrendMicro system is more affordable than those of CrowdStrike and Heimdal Security.
Pros:
- Can Detect System Vulnerabilities: Preventative scanning as well as live security monitoring
- Virtual Patching: Can isolate unpatched applications and systems until fixes are deployed
- Stops Browser-Based Threats: Prevents crypto mining, and clickjacking
Cons:
- No On-Premises Option: Only available as a cloud-based solution
TrendMicro offers XDR in two formats. The first of these is called Vision One, which is a coordinating SaaS layer offered to customers of TrendMicro onsite security packages. The other option is called Managed XDR, which is a fully managed, outsourced SOC service.
9. Exabeam
Exabeam is a cloud-based SIEM that expands out into a security operations suite to form an XDR. The majority of the Exabeam system is based in the cloud with onsite elements deployed as relays. The device agents upload log messages and receive mitigation instructions.
Key Features:
- A SIEM: Delivered from the cloud
- UEBA: Insider threat detection
- Automated Remediation: Playbooks for responses
Why do we recommend it?
Exabeam is similar to the LogRhythm XDR platform because the company doesn’t produce its own on-premises AV unit but deploys agents on a site to collect data for threat hunting. Essentially, this is a remote AV system that can spot insider threats, account takeovers, and intruders as well.
Step one in this SaaS SIEM service is the creation of an Exabeam Data Lake. This is a consolidated poll of records that gets constantly added as new uploads arrive from device agents. These records are made available in the web-based console for viewing and sorting by the user but their main purpose is to provide a data mine for the threat detection service in the Exabeam XDR.
Exabeam Advanced Analytics operates as a UEBA service and establishes a pattern of normal behavior on a client-by-client basis. This reduces false-positive reporting and gives the threat hunter a baseline to compare activity records against.
Incident response can be varied according to the preferences of the user. The XDR platform includes the Exabeam Incident Responder. this is where the user decides on the level of threat mitigation automation. The response is dictated by “playbooks.” These are workflows that get triggered by a specific type of threat. That response could just be a notification – which is the default. Otherwise, the user can set up an automated response to shut down detected threats.
Who is it recommended for?
This cloud-based SIEM is able to gather logs, detect threats, and implement responses from its cloud location. On-site agents mediate between locations and can interface to third-party systems in order to shut down threats. Therefore, buyers will need to have other security systems on site from third-party providers.
Pros:
- Supports Incident Response: Workflows, playbooks, and automation
- Offers Useful Query Features: Manual searches for filtering large datasets
- Can be Used for Compliance Reporting and Internal Audits: Covers HIPAA, PCI DSS, etc.
Cons:
- Lacks Live Network Monitoring Capabilities: Wasn’t initially designed as a SIEM tool
An optional extra for the Exabeam XDR system is an archiving to store log files. The Exabeam XDR SaaS is available on a free trial.
10. ImmuniWeb
ImmuniWeb offers penetration testing and a vulnerability scanner. These are offered as a platform that can be combined with a SIEM to create an XDR. The SIEM isn’t included, however, so you will need to source that elsewhere on advice from the ImmuniWeb team.
Key Features:
- A Vulnerability Scanner: Continue checks through to live activity scanning
- Focuses on System Security Weak Points: Examines events at known vulnerabilities
- Penetration Testing: Emulates the actions of hackers
Why do we recommend it?
ImmuniWeb provides useful components for an XDR rather than a full threat detection and response system. You would use this service to discover which parts of your system are more vulnerable to attack and then take steps to remove those weaknesses or to focus security monitoring on those vulnerable points.
The difference between penetration testing and vulnerability scanning is that penetration testing is a manual process and vulnerability scanning is automated. So, the ImmuniWeb services that you would subscribe to for your self-assembled XDR would be its Discovery and Continuous systems.
ImmuniWeb Discovery is an external scan that searches through Dark Web sites for any indications that your site has been compromised. This could be because user account details are up for sale or hackers specifically mention your services or URLs when advertising attack tools.
ImmuniWeb regularly sweeps hacker sites for information on attack strategies and feeds that knowledge into its Continuous service. This is a vulnerability scanner that looks through a client’s system from an external viewpoint, testing its protection against any newly-discovered attack vector.
Who is it recommended for?
ImmuniWeb can be useful for large businesses and consultancies that want to perform a full system audit to get security up to standard. Continuous scanning keeps the system up to that newly achieved high level and a Dark Web scanner alerts the business to heightened risk.
Pros:
- Uses the OSINT Framework: Implements AI processes to proactively stop threats
- Includes Features that are Production-Safe: Places a minimal impact on your network
- Includes Supply Chain Attack Tools: Also a Dark Web scanner
Cons:
- Not the Best Fit for Smaller Networks: However, SMEs could try ImmuniWeb’s free tools
The ImmuniWeb service is entirely cloud-based and is offered in three editions: Corporate Pro, Corporate, and Express Pro. These are all subscription services with a monthly charge rate.
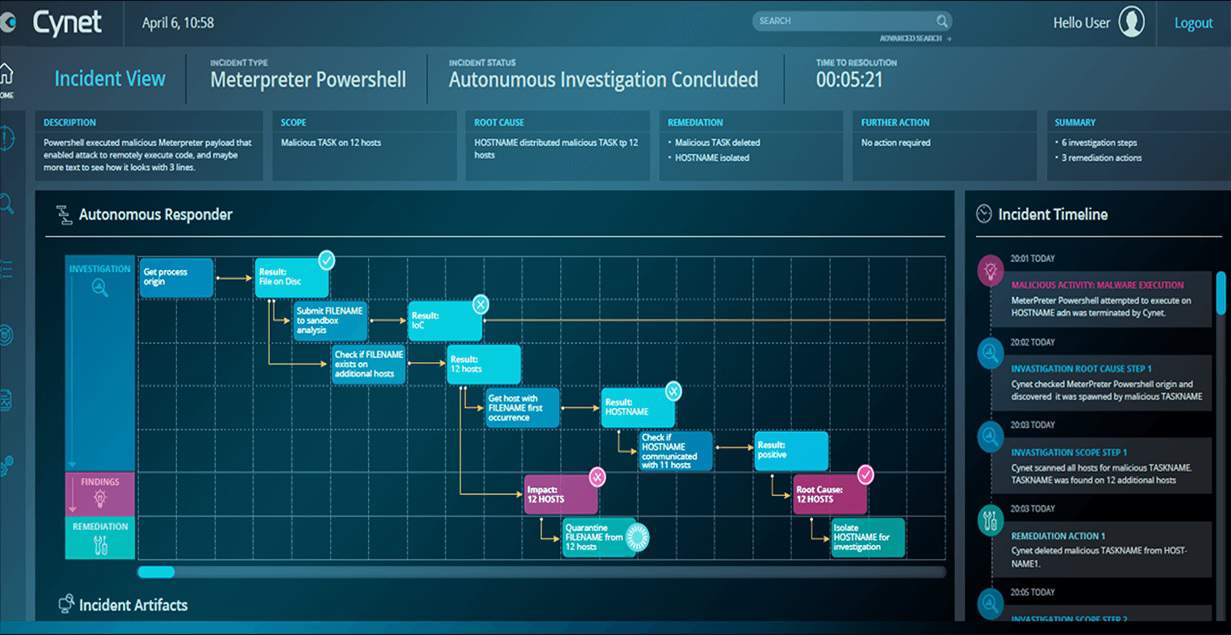
11. Cynet XDR Platform
Cynet calls its XDR system an Autonomous Breach Protection platform. It links together next-generation antivirus, EDR, UEBA, network traffic analysis, and deception intelligence in a classic on-site/cloud combination that typifies an XDR.
Key Features:
- A Range of Innovative Detection Methods: Includes deception technology
- Endpoint Protection: Antivirus, critical resource protection, and device control
- Cloud Protection: CSPM and SSPM
Why do we recommend it?
The subscription plans of the Cynet XDR Platform provide buyers with the option to choose endpoint protection, and EDR, a full XDR, or a hybrid protection service for on-premises and cloud resources. This creates a wide spread of products that build upon each other and is similar to the strategy adopted by CrowdStrike.
The data collection element in this SaaS service is called Sensor Fusion. These are log message collectors and network monitoring sensors that generate their own activity records. These are uploaded to the Cynet XDR Platform service, which performs a SIEM search for threats.
The Deception module of Cynet XDR Platform is very good – it is a unique service created by this business. The Deception strategy is to work as a honeypot. It creates fake, weakly-protected user accounts that attract hackers. It also diverts malicious activities with fake data files and deceptively easy-to-change (but fake) device settings.
Who is it recommended for?
The Cynet EDR/XDR options are focused on mid-sized to large businesses. The Essential Plan could work well for small businesses because it is mainly implemented on each device as an AV. However, its pricing puts it at the high end of the AV market and many buyers might proffer the cheaper solution offered by Trend Micro.
Pros:
- Multi-Level Detection: Combines backend threat intelligence with live network data
- Includes UBA: Looks for suspicious user actions
- Vulnerability Management: Preventative system hardening
Cons:
- Could Use a Longer Trial: The free trial only lasts 14 days
Cynet XDR Platform uses AI-based UEBA to zoom in on intruder activity and leave genuine users alone. The service includes an armory of scripts and strategies that automate threat response. This mitigation service also interfaces with other system services in a SOAR defense strategy. Cynet offers a 14-day free trial of its Cynet XDR Platform.