Wireshark is a very popular packet sniffer. It can be installed on Windows, Linux, Unix, and Mac OS, and best of all, it’s free. Wireshark puts your network card into promiscuous mode so that your computer picks up all network packets, not just those intended for your computer. There is an option to use the tool just for the packets meant for your device. Hackers regularly use Wireshark and so many network administrators are wary of it.
The Wireshark system can capture packet traces from wired networks, wireless systems, and also Bluetooth. Wireshark doesn’t actually gather packets itself. The WinPcap program collects packets on Windows devices. On Linux and Unix you need dumpcap. Even though Wireshark is not directly responsible for the most powerful part of its operations, the network interface of Wireshark makes it a winner. There is a command-line version of the system, called Tshark.
Here is our list of the best Wireshark alternatives:
- LiveAction Omnipeek EDITOR’S CHOICE This network protocol analyzer provides real-time analysis and data visualizations to troubleshoot network performance issues and security incidents. It supports various network segments, including Ethernet, 1/10/40/100 Gigabit, 802.11, voice, and video over IP. Runs on Windows.
- Ettercap A packet sniffer that is widely used by hackers and can give useful information to network defenders.
- Kismet A wireless packet sniffer that evades intrusion detection systems.
- SmartSniff A free packet sniffer that includes packet analysis functions.
- EtherApe A network mapper that shows live connections and offers the option to capture packets.
Wireshark saves data in capture files that follow the pcap format. The Wireshark network interface can show you the captured packets, sort them, categorize them, and filter them. You can load stored packets into the interface for analysis.
The analysis engine of Wireshark is not that great and many users choose other tools to get better insights into their data.
The Best Wireshark alternatives
Our methodology for selecting packet sniffer tools like Wireshark
We reviewed the market for Wireshark alternative packet sniffers and analyzed the options based on the following criteria:
- Solutions for Windows, macOS, and Linux
- Options for LAN and wireless networks
- The ability to interpret WinPcap or libpcap files
- A graphical interpretation of captured packets
- The ability to calculate packet flow statistics
- A free tool or a paid system that includes a free tool for assessment
- Value for money represented by a free tool that is easy to use or a paid tool that repays its purchase price with efficiency gains
1. LiveAction Omnipeek
Omnipeek from LiveAction isn’t free to use like Wireshark. However, the software has a lot to recommend it and you can get it on a 5-day free trial to test whether it will replace Wireshark in your toolkit. Like Wireshark, Omnipeek doesn’t actually gather packets itself. An add-on called Capture Engine intercepts packets on a wired network and there is a separate Wifi Adapter for wireless networks. One attribute in which Omnipeek doesn’t compete with Wireshark is the operating systems that it can run on. It can’t operate on Linux, Unix, or Mac OS. To run Omnipeek you need 64-bit Windows 7, 8, or 10, or Windows Server 2008 R2, 2012, 2012 R2, or 2016.
Key Features:
- Packet Capture Add-On: Enables the capture of packets on both wired and wireless networks.
- Comprehensive Packet Analysis: Provides detailed analysis of captured packet data.
- Advanced Analytical Tools: Includes tools for in-depth network traffic analysis.
- Graphical Data Interpretations: Offers visual representations of network data through graphs and charts.
- Automated Performance Analysis: Automatically tracks and reports network performance metrics.
Why do we recommend it?
Omnipeek provides both a packet capture tool and a protocol analyzer. This system generates graphics from packet header data, which you don’t get from Wireshark. The tool also lets you see each packet header. This system can capture packets from wireless networks as well as wired LANs and allows packets to be stored to file.
The analytical capabilities of Omnipeek are superior to those of Wireshark. Omnipeek can scan packets for signs of trouble or detect changes in transfer speeds. These events can be set to trigger alerts. So, Omnipeek is a network management system as well as a packet sniffer. The traffic analyzing module can report on end-to-end network performance for connections and also link performance. This troubleshooting tool is also able to report on-demand on interfaces to web servers.
Who is it recommended for?
This tool is easier to use than Wireshark because you don’t need to learn a detailed query language in order to get useful data out of it. Many of the data groupings that you would need to implement filters for in Wireshark are implemented automatically in Omnipeek. Although this tool isn’t free, it is worth paying for because it saves a lot of time.
Pros:
- Sophisticated Interface: The interface includes graphs and charts for easy data interpretation.
- Flexible Packet Capture: Offers various strategies for capturing network packets.
- Manual Analysis Tools: Provides tools for detailed, manual network data analysis.
- Performance Tracking: Automatically tracks and alerts on network performance issues.
- Wireless Traffic Capture: Capable of capturing packets from wireless networks.
Cons:
- Windows-Only: The software is not compatible with Linux, Unix, or Mac OS.
EDITOR'S CHOICE
LiveAction Omnipeek is our top pick for a packet sniffer that is a good alternative to Wireshark because this network protocol analyzer offers real-time analysis for network performance troubleshooting and security investigations. The package is compatible with Ethernet, including Gigabit systems, 802.11, voice, and video over IP, making it versatile for diverse networking environments. Omnipeek’s advanced packet capture capabilities allow users to monitor network traffic and identify potential bottlenecks, latency issues, and security threats. Its expert analysis tools provide in-depth insights into network behavior, enabling quick diagnosis and resolution of performance problems. Users can drill down into specific packets to understand the root cause of issues and make informed decisions on network optimization. The tool also offers comprehensive visualizations, such as graphs, charts, and dashboards, to present network data in an easily understandable format. These visualizations help network administrators and engineers quickly grasp complex network interactions and make data-driven decisions. Omnipeek integrates seamlessly with other LiveAction products, providing a unified platform for network performance management and security monitoring. This integration ensures that all aspects of network and application performance are monitored cohesively, offering a holistic view of the IT environment. Omnipeek’s user-friendly interface and customizable features make it accessible to both novice and experienced users, enhancing its utility in various network management scenarios. By leveraging LiveAction Omnipeek, organizations can ensure optimal network performance, maintain high levels of security, and quickly resolve network issues.
OS: Windows
2. Ettercap
Ettercap’s website makes no secret of the fact that it was designed to facilitate hacking.
Key Features:
- Penetration Testing Tool: Designed specifically for testing network security.
- Hacker Utility: Commonly used by hackers for various attacks.
- Intrusion Detection: Monitors and detects unauthorized activities.
- User Activity Tracking: Tracks and logs user actions on the network.
Why do we recommend it?
Ettercap is a penetration testing tool. It is closer to TShark because its output operates at the command line, although it tries to emulate a GUI screen. This system is able to perform a range of attacks, not just view packet data, so it has more features than Wireshark.
As Wireshark is a well-known hacker tool, the Ettercap claim puts it in the same category and they are both free to use. Ettercap matches Wireshark’s portability because it can run on Windows, Linux, Unix, and Mac OS. Despite being designed as a utility for hackers, the tool can also be useful to network administrators. Ettercap can detect other hacker activities and intrusions, so it is very useful for system defense.
Who is it recommended for?
Although Ettercap is easier to use, it isn’t as user-friendly as Omnipeek. This is a free tool, but it isn’t suitable for use by casual users because you need to spend time learning how the system works. The Ettercap system is widely used by hackers and penetration testers.
Pros:
- Facilitates Hacker Strategies: Allows penetration testers to simulate hacker attacks.
- Intrusion Detection: Can monitor and follow individual users to detect intrusions.
- Connection Control: Can terminate connections to thwart malicious activities.
- Versatile for Security: Useful for both penetration testing and defensive measures.
Cons:
- Clunky Interface: The user interface is not very intuitive and can be difficult to navigate.
Ettercap uses the libpcap library to capture data packet traces. The Ettercap software itself can create several network attacks including ARP poisoning and MAC address masquerading. Ettercap is a powerful hacker tool with many more facilities than those of Wireshark. It can capture SSL security certificates, alter packet contents in transit, drop connections, and capture passwords. System defenders also get useful facilities in Ettercap. It can identify malicious users and isolate them from the network. If you want to gather evidence, you can track the actions of suspicious users and record their deeds instead of banning them. Ettercap is way more powerful than Wireshark.
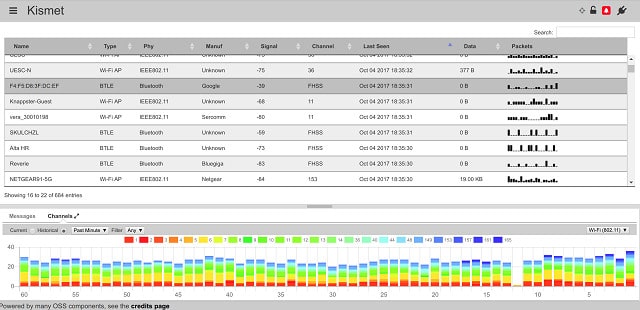
3. Kismet
Kismet can’t intercept packets on wired networks, but it is great for wireless packet sniffing. The standard Kismet tracks wifi systems, but it can be extended to detect Bluetooth networks as well. The wifi standard has several versions. Kismet can operate with 802.11a, 802.11b, 802.11g, 802.11n. Kismet is included with Kali Linux. The software will work on Linux, Unix, and Mac OS.
Key Features:
- Wireless Packet Sniffer: Specializes in capturing data from wireless networks.
- Free to Use: Available at no cost for users.
- Stealthy Operation: Operates without being detected by network security systems.
Why do we recommend it?
Kismet is a free tool and it specializes in capturing data from wireless systems. The display of the Kismet console is easy to read and includes graphics. This tool provides the option of collecting packet headers only or entire packets. However, it doesn’t crack wireless encryption.
Kismet’s data collector doesn’t probe networks like other packet sniffers, so intrusion detection systems can’t spot its activities. This makes it a powerful tool for hackers who have access to a computer that is connected to the network. Standard network monitoring systems will spot the presence of the device on which Kismet is running, but won’t see that the program is gathering data packets on the network. The default mode of Kismet only collects packet headers, but it can also be used to reap network traffic dumps which captures all packets including the data payloads. Packets can be analyzed, sorted, filtered, and saved to a capture file. If you don’t like the front end of Kismet, you can open a saved file in a different tool for analysis.
Who is it recommended for?
Kismet is a hacker tool, useful for a range of tricks, but it isn’t directly a snooping utility because it can’t crack the transmission encryption that is applied to all WiFi systems. This tool is very difficult to detect and it can evade network security monitors. Penetration testers should get to know this tool.
Pros:
- Undetectable by Security Systems: Kismet evades detection by network defense mechanisms.
- Supports Multiple WiFi Standards: Compatible with 802.11a, b, g, and n standards.
- Comprehensive Packet Analysis: Offers tools for in-depth packet analysis and sorting.
Cons:
- No Windows Support: The software does not have a version for Windows.
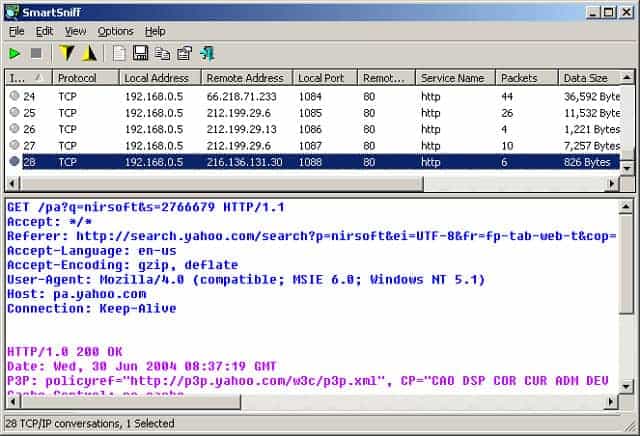
4. SmartSniff
SmartSniff works on Windows environments. The packet sniffer works on wired networks and is free to use. The collector can operate on wireless networks but only those wifi systems that include the computer that hosts the sniffer program.
Key Features:
- WinPcap Integration: Utilizes WinPcap for packet capturing.
- Wireless Packet Sniffing: Capable of sniffing packets on wireless networks with compatible hardware.
- Packet Content Display: Shows the contents of captured packets in a split-screen format.
Why do we recommend it?
NirSoft SmartSniff is a packet analyzer that operates in a similar way to Wireshark. The packet display screen is split, with analyzed summaries shown in the top panel and the actual packet header contents shown in the lower panel. This tool doesn’t have a sophisticated filtering language like Wireshark.
The program includes a collector. However, this native system isn’t very effective and it is more usual to install WinPcap to gather packets. Packets get captured on demand — you turn the capture on and then off in the console. The top pane of the console shows connections between computers. When you click on one of these records, the traffic of that connection displays in the bottom panel. Plain text traffic is shown as is and you can view encrypted packets as a hexadecimal data dump. Captured data can be filtered to show only TCP, UDP, or ICMP packets and each packet gets tagged according to the application that it relates to. You can save packets to a pcap file to be reloaded into the interface later, or for analysis with a different tool.
Who is it recommended for?
The absence of a query language is actually a blessing for many because that means anyone can use SmartSniff straightaway without any training. That means this free tool is useful for any network manager as well as for hackers and penetration testers. SmartSniff runs on Windows.
Pros:
- User-Friendly Filters: Provides packet analysis filters similar to those in Wireshark.
- Conversation Tracking: Allows users to follow network conversations easily.
- Protocol Traffic Highlighting: Highlights specific protocol traffic for easier analysis.
Cons:
- Outdated Interface: The user interface is dated and not very visually appealing.
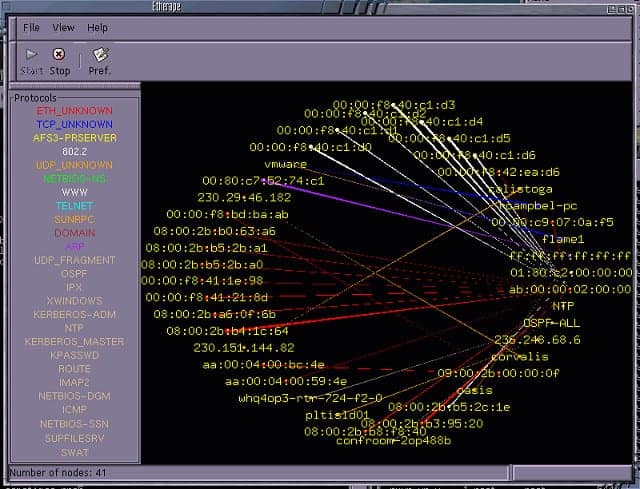
5. EtherApe
EtherApe is a free utility that runs on Linux, Unix, and Mac OS. It creates a network map by picking up connected devices’ messages. The hosts on the network are plotted on the map and labeled with their IP addresses. EtherApe then captures all of the packets traveling between those hosts and displays them on the map in real time. Each transfer is depicted by a color, which represents its protocol or application.
Key Features:
- Network Mapping: Visualizes network traffic with real-time maps.
- Packet Capture: Captures packets between connected devices.
- Free to Use: Available at no cost for users.
Why do we recommend it?
EtherApe is a free tool that has an unusual way to display traffic on a network by drawing lines between the endpoints in each conversation. Although the graphic is something that Wireshark doesn’t have, it isn’t much use and can be confusing. Its filter option menu is more useful.
The tool can track both wired and wireless networks and it can also depict virtual machines and their underlying infrastructure. The map tracks both TCP and UDP traffic and can detect both IPv4 and IPv6 addresses.
Each node in the network map is an icon that allows access to details of the performance of that piece of equipment. You can switch views to see the links on an end-to-end connection with traffic depicted on them. You can filter all of the maps to just show specific applications or traffic from specific sources. You can also switch the network data representation to identify port numbers rather than applications. The port number traffic tracking will only show TCP traffic.
Who is it recommended for?
EtherApe is a network traffic research tool that will be of more interest to network managers than to hackers or penetration testers. EtherApe doesn’t run on Windows but it is available for Linux, macOS, and Unix and it is free to use.
Pros:
- Tracks Wired and Wireless Traffic: Capable of monitoring both types of network traffic.
- Visual Network Maps: Innovative graphical representation of network connections.
- Protocol and Source Filters: Allows filtering by specific protocols or traffic sources.
Cons:
- Old Interface: The user interface is outdated and not very intuitive.
EtherApe only captures the headers of packets, which preserves the privacy of the data that is circulating around your network. That limitation may reassure your company’s CIO and allow you to use this packet sniffer without fear of compromising the business’s legal obligations to non-disclosure.
Switch from Wireshark
Even if you are perfectly happy with Wireshark, take a look at the alternatives in this list because you might find that one of them has functions that you need and aren’t in Wireshark. It is always good to explore alternatives rather than just using the first tool that you hear about. Wireshark is great, but it is not the most comprehensive tool on the market. Depending on the activities that you want to pursue with a packet sniffer and the limitations placed on you by your company, one of these tools may work better for you than Wireshark.
Have you tried a packet sniffer? Do you use Wireshark regularly? What do you use it for? Are you a fan of a packet sniffer that isn’t on our list? Leave a message in the Comments section below to share your knowledge.
Wireshark & Alternative tools FAQs
Can Wireshark do deep packet inspection or do I need something else?
Wireshark is a packet capture tool; deep packet inspection (DPI) refers to an automated process of scanning packet headers for information on its contents and purpose. Wireshark gathers packets for analysis by manual processes or to be imported into analysis tools, it does not include automated procedures for DPI.
Is Wireshark a vulnerability scanner?
A vulnerability scanner searches through a network or a device for known security weaknesses, such as open ports. Wireshark is a packet capture tool. Therefore, Wireshark is not a vulnerability scanner.
Is Wireshark good at port scanning?
Wireshark captures packets as they travel around a network. A port scanner sends test packets to a device to spot which ports are open. As Wireshark listens for packets and doesn’t send any out, it cannot be used for port scanning.
Which tool is a command line alternative to Wireshark?
tcpdump is a good command line packet capture utility that runs on Linux and uses a library of procedures called libpcap to access passing network traffic and display it on the screen and write it to files.
On Windows, the equivalent of tcpdump is WinDUMP, which uses the Windows PCAP library of procedures.
See also:
Wireshark Cheat Sheet
Ultimate Guide to TCP/IP
How to use Wireshark
How to use Wireshark to capture and inspect packets
Wireshark ‘no interfaces found’ error
Best packet sniffers
Downloadable tcpdump Cheat Sheet
What is tcpdump?
Packet Capture Guide










Hi, Very good article.
I’m a wireshark user that now looking for the alternative. In wireshark I have issue in analyzing the packets. I use wireshark to sniff the Skype V8.33 video call to analyze the RTP streams, but when I decode UDP to RTP, most of it has “Unknown RTP version 3”, so I cannot analyze the RTP streams. Thanks for the article, I’ll try the alternatives.