Are you looking for the best Security Orchestration and Automation (SOAR) software? We’ve got you covered. We’ve put some of the top SOAR tools to the test to help you find which solutions are best for you. Let’s dive in.
Here is our list of the best SOAR software:
- ManageEngine Log360 EDITOR’S CHOICE This SIEM liaises with applications to collect log data and interfaces to service desk tools to send notifications. Runs on Windows Server. Start 30-day free trial.
- Heimdal Threat Hunting and Action Center This cloud platform coordinates the activities of on-premises tools that are also provided by Heimdal.
- Rapid7 InsightConnect Ingrates well into other Rapid7 tools such as Metasploit.
- Logpoint Cloud-based security service offers a SIEM system that collects data from all around your system to correlate activity records.
- SolarWinds Security Event Manager Provides the best overall SOAR offering by combining ease of use with powerful remediation options suitable for both large and growing organizations
- LogRhythm NextGen SIEM Platform Uses behavioral analysis to stop internal and external threats.
- IBM Security QRadar SOAR This cloud-based tool is designed for use by a Security Operations Center team and it offers options to tailor the service for integrated threat response.
- Chronicle SOAR This security service on the Google Cloud Platform is able to implement automated responses through a series of playbooks.
- Palo Alto XSOAR Comprehensive security operations platform designed to assist organizations in streamlining and automating their incident response processes.
- Swimlane SOAR solution designed to streamline and automate security operations workflows.
The Best SOAR Software
Our methodology for selecting the best SOAR software
We reviewed the market for SOAR systems and assessed the options based on the following criteria:
- Contribution to a threat-hunting goal
- Interfaces with many oyster packages
- Data exchange
- Automated launch for script-based execution
- Ability to receive or send triggers
- Free trial or a demo to enable an assessment without paying
- Value for money from a system that pays for itself in productivity savings
Taking this list of requirements into consideration, we found a number of excellent security products that are able to interface with third-party tools to detect and block malicious activity.
1. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 is a SIEM system that uses orchestration to extract log data from third-party software and cloud platforms. The tool also interfaces to service desk packages to send notifications when it discovers a suspicious event.
Key Features:
- Security Tool Suite: Integrates six distinct security tools for comprehensive protection.
- Behavior Analytics: Utilizes user and entity behavior analytics to detect anomalies.
- Log Integration: Gathers log data from both operating systems and a variety of security tools.
- Alert Management: Sends alerts to service desk packages for immediate action.
Why do we recommend it?
ManageEngine Log360 is a large package of security tools that provides a SIEM and a data loss prevention service. This package deploys SOAR to gather information on events and also to implement responses to detected threats. This system also has a threat intelligence feed and uses UEBA to detect suspicious activity.
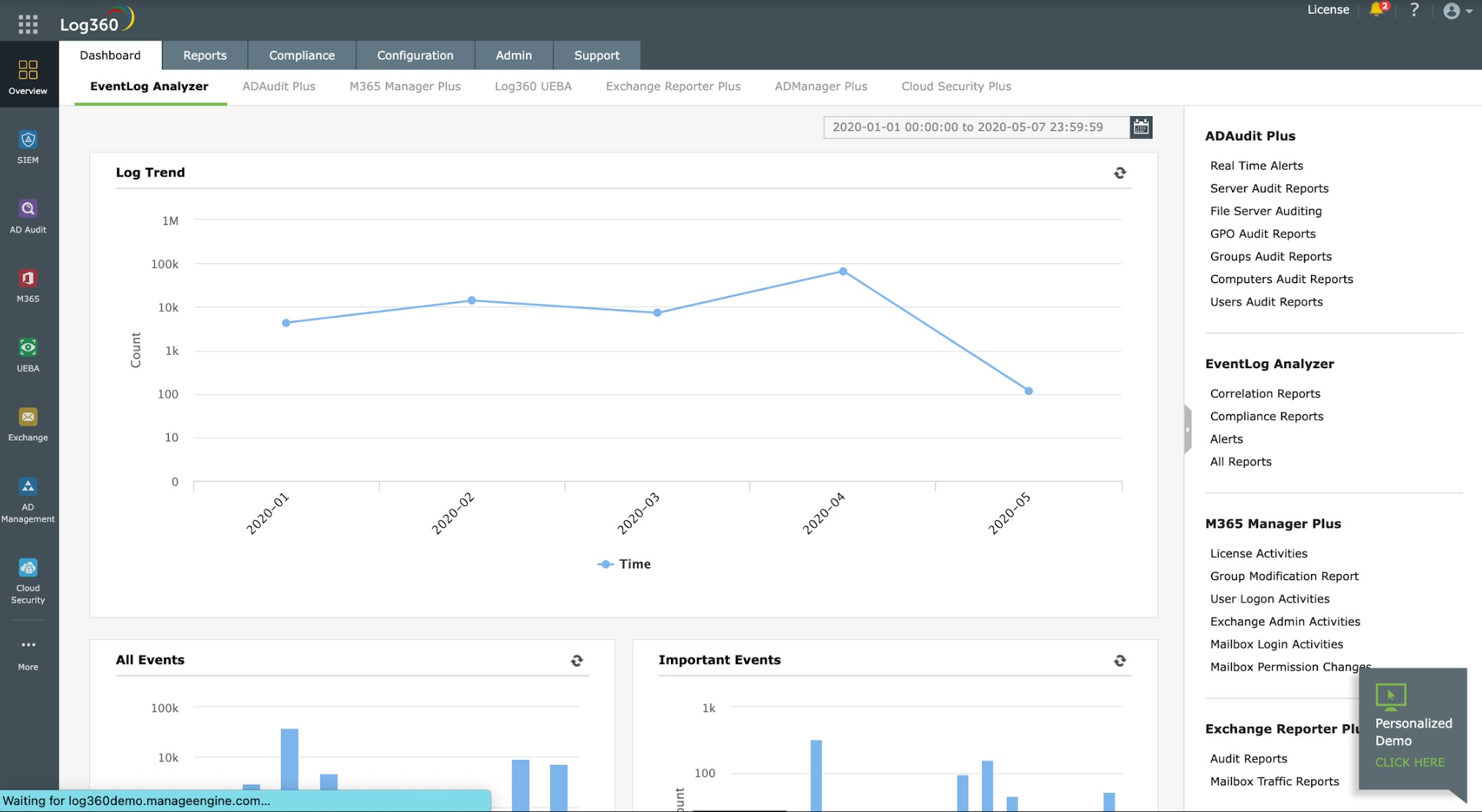
The package includes a library of agents. You install one on each endpoint and you can also setup an agent on cloud platforms, including AWS, Azure, and Salesforce. The agents gather log messages – this includes Windows Events from the Windows operating system and Syslog from Linux. The service is able to interact with more than 700 software packages to extract log data.
The agents send those log messages to a central log server. Log360 collects data from many locations simultaneously. The server converts the formats of these messages into a neutral format. This enables data from different sources to be collected together and sorted. The dashboard for Log360 shows throughput and you can look at messages in a data viewer as they arrive. The data viewer also includes analytical features, including sort, group, and filter.
The log manager stores log messages in files. That’s important if you need to conform to a data protection standard because they require logs to be available for compliance auditing. The Log360 system provides compliance reporting for HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA.
ManageEngine provides a live threat intelligence feed. This is a distilled digital tip line that feeds the latest attack vectors into the threat detection system. This intelligence is gathered from all over the world and identifies current campaigns that use specific tricks to access business systems.
When the SIEM detects a suspicious event, it raises an alert. The tool can send alerts through to service desk systems, including ManageEngine ServiceDesk Plus, Jira, and Kayoko.
Who is it recommended for?
This system is flexible because you can define the degree of automation that you want to be used for responses. This means that the tool has a wide audience because companies that have security analysts on staff can fine-tune the mechanisms within the package. The software runs on Windows Server.
Pros:
- Extensive Log Collection: Capable of pulling logs from over 700 applications, ensuring thorough monitoring.
- Hybrid Monitoring: Effectively monitors both onsite systems and cloud-based platforms.
- Service Desk Integration: Automatically notifies service desk tools upon threat detection, facilitating rapid response.
Cons:
- Platform Limitation: The server component is not compatible with Linux, though the agent is.
ManageEngine Log360 installs on Windows Server and you can assess it with a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Log360 is our top pick for a SOAR package because it integrates advanced security orchestration, automation, and response (SOAR) capabilities with comprehensive SIEM functions. The system combines real-time log management, event correlation, and automation workflows to provide a unified, efficient approach to cybersecurity. It empowers organizations to respond to security incidents faster, with minimal manual intervention, which is essential in today’s rapidly evolving threat landscape. One of Log360’s key strengths is its built-in automation. Security teams can define custom response actions for specific security events, ensuring quick and appropriate responses to detected threats. This automated playbook approach reduces human error and accelerates incident resolution, enhancing overall security posture. The tool also integrates with a wide range of third-party security systems, including firewalls, antivirus tools, and network devices, to orchestrate a cohesive response across the security stack. It improves coordination between security tools and teams, fostering better collaboration. Log360’s attractive dashboard makes it easy for security professionals to design, implement, and monitor automated workflows, without needing deep technical expertise.
Download: Get a 30-day FREE Trial
Official Site: https://www.manageengine.com/log-management/download.html
OS: Windows Server or SaaS
2. Heimdal Threat Hunting and Action Center
Heimdal Threat Hunting and Action Center is a cloud-based package that forms part of a cybersecurity platform. While SOAR systems are typically designed to coordinate third party tools, this package only works with other Heimdal tools. However, it uses standard SOAR processes, forming a hub between many instances of cybersecurity tools on a site.
Key Features:
- Data Reception: Collects data from integrated Heimdal security systems.
- Threat Search: Analyzes aggregated data to detect security threats.
- Endpoint Scanning: Conducts thorough scans on endpoints to identify vulnerabilities.
- Security Instruction: Directs and manages on-site Heimdal security tools for proactive defense.
Why do we recommend it?
Heimdal Threat Hunting and Action Center adds value to other Heimdal tools, particularly the Next-Generation Anti-Virus package. By coordinating the capabilities of multiple tools, this cloud-based system can spot account takeover events, intrusion, insider threats, and data theft. The package implements threat hunting within its processes through a unit called the XTP Engine.
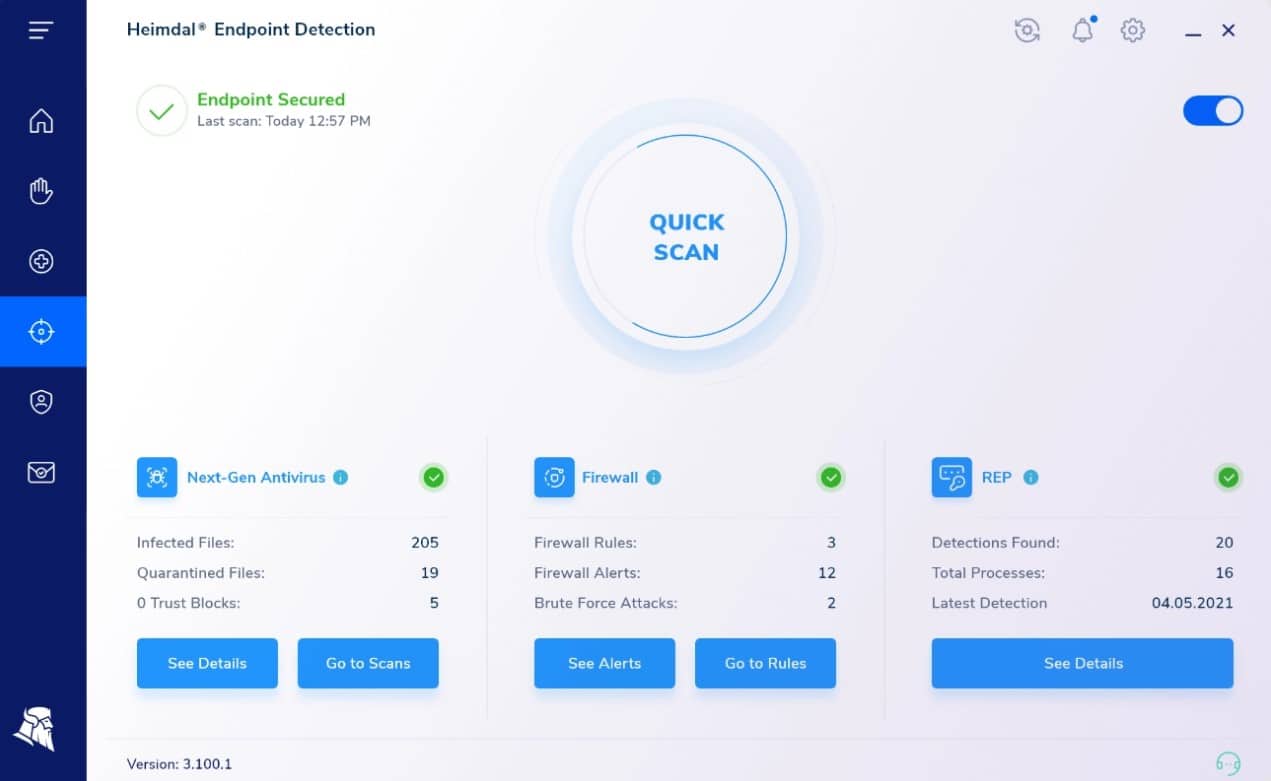
A SOAR system coordinates the efforts of other security tools, connecting identified threats with a playbook of actions. Heimdal Threat Hunting and Action Center does this with multiple on-site Heimdal products. The cloud service needs at least three on-premises packages to be installed before it will operate. One of those three must be the Heimdal Next-Gen Anti-Virus system, which incorporates a mobile device management (MDM) system and runs on Windows, macOS, Linux, Android, and iOS.
The two other services that must be in place can be selected from a list of cybersecurity systems available from Heimdal. These include Network Security, Email Security, Patching & Asset Management, and Endpoint Security.
As well as threat detection, the Heimdal tool can scan endpoints for vulnerabilities. This risk assessment service is enhanced by a system hardening threat intelligence service that warns all endpoints on a network if one is attacked.
The threat hunting part of the Heimdal package is implemented by the XTP Engine. XTP stands for Extended Threat Protection. The Action Center is a series of playbooks that get triggered by the detection of a threat. There are different instructions in the Action Center for different types of threats. These are implemented through communications with those on-site Heimdal tools.
Who is it recommended for?
This package is recommended for use by mid-sized companies. Its services would be unnecessarily complicated for a small business and a larger business would probably expect to set up a security operations center with a much larger toolset. This service squeezes extra value from other Heimdal services by coordinating threat detection and response across an enterprise
Pros:
- Enhanced Integration: Amplifies the effectiveness of other Heimdal security tools.
- Unified Security Environment: Establishes a comprehensive security network across the enterprise.
- Centralized Intelligence: Centralizes threat data to foster a private threat intelligence network.
- Customizable Tool Selection: Allows flexibility in choosing security modules from Heimdal’s offerings.
Cons:
- Dependency on Other Products: Requires multiple Heimdal products to function, limiting its standalone utility.
Heimdal doesn’t offer a free trial of the Threat Hunting & Action Center and there is no price list. Your investigation into this service should start by requesting a free demo.
3. Rapid7 InsightConnect
If you know anything about cybersecurity, you’ve likely heard the name Rapid7. InsightConnect is Rapid7’s SOAR software, which offers seamless integrations into their other security products to help help users build a comprehensive security system. InsightConnect allows you to build an efficient SOAR system that cuts down on manual tasks and implements highly customizable remediation policies.
Key Features:
- SaaS Offering: Delivers a cloud-based solution for simplified accessibility and management.
- Data Collection: Gathers crucial data from operating systems and network devices.
- Automated Workflows: Features a visual workflow builder for creating automated remediation strategies.
Why do we recommend it?
Rapid7 InsightConnect is an extension to the security tools on the Rapid7 platform of security tools. It implements SOAR to improve the effectiveness of the InsightIDR system, which is both a SIEM and an XDR. By itself, the InsightIDR package draws its source data from installed agents, which also implement responses.
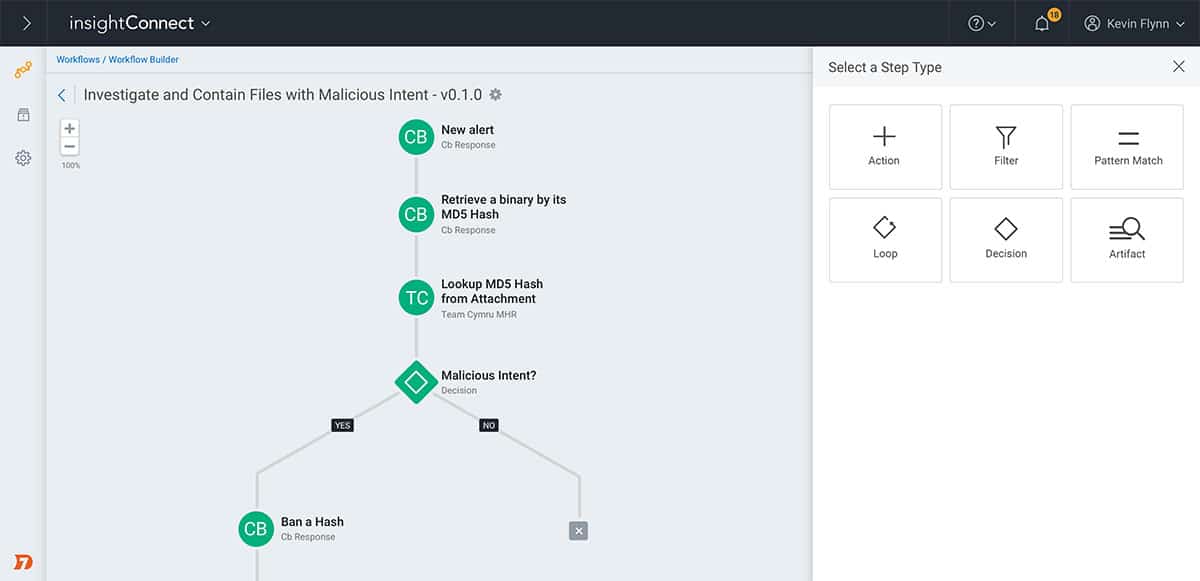
Over the years, Rapid7 has done an excellent job building a more user-friendly environment for those who prefer more sophisticated tools outside of the command line. InsightConnect makes it easy to get started with over 300 plugins that enable integrations and workflows into your environment. This use of plugins is convenient and helps keep the base package lean for those who don’t need the additional options.
One of my favorite parts of the software is the incident response, workflow builder. The tool is highly visual and allows you or your team to build remediation that resembles a flowchart. This enables users to construct complex remediation solutions with ease to visualize every step of the process.
InsightConnect can also cover automated investigations of inbound and outbound emails. As email is still the number one vector of compromise, InsightConnect can identify and stop phishing attacks, malicious attachments, and spam before it hits your mail server.
Busy remediation teams can use InsightConnect to prioritize and manage new vulnerabilities as well. As vulnerabilities are discovered and submitted, the platform gives remediation teams the right tools to streamline validation, prioritization, and remediation to ensure that the network is never exposed longer than necessary.
Lastly, the platform is highly collaborative and was designed with large-scale teams in mind. Companies already using messaging tools integrate into platforms like Slack or Microsoft Teams and offer webhooks for ITSM solutions such as ServiceNow and JIRA.
Who is it recommended for?
The InsightConnect system is a good choice for businesses that have many security systems already installed that would otherwise be ignored by the InsightIDR package. Examples of such services would be on-device malware systems and firewalls on endpoints and on network devices.
Pros:
- Collaborative Environment: Supports integration with popular communication tools like Slack and Microsoft Teams.
- Vulnerability Management: Includes robust tools for managing and prioritizing new vulnerabilities effectively.
- Visual Workflow Design: Offers a user-friendly, graphical interface to design and visualize remediation workflows.
Cons:
- Complex Upgrades: Updating plugins within existing workflows can be cumbersome.
- Challenging Onboarding: The initial setup process can be intricate, especially in larger organizational settings.
4. Logpoint
Tested on: Cloud-based/SaaS

The Logpoint system operates from the cloud and connects to your network through the installation of an agent on one of your servers. Logpoint calls its security monitoring package a ‘converged SIEM‘. This term denotes the integration of SOAR and UEBA in the threat detection package.
Key Features:
- Cloud-Based SIEM: Offers a secure, scalable system for monitoring network security.
- Data Collection Integration: Collects and analyzes data from multiple sources for enhanced security insights.
- Automated Threat Response: Automatically responds to detected anomalies to mitigate threats swiftly.
- Compliance Support: Aids in adhering to various data protection regulations like GDPR and CCPA.
- Multi-Region Availability: Available in multiple regions, providing versatile service access globally.
Why do we recommend it?
The Logpoint system is a good choice for those businesses that are comfortable with cloud-based security systems. This package uses on-site agents to liaise with third-party security tools for data gathering and for threat response. The package also deploys user and entity behavior analytics (UEBA) to spot anomalous activity.
The data collection system built into the Logpoint agent goes beyond just picking up circulating log messages. It also interfaces with applications and queries statuses, gathering live activity reports. These feeds are added to the collected log messages to create a pool of data for threat hunting.
The Logpoint system builds up a baseline of regular behavior by tracking all activity per user account and device. Threat hunting is conducted as anomaly detection. Deviations from the standard provoke an alert. This also triggers automated responses.
The Logpoint agent uses its compatibility with third-party tools to shut down threats. Examples of these actions are instructions to access rights managers to suspend compromised user accounts and the creation of new firewall rules to block communication with a suspicious IP address. 
Logpoint is based in Denmark, with additional offices in other European nations, plus the USA and Nepal. Due to its location, the Logpoint team is particularly skilled at building GDPR compliance. The SIEM is also good for businesses that need to comply with CCPA and SCHREMS-2.
Distinguished by its ‘converged SIEM’ approach which integrates SOAR and UEBA technologies. This system enhances threat detection and response by utilizing on-site agents that communicate with third-party security tools, thereby orchestrating a comprehensive security management process.
The UEBA feature effectively identifies unusual activities, which significantly bolsters security measures no matter your environment. Additionally, Logpoint’s adaptability in working with external applications contributes to its robust defense mechanisms, ensuring swift and automatic threat neutralization. During testing, we appreciated how seamlessly it integrates with varied environments, promoting ease of compliance with standards like GDPR, making it ideal for diverse organizational needs.
Who is it recommended for?
Logpoint uses a charge rate that is based on the number of devices that send data to the Logpoint threat hunting system. This is a very scalable pricing structure and makes the service affordable to businesses of all sizes. The service collects data from applications and operating systems as well as security tools.
Pros:
- Enhanced Security Monitoring: Integrates SOAR and UEBA for comprehensive threat detection and response.
- Compliance Readiness: Facilitates adherence to regulations such as GDPR, CCPA, and SCHREMS-2.
- Scalable Pricing: Offers a flexible pricing model based on the number of monitored devices.
Cons:
- Manual Data Analysis: While it organizes log messages effectively, manual analysis is still required for detailed investigations.
The service doesn’t just collect log messages, it also organizes them into log files, which is great for compliance auditing. Those files are also available for manual searching and analysis, which can be useful for tasks such as capacity planning and budgeting. You can book a demo to study the Logpoint system.
5. SolarWinds Security Event Manager
Tested on: Windows Server
SolarWinds Security Event Manager (SEM) provides administrators with an on-premises SOAR solution in a single yet powerful platform. What makes SEM stand out is its ability to provide templates and out-of-the-box settings without restricting sysadmins who want to build their solutions. These templates extend to compliance reporting as well, helping companies maintain and prove their compliance with regulatory requirements such as HIPAA, PCI DSS, and SOX.
Key Features:
- Regulatory Compliance: Supports adherence to HIPAA, PCI DSS, and SOX, ensuring regulatory requirements are met.
- Log Forwarding: Capable of routing log data to other analysis tools or storage solutions.
- Threat Database: Includes a comprehensive database for ongoing threat intelligence updates.
Why do we recommend it?
SolarWinds Security Event Manager is a SIEM tool that also manages log files. It provides compliance auditing and reporting for HIPAA, PCI DSS, and SOX. this system is able to gather information from third-party security tools, such as firewalls. It also sends threat response instructions to firewalls and access rights managers.
Rather than managing orchestration, automation, and remediation across multiple platforms, SEM combines those options into a single solution without making the platform over-complicated and difficult to navigate. Additionally, for data that needs to be sent elsewhere, Security Event Manager offers some of the broadest range of integrations into other remediation and ticketing platforms.
The platform keeps large-scale enterprises in mind with highly scalable features like data normalization that can work across multiple applications or sites. This works excellent in its default state and helps dramatically reduce the amount of time sysadmin spend on tweaking their data collection settings.
On the back end, this data is automatically compared and integrated into the SolarWinds threat intelligence database. Here, the latest threat statistics and models are automatically applied to your data. Gone are the days of needing to make sure your threat databases are being kept up to date. This same threat intelligence integration can identify internal threats and prevent improper resource access from staff members.
There are dozens of advanced workflow templates to choose from to help streamline the remediation process. These work well as is but can be customized to suit the needs of your environment. While many SOAR software struggle when it comes to filtering, SEM excels in this department. Data filters are intuitive and help provide a live look into specific data that needs attention.
When you’ve discovered a threat that needs remediation, In addition, this SEM makes it easy to build an automated remediation or custom alert template. The automated workflow builder uses a simple GUI that allows the user to choose an action or series of actions to execute given a specific condition. Conditions can be based on thresholds or single events, giving you maximum control and flexibility over how you defend your network.
SEMs event correlation rules help keep your SOAR software working proactively. There are over 700 correlation rules to choose from, offering an out-of-the-box solution or solid foundation to build from. These rules can be as straightforward or complex as you need them to be and offer actions such as disabling accounts, shutting down USB ports, and quarantining hosts or subnets based on the threat.
Who is it recommended for?
This package is a good choice for companies that prefer to run security software in-house rather than relying on cloud systems. The software package runs on Windows Server. This is a big solution with a great deal of processing capacity and it is particularly suitable for use by large organizations.
Pros:
- Comprehensive Monitoring: Monitors a range of operating systems including Windows, Linux, Unix, and Mac.
- Integrated NIDS Tools: Integrates with tools like Snort, enhancing network intrusion detection capabilities.
- Ready-to-Use Alerts: Features over 700 pre-configured alerts and correlation rules for immediate operational insight.
Cons:
- Complex Features: The vast array of features requires a significant time investment to fully leverage.
You can test the fully functional version of SolarWinds SEM completely through a 30-day free trial.
6. LogRhythm SIEM Platform
LogRhythm is a popular SIEM/SOAR platform used by enterprises across the globe. NextGen SIEM combines the data collection of traditional SIEMs and pairs it with LogRhythems SmartResponse automation to immediately stop threats either on-premises or from the cloud.
Key Features:
- Cloud Deployment: Offers a flexible, cloud-based SIEM solution.
- Comprehensive SIEM Capabilities: Acts as a full SIEM system with extensive data collection and analysis.
- Behavioral Analytics: Utilizes user and entity behavior analytics to detect anomalous activities.
Why do we recommend it?
The LogRhythm SIEM Platform is built on a modular plan and there is a SOAR element to this stack. The tool is able to collect data from third-party security tools and it can send response instructions to access rights managers and firewalls to block communications from specific IP addresses and suspend user accounts.
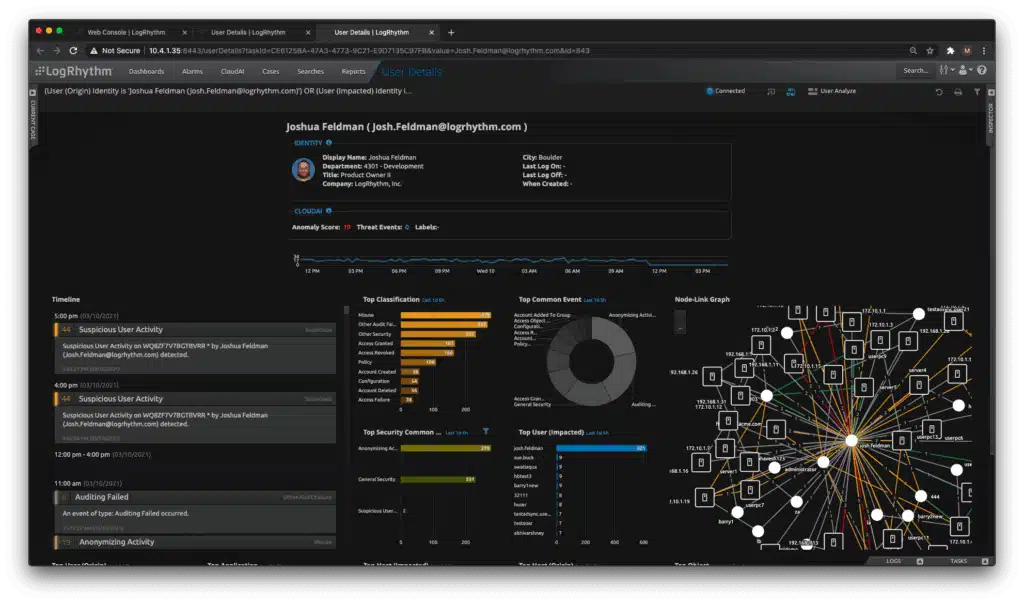
The platform is visually stunning, allowing users to create insightful dashboards through a collection of premade widgets. These views can display real-time insights to NOC teams or display custom information to specific staff members.
The automated threat response templates make it easy to implement simple remediation actions such as disabling user accounts or killing specific processes. These actions can be paired with conditional or threshold-based alerting, allowing you only to involve team members when automated remediation reaches its limits.
The platform comes with two additional add-on features which pair nicely with the NextGen platform. First, UserXDR can detect user-based threats such as account takeovers and insider attacks.
This technology users behavioral analysis through machine learning to understand the context behind user actions and intentions. In addition, NetworkXDR provides extra network analysis to detect threats attempting to move laterally within the network. This can help detect privileged access abuse and privilege escalation attempts.
Users benefit from LogRhythm’s vast intelligent network that continuously feeds the latest threat data into each customer’s deployment. This helps businesses scale their products without having to worry about higher operating costs. In addition, like most SOAR software, LogRhythm automatically normalizes data once received, allowing companies to collect data from a wide variety of environments and formats without issue.
Lastly, the platform can automatically archive data for long-term storage or index for better searchability. This option between cold and warm storage solutions is a bonus and gives users flexible options depending on how often they need to parse data.
Who is it recommended for?
This SIEM system is based in the cloud and operates through agents that are installed on the protected network. This is a large and complicated system with many elements and it is particularly suited for use by large organizations. The capacity of this tool would be too much for small businesses.
Pros:
- User-Friendly Setup: Features wizards for easy setup of log collection and security configurations.
- Customizable Interface: Provides a sleek, visually appealing, and highly customizable user interface.
- Advanced Analytics: Employs AI and machine learning for sophisticated behavior analysis.
Cons:
- Lack of Trial Option: Does not offer a free trial to test its features before committing.
- Limited Cross-Platform Support: Could benefit from enhanced support for multiple platforms.
7. IBM Security QRadar SOAR
IBM is leveraging its knowledge of big data and scalability to create a SOAR platform of its own. IBM uses a combination of automation paired with a playbook or set of guidelines that help determine which automated remediation a threat should have applied to it. The SOAR software can be used either on-premises, in a hybrid cloud environment, or purchased as a SaaS option.
Key Features:
- Hybrid Compatibility: Well-suited for hybrid cloud environments, offering flexible deployment options.
- Visual Process Maps: Features detailed flow charts to aid in understanding and managing security processes.
- Playbook Designer: Allows for the creation of automated response strategies tailored to specific threats.
Why do we recommend it?
IBM Security QRadar SOAR is a customizable security threat response system that includes integrations with hundreds of third-party systems. The tool combines discoveries from your existing security tools with a threat intelligence feed. Through a series of playbooks, which are like action templates, your team defines different responses according to the source of each alert.
IBM Security SOAR focuses heavily on automating as many manual tasks as possible, freeing up time for technicians to work on more complex investigations. Visually the platform is sleek and designed to highlight critical security incidents that need attention. In addition, the tool makes good use of color to accent metrics, brings attention to critical alerts, and leverages dark colors to keep it easy on the eyes for long-term use.
Unlike some SOARs, IBM has a series of ways teams can visualize data through different topological maps and flow charts, making, breaking down complicated workflows. This design is handy for larger network operation centers and more extensive internal security departments.
Each incident can automatically be remediated through automated action. How that is carried out is controlled through the Playbook Designer, which is surprisingly easy considering how complicated SOARs can get. Playbooks are designed to be dynamic and flexible, which helps keep remediation actions agile in the face of evolving threats.
This strategy also helps prevent overly aggressive security responses that hinder legitimate work from occurring. Playbooks can also be built to determine how a breach should be handled, allowing your team to know right where to start if an attack does succeed.
Each incident can be recorded and visualized through an incident visualization graph. This provides a 10,000-foot overview of exactly how a threat entered the network, what it did, and where it spread to in the network. These high-level insights can save valuable time when investigating a time-sensitive security issue such as ransomware or spyware and be used to teach and train new staff.
Who is it recommended for?
This solution is designed for use by a security operations center (SOC). That means it is aimed at large businesses or managed service providers. The system provides the opportunity to notify non-technical departments of breaches, such as the Finance Department or HR.
Pros:
- Advanced Visualizations: Utilizes sophisticated graphical representations to make data analysis intuitive.
- Flexible Automation: Offers dynamic playbooks that adapt to changing security needs and simplify threat response.
- Versatile Deployment: Supports on-premises, cloud, and hybrid installations, catering to various organizational needs.
Cons:
- Enterprise Focus: Primarily designed for large organizations, potentially less ideal for medium-sized businesses.
- Lengthy Setup: The implementation and onboarding process can be extensive and time-consuming.
8. Chronicle SOAR
Chronicle SOAR is part of the Chronicle Security Operations suite from Google Cloud. This package was bought by Google and was known as Siemplify until early 2022. The system received signals from your SIEM or other threat detection systems and manages automated responses through a series of playbooks that you set up. Although this is a Google product, it can interact with tools on other platforms from other providers.
Key Features:
- MSP-Friendly: Designed to meet the needs of managed service providers effectively.
- Intuitive Playbook Builder: Features an easy-to-use interface for creating and managing playbooks.
- SIEM Enhancement: Adds significant SOAR capabilities to existing SIEM systems for enhanced security management.
Why do we recommend it?
Chronicle SOAR is a service on the Google Cloud Platform (GCP). It is an automation tool for threat responses that cut down the amount of work that SOC staff need to implement in order to block attacks. The automation also enables responses to be implemented quickly.
While the dashboard can be tricky to get just right, it provides a customizable way to view all your key insights and metrics across your entire organization. For example, the alert distribution feature allows you to see which threats triggered a particular alert. This is useful for both reporting as well as stopping alert fatigue across your security teams.
To assist technicians, Chronicle SOAR comes with root cause analysis that provides crucial threat details, so staff know where to start looking for problems. In addition, a unique storyline view can be toggled to see just how a threat entered the network and if it spread across multiple hosts or devices. This simple but powerful visualization helps techs stop threats faster and cut down when your systems are exposed.
All data is normalized and made searchable upon ingestion and comes with the ability to archive it for long-term storage. This is helpful if your team needs to review incidents to support a legal case or keep in line with regulatory compliance.
If you trialed Siemplify and you are now investigating Chronicle SOAR, you will notice that the tool is pretty much still the same system. It is organized for use by a team, and its workflow setup is very easy to use. You don’t need to spend time learning the intricacies of this system.
Who is it recommended for?
The Chronicle SOAR system is intended for SOC teams, so it is not designed for small businesses. Managed service providers are another target market for this system. Current users of the system point out that this tool provides an interface to many underlying security systems. So, it removes the need to log into several different systems.
Pros:
- Rapid Playbook Development: Enables teams to quickly construct and modify playbooks using a graphical editor.
- Threat Prioritization: Efficiently highlights and sorts threats by severity to focus on the most critical issues.
- Effective KPI Management: Supports robust tracking of key performance indicators to monitor security effectiveness.
Cons:
- Lacking Documentation: The available documentation does not sufficiently explain all features and functionalities.
- Bug Issues: Newer versions tend to include bugs that could be minimized with more comprehensive pre-release testing.
9. Palo Alto XSOAR
Palo Alto Networks Cortex XSOAR (Extended Security Orchestration, Automation, and Response) is a comprehensive security operations platform designed to help organizations streamline and automate their incident response processes. It combines security orchestration, automation, and response (SOAR) capabilities with case management, threat intelligence management, and collaboration tools.
Key Features:
- Security Orchestration: Automates complex workflows across various security tools and processes to enhance efficiency and consistency in incident response.
- Automation: Reduces manual intervention by automating repetitive and time-consuming tasks, allowing security teams to focus on more strategic activities.
- Incident Response: Facilitates faster and more effective incident management by integrating with a wide range of security tools and providing a centralized platform for monitoring, investigation, and remediation.
- Case Management: Organizes and tracks incidents through a structured approach, ensuring that all steps in the incident response process are documented and followed.
- Threat Intelligence Management: Aggregates and correlates threat data from various sources, providing actionable intelligence to improve detection and response efforts.
- Collaboration Tools: Enhances team communication and coordination during incident response with built-in collaboration features.
- Customizable Playbooks: Predefined and customizable playbooks standardize and automate response procedures, ensuring that incidents are handled consistently and efficiently.
- Integration: Supports integration with a wide range of third-party security tools and platforms, allowing organizations to leverage their existing security investments.
Why Do We Recommend It?
Palo Alto XSOAR earns its place among the best SOAR software due to its powerful automation capabilities and centralized security management. It automates repetitive tasks across various security tools, both from Palo Alto Networks and third-party vendors. This frees up security analysts for more strategic work and leads to faster incident response times.
Who Is It Recommended For?
Palo Alto XSOAR is ideal for organizations with complex security environments that utilize multiple security tools. If you’re already invested in the Palo Alto Networks ecosystem and have the resources to handle a potentially complex platform, XSOAR offers a strong integration advantage.
Pros:
- Advanced Automation: Excels at automating repetitive security tasks, freeing up security analysts for more strategic work.
- Centralized Hub: Acts as a central platform integrating with various security tools, both from Palo Alto Networks and third-party vendors.
- Faster Incident Response: Streamlined workflows and automation enable quicker detection, investigation, and remediation of security incidents, minimizing potential damage.
- Improved Security Posture: By automating tasks and consolidating security data, XSOAR can help organizations identify and address vulnerabilities more effectively, ultimately strengthening their overall security posture.
- Scalability: Adapts to growing security needs, allowing organizations to add new integrations and functionalities as their security landscape evolves.
Cons:
- Complexity: Learning and configuring XSOAR can be challenging, especially for organizations with limited security expertise. This can lead to a steeper learning curve and a need for additional training or skilled personnel to utilize it effectively.
- Cost: Licensing fees can be a significant factor, especially for smaller organizations. It’s important to weigh the cost against the potential return on investment.
10. Swimlane
Swimlane is a security automation company focused on preventing breaches and ensuring continuous compliance. Its low-code platform acts as the central hub for the entire security team. Swimlane Security Platform is a SOAR solution designed to streamline and automate security operations workflows.
Key Features:
- Automation: Automates repetitive and manual security tasks, reducing the workload on security teams and allowing them to focus on more strategic activities.
- Orchestration: Integrates with a wide range of security tools and platforms, enabling seamless data sharing and coordinated responses across the security ecosystem.
- Incident Response: Provides robust incident response capabilities, including automated playbooks, case management, and real-time collaboration tools.
- Threat Intelligence: Aggregates and correlates threat data from multiple sources, providing actionable insights and enhancing threat detection and response.
- Analytics and Reporting: Offers powerful analytics and reporting tools to track key performance indicators (KPIs), measure the effectiveness of security operations, and identify areas for improvement.
- Flexibility and Customization: Allows users to create and customize workflows, playbooks, and integrations to meet their unique security requirements.
Why Do We Recommend It?
Swimlane SOAR excels at automating repetitive security tasks, freeing up security analysts to focus on complex investigations and strategic initiatives. This automation can significantly improve the efficiency of your security team.
The primary goal of Swimlane SOAR is to enhance the efficiency, effectiveness, and consistency of an organization’s security operations. By integrating and automating multiple security tools and processes, Swimlane helps security teams to manage threats more effectively and respond to incidents faster.
Who Is It Recommended For?
Swimlane SOAR is particularly well-suited for organizations seeking to streamline security operations and empower security analysts. If your organization prioritizes automation and has the resources to manage a potentially complex platform, Swimlane SOAR is a compelling choice.
Pros:
- Enhanced Efficiency: Automates repetitive security tasks like incident response, threat analysis, and vulnerability management, freeing up valuable analyst time for more strategic work.
- Faster Incident Response: Streamlines workflows and automates actions, enabling quicker detection, investigation, and remediation of security incidents.
- Improved Security Posture: By centralizing security data, automating workflows, and offering advanced analytics, Swimlane SOAR helps identify and address vulnerabilities more effectively.
- Customizable Workflows: Supports low-code and no-code development for creating custom workflows and playbooks, making it accessible to users with varying technical expertise.
- Strong Integrations: Offers seamless integration with various security tools, both from Swimlane and third-party vendors. This allows you to centralize security operations and automate data flow across your existing security ecosystem.
Cons:
- Potential Complexity: While the swimlane interface simplifies workflow visualization, the overall platform can have a learning curve for new users.
- Cost: Licensing fees can be a significant factor, especially for smaller organizations. It’s important to weigh the cost against the potential return on investment for your security needs.
Which SOAR software is right for me?
We’ve taken a hard look at some of the best SOAR software available, but which is best for you? For almost all organizations, SolarWinds Security Event Manager will provide the best balance between ease of use, automation options, and affordability compared to other tools on the market.
While many SOAR software vendors focus only on massive enterprise networks, SolarWinds Security Event Manager offers a truly scalable solution that allows even medium-sized businesses to take advantage of SOAR systems.
Do you leverage automation in your cybersecurity strategy? Let us know in the comments below.
SOAR software FAQs
What is SOAR software?
SOAR means Security Orchestration, Automation, and Response. These tools are able to collect data from third-party tools, particularly security systems, such as firewalls – this is the “security orchestration” part. Automation and Response are provided by a workflow or “playbook” library. These are lists of triggers and actions to perform in each circumstance. The actions will be instructions to other systems, such as access rights managers or firewalls, to shut down malicious activity.
Can SIEM replace SOAR?
Don’t see SIEM and SOAR as rivals. Rather, SOAR is a coordination method, while SIEM is a data processing and analysis tool. The ideal play-off between the two is a merger rather than a competition. You want your SIEM to have SOAR capabilities so that it can react to detected threats automatically by invoking the services of tools that you already have installed on your network.
What is XDR technology?
XDR extends endpoint detection and response. This system should coordinate endpoint-resident security tools to identify a threat to the entire network. XDR adds to EDR because it is able to interact with third-party tools to gather intelligence and implement responses outside the core EDR group.