There are many types of ransomware attacks, and they can all ruin your business. Ransomware can be implemented in many ways but the two most frequently practiced strategies are the encryption of files and data theft
Hackers that use encryption-based ransomware render all files on a computer unusable by encrypting them. Usually, the only way to recover those files is to pay for the decryption key. To protect yourself and your business from these thereats, ransomware scanners can stop the threat before it causes damage.
Disclosure ransomware attacks steal data from your system, and the hacker threatens to publish that information if a ransom isn’t paid. Suppose your company holds personally identifiable information (PII) on members of the public, and that data gets released. In that case, you can be fined and sued, and you will lose data security standards accreditation.
In some business sectors, compliance with data privacy standards is a condition of contracts. For example, the payment card clearing sector requires conformance to PCI DSS. If you don’t have that accreditation, you can’t process payments by card – for most online businesses, that ban would put them out of business. So, there is a lot at stake.
Here is our list of the best ransomware scanners:
- ManageEngine Log360 (FREE TRIAL) This is a SIEM system that can spot all types of malicious activity, whether manual or automated. It can protect against all ransomware and data theft threats. It runs on Windows and Windows Server. Access the 30-day free trial.
- BitDefender GravityZone A package of security tools that includes antivirus checks at many points of the system, including just before uploading to backup storage.
- Rapid7 InsightIDR A next-generation SIEM that includes automation actions to block ransomware and other malicious activity. This is a SaaS platform.
- SpinOne A cloud-based service that offers ransomware protection, backup and recovery, data loss prevention, and compliance reporting for the major SaaS productivity platforms.
- Exabeam A next-generation SIEM that uses AI methods to identify abnormal activity, such as ransomware actions. This cloud-based system will also block malware and intruders.
- LogRhythm NextGen SIEM Platform A suite of anti-malware tools that combine to identify, block and remove ransomware, other malware, and intruders. They are offered as a cloud service, as an appliance, or as software for Windows Server.
Protection against ransomware
You can’t afford to let hackers get at your essential data stores. Data thieves manually gain access to a system and explore it to find valuable data. Ransomware is an automated process and can be a bit hit and miss.
Some ransomware will only infect the computer to which it first gets access, while others can move around the network, infecting all of the endpoints before triggering the attack. You improve your chances of recovering from an encryption ransomware attack by backing up all files and then just restoring them, wiping out the encryption without paying the ransom. However, some ransomware systems can infect backup stores as well.
Disclosure ransomware is very difficult to recover from without paying the ransom. Therefore, preventing this type of attack is your only hope. So, defending stores of PII is very important. The most important way to protect against all types of ransomware is to install security software that will spot it as soon as it gets onto an endpoint and prevent it from triggering.
Ransomware scanners
Ransomware is an automated attack. It is malware, so your best form of defense against these attacks is through advanced malware detection systems. Spotting ransomware requires a combination of security services. It needs significantly evolved systems that spot anomalies rather than the old-fashioned type of anti-virus packages that just look for a list of filenames or processes. Ransomware is evolving all the time, and you don’t want to be caught out as the first victim of a new variant that AV companies haven’t spotted yet.
There are two types of systems that provide appropriate defense against ransomware; next-generation AVs and next-generation SIEMs. In addition, some security system providers have developed services that form a platform of protection services. These systems establish a baseline of regular activities performed by each user and device. This is called user and entity behavior analytics (UEBA). A typical next-gen system that flags any activity that doesn’t fit that pattern of normal behavior.
The next-gen strategy defends against previously unencountered malware. This is important in ransomware because that type of system only operates for a short period. After a brief attack campaign, the hackers revamp their ransomware so that it won’t be spotted by those security systems that have recorded its operating procedures and updated all instances with this information.
Hackers are constantly changing their ransomware into new versions or even entirely new systems. They can use several different entry methods, but the most common are:
- RDP attack through an unprotected port
- Installer disguised as an email attachment
The use of the Remote Desktop Protocol is an intruder-like strategy, and a download from an email attachment is a typical method used by Remote Access Trojans (RATs). In addition, some ransomware combines these two operating methods, using a download for the initial infection, and then RDP to replicate the malware around the network, continuing to seize all devices and backup stores.
A competent ransomware scanner will catch both of these two infection methods.
The Best Ransomware Scanners
The most appropriate ransomware protection system for you depends greatly on your operating configuration. For example, you need to be sure that the ransomware scanner can interact with the operating systems that you are running on your sites. In addition, if you use cloud storage, you need to ensure that your scanner can identify ransomware before it gets uploaded. Beyond these operating system considerations, there are several important factors to determine.
Our methodology for selecting a ransomware scanner
We reviewed the ransomware prevention system market and analyzed tools based on the following criteria:
- Spots zero-day attacks
- Behavior baselining and anomaly detection
- Alerts for detected attacks
- Implements automated threat prevention actions
- System-hardening features
- Free trial or a demo system for a cost-free assessment
- Good value for money
Depending on whether you hold a lot of PII on your system, you might need to consider buying in several tools to protect your company from ransomware attacks. Using the above selection criteria, we drew up a shortlist of some excellent ransowmare scanners that will keep you safe from ransomware.
1. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 is a SIEM-based threat intelligence platform that can spot automated attacks, such as ransomware and manual intrusion by data thieves.
Key Features:
- SIEM tool
- Log analysis
- Security orchestration, automation, and response
- Active Directory protection
Why do we recommend it?
ManageEngine Log360 is a vast package of data protection and threat hunting systems. The package has a SIEM, a SOAR for coordinating third-party security tools, Active Directory risk assessment and protection, and a file integrity monitor. These facilities should spot account takeover and file renaming events, which are the typical opening moves of a ransomware attack.
As well as using log messages as data input, Log360 receives a threat intelligence feed from outside the business. This provides new tactics to look out for when scouring through activity reports. In addition, the service displays events live on the system dashboard as each log message gets added to the pool, and then stores logs for later research.
Log360 includes processes for scrutinizing Active Directory to recommend tighter access controls. This is useful for reducing the vulnerability of a business if one account gets compromised. Anomaly detection can then identify potential zero-day ransomware attacks, and the threat intelligence feed gives Log360 indicators of compromise that identify specific chains of actions as likely ransomware activity. It can also remember malware activity and the actions of intruders and malicious insiders.
Who is it recommended for?
This is a very large package that provides a full suite of security tools. The service would be too much for a small business but it is ideal for a large organization that is tooling up a central security operations center (SOC). The suite also protects cloud applications although it runs on site on Windows Server.
Pros:
- Fast scanner for ransomware thanks to a threat intelligence feed
- Anomaly detection to spot zero-day attacks
- Covers cloud platforms as well as onsite endpoints
- Can trigger actions to shut down attacks
- Spots manual malicious actions as well as ransomware and malware
Cons:
- Doesn’t include backup management
Log360 runs on-site and installs on Windows Server. However, it is also able to supervise AWS, Azure, and Exchange Online. You can get a 30-day free trial of the tool.
EDITOR'S CHOICE
ManageEngine Log360 is our top pick for a ransomware scanner because it offers a comprehensive and highly effective solution to detect, prevent, and respond to ransomware threats in real time. As ransomware attacks become more sophisticated, organizations need a tool that can quickly identify malicious activities and mitigate risks before significant damage occurs. Log360 implements a range of detection techniques to address these challenges. One of Log360’s most important services is its ability to monitor file system activity, including detecting unusual changes to files and folders that could indicate ransomware encryption. By continuously scanning for abnormal file access patterns or rapid, large-scale file modifications, Log360 can alert administrators to potential ransomware activity before it spreads across the network. The tool’s integrated SIEM (Security Information and Event Management) functionality collects and correlates logs from multiple sources, providing a centralized view of suspicious events and improving overall visibility. Log360’s file integrity monitoring tracks changes to critical files and can help identify the initial entry point of a ransomware attack. The tool’s real-time alerts and automated responses ensure that IT teams are immediately notified, enabling rapid incident response. Moreover, its customizable dashboards allow administrators to visualize security data effectively, making it easier to identify patterns and threats. ManageEngine Log360 provides a holistic approach to cybersecurity, combining proactive detection, alerting, and real-time monitoring.
Download: Download a 30-Day Free Trial
Official Site: https://www.manageengine.com/log-management/siem-solution-log360.html
OS: Windows Server
2. BitDefender GravityZone
BitDefender GravityZone is a bundle of security systems to protect all devices on a network from ransomware and hacker attacks. This package is powerful on malware sweeps that occur at several points in the system and spot malware ingress. In addition, all endpoints get AV systems that scan each new file dropped onto the device.
Key Features:
- Anti-malware
- Backup and recovery
- Scans files before saving in backup
Why do we recommend it?
BitDefender GravityZone provides strong ransomware protection by combining antivirus and threat detection with a backup service. The platform also includes a vulnerability scanner and a patch manager to reduce the risk of attack. Other options include user behavior tracking and email security.
An important feature of this package that many other anti-ransomware systems lack is its backup manager. You can pair this backup service with your cloud storage account or open a cloud file space account with BitDefender. This backup system also scans each file for malware before uploading it to storage. This gives you the best defense against encryption ransomware.
GravityZone includes a vulnerability manager that tightens security and will harden your system against RDP-based ransomware. It also has a file integrity monitor that blocks data theft and encryption.
Who is it recommended for?
This service is suitable for businesses of all types and sizes. However, it could be particularly interesting for small businesses because the full package with all add-ons provides just about all of the threat protection systems that they need. Although the package doesn’t include a SIEM, a small company doesn’t have a great need for such a tool.
Pros:
- Ransomware scans at all critical locations on a system, including endpoints
- Backup manager with full malware scans
- File integrity monitoring
- Vulnerability manager
Cons:
- Large number of services can be difficult to track
GravityZone installs as a virtual appliance, and it is available for a one-month free trial.
3. Rapid7 InsightIDR
Rapid7 InsightIDR is an extended detection and response (XDR) service. The package is cloud-based but focused on defending endpoints, which are the landing zones for all ransomware. The service installs agents on all endpoints to scan directly for all types of malware, including ransomware. This service is also good for spotting intruder activity.
Key Features:
- Cloud-based SIEM
- Deception technology
- User activity profiling
Why do we recommend it?
Rapid7 InsightIDR is a hybrid system that operates its threat detection searches on the cloud, based on activity logs uploaded from on-premises agents. The central package is a SIEM and it can be enhanced with a network detection and response unit and a user behavior tracking service.
The modules in InsightIDR include a threat intelligence feed and UEBA for anomaly detection. Both the feed and activity reports form inputs to a SIEM system that quickly scans for threats. A great feature of InsightIDR is that it sets up honeypots on the network to attract hackers and malware, making them easier to detect.
Who is it recommended for?
The core endpoint protection system is all you need for ransomware protection. This is an affordable solution with a rate per asset per month, which makes the system suitable for all sizes of businesses. The platform also provides a SOAR in an extra module, which can completely coordinate all of your security systems.
Pros:
- Endpoint agents spot new files that could be part of a ransomware
- Threat intelligence feed
- Honeypots to draw ransomware and hackers into the open
- UEBA for activity baselining
Cons:
- No backup management
- Vulnerability scanning costs extra
Rapid7 offers InsightIDR for a 30-day free trial.
4. SpinOne Ransomware Protection
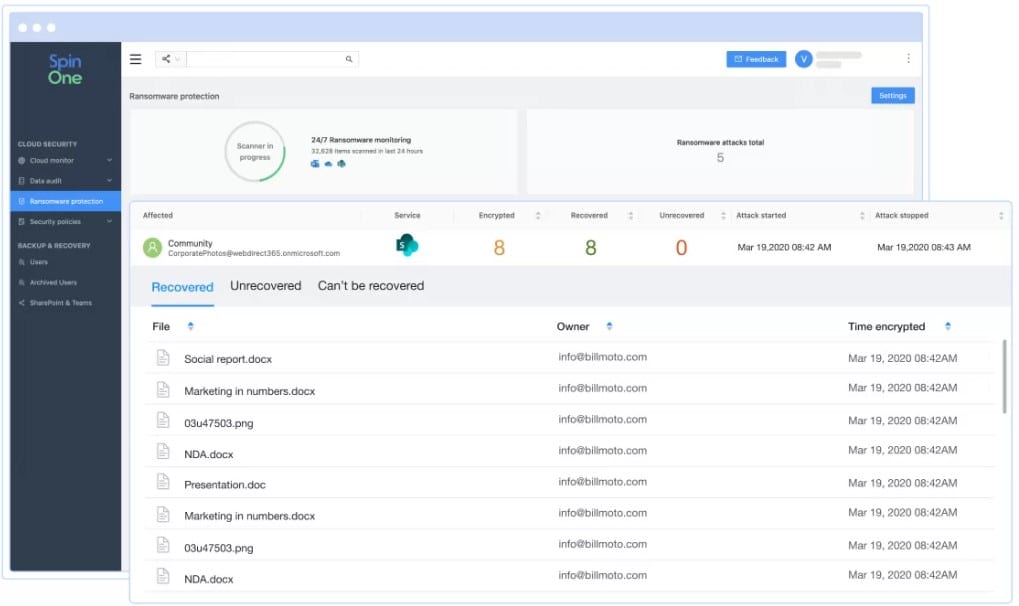
SpinOne from Spin.ai is a package of data protection systems that is delivered from the cloud and integrates into four of the most widely-used cloud platforms; Microsoft 365, Google Workspace, Slack, and Salesforce. This package includes ransomware scanning and remediation. There is also a backup and recovery system built into the SpinOne platform.
Key Features:
- Ransomware Detection and Response
- Data Loss Prevention
- Security Posture Management
- Microsoft 365, Slack, Salesforce, and Google Workspace
- Backup management
Why do we recommend it?
Spin.ai provides protection for SaaS systems, such as Microsoft 365 and Google Workspace. The platform has a ransomware detection and response module, called SpinRDR. The SpinOne package includes all three Spin.ai services – the other two being SpinSPM for risk assessment, and SpinDLP for data loss prevention.
SpinOne provides automated workflows for dealing with a detected ransomware encryption incidence. Ransomware has to operate from a third-party server in order to infect cloud file storage systems, so SpinOne immediately disconnects API access to the filespace. This prevents the ransomware from infecting more files.
The service will isolate infected files while it checks through its activity logs to identify the source of the ransomware. It then reports on its findings, deletes the encrypted files, and copies over replacements from the backup.
Who is it recommended for?
SpinRDR is suitable for businesses that subscribe to SaaS platform rather than the providers of those systems. Any business of any size would benefit from this package. The full SpinOne package will appeal more to businesses that manage sensitive data. Spin-ai doesn’t publish its price list or specify whether there are minimum order requirements.
Pros:
- Backup and recovery service
- Ransomware scanning
- Protection for sensitive data
- User activity tracking and behavior analysis
- Automated ransomware mitigation strategies
Cons:
- Each plan only protects one specific cloud platform
SpinOne plans each protect one specific platform. You can try any of the four editions with a 15-day free trial.
5. Exabeam
Exabeam is a cloud platform that offers the next-generation SIEM. This system coordinates with device agents to spot new files and record activity, and this is an excellent way to spot ransomware.
Key Features:
- Cloud SIEM
- Threat intelligence
- Automated responses
Why do we recommend it?
The Exabeam platform provides a log manager and a SIEM. Some extra services to enhance those core threat detection systems include a threat analysis package, a threat intelligence feed and a SOAR, called Fusion for automated responses that operate through third-party tools.
The features of the Exabeam system include a threat intelligence feed that informs the log scanning process. Logs are gathered and uploaded by device agents, which also perform their analysis of activities onsite. In addition, the anomaly detection system of Exabeam establishes a baseline of normal activities with UEBA and then looks for deviations from that standard.
The Exabeam service offers an extra module to interact with other systems on your network to shut down attacks. This is called security orchestration, automation, and response (SOAR). It interfaces with firewalls and access rights management services to automatically block ransomware and other malware. It is also able to shut down insider threats and data theft attempts.
Who is it recommended for?
Exabeam includes a log server that accepts logs from your existing systems, such as Windows Events from PCs, so it operates without an agent. You have to set up the destination of each of your log-generating applications or use a log collector and forwarder. This is a little complicated and makes the package more appropriate for large businesses with expert administrators.
Pros:
- Fast identification of ransomware files and other malware
- AI-based UEBA baselining for anomaly detection
- Highly rated threat intelligence feed from SkyFormation
- Automated responses to shut down ransomware and hacker activity
Cons:
- No data discovery processes
- No backup management
6. LogRhythm NextGen SIEM Platform
LogRhythm NextGen SIEM Platform is a collection of security modules that are organized into a stack. This combines local intelligence gathering with a significant threat hunter and is an excellent service for catching ransomware.
Key Features:
- Protection for hybrid systems
- Host on your cloud account
- SaaS option
Why do we recommend it?
LogRhythm NextGen SIEM Platform is an on-premises package that can be installed on Windows Server or you can get it loaded onto an appliance. There is also a SaaS version, which is called LogRhythm Axon. this is a high-end service that will detect all types of threats through anomaly detection and user behavior analytics.
The LogRhythm package is organized into services. These include UEBA for activity baselining and a threat intelligence feed for indicators of compromise. Additionally, log message uploads are supplemented by live network activity monitoring and device agent reports on endpoint events. These provide inputs to the threat hunting SIEM.
When threats are identified, the LogRhythm system deploys SOAR to coordinate blocks with other security software on your system. This service quickly detects and shuts down hacker activity and insider threats as well as malware attacks.
LogRhythm is available as on-premises software for Windows Server, an appliance, and a hosted SaaS system.
Who is it recommended for?
The LogRhythm system is a great package for a corporate security operations system. Typical installations cost between $30,000 and $40,000, so this is a system that only large companies could afford. Opting for a subscription and going for the Windows Server or SaaS versions instead of the appliance brings the price down.
Pros:
- Gathers event data on endpoints to spot ransomware arrival
- Co-ordination with endpoint agents and other onsite security products to feed activity reports into a SIEM
- Automated responses to shut down malware and hacker activity
- Range of deployment options that include onsite installation, a hosted service, and a network appliance
Cons:
- No data discovery service for sensitive data classification
- No backup manager