IP and network scanners are tools that uncover hidden endpoints, detect vulnerabilities, and understand exactly what’s running behind your firewalls. You can’t protect or manage what you can’t see, so network scanning has become essential for visibility, control, and security.
Manual checks cannot keep pace with constant changes. Hence, you need smart tools that automatically map your network, analyze traffic, and alert you before minor issues escalate into major problems. In other words, these smart tools eliminate the blind spots and reactive struggles that typically create major pain points for IT teams.
IP and network scanner software can help your organization avoid the following pain points:
- Avoid blind spots caused by unmanaged, unknown, or forgotten devices on your network.
- Reduce the time spent manually tracking IPs, subnets, or device details across spreadsheets.
- Prevent IP conflicts that disrupt services and are difficult to troubleshoot manually.
- Eliminate guesswork when identifying what is connected to your network and whether it should be there.
- Gain faster detection of unauthorized or rogue devices that may introduce security risks.
- Save effort by automating routine network discovery and monitoring tasks that would otherwise be repetitive.
- Simplify compliance by maintaining an accurate, real-time inventory of all network-connected assets.
This guide will show you the best IP and network scanner tools to help you gain complete visibility and control over your network.
What is an IP scanner?
An IP scanner is a network utility designed to identify and analyze devices connected to a network by scanning a range of IP addresses. These tools are essential for administrators seeking to maintain visibility over their infrastructure, as they provide valuable insights into the devices and systems operating within a network. IP scanners are versatile and serve various purposes, making them indispensable for IT management, troubleshooting, and security.
Why Use an IP Scanner?
One primary use of IP scanners is network inventory management. By scanning for active devices, these tools help administrators maintain an accurate record of all devices connected to the network. This is especially useful in environments where devices frequently join or leave the network, such as offices with bring-your-own-device (BYOD) policies.
IP scanners are also valuable for troubleshooting and performance monitoring. They can identify devices that may be causing network congestion or failing to respond. For instance, if a printer, server, or workstation goes offline, an IP scanner can quickly detect its status, aiding in fast resolution.
From a security perspective, IP scanners help detect unauthorized devices that may have connected to the network without permission. Identifying these rogue devices allows administrators to mitigate potential threats and enforce access policies. Advanced IP scanners can also provide details about open ports and services running on devices, offering insights that enhance vulnerability assessments.
IP scanners serve as foundational tools for capacity planning as well, helping organizations determine whether their network infrastructure can handle current and projected loads.
IP Scanner Configurations
Whether integrated into comprehensive network monitoring solutions or used as standalone utilities, IP scanners support a wide range of administrative and security tasks, ensuring that networks remain efficient, secure, and well-managed. By leveraging these tools, businesses can maintain control over their network environments, ensuring optimal performance and safety.
Based on my independent research, here’s my suggested list of the best network scanners, network analysis & management tools for buyers:
- ManageEngine OpUtils EDITOR’S CHOICE A network scanning and IP address management tool designed to help you monitor IP usage, detect rogue devices, and manage switch ports with real-time visibility. Start a 30-day free trial.
- Paessler PRTG Network Monitor (FREE TRIAL) A unified monitoring platform that tracks network performance, devices, services, and traffic through customizable sensors for comprehensive, real-time oversight. Start a 30-day free trial.
- Site24x7 Network Monitoring (FREE TRIAL) A cloud-based solution that monitors network availability, performance, and device health across distributed environments. Start a 30-day free trial.
- ManageEngine Vulnerability Manager Plus (FREE TRIAL) An endpoint-focused security and vulnerability management tool that scans your network for risks, misconfigurations, and missing patches to strengthen overall security posture. Start a 30-day free trial.
- Nmap Α versatile network mapper for host discovery, port and service scanning, OS fingerprinting, and automation via the NSE scripting engine.
- Masscan Ultra-fast TCP/port scanner optimized for internet-scale scans when you must probe millions of addresses quickly.
- Angry IP Scanner A lightweight, cross-platform GUI tool for fast IP/port sweeps and quick desktop inventories.
- Fing Mobile-first discovery and monitoring app that gives rapid device lists, basic diagnostics, and simple alerts for small networks.
- SolarWinds IP Address Manager (IPAM) Enterprise-grade IPAM that centralizes IP/DHCP/DNS management, conflict resolution, and workflow controls.
- Lansweeper An agentless asset discovery and inventory platform that builds hardware/software catalogs and integrates with ITAM/ITSM systems.
If you need to know more, explore our vendor highlight section just below, or skip to our detailed vendor reviews.
Βest network scanners & monitoring highlights
Top Feature
Real time IP address management, switch port mapping, and rogue device detection from one console
Price
Free for one subnet and one switch, Professional starts at $345 for 250 IPs and switch ports
Target Market
Network administrators in businesses of all sizes
Free Trial Length
30-day free trial
Additional Benefits:
- Provides clear visibility into IPs devices and switch ports, supports daily network monitoring
- Centralizes IPAM and switch port mapping, reduces the need for separate network tools
- Helps manage IP space and avoid conflicts, spots unexpected changes across subnets
- Scales from free single subnet to large deployments, backed by ManageEngine for support
Features:
- Scans IPv4 and IPv6 subnets, finds active unused and conflicting IPs
- Builds device inventory with IP MAC hostname and vendor details
- Monitors DHCP scopes in real time, tracks IP pool usage and prevents exhaustion
- Maps devices to switch ports with IP MAC and VLAN details
- Detects rogue devices and scans ports, includes Ping TraceRoute SNMP DNS and MAC tools
Top Feature
Automatic network discovery with continuous monitoring, unifies scanning and visibility
Price
Starts at $179 per month, for 50 devices
Target Market
Small medium and large organizations, need comprehensive network visibility and monitoring
Free Trial Length
30-day free trial
Read more ▼
Top Feature
Automated device discovery and IP visibility, tied to continuous network monitoring
Price
Pro edition starts at $42 per month
Target Market
SMBs MSPs and large enterprises, need unified network visibility
Free Trial Length
30-day free trial
Read more ▼
Top Feature
Security oriented network discovery, evaluates every device for vulnerabilities
Price
Available in Professional, Enterprise, and Free editions, with annual subscription pricing from $695 per year
Target Market
Teams where network discovery must be paired with security assessment
Free Trial Length
30-day free trial
Read more ▼
Top Feature
Deep host and port interrogation, reveals services versions and likely attack paths
Price
Free
Target Market
Organizations or users who need in depth insight into their networks
Free Trial Length
Free and open source
Read more ▼
Top Feature
Ultra fast TCP port scanning, maps huge address ranges in minutes
Price
Free
Target Market
ISPs large organizations security teams and researchers
Free Trial Length
Free and open source
Read more ▼
Top Feature
Fast low overhead IP range scanning, shows live hosts and open ports
Price
Free
Target Market
SMBs educators and home users, need a fast way to see connected devices
Free Trial Length
Free and open source
Read more ▼
Top Feature
Mobile-first device discovery, quick diagnostics, optional always-on monitoring via Fingbox or Agent
Price
Free for basic network management, paid version starts at $39
Target Market
Home users, small business owners, IT professionals
Free Trial Length
Free trial via mobile purchase only, 7-day trial period
Read more ▼
Top Feature
Centralizes IP, DNS, DHCP management in Orion, replaces spreadsheets with automation
Price
Not publicly listed, contact sales for a custom quote
Target Market
Medium to large enterprises with hybrid networks
Free Trial Length
30-day free trial
Read more ▼
Top Feature
Automates asset discovery and inventory, delivers centralized visibility across diverse IT environments
Price
Free plan for up to 100 assets, paid plans from €219/month, billed annually
Target Market
Mid-sized to large organizations needing centralized visibility of all IT assets
Free Trial Length
Read more ▼
Key points to consider before purchasing an IP & network scanner
- Scope and scale: Think about the size of your network. Are you scanning a small home setup, a corporate LAN, or multiple subnets across regions?
- Depth of analysis: Decide whether you need to see which devices are online or want full details, such as open ports, running services, and OS information.
- Integration and automation: Pick a scanner that fits smoothly into your current setup. It should work with the tools you already use and support automation through scripts or APIs.
- Ease of use: Pick a tool that fits your comfort level. Command-line options give you more control, while visual tools with dashboards and reports are easier to use.
- Cost and licensing: Find the right balance between your budget and what you need. Open-source scanners are flexible and often free, but paid versions usually come with dedicated support, advanced features, and scalability for larger networks.
- Support and community: A strong user base or responsive vendor makes troubleshooting and learning much easier for you.
To dive deeper into how we incorporate these into our research and review methodology, skip to our detailed methodology section.
The Best Network Scanners & Monitoring Software
1. ManageEngine OpUtils (FREE TRIAL)
Best For: Network administrators in businesses of all sizes who need clear visibility and control over their network.
Price: Free for one subnet and switch; pro version starts at $345 for 250 IPs and switch ports.

ManageEngine OpUtils is a toolkit that empowers your IT team to monitor network activity. It provides a clear view of IP addresses, connected devices, and switch ports, so administrators can see how the network is organized and where everything resides. It offers a unified console that simplifies IP address management (IPAM) and switch port mapping.
The name “OpUtils” is short for “Operations Utilities.” It reflects the tool’s purpose as a collection of utilities that support day-to-day network and IT operations. Rather than being a single-purpose scanner, it bundles multiple operational tools, such as Ping, SNMP, TraceRoute, DNS, MAC resolvers, and port scanners, into a single platform.
OpUtils works across multiple subnets and pulls in details from DHCP, DNS, and SNMP to keep information accurate. As an IP scanner, OpUtils checks entire subnets or address ranges to see which IPs are active, unused, or conflicting. During each scan, it identifies devices and collects basic information such as their IP addresses, MAC addresses, and hostnames. Scanning entire subnets and collecting device information makes it easier to manage IP space, avoid conflicts, and spot unexpected changes.
ManageEngine OpUtils comes in two main editions: a Free Edition for basic network scanning and IP management on a single subnet and switch, and a Professional Edition that unlocks all tools for complete IP address management, switch-port mapping, rogue device detection, and more.
OpUtils Key Features:
- IP Address Scanning: Discovers all IPv4 and IPv6 addresses in a subnet, identifies active and unused IPs, and detects conflicts.
- Device Discovery: Collects details such as IP addresses, MAC addresses, hostnames, and vendors to build an accurate inventory of connected devices.
- DHCP Scope Monitoring: Tracks IP pool usage in real time to ensure efficient allocation and prevent exhaustion.
- Port Scanning: Scans devices for open, closed, or filtered TCP/UDP ports to identify running services and potential vulnerabilities.
- Switch Port Mapping: Maps devices to specific switch ports, showing IP, MAC, and VLAN details for easier troubleshooting and tracking.
- Rogue Device Detection: Identifies unauthorized devices on the network and triggers alerts for potential threats.
- Network Utility Tools: Provides additional tools like Ping, TraceRoute, SNMP utilities, DNS resolver, and MAC resolver for diagnostics and troubleshooting.
Unique Buying Proposition
The single most compelling reason to choose ManageEngine OpUtils over competitors is its ability to provide real-time visibility and network management from a single platform. It integrates over 30 network management tools, which reduces the need to use multiple separate applications.
OpUtils is developed by ManageEngine, a company with extensive experience in IT and network management. This, in our opinio,n signals reliability, trust, and long-term support. It also reassures businesses that the product is enterprise-ready, scalable, and able to keep pace with evolving network challenges.
Feature-In-Focus: IP address management, switch‑port mapping, and rogue-device detection
ManageEngine OpUtils emphasizes IP address management, switch‑port mapping, and rogue-device detection as its standout features. This trio of features addresses the most common and critical challenges in network management: IP tracking, physical connectivity, and security.
Why do we recommend OpUtils?
We recommend ManageEngine OpUtils because it provides a complete, real-time view of your network devices and their connections. Features such as automated IP address management, switch-port mapping, port scanning, and rogue-device detection enable you to quickly see which devices are active, where they’re connected, and whether anything unusual is happening.

Who is OpUtils recommended for?
We recommend OpUtils for network administrators in small to medium businesses, as well as larger enterprises who need both visibility and control. If you manage multiple subnets, switches, or a growing number of devices, this tool helps you track IP usage, detect unauthorized devices, and manage your network efficiently. Even if your network is smaller, the free edition provides a practical way to monitor and manage a single subnet.
Pros:
- Comprehensive network visibility: Monitor IP addresses, switch ports, and devices from a single dashboard.
- Automated management: Supports automated IP scanning, port mapping, and rogue-device detection.
- Scalable for different environments: Suitable for small networks as well as large enterprise deployments.
- Backed by ManageEngine: Developed by a company with decades of IT management experience.
Cons:
- Limited free edition: The free version is restricted to one subnet and one switch, which may not meet the needs of growing networks.
Get started with a 30-day free trial.
EDITOR'S CHOICE
ManageEngine OpUtils is my top pick for a network scanner that provides network analysis and management because this package includes three systems: A port scanner, a switch port mapper, and an IP address manager. The IP address manager (IPAM can form part of a full DDI service, interfacing with your DHCP server and DNS server to reconcile IP addresses in use with address pools and hostname mappings. The switch port mapper identifies which device is connected to which port on a switch. The port scanner deals with logical ports on all of your devices. It will list all open ports, letting you see where your security can be tightened by closing unused ports. The full package has lots of extra freebies that enhance those three central services. ManageEngine also provides a network device monitor, called OpManager, and a network traffic monitor, called the NetFlow Analyzer. If you buy all three units, they all slot together into a single dashboard, giving you full visibility of network activity and providing alerts that will warn you if devices are in error or are overloaded.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/products/oputils/download.html
OS: Windows Server, Linux, and AWS
2. Paessler PRTG Network Monitor (FREE TRIAL)
Best For: Organizations that need comprehensive network visibility and monitoring.
Price: $179 per month for 50 devices
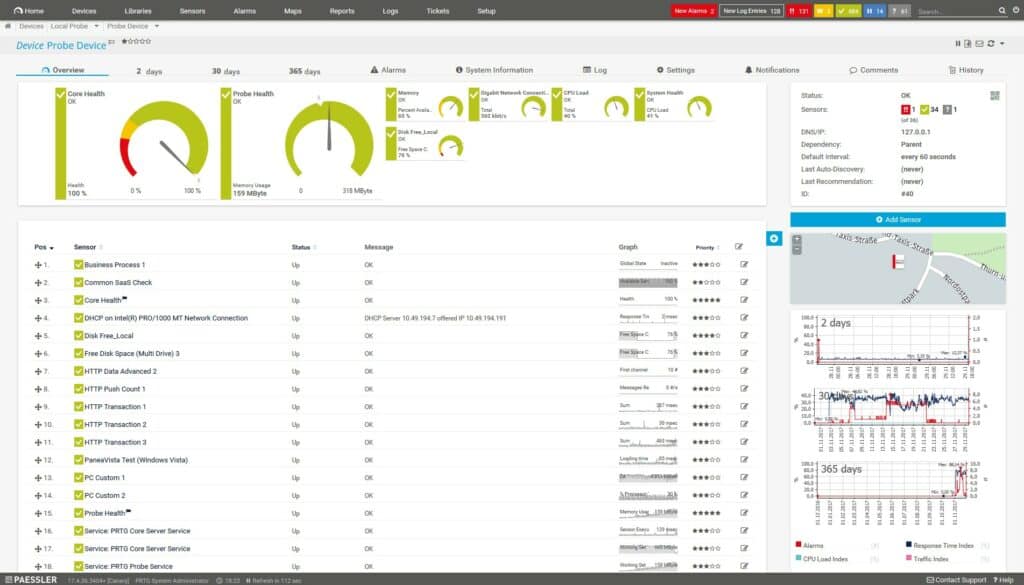
PRTG Network Monitor is a widely used network monitoring platform that offers continuous insight into system performance and availability. In addition to its broader monitoring functions, it can operate as an IP and network scanner by automatically discovering devices within specified IP ranges, identifying addresses and ports, and using protocols such as ICMP and SNMP to determine device status.
It also organizes discovered devices into structured views and applies sensors to track metrics such as bandwidth, service availability, and traffic levels. You can use PRTG to keep an updated inventory of your connected devices, detect unauthorized equipment, and observe network behavior over time.
However, if your only requirement is basic IP and network scanning PRTG may be more than you need. Deploying PRTG solely for simple IP scanning can be excessive in cost, configuration time, and system overhead. In such cases, simpler tools such as ManageEngine OpUtils Free Edition, Angry IP Scanner, or Advanced IP Scanner may be a more practical choice.
PRTG Key Features:
- Automatic Network Discovery: Scans IP ranges and subnets to identify devices, hostnames, MAC addresses, and open ports.
- ICMP (ping) monitoring: Detects live hosts, response times, and availability.
- SNMP-based Data Collection: Gathers device status and basic operational information from network hardware.
- Port Scanning: Checks TCP/UDP ports to identify running services and assess accessibility.
- Device Classification and Grouping: Organizes discovered devices into structured trees for easier management.
- Continuous Updates: Reflects network changes automatically as devices appear, disappear, or change state.
- Sensor Deployment: Creates sensors to monitor traffic, bandwidth, uptime, and service behavior after discovery.
Unique Buying Proposition
The unique buying proposition of PRTG, as an IP and network scanner, is its ability to go beyond simple discovery and integrate scanning directly into a complete, continuous monitoring framework. PRTG links discovery with real-time sensors, historical data, alerts, and performance metrics.
Each device discovered during a scan can be monitored immediately for bandwidth, uptime, traffic, and service status. As a customer, you get a single system that handles device discovery and ongoing monitoring together, reducing the need for multiple tools and offering deeper insight than basic scanners.
Feature-In-Focus: Automatic network discovery
The most prominent feature of PRTG as an IP and network scanner is its automatic network discovery, which continuously scans defined IP ranges and subnets to identify devices, their IP addresses, open ports, and basic status information. As a result, you can quickly detect new or unauthorized devices, understand your networkis structure, and spot potential issues early.
Why do we recommend PRTG?
We recommend PRTG for its automatic device discovery and continuous monitoring capabilities, which enable you to identify IP addresses, MAC addresses, hostnames, and open ports, and to track bandwidth, uptime, traffic patterns, and service availability in real time.
Its ability to maintain an up-to-date network map, automatically detect changes, and consolidate monitoring into a single platform provides more comprehensive operational insight than basic scanning tools.

Who is PRTG recommended for?
The target market for PRTG Network Monitor includes small, medium, and large organizations that need comprehensive visibility and monitoring of their IT infrastructure. Organizations with multiple subnets, distributed networks, or critical systems that demand real-time status updates and performance tracking will benefit most.
Pros:
- Customizable alerts and notifications: Allow teams to respond quickly to performance issues or network changes.
- Scalable for growing networks: Can handle small offices up to large enterprise environments with multiple sensors.
- Detailed reporting and analytics: Provides historical data and trend analysis for planning and optimization.
- Vendor support and reliability: Backed by Paessler, a well-established company with ongoing updates and support.
Cons:
- Complex setup for small deployments: Initial configuration can be time-consuming and may require technical expertise.
You can download the 30-day free trial.
3. Site24x7 Network Monitoring (FREE TRIAL)
Best For: SMBs with limited IT resources to large enterprises and distributed networks
Price: Pro edition starts at $42 per month

Site24x7 Network Monitoring functions as an IP and network scanner. It can automatically scan IP ranges and subnets to discover devices, collect details such as IP addresses and interface status, and maintain an updated inventory using SNMP and other protocols. It also supports IP address tracking and helps teams understand how addresses are allocated and used across the network.
You can use Site24x7 to maintain an accurate, real-time view of all connected devices, detect new or unauthorized endpoints, and document networks as they evolve. Although Site24x7 can be used solely for scanning, its broader monitoring and analytics capabilities may exceed what is necessary if the goal is limited to simple device or IP discovery. In that case, a lighter-weight or simpler tool might be more efficient.
Site24x7 Key Features:
- Automated Network Discovery: Scans your environment automatically and identifies devices without manual effort.
- Extensive Device Support: Monitors over 11,000 device types from 450+ vendors using built-in templates or custom profiles.
- Multi-protocol Monitoring: Uses SNMP, WMI, and API integrations to track traditional devices and SD-WAN technologies, including Cisco Meraki and ACI.
- Traffic Analysis: Monitors network flows via NetFlow, JFlow, sFlow, IPFIX, NetStream, and AppFlow to show bandwidth usage and traffic patterns.
- Real-time Visibility: Detects new devices, removed endpoints, bandwidth spikes, non-compliant configurations, and potential risks as they occur.
- Cloud-based Access: Provides secure, anywhere access to network data through a fully cloud-hosted platform.
- Custom Dashboards and Maps: Offers visual dashboards, topology maps, and configurable reports to present data in the format you prefer.
- Security Insights: Flags rogue devices, misconfigurations, and other security issues within the network.
Unique Buying Proposition
Site24x7’s unique buying proposition as an IP and network scanner is its ability to deliver automated device discovery, IP address tracking, and continuous performance monitoring in a single unified platform.
It links each discovered asset to live performance metrics, interface statistics, alerts, status checks, and topology insights to create an operational workflow that many standalone scanners cannot offer. The result is a broader, more actionable view of the environment, which differentiates Site24x7 from tools that only inventory or scan.
Feature-In-Focus: Automated device discovery and IP address management
Site24x7 consistently places automated discovery, topology mapping, and IP visibility at the center of its network-monitoring capabilities.
On the product pages, these elements are presented before other technical features, and many functions (interface monitoring, performance metrics, alerts, bandwidth tracking) depend on this discovery layer.
Why do we recommend Site24x7?
We recommend Site 24×7 because it provides continuous network monitoring, historical performance data, traffic and interface insights, and real-time alerts. The scanning process is what initially discovers and identifies all devices, IP addresses, and network interfaces on your network. The continuous monitoring, traffic insights, and alerts turn that static snapshot into actionable, real-time network intelligence.

Who is Site24x7recommended for?
Site24x7 is aimed at a wide range of organizations, from SMBs with limited IT resources to large enterprises and distributed networks that require unified visibility across servers, devices, and SD‑WAN links.
It is also suitable for MSPs and IT teams managing multiple client networks, thanks to its cloud-based deployment, scalable architecture, and multi-vendor support.
Pros:
- Increased efficiency: Automated discovery and monitoring reduce manual work and save time.
- Reduced downtime: Real-time monitoring and proactive issue identification help prevent outages.
- Improved security posture: Detects rogue devices, vulnerabilities, and unauthorized changes.
- Proactive issue identification: Alerts and notifications help you address potential problems before they affect operations.
- Advanced reporting features: Offers detailed insights into network performance, traffic, and IP usage.
Cons:
- Complex setup for smaller networks: Initial configuration and device template matching can require technical expertise.
The Network Monitor is part of the Site24x7 Infrastructure package, which is available for a 30-day free trial.
ManageEngine Vulnerability Manager Plus (FREE TRIAL)
Best For: Use cases where network discovery needs to be paired with a security assessment.
Price: Available in Professional, Enterprise, and Free editions, with annual subscription pricing from $695 per year for 100 workstations, single technician in the Professional edition and $1,195 per year for 100 workstations, single technician in the Enterprise edition, while the Free edition supports up to 20 workstations and 5 servers at $0; add-ons such as Failover Server (from $1,195) and Secure Gateway Server ($300), and higher slabs are provided under flexible, quote-based pricing.

ManageEngine Vulnerability Manager Plus (VMP) is a vulnerability management platform that helps you identify, assess, and remediate security risks across endpoints and network devices. It is primarily aimed at strengthening an organization’s security posture rather than managing network operations or performance.
VMP qualifies partly as an IP/network scanner because it performs network-based discovery to identify devices within defined IP ranges or subnets. However, this discovery or scanning primarily serves its core purpose of identifying vulnerabilities, misconfigurations, missing patches, insecure firmware, and other security risks. It does not function as a traditional network scanner designed to map topology, track bandwidth, or monitor live network performance.
ManageEngine Vulnerability Manager Plus Key Features:
- Network Device Discovery: Scan IP ranges or subnets to identify network devices, including routers, switches, firewalls, and other connected hardware.
- Device Inventory: Collect detailed information about discovered devices, including vendor, model, OS/firmware version, and open ports.
- Vulnerability Assessment: Identify security vulnerabilities, misconfigurations, open ports, and outdated firmware on network devices.
- Credentialed Scanning: Use SNMP, SSH, or other credentials to perform authenticated scans for more accurate vulnerability detection.
- IP and Network Mapping for Security: Build a managed inventory of network devices to visualize the attack surface and maintain security visibility.
- Integration with Patch Management and Remediation: Link device discovery and vulnerability detection with automated patching workflows for endpoints and network devices.
Unique Buying Proposition
As an IP/network scanner, ManageEngine Vulnerability Manager Plus’ unique selling proposition is its security-focused approach to network discovery. VMP uses its scanning capabilities to immediately assess the security state of every discovered asset. Each IP or device identified through scanning is automatically evaluated for vulnerabilities, misconfigurations, risky ports, missing patches, weak settings, and outdated firmware.
Feature-In-Focus: Security-oriented device discovery
As an IP/network scanner, the feature in focus for ManageEngine Vulnerability Manager Plus is its security-oriented device discovery. VMP’s discovery/scanning feature is oriented around security. It discovers devices to build an inventory, then assesses each device for vulnerabilities rather than simply mapping the network or monitoring performance.
Why do we recommend ManageEngine Vulnerability Manager Plus?
We recommend ManageEngine Vulnerability Manager Plus because it ties device discovery directly to security analysis. VMP is appropriate in situations where you need visibility into both the devices on your network and the security issues affecting them. Its documentation and feature set show that it delivers deeper, security-focused insight than standard network-scanning tools.

Who is ManageEngine Vulnerability Manager Plus recommended for?
ManageEngine Vulnerability Manager Plus is suitable for use cases where network discovery needs to be paired with a security assessment. It also aligns well with security-driven workflows, such as compliance audits, attack surface reduction, and continuous vulnerability management. In these cases, asset visibility and security analysis must operate together rather than as separate steps.
Pros:
- Integrated discovery and security context: VMP identifies network assets and immediately evaluates them for vulnerabilities, missing patches, misconfigurations, and risky software.
- Broad endpoint coverage: It scans Windows, macOS, and Linux systems across on‑premises and remote environments, offering consistent visibility.
- Operational depth: Patch automation, configuration assessment, and threat‑based prioritization extend its value beyond basic IP discovery.
Cons:
- More complex to deploy than simple scanners: Because it includes patching, configuration checks, and agent‑based analysis, setup and ongoing management require more effort.
ManageEngine Vulnerability Manager Plus is offered on a 30-day free trial.
5. Nmap
Best For: Organizations or users who need in-depth insight into their networks
Price: Free and open-source

Nmap (Network Mapper) is an open-source utility that allows you to explore networks, discover hosts, and identify services running on them. Nmap uses raw IP packets to scan networks and analyze responses from devices. It also performs topology mapping with NSE scripts for automation and light checks. Its outputs drive target prioritization, exploit selection, and risk assessment.
When it comes to active scanning, Nmap dominates that role due to its ability to reveal reachable services, specific software versions, and likely attack paths. The result is an asset inventory listing open ports, running services, versions, and potential vulnerabilities to guide testing.
However, since the project does not include a commercial service-level agreement (SLA), you will need to handle tasks such as validation, fine-tuning, and integrating additional tools or support on your own to meet enterprise-level requirements.
Nmap Key Features:
- Host Discovery: Quickly finds which IPs are alive using ICMP, ARP, or TCP probes.
- Port Scanning Variety: Multiple scan types let you detect open, closed, or filtered ports and adapt to firewalls or privilege limits.
- OS Fingerprinting: Infers the target operating system and device type from TCP/IP behavior to facilitate the selection of applicable exploits.
- Nmap Scripting Engine (NSE): Runs modular Lua scripts for discovery, vulnerability checks, brute force attempts, and custom tests.
- GUI Front-end (Zenmap): Provides visual profiles, saved scans, and a more straightforward user interface for analysts who prefer a graphical interface.
- Service & Version Detection: Probe open ports to identify applications and versions, enabling you to map them to known vulnerabilities.
- Extensible and well-documented: Nmap has a strong user community, frequent updates, and detailed documentation. You can rely on its results and easily expand its features when needed.
Unique Buying Proposition
Nmap has a long history of development and an open-source model. It has been maintained and refined over several decades by a global community, with ongoing updates to support new network technologies and security standards. Because it’s scriptable, highly tunable, and works across different platforms and protocols, you can adapt it to virtually any network environment.
Feature-In-Focus: Detailed host and port interrogation
Nmap excels at identifying live hosts, enumerating open ports, determining service versions, and inferring operating systems, with a level of depth and precision that many scanners cannot match. This capability is the foundation of its long‑standing reputation.
Why do we recommend Nmap?
We recommend Nmap because it provides deep insight into your network. It shows active hosts, open ports, running services, and even operating systems. Its open-source nature, flexibility, and automation features make it a powerful and cost-effective tool.
Anyone who needs precise, customizable scans will find Nmap a proven, reliable choice, backed by a strong, trusted community.

Who is Nmap recommended for?
Nmap is best suited for organizations or users who need in-depth insight into their networks—particularly IT administrators, cybersecurity experts, and advanced users with a solid understanding of networking basics.
Nmap is accessible enough for newcomers to learn through tutorials and basic commands, but its full power is realized through experience.
Pros:
- Comprehensive network visibility: Provides a detailed view of your network devices, services, and potential vulnerabilities.
- Cost-effective: Nmap is free and does not require a license.
- Highly configurable: You can tailor scans to your specific requirements with a wide range of options and commands.
- Cross-platform compatibility: Works on Linux, Windows, FreeBSD, OpenBSD, Solaris, Mac OS X, and more.
Cons:
- Limited traffic observation: Nmap is predominantly active and won’t monitor traffic trends without repeated scans or external capture tools.
- Slow UDP scans: UDP scans can be slow and may miss services due to rate limits and ICMP filtering.
- Support limitations: Community support is strong but may not meet the reliability or responsiveness of enterprise-level SLAs.
6. Masscan
Best For: ISPs, large organizations, security teams, and researchers who need to scan massive networks.
Price: Free and open-source

Masscan is a high‑performance, Internet‑scale TCP port scanner built to probe very large address ranges quickly. It sends raw, asynchronous packets from the host to detect open TCP ports across millions of IPs faster than many traditional scanners.
The project is open‑source and community‑driven. The main code and issue tracking for Masscan are hosted on GitHub, where it’s maintained by its creator, Robert David Graham, along with help from the open-source community. Updates don’t follow a fixed schedule; they mainly focus on fixing bugs, improving speed, and refining how the tool handles protocols. There’s no official support or service agreement, but you can get help or report problems through GitHub and community forums.
Best practice is to use it for fast bulk discovery, then feed the results into a more in-depth scanner, such as Nmap, for service fingerprinting and validation.
Masscan Key Features:
- Extreme scan speed: It can probe millions of IP addresses per second when tuned, allowing you to scan very large ranges quickly.
- Asynchronous raw-packet engine: It sends and receives packets directly for high throughput with low CPU overhead.
- TCP SYN focused: Optimized for fast TCP port discovery (primary use case), not full service/OS fingerprinting.
- Flexible targeting: Large CIDR ranges, port lists, exclusions, and randomized scan ordering for broad discovery.
- Simple output formats: XML/JSON/grepable outputs and options to save/resume scans for automation.
- Integration-friendly: Results are easily feedable into tools like Nmap or parsers for follow-up analysis.
- Low resource footprint: Designed to run on modest hardware while driving high network I/O.
Unique Buying Proposition
Masscan’s unique value is raw, internet-scale speed for discovery. It identifies open TCP ports across huge address ranges far faster than other scanners. You can map a large attack surface in minutes, not hours.
However, Masscan provides limited service/version detection, can be noisy (requiring authorization), and requires root/administrator privileges for raw sockets.
Feature In Focus: Ultra‑fast, large‑scale port scanning
Masscan enables security practitioners, network administrators, or researchers to perform rapid reconnaissance and large‑scale network‑wide scanning. It can quickly build a map of reachable hosts and open ports across very large subnets or even global IP ranges.
Why do we recommend Masscan?
We recommend Masscan when you need to quickly map an ample address space. I’ve used it in reconnaissance pipelines and large-scale inventory runs, and found it to be fast, efficient, and reliable for large-scale discovery.
Its raw, asynchronous packet engine allows you to probe millions of IP addresses per second while keeping CPU usage low. In fact, the name Masscan comes from its core purpose: mass scanning.

Who is Masscan recommended for?
Masscan is suitable for ISPs, large organizations, security teams, red teams, CERTs, and researchers who need to quickly scan large networks. However, to use it effectively, you must be comfortable with command-line tools and have the necessary permissions to run scans safely.
Pros:
- Low system impact: The asynchronous raw-packet engine offloads work to the network, resulting in a low CPU footprint.
- Lightweight and versatile: Single binary with few dependencies, making it easy to script and run on many hosts.
- High performance: Can scan millions of IPs per second when properly tuned.
Cons:
- No passive monitoring: Provides only active, point-in-time scans without continuous network visibility.
- Limited detail on services: Finds open TCP ports but gives minimal banner or OS information.
- Potential network impact: Improper scan rates or target selections can cause outages or trigger blacklisting.
7. Angry IP Scanner
Best For: SMBs, educators, and home users who need a fast way to check what’s connected to their network.
Price: Free and open-source
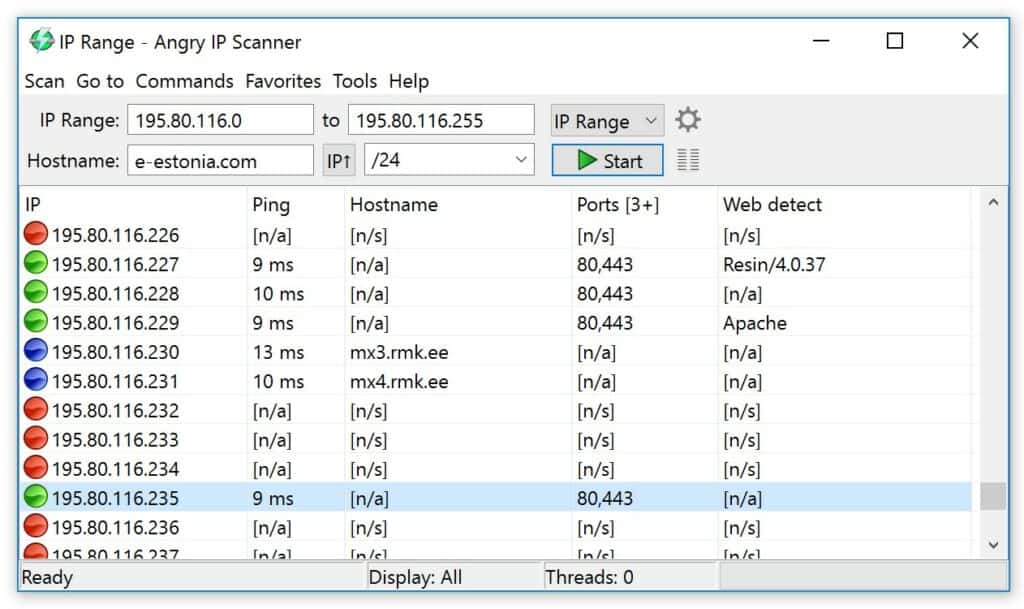
Angry IP Scanner is a lightweight, open-source network scanner with a simple GUI that quickly discovers live hosts, resolves hostnames, and checks common ports across IP ranges. It is Java-based and cross-platform, portable (no install required), and easy to use for quick inventories, troubleshooting, or small-scope audits.
The name “angry” in Angry IP Scanner isn’t literal. It serves as a branding element to signal speed and impact. In other words, it is a cheeky way to say the tool moves fast and hits ranges hard. It’s a no-nonsense scanner that blasts through IPs, returns quick results, and keeps things simple.
Angry IP Scanner Key Features:
- Fast parallel Scanning: Scans multiple IPs simultaneously for quick results.
- Cross-platform Java App: It runs on Windows, macOS, and Linux with a single portable binary.
- Simple IP Range Input: Scan single IPs, ranges, or CIDR blocks with minimal setup.
- Host Discovery: Utilizes pings and ARP checks to quickly locate live hosts.
- Port Scanning: Probes standard ports or custom port lists to show open services.
- Low Setup Overhead: It comes with minimal configuration options that appeal to non-experts.
Unique Buying Proposition
The unique buying proposition of Angry IP Scanner is its simplicity, speed, and ease of use. It does not need installation, admin rights, or complex dependencies.
The software is perfect for quick audits, troubleshooting connectivity issues, or verifying device inventories in environments where deploying heavier tools like Nmap or SolarWinds is not feasible.
Feature-In-Focus: Fast, low‑overhead IP range scanning
Angry IP Scanner quickly identifies active hosts using ping sweeps, gathers essential device details such as IP addresses, hostnames, and MAC addresses, and detects open ports. Network administrators or IT users can rapidly map and assess their network without overloading systems.
Why do we recommend Angry IP Scanner?
We recommend Angry IP Scanner because it delivers quick, reliable visibility. When you need to confirm what’s online, check open ports, or identify rogue devices, it gives you instant feedback in a clean, visual format.
Its simplicity saves time and reduces user error, and makes basic network assessment accessible to a broader range of users, even those with limited technical experience.

Who is Angry IP recommended for?
Angry IP Scanner is suitable for IT technicians, network administrators, small business owners, educators, and even home users who need a quick way to see what’s connected to their network.
It is easy enough for beginners to get started right away, yet still robust and reliable enough for IT professionals to keep in their everyday toolkit.
Pros:
- Fast Scanning: Fast parallel scans for quick results on LANs.
- Cross-Platform & Portable: Runs on Windows, macOS, and Linux with no installation required.
- Plugin Extensibility: Supports plugins for additional checks such as SNMP, HTTP title, and NetBIOS.
- Flexible Use Cases: Useful for ad-hoc troubleshooting, small inventories, and educational environments.
Cons:
- Limited Detection Depth: Provides less detailed service/version and OS detection compared with Nmap.
- Not Enterprise-Scale: Unsuitable for large-scale scans or continuous monitoring.
- Potential IDS/IPS Triggers: Aggressive scanning may trigger security systems on sensitive networks.
- Limited Automation: Offers minimal automation compared with CLI-based tools, though exports provide some flexibility.
Angry IP Scanner is worth a look for enterprises that need a free network scanning solution. The platform is available on Windows, Mac, and Linux. You can download the software for free from this link here.
8. Fing
Best For: Home users, small business owners, and IT professionals
Price: Free for basic network management. Paid version starts at $39

Fing is a mobile-first, user-friendly network scanner and monitoring platform that you can deploy for quick device discovery, simple diagnostics, and optional continuous monitoring through Fingbox or Fing Agent. It combines cloud-backed features with local tools for straightforward network visibility.
Fing began as a lightweight network scanner and has expanded into a product family that includes the Fing mobile app (iOS/Android) for on-the-go scans, Fing Desktop for scheduled tests, Fing Agent or Raspberry Pi agents for always-on monitoring, and Fingbox hardware for local, persistent oversight and IoT controls. The platform connects these components through a cloud dashboard and a Local API for automation.
When I pointed my phone at a Wi-Fi network, Fing filled the screen in seconds with every connected device: IP address, MAC address, vendor fingerprint, and even quick hints of open ports and basic services. You can also run basic diagnostic tools, such as ping, traceroute, Wake-on-LAN, and speed tests, directly from the app. With Fingbox or Agent enabled, the platform provides continuous checks, device history, and options to pause or block specific endpoints.
However, I find Fing to be intentionally surface-level. It delivers fast discovery but lacks deep inspection features such as detailed service or version fingerprinting found in tools like Nmap or enterprise vulnerability scanners. Some advanced functions are paywalled, and continuous monitoring depends on Fingbox hardware. It’s best suited for quick network assessments rather than full-scale analysis.
Fing’s Key Features:
- Device Discovery: Instantly identifies all devices connected to your network, showing their IP addresses, MAC addresses, device names, and manufacturers.
- Network Scanning: Detects new, unknown, or suspicious devices in seconds.
- Ping and Traceroute Tools: Helps you test connectivity and trace network routes directly from the app.
- Wake-on-LAN: Enables you to wake compatible devices on your network remotely.
- Alerts and History: Tracks when devices join or leave your network, with optional notifications and activity history.
- Fingbox/Agent Integration: Enables continuous monitoring, parental controls, and device blocking or pausing.
- User-Friendly Interface: Mobile-first design with clear visuals and easy navigation for both beginners and pros.
Unique Buying Proposition
Fing’s unique value is its ability to make network visibility instant, intuitive, and accessible to anyone. You don’t need to be a network engineer to use it; just open the app, and within seconds you can see every device on your network, along with key details such as IP addresses, MACs, and vendors.
Why do we recommend Fing?
We recommend Fing because it offers fast, user-friendly network visibility. It bridges the gap between simplicity and utility, and gives you quick insights to spot unknown or suspicious devices. You can scan your network right from your phone and get instant scan results.

Who is Fing recommended for?
Fing’s target market includes home users, small business owners, and IT professionals who need quick, reliable visibility into their networks. Because it is easy to use and mobile-friendly, Fing appeals to both non-technical users and tech-savvy users who want a lightweight, on-the-go diagnostic companion.
Pros:
- User-friendly interface: Easy to use, with a clean and intuitive interface suitable for all skill levels.
- Quick network discovery: Fast and accurate device discovery with instant network visibility.
- Cross-platform accessibility: Works across mobile and desktop platforms for flexible access.
- Enhanced monitoring options: Fingbox or Agent adds continuous monitoring, alerts, and parental/IoT controls.
- Cloud synchronization: Cloud sync keeps your scan history and settings available on all devices.
Cons:
- Limited depth: Surface-level scanning; lacks deep service or vulnerability analysis.
- Feature restrictions: Some advanced features are locked behind paid plans or require Fingbox hardware.
- Limited customization: Limited customization and automation capabilities compared to Nmap and similar tools.
- Privacy considerations: Relies partly on cloud processing, which may raise privacy or data-handling concerns for sensitive networks.
9. SolarWinds IP Address Manager (IPAM)
Best For: Medium to large enterprises with hybrid networks
Price: Not publicly listed

SolarWinds IP Address Manager (IPAM) is a centralized tool for managing IP addresses, DNS, and DHCP from one interface. It’s part of the SolarWinds Orion Platform and is meant to replace manual spreadsheets with an automated, structured system. The software helps you discover subnets, allocate and reclaim addresses, track utilization, and detect conflicts. It can integrate directly with your existing DHCP and DNS infrastructure for consistency and automation.
In practice, deploying IPAM requires planning, especially in larger environments. You will need to size hardware correctly and choose a license that matches your network scale, as pricing increases with the number of managed IPs and nodes. Small networks may find the entry cost higher than lightweight alternatives.
However, as with any enterprise tool, staying current with ongoing maintenance, such as updates, configuration checks, and integration management, is also necessary to keep it running reliably.
SolarWinds IPAM Key Features:
- Automated IP Tracking: Automatically discovers and manages IP addresses across both on-premises and cloud networks.
- Unified DHCP and DNS Management: You can control DHCP and DNS settings from one console for configuration consistency.
- Automatic Conflict Detection and Resolution: Continuously monitors your network to identify and resolve IP address conflicts.
- IP Utilization Reporting: Generates detailed reports on IP allocation and usage so you can better plan capacity, reclaim unused addresses, and optimize overall resource utilization.
- Infoblox Integration: Seamlessly integrates with Infoblox to provide a unified, centralized IP management system across multi-vendor or hybrid networks.
- Customizable Alerts and Notifications: Allows you to set up personalized alerts for IP-related events.
Unique Buying Proposition
SolarWinds IPAM uniquely stands out for its seamless integration with the broader SolarWinds ecosystem, particularly the Orion Platform. If you already use SolarWinds tools like Network Performance Monitor (NPM) or Server & Application Monitor (SAM), IPAM connects seamlessly. You can see IP address data in the same dashboards where you monitor uptime, performance, and alerts, which saves time and reduces blind spots.
From experience, this integration makes a real difference when troubleshooting. You can use it to pinpoint the cause of an outage and trace everything from a device’s IP assignment to its performance. That’s why teams already using SolarWinds often keep IPAM as part of their toolkit.
Feature-In-Focus: Integrated IP management
SolarWinds IPAM emphasizes the ability to manage and monitor the full IP space of a network, including addresses, subnets, and DNS/DHCP integration. It enables automated network scanning (IPv4 and IPv6) on a periodic or on-demand basis to discover active IP addresses, subnets, and connected devices.
Why do we recommend SolarWinds IPAM?
We recommend SolarWinds IPAM because it helps you manage, track, and prevent conflicts across your network. From experience, the real challenge in enterprise networks isn’t discovery alone. It keeps everything organized and coordinated across multiple DHCP and DNS servers. IPAM automates these tasks, reduces errors, and saves time.
Its integration with the Orion Platform is another big advantage. You can see IP data alongside device performance and network health. Taken together, these capabilities make IPAM a practical, reliable choice for teams managing large or hybrid networks.

Who is IPAM recommended for?
The target market for SolarWinds IPAM is primarily medium- to large-sized enterprises and organizations with hybrid networks spanning on-premises and cloud environments. It is aimed at network administrators, IT operations teams, and infrastructure managers who need centralized control over IP addresses, DHCP, and DNS across multiple sites or vendors.
Pros:
- Orion platform integration: Correlate IP data with device performance, network health, and alerts in a single view.
- Proactive network management: Provides detailed utilization reports and customizable alerts for proactive network management.
- Workflow automation: Allows integration with other systems and automated workflows via APIs for efficiency.
Cons:
- Cost considerations: The cost increases with the number of IPs and nodes, which can make it pricey for smaller networks.
- Complex deployment: Requires planning and technical expertise.
- Dependency on network services: Needs properly functioning DHCP/DNS servers and correct network credentials to operate thoroughly.
10. Lansweeper
Best For: Mid-sized to large organizations that need centralized visibility of all IT assets
Price: From €219/month (billed annually)

Lansweeper is a network management and IT asset discovery tool that performs automatic scanning, inventory, and management of devices on a network. It can identify hardware, software, and connected equipment across Windows, Linux, macOS, virtual machines, and IoT devices.
Lansweeper is considered an IP and network scanner because it discovers and maps devices across a network. It scans IP ranges and subnets, collects information such as IP and MAC addresses, and tracks connected hardware, software, and services.
Lansweeper is a commercial product with a subscription-based licensing model. Licensing is based on the number of devices or assets being managed. A free plan is available for up to 100 assets. Larger networks require paid tiers (Starter, Pro, Enterprise) depending on asset count.
Unique Buying Proposition
Lansweeper is known for being relatively easy to deploy. It works across many types of devices and operating systems, and gives detailed inventory reports. This is where it really adds value compared to other scanners, even if the features themselves aren’t completely unique.
According to the vendor, Lansweeper includes active IP range scanning through its “Active IT Discovery” feature. Its dashboard and BI-driven analytics allow users to analyze asset usage, performance, and risk metrics in more depth rather than only displaying device lists.
Feature-In-Focus: Automated network discovery
Lansweeper detects all devices on a network, including servers, workstations, network gear, IoT/OT devices, and cloud assets, using active, passive, or agent-based scanning. In return, you gain up-to-date, centralized visibility of all connected devices, which reduce blind spots, simplifies inventory management, and enhances security and compliance
Why do we recommend Lansweeper?
Many scanners can show you what’s connected, but Lansweeper goes further by tying that discovery to asset and software details. You can see not just an IP address, but who’s using the device, what software it runs, and whether it poses a risk.
It is not the fastest scanner per se, but it’s reliable for environments where inventory accuracy and ongoing management matter more than raw scan speed.

Who is Lansweeper recommended for?
Lansweeper is best suited for mid-sized to large organizations that need centralized visibility of all IT assets across complex or hybrid networks. MSPs and enterprises with diverse hardware, virtual machines, and IoT devices also use it to keep asset data accurate.
Pros:
- Comprehensive Asset Discovery: Automatically discovers a wide range of assets (physical, virtual, cloud, IoT) and pulls detailed information.
- Robust Reporting and Analytics: Provides strong reporting and analytics that support inventory, audits, and overall network visibility.
- Flexible On-Premises Deployment: Offers an on-premises option that gives you full control over your data, useful for environments sensitive to cloud storage.
Cons:
- Technical Reporting Requirements: Reporting and customization may require SQL knowledge or deeper database expertise, limiting accessibility for less technical teams.
- Limited Advanced ITAM Features: Some capabilities such as software deployment, remote patching, and full ITAM workflows—are less developed than in specialized tools.
- Potentially High Cost at Scale: Pricing can become expensive in larger environments, and smaller networks may see fewer benefits relative to cost.
Choosing a Network Scanner & Monitoring Tool
Whether you’re looking for a scanner to locate vulnerabilities or for a tool to discover connected devices, the closer you monitor your devices and potential vulnerabilities the better you’re able to protect your network and stay safe from cyber attackers.
My top picks for this list are ManageEngine OpUtils and Paessler PRTG Network Monitor for network monitoring and Acunetix for vulnerability scanning. Between them, these tools have everything you need to start maintaining an inventory of devices or scanning for weaknesses.
Our methodology for choosing IP and network scanner tools
Our methodology for selecting the best IP and network scanner tools extends beyond technical performance and feature comparison. Our approach includes:
1. Organizational Fit
We checked how easily the tool fits into your existing workflows, how quickly your team can adopt it, and whether it requires major training or process changes.
2. Vendor Strength and Innovation
We looked at the vendor’s track record, product roadmap, and ecosystem to see whether the tool will stay relevant as your network and needs grow.
3. Risk and Contract Considerations
We reviewed SLAs, data ownership, security terms, and exit options to ensure you’re protected against operational or compliance risks.
4. Long-Term Suitability
We assess whether the tool can support your ongoing needs and provide lasting value rather than just solving a short-term issue.
Broader B2B Software Selection Methodology
We evaluate B2B software using a consistent, objective framework that focuses on how well a product solves meaningful business problems at a justified cost. This includes assessing overall performance, scalability, stability, and user experience quality. We examine real-world feedback from practitioners to understand how the software behaves outside of controlled demos.
We also review vendor transparency, roadmap clarity, support responsiveness, and the pace at which meaningful improvements are released. We follow this approach in order to ensure that each of our recommendations is grounded in practical value, long-term viability, and operational impact, not marketing claims.
Check out our detailed B2B software methodology page to learn more.
Why Trust Us?
Our work is produced by a team of IT and business software professionals with extensive hands-on experience evaluating, deploying, and managing enterprise technology. We analyze software independently, using evidence-based methods and industry best practices to ensure our assessments remain unbiased and technically sound.
Our goal is to provide you with clear, reliable insights that help reduce risk, shorten evaluation cycles, and support confident decision-making when selecting complex business technology.
Network Scanners FAQs
What are 3 types of network scanning?
The three network scanning types are port scanning, network scanning, and vulnerability scanning. Port scanning identifies open ports, network scanning lists all IP addresses in use together with related device identifiers, such as hostnames, and vulnerability scanning works through a list of known system weaknesses to see if they exist in the present network.
What is a null scan?
A null scan is a probe to identify open ports. The scanning strategy gets its name because it is implemented with a TCP packet with a sequence number of 0 and no set flags. This packet is meaningless to the contacted device and so provokes an RST response. The response discloses the operating status of each responding port. This discovery technique is often used by hackers.
What are the network scanners for Bulk Extractor?
Bulk Extractor includes 24 scanners, including bulk, which activates all the 23 other scanners. Only one scanner directly relates to network data. This is the net scanner, which is a packet sniffer. Bulk scanner only searches through the device on which it is resident. It gets network packets data from virtual memory, which is those live packet traffic traveling in and out of the device. Packets are dumped to a file in libpcap format.
How do I block network scanners?
Prevent hackers from probing your network with a network scanner by installing a network firewall. The firewall should be a standalone device so that its activities don’t hijack the resources of a hosting server. Non-hardware firewall substitutes are available from cloud providers. These are called “edge services;” and they block network scanning strategies before they reach your network gateway.













