Millions of networks around the world are under constant threat from myriad types of attacks that originate from just as many sources and geographical locations. As a matter of fact, right at this moment, there are hundreds of attacks occurring every single second.
Effectively defending against such a barrage would require proactive analysis of past attacks as well as forecasting future threats. Only a proactive approach, using the information that the network already has stored, will help administrators keep the attackers at bay.
Here is our list of the best malware detection tools and analysis software:
- SolarWinds Security Event Manager EDITOR’S CHOICE The best defense for businesses looking for a robust system that can handle a large number of devices and the log data that comes from them. Start 30-day free trial.
- ManageEngine Log360 (FREE TRIAL) This large package provides security for on-premises systems and cloud services with integrated user monitoring and data loss prevention. Start a 30-day free trial.
- ESET Protect (FREE TRIAL) An anti-virus endpoint protection package that can be extended by cloud-based centralized threat hunting. Runs on Windows, macOS, Linux, iOS, and Android. Start a 30-day free trial.
- LogRhythm NextGen SIEM Platform Complete defense system that takes care of threats from start to finish in a single, unified architecture.
- Splunk Enterprise Security SIEM tool that keeps up with the sophistication of the complex threats of today and has advanced security monitoring and threat detection capabilities.
- SentinelOne Singularity Platform This package offers an XDR that gathers data from operating systems and third-party tools and then merges that information for threat hunting. This is a cloud-based system.
- CrowdStrike Falcon An endpoint protection platform that uses AI processes to detect malware activity. This innovative cybersecurity tool combines the use of onsite data collection agents with a cloud-based analysis engine.
- CyberRes ArcSight ESM Real-time correlation of log data, at the rate of 100,000 events per second makes this the fastest SIEM solution available for enterprises.
An effective defense tactic would have a system in place that monitors your system and lets you know when something goes wrong, preferably before too much damage was caused.
Although they say prevention is better than cure; the anticipation of an attack is probably the best defense strategy.
What malware tool options are available?
There are many ways network administrators can address these malware issues, some of which include:
- Installing antiviruses and antimalware solutions to fight the threats head-on
- Creating technology awareness among network users to prevent data leaks and theft – whether intentional or not
- Implementing and enforcing policies, ensuring the physical safety of hardware devices
- Regularly updating and patching the operating system and application software
But, once you have taken all of these protective measures, it still won’t mean that your job is done. You need to keep monitoring your network as well as the defense strategy that is protecting it. You will need to keep an eye out for signs of external threats, and loopholes that might open up. In case of an imminent threat, you need to come up with an effective defense strategy to implement based on real-time analysis of behavioral data gleaned from your network.
What is an SEM tool?
To understand the tool, we need to make sure we understand what security event management is, to begin with.
Security event management is the computer and network security field that handles the process of gathering, monitoring, and reporting on security events in software, system or networks.
Thus, an SEM tool is an application that monitors system event data (usually stored in event logs), extracts information from it, correlates or translates it into actionable advice, and presents it to whomever it may concern. It does so in a preferred notification or alert delivery method, and with the intention of taking further action to remedy the suspicious or malicious issues reported.
The source of logged data can be security devices like firewalls, proxy servers, intrusion detection systems (IDS Software, NIDS, HIDS, etc.), and switches or routers.
SIM vs. SEM vs. SIEM
At this point we thought it would make sense to shed light on these three closely related terms:
- SIM (security information management): is an application that automates the collection of event log data from various security and administration devices found on a network. It is a security product that is mainly used for long-term storage of the data that can then be used for ad-hoc reporting.
- SEM (security event management): when it comes to these security systems, everything is in real-time as it monitors events, standardizes data inputs, updates dashboards, and sends out alerts or notifications.
- SIEM (security information and event management): these security systems provide the services of both SIMs and SEMs – they do everything from collecting the data to forensic analysis and reporting on it.
It should be noted that SEM and SEIM are used interchangeably and can both come in the form of software solutions, hardware devices or SaaS services.
Advantages of using an SEM tool for malware detection and analysis
One key advantage of using an SEM tool is that it is an optimal solution to the “expenses vs. expertise” conundrum. Here’s the explanation:
Small businesses can’t afford to spend a lot on their IT infrastructure, let alone have a team of competitive tech gurus on their payroll. And yet, 43% of SMBs [PDF] are targeted when it comes to hacking and data breaches.
This all means that an SEM becomes the optimal solution because it provides the services of a team of network security experts at a fraction of the price it would take to have them on board full time. Because, once it is configured correctly, it becomes a round-the-clock defense system scrutinizing every registered trigger-event and waiting to employ the appropriate alert or response.
Armed with an SEM tool, you will be able to take care of:
- Security – tracking and handling malware
- Compliance – auditing and reporting become a breeze
- Troubleshooting – testing and prodding network and devices are easier with logs
- Forensic analysis – logged data can give crucial evidence and insights into what happened
- Logs management – retrieving and storing log data is automatic
The best malware detection tools
Our methodology for selecting a good Security Event Manager tool
When looking for a decent SEM tool, there are features that you might want to make sure are included with your choice:
- Event logging – …obviously!
- Intelligence – it should be smart enough to interpret logged events. It should be able to, at the very least, detect basic suspicious activities right out of the box, with default use case templates and configurations.
- Flexibility – the capability for both structured and unstructured search through logs and data.
- Responsiveness – be able to give the right type of alerts, at the right time, due to the right reasons or suspicions, and to the right user or administrator.
- Limitless boundaries – an elastic ability to address all user requests by leveraging any, and all of the available data for clear, concise, accurate, and comprehensible reports.
- Compatibility – ability to integrate with as many hardware and software solutions for easy, seamless integration into a wide range of a network.
- Cloud capabilities – this is the age of cloud computing and the technology continues to be adopted widely; this makes it critical that your new SEM solution is compatible as well.
With that out of the way, let’s move on to the five best malware detection and analysis tools for your network.
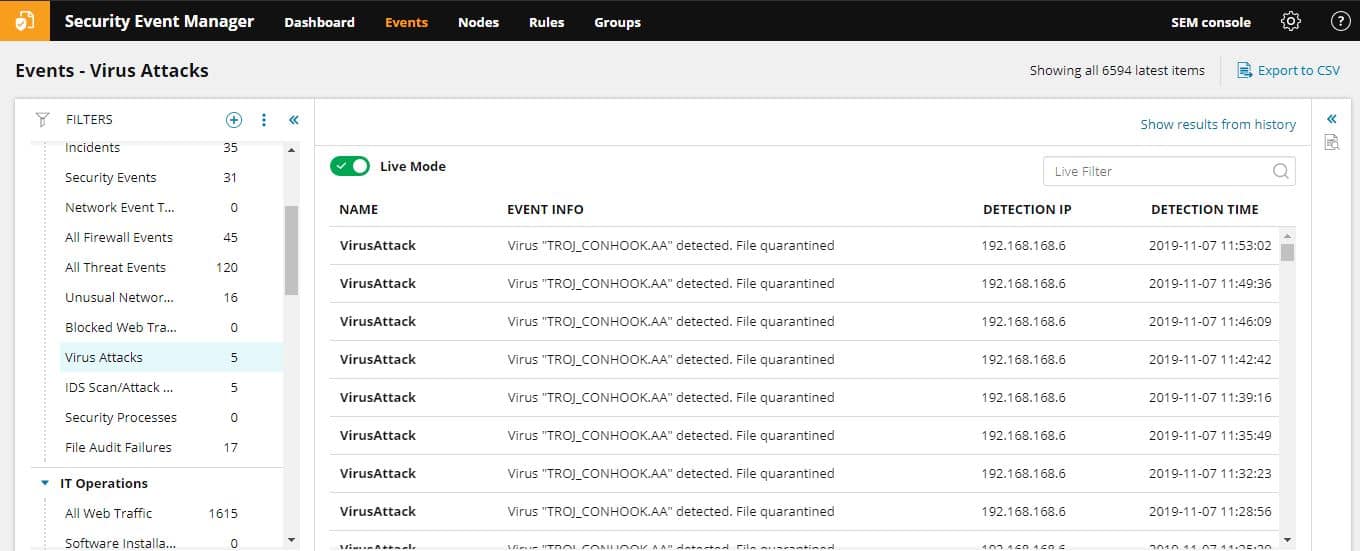
1. SolarWinds Security Event Manager (FREE TRIAL)
SolarWinds Security Event Manager (SEM) is one of the leaders in intrusion detection and threat removal technology solutions. It was formerly known as its Log & Event Manager (LEM).
Key Features:
- Log Collection and Consolidation: It collects and consolidates logs from various sources, enabling comprehensive monitoring and analysis of security events.
- Centralized Threat Hunting: SEM offers centralized threat hunting capabilities, allowing security teams to proactively search for and respond to potential threats.
- Orchestration for Responses: The solution includes orchestration features for automated response actions, streamlining incident response processes.
- Integration with NIDS Tools: It supports tools like Snort, allowing SEM to be part of a larger Network Intrusion Detection System (NIDS) strategy, enhancing threat detection capabilities.
- Pre-Configured Alerts and Rules: SEM comes with over 700 pre-configured alerts, correlation rules, and detection templates, providing instant insights and enhancing threat detection efficiency.
Why do we recommend it?
SolarWinds Security Event Manager is a SIEM that operates its own log manager. The logs are collected from around the system. Threat hunting is implemented on those logs and it can spot malware activity as well as intruders and insider threats. The tool is a software package that runs on Windows Server.
To be honest, it is a tool that has everything required to keep a network safe. It is an SEM that helps network administration and security personnel better detect, respond to, and report on the detection of malware or suspicious activities and many people agree with us.
Other features to take note of:
- The price won’t break the bank – SolarWinds proves quality doesn’t have to come with a high price tag.
- SolarWinds Security Event Manager has a UI that is easy to learn, navigate, and master.
- The SEM File Integrity Monitor (FIM) keeps an eye on Windows files, folders, critical system files, and registry keys to make sure they aren’t tampered with.
- SEM can also be used to monitor Active Directory events including creation or deletion of user accounts and groups, or any other suspicious activities like login
- One of the best threat detection and automated reporting capabilities make it a joy to work with this SEM.
- SolarWinds Security Event Manager is famous for being a robust system that can handle huge amounts of logged data sourced from a large number of nodes.
- Finally, Security Event Manager also helps predetermine any weak points that could be exploited or used against a network and then automates the remedy so they are patched as soon as possible.
Who is it recommended for?
This is a large system that is suitable for use by big companies. The tool’s reach is dictated by its log sources, which can come from multiple sites and cloud platforms. The management of logs makes this an important system for businesses that need to prove compliance with HIPAA, PCI DSS, and other data protection standards.
Pros:
- On-Premises Package: SEM is designed as an on-premises security package, providing control and security for organizations that prefer to manage their security infrastructure locally.
- Enterprise-Grade Monitoring: SEM is built with enterprise environments in mind, capable of monitoring Windows, Linux, Unix, and Mac operating systems.
- Intelligent Reporting and Response: Its threat response rules are easy to build and use intelligent reporting, reducing false positives and improving response accuracy.
- Integration with Other Tools: Integrates with other SolarWinds and third-party security tools, providing a more robust security posture and streamlined operations.
Cons:
- Feature Density: SEM is feature-dense, which means it may require time and effort to fully explore and utilize all its capabilities effectively.
A point that would make anyone partial to SolarWinds SEM is the fact that the company doesn’t just show you the door once you have made a purchase. On the contrary, their Support Services have won awards and continue to help their clients accelerate business outcomes. You can download the SolarWinds Security Event Manager on a 30-day free trial.
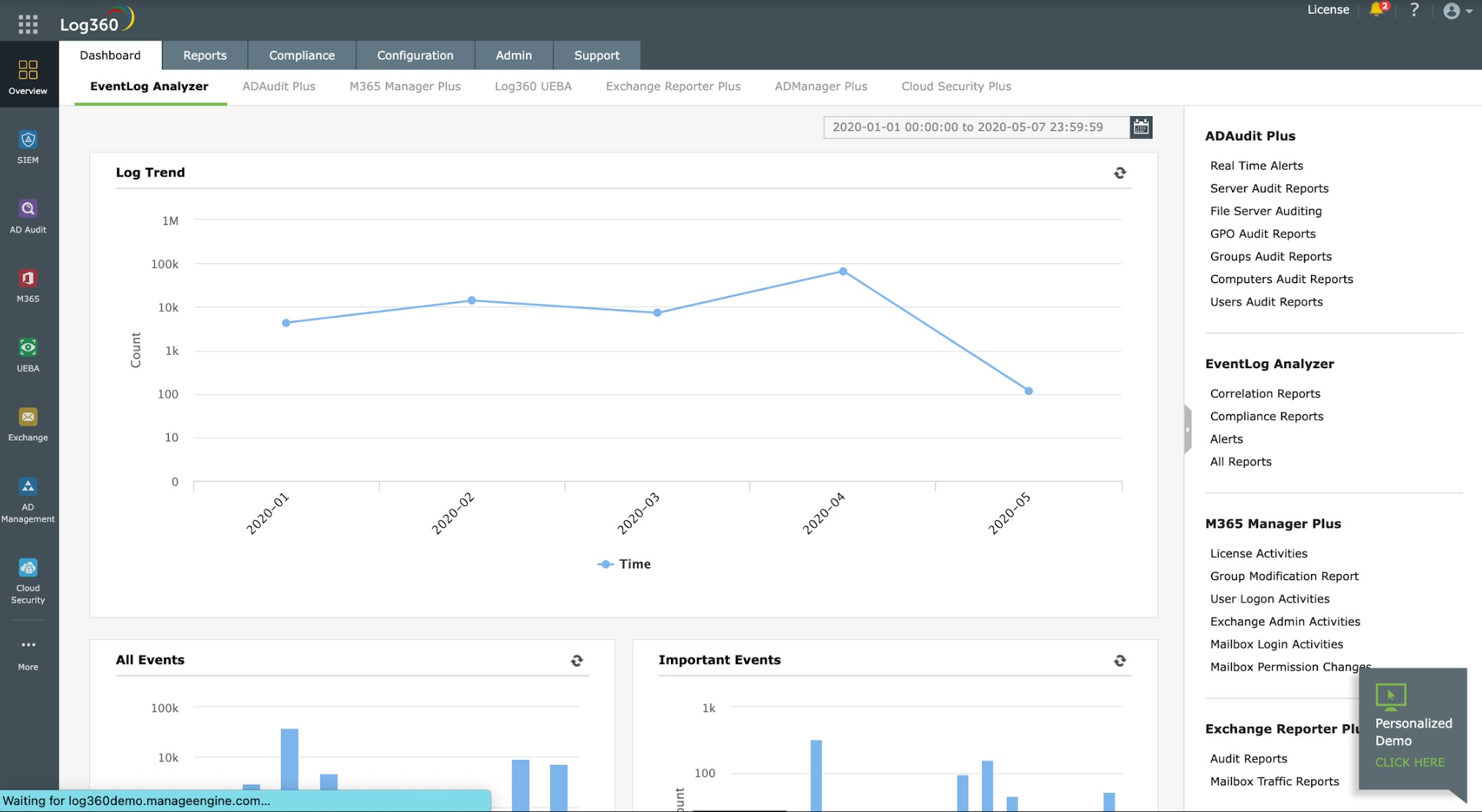
2. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 combines many security functions in one package. It provides a log manager, a SIEM system, a data loss prevention service, a cloud access security broker, user and entity behavior analytics, security orchestration, automation, and response, cloud security monitoring, insider threat detection, file integrity monitoring, and compliance reporting.
Key Features:
- Advanced Threat Detection: Utilizes rule-based analytics and machine learning to identify potential threats. This includes detecting unusual access patterns, data breaches, and other indicators of malware infection.
- Comprehensive Log Management: Aggregates logs from servers, applications, databases, and network devices, providing a centralized platform for easier analysis and correlation of data.
- Instant Alerts and Automated Response: Configurable alerts notify administrators about potential threats, and automated response actions can be set up to mitigate risks immediately.
- Forensic Analysis: Tools are provided for conducting in-depth investigations into security incidents, helping teams trace the root cause and the extent of a breach.
- Compliance Reporting: Offers prebuilt reports for various regulatory requirements such as GDPR, HIPAA, PCI-DSS, and more.
Why do we recommend it?
ManageEngine Log360 provides extensive log management and security monitoring services. This is a SIEM tool with many other functions associated with it. Apart from providing its own log manager for threat-hunting source data, this package can take the Webroot BrightCloud threat intelligence feed to speed up threat detection.
Log360 is actually a bundle of many ManageEngine security products. It is built around a SIEM, which will identify malware activity and also manual intrusion. The system has a threat intelligence feed, which tailors the threat-hunting activity of the SIEM to recent attack campaigns. The service relies on data from log files and network activity. These are gathered from all operating systems and applications running on your endpoints.
New malware emerges every day and so searching through a list of known malicious software is an outdated strategy. This package spots all types of malicious code by its activity. So, malware masquerading as a genuine software package can immediately be spotted and blocked.
The system scans for anomalies and deploys user and entity behavior analytics (UEBA) to baseline normal activity and reduce the number of false positive alerts. File integrity monitoring will trigger an alert if ransomware starts its encryption processes and these activities can be shut down immediately through security orchestration, automation, and response mechanisms.
While the tool will immediately block malware activity, it will also generate log records of the attack and all mitigating responses and also raise an alert. You can get the service to channel alerts into a ticketing system, such as Manage Engine ServiceDesk Plus.
Along with all of this, you also get a log manager, which can organize log messages from different sources into a common format and store them in files with meaningful names in an organized directory structure. These logs can be archived or accessed for compliance auditing. The system includes compliance reporting for PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA.
Who is it recommended for?
This is a large package that is suitable for big organizations. The bundle includes a CASB service to strengthen cloud protection, making the platform useful for businesses that have both cloud-based and on-premises resources. It also implements data loss prevention, so you get a full toolset for a Security Operations Center with this package.
Pros:
- Enhanced Visibility: Provides visibility across the entire network, which is crucial for detecting hidden malware that can bypass traditional antivirus solutions.
- Proactive Security Measures: The ability to set up real-time alerts and automated responses enables proactive management of security threats.
- Scalability: Suitable for both small businesses and large enterprises, as it can handle vast amounts of log data and grow with the organization’s needs.
- Support for Compliance: The comprehensive compliance reporting capabilities make it easier for organizations to meet strict regulatory requirements, reducing the risk of penalties.
- Integration with Other Tools: Integrates with other ManageEngine and third-party security tools, providing a more robust security posture and streamlined operations.
Cons:
- Dependence on Log Data: Its effectiveness heavily relies on the quality and comprehensiveness of the log data collected; gaps in log coverage can reduce the efficacy of the malware detection.
- Cost: While providing extensive functionality, the cost can be a barrier for smaller organizations or those with limited budgets.
The features of the Log360 package require a team to fully manage them and so this is a system for use by a large business with a specialist cybersecurity team. This software package runs on Windows Server and you can get it on a 30-day free trial.
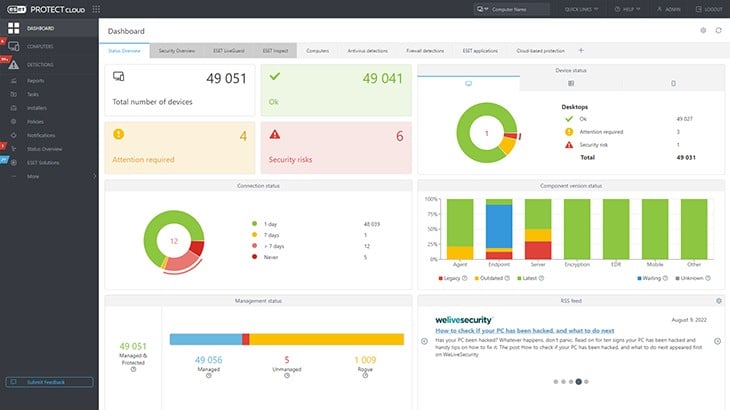
3. Eset Protect (FREE TRIAL)
ESET Protect is a threat detection system that will spot malware and human-driven attacks. The core unit of this system is an on-device software package that will run on Windows, macOS, Linux, iOS, and Android. This service will protect mobile devices as well as computers.
Key Features:
- Anomaly Detection: Eset Protect includes anomaly detection capabilities, allowing it to identify unusual behavior and potential security threats.
- Cloud-Based Sandboxing: It leverages cloud-based sandboxing for analyzing and executing potentially malicious files in a secure environment, minimizing risks to endpoints.
- Local and Centralized Threat Hunting: The solution supports both local and centralized threat hunting, providing flexibility in security monitoring and response.
Why do we recommend it?
ESET Protect gives you an autonomous on-device malware protection system. Many viruses will try to prevent cloud-based cybersecurity systems from blocking their actions by making the device impossible to contact but ESET Protect will continue to function in those circumstances. A cloud SIEM service adds extra threat detection capabilities.
The detection system looks for well-known malware strategies, such as reconnaissance scans and attempts at lateral movement. The system also identifies excessive login attempts that indicate password cracking activity. File name changes and encryption would indicate ransomware.
The base edition, called ESET Protect Entry, gives you that on-device software and also provides a cloud-based console that shows a company-wide overview of all ESET Protect installations. Move up to the ESET Protect Advanced edition to turn that cloud component into a SIEM service. This plan also provides cloud sandboxing to examine downloaded software.
ESET Protect Complete provides vulnerability scanning and patch management. This level adds protection for cloud services and also email systems, which might be on-premises or on the cloud.
All plans provide automated responses, which are implemented by the endpoint units. The top plan, ESET Protect Elite can extend threat remediation instructions out to third-party tools, such as access rights managers and firewalls.
Who is it recommended for?
The smallest package that you can buy covers five devices. ESET includes a multi-tenanted architecture for its cloud XDR, which makes the package suitable for use by managed service providers. ESET also offers ESET Protect MDR, a Managed Detection and Response package, which includes the services of technicians to run your protection system remotely.
Pros:
- Multi-Level Threat Detection: Eset Protect offers multi-level threat detection for malware and malicious actors, enhancing security posture and threat mitigation.
- System Hardening: It includes a vulnerability scanner for system hardening, helping organizations identify and address security weaknesses proactively.
- Private Threat Intelligence Network: The solution features a private threat intelligence network that warns all endpoints when one is attacked, improving overall threat response and collaboration.
Cons:
- Minimum Device Requirement: Eset Protect is not available for less than five devices, which could be a limitation for smaller organizations or environments with fewer endpoints.
While the minimum number of devices you can buy this system for is five, the top plan, ESET Protect Elite is priced for a minimum of 26 devices. ESET Protect is available for a 30-day free trial.
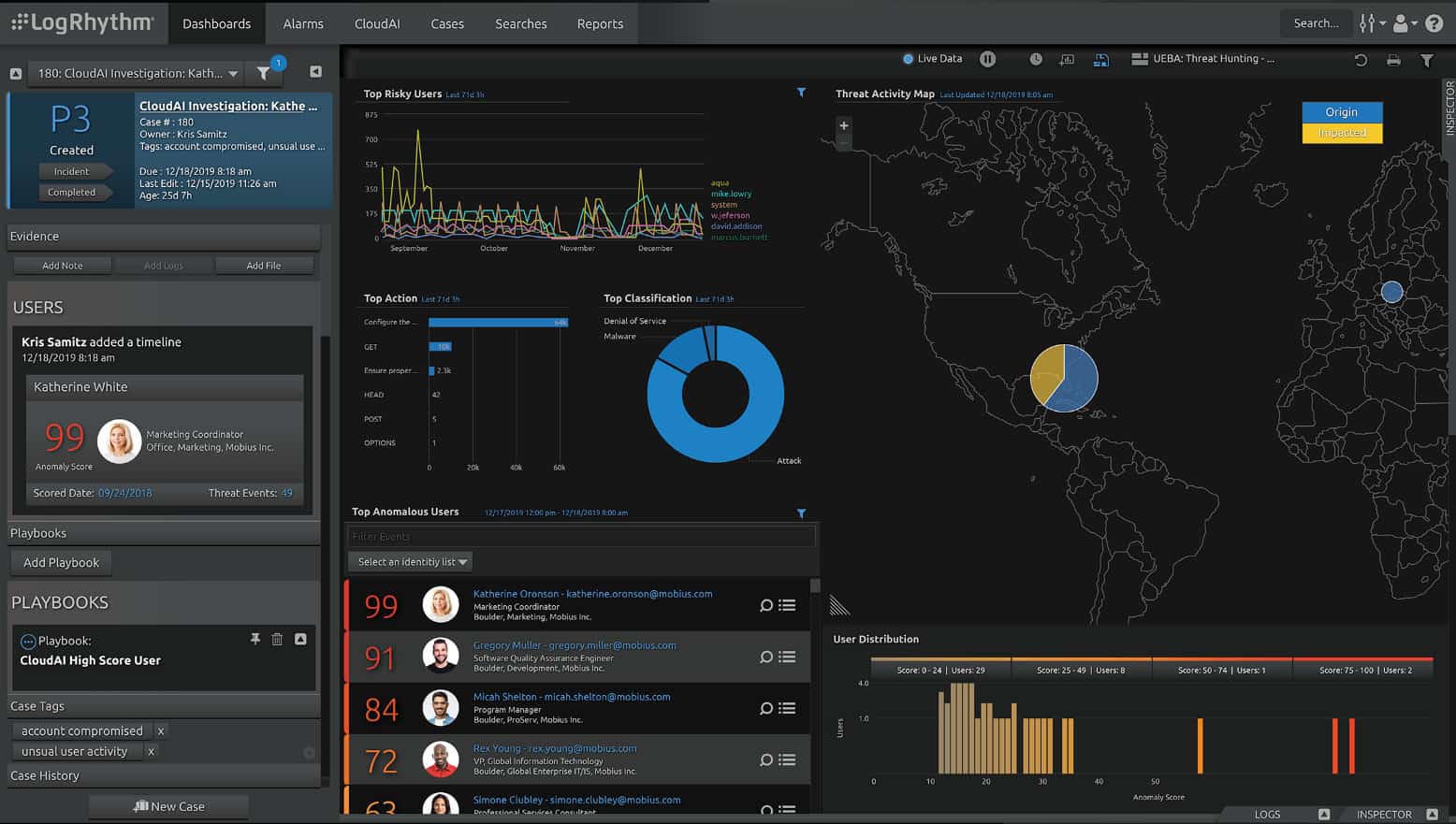
4. LogRhythm NextGen SIEM Platform
LogRhythm NextGen brings log management, security analytics, and endpoint monitoring together which makes it a powerful tool to identify threats and thwart breaches.
Key Features:
- User and Entity Behavior Analytics (UEBA): It includes user and entity behavior analytics capabilities, enabling the detection of abnormal or suspicious behavior within the IT environment.
- Zero-Day Detection: The platform incorporates zero-day detection mechanisms, helping organizations identify and respond to emerging threats.
- Case Management and Forensics: Provides tools for managing security incidents and conducting forensic investigations to understand attack vectors and the impact of breaches.
- Compliance Automation: Supports compliance with major regulations through comprehensive data collection, real-time analysis, and detailed reporting.
Why do we recommend it?
LogRhythm NextGen SIEM Platform is a cloud-based system that gathers logs from all levels of the stack. It can also receive activity records from other cloud platforms. The SIEM detects manual and automated actions, which provide malware detection and analysis. User and Entity Behavior Analytics creates an activity baseline for anomaly detection.
LogRhythm SIEM has a unique feature that makes it stand out from the crowd: its Threat Lifecycle Management process. In order to make it efficient in detecting and stopping threats, this company has come up with a unique approach to tackling the task with end-to-end threat processing capabilities.
In other words, with this SIEM solution, all threats are managed in one place – from detection right through to responding and recovering from it.
Also, LogRhythm uses data analysis to spot threats before they can cause any major damage, if at all. The SIEM presents admins with detailed activities of all connected devices so they can then forecast future threat occurrences – based on previous experiences. Once they spot such suspicious behaviors they can shut them down before they happen, or as soon as they have been detected.
Other features of LogRhythm:
- LogRhythm Enterprise [PDF] is for larger networking environments and comes with an arsenal of tools.
- Meanwhile, LogRhythm XM [PDF] is for SMBs with a smaller reach and lower processing power.
- The company also offers a hardware option as well as LogRhythm Cloud – a cloud solution for clients who prefer not to be bothered with overhead or hardware maintenance.
All this comes with a SIEM solution that has, quite unsurprisingly, been named Best Security Information and Event Management Software of 2019 by Gartner.
Who is it recommended for?
This system is suitable for businesses that operate multiple sites and also use cloud services. The package is able to pull activity data from any location, operating through agent programs, which it downloads onto every monitored system. The tool is suitable for use by a security operations center.
Pros:
- Cloud-Based Service: LogRhythm NextGen SIEM Platform is a cloud-based service, offering flexibility and scalability for security monitoring and analysis.
- User-Friendly Setup: LogRhythm NextGen SIEM Platform uses simple wizards for setting up log collection and other security tasks, making it more beginner-friendly and reducing setup complexity.
- Sleek Interface: It features a sleek and highly customizable interface, visually appealing and providing a seamless user experience.
- AI and ML Integration: The platform leverages AI and machine learning (ML) technologies for behavior analysis, improving threat detection accuracy and efficiency.
Cons:
- Lack of Trial Option: One potential drawback is the absence of a trial option, which could limit organizations’ ability to evaluate the platform before full implementation.
- Cross-Platform Support: Some users may find that additional cross-platform support would be beneficial, enhancing compatibility across different IT environments.
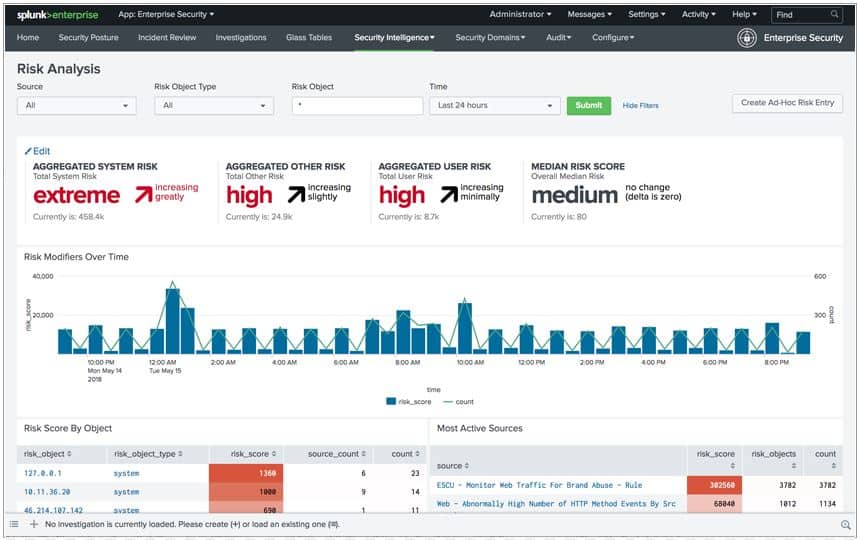
5. Splunk Enterprise Security
This is also another top-reviewed SIEM solution. A free version lets users see exactly how great a solution it is. Although you can only index 500 MBs per day, it serves enough to show why Splunk ES has earned praises.
Key Features:
- Comprehensive Security Insights: Splunk ES aggregates and analyzes vast amounts of data, providing deep insights into potential security threats, including sophisticated malware.
- Advanced Threat Detection: Utilizes advanced analytics and machine learning to detect unusual behavior and known threat patterns, helping to identify malware and other cyber threats quickly.
- Threat Intelligence Integration: Splunk ES integrates with external threat intelligence feeds to enhance its detection capabilities with the latest information on emerging threats.
- Compliance Reporting: Provides extensive reporting features that help organizations meet regulatory compliance requirements across various standards.
- Behavior Analysis: Splunk Enterprise Security can utilize behavior analysis to detect threats that may not be discovered through traditional log monitoring, enhancing threat detection capabilities.
Why do we recommend it?
Splunk Enterprise Security is an on-premises software package that also has a SaaS version in the cloud. Security scanning operates on data collected from around your system and it is implemented in the Splunk data analysis tool. The system sends out alerts when it detects malware, intruders, or insider threats.
Looking at a few more details, we have:
- The use case library in Splunk Enterprise Security strengthens a business’ security presence; with over 50 cases available, there is no shortage of plans and templates that can be used straight out of the box and are categorized into Abuse, Adversary Tactics, Best Practices, Cloud Security, Malware, and Vulnerability.
- Meanwhile, security events can be grouped by separate segments, host types, sources, assets, and geographical locations.
- Splunk ES has the capacity to analyze almost all formats of data from numerous sources – logs, databases, views, and more – and then bring them together via normalization.
- This SIEM tool has direct mapping to malware knowledgebase websites like Mitre Att&ck and applies strategies like cyber kill chain, CIS 20 Controls, and NIST Cyber-security framework; Splunk ES is, therefore, able to stay up-to-date and ahead of even the latest attack methods.
- Capable of working with a wide range of machine data whether it be from local sources or the cloud.
- A rather unique feature that makes Splunk awesome is its ability to send alerts and notifications using webhooks for third-party apps like Slack (in multiple channels, no less).
- Splunk Enterprise Security, too, is another SIEM solution that has been given great reviews on Gartner.
To be honest, the only complaint that can be made against this SIEM is its price tag – the licensing could be out of the reach of many SMBs.
Who is it recommended for?
This package is suitable for mid-sized and large organizations. Small businesses won’t need such a complex solution. The Splunk system chapters to all markets by having both on-premises and cloud versions. The installed edition runs on Linux or Windows Server. The security system can be expanded by performance management modules.
Pros:
- Excellent User Interface: It features an excellent user interface that is highly visual and offers easy customization options, improving user experience and flexibility.
- Reputable Analytical Tool: Splunk Enterprise Security is recognized as a successful analytical tool, offering robust capabilities for security monitoring and analysis.
- Good for Hybrid Environments: The platform is well-suited for hybrid environments, providing visibility and control across both on-premises and cloud-based systems.
- Platform Compatibility: It is available for both Linux and Windows environments, offering flexibility in deployment.
Cons:
- Opaque Pricing: One drawback is the lack of transparent pricing, as it requires a quote from the vendor, making budgeting and cost estimation challenging for organizations.
- Not Ideal For SMBs: While well-suited for large enterprises, Splunk Enterprise Security may be less suitable for smaller organizations due to its scale and complexity.
- Learning Curve: The platform uses Search Processing Language (SPL) for queries, which can steepen the learning curve for users new to the platform and SPL syntax.
6. SentinelOne Singularity Platform
The SentinelOne Singularity Platform is based in the cloud and it collects data from its own on-premises agent and from other security tools that are already present on the site. All of this data from different sources arrives in incompatible formats, so the SentinelOne server consolidated them all into a common format.
Key Features:
- Behavioral AI: SentinelOne uses behavioral AI to monitor and analyze device behavior continuously, allowing it to detect and respond to threats in real time, including zero-day and advanced malware.
- Automated EDR: Provides automated threat detection, hunting, and response capabilities, which include full remediation and rollback options to reverse any changes made by malware.
- ActiveEDR: Unlike traditional EDR tools that require manual input, SentinelOne’s ActiveEDR is driven by autonomous technology that can trace and mitigate threats without human intervention.
- IoT Security: Extends beyond traditional endpoints to provide security for IoT devices, providing a broader scope of protection.
- Visibility and Control: Offers full visibility into all network activities with comprehensive control options that enable detailed policy enforcement and threat hunting capabilities.
Why do we recommend it?
This system is an XDR. That is it expands on the traditional endpoint detection and response (EDR) strategy by pulling in activity scanning from networks and third-party tools. The platform standardizes all incoming messages on the cloud to create a data lake for threat hunting. Responses can involve sending instructions to third-party tools.
The SentinelOne system is flexible because it can pull in activity data from anywhere. You just have to set up a feed from those tools into the SentinelOne log server. This task is made easier by a library of integrations, which sets up the feeds from those third-party tools for you. Data can also come from operating systems and cloud platforms.
The threat hunting unit of SentinelOne Singularity is implemented as a rules base. This has a series of tests with related conclusions. Those conclusions will raise alerts and they can also be adjusted to automatically respond to the discovery of the threat. You can also add your own new rules to the set.
Responses can involve writing firewall rules to block traffic from a malicious external source or reaching into an access rights manager and suspending a compromised account. The precise degree of automation is up to the system administrator of the company that subscribes to the SentinelOne Singularity platform.
Who is it recommended for?
Large organizations with many different platforms and assets would benefit the most from this package. The SentinelOne system is able to consolidate data from many different sources and coordinate responses among many tools. So a straightforward small network with few systems operating on it wouldn’t get value for money from this tool.
Pros:
- Advanced Malware Protection: AI-driven technology provides superior detection of advanced malware, including ransomware and stealthy attacks, by identifying malicious behaviors.
- Automated Response and Remediation: Reduces the burden on IT teams by automatically containing and remedying threats, significantly reducing response times and operational overhead.
- Holistic Endpoint Coverage: Protects a diverse range of devices including desktops, mobile devices, and IoT devices, ensuring comprehensive security coverage.
- User-Friendly: Despite its sophisticated technology, it is designed to be user-friendly, with an intuitive interface that simplifies complex security operations.
Cons:
- Cost Considerations: The extensive features and advanced technology come at a premium cost, which might be prohibitive for smaller organizations with limited budgets.
The SentinelOne Singularity platform is a comprehensive system and large organizations will get the most out of it. However, the platform’s services are priced per endpoint, which makes it scalable and, potentially suitable for any size of business. The minimum order size for an account is for five endpoints. There are five plan levels and only the top edition covers the security of networks – the others all focus on endpoint protection. You can access a free demo to examine the platform.
7. CrowdStrike Falcon
CrowdStrike Falcon is an endpoint protection platform (EPP). It doesn’t operate on network event data, but collects event information on individual endpoints and then transmits that over the network to an analysis engine. As such, this is a SIEM tool. The activity monitor is an agent, resident on each protected endpoint. The analysis engine resides in the Cloud on the CrowdStrike server. So, this is a hybrid on-site/cloud solution.
Key Features:
- Protects Endpoints: CrowdStrike Falcon is designed to protect endpoints, providing security against various threats and attacks.
- Shares Endpoint Event Data: It shares endpoint event data across the platform, enhancing visibility and collaboration in threat detection and response.
- Creates a Response Platform: The platform includes features to create a response platform, enabling quick and effective response actions to security incidents.
- Anomaly Detection: It includes anomaly detection capabilities, identifying and alerting on abnormal behavior or potential threats.
Why do we recommend it?
CrowdStrike Falcon offers modules that can be assembled into a variety of threat detection configurations. All of the units in this suite are cloud-resident, except for one on-device module, called Falcon Prevent. This is an anti-malware system that uploads activity data to the cloud for central threat hunting, creating a SIEM.
The EPP is composed of modules and marketed in editions. Each edition involves a different list of modules, but all of them include the Falcon Protect system. Falcon Protect is a next-generation AV that monitors processes on an endpoint rather than using the traditional AV method of scanning for known malicious program files.
The agent on the endpoint composes event logs from process activities and then transmits those records to the CrowdStrike server for analysis. A traditional SEM works on live data. However, Falcon Protect just uses a logging process to collate and transmit events to the analysis engine, so it is near-live. It still qualifies as a SEM because it is able to report on malicious activity immediately and it doesn’t search through existing historical event records for its source material.
An advantage of the split data gathering and analysis processes of Falcon Prevent is that the event data is stored for secondary analysis. Operating on live data sometimes misses suspicious activity that is implemented through the manipulation of authorized processes. Some malicious activity can only be spotted over time by linking together seemingly innocent actions that can amount to a data theft attempt or a sabotage event.
Who is it recommended for?
Falcon Prevent needs to be installed on every endpoint in the enterprise. This makes the tool complicated to manage for very large enterprises. Small businesses will find cheaper on-device AV systems, so this package is best suited to mid-sized enterprises. A central controller reaches out to remote devices.
Pros:
- Cloud-Based Coordination: CrowdStrike Falcon operates on a cloud-based coordination model, offering scalability and flexibility in security operations.
- Advanced Threat Detection: CrowdStrike Falcon doesn’t rely solely on log files for threat detection but also uses process scanning to detect threats immediately, enhancing threat detection capabilities.
- Integrated HIDS and Endpoint Protection: It acts as a Host Intrusion Detection System (HIDS) and endpoint protection tool in one, providing comprehensive security coverage.
- Deployment Flexibility: CrowdStrike Falcon can be installed either on-premise or directly into a cloud-based architecture, offering deployment flexibility.
- Lightweight Agents: The agents used by CrowdStrike Falcon are lightweight, ensuring minimal impact on server performance and end-user devices.
Cons:
- Short Trial Period: Some users may find that a longer trial period would be beneficial for fully evaluating the platform’s capabilities and effectiveness.
CrowdStrike’s bundles include threat prevention, threat analysis, and device control modules. The base package is called Falcon Pro and the higher plans are Falcon Enterprise and Falcon Premium. CrowdStrike also offers a managed cybersecurity service, called Falcon Complete. CrowdStrike offers a 15-day free trial of Falcon Pro.
8. CyberRes ArcSight ESM
CyberRes ArcSight ESM is an enterprise security manager that has been around for almost two decades. Over those years it has continued to grow and evolve into the truly amazing network malware analysis and detection tool it is today.
Key Features:
- Real-Time Monitoring and Correlation: ArcSight ESM excels in collecting and analyzing data from various sources in real time, allowing it to identify and correlate potential security events quickly.
- Advanced Security Analytics: Uses complex event processing and analytics to detect unusual patterns and behaviors that could indicate malware or other cyber threats.
- Scalable Data Collection: Capable of handling vast amounts of data from diverse sources, making it suitable for large organizations with extensive IT infrastructures.
- Threat Intelligence Integration: Supports integration with threat intelligence feeds to enhance detection capabilities with the latest security information and trends.
- Automated Response Capabilities: Includes features for automated response to identified threats, helping to mitigate risks promptly and effectively.
Why do we recommend it?
CyberRes ArcSight ESM is a centralized threat detection system that optimizes the power of your existing security systems by implementing security operations, automation, and response (SOAR). This means that the tool operates a SIEM on the cloud and then sends response instructions to your firewalls, on-device AVs, and access rights manager.
This tool can lay claim to being one of the best SIEM tools out there with its ability to meet any scalability requirements as it can now analyze 100,000 events per second!
Do you have a new vendor joining your network? No problem; this SIEM’s structured data can be easily consumed by third-party apps. Also, their acquisition of Interset – a security analytics software company earlier this year means they aim to better improve the behavioral analytics and machine learning capabilities of ArcSight.
Loaded with these features, it becomes quite clear that ArcSight is the ideal SIEM tool for larger and complex system-on-chip (SOC) environments and managed security services providers (MSSPs). It is also a truly infrastructure-independent SIEM tool whose services can be delivered via software, hardware, as well as cloud services like Amazon Web Services (AWS) and Microsoft Azure.
Meanwhile, distributed correlation allows scalability and, thus, ArcSight’s SIEMs can grow as fast, and as big, as they may be required to be and cuts the times between mean time to detect (MTTD) and mean time to respond (MTTR).
Finally, the whole suite has new UI options galore which means ArcSight now comes with fresh charts, dashboards, consoles, etc., that make it easy as well as a pleasure to fight malware with. Also, large numbers of use-case solutions and packages help build a solid defense that can then be shared (using rule sets and logic) among clients or businesses facing similar issues.
All in all, this is a great SEM tool!
Who is it recommended for?
CyberRes is aimed at large organizations that run security operations centers. Although this tool provides automated detection and response, it should be managed by a team of security specialists. This is because the reports of this package show how multi-site hybrid system security can be tightened to prevent further attacks.
Pros:
- Improved Incident Response: The automation and real-time analytics help reduce the time between threat detection and response, potentially limiting the impact of attacks.
- Enhanced Situational Awareness: Gives security teams a holistic view of the security landscape, including user activities and network events, enhancing overall situational awareness.
- Scalability and Flexibility: Highly scalable, capable of expanding to meet the needs of growing businesses and adapting to complex, evolving IT environments.
- Support for Regulatory Compliance: Helps organizations meet compliance requirements with detailed audits and reports, reducing the risk of penalties and non-compliance issues.
- Good for MSSPs: It is well-suited for Managed Security Service Providers (MSSPs), providing features that support multi-tenant environments and scalable security operations.
Cons:
- Customization Challenges: Users may find it challenging to customize the look and feel of the main dashboard, which can impact user experience and personalization.
Deciding on a malware detection and analysis tool
Our choices (yes, there’s two, we couldn’t choose between them) for the best malware detection and malware analysis tools for your network would have to be SolarWinds SEM for the superior, yet affordable SEM tool as well as LogRhythm NextGen SIEM Platform for a full defense system that has unique defense strategies.
Let us know what you think or share your personal experiences with us. Leave a comment down below.
Malware Detection Tool FAQs
What are the different types of malware?
There are 10 types of malware:
- Virus – Malicious executable programs.
- Trojan – A virus that is disguised as a desirable file but lets other malware in.
- Remote access Trojan (RAT) – A program that lets hackers in, possibly getting control of the Desktop or webcam.
- Worm – Malware that can replicate itself across a network.
- Rootkit – Malware that gets down into the operating system, making it difficult to detect or remove.
- Fileless Malware – Malware that loads directly into memory often from an infected Web page.
- Spyware – Logs user activity.
- Keylogger – Secretly records user keystrokes.
- Adware – Injects advertisements into software and web pages.
- Bot – Performs action against other computers without the owner’s knowledge.
What is malware static analysis?
The static analysis of malware involves scanning malicious code and assessing its characteristics without executing it.
What is dynamic malware analysis?
Dynamic malware analysis is an assessment method that requires malware to be run so that its actions can be recorded. This type of analysis should be performed in an isolated environment, called a sandbox, to prevent the test from causing actual damage to the host system.
In what order should you perform malware analysis techniques?
Follow these steps to perform a full malware analysis:
- Identify all of the files that contribute to a malware system.
- Perform static analysis, examining identifiers, such as metadata and possible traces of how this software appeared on your system. Carry out research on the data you record.
- Perform advanced static analysis, reading through the code, and mapping how the different modules of the suite work together and what system resources or resident software it exploits.
- Perform dynamic analysis, running the code in a sandbox environment, which you thoroughly isolated from the rest of your business. Log the changes that the malware made to the system in order to work out its purpose.