A business needs to ensure its data is secure to assure its clients that whatever information they hand over– will be safe from prying eyes regardless of the data types.
Here is our list of the best cybersecurity risk management tools:
- ManageEngine Vulnerability Manager Plus EDITOR’S CHOICE An on-premises package that provides a vulnerability scanner and a patch manager with automated processes to update systems configurations. Runs on Windows Server. Start a 30-day free trial.
- ManageEngine Log360 (FREE TRIAL) A SIEM tool that detects, prioritizes, and responds to security threats across on-premises, cloud, and hybrid networks. It offers advanced analytics, machine learning-based anomaly detection, and integrated risk management capabilities. Runs on Windows Server. Get a 30-day free trial.
- ZenGRC A cloud-based and on-premise governance, risk, and compliance (GRC) management tool for auditing, managing, and monitoring business infrastructures; it is a solution that is simple to integrate.
- Resolver Risk Management Software A tool for risk management, security, compliance, incident management, and more; it shows all current risks in a single platform and provides data-driven recommendations to resolve them.
- SAI Global’s Digital Manager 360 A highly scalable cloud-based platform that offers flexible, scalable, and configurable modules for risk management and compliance audit across entire enterprise networks.
- SolarWinds Cybersecurity Risk Management and Assessment Tool Analyzes and audits access issues across files, folders, and servers to simplify administrators’ jobs.
- LogicManager IT risk management software This tool makes sure organizations’ IT systems and data are secure, accurate, and in compliance with industry standards; it identifies gaps and generates heat maps to visualize any current risks.
- CURA Enterprise Risk Management A cloud-based suite of tools for cybersecurity risk management that is efficient in monitoring risk of loss caused by human error and external events; it has real-time, insightful, and highly interactive dashboards and reports for a better understanding of risks.
- Pathlock A GRC tool that prevents unauthorized access of sensitive data and gives insight into risks that are all controlled from a central dashboard; this is an ideal choice for businesses looking for industry standards compliance.
Now, these prying eyes could come from anywhere – even from within the network itself; this means there is always a need for some of the seven best cybersecurity risk management solutions we will see in this post.
But, before we do, here is a brief list of the best cybersecurity risk management solutions.
What Constitutes a Cybersecurity Risk?
A cybersecurity risk refers to the likelihood of exposure, compromise, or loss of sensitive information caused by cyberattacks or data breaches. This risk encompasses potential damage to an organization’s data, technical infrastructure, and reputation. For example, an attack could lead to the loss of mission-critical data, disruption of operations, or harm to a business’s credibility with customers and partners.
On the other hand, cybersecurity involves the technologies, processes, and strategies used to safeguard a company’s intellectual property, customer information, and other sensitive data from malicious actors. These threats can originate from external attackers or internal sources, highlighting the importance of a comprehensive security approach that spans all levels of an organization’s network.
What is a Cybersecurity Risk Management Tool?
A cybersecurity risk management tool is a specialized solution designed to help organizations evaluate and mitigate the risks that threaten their IT systems and data. These tools identify vulnerabilities in software, hardware, and networks, allowing businesses to understand the level of exposure they face and the potential impact of an exploit.
Beyond identifying risks, these tools provide continuous monitoring and auditing of an organization’s security posture. They assess the health of digital assets, track emerging threats, and generate reports to help IT teams prioritize issues. By pinpointing vulnerabilities, these tools empower businesses to take proactive measures, such as applying patches or implementing new security protocols, to eliminate or minimize risks.
The ultimate goal of using cybersecurity risk management tools is to prevent exploitation by malicious actors, whether inside or outside the network. Regardless of an organization’s IT architecture or operational complexity, these tools serve as a vital line of defense in protecting sensitive data and ensuring business continuity.
What makes for an excellent cybersecurity management solution?
Some features to look for in a cybersecurity management solution:
- Risk identification – the first and obvious feature is its capabilities to spot vulnerabilities as they arise.
- Vulnerability Assessment (VA) – it should assess the risks and rank them according to seriousness to help prioritize which ones need to be tackled immediately and which ones can be “tolerated” temporarily until all significant issues have been resolved.
- Breach and attack simulation (BAS) keeps up with the latest threats and runs simulated attacks to assess how well the cybersecurity defenses will hold up.
- Insightful dashboards, actionable reports – it needs to present all findings and updates on a dashboard that is informative and easy to understand while also generating regular reports to let stakeholders know about the current security status or use as proof of legal compliance or meeting industry standards.
- Multi-alert system – all concerned personnel should be alerted with multiple methods like email, text, and messages to applications like Slack.
- Scalability – the solution should grow along with the business’ IT landscape and accommodate all changes to its processes and the network’s architecture.
- Price – the solution’s price should have a positive ROI; better yet, it could be free and still perform better than the premium ones.
We have compiled the seven best cybersecurity risk management solutions based on these features and found them worthy of being on this list.
The Best Cybersecurity Risk Management Solutions
Now, let’s have a detailed look at each of the best risk management tools.
1. ManageEngine Vulnerability Manager Plus (FREE TRIAL)
ManageEngine Vulnerability Manager Plus is a package of tools to assess risk and vulnerability in endpoints, Web systems, and mobile devices. IT can scan and assess equipment running Windows, macOS, and Linux and the automated processes in the package include steps to fix any problems that the scanner finds.
Key Features:
- Scans for misconfigurations: Identifies security weaknesses
- Checks OS and software: Identifies outdated systems
- Identifies user account weaknesses: Abandoned accounts, wide permissions
- Tightens Web server security: Looks for susceptibility to tampering or inability to cope with traffic floods
Why do we recommend it?
ManageEngine Vulnerability Manager Plus is a preventative security package. The tool scans endpoints and looks for misconfigurations. It makes a list of the weaknesses that it discovers. While some of those vulnerabilities can be fixed automatically, the majority require manual action and so are listed for action with guides on what needs to be done.
Some further features of Vulnerability Manager Plus are:
- A vulnerability scanner that runs every 90 minutes, crawling through your hardware inventory and assessing each device.
- A risk assessment procedure that examines the configurations of OSs and the settings of software to spot security weaknesses
- A software inventory service that identifies the current patch status of each OS and software installation on your network.
- A tool that is able to spot unauthorized or end-of-line software on devices and alert about them.
- Remediation procedures that include scripts to update configurations and block zero-day attacks.
- A patch manager that will automatically schedule needed updates for OSs and software and run them during maintenance windows.
- Hardening for Web servers and Web assets to block internet-based attacks, such as DDoS and cross-site scripting.
- System assessments for issues such as open ports, port forwarding, and access list loopholes.
- A free edition that will cover up to 25 devices
Who is it recommended for?
This package is suitable for businesses of any size. If you only want to use SaaS systems, you won’t like this package because it is only available for self-hosting. The software runs on Windows Server but it can scan endpoints running Windows, macOS, and Linux across the network.
ManageEngine Vulnerability Manager Plus runs on Windows Server and it is available for a 30-day free trial.
Pros:
- Scans multiple platforms: Operates on endpoints running Windows, macOS, and LinuxProvides a prioritized guide: Lists all vulnerabilities by severity
- Automated patching: Patches Windows, macOS, Linux, and software packages
- Identifies unauthorized software: Lists user-installed software and malware on each endpoint
Cons:
- Only available for Windows Server: No SaaS option or software for Linux
EDITOR'S CHOICE
ManageEngine Vulnerability Manager Plus is our top pick for a cybersecurity risk management tool because it is designed to help organizations detect, assess, and remediate vulnerabilities across their IT infrastructure. The package creates a centralized platform for identifying security weaknesses, misconfigurations, missing patches, and other potential risks. This allows businesses to prioritize and resolve issues before they are exploited by attackers. Vulnerability Manager Plus implements continuous vulnerability assessments, providing real-time visibility into the security posture of your network. It covers a wide range of assets, including endpoints, servers, and virtual machines, ensuring that potential risks are identified across the entire IT environment. The tool also prioritizes vulnerabilities based on severity, business impact, and exploitability, helping IT teams focus on critical issues that pose the most significant threats. In addition to identifying vulnerabilities, the system provides automated patch management, helping organizations keep their systems up to date with the latest security patches. The tool also offers detailed reports and dashboards, allowing security teams to track remediation progress and maintain compliance with industry standards.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/vulnerability-management/download.html
OS: Windows Server
2. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 is a comprehensive Security Information and Event Management (SIEM) that will detect, categorize, document, and shut down cybersecurity attacks across on-premises, cloud, and hybrid environments. The package uses machine learning-based anomaly detection and can be set up to implement responses automatically.
Key Features:
- Real-Time Monitoring: Continuous monitoring of network activities, user behavior, and security events.
- Event Correlation: Correlates data from various sources to identify potential threats.
- Threat Intelligence: Provides up-to-date threat information to enhance security measures.
- File Integrity Monitoring: Detects unauthorized changes to critical system files.
Why do we recommend it?
ManageEngine Log360 is highly recommended for its robust security features, ease of use, and cost-effectiveness. It offers comprehensive threat detection and response capabilities, making it an essential tool for safeguarding your organization’s data and infrastructure.
This software package is actually a bundle of other ManageEngine tools. These include ADAudit Plus, which provides user activity tracking, and EventLog Analyzer, which is the log collection and processing element in the package. You might not need all fo the functions in the Log360 system, in which case, you could be better off just buying those individual modules. The full Log360 bundle provides an extensive library of system security management tools.
Who is it recommended for?
ManageEngine Log360 is ideal for organizations of all sizes, particularly those with complex IT environments. It is suitable for businesses looking to enhance their cybersecurity posture, comply with regulatory requirements, and streamline their security operations. There is no Free edition of this package, so small businesses would be better off looking at EventLog Analyzer, which does have a free version.
Pros:
- User Activity Monitoring: Tracks user actions to identify suspicious behavior.
- User-Friendly Interface: Easy to navigate and manage.
- Customization: Highly customizable to fit specific security requirements.
- Integrations: Seamlessly integrates with other security tools and systems.
Cons:
- Resource intensive: The package includes many modules that will all run simultaneously.
ManageEngine Log360 installs on Windows Server. The package is available for a 30-day free trial.
3. ZenGRC
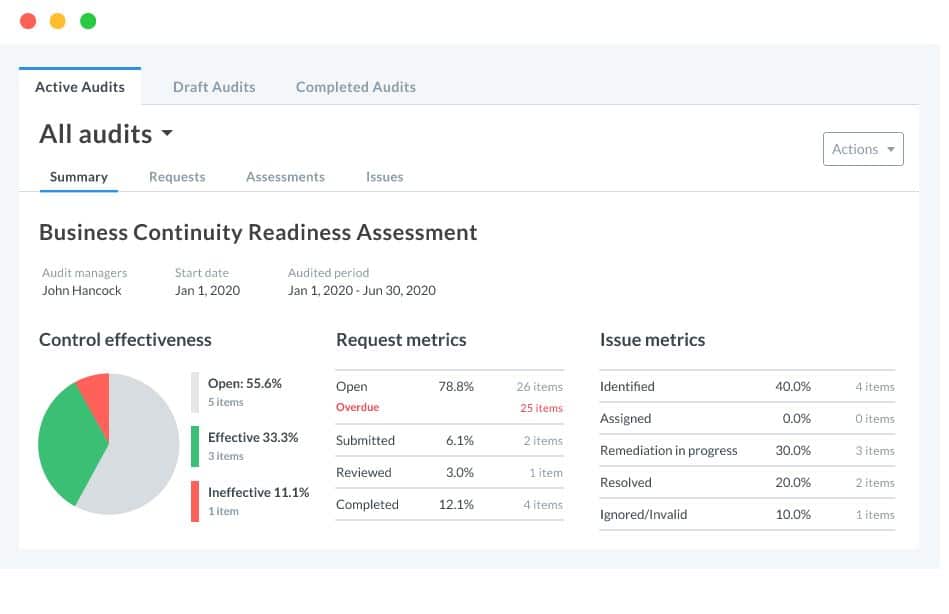
The RiskOptics ZenGRC solution allows security and compliance teams to perform audits and gather evidence using a single integrated tool that reveals information and reports on security risks in a business network.
Key Features:
- Risk Observation, Assessment, and Remediation Platform: Abbreviated to ROAR
- Assesses Divergence from Standards: Tunable for compliance
- Performs Scans to Identify Risks: Looks at user accounts, operating systems, and network device configurations
Why do we recommend it?
ZenGRC is a package of tools that enforces data privacy in accordance with specific data protection standards. Risk management is part of that remit. The package assesses your site for the presence of cybersecurity tools rather than providing that security. The main screen of the system lists the tools that you have and identifies their purpose.
This flexible solution – it comes in the cloud and on-premises versions –uses customizable control designs and tests to help protect businesses and meet the privacy expectations of their customers.
Some further features of ZenGRC:
- ZenGRC is a governance, risk, and compliance (GRC) management platform; it is ideal for businesses of all sizes in any industry looking for help in internal auditing, compliance, and IT security.
- Thanks to automatic and innovative features, simpler and faster audit cycles allow for continuous monitoring with minimum manual intervention required.
- It can evaluate risks across connections, systems, business divisions, and controls using customizable risk calculations that offer multivariable scoring and ranking options based on control frameworks and risk assessment methods like the Secure Controls Framework (SCF), National Institute of Standards and Technology (NIST) standards, and Center for Internet Security Risk Assessment Method (CIS RAM) methods.
- This risk management system can integrate with existing security solutions to evolve current risk and compliance programs; it presents it all in optimized visualizations and in-depth reporting dashboards.
- ZenGRC shows where risk is changing in a network and simplifies audit and compliance management by providing complete overviews of the control environments; it offers easy access to information necessary for program evaluation and continual compliance monitoring to address critical issues at any time.
Who is it recommended for?
This package is specifically designed to meet compliance with SOC 1/2, ISO 27001, PCI DSS, HIPAA, and SOX. However, there is no mention of GDPR, CCPA, or other protection standards for personally identifiable information. So, if you are particularly in need of a PII risk assessment service, you should look elsewhere.
Pros:
- Works to compliance: SOC1/2, ISO 27001, PCI DSS, HIPAA, and SOX
- Implement multiple frameworks: Comply with several data protection standards
- Tracks progress to compliance: Lets you know when the goal has been achieved
Cons:
- No free trial: Get a demo
Book a ZenGRC demo for FREE.
4. Resolver Risk Management Software
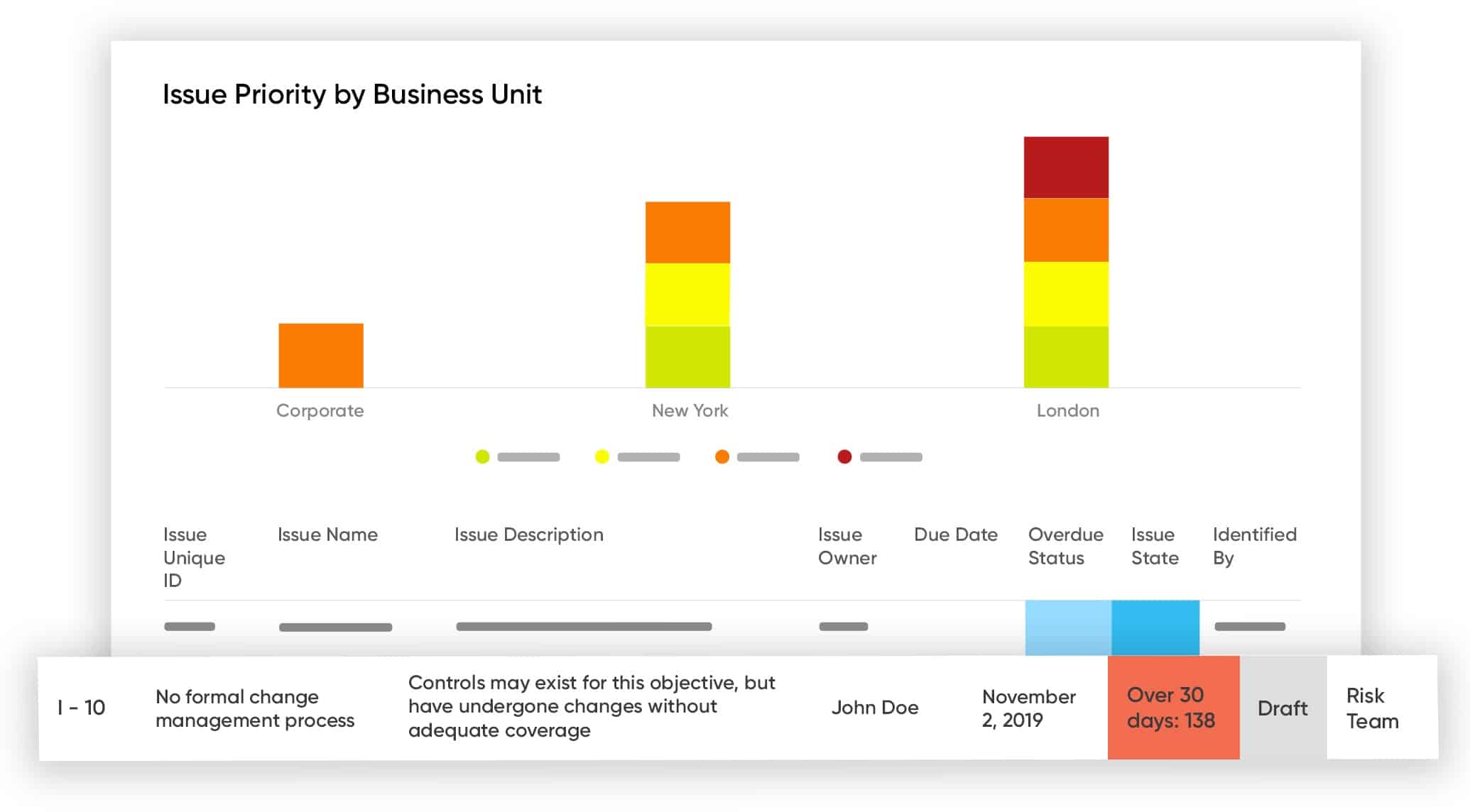
Resolver Risk Management Software offers a suite of tools that cover the risk management and security auditing needs of the entire stack of any network. It is a tool that has won numerous awards and remains an industry favorite. It can also help with other issues like compliance, incident management, and much more.
Key Features:
- Centralized Risk Assessments: Creates an enterprise-wide risk score
- Allocates Risk Remediation Tasks: Identifies roles and responsibilities
- Creates a Timeline: Highlights tasks that are overdue
Why do we recommend it?
Resolver Risk Management Software implements both internal risk assessment and third-party risk assessment. The package is a task scheduler for a team of risk assessors. You register all of the team in the package with individual accounts and assign roles. The service that assigns data-gathering goals to each team member.
What makes Resolver stand out, though, is its ability to link risks with incidents – so that assessments of what could happen are related to what did happen.
Looking at some more features of the Resolver Risk Management Software:
- Resolver allows risk managers to view all existing threats from a single platform; this helps them provide data-backed recommendations that can positively impact the bottom line.
- They can also make informed decisions to focus the right resources on the risks that have the most significant impact on the business’ mission-critical processes; the tool’s easy-to-use interface allows companies to increase adoption across their network while also making it easy to work with the solution.
- Resolver allows for accurate and up-to-date insights into the full scope of covered digital assets thanks to its real-time reports that can be made accessible to stakeholders.
- They can quickly evaluate their risks using step-by-step guidance and documentation for controlling and mitigating threats while archiving the risk events on portals that concerned stakeholders can access to help with investigations.
- It is a highly configurable solution that requires no code and uses drag-and-drop configuration to create custom security frameworks to meet any network architecture or business process workflows; the workflow and orchestration engine allows for easy definition of scheduled persons, alerts, task management, and more.
Who is it recommended for?
The main audience for this package lies with businesses that are implementing compliance with data privacy standards. The usual purpose of risk systems is to identify sensitive data and put in place systems to protect it. This tool also provides live reporting through to Service Desk teams that indicate that a breach has occurred.
Pros:
- Management automation: Removes the need for senior management to filter down instructions
- Attractive graphs and reports: Create presentations to inform those who are not directly involved in the data governance project
- Delivered from the cloud: Dispersed teams can all access the same dashboard
Cons:
- No on-premises version: This is a hosted package
Request a Resolver Risk Management Software demo for FREE.
5. SAI Global’s Digital Manager 360
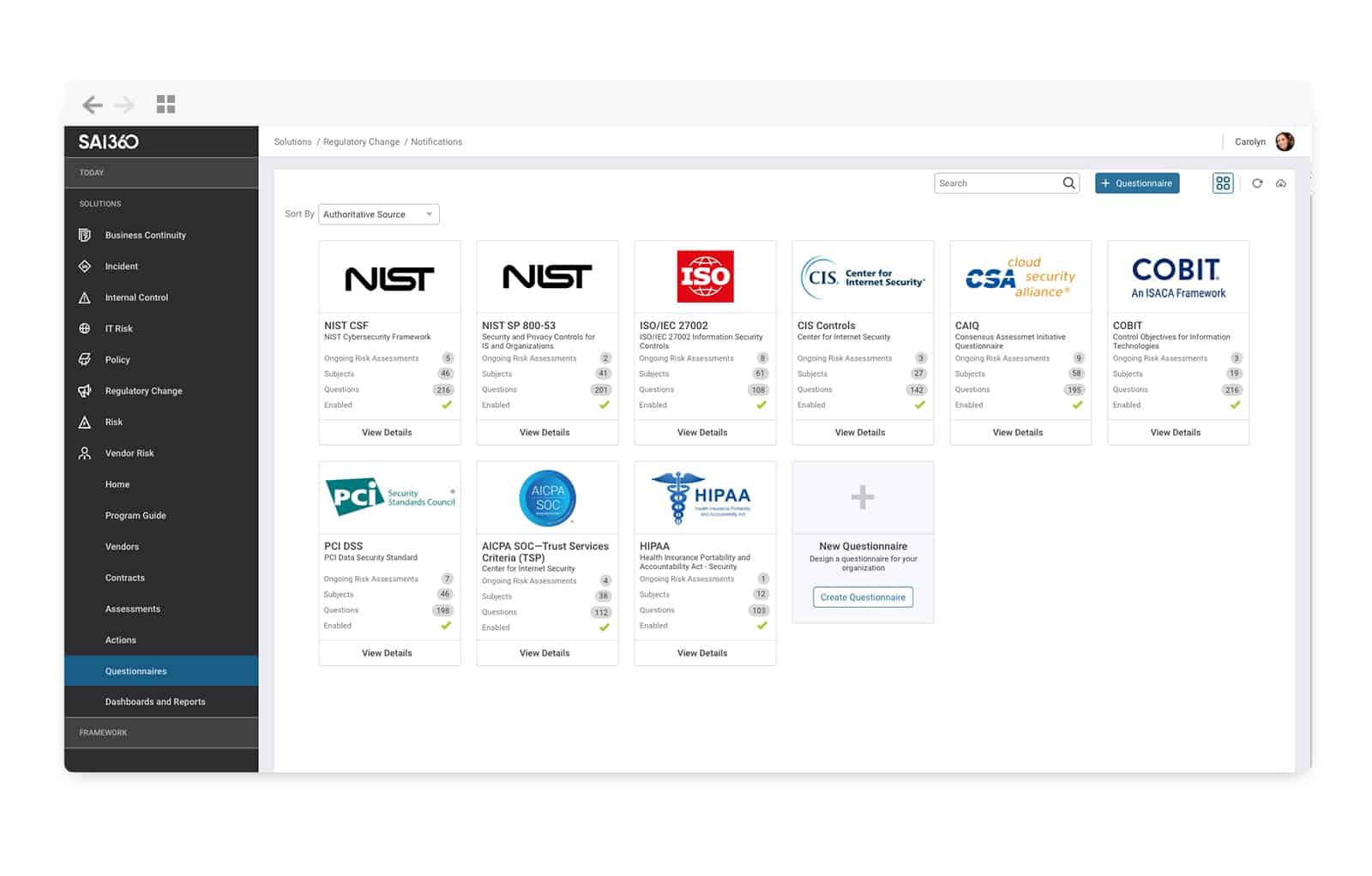
SAI Global’s Digital Manager 360 (acquired by Intertek) enables cybersecurity taskforces to manage digital risks and compliances across enterprises and extended networks. They can use the tool to assess and monitor adherence to security frameworks across the web and cross over into third-party relationships.
Key Features:
- A Choice of Standards to Follow: Includes PCI DSS, HIPAA, and CCPA
- Multiple Compliance: Get compliant with several data privacy standards simultaneously
- Employee Training: Order compliance training alongside the governance package
Why do we recommend it?
SAI Global’s Digital Manager 360 is designed to support the implementation of compliance with PCI DSS, HIPAA, and US PII protection legislation. The package includes a risk assessment service. Risk investigation extends to vulnerability management that examines the weaknesses in operating systems and data accessing software.
This GRC platform contains flexible, scalable, and configurable modules for a better insight into risk management. Some of the modules include IT Vendor Risk Management, Digital Enterprise Risk Management, Business Continuity Management, and Digital Incident Management – all of which can be used to cover every angle of a business’s IT assets and mission-critical processes.
More features from SAI Global’s Digital Manager 360:
- It provides a single, scalable cloud-based platform with proven capabilities to help reduce digital risks – straight out of the box – and the versatility of installing it on-premise.
- Minimal configuration is needed to gain complete visibility into IT risks and threats; it hits the ground running within minutes of deployment thanks to dozens of out-of-the-box integrations – which can be extended by configuring additional custom integrations.
- Businesses can cut IT security costs because it integrates well into any current IT GRC management lifecycles without costly configurations or third-party solutions; the platform improves consistency by automating tasks which helps in avoiding errors or security lapses.
- Digital Manager 360 provides a comprehensive library of over a thousand legal standard frameworks – with over 100,000 control sets – that help follow guidelines set out about industry standards and authorities.
- Administrators stay on top of issues thanks to a centralized view of risks that give insights into the whole stack of the IT infrastructure; they remain informed thanks to one-click reports and dashboards that authorized stakeholders, and decision-makers can also access.
Who is it recommended for?
SAI Global focuses on the US market. All of its PII protection services are geared towards the legislation of US states, including California, Nevada, and Maine. There isn’t even any mention of Canadian regulations in the sales pages of this tool. So, if you operate within the USA, you should consider this package.
Pros:
- Identifies risks and prioritizes them: Fix the biggest problems first
- Monitors progress: Shows the improvements already implemented
- Chart and reports: Great for presentations
Cons:
- Focused on USA compliance: Doesn’t cover GDPR
Try Digital Manager 360 – request a demo for FREE.
6. SolarWinds Cybersecurity Risk Management and Assessment Tool
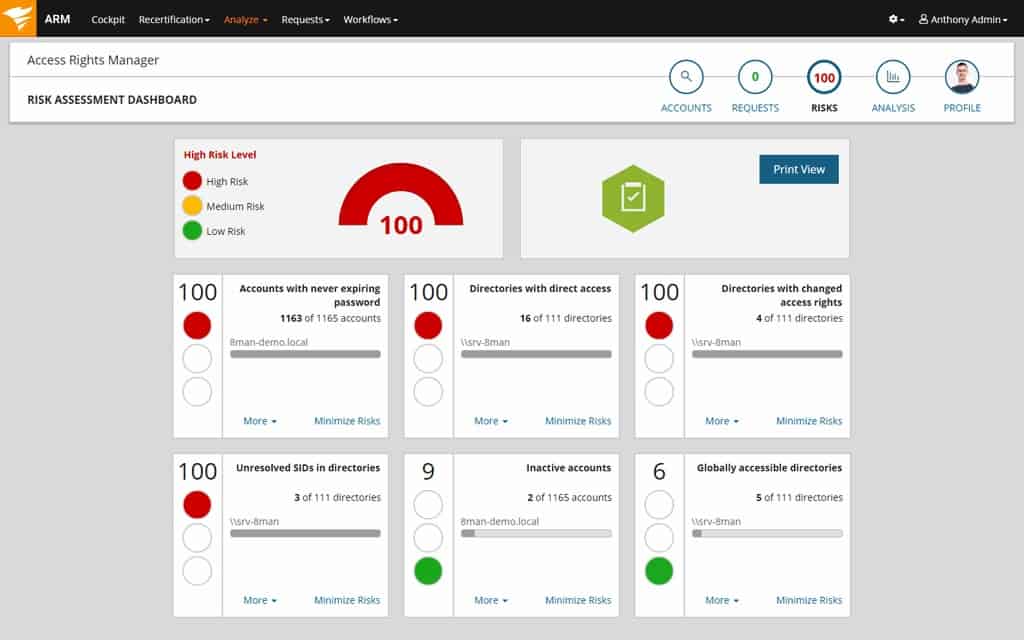
With SolarWinds Cybersecurity Risk Management and Assessment Tool, we have a tool made by one of the leading network and server management solutions makers out there. It analyzes and audits access across files, folders, and servers while proactively detecting data risks based on insecure account configurations and unauthorized accesses.
Key Features:
- Active Directory management: Use this tool as a front-end for AD
- Abandoned account detection: Clear out unused accounts
- Creates role-specific access: Provides templates to tighten access controls
- Scans for insecure account configurations: Reduces risk
- Log user activity: Look for failed login attempts
Why do we recommend it?
The SolarWinds Cybersecurity Risk Management and Assessment tool is delivered by the Access Rights Manager. This system focuses on account security and permissions management. It looks for abandoned accounts for deletion and helps you tighten up the allocation of permissions and users to groups. The system also enforces secure password policies.
Here are some more of SolarWinds Cybersecurity Risk Management and Assessment Tool features:
- This is a simple cybersecurity risk management solution for enforcing security policies with automated secure account provisioning; simplifying cybersecurity risk management allows for easy scaling to meet any changes in security and compliance mandates.
- SolarWinds Access Rights Management (ARM) is an add-on feature that allows for the easy reviews of user provisioning and permissions across the domain; it helps address IT risk exposures by reversing access, implementing two-factor authentication, enabling secure rights delegation to prevent risk exploitations before they even occur.
- The tool tracks and monitors user access activity to help minimize the impact of insider threats and mitigates any issues quickly; it offers fast and accurate account provisioning and delegation of access rights management for easier collaboration.
- Administrators stay informed with the help of accurate, detailed, and on-demand reports that outline which users accessed what assets and when.
- ARM helps with compliance by centralizing audit trails across Active Directory, helps facilitate internal and external IT security audits, and supports incident responses.
- It also helps establish cybersecurity risk assessment baselines with detailed reports that can be used for GDPR, PCI DSS, HIPAA, or IT SOX compliance.
Who is it recommended for?
This system is suitable for businesses that use Active Directory for their access rights management system. The tool runs on Windows Server, so you pretty much need to be a Windows-centric company to benefit from the tool. Implement user activity tracking with this package and log access to sensitive data.
Pros:
- Sensitive data protection: Logs access to categorized files
- User group mapping: Get a visual representation of user allocations to groups
- Authentication policies: Enforce complex passwords, password rotation, and 2FA
Cons:
- No SaaS version: Only available as a software package for Windows Server
You could try SolarWinds Cybersecurity Risk Management and Assessment Tool on a free trial.
7. LogicManager IT risk management software
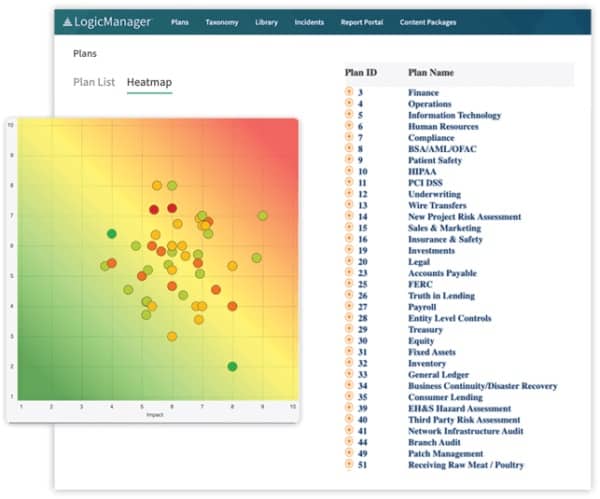
Equipped with LogicManager IT risk management software, administrators can ensure their organization’s IT systems and data are secure, accurate, and meet the industry’s ever-evolving privacy and security compliance requirements.
Key Features:
- Identifies risk dependencies: Focuses on the root issues that need to be fixed
- Project library: Centralizes all risk assessment and management documentation
- Identifies goals: Records and displays progress towards compliance
Why do we recommend it?
LogicManager IT risk management software provides a library of checks that need to be followed in order to identify risk. That risk relates to the assets of the company that are most likely to be targeted, which means sensitive data. Assessment team members get accounts within the system, with roles. The package then assigns tasks to each with deadlines.
They can also house all their compliance information in one centralized repository, complete with ready-made libraries of risks, standards, and regulations.
Let’s have a look at some features of the LogicManager IT risk management software:
- This solution helps prioritize critical resources and identify gaps in IT asset protection with intuitive and objective risk assessments; it is easy to use, and master and the reporting options provide a lot of flexibility.
- LogicManager is versatile – it offers a wide variety of solutions with features for risk management, vendor management, cybersecurity management, financial compliance, and much more.
- One forte of this tool is its reporting capabilities – it offers highly configurable and engaging reports to be used by internal stakeholders and decision-makers that can also access interactive dashboards; these reports can also be used to prove compliance to regulators or presented to boards and senior management.
- Users can generate heat maps for in-depth insights into common risks, the effectiveness of the controls in place, and assign actions based on analysis; they can see protocols that are mapped across frameworks which, in turn, help identify risks that are specific to certain parts of the business with the help of intuitive reports.
- LogicManager helps oversee risk monitoring activities – it ensures correct and efficient control placement, testing, metrics collection, and incident handling using automated workflows.
- Its historical data helps with identifying trends, trail audits, and events management over selected periods.
Who is it recommended for?
As with most of the packages on this list, the main value of this system lies in its ability to get a company into compliance with a specific data privacy standard. Once that alliance has been achieved, the service moves into the background and the risk assessment team members can return to their regular tasks.
Pros:
- Cloud-based system: Create multiple user accounts for team collaboration
- Establishes benchmarks: Enables teams to discuss shared tasks and goals
- Risk templates: Pointers for common problems
Cons:
- No free trial: No price list
Try Logicmanager IT risk management software – request a FREE demo.
8. CURA Enterprise Risk Management
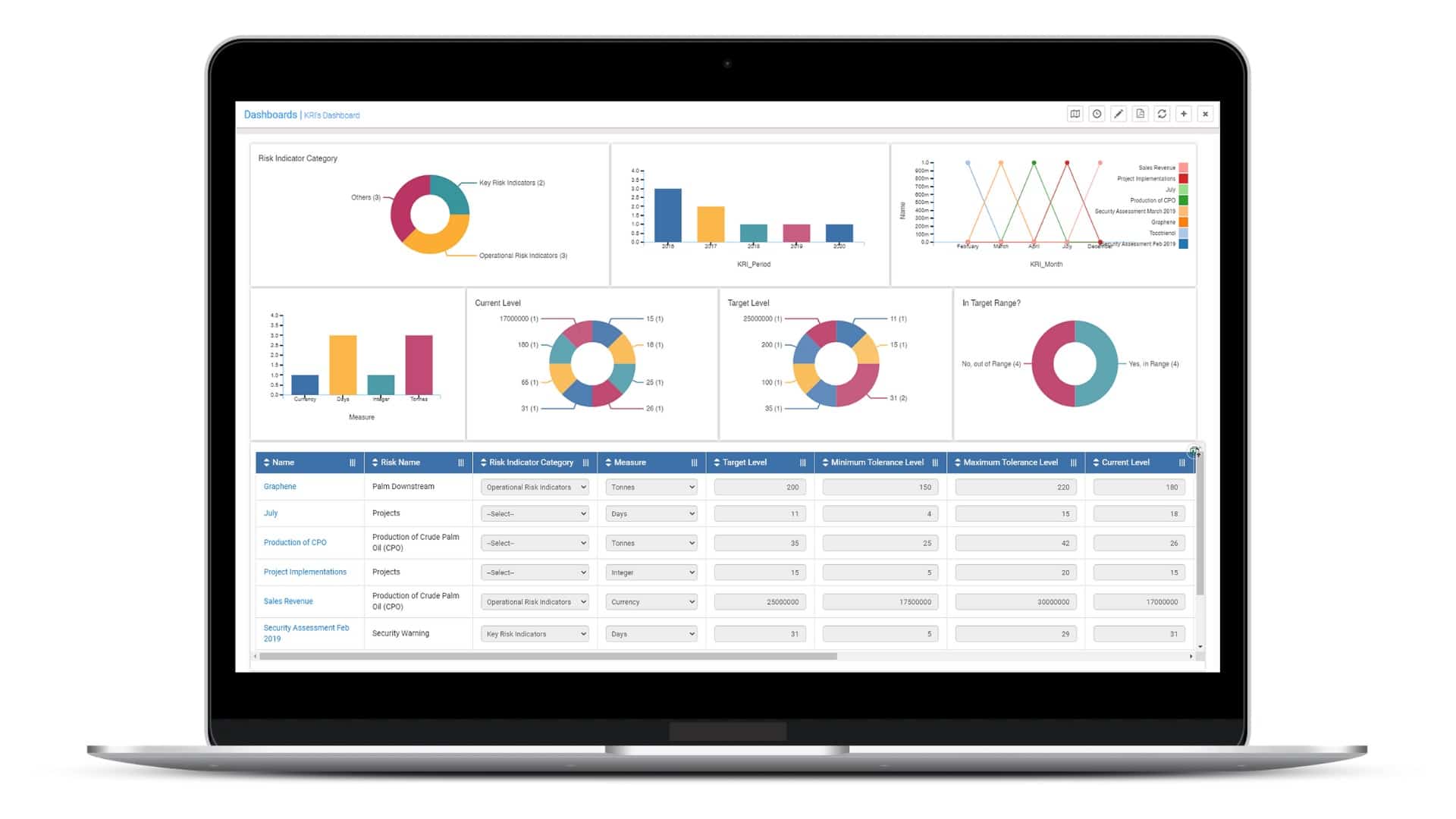
CURA Enterprise Risk Management is a web-based suite of tools for managing enterprise or project risks, incidents, business continuity, compliance, operational risks, and information security.
Key Features:
- Focused on Integrating Risk Considerations: Builds risk assessment into business decisions
- Risk Controls: Provides assessment automation
- Integration with Third-Party Tools: Build this GRC system on top of the security systems that you already use
Why do we recommend it?
CURA Enterprise Risk Management is a package of measures that can adapt working practices and IT systems to integrate automatic protection for sensitive data. The platform doesn’t implement data protection but records the actions of third-party cybersecurity tools that are already in place. If no such systems exist, the platform identifies the types of systems that are needed.
It enables businesses to effectively and efficiently manage their cybersecurity risks and prevent loss of data resulting from human error factors and other external events.
There are more features of the CURA Enterprise Risk Management, including:
- Visual and interactive dashboards, surveys, a self-assessment portal, notifications, workflow management, multiple-deployment capabilities, and custom configurations are some of the primary features of CURA.
- The platform allows for tracking of information via libraries, data parameters, and calculation metrics; it helps create automated, repeatable processes – that include risk assessment and analysis – and the implementation of risk controls.
- Meanwhile, its applications – built on a unified platform – can be integrated with third-party dashboards and reporting tools to create a GRC system across the full scope of the enterprise.
- It has solutions available as standalone applications or add-on modules to a more comprehensive implementation based on the CURA Enterprise GRC Platform.
- It offers real-time visibility through interactive dashboards and reports and alerts users and managers to tasks, actions, and escalations regarding risk resolutions and controls testing.
Who is it recommended for?
The emphasis of this package is ongoing compliance monitoring. However, the makers of the tool realized that the task of compliance management is easier if the platform can dictate the systems that should be put in place to enforce security. Thus, it is also a risk assessment and compliance implementation package.
Pros:
- User accounts for team members: Give access to risk management team members with different roles
- Constructs a timeline: Sets up goals and priorities and allocates tasks
- Alerts for priorities: Reminds those responsible for tasks if they are falling behind
Cons:
- More for creating GRC systems: Not so hot at assessing current services for compliance shortfalls
Request a CURA Enterprise Risk Management demo for FREE.
9. Pathlock
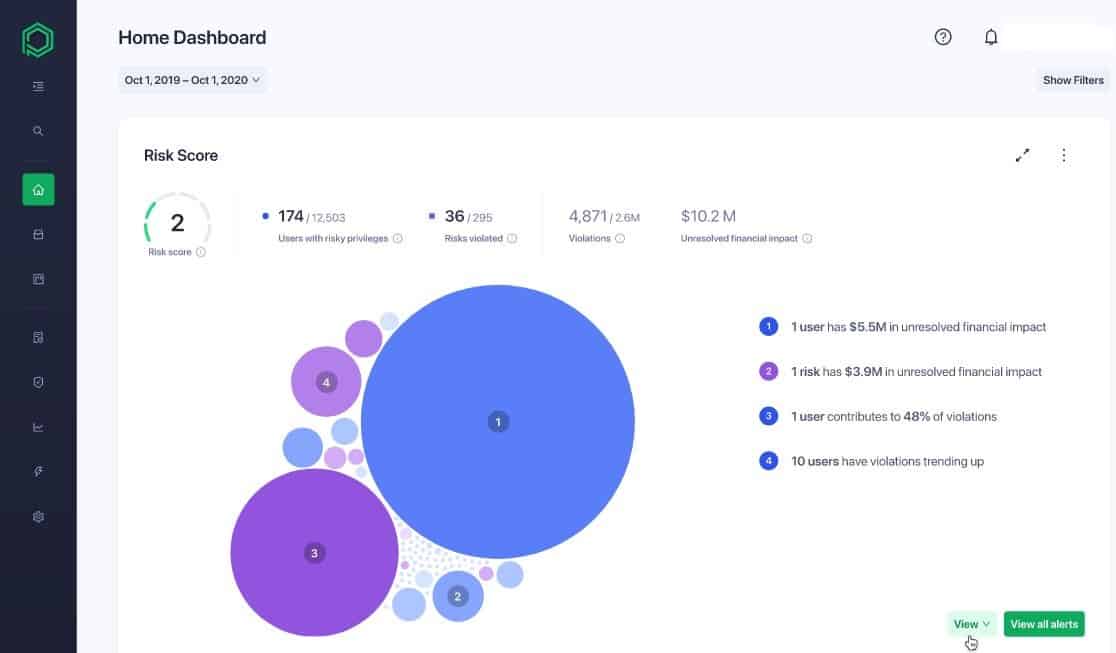
Pathlock is a governance, risk, and compliance tool for finance, IT, and other mission-critical business processes.
Key Features:
- A Platform of Tools: Assemble the modules to create a full GRC package
- Includes Sensitive Data Management: Identifies and categorizes data that needs to be protected
- Data Loss Prevention Tools: Protects data against leakage, misuse, and theft
Why do we recommend it?
Pathlock provides three phases of compliance management, which includes risk management. Those phases start with the introduction of GRC systems, which is where risk management is the most important task. It moves through to control implementation, and then ongoing cybersecurity protection.
It also monitors user activity to spot out-of-policy transactional activity and prevent unauthorized access to sensitive data – with protection at the database or application level and the field level.
More Pathlock features:
- With Pathlock, administrators can see access violations and understand the business impact of their approval decisions; they can track breaches and incidents to ensure that corrective action is taken immediately.
- It demonstrates risk reduction over time using a central dashboard; it provides stakeholders with visibility into the actual bottom-line cost of risk and its impact on the business processes; and with this in mind, the tool also prioritizes compliance efforts based on the dollar-value effect of each risk.
- It is the tool to use when trying to achieve compliance to the likes of SOX, HIPAA, PCI, and GDPR – as it helps identify the relevant data that needs to be secured so administrators can put the proper measures in place to restrict access.
Who is it recommended for?
This package is designed to create compliance with PCI DSS, HIPAA, CCPA, and GDPR, and other standards. The package adapts to each phase of GRC adoption, ending up as a security monitoring system, similar to a SOAR. Unfortunately, Pathlock doesn’t publish a price list or even descriptions of its plans, which makes assessing its suitability for different types of businesses difficult.
Pros:
- User security: Identifies weak points in access rights management
- Configuration management: Identifies configuration errors, produces remediation, and prevents further change
- Manual and automated process controls: Enforces best practices
Cons:
- No price list: No explanation of what packages are available
Request a Pathlock demo for FREE.
What steps are involved in cybersecurity risk management?
Ok; now that we have seen the solutions, let’s have a brief look at the five significant steps involved in cybersecurity risk management:
- Taking stock of valuable digital assets – this helps with defining the scope of the risk management campaign.
- Identifying risks, past and present – laying out any and everything that could happen to all aspects (storage, communication, sharing, connectivity, processing, etc.) of the assets from both within and beyond the network’s boundaries.
- Planning for an attack – testing attacks using known and unknown methods to see the impacts and worse-case scenarios; then creating controls for the prevention of each one of these attacks.
- Reviewing controls – time should be spent studying each management to gauge efficiency and accuracy before being accepted as a permanent solution.
- Creating cybersecurity awareness – this step stops the problems from occurring in the first place. A security-aware workforce addresses the cybersecurity risk issue at the root level by totally avoiding behaviors that create them, to begin with.
Advantages of risk management and implementing cybersecurity risk management tools
Maintaining an efficient security infrastructure creates the ability to respond quickly in the face of attacks. In addition, these tools help in quickly identifying threats, assessing how dangerous they are, and improving mitigation times and efforts. And finally, their capability to prioritize the risks by threat levels ensures resources are correctly allocated.
But, there’s more:
- Cost-saving – cybersecurity incidents costly affairs to clean up. Also, in case of successful attacks, the damage can linger, causing issues for a long time. In some cases, the businesses never recover from a data loss.
- More security health insight – security audits provide an opportunity to learn how well a business handles its security and find out where improvement can be made.
- Compliance – businesses can make sure they meet all compliance requirements and governmental standards. This increases trust with their clients and even gives them a competitive edge over similar enterprises.
- Benefits for employees – staff members will be more tech-savvy and especially cybersecurity aware and will help secure the business’ data. In addition, regular cybersecurity awareness workshops and IT training should be part of a business
A business gains by choosing to deploy one of the seven best cybersecurity risk management solutions we have just seen. And to be honest, there is no downside to these tools. What do you think? Let us know; leave us a comment below.