Although the Cloud-Native Application Protection Platform (CNAPP) is a new concept, it builds on four pre-existing technologies. However, these four predecessors are relatively new:
- Cloud Security Posture Management (CSPM) Risk scanning for cloud assets
- Cloud Service Network Security (CSNS) Implemented by a web application firewall (WAF)
- Cloud Infrastructure Entitlement Management (CIEM) Access right management for the cloud
- Cloud Workload Protection Platform (CWPP) Threat protection for cloud-based assets
The beauty of this modular composition is that many cloud protection providers already had the building blocks in place, so all they had to do was package them into a bundle to launch their new CNAPP products. Consequently, there are some excellent CNAPP systems to choose from.
Here is our list of the best Cloud-Native Application Protection Platforms:
- Cyscale CNAPP This platform integrates compliance management for HIPAA, PCI DSS, GDPR, and SOC 2 into its cloud security features.
- CrowdStrike Falcon Cloud Security This package takes the CrowdStrike Falcon brand into comprehensive cloud security. This package includes a threat intelligence feed and integration with the AWS, Azure, and GCP systems.
- Ermetic Cloud Native Application Protection Platform This challenger provider grew its CNAPP out of a successful CIEM, which was its first product and has now expanded to a full cloud security package.
- PingSafe This cloud-based service is a CNAPP with all of the classic elements of CSPM, CWPP, Kubernetes Security Posture Management, Infrastructure as Code, and Cloud Detection and Response.
- Zscaler Posture Control This new package from an established Zero Trust Access provider includes a threat intelligence feed and strong user account controls.
- Palo Alto Prisma Cloud Code, platform, and service security scanning and attack prevention from a leader in cybersecurity.
- Check Point CloudGuard This cloud platform includes CSPM, CSNS, and CWPP modules that combine into a CNAPP service.
You can read more about each of these options in the following sections.
The Best Cloud Native Application Protection Platforms
Our methodology for selecting a CNAPP
We reviewed the market for Cloud-Native Application Protection Platforms and analyzed options based on the following criteria:
- A package that includes CSPM, CSNS, CIEM, and CWPP
- Infrastructure-as-Code configuration management and vulnerability scanning
- Kubernetes Security Posture Management (KSPM) to protect the coordinators of container deployment
- CI/CD pipeline integration
- Messaging to project management tools
- A free trial or a demo for a no-cost assessment opportunity
- A hosted package that provides value for money
With these selection criteria in mind, we identified emerging CNAPP systems that are out of the gate at the head of the pack.
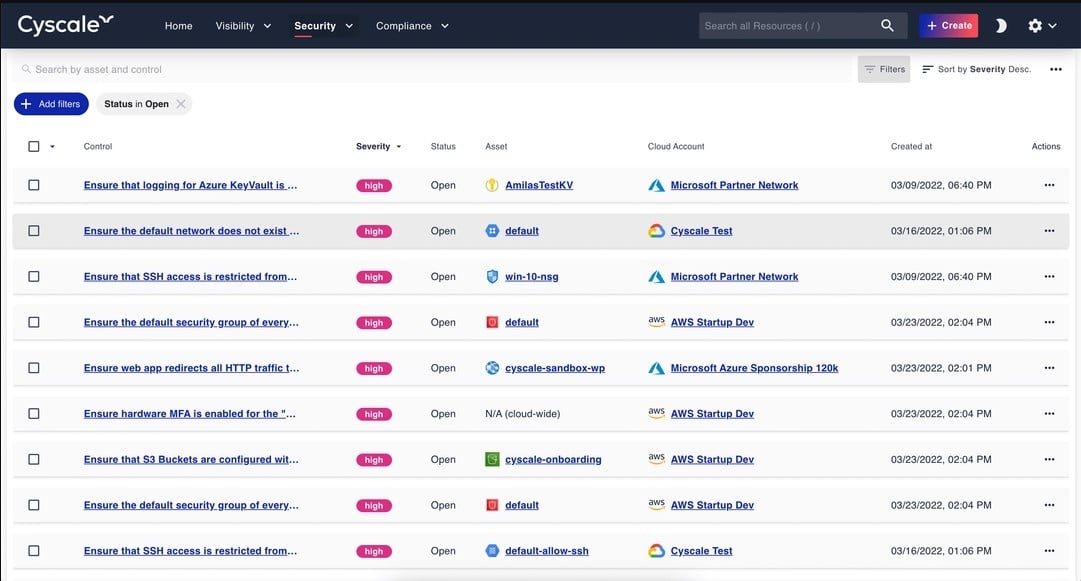
1. Cyscale CNAPP
Cyscale CNAPP is a new cloud security service that provides compliance management as well as threat prevention and detection systems. This package can protect AWS, GCP, Azure, and Alibaba Cloud systems. It will scan VMs, containers, storage, compute accounts, and serverless hosts.
Key Features:
- The Full CNAPP Package: CSPM, CWPP, CIEM, and KSPM
- Compliance Management: HIPAA, PCI DSS, GDPR, and SOC 2
- Vulnerability Scanning: Provided by the CSPM unit
- Live Security Scanning: From the CWPP module
- Access Rights Security Assessments: From the CIEM service
Why do we recommend it?
Cyscale CNAPP provides compliance management that is threaded through the security platform. This is the outstanding feature of the service and isn’t matched by any of the other tools on this list. This system can protect Alibaba Cloud accounts, which is another service that rivals on this list do not provide.
The console presents a library of security control templates, which make creating a security policy easy. These settings are then applied to the threat prevention measures of the CSPM and the threat detection services of the CWPP.
Who is it recommended for?
This platform is important for businesses that handle sensitive data through their Cloud systems or that have user-facing interfaces that could, if not properly secured, provide an entry point for data thieves. The system can also generate compliance reports and guide data-handling departments.
Pros:
- Data Security: Establishes a data inventory
- Protects Virtual Systems: Scanning for VMs, containers, and Kubernetes
- Protects Software Running on Four Cloud Platforms: AWS, Azure, GCP, and Alibaba Cloud
- Security Policy Templates: Provides guidance for security strategies without imposing one framework
- Suitable for Operations Management: Watches over managed applications that are hosted on cloud platforms
Cons:
- Not a Development Security Testing Service: Not suitable for DevOps teams
The main strength of the console for Cyscale is that it makes creating security controls easy through templates and compliance automation. Get a 14-day free trial to assess the service.
2. CrowdStrike Falcon Cloud Security
CrowdStrike Falcon Cloud Security is the definitive CNAPP on the market at the moment. This system checks all the boxes of a CNAPP platform and then adds a few more features, such as a threat intelligence feed. The package specifically monitors the platform, services, and hosted software on AWS, Azure, and Google Cloud Platform.
Key Features:
- Threat Intelligence Feed: Adapts the threat hunting strategy according to known current threats
- Container and Platform Security Scanning: Examines application delivery mechanisms
- Preventative Security Scans for Microservices: Serverless hosting configuration checks
- Code Repository Integration: Good for DevOps teams
Why do we recommend it?
CrowdStrike Falcon Cloud Security builds on CrowdStrike’s growing excellence in cloud security. The company started out providing a hybrid AV under the Falcon brand and quickly moved to Cloud security. This package speeds up threat blocking through preventative measures in every layer of Web application provision plus adaptation to current threat campaigns.
This system provides configuration checks for platforms, containers, Kubernetes, and middleware. It also provides scanning for code under development in a continuous testing scenario for CI/CD pipelines, reporting back to development management tools, and bug tracking. Live code is checked as it is delivered and responses or other access by users are checked for malicious activity.
The system provides reports for development activity and live scans for Web applications that are running. The tool’s console shows alerts for detected threats but instant remediation will occur simultaneously and automatically.
Who is it recommended for?
This platform is a useful package for teams that provide and support Web applications. The system can be used just by an operations team, or it can be integrated into the production pipeline for businesses that also develop their own applications in a DevOps scenario.
Pros:
- Security Orchestration: Production security testing automation
- Vulnerability Scanning of Cloud Infrastructure: Preventative configuration checks
- Tracking of Live App Activity: Includes attack surface scanning
- Identifies Attacks on Infrastructure: Blocks attacks on running applications
Cons:
- Lacks User Account Management: Missing insider threat detection
The CrowdStrike system has a strong emphasis on prevention and protection against external threats. It ensures that all components involved in the hosting and delivering applications are hardened against attack and monitored for live malicious misuse. It isn’t so strong at insider threat detection. You can contact CrowdStrike to get an assessment of your Cloud-based system for a recommendation on which Cloud security services you need.
3. Ermetic Cloud Native Application Protection Platform
Ermetic Cloud Native Application Protection Platform is strong on user account security. The platform’s creators started as a Cloud Identity and Entitlement Management (CIEM) provider. The group added Cloud Security Posture Management (CSPM) and a Cloud Workload Protection Platform (CWPP) to form its CNAPP solution.
Key Features:
- Suitable for DevOps: Prevents security weaknesses being written into the code
- Blocks Internal Threats: Also external threat prevention and protection
- Protects Services on Major Cloud Platforms: Integration with AWS, GCP, and Azure
Why do we recommend it?
DevOps strategies can open up backend weaknesses in Web application security, particularly if temporary staff or external consultancies are drafted in for the development effort. Keeping track of all the people involved in a large Web system’s development can be almost impossible, so tightly controlling backend access to live systems is very important.
This platform can provide a Zero Trust user access management strategy for internal users, as well as external prevention and protection security scanning against external attacks.
The CSPM provides a discovery service for all resources. It scans cloud accounts, including serverless hosting systems, containers, and Kubernetes coordinators, and merges into the CIEM for user account auditing and access controls. This process hardens systems against attack by tightening asset configurations, removing abandoned accounts, improving password security, and limiting privileges and permissions.
The CWPP section scans those same assets, looking for access to sensitive data or attempts to get into services, such as databases, through front-end attacks.
Who is it recommended for?
Ermetic stresses that its CNAPP is designed for DevSecOps. It is suitable for use by Web applications and mobile app providers. The crucial attribute of the target market for this system is Web app owners and managers. This is whether those apps were developed in-house, created with the assistance of external consultants, or acquired.
Pros:
- A Good CIEM: Strong user account security and access controls
- Provides a CSPM: Threat prevention scans: System hardening
- Respectable CWPP: Live data protection and threat detection
Cons:
- Doesn’t Include a Threat Intelligence Feed: Would speed up threat hunting
The Ermetic package includes many development security features such as scanning for Infrastructure-as-Code systems and integration into bug trackers, code repositories, and development management tools. Access a free trial.
4. PingSafe
The PingSafe CNAPP has a range of applications, which include vulnerability management, and penetration testing as an offensive security tool. The system will scan cloud platforms and identify configuration weaknesses and credentials exposure. The tool will secure cloud platforms, Web applications, Infrastructure as Code, and containers.
Key Features:
- A CSPM: Implements preventative scanning
- A CWPP Unit: For live application protection
- Infrastructure Security: Through Infrastructure-as-Code security and Kubernetes Security Posture Management
Why do we recommend it?
PingSafe is a flexible package that prevents, monitors, blocks, and analyzes attacks on cloud systems. This system is based in the cloud and examines all of the infrastructure that is involved in app and platform delivery, such as Infrastructure as Code and the containers that deliver the applications.
This system will scan all of your cloud systems and applications continuously. It can spot code injection and probing activity. It will implement repairs on code that has been altered by an attacker, stripping out those new lines to restore the system to its original secure state. The tool will also analyze past attacks and review code and infrastructure it looks for more changes that can be made to harden the system against another attack of the same type.
PingSafe is a comprehensive package for securing cloud-based applications to protect them against attacks. The platform doesn’t include access rights management or live performance monitor; it focuses on identifying and rectifying security weaknesses and looking for external threats. This platform will implement automated responses if it identifies a threat and it will also inform your team of an ongoing attack. Retrospective analysis makes sure that the attack vector will never succeed again.
Who is it recommended for?
This package is suitable for any business that develops and supports Web applications and SaaS platforms for use by other companies. It is also useful for companies that pay for those services. The package also includes compliance management, so it is particularly necessary for companies that handle sensitive data.
Pros:
- Code Repository Integration: Security scanning for CI/CD pipelines
- Offensive Security Engine: Attack analysis and replays
- Cloud Detection and Response: Automated responses on the detection of a threat
Cons:
- Doesn’t Include a Cloud Infrastructure Entitlement Management Unit: CIEM would provide access security assessments
The PingSafe system can have many uses and your team might not use all of its systems, for example, its penetration testing tools. There isn’t a free trial for the CNAPP package but you can get a demo.
5. Zscaler Posture Control
Zscaler Posture Control is a new addition to a platform that has had great success in providing security for virtual networks and implementing Zero Trust Access for cloud services. The Zscaler platform provides building blocks that can be assembled into different security strategies. To implement CNAPP here, you would use the Zero Trust Access components for a CIEM solution and then add on CSPM and CWPP units.
Key Features:
- Flexible, Modular Approach: A set of tools that you can assemble into your preferred security strategy
- Aimed at DevOps Environments: Facilities for preventative testing during development and release phases
- Threat Intelligence: From Zscaler ThreatLabz
Why do we recommend it?
Zscaler Posture Control is a self-assembly solution that demystifies the terminology of cloud security. You would construct a security service that suits your business, rather than trying to fit a buzzword over your system. After you implement all the units that give you what you want, you might end up with something that an expert would call a SASE or a ZTA, or a CNAPP.
The Zscaler platform provides system hardening and then security scanning for platforms, containers, and Kubernetes. The platform also offers data protection measures and compliance reporting.
Who is it recommended for?
The company presents its CNAPP for use by DevOps teams. However, it suits any business that uses or manages Cloud systems. You don’t have to be a cybersecurity expert to set up a sophisticated cloud security service with this package, so it is suitable for small businesses as well as large corporations.
Pros:
- Infrastructure-as-Code Security: Implemented during development to catch security weaknesses
- Built-In Access Controls: Implements a least privileged access strategy
- Includes Connection Security: Zero Trust Connectivity
Cons:
- Doesn’t Impose a Specific Strategy: Suitable for businesses that have their own security experts
Zscaler is a low-stress solution because it doesn’t get too caught up in cybersecurity terminology – its services are easy to understand. The Zscaler menu of services has grown rapidly, and now its subscription plan structure has become complicated. The best way to work out which plan you need is to request a demo, which also provides you with a consultation.
6. Palo Alto Prisma Cloud
Palo Alto Prisma Cloud has been around for a while and pre-dates the creation of the CNAPP term. So, this was implementing CNAPP by providing all the cloud security modules that anyone would need. This system has extensive development management modules and integrations with bug trackers and project management systems.
Key Features:
- Suitable for DevOps Teams: Specializes in security testing during development and release stages for Web applications and SaaS systems
- Threat Intelligence Feed: Native to the Prisma Cloud platform
- Cloud Network Security: VPN-based connection protection
Why do we recommend it?
Palo Alto Prisma Cloud is a product by a highly-respected brand. It is similar to the Zscaler system in that it presents modules that provide so many options that CNAPP is a subset of everything that you could do with the platform’s modules.
The Prisma Cloud platform includes all the classic elements of CNAPP provision: Access control, WAF, CSPM, and CWPP. This system also provides extras that are suitable for development teams. These include code version control, developer access controls, Infrastructure-as-Code security assessments, and development management system integration.
Who is it recommended for?
The full platform is suitable for DevOps teams. The full package is very comprehensive and, although Palo Alto doesn’t publish a price list, it feels expensive. This is a solution for large industrial-scale developers and provides Web applications and SaaS systems. It would be too much for small developers or businesses that use cloud services instead of creating them.
Pros:
- Very Comprehensive Package: Includes nine specialized cloud security modules
- A Reliable and Competent Provider: Palo Alto is a leading cybersecurity brand
- Identifies Secret Exposure Opportunities: Implemented by a CSPM
Cons:
- No Price List: You have to request a quote
It would be nice to see a price list and what packages are available from the platform. For example, if it is possible to pay for only some services of the platform, then the market for the Prisma Cloud system would be much wider. You can assess Palo Alto Prisma Cloud with a free trial.
7. Check Point CloudGuard
Check Point CloudGuard is another reliable system from a highly respected provider that understood all the elements of CNAPP and delivered them before the term was invented. The package is composed of Cloud Security Posture Management, a Cloud Workload Protection Platform, Cloud Infrastructure Entitlement Management, Web Application and API Security, and Network Security.
Key Features:
- Suitable for Web Application Development: Security testing in the CI/CD pipeline
- Live Application Support: With its Continuous Cloud Security module
- Pipeline Security: Code and SBOM security
Why do we recommend it?
Check Point CloudGuard is such a close competitor to Palo Alto Prisma Cloud that it would be unfair to mention one and not the other. Check Point is as respected as Palo Alto in the cybersecurity marketplace, and both platforms provide extensive protection for DevOps teams.
The Check Point system enforces security standards in the development phase for Web applications and checks that interactions with services, such as APIs, hosting platforms, and delivery systems don’t reveal internal security controls or provide entry points for intruders or malware. Those checks are repeated into production and during the service life of the applications.
The package constantly verifies that configurations in services haven’t been set up with weaknesses or loosened as an operations workaround in response to some access or performance problems.
The system provides separate access controls for developers, operations technicians, users, and customers.
Who is it recommended for?
This package is suitable for large-scale developers and providers of Web or cloud systems. For example, a business that delivers its software on the SaaS model would use CloudGuard. The package is so similar to Palo Alto Prisma Cloud that any business considering one should also try the other.
Pros:
- Development Security: Scans code from within the IDE
- User Account Categories: Provides account types for developers, technicians, users, and customers
- Compliance Management: Implemented by the CSPM module
Cons:
- No Price List: You have to consult for a quote
You can get a requirements assessment for your system from a Check Point security consultant.