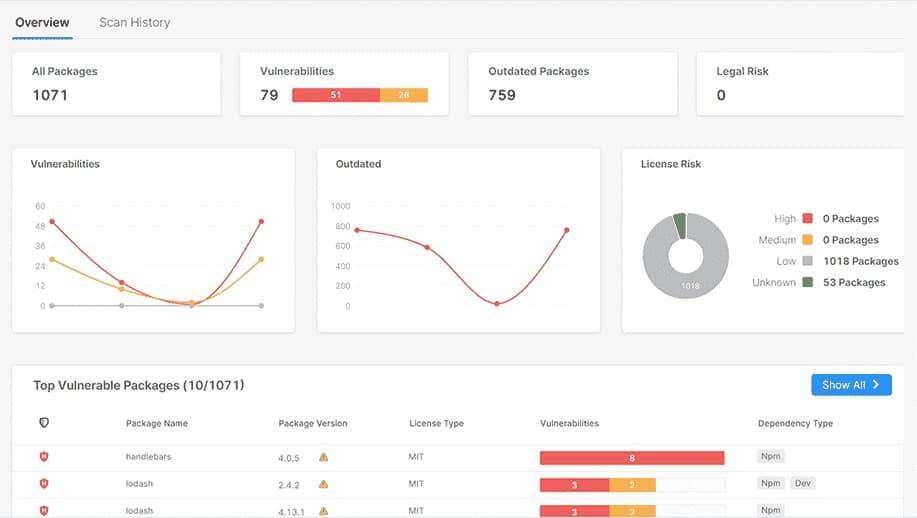
There are several strategies for Application Security Testing (AST), and it can be challenging to work out which type you need for your enterprise. The first step in this task is to identify each kind of AST.
Look for:
- DAST – Dynamic application security testing
- SAST – Static application security testing
- IAST – Interactive application security testing
There are only two types of testing systems: DAST and SAST. IAST is a combination of both DAST and SAST. Dynamic application security testing involves running the application, and static application security testing performs its tasks by analyzing the program’s code.
Here is our list of the best applications security testing tools:
- GitLab Ultimate CI/CD pipeline management package with a DAST system built. This is a cloud-based service.
- AppCheck This cloud-based service integrates with project management and issue tracking systems.
- Invicti DAST package can also operate as a vulnerability scanner. This system can be integrated into a CI/CD pipeline, and it helps towards compliance with HIPAA and PCI DSS. Available as a cloud service or for installation on Windows or Windows Server.
- Aikido Security Cloud-based platform provides a range of security testing services that include software composition analysis, static application security testing, and dynamic application security testing units.
- SonarCloud Hosted code quality and security analysis tool integrates with CI/CD platforms, providing real-time feedback to ensure clean, maintainable code.
- Acunetix Automated DAST system that is ideal for use by IT Operations technicians. It runs on Windows, macOS, and Linux.
- Checkmarx Cloud-based application testing platform that offers DAST and SAST services, which will give you an IAST if you combine the two plans. CI/CD pipeline integration makes this a good choice for DevOps teams.
- Veracode Cloud-based platform offers a range of application security testing services, including DAST and SAST packages. The company also has a penetration testing team.
- HCL AppScan DAST, SAST, and IAST options to test web and mobile apps. Offered as a cloud platform, but the software can also be self-hosted on Windows and Windows Server.
You can read more about each of these options in the following sections.
DAST is the only method that the users of commercial software can deploy. Without access to the code of an application, You are left with one option – run the software and test scenarios. This is a type of penetration testing or vulnerability scanning. The testing system starts with a list of known vulnerabilities and watches the operations of the application to see if that weakness exists.
SAST is a little like a QA check on code before it moves into acceptance testing, and it is part of unit testing. Like the DAST system, the SAST package has a list of weaknesses to look out for when reading through the program.
So, SAST is used for code verification, and DAST is used for acceptance testing. Businesses that produce commercial software need to make all efforts to ensure that the products do not include security weaknesses. This would consist of those companies that run SaaS platforms.
Software producers need to catch errors and weaknesses early to minimize the amount of rework that has to be done to fix the detected problem. So, the development team would use SAST. The marketers of that software and the technicians who will be supporting it once it is live need to perform DAST exercises to ensure no security problems in the system before it is made available to customers.
So, those businesses using both SAST and DAST would benefit from an application security testing package that performs both types of tests – an IAST system.
This is a very brief explanation of the meanings of DAST, SAST, and IAST. You can learn more about dynamic application security testing by looking at DAST (Dynamic Application Security Testing), including DAST tools. For a detailed explanation of static application security testing, could you read SAST (Static Application Security Testing), including SAST tools. Finally, you will find more information on interactive application security testing in What is IAST (Interactive Application Security Testing), including IAST tools? We have summarized their recommendations below if you have time to read the three reports.
The Best Application Security Testing Tools
When looking for an application security testing system, you need to look for services advertised as SAST, DAST, or IAST.
What should you look for in an application security testing tool for your business?
We reviewed the market for ASTs and analyzed tools based on the following criteria:
- Package that provides tools for manual testing and automated systems
- Selection that includes on-premises tools and cloud-based services
- Option to run tests on software that is still inaccessible to the outside world
- Testing services that can identify when different modules have been called
- Service that will integrate with project management and bug tracking systems
- Free trial or a free demo for a risk-free assessment
- Value for money, represented by a good set of tools at a reasonable price
With these selection criteria in mind, we looked for a range of AST systems suitable for all types of businesses.
1. GitLab Ultimate
GitLab is a source code management system that is delivered from the cloud. The package is available in three plans, and the lowest of these is Free. Unfortunately, that base plan doesn’t include many project management features, and you have to go up to the top edition, Ultimate, to get application security testing.
Key Features:
- Dynamic Testing: Provides on-demand DAST capabilities for comprehensive application security.
- Developer Support: Tailored features and tools to aid developer productivity and code security.
- CI/CD Integration: Seamlessly incorporates into continuous integration and deployment processes for streamlined workflows.
Why do we recommend it?
GitLab Ultimate is favored for its dynamic testing capabilities and developer-centric features, providing essential tools for improving code security and productivity within DevOps workflows.
The DAST functions of GitLab Ultimate are available on demand. Still, they can be integrated into the development platform and scanned every time code is committed to the repository. This gives feedback with actionable insights into the security weaknesses in the code, enabling developers to fix the problems quickly. This service runs within the CI/CD framework included with GitLab Ultimate.
Who is it recommended for?
Recommended for development teams needing advanced security testing features integrated directly into CI/CD pipelines, especially those looking to enhance API security and automate code testing.
Pros:
- API Security Insights: Delivers targeted DAST for API testing, offering valuable feedback for immediate improvements.
- Automated Code Testing: Facilitates automatic dynamic and static analysis of newly committed code, enhancing security.
- Optimized DevOps Practices: Supports efficient DevOps workflows, integrating security into the development lifecycle.
Cons:
- Limited Plan Accessibility: Advanced testing features are not available in the Free version, requiring an upgrade to Ultimate.
GitLab Ultimate is also available for self-hosting on a Linux server or a cloud account. The package is offered on a 30-day free trial.
2. AppCheck
AppCheck is a SaaS platform that offers application security testing services. These are automated tools, but a penetration testing consultancy developed them, and they also offer their services for human-driven testing. However, penetration testing from a team is an expensive exercise and not intended for regular app testing.
Key Features:
- Comprehensive AST: Offers a blend of DAST and SAST through an IAST approach for thorough security testing.
- On-Demand Scanning: Enables vulnerability scanning whenever needed, ensuring flexibility.
- Expert Backing: Developed and supported by experienced penetration testers for enhanced accuracy.
Why do we recommend it?
AppCheck stands out for its hybrid approach to application security testing, combining DAST and SAST methodologies through an IAST framework, supported by expert penetration testers.
The AppCheck automated testing services perform a mix of both DAST and SAST to create an IAST package. The tester can be plugged into a CI/CD workflow, and results can be channeled through project management tools, such as JIRA and Team City.
Who is it recommended for?
It’s particularly suited for teams requiring flexible, on-demand vulnerability scanning and those who value the integration of automated tools with the option for expert human penetration testing insights.
Pros:
- CI/CD Pipeline Compatibility: Seamlessly integrates with continuous integration and deployment workflows.
- Automated Reporting: Streamlines feedback through integration with project management tools like JIRA.
- Professional Expertise: Combines automated tools with the option for expert human penetration testing.
Cons:
- Cloud-Only Deployment: Lacks an on-premises solution, limiting deployment flexibility for some organizations.
The AppCheck system is cloud hosted, so there is nothing to install to use the service. However, you can test the service by accessing a free scan at the AppCheck website.
3. Invicti
Invicti is a cloud platform that offers DAST. The company also provides an IAST package, which includes SAST code checking, but there isn’t a separate SAST-only plan available. Instead, customers can opt to get the code for the package and run it on their servers.
Key Features:
- Dynamic Security Analysis: Specializes in DAST while offering comprehensive IAST capabilities.
- Development Integration: Easily integrates with DevOps and project management tools for streamlined processes.
- Versatile Deployment: Provides options for cloud-based or on-premises implementation.
- Intelligent Scanning: Employs AI to enhance vulnerability detection and analysis during application runtime.
Why do we recommend it?
Invicti is recommended for its use of AI in enhancing DAST and IAST capabilities, offering comprehensive insights into applications during runtime for accurate vulnerability assessment.
Effectively, the Invicti system is a vulnerability scanner specializing in checking web applications’ operations. The system can be launched manually or plugged into a workflow to integrate it into a CI/CD pipeline.
This testing system looks at operating modules and uses AI procedures to identify potential security issues, which could lie with cohesion between functions. This means that the tool needs to work while the applications are running. Other implementation options set the scanner through a standard CVE list of weaknesses.
Invicti offers a range of options, including a vulnerability scanner, a unit tester, and an integrated tester for a CI/CD pipeline. As well as scanning for known vulnerabilities, this package can use AI to spot potential security loopholes in code. This is a great support system for developers and will improve programmers’ knowledge of avoiding creating insecure code.
Who is it recommended for?
This tool is ideal for organizations looking for versatile deployment options and those who prioritize AI-augmented detection and integration with DevOps workflows for continuous security assessment.
Pros:
- Extensive Application Insight: Identifies and analyzes all associated services, modules, and frameworks.
- Operational Testing: Focuses on applications during runtime for real-world vulnerability assessment.
- AI-Augmented Detection: Leverages artificial intelligence to identify and prioritize potential security risks.
- Workflow Integration: Designed to fit within CI/CD pipelines for continuous security assessment.
- CVE Reference Checking: Cross-references standard CVE lists to ensure thorough vulnerability identification.
Cons:
- Version Clarity Needed: It’s important to choose the appropriate version for specific needs, indicating potential complexity in offerings.
There are three editions of Invicti. One is a straightforward vulnerability scanner, while the other two are suitable for DevOps teams. The on-premises version runs on Windows and Windows Server. You can assess Invicti by accessing a demo account.
4. Aikido Security

Aikido Security uses open source software that is written to provide application security scanning. The Aikido platform acts as an orchestrator for these third-party tools. It maintains a library of systems for each testing category and users can add extra tools to the list. These additional systems might be other free tools or subscription systems.
Key Features:
- Comprehensive Testing Suite: Supports SAST, DAST, and SCA for thorough security analysis.
- Pipeline Compatibility: Seamlessly integrates with CI/CD pipelines for efficient workflow management.
- Orchestration Hub: Centralizes control over various third-party scanning tools.
- Live Environment Scanning: Offers extensive scanning capabilities for operational systems and infrastructure.
Why do we recommend it?
Aikido Security is recommended for its comprehensive approach to security analysis, integrating SAST, DAST, and SCA within a unified platform for enhanced vulnerability identification and management.
Aikido Security includes a range of application security testing services, which move from pre-project component scanning for libraries, frameworks, and APIs, code testing, and then vulnerability scanning for live systems. Live application scanning extends to container and platform security checks and tests to identify secrets leakage, which can occur between modules.
Who is it recommended for?
This tool is ideal for organizations aiming to streamline their security posture within CI/CD pipelines, particularly those seeking to centralize control over various scanning tools and requiring extensive live environment scanning capabilities.
Pros:
- Unified Tool Management: Simplifies the use of multiple free and subscription-based scanning tools.
- DevOps Integration: Facilitates smooth incorporation into continuous integration and deployment processes.
- Comprehensive Reporting: Delivers detailed insights and remediation guidance for identified vulnerabilities.
- Resourceful Compliance Aid: Provides a rich library of documentation to support compliance efforts.
Cons:
- Lacks Active Defense: Focuses on vulnerability identification without offering direct threat mitigation solutions.
There are four editions to Aikido Security with more features in each more expensive higher plan. The basic plan costs nothing and you can use the Free Edition to examine how Aikido Security works. Try it free.
5. SonarCloud

SonarCloud is a leading cloud-based Static Application Security Testing (SAST) tool that empowers development teams to identify security vulnerabilities and code quality issues early in the development lifecycle. By integrating seamlessly with CI/CD pipelines, it enhances security practices while promoting clean, maintainable code.
Key Features:
- Comprehensive Static Code Analysis: Scans through programming code
- Error Identification: Detection of security vulnerabilities and bugs
- Customizable Quality Gates: Enforce standards
- Collaboration Tools: Supports team engagement
- Pull Request Analysis: Analyzes code in pull requests to catch issues early in the development process.
Why do we recommend it?
SonarCloud stands out for its robust vulnerability detection capabilities and seamless integration with existing workflows. Its real-time feedback helps teams address security issues before deployment, making it an essential tool for organizations committed to maintaining high code quality and security standards.
By utilizing advanced algorithms, SonarCloud analyzes codebases and highlights potential security risks, enabling developers to make informed decisions. Its user-friendly interface provides actionable insights, allowing teams to prioritize fixes based on severity and impact, thereby improving overall software resilience.
Who is it recommended for?
SonarCloud is ideal for software development teams, DevOps professionals, and security-focused organizations. It benefits both small startups and large enterprises seeking to enhance their security posture while fostering a culture of code quality and continuous improvement. Open source projects and individual developers can access the Free edition.
Pros:
- Easy Integration with CI/CD Processes: Automated rework routing
- Easy to Use: User-friendly and intuitive interface
- Well Supported: Regular updates and feature enhancements
Cons:
- No On-Premises Version: Requires internet access for full functionality
SonarCloud offers a 14-day free trial that allows teams to explore its features and capabilities without any commitment. This trial provides access to essential functionalities, enabling organizations to assess its impact on their security practices before deciding on a paid plan. It’s an excellent way to experience the benefits firsthand.
6. Acunetix
Acunetix offers a vulnerability scanner and an IAST tool to integrate into a CI/CD pipeline. The IAST discovers all assets and then performs dynamic scans on them. Once a vulnerability has been identified, it zooms in and applies static scans to the code to define precisely which line needs to be fixed.
Key Features:
- Advanced Vulnerability Detection: Utilizes a sophisticated scanner to identify over 7,000 vulnerabilities.
- Integrated Code Analysis: Offers dynamic and static scanning capabilities for in-depth code examination.
- Comprehensive SCA: Performs software composition analysis to assess open-source dependencies.
- CI/CD Pipeline Integration: Seamlessly fits into development workflows for continuous testing.
Why do we recommend it?
Acunetix is notable for its advanced vulnerability detection capabilities, capable of identifying a wide range of security issues, integrated seamlessly into CI/CD pipelines for continuous testing.
The Acunatex system scans for more than 7,000 vulnerabilities. It performs software composition analysis (SCA), which identifies the open-source elements in the application dependency chain and assesses each of those packages. The SCA will spot any open source code that is outdated and can be replaced by newer versions. Static analysis can scan JavaScript, PHP, and .NET frameworks code.
Who is it recommended for?
Recommended for teams seeking operational flexibility and deep insight into software dependencies, with a need for broad language support in their security management processes.
Pros:
- Operational Flexibility: Serves dual purposes as both a vulnerability scanner and a CI/CD integration tool.
- Deep Dependency Insight: Maps and analyzes software components for better security management.
- Broad Language Support: Capable of scanning JavaScript, PHP, and .NET frameworks for vulnerabilities.
Cons:
- Purpose-Specific Editions: Requires careful selection of editions based on intended use, adding complexity to the decision-making process.
Acunetix is delivered as a cloud service, but you can get the software and run it on your servers. The system will install on Windows, macOS, and Linux. But, first, access the demo system to assess Acunetix.
7. Checkmarx
Checkmarx is a platform that delivers tools for developers and managers on app creation projects and systems for ongoing application verification that IT Operations technicians can use. The Checkmarx stable includes SAST for code checking and IAST for integrated testing in a CI/CD pipeline.
Key Features:
- Automated Application Security Testing: Delivers a comprehensive suite for automated security analysis.
- Robust SCA: Identifies risks in software components, including open-source dependencies.
- Versatile Vulnerability Scanning: Offers a broad range of scanning options to identify potential security flaws.
Why do we recommend it?
Checkmarx delivers a comprehensive automated security analysis suite, offering robust static and dynamic scanning options alongside software composition analysis for in-depth security assessments.
The automated testing process will highlight security weaknesses in new code and register to rework with issue trackers, updating your project and team management workflows to reassess delivery timelines.
Who is it recommended for?
Ideal for organizations looking for comprehensive OWASP coverage and streamlined integration into project management workflows, with flexible testing options tailored to various security needs.
Pros:
- Comprehensive OWASP Coverage: Provides on-demand scanning capabilities for the OWASP Top 10 vulnerabilities.
- Streamlined Project Integration: Automates security feedback into project management workflows for efficient guidance.
- Flexible Testing Options: Includes a choice of IAST, DAST, and SAST for tailored security assessments.
Cons:
- High Cost for IAST: The integrated testing package may represent a significant investment.
The integrated development package of the IAST system from Checkmarx has a high price. Therefore, it will be more attractive to large software development organizations than small businesses and startups. The company also offers security coding training for programmers and a development framework called KICS.
8. Veracode
Veracode offers a cloud platform that includes application security testing tools for development teams and IT Operations technicians. The platform consists of a discovery module that will let the buyers of web and mobile applications discover all of the backend services that support their new software. Testing tools can be launched on-demand, on a schedule, or as part of a workflow.
Key Features:
- Static Application Security Testing (SAST): Analyzes source code to identify vulnerabilities like SQL injection, cross-site scripting (XSS), and buffer overflows.
- Dynamic Application Security Testing (DAST): Simulates attacks to uncover runtime vulnerabilities in web applications and APIs.
- Software Composition Analysis (SCA): Identifies and manages security risks within open-source and third-party software dependencies.
Why do we recommend it?
Veracode offers a comprehensive application security platform that integrates seamlessly into the software development lifecycle, providing tools like Static Application Security Testing (SAST), Dynamic Analysis, and Software Composition Analysis (SCA) to identify and remediate vulnerabilities.
Its cloud-based architecture ensures scalability and accessibility, allowing development and security teams to collaborate effectively in securing applications from code to cloud.
Veracode provides a scripting language that enables customized testing and an automated DAST service. Developers get SAST, which can be launched on-demand or integrated into respiratory storing processes. In addition, software composition analysis lets system designers and IT operations technicians check through open-source modules for outdated code.
Who is it recommended for?
Veracode is ideal for organizations seeking to embed security into their DevSecOps processes, enabling developers to detect and fix security flaws early in the development cycle.
It’s particularly beneficial for enterprises that require compliance with industry standards and need a centralized platform to manage application security across diverse development environments.
Pros:
- Interactive Application Security Testing (IAST): Monitors deployed applications for real-time attack attempts and suspicious activity.
- Penetration Testing: Engages expert security professionals to manually test applications for complex vulnerabilities.
- Compliance Management: Ensures adherence to industry security standards like PCI DSS, HIPAA, and GDPR.
Cons:
- No Free Trial: You can request a demo.
The Veracode cloud platform is straightforward to use. Both for on-demand testing and scheduled checks, the user just has to enter a URL in the screen of the testing dashboard. Veracode also offers the services of a penetration testing team. You can get a demo of the DAST system at the Veracode website.
9. HCL AppScan
AppScan is offered in four editions that provide SAST, DAST, IAST, and SCA for developers and IT operations teams. Additionally, this service has options for on-premises hosting and a SaaS package.
Key Features:
- Dynamic Application Security Testing (DAST): Automated security testing that is implemented by running the application under examination.
- On-Demand Option: Suitable for use during penetration testing.
- DevSecOps Integration: Integrates security scanning tools into development pipelines for continuous code improvement.
Why do we recommend it?
HCL AppScan provides a comprehensive suite of application security solutions, including Static (SAST), Dynamic (DAST), and Interactive (IAST) testing, as well as Software Composition Analysis (SCA), enabling organizations to identify and remediate vulnerabilities throughout the software development lifecycle.
The platform integration capabilities with various development environments and CI/CD pipelines facilitate seamless adoption into existing workflows, promoting a shift-left approach to security.
The DAST service is called AppScan Standard, and it is a software package that you host on Windows Server. This package is automated, and it can be run on a schedule by IT Operations teams or integrated into a CI/CD pipeline. AppScan Standard is available for a 30-day free trial. When used for live application testing, the service operates as a vulnerability scanner that includes searches for the OWASP Top 10. The results are reported with a severity score for resolution prioritization.
Who is it recommended for?
HCL AppScan is ideal for organizations aiming to enhance their application security posture by incorporating comprehensive testing methodologies across different stages of development.
HCL AppScan is particularly beneficial for development and security teams seeking to collaborate effectively, establish security policies, and scale testing throughout the application lifecycle.
Pros:
- Security Education and Training: Empowers developers and security teams with knowledge and best practices for building secure software.
- Threat Intelligence: Provides actionable insights into the latest security threats and vulnerabilities to proactively protect applications.
- Application Security Risk Management: Gains centralized visibility and reporting on application security risks across the organization.
Cons:
- Offers a Complicated Menu of Services: Deciding on the right plan requires planning.
AppScan Source is a service for programmers. This is a SAST service, and it includes AI interpolation to spot incremental steps that could result in security weaknesses. This service catches design faults early, thus, saving development costs. This is also an on-premises system for Windows Server. The AppScan Enterprise edition includes all of AppScan Standard and AppScan Source features. This plan is available for a 30-day free trial.
A SaaS version of AppScan Enterprise is available, and that is called AppScan On Cloud.