Access management, often referred to as Access Rights Management (ARM) or access control, plays a crucial role in securing organizational resources and safeguarding sensitive data. At its core, access management ensures that users within an organization have the right level of access to the systems, applications, and data they need to perform their jobs. Effective access management helps protect both organizational assets and individual users by controlling who can view, modify, or delete data and resources across your network.
Here is our list of the best access rights management software:
- Atera EDITOR’S CHOICE An RMM system for MSPs that monitors and manages all aspects of a network, including access rights Access a 30-day free trial.
- ManageEngine AD360 (FREE TRIAL) This bundle of ManageEngine tools focuses on Active Directory management and the use of AD for security monitoring. This package is only available for Windows Server. Get a 30-day free trial.
- ManageEngine ADAudit Plus (FREE TRIAL) An intrusion detection system that uses Active directory as a rights reference. Start a 30-day free trial.
- N-able Passportal A cloud-based password and access rights controller that can interact with on-site access rights controllers.
- Paessler PRTG Active Directory Monitor An Active Directory monitor that is part of the PRTG network management and monitoring tool. Installs on Windows Server.
- SolarWinds Access Rights Manager Manages resource access through Access Directory and installs on Windows Server.
- Apache Directory A free LDAP implementation that installs on Windows, Linux, Unix, and Mac OS.
- 389 Directory Server A free LDAP-based access rights manager that runs on Linux GNOME environments.
- FreeIPA An LDAP implementation for RHEL Linux and Mac OS. IPA stands for Identity – Policy – Audit.
- LDAP Account Manager A free LDAP access rights manager for Fedora, Debian, and Suse Linux.
- AWS Directory Service A cloud-based Active Directory manager provided by Amazon Web Services.
- JumpCloud An Active Directory and LDAP blend that is based online but can monitor both Windows and Linux systems on your premises.
Today, organizations rely on a growing mix of on-premise, cloud, and hybrid systems. This requires the management of access across multiple platforms and applications and that can quickly become overwhelming. Without proper controls in place, organizations are vulnerable to insider threats, data breaches, and compliance violations, all of which can result in significant financial, operational, and reputational damage.
This is where access management software tools come into play. These tools streamline the process of defining, enforcing, and monitoring access policies, ensuring that users are granted the appropriate level of access to perform their roles. The right access management solution also helps prevent unauthorized access, reduces the risk of data theft or accidental deletion, and simplifies compliance with regulations like GDPR, HIPAA, and PCI-DSS.
In this article, we’ll explore the best access management software tools currently available, highlighting features such as role-based access control (RBAC), multi-factor authentication (MFA), and auditing capabilities. Whether you’re looking to strengthen security or improve efficiency, the right access management solution will help safeguard your organization’s digital infrastructure while simplifying user access management.
The best access rights management tools
Our methodology for selecting access rights management tools
We reviewed the market for access rights management software and analyzed the options based on the following criteria:
- Automated interfacing to all native access rights managers to check on replication issues
- Support to implement a new ARM strategy
- Analysis of user permissions and groups
- An interface that is easier to use than the underlying access rights manager
- A system that enables full control of all access rights through one interface
- A free trial for assessing the software without having to pay
- A package that offers value for money and pays for itself through improved efficiency
The following sections give details on each of these options so your users have the correct access privileges on your network.
1. Atera (FREE TRIAL)
Atera is a remote monitoring and management (RMM) system that is specifically designed for use by MSPs (managed service providers). As a system monitoring and management platform, this package can monitor, backup, and restore access rights management systems, such as Active Directory.
Key features:
- A Cloud-Based SaaS Package: Part of a remote monitoring and management system
- Technician Team Management Tools: The key management service is the automated ticketing system
- Roles and Permissions Management: Built into the Atera system
- Patch Management: Manages and deploys patches to keep systems up-to-date and secure
- IT Automation and Scripting: Automates routine tasks and scripts to improve efficiency and reduce manual effort
Why do we recommend it?
Atera started out as a package for managed service providers and it now offers a version that is aimed at IT departments. The company offers Azure AD syncing in the top edition of both versions of the system and also provides full Azure AD integration with all editions of the IT Department version of the system. That means the IT Department version is more relevant for organizations hoping for an integrated access rights management solution. The automated monitoring services built into the Atera package look after applications, such as Active Directory, as well as servers and networks. In the case of the MSP version, those applications are operating on client sites.
The Atera system also includes a professional services automation (PSA) package. The PSA is an advanced management system that helps MSPs run the business of serving client networks. Part of the PSA’s features is a password repository. This forms an access rights management system for the automated and manual interventions that the MSP has to make in the networks, servers, and applications deployed by its clients.
The Atera package is delivered from the cloud, so the MSP does not have to install or maintain software on its own servers to use it. In fact, the MSP does even need servers to operate its business when it uses Atera.
The platform is accessed through a standard web browser and there is also a mobile app for technicians to get to the system administration console. All-access to the dashboard is password protected with user accounts. The access management part of the Atera system is integrated into the service.
The Atera RMM and PSA bundle is charged for by subscription with fees levied per technician per month. This is a great option for independent support technicians and small MSPs because it removes the need for paying for all of the necessary software that an MSP has to have. The charging structure is very scalable and it is easy to add more technician subscriptions as the business takes on new clients and expands.
Who is it recommended for?
The Atera package is interesting for businesses of all sizes because it is charged for per technician per month. Thus, small businesses get all of the functions offered to large organizations at a manageable price. Now that the company has created a version of each of its editions for IT Departments, this system is useful for all types of businesses, not just managed service providers.
Pros:
- Restrict Technician Access: Provide access to the Atera system only
- Store Credentials: Keep access credentials for clients’ systems within Atera
- Secure Remote Access: Allows technicians to remotely access and troubleshoot devices without needing to be on-site
- Entra ID Sync: For technician accounts
Cons:
- Doesn’t Provide a Password Vault: Access rights are stored in Entra ID
Atera is available for a no-obligation 30-day free trial for any MSP that is investigating new RMM and PSA options.
EDITOR'S CHOICE
Atera is our top pick for an access rights management software system because it provides a comprehensive solution for efficiently managing and securing user permissions across network devices. Its cloud-based platform allows for seamless access and integration, offering IT teams a centralized control system to monitor and manage access rights in real time. The software features automated user provisioning, role-based access controls, and audit trails that help ensure that only authorized individuals have access to sensitive data, enhancing overall security. Atera’s intuitive dashboard and centralized user management tools make it easy to assign, modify, and revoke access based on predefined roles. The platform’s scalability ensures that organizations of all sizes can effectively manage permissions, and its reporting capabilities allow administrators to quickly identify any potential security gaps. With built-in compliance monitoring, Atera helps meet industry standards and regulatory requirements, reducing the risk of unauthorized access and potential breaches. By offering an efficient and automated approach to access rights management, Atera significantly reduces the administrative burden on IT teams.
Download: Access a 30-day FREE Trial
Official Site: https://www.atera.com/signup/
OS: Cloud-based
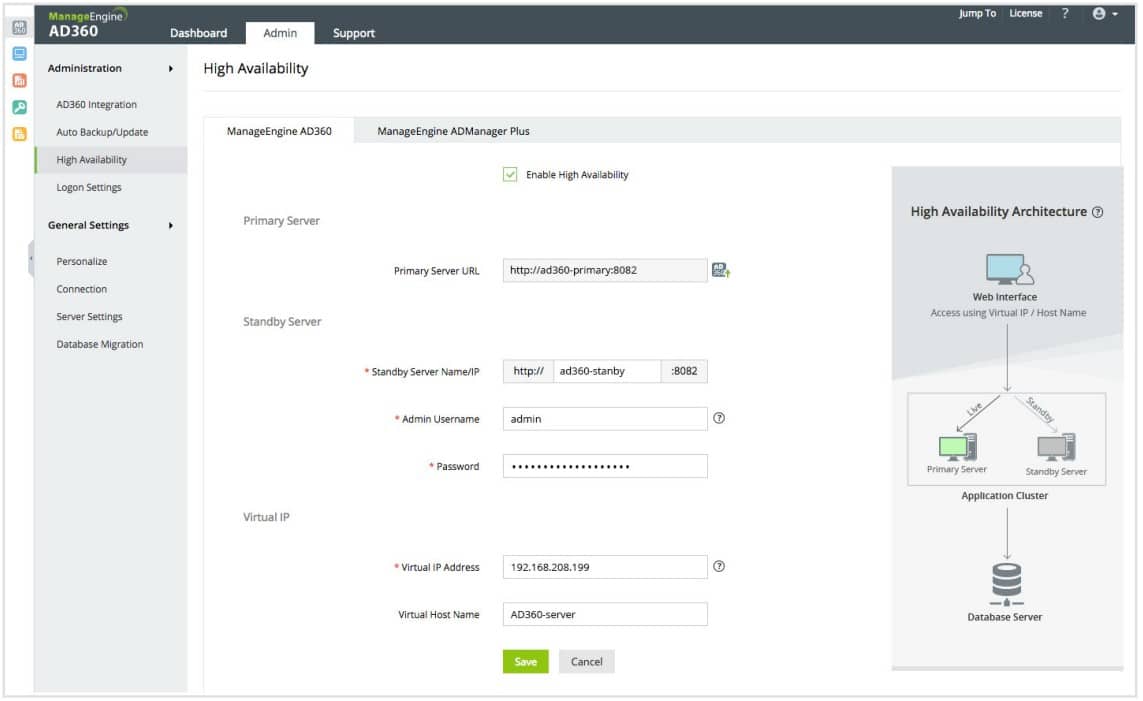
2. ManageEngine AD360 (FREE TRIAL)
ManageEngine offers a number of user authentication monitoring systems. All of them are based on Active Directory. AD360 is the first of those tools on our list. The focus on Active Directory means that this tool will only be of any use to you on the Windows Server environment, although ManageEngine usually writes all of its software so that it can also run on Linux. This is a very comprehensive AD management system that not only accesses the AD files but keeps an eye on them to protect them from hacker tampering.
Key Features:
- A Megapack: Includes seven ManageEngine modules
- Based on Active Directory: Will also manage Azure AD
- Provides a Frontend for Active Directory: Managers will use the ADManager Plus interface instead of the AD interface
- Tracks User Activity: ADAudit Plus provides user behavior analytics to spot insider threats or account takeover
- Spots Inactive Accounts: These abandoned accounts are targets for intruders
Why do we recommend it?
ManageEngine AD360 is actually a bundle of seven ManageEngine tools that relate to Active Directory. Four of these – ADManager Plus, Exchange Reporter Plus, M365 Manager Plus, and SharePoint Manager Plus – provide better management of Active Directory. The three remaining tools – RecoveryManager Plus, ADAudit Plus, and ADSelfService Plus – provide system monitoring and management services that operate on data held within Active directory instances. So, this is a very large bundle of services and you might not need all of the modules. For example, the ADAudit Plus system is concerned with compliance management, file integrity monitoring, and user behavior analysis. You might just want that tool, and if so, see the next henry in this review. The RecoveryManager Plus package is only concerned with backing up Active Directory in all its various implementations, such as for network access, Azure, and Microsoft 365 elements.
AD360 controls Active Directory coverage of file systems, network resources, Microsoft Office, and Microsoft Exchange Server email systems. It can also track access to cloud-based services through remote domain controllers. The interface of this management tool gives you access to AD records. You can add, delete, alter, and suspend access rights through AD360.
You can create a single sign-on environment through AD360 and employ the tool’s multi-factor authentication management capabilities. The control console layout can be adapted. That makes it possible to give partial views to junior staff and Help Desk staff, so they can complete delegated tasks without getting full access to your user permissions system.
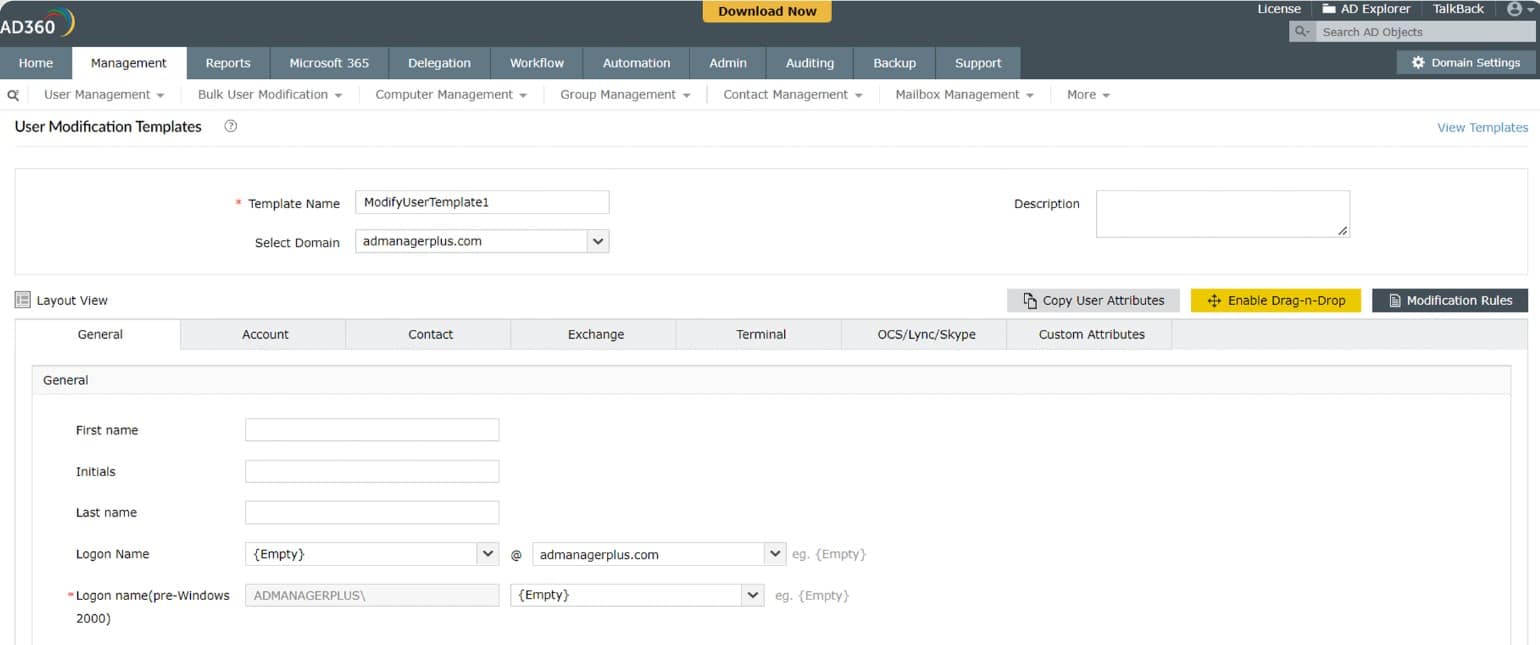
The actions needed to create a new user account are made easier by user templates. These also control the creation of user groups. New accounts can also be created in bulk by loading data from a CSV file. Account suspension and deletion can also be carried out in bulk.
Who is it recommended for?
The first characteristic of a typical buyer of ManageEngine AD360 is a business that uses all Microsoft products. While AD can be used for general system access, the full complement of tools in the AD360 package includes units that specifically relate to Microsoft systems. So, to get the best value out of this system, you need to be a mid-sized or large business that is heavily dependent on Active Directory. While ManageEngine is very good at creating free editions for many of its products, there is no free version of AD360, so this package will not be accessible to cash-strapped small businesses.
Pros:
- Creates and Enforces Security Policies: Defines and consistently enforces security measures
- Automated Onboarding: The manager creates a template and allocates one to a new account
- Standardizes Account Management: Will front for many AD domain controllers that apply to different applications
- Single Sign-On: Enables the implementation of SSO
- On-Premises Software: There is no cloud version
Cons:
- For Windows Server: Not available for Linux or macOS
AD360 is a great IAM package that includes auditing, analysis, and reporting tools. ManageEngine lets you take a 30-day free trial of the software so that you can test it out without risk.
3. ManageEngine ADAudit Plus (FREE TRIAL)
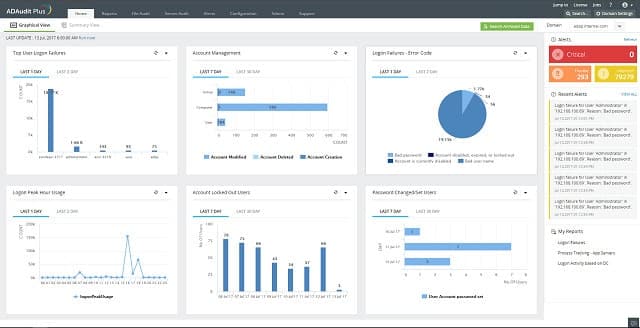
ManageEngine ADAudit Plus is a little different from the other access management tools on this list because it is concerned with monitoring activities for the purposes of security rather than enabling access to permission-editing tools for administration.
The key activities of this tool are to track user activities, such as log on and log off times, and failed login attempts. The tool monitors changes on the domain controllers and any alterations to the user permissions database of Active Directory. These changes are written to a log to be reported and they will also trigger an alert. Alerts are shown in the software’s dashboard and they can also be sent to you by email. The auditing reporter stores the previous values of the AD directories, making it easy to restore earlier settings.
Key Features:
- Focused on User Activity Tracking: Also available as part of ManageEngine Log360
- On-Premises or Cloud: Download a software package or activate a service on AWS and Azure marketplaces
- Tracks Logins: Looks for unusual login activity
Why do we recommend it?
ManageEngine AD Audit Plus is a data loss prevention and intrusion detection system that uses data from Active Directory to track system activity. As well as mining Active Directory for information, this system protects AD from unauthorized change. Naturally, the ability to create accounts or improve account permissions would be a major advantage to any intruder, so protection against such unauthorized changes is central to the purposes of ADAudit Plus. this is because Active Directory needs to be definitive and secure in order to anchor the system protection services of This ManageEngine tool. The system looks at failed login attempts that could indicate brute force password cracking, anomalous behavior, which could mean account takeover, and unexpected file access, which shows a risk for data theft.
The audit trail of ADAudit Plus offers you two activity perspectives simultaneously. These are user activities and hardware/file system utilization. These audits record the team member who implemented each data change. For standards compliance, audit data needs to be stored in archives for three years. This is a requirement of HIPAA, PCI-DSS, SOX, GLBA, and FISMA. ADAudit Plus compresses these audit files, while also indexing them for rapid access.
A reporting module includes more than 150 pre-written report formats, but it is also possible to build your own. Reports can be scheduled to run periodically and they can be mailed out automatically. Reports can be generated in CSV, XLS, HTML, and PDF formats.
Who is it recommended for?
This package is a good option for all businesses that rely on Active Directory for their access rights management services. It is particularly useful for companies that need to show compliance with data protection standards because providing account security measures is a requirement of those systems. This tool can be tailored to enforce and report on compliance with HIPAA, PCI-DSS, SOX, GLBA, and FISMA. There is a free edition that is limited to monitoring activities on 25 endpoints. That sounds like an interesting package for small businesses. However, there is a 30-day free trial of the full, paid version and the free edition is only able to generate reports on data collected during that period, it is not able to continue with system activity tracking. Therefore, small businesses need to look at the paid editions and decide whether they are suitable for their budgets.
Pros:
- Account Takeover: Identifies business accounts that are being used by outsiders
- Insider Threats: Identifies unusual user activity, alerts, and increases activity tracking
- File Integrity Monitoring: Option to restrict and track access to sensitive files
Cons:
- Free Edition Limits: Only collects activity data from 25 workstations
The ADAudit Plus tool isn’t free, but you can get it on a 30-day free trial. ManageEngine offers several free tools for working Active Directory. These include a CSV Generator, which will extract AD records, the Active Directory Query Tool, the Last Login Reporter, and the AD Replication Manager.
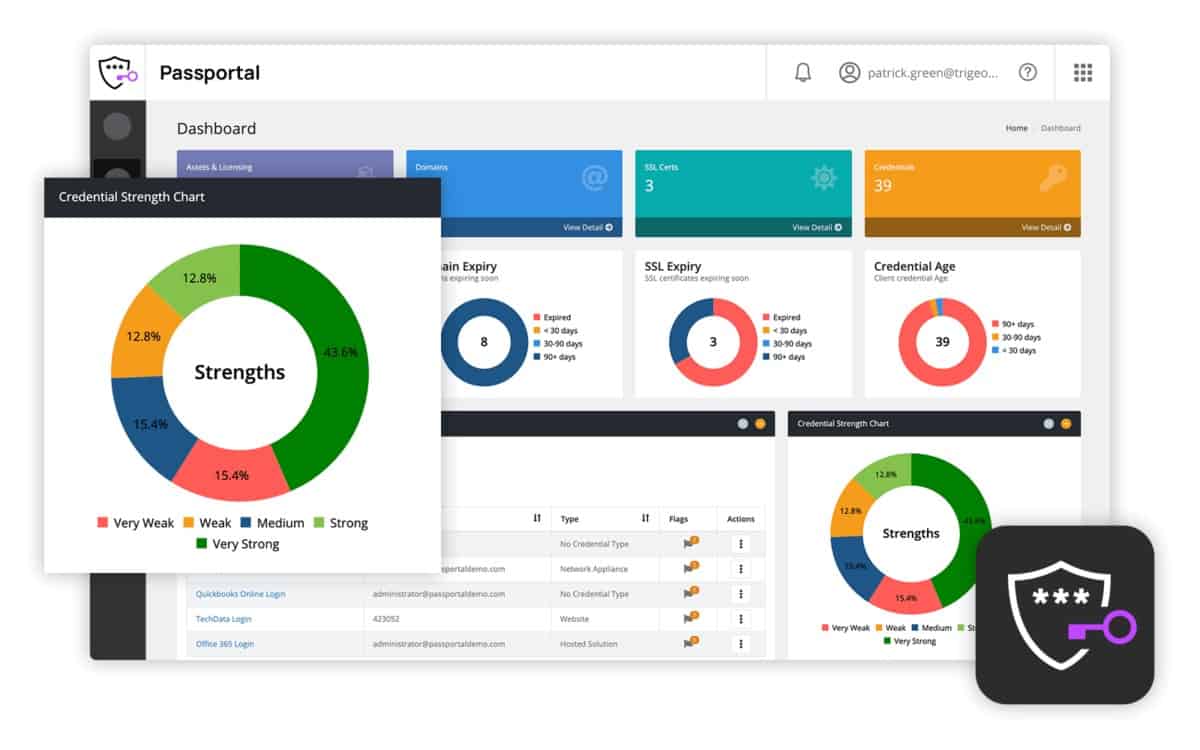
4. N-able Passportal
Passportal is a cloud-based password manager, which extends to a full access rights manager. The tool is able to control access rights for an organization over multiple sites and also include remote services, such as AWS and Azure cloud servers.
Key Features:
- Team Password Vault: Suitable for access to clients’ systems by MSP technicians
- Confidential Password Distribution: Password fields are filled in without the user seeing them
- Confidential Document Storage: Also holds system secrets, such as shared keys
Why do we recommend it?
N-able Passportal is a password vault system that updates Active Directory and other LDAP systems with the stored passwords set up for technician access to third-party systems. The N-able brand is a platform of tools for use by managed service providers (MSPs). The Passportal system is a hosted SaaS package, so you don’t need to run the software on your own server. The tool will interact with your access rights management system on your site or on the cloud. However, it must be an LDAP-based system, such as Active Directory. The system operates in such a way that the technician never gets to see the access credentials. This is a good security measure to prevent inappropriate access or the security risks that arrive when an employee leaves the company.
This service is aimed at MSPs and is multi-tenanted. Managed service providers can use this tool to manage the access rights of all resources on the systems of all of their clients. The tool can also be used in-house by IT departments.
The password manager acts as a central controller that unifies the many different access rights systems operating on for one business. Changes to passwords and access rights made in Passportal get updated automatically to the access rights controllers on site. These include Active Directory, Office 365, Azure servers, and LDAP implementations.
The Passportal system starts its service life for a client by searching for existing access rights managers and extracting out all permissions that they contain. Once this data has been drawn into Passportal, the system administrator can start setting access rights and passwords through the Passportal interface and doesn’t need to sync those to the local controllers. Passwords are stored in an online password vault, which is secured with encryption.
Passportal can be set to enforce password rotation and will also set complex passwords. It can be set so that passwords nominated by users will only be accepted if they have a pre-set level of complexity.
Who is it recommended for?
N-able Passportal is a package that is designed for use by MSPs. It provides confidential credentials distribution to the systems of their clients. The system also includes a secure storage space for important documents. This combination is interesting for MSPs of all sizes because reduces the risk of the disclosure of trade secrets, such as contract conditions and it also provides clients with a guarantee that any information held about them will be fully protected.
Pros:
- Cloud-Based System: A SaaS platform
- Multi-platform Operations: Controls passwords for on-premises systems and cloud services
- Implement Password Policies: Generates complex passwords and rotates them regularly and automatically
Cons:
- No Price List: You have to contact the sales team to get a quote
The base Passportal package includes the password manager and a document manager. This document manager also comes with secure storage. It is possible to store user help pages within this system to help the user community to understand the company’s policies around password management. N-able offers a demo system of Passportal so you can check it out before buying.
5. Paessler PRTG Active Directory Monitor
Paessler PRTG is one of the major network monitoring tools on the market. Fortunately, this very comprehensive management system is composed of modules, called sensors. You only pay for the sensors that you activate even though the software that you installed contains all of the sensors in the complete system. One of those sensors is an Active Directory monitor. The great thing about the Paessler charging structure is that you can use the software for free if you only activate up to 100 sensors.
Key Features:
- A Full Stack Observability Package: Monitors networks, endpoints, and software
- Active Directory Auditing: Gathers messages from the Windows Security Event Log
- Alerts: For AD object changes
Why do we recommend it?
Paessler PRTG Active Directory Monitoring is offered in two sensors within the PRTG package. The first of these is the Active Directory Replication Errors sensor, which tracks the activities of AD account data propagation between domain controllers. This system raises alerts if problems arise during that data transfer process. The second tool is a Windows Event Log sensor. Like all Microsoft systems, Active Directory logs actions and errors through the Windows Events mechanism. These messages can be filtered by source and so you adapt this sensor in its settings so that it specializes in channeling AD error messages.
So, even though this is a monitoring service with lots of features, you could just turn on the AD sensor and it will cost you nothing. However, if you ever decide to explore the infrastructure monitoring modules, you already have all of the software installed and you just need to turn all the other bits on.
The PRTG system only runs on Windows Server, so it focuses on monitoring Active Directory. PRTG is purely a monitoring system; it does not include management functions, so you will be able to supervise and audit your Active Directory forest, but you can’t use this tool to update your databases.
This monitor is particularly strong on the prevention or identification of database replication errors. This tool provider is the only one on this list that stresses the frequency and dangers of faults and link failures that can occur when domain controllers propagate their databases to neighbors in the forest. The PRTG monitor spots differences in access permissions databases around the network and raises alerts to help you get those problems fixed as quickly as possible.
Who is it recommended for?
Paessler PRTG is a collection of many monitoring tools and you customize the package by deciding which of the sensors to turn on. The price of the package is a fee for an allowance of sensors, so the more sensors you want, the more you pay. The minimum number of sensors that you can buy is 500. However, you can activate 100 sensors for free. That gives small businesses a free Active Directory monitoring package and then they still have enough left of their free allocation to activate network, server, or application monitoring systems. Larger businesses will need to pay for a larger number of sensors. However, this system still presents a good deal because you don’t end up paying for a fixed package that would contain monitors for systems that you don’t have. The on-premises version of PRTG runs on Windows Server and it is also available as a SaaS platform.
Pros:
- Multi-Platform: A software package for Windows Server or a SaaS platform
- Monitors Replication Errors: Draws attention to problems when copying account data from one domain to another
- Identify Logged-Out and Inactive Accounts: Dormant accounts are frequently hijacked by intruders
Cons:
- Windows only: No on-premises package for Linux
PRTG Active Directory Monitor has strong auditing procedures and would work well in partnership with an AD query and editing tool to provide you with full identity and access rights management system.
Related post: File Rights & Activity Monitoring Software
6. SolarWinds Access Rights Manager
Key Features:
- Interfaces to Access Directory: This package runs on Windows Server
- Cloud Option: Also interfaces to Azure AD
- User Access Monitoring: Fulfills a requirement of GDPR, PCI DSS, and HIPAA
Why do we recommend it?
SolarWinds Access Rights Manager is the leading package for managing Active Directory. This system provides a front end for many of the routine tasks you need in order to coordinate accounts between DCs. It offers automated utilities for those standard tasks that many system administrators often overlook, such as checking for abandoned accounts. Very few businesses can afford to have an expert working only on access rights, so hard-pressed system administrators who are covering many bases need an automated AD management system and the SolarWinds package is the best on the market.
The Access Rights Manager keeps track of activities impacting the domain controllers operating on your network. It will alert you if any changes are made to records in the databases of AD. This is a crucial monitor because accessing Active Directory to change permissions is a strategy used by hackers and malware. The auditing features extend to listing changes to mailboxes, calendars, and shared folders in Microsoft Exchange.

You will be able to change the permissions in AD records through the Access Rights Manager. The interface also allows you to add, suspend, and delete permissions. The tool also includes a self-service module that is web-based and lets users create or alter their own accounts. This is a great cost saver because it reduces the calls to the Help Desk in the case of forgotten passwords.
The tool includes an analysis module, which will report on all of the activities of listed users. This is another cybersecurity feature because it will help you spot anomalous behavior that could signal a compromised account that is being used by a hacker.
Who is it recommended for?
The Active Directory system already has its own management console that includes a lot of features, such as account searches and a backup utility. However, many system administrators feel forced to learn PowerShell in order to speed up and automate routine maintenance tasks, and that strategy can cause problems instead of providing solutions. This is why this SolarWinds system is necessary. It is a tried and tested system to improve security checks and automate maintenance and it is created by experts, so you don’t need to spend any of your own time trying out your own script-based custom solutions. Compliance management can be particularly problematic for administrators who just don’t have the time to do their regular tasks. This tool is particularly useful for businesses that need to provide compliance auditing and reporting because the SolarWinds system takes care of that responsibility automatically. The software for SolarWinds Access Rights Manager runs on Windows Server.
Pros:
- Application Access Controls: Active Directory is also used for Microsoft systems, including Exchange Server and SharePoint
- Abandoned Account Discovery: Audits account activity to identify accounts no longer in use
- Permissions Auditing: Suggests more granular user groups to limit the opportunity for lateral movement
Cons:
- Runs on Windows Server: Not available for macOS or Linux
A reporting tool in the Access Rights Manager helps you create documentation to demonstrate standards compliance and to communicate with other departments. You can get a 30-day free trial to test the system for yourself.
7. Apache Directory
Apache Directory runs on Windows, Linux, Unix, and Mac OS. This is an LDAP implementation, which is the top pick for Linux users. Apache is well-known for its web server system. Apache Directory is open-source like Apache HTTP Server, but the two projects are not linked. A big attraction of this access rights management system is that it is free to use.
Key Features:
- Free to Use: A permanently free system, not a free trial
- Active Directory Alternative: This is an LDAP-based system, as is Active Directory
- An Access Interface: The interface is a separate unit, called Apache Directory Studio
Why do we recommend it?
Apache Directory is probably the best access rights management option for Linux users. Apache is famous as part of the LAMP collection, forming the A in that acronym with Linux providing the L. Apache Directory is a modular system that you can choose to add bits onto. All of those extras a free and you are probably going to opt for them because they give you necessary features, such as encryption. The Apache Directory system requires training to fully master and unfortunately, the Apache website where you get the software doesn’t provide any. Fortunately, there are plenty of other sites, such as Linux.com that offer free guides on how to set up and use the Apache Directory system.
The software for this application creates two modules. The server part of the package is called Apache DirectoryDS. This is the main engine of the access management system and includes the permissions database. The other part of the package is a client, called Apache Directory Studio. This is the user interface for the directory and enables you to view records. The front-end also gives you the ability to add records, amend them, and delete them.
Other elements can be added to the basic Apache Directory package. These extensions are all free of charge. Apache Fortress adds attribute and role-based access control and it also facilitates delegated administration and password policy services. Apache Kerby is a Kerberos implementation that adds encryption to your directory communications. Two other options are the Apache Directory API and Mavibot, which is a multi-version concurrency control BTree system (MVCC), written in Java, which could replace the Apache DirectoryDS module.
Apache DirectoryDS uses a multi-master replication system. This means that the database can be distributed, in that different domain controllers contain different records. However, each database can be replicated to make them available in closer proximity to the user access points.
Who is it recommended for?
Apache Directory is the first choice for businesses that run Linux instead of Windows. It is very similar to Active Directory because both are based on the LDAP standard. So, anyone who has experience in running AD will be able to adapt to working with Apache Directory. The most notable feature of the Apache Directory system is that it is free to use, so it is accessible to even the smallest business. Replication features in the Apache Directory make it suitable for use by large businesses.
Pros:
- On-Premises Software: Will run on Windows, macOS, and Linux
- Free Extension: A library of extensions provides specialized security services
- A Distributed Database: The multi-master replication system
Cons:
- No User Guide: Knowledge of how to use the system is difficult to find
8. 389 Directory Server
389 Directory Server is a simple but efficient LDAP implementation for Linux. This is a free piece of software developed by the Fedora Project. This is an open-source project, so you won’t get any support from the software provider, because it is developed by volunteers on a shoestring budget.
Key Features:
- A Free System: Available for Linux
- Similar to Active Directory: This is an LDAP-based package
- High Availability: Uses an asynchronous multi-supplier replication architecture
Why do we recommend it?
389 Directory Server is an alternative to Apache Directory for Linux users. This is a free, open-source system. That means it is possible to get the source code and adapt it for your own project if you want. However, given the complexities of access rights management, it is probably more advisable to use the off-the-shelf package as it is. It’s up to you where you host this system but the option to install it on a Cloud Compute account is there. The managers of the 389 Directory Server system claim that it has excellent speed and can be easily replicated for distributed access rights management.
The software download includes a GUI interface for the GNOME environment. However, to get the best out of this service, you should pair it up with a more comprehensive identity and access management solution.
The big benefit of LDAP being a protocol, rather than a piece of software is that anyone can develop LDAP applications. As long as it complies with the protocol, it will be compatible with all other software written to those guidelines.
An example of independently-developed companion applications that can work well with 389 Directory Server is the next access rights management tool in our list.
Who is it recommended for?
Being free, 389 Directory Server is a good choice for small businesses. Its processing capacity and replication features also make it a useful option for very large businesses. The main criterion for any business choosing 389 Directory Server is that it should have a server that runs Linux and is largely Linux based across the entire network. If you prefer to operate all of your software on cloud servers, you will be able to use this system … even on Azure.
Pros:
- On-Premises or Cloud: The software can be installed on a Linux-based cloud account
- Wide Audience: Small businesses will like the fact that it is free, and large businesses will be drawn to its speed of operation
- GUI Interface: For GNOME platforms
Cons:
- Not Well Known: The pool of technicians experienced in managing this system is small
9. FreeIPA
FreeIPA is a clever combination of LDAP applications developed by others. The directory manager for FreeIPA is 389 Directory Server, which you just read about. The FreeIPA strategy of bundling together compatible free applications is a good idea. The fact that most of this tool is already being used all over the world means those components have all undergone real-world testing and so have been proven to work.
Key Features:
- Free Tool: Free forever
- Multi-Platform: Runs on RHEL (Linux) and macOS
- Similar to Active Directory: Based on LDAP
Why do we recommend it?
FreeIPA isn’t an alternative to 389 Directory Server, it is an adaptation of it. This is a free bundle of access rights management/identity and access management modules that are gathered from other providers. All of the tools are open source and free, so all the FreeIPA team has done is take away the work of slotting together the best-of-breed elements that you will need to fully enhance the basic 389 Directory Server. A good parallel for this approach is the Apache Directory system that has a core unit, which is the equivalent of 389 Directory Server, and then add-ons.
This identity and access management tool can be installed on Red Hat Enterprise Linux (RHEL) and Mac OS. The “Free” in the name speaks for itself and “IPA” stands for “Identity, Policy, and Audit.” That name tells you all of the functions of this application. The “identity” part of the name is covered by the LDAP access permissions database. This is the basic access manager.
For data security conformance, you really need to have auditing functions added to your resource access controller and that’s what Free IPA provides. It also enables you to set system-wide configurations and standardize user access rights permissions through templates. This is what the “policy” part of the FreeIPA name refers to.
The package includes a user interface that interacts with the 389 Directory Server, providing an easier way to update, add, and remove records than the native front end that is bundled in with the server program. You also get a Kerberos implementation, which will enable you to add encryption and authentication procedures to your access management communications. This extra security is very important if you want to get remote access to domain controllers on other sites, or if you employ cloud resources in your network.
Who is it recommended for?
If you have Linux servers and you don’t want to pay for your access rights management system, then the two front runners that you will probably choose for your shortlist are Apache Directory and FreeIPA. By selecting FreeIPA, you are also trialing 389 Directory Server. Systems administrators with Linux servers are very lucky to have two very proficient options to consider – and both of them are free.
Pros:
- A Compendium of Tools: This is a collection of free LDAP tools developed by other open-source projects
- Compatible with 389 Directory Services: Add directory management utilities
- Single Sign-On: Use this system to implement SSO
Cons:
- No Windows Version: Only available for Linux and macOS
10. LDAP Account Manager
LDAP Account Manager is a free access management tool with a paid alternative, called LDAP Account Manager Pro. Both versions of the software run on Fedora, Debian, and Suse Linux.
The free LDAP Account Manager includes a server, which guards the permissions database and acts as a domain controller. There is also a client program included in the package and that is an interface that enables administrators to add, delete, and alter access permissions.
Key Features:
- A Free Tool: Available for Fedora, Debian, and SUSE Linux, and Free BSD
- Two Units: The server stores permissions and the client is a user interface to it
- Available for Docker: You could run the system on Windows within a Docker container
Why do we recommend it?
LDAP Account Manager is an implementation of the Lightweight Directory Access Protocol that operates on Gnome distros of Linux. It is also available for BSD Unix and it can run on Docker as well, which offers a way to get it onto Windows or macOS. LDAP is the universal access rights management protocol that most other ARMs, including Active Directory, are based on. So, this free implementation gives you a nice alternative to just about every other ARM on the market. The GUI interface of this tool makes managing ARM on Linux a lot easier than trying to use a command line system.
The paid version of the tool has more functions in it. These include a facility to manage multi-factor authentication and a self-service system that also has a lost password reset feature.
LDAP Account Manager falls short of being an identity and access management solution because it doesn’t include audit functions. However, as this is an LDAP implementation, it will be compatible with other LDAP utilities and you could add on audit capabilities from other sources.
Who is it recommended for?
LDAP Account Manager is free to use but you get more features with the paid version, called LDAP Account Manager Pro. The free tool competes with Apache Directory and FreeIPA, however, those rivals have more features and offer more flexibility of implementation. The big advantage that LDAP Account Manager has over its rivals is that it can run on Docker, which means that you can use it on Windows.
Pros:
- A Paid Version: LDAP Pro provides more features, such as compatibility with Active Directory
- Multi Factor Authentication: Available in the Pro edition
- Securely Stores SSH Keys: Useful for pre-shared keys
Cons:
- Cannot Run Directly on Windows: It has to be implemented in Docker over Windows
11. AWS Directory Service
AWS stands for Amazon Web Services. This top-rated cloud provider offers storage space, Web hosting, and a very wide range of services, including a cloud-based Active Directory manager. Although the Directory Service is a great option for those who host their Amazon Web Services or application and file servers on AWS.
Key Features:
- Manages On-Premises Active Directory: Doesn’t interface with Azure AD
- Provides Access to AWS Services: Including third-party tools hosted on AWS
- Compliance Reporting: HIPAA and PCI DSS
Why do we recommend it?
AWS Directory Service is a cloud-based Active Directory implementation that is hosted on the Amazon Web Services platform. The package is able to manage your Windows access rights and credentials for other Microsoft systems, whether they are running on your site or on other cloud platforms. A big advantage that this service has over running your own Windows-based Active Directory is that it is a managed service, so issues such as backup are taken care of for you.
AWS’s Active Directory implementation is compliant with HIPAA and PCI DSS requirements because it includes auditing functions to help ensure data integrity. System snapshots are taken daily, but you can also get them on-demand at critical points, such as just before an application update.
This AD enables group policy implementation and can also manage a single sign-on strategy. You can merge different server subscriptions into a single forest, or choose to keep some domain controllers separate.
Although the online platform can be accessed through a browser, making its interface operating system-neutral, the access management service only interacts with Active Directory, so it can only be of use to those operating a Windows environment onsite.
The charging methodology is very scalable because fees are levied as a metered service. The great thing about that is that you don’t have to pick through different subscription plans and worry that you might be locked into a service volume that your business might outgrow. Another great aspect of the charging structure is that you pay at the end of the month once the throughput of the month has been calculated, so you don’t have to pay large amounts of money upfront as you would with a yearly subscription plan.
Who is it recommended for?
This is a good solution for multi-site businesses because of its cloud location. Your administration work can be carried out through any Web browser, so you could work on it from home. At the other end of the scale, the AWS Directory Service is also a good choice for small businesses because you don’t need to have an expert on staff to manage the software for you. Businesses that operate a virtual office will particularly benefit from this package.
Pros:
- AD Backup: Creates a cloud backup service for Active Directory
- Automates Replication: The service requires a minimum of two domains
- Free for Small Businesses: AWS Directory Service is part of the AWS Free Tier
Cons:
- Doesn’t Operate with Azure AD: Only coordinates access for AWS-based system with an on-premises AD domain
The minimum service level caters to two domains and additional domains are charged at a lower hourly rate. Amazon offers the AWS Directory Service on a 30-day free trial.
12. JumpCloud
JumpCloud is a very interesting service that probably points the way to the future of access management systems. This is an online service, just like the AWS Directory Service. However, unlike the AWS service, JumpCloud can manage your onsite resources and the services of any cloud provider that you integrated into your network.
Key Features:
- Cloud-Based System: Hosted and managed
- Five Plan Levels: Ranges from device management without ARM to a full private cloud service
- Vulnerability Scanning: Recommends device configuration hardening
Why do we recommend it?
JumpCloud is a cloud-based access rights manager that breaks the tribal Windows vs Linux division of the IT industry. This system can manage access to resources anywhere, no matter what operating system each runs on. It will also manage access to cloud services. JumpCloud has a grid-like menu of services that creates a complicated calculation for the fees required for the system’s various packages. However, you can select a Single Sign-On option, and there are also opportunities to manage connection security systems, such as VPNs.The JumpCloud system comes with out-of-the-box integrations that just need activating to get the service managing access to your subscription and equipment, such as Google Workspace, Salesforce, and CrowdStrike systems, or Juniper network devices.
The concept of this service is that it is just as though you are running Active Directory on your own server, except that all of the processing is actually done on JumpCloud’s server remotely. This is a useful advancement on the traditional AD concept because it means your audit files are automatically written to a remote location, keeping them safe from potential onsite environmental disasters. Your audit data’s safety is the responsibility of JumpCloud.
The JumpCloud service model recognizes that a large part of network activity now happens across the internet. Consider the number of employees that now work off-site, agents, delivery staff, client site consultants, artisans, and operatives and add on the growth in telecommuting. You can see how much of your network traffic actually takes place offsite and how often authentication and access rights are really negotiated over the internet. So, moving the Active Directory server to the cloud makes no difference at all to processing efficiency.
Another unusual feature of the JumpCloud service is that it has managed to emulate Active Directory so that it can operate on Linux. This is really a dressed-up LDAP service, but it’s very convincing and helps you use both Windows and Linux servers in a mixed environment, administered with one skillset.
The JumpCloud system is well worth the time to investigate and you can use the system for free permanently to serve up to 10 users. This is great news for startups, and large organizations can use this free service to investigate the system and expand to full coverage once the trial works out well.
Who is it recommended for?
The JumpCloud subscription is levied at a rate per user, which makes it very scalable. It is suitable for small businesses and large organizations alike. The “a la carte” pricing is a little complicated and so you have to make calculations of how much all of the features that you want to use are going to cost before fully committing to an account with JumpCloud.
Pros:
- Cross-Platform: Manage access to resources on Windows and Linux, plus cloud services
- User Activity Logging: For insider threat and account takeover detection
- Passwordless Authentication: Only available in the highest plan
Cons:
- Priced Per User: Large organizations can end up with a very large invoice
Implementing access rights management
The options on our list should give you plenty to explore. This guide can only give you a taste of each of these great tools, but hopefully, with just the brief descriptions, you can start to narrow down your options, making provisioning decisions a lot easier. All of the tools on this list are either free or offer a free trial, so you won’t waste any money trying out a few of them.
Do you already have an access management system? Which tool did you go for? Have you tried any of the tools on this list? Leave a message in the Comments section below and share your experience with the community.
Access Rights Management FAQs
What is the difference between identity management and access management?
Identity management relates to the creation, maintenance, suspension, and deletion of user accounts on a system. User accounts can be grouped into levels of authority. Access management allows user accounts to access different resources. Access management also determines what level of access a user has to each resource. Permission levels can be allocated to groups of users.
What is the difference between IdM and IAM?
IdM stands for Identity Management; IAM means Identity and Access Management. IdM deals with the management of user accounts in an organization. IAM links together a pool of user accounts with a pool of guarded resources. IdM authenticates a user’s identity while Access Management lists the users that are allowed to access a resource. IAM groups together Identity Management and Access Management.
Is identity and access management part of cybersecurity?
Yes. Identity and Access Management (IAM) is part of cybersecurity practices. The existence of access controls makes it harder for outsiders to gain access to resources. It also segments the user community so that one valid user account can’t get access to every resource and only has rights to perform certain actions on the resources to which they have access. This limits the amount of damage that an insider threat can do. An important part of Identity Management is the control of passwords through rotation and complexity enforcement to prevent outsiders from guessing their way in. Abandoned accounts also need to be identified and deleted because they are often the most vulnerable user accounts to hacker takeover.