What Is AWS WAF?
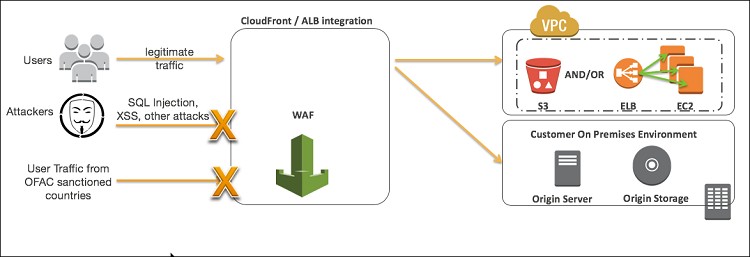
AWS WAF (Web Application Firewall) is a security service provided by Amazon Web Services (AWS) that helps protect web applications from various common threats and vulnerabilities. It acts as a protective layer between an application and the internet, enabling users to control and filter incoming traffic based on customizable rules. AWS WAF is specifically designed to block malicious traffic, mitigate attacks, and ensure that web applications remain secure, efficient, and high-performing.
AWS WAF is particularly useful for defending against common web attacks, including SQL injection, cross-site scripting (XSS), and Distributed Denial of Service (DDoS) attacks. By offering protection against such vulnerabilities, AWS WAF helps prevent data breaches, downtime, and other issues that could compromise an organization’s web applications and services.
How Does AWS WAF Work?
The service works by allowing users to define security rules that filter HTTP/S requests to their web applications. These rules can be configured to block or allow traffic based on specific conditions, such as IP addresses, request patterns, geographical location, or particular HTTP headers. AWS WAF supports both predefined managed rules and custom rules, giving users flexibility in creating security policies tailored to their unique requirements.
AWS WAF is fully integrated with other AWS services, such as Amazon CloudFront (content delivery network), Amazon API Gateway, and AWS Application Load Balancer. This integration ensures that WAF policies can be applied to incoming web traffic seamlessly across various AWS infrastructures. With its scalability and flexibility, AWS WAF is a valuable tool for organizations seeking to enhance the security of their web applications and safeguard their online presence.
Setting Up AWS WAF
One of the main reasons AWS WAF has rapidly increased in popularity is due to its easy implementation. The only prerequisite to get started is that you have an AWS account, which makes setup significantly easier than other cloud-based application firewalls.
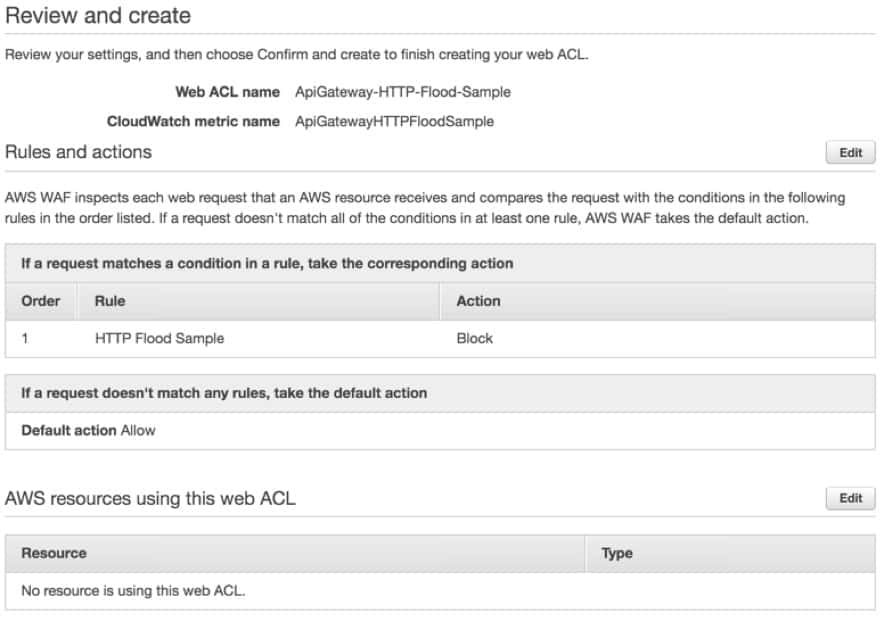
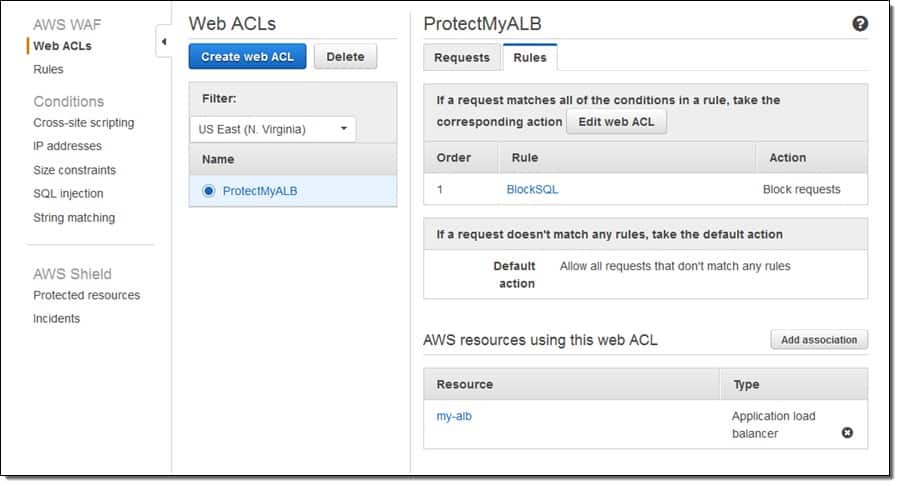
Once signed in, you’ll run through a wizard that guides you through creating and configuring your ACL (Access Control List). The ACL is the first line of defense against unauthorized access and attacks against your web services. This is where you’ll be able to allow or block web requests, set rules based on IP addresses, and configure specific policies that dictate whether or not traffic is allowed to reach your web applications.
When configuring your rules you’ll have the ability to have them applied to a group or remain independent by themselves. Creating rules groups helps you cut down on the clutter and originate your security policies more effectively. Rules detect requests by matching data found in the string to a ruleset you configure.
While setting up string rules can be a bit complicated, AWS WAF does provide a visual editor that guides you through the rule creation process. Depending on your rule sets there may be a time when you can only use the Rule JSON Editor. The JSON editor isn’t as intuitive as the visual editor, but it does give you more freedom to create more customized and in-depth rulesets. The JSON editor can also be used to copy configurations across multiple web ACLs if needed.
If you don’t have your custom rules configured just yet, you can utilize Amazon’s Managed Rules group to get a jumpstart on getting your WAF up and running. AWS Managed Rules are preconfigured rules that follow industry best practices and are written by the AWS security team. Managed rules are automatically updated and closely follow IP reputation lists and OWASP standards.
If you’re looking for more out-of-box options AWS Marketplace has a number of managed rules for purchase. Companies such as Cyber Security Cloud, F5, and Fortinet offer their own versions of managed rules that help block everything from botnet driven attacks to cross-site scripting attacks.
This combination of flexible configuration and prepackaged rulesets makes AWS WAF simpler to set up than most alternatives.
Features & Integrations
In addition to the ACL, there are a number of additional features and integrations that give AWS WAF extended capability and protection.
Through a full-featured API, the firewall can be completely controlled and configured through a set of requests. As most firewalls have API access, few are as extensive as Amazon’s WFA. Rather than wasting time logging into a GUI, developers can quickly make changes and configurations as they build their application.
While this approach would require a deeper knowledge of the platform, a dev team could build a security ruleset as a part of the deployment process. In theory, this could cut down on complicated handoffs between teams, and shorten the development cycle. Developers could also apply scripting automation through this API to build out custom security rules, groups, and policies based on whatever their template or internal policy requires.
Automation can also be applied to deploy AWS WAF instances automatically with the use of AWS CloudFormation. Here you can create a master template that dictates what security settings, rulesets, and configurations the firewall needs. This feature makes spinning up new environments quick and ensures you have consistency across all of your products.
AWS WFA heavily relies on an Amazon CloudWatch integration to provide additional insights and real-time visibility. CloudWatch gives you extended visibility into your WAF security events and acts as a SIEM extension for your firewall.
One of the most useful integrations for your WAF is the alerting feature, which you can fully customize through thresholds and alert templates. CloudWatch can help keep your security team alerted to configuration changes and events, as well as provide AI-powered services like anomaly detection.
Challenges With AWS WAF
While AWS WAF proves to be a versatile cloud-based security solution, it doesn’t come without some challenges.
You’ll need dedicated security personnel. AWS WAF can be complicated when building custom rulesets and policies. A misconfiguration on your WAF could spell disaster and allow access to more vulnerable areas of your applications. There are many instances of data breaches occurring due to misconfigured AWS settings, one notable incident occurred when Capital One failed to secure its WAF.
An attacker used a common attack called a Side Server Request Forgery to trick AWS WAF into sending information to the attacker. This resulted in the theft of over 100 million credit card application records and was a direct result of a misconfigured WAF.
Without a highly trained IT security professional in place, an organization can fall victim to a hacker taking advantage of weaknesses in poor configurations. Alternatively, your IT staff can mitigate risk by utilizing a product such as Access Advisor, which helps scope AWS roles and identify permission issues.
AWS WAF lacks some built-in features. You’ll find that using Amazon’s WAF requires a number of integrations or add-ons for features that you might expect to be built in. For instance, AWS WAF can collect data on traffic, but to pull any meaningful information through the WAF can be cumbersome and time-consuming.
If you want to manage logging for your web ACL, you’ll need to enable and configure Kinesis Data Firehose, which has its own separate learning curve and limitations. When a WAF has too many add-ons and features, it can become difficult to not only manage them all but to also gain a deep understanding of all of the systems in place.
It’s this same lack of understanding and confusion that can cause misconfigurations, and ultimately data breaches. Once again, having a security professional in place can mitigate this risk, but having a WAF that incorporates a built-in solution would eliminate it.
Rulesets will need to be managed, updated, and audited. WAF firewall rules may seem static, but as the threat landscape changes, your firewall rules will need to follow suit. Managed Rules are a streamlined alternative to creating your own, however, this does come with two drawbacks. Managed Rules will cost your company money and need to be purchased on the AWS Marketplace. While this is still considerably less expensive than hiring a consultant, it’s still an additional cost.
Managed Rules also do not allow for rule modification. This means your ability to alter or customize a ruleset deployed on AWS Marketplace is limited. This puts you in a box when it comes to security and flexibility. If you choose to build your own rulesets they will periodically need updating to reflect new and evolving threats. Permissions to your AWS environment should also be audited regularly, depending on the size of your organization.
Pricing
Pricing for AWS WAF is linked to the number of Access Control Lists you use, the volume of requests you process, and the number of rules you have added to each ACL. This pricing model can be a bit complicated, but with proper planning, you can estimate your costs based on current usage and future needs.
Monthly pricing currently starts at $0.60 per million requests, $1.00 per rule, and $5.00 per access control list. There is also a small fee for creating additional rule groups. Planning exactly how many rules and groups you’ll need can be difficult, especially if you’re new to the AWS platform. To help new users, Amazon has created a pricing calculator to help you get a better idea of what your monthly costs would be.
Why choose AWS WAF?
AWS WAF is a flexible firewall solution that leverages the power of Amazon’s cloud to give businesses affordable and scalable protection. While their pricing can be a bit complicated, it helps lower the bar to entry for smaller businesses and cash strapped startups. AWS WAF is a great option; just make sure you have someone who is knowledgeable in AWS to configure and administer your WAF.
AWS WAF Alternatives
If you’re looking to move away from the AWS platform, check out our shortlist of competitive AWS WAF alternatives. Be sure to check out our updated post on the best WAFs.
- AppTrana Managed Web Application Firewall This WAF solution comes with its own fully managed security team and features customized security policies, contractual SLAs, and 24×7 support.
- Cloudflare WAF Leverages its large cloud-based infrastructure to build powerful rulesets and policies with relative ease through intuitive dashboards and wizards.
- Barracuda Web Application Firewall Barracuda has three WAF offerings that provide adequate protection from threats and a host of automated remediation. Solutions include on-premises, cloud-based, and as a managed service.
- F5 Advanced Web Application Firewall Utilizes proactive botnet defenses, behavioral analytics, and application-layer encryption to defend your services against threats, and secure communications between your ancillary systems.
AWS WAF FAQs
Is AWS WAF included in AWS Shield?
AWS Shield Standard does not include the AWS WAF service. AWS WAF is included with AWS Shield Advanced.
What conditions are AWS WAF web application firewall rules based on?
AWS WAF application firewall rules can be based on:
- IP addresses
- HTTP headers
- HTTP message body
- Custom URIs
What are three chargeable elements of AWS WAF?
The price you pay for AWS WAF is calculated according to three chargeable elements:
- The number of incoming requests that WAF has to process
- The number of Web ACLs that you have
- The number of Rules within each of the Web ACLs