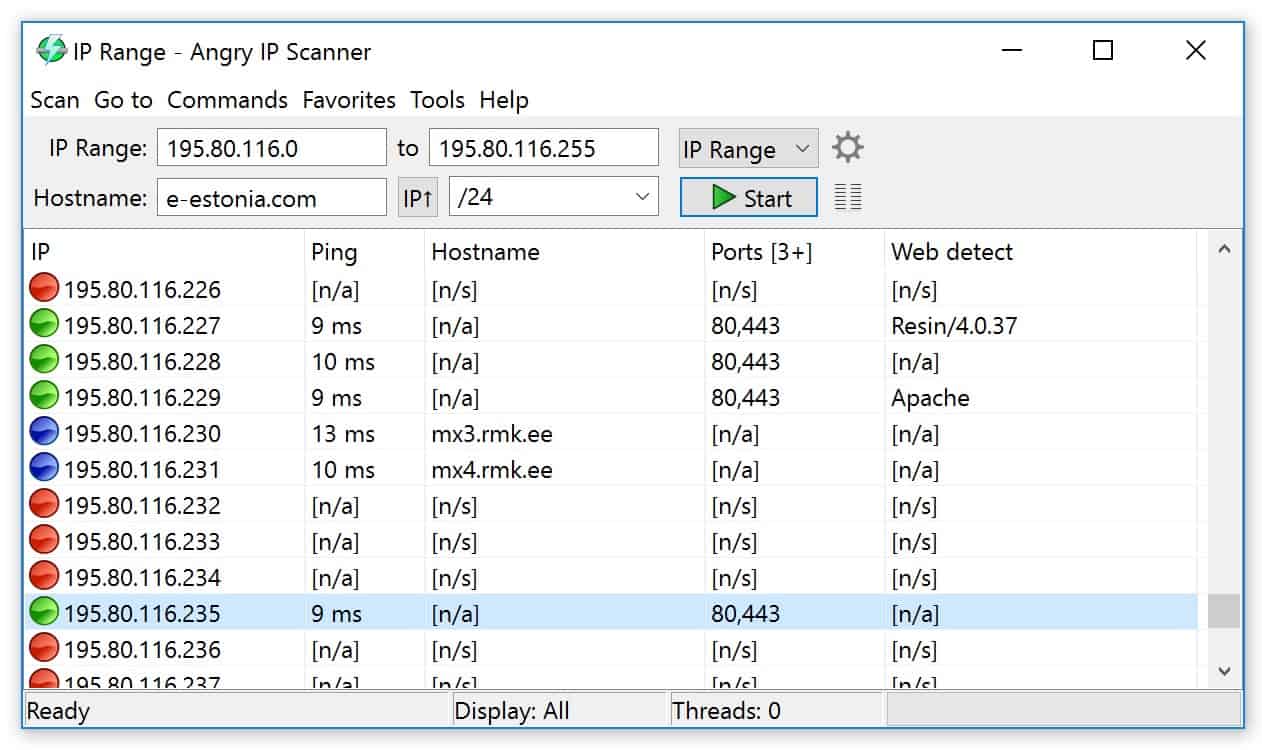
Angry IP Scanner Review
Angry IP Scanner is a fast and lightweight tool that provides all the features you would need from an advanced network scanner. If a device has ever lost it’s IP address on your network, you’ll know the frustration of trying to find that device remotely. Angry IP makes scanning your LAN simple. Set the range of IP addresses you’d like to scan and press start. In seconds your list will be filled with your network devices along with each device’s ping time, open ports, MAC address, and hostname.
One of our personal favorite features of Angry IP is the ability to save favorite IP ranges and hostnames all without having to sign in to an online account. Your favorite information is stored locally and can easily be saved to your network or cloud drive.
If you’re looking to scan your web server or any external IP address you can do so from the exact same interface. Once you’ve found what you’re looking for you can export your results to CSV, TXT, or XML format.
Unlike some tools on the market, Angry IP’s open-source code allows anyone to analyze the code and build their own plugins to extend the functionality of the network scanner.
Above everything else, Angry IP is fast and easy to use, which is exactly why it currently has over 29 million downloads. Combine that with its cross-platform flexibility and it’s clear why Angry IP Scanner is the most popular tool in its space.
Key Features:
- Multi-threaded network scanning for fastest results possible
- Flexible exporting options. CSV, TXT, or XML format
- Ability to save favorite IP ranges and devices
- No account or login needed
- Open source tool and free
Here is our list of the best Angry IP Scanner Alternatives:
- Nmap EDITOR’S CHOICE This free command line port scanner has many different discovery features that can reveal important information about a network and is probably the most widely used tool for hackers and penetration testers. Runs on Windows, Mac OS, and Linux.
- Lansweeper A network monitoring tool that includes IP address management functions.
- Netcat IP address and port scanning as part of a free tool for Windows, Mac OS, and Linux.
- ZMap An adaptation of Nmap for Linux and Mac OS.
- Wireshark An iconic packet sniffer that can be used to identify addressing issues.
- Invicti A full system security tool for Web assets that will perform vulnerability scanning and can also be used for automated testing in CI/CD pipelines.
- Acunetix Combines both network device scanning and web application scanning in a GUI interface designed for Windows and Linux.
- GFI LanGuard A network equipment security monitor that includes an autodiscovery feature.
- SoftPerfect Network Scanner A close competitor to Angry IP Scanner with some nice extras
The best Angry IP Scanner Alternatives
Our methodology for selecting IP scanner tools
We reviewed the market for software like Angry IP Scanner and analyzed the options based on the following criteria:
- A scanner that matches or beats the functionality of Angry IP Scanner
- Options that run on Windows, macOS, and Linux
- The ability to specify an IP address range or a non-sequential list fed in from a file
- Port scanning capabilities
- Nice to have a graphical interface with data visualizations
- A free trial or money-back guarantee for a cost-free assessment
- Value for money in paid tools and a worthwhile service from free tools
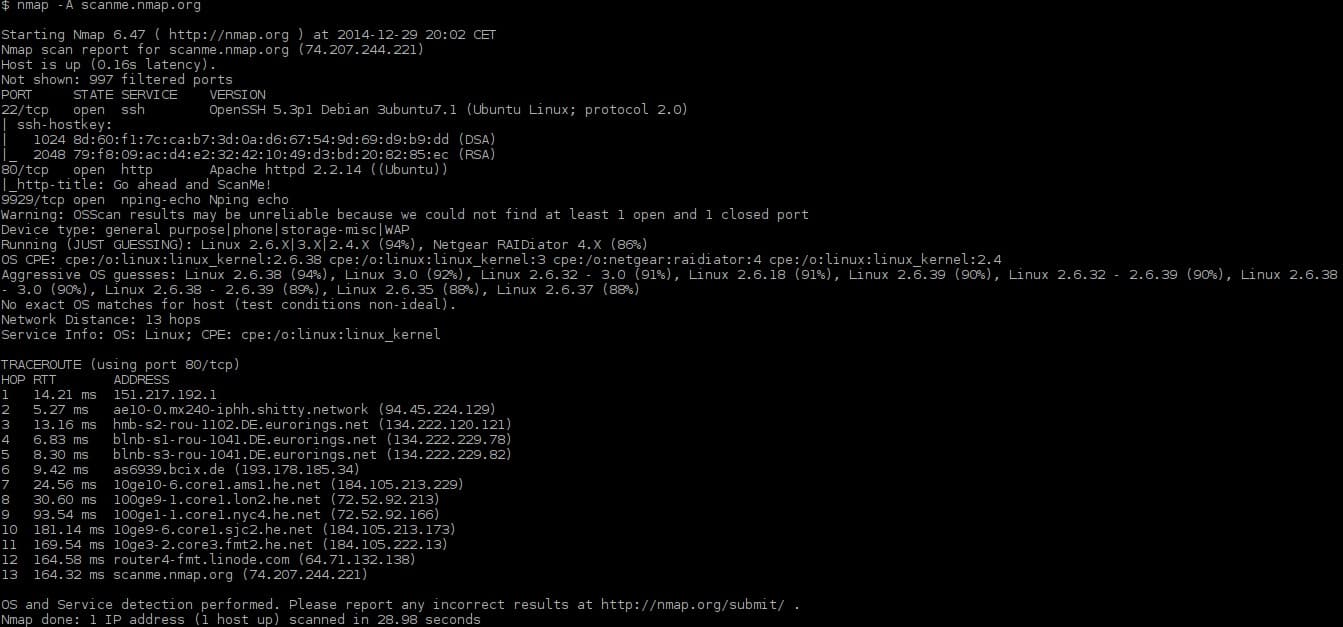
1. Nmap
If you’re a network administrator looking for more depth and raw power from a port scanner, look no further than Nmap. What Nmap lacks in frills and functional GUI it makes up for with sheer command-line based power. If you’re not a fan of strictly just a command-line interface, you can always use Zenmap, which is the exact same software just with a graphical interface. Both Nmap and Zenmap are free to use and available for Windows, Mac, and Linux.
Key Features:
- Port Scanner: Powerful port scanning tool that can identify open ports and services running on network devices.
- Network Device Identification: Identifies all devices connected to a network, providing information about their IP addresses, operating systems, and other details.
- Device Information: Provides detailed information about network devices, including their response to various probes and scans.
- Security Tool Capabilities: Doubles as a security tool, allowing administrators to discover open ports and applications communicating over suspicious ports.
- Device Fingerprinting: Gather a range of identifying factors about each device.
Why do we recommend it?
Nmap is free and it is often used by hackers and so it is also used by penetration testers. This is a command line tool, which is difficult for infrequent users to handle but regular users of the system who can master the long list of options get a lot of network information from it.
Nmap takes network monitoring & discovery a step further and provides the tools and features that allow for in-depth security audits and vulnerability scans ports on your network and devices. Nmap has all of the standard scanning capabilities that Angry IP has such as DNS resolution, ping checks, and port status reporting, but can go much deeper when it comes to querying ports.
While most run-of-the-mill port scanners only allow for standard scanning, Nmap can perform much more detailed types of scans. For instance, Nmap allows for SYN stealth scans which lets you quickly scan thousands of ports without being flagged by a device’s firewall. Named a “stealth scan” due to it never actually completing a TCP connection to the device. This can be especially useful when testing the security of your own network to see how your devices respond to specifically crafted packets.
Another example of higher-level network scanning is source port manipulation. Sometimes misconfigured devices will accept network traffic only if it’s coming from a specific port. With Nmap, you can craft packets to look like they’ve come from a specific port, and test if your devices are vulnerable to this type of network attack.
Who is it recommended for?
This isn’t a tool that a network manager would use for day-to-day administration or standard network testing. Instead, it is an investigative tool for system testing and also for attack planning. The free Zenmap tool provides a GUI frontend for Nmap, which makes this system easier to use.
Pros:
- Large Open-Source Community: Widely used and supported by a massive open-source community, making it a popular and trusted networking tool with ongoing development and updates.
- GUI Version (Zenmap): Offers a GUI version called Zenmap, which lowers the barrier to entry for new users who may find command-line interfaces intimidating.
- Straightforward Syntax: The syntax of NMap commands is straightforward and not difficult to learn for most users, making it accessible for network administrators and security professionals.
- Extensive Command Set: A powerful facility for exploring and documenting networks.
- Multiple Platforms: Runs on Windows, macOS, Linux, and Unix.
Cons:
- Overkill for Simple Troubleshooting: Extensive capabilities could be overkill for simpler troubleshooting tasks that do not require advanced port scanning or network device identification.
- Security/Auditing Focus: While NMap is versatile, it is better suited as a security and auditing tool rather than a general-purpose network troubleshooting tool.
Nmap allows you to dive incredibly deep into your network devices and is one of the most detailed port scanning programs available. It’s definitely not as user friendly as Angry IP but goes miles beyond what your average port scanner could accomplish. Best of all you can download it for free.
EDITOR'S CHOICE
Nmap is our top pick for an Angry IP Scanner alternative because it offers a much deeper level of functionality, making it ideal for network administrators, security professionals, and advanced users. Nmap (Network Mapper) is not just an IP scanner; it’s a comprehensive tool for network discovery, security auditing, and vulnerability assessment. Unlike Angry IP Scanner, which primarily focuses on ping sweeps and port scanning, Nmap allows users to perform sophisticated scans, including OS detection, version detection, service identification, and scriptable interactions. Its built-in scripting engine (NSE) enables the execution of custom scripts for tasks like detecting specific vulnerabilities or conducting in-depth network analysis. Another advantage of Nmap is its extensive documentation and active community, which provide expert support and continuous improvements. Nmap can scan large networks quickly and accurately, offering advanced techniques like stealth scanning and evading detection, which are vital for penetration testing or security assessments. Nmap’s flexibility extends beyond simple command-line use; it also has a graphical user interface through the Zenmap front end, making it accessible for both command-line experts and those preferring a more visual approach.
OS: Windows, Linux, macOS, and Unix
2. Lansweeper
Lansweeper operates more as a permanent network monitoring tool rather than a piece of software you use once in a while during troubleshooting. It gives network administrators and MSPs powerful port scanning capabilities combined with features such as network inventory management, uptime reports, and Active Directory integrations.
Key Features:
- Agentless Device Management and Metrics: Manages and gathers metrics from devices without requiring an installed agent, simplifying setup and maintenance.
- Registry Scanning Capabilities: Can scan and gather detailed information from device registries, enhancing inventory accuracy.
- Inventory Management: Comprehensive inventory management features allow tracking of hardware, software, and user data across the network.
- Active Directory Integration: Integrates with Active Directory to streamline user and device management, leveraging existing directory structures.
- Reporting and Alerts: Lansweeper generates reports on various aspects of your network inventory, including hardware details, software usage, and potential security vulnerabilities.
Why do we recommend it?
Lansweeper is a paid tool that is a lot more complex than Angry IP Scanner. A network sweep with this tool returns more than just address details and response time. You can use this system to populate an asset inventory and perform vulnerability scanning. You also get live asset usage data.
One of my favorite features of Lansweeper is the ability to perform registry scans. Once enabled, you can scan all of the devices in your network and populate a list based on which machines have specific registry keys or values present. This feature allows you to find everything from program installations to traces of malware.
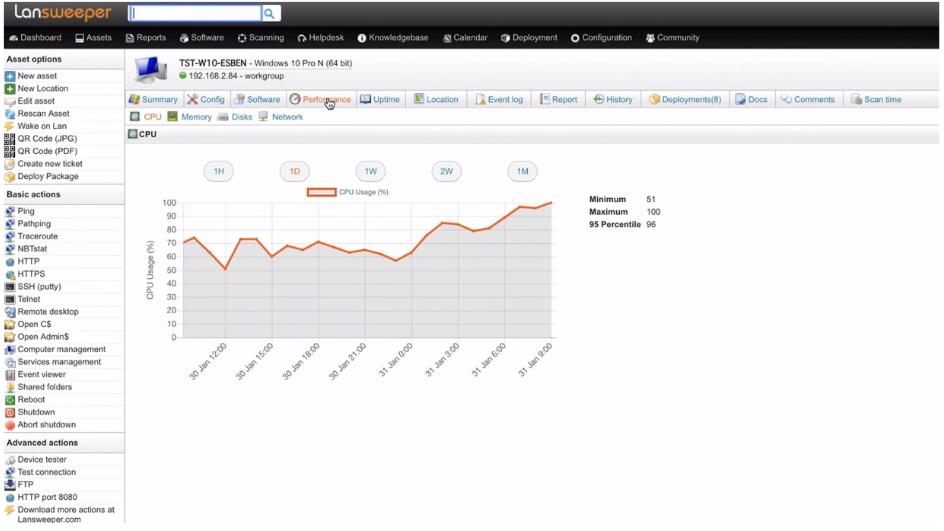
Lansweeper stands out from the crowd by providing agentless reporting of a PC’s usage metrics in a level of detail that you would expect from a full-fledged network agent. Under the Asset page, you can view the CPU, memory, disc usage, and network statistics of a device.
Performance Counter Monitor also allows you to measure each device’s overall performance to help identify bottlenecks your users might encounter. You can also analyze the resource consumption across your entire network as a whole, which helps estimate how much hardware a cloud or remote desktop server would need for your users.
Who is it recommended for?
Lansweeper will run continuously and so it is more useful as a network device monitor than as a node availability tester. The system offers a free edition to monitor up to 100 devices, which is suitable for small businesses. Paid editions are suitable for mid-sized and large organizations.
Pros:
- Automatic Device Discovery: Automatically discovers devices through customizable search filters, making it ideal for BYOD (Bring Your Own Device) networks where new devices frequently connect.
- Agentless Scanning: The agentless approach minimizes setup time and avoids potential software conflicts on devices.
- Easy to Use: Lansweeper boasts a user-friendly interface that simplifies network discovery and asset management.
- Cost-Effective: The core features of Lansweeper are available in a free version, making it a budget-friendly option for smaller networks.
Cons:
- Limited Free Version: The free version is limited to managing up to 100 assets, which may not be sufficient for larger networks or growing businesses.
- Security Concerns: Since Lansweeper is agentless, it might not be suitable for networks with very strict security requirements.
Lansweeper clearly stands out from other network device scanners as it extends its capabilities into inventory management and machine maintenance. If you’re looking for a hybrid network scanner and inventory manager, Lansweeper is a great tool to use and is compatible in any Windows environment.
You can use Landsweeper completely free, tracking up to 100 assets. The Enterprise version of the software starts at $1.00 (£0.81) an asset. Start with their 30-day free trial.
3. Netcat
Netcat is a free and flexible open-source tool that was first built to read and write UDP and TCP network connections across any port. Over the years the tool transformed and took on new powerful features like port scanning, packet sniffing, and port redirector. Netcat is much like Nmap, as it does not have a graphical interface and can be difficult to learn.
Key Features:
- Basic Port Scanning: Allows you to scan specific ports on target devices to identify open ports and potentially running services
- Network Scanning: Capable of scanning networks and monitoring ports to gather information about networked devices and services.
- Packet Crafting and Raw Network Data Monitoring: Allows users to craft and send packets, as well as monitor and analyze raw network data for security and research purposes.
- Security Research Tool: Often used by security professionals for testing and probing network vulnerabilities, creating backdoors, and analyzing network behavior.
- Server Capabilities: Can act as a server for multiple protocols, enabling communication and data transfer between hosts.
Why do we recommend it?
Netcat is a free tool that joins Nmap as an essential part of a penetration tester’s toolkit. You wouldn’t use Netcat for continuous scanning but for research. This tool is used for Transport Layer scanning and traffic injection. So, it provides port scanning like Angry IP Scanner but also allows traffic modification.
Some would say that Netcat is more of a security tool than a port scanner, and they would be half right. At the heart of most security tools is a powerful network scanner, and a network scanner can be used as a security tool.
Netcat lacks a lot of the documentation you can easily find with software like AngryIP or Nmap which in my opinion is its biggest drawback. If you’re thinking about trying out Netcat, check out our Netcat Cheat Sheet to quickly pull up powerful and useful commands. Netcat is compatible with Windows, Linux, and macOS systems.
Although there is a ton of security testing and network scanning you can do with Netcat, it’s probably not going to be a practical tool for your average day-to-day use. More basic tools such as Lansweeper or even Zenmap would have less of a learning curve and archive most if not all of what you need to accomplish.
Who is it recommended for?
The Netcat system is at its best when it is used for manual asset discovery and system exploration. This utility runs at the command line, which makes it a little difficult to use but it is a powerful research tool. It can also be used as an attack tool to set up a backdoor on a device.
Pros:
- Cross-Platform Availability: Available for various operating systems like Windows, Linux, and Unix, ensuring compatibility across different environments.
- Lightweight and Portable: Being a small program often pre-installed on Linux distributions, Netcat doesn’t require complex setup.
- Multifunctional: Netcat’s versatility extends beyond scanning, making it a valuable tool for network communication tasks like file transfers and creating simple network servers.
- Customization Options: Command-line flags allow you to tailor scans by specifying target ports, protocols (TCP, UDP), and output formatting
- File Transfer Support: Supports file transfer between host and client, providing additional functionality beyond standard network scanning.
Cons:
- Limited Information Gathering: Provides basic open port information but doesn’t offer deeper insights into specific services or applications running on those ports.
- Complexity for Simple Tasks: Netcat’s versatility and powerful features can make it overly complicated for users seeking a simple IP scanning tool without the need for advanced network manipulation.
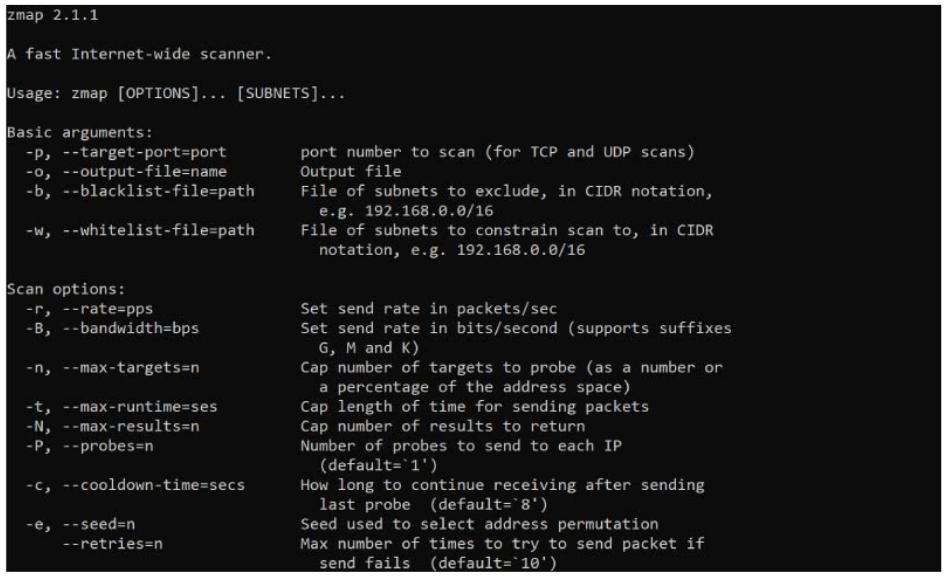
4. ZMap
ZMap was built by researchers out of the University Of Michigan to be a faster, more updated version of Nmap. The ZMap tool is a part of about a dozen different open source networking tools that are free for download and works in Linux and macOS environments.
Key Features:
- Extremely Fast Network Scanning: Designed for rapid scanning of large networks, making it efficient for gathering information about a large number of hosts.
- Security Focus: Built with a focus on security research and penetration testing, providing advanced scanning capabilities for security professionals.
- Lightweight Design: Features a lightweight and streamlined design, avoiding unnecessary scanning features or add-ons to optimize performance and resource usage.
- Open Source: Completely open-source software, allowing users to access and modify the codebase according to their needs.
Why do we recommend it?
Zmap is a network scanner, which makes it similar to Angry IP Scanner. However, it has more in common with Nmap and, in fact, it was written to provide an improvement on the Nmap service. This is a command line tool and its functions are controlled by the options appended to the command.
ZMap, just like Nmap and other network scanners can search for connected devices, probe ports, and discover services both in local and external networks. One of the biggest distinctions between the two tools is how they scan. Nmap was built to be a flexible multi-tool that can probe a large number of ports on a smaller number of devices. Where ZMap is optimized to probe an individual port across a vast amount of scanned devices.
This level of scanning speed and efficiency will prove to be even more valuable as more devices begin to use IPv6, which has a significantly larger address space. The developers have even claimed that it can scan the entire IPv4 address space in under 45 minutes on a 10gigE connection.
Who is it recommended for?
This is not a tool for casual use or for easy access because of the difficulty for occasional users to remember the finer points of the options for the command. So, network managers are less likely to use this tool than Angry IP Scanner. This is a substitute for Nmap for use by penetration testers.
Pros:
- Similarity to Nmap: Shares similarities in syntax and backend with Nmap, making it familiar to users already accustomed to Nmap’s functionality.
- Updated Alternative: Provides a modern and updated alternative to Nmap, particularly for users on Mac and Linux operating systems.
- Low Resource Usage: Being lightweight, ZMap consumes minimal system resources during scanning operations, ensuring efficient performance.
- Open Source Nature: Being open source, ZMap encourages community contributions, bug fixes, and customization to suit specific use cases.
Cons:
- Complexity for Basic Tasks: ZMap’s advanced capabilities and focus on security may make it overly complex for users seeking simple IP address discovery or basic network scanning tasks without the need for advanced features.
- Limited Platform Support: Primarily designed for Linux environments, and porting it to other operating systems might require additional effort.
While most network administrators won’t need this level of scanning speed and breadth, ZMap is still a great (and free) piece of software to have in your bag of tools.
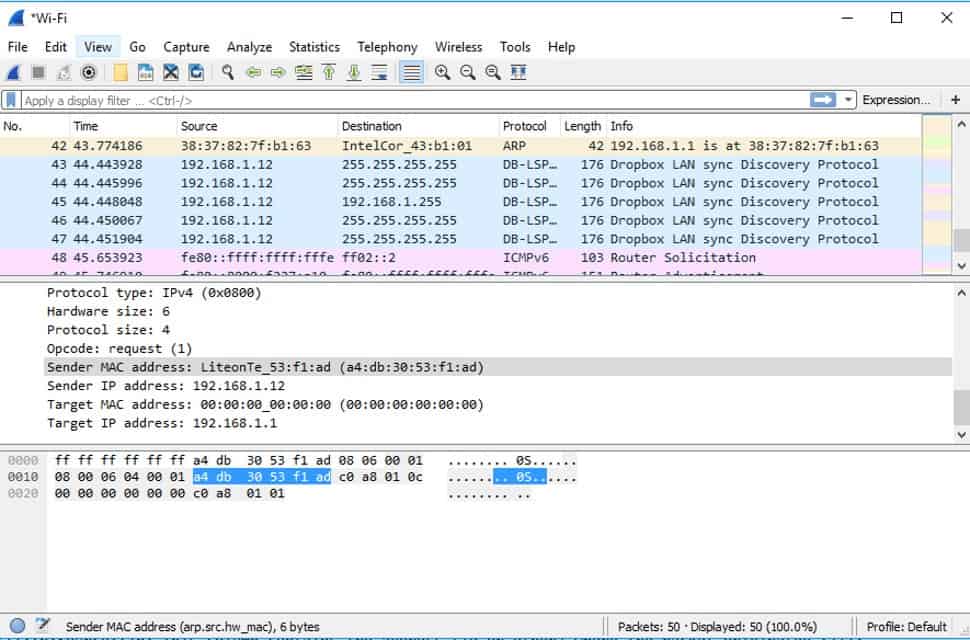
5. Wireshark
Wireshark is one of the most popular open-source network traffic analyzers and is used by millions of technicians across the world. Wireshark can be used to identify network problems such as broadcast storms, or even run as a security audit tool to help identify bad or malicious traffic.
Key Features:
- Captures, Displays, and Stores Packets: Capture, display, and store network packets, providing detailed insights into network traffic and protocols.
- Real-Time Packet Analysis: Allows for the real-time analysis of network packets, providing insights into network traffic and behavior.
- Filter and Search Feature: Includes an easy-to-use filtering and searching mechanism to focus on specific packets or protocols.
- Data Export: Enables exporting captured data to various formats such as XML, PostScript, or plain text for further analysis or reporting.
- Color-Coded Rules: Utilizes a color-coded rule feature for more intuitive analysis, helping users identify patterns and anomalies.
Why do we recommend it?
Wireshark is a different type of tool from a scanner because it captures traffic. It is a packet analyzer rather than a port scanner or IP address checker. Like many of the other tools on this list, Wireshark has its own language. However, in this case, that language is used for searching and filtering packets.
The beauty in Wireshark is that your network scans can be as broad or as granular as you make them. With a few clicks, you can begin capturing a snapshot of all packet traffic across your local area network. It can be overwhelming at first to see every single packet across a network, but Wireshark makes isolating specific events simple with its color coding and filtering features.
If you’re going over a capture packet file, you can slowly start to hide network traffic you know is legitimate until you’re left with data that still needs an explanation. For instance, In the filter bar at the top, you can enter not(tcp.port==80) which will hide any TCP traffic going over port 80 from your capture results. You can continue adding to this string of filters until you’re left with network traffic that needs deeper inspection. You can also save these filters to make future inspections quicker.
Who is it recommended for?
Wireshark is a free tool and it provides very detailed information about traffic because it shows you the actual packets traveling on the network. A busy network manager would probably use a packaged traffic analyzer with graphs rather than this packet-searching tool. This is a research utility for deep analysis.
Pros:
- Massive Open-Source Community: Benefits from a large open-source community that regularly updates the software and introduces new features.
- Professional Grade: Designed by network professionals for network professionals, ensuring comprehensive packet analysis capabilities.
- Packet Data Saving: Allows users to save captured packet data for later analysis, troubleshooting, or archival purposes.
- Active Open-Source Community: Wireshark benefits from a large open-source community that keeps the software updated and introduces new features periodically.
Cons:
- Complexity: Not user-friendly for non-technical users, with a steep learning curve even for IT professionals unfamiliar with packet analysis tools.
- Data Overload: Pulls all data over the network unless filtered, potentially overwhelming users with excessive information unless specific filters are applied.
While tools like AngryIP are more geared toward device discovery, Wireshark was built to analyze individual packets, so you can identify misconfigurations and security problems on your local network. You can download Wireshark for free and it’s compatible with Windows, macOS, and Linux operating systems.
Related posts:
6. Invicti
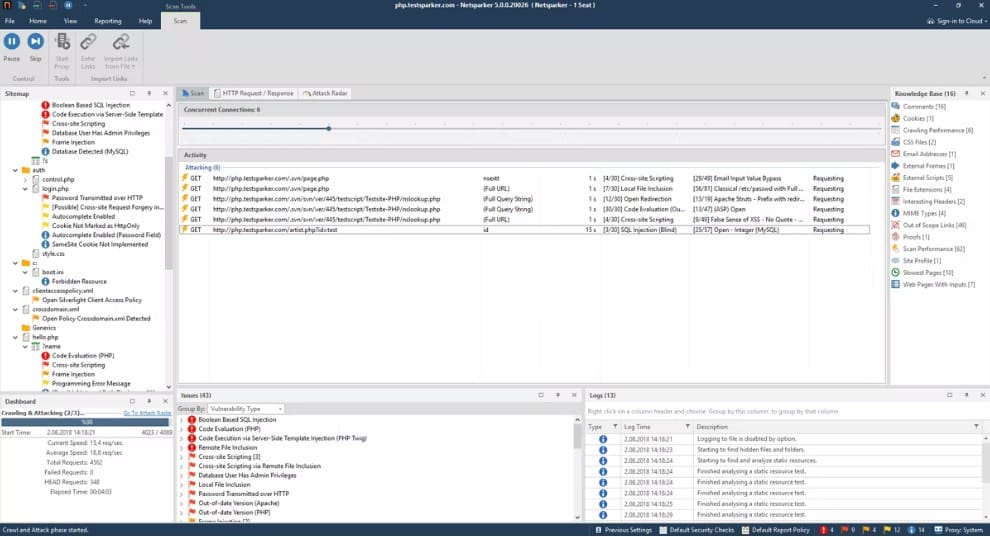
Invicti doesn’t operate on networks and it doesn’t scan for IP addresses, so at first glance, this isn’t a good match for the functionality of Angry IP Scanner. However, we have included the Invicti system here for those businesses that have moved on from the network-based world that Angry IP Scanner used to work well for. One of the reasons that Angry IP Scanner is out of date and needs to be replaced is that so many businesses now use cloud resources.
Key Features:
- Extensive Vulnerability Coverage: Covers a wide range of web application vulnerabilities, including OWASP Top 10, CWE Top 25, and zero-day vulnerabilities.
- CI/CD Pipeline Testing: Integrates seamlessly into Continuous Integration/Continuous Deployment (CI/CD) pipelines for automated security testing.
- Integration with SDLC: Can be integrated into your Software Development Lifecycle (SDLC) to enable security testing throughout the development process, promoting “shift left” security practices.
- Issue Tracker Reporting: Reports scan results directly to issue trackers and ticketing systems for efficient vulnerability management and remediation.
- DAST, SAST, and IAST: Provides Dynamic Application Security Testing (DAST), Static Application Security Testing (SAST), and Interactive Application Security Testing (IAST) capabilities for comprehensive security assessment.
Why do we recommend it?
Invicti is an ideal tool for scanning web applications and providing security for IT assets. The tool is very sophisticated and has a number of uses. For example, it can be used by developers to check on the validity and security of APIs and services that will be plugged into a new application under development.
An exciting improvement that Invicti offers over Angy IP Scanner is that it can be used for application development testing. The Invicti system practices dynamic application security testing (DAST), which runs code and analyzes the results. It also has a SAST service. This is a static application security testing service, which scans through code for known security errors. Combining both of these systems provides an interactive application security testing tool, (IAST).
Like most vulnerability scanners, Invicti looks for a series of well-known security mistakes. However, this system also applies AI processes to examine code and see where combinations of packages could create weaknesses. This field includes scenarios where a unit by itself is secure but the way it passes data or control instructions to other modules creates vulnerabilities. This means that the Invicti system goes above and beyond the functionality offered by other web asset vulnerability scanners.
Invicti can be set up to scan continuously. This means that it will spot when supporting modules to your user-facing systems change and introduce new weaknesses. Launch automation is also necessary for CI/CD pipeline testing, which can be set up as part of a workflow.
Who is it recommended for?
Invicti provides the best service for DevOps teams. This is because the scanning services of this tool can be deployed to test components that feed into new applications, can test completed applications before releasing them, and to provide ongoing security testing for Web applications once they are in operation.
Pros:
- Alerts for IT Operations: Notifies IT operations technicians about web asset vulnerabilities, allowing for proactive threat mitigation.
- Vulnerability Detection: The dynamic scanning approach helps identify a broad spectrum of vulnerabilities, reducing the risk of exploitable weaknesses in your web applications.
- Reduced False Positives: Proof-based scanning minimizes the need for manual verification of findings, saving time and resources.
- Security Testing: Offers a range of security testing methods (DAST, SAST, IAST) to cover different aspects of application security.
- Actionable Reporting: Detailed reports with clear remediation guidance empower developers to address security issues effectively.
Cons:
- Limited Comparison: Not a direct competitor to Angry IP Scanner, which is primarily a network scanner, whereas Invicti focuses on web application security testing.
- No Free Trial: Lacks a free trial option, which may limit the ability of users to evaluate the platform before making a purchase decision.
Invicti doesn’t publish a price list for its services. So you need to contact the Sales Department to get a quote. This is a cloud platform but you can elect to download the code and host it yourself – it runs on Windows Server.
7. Acunetix
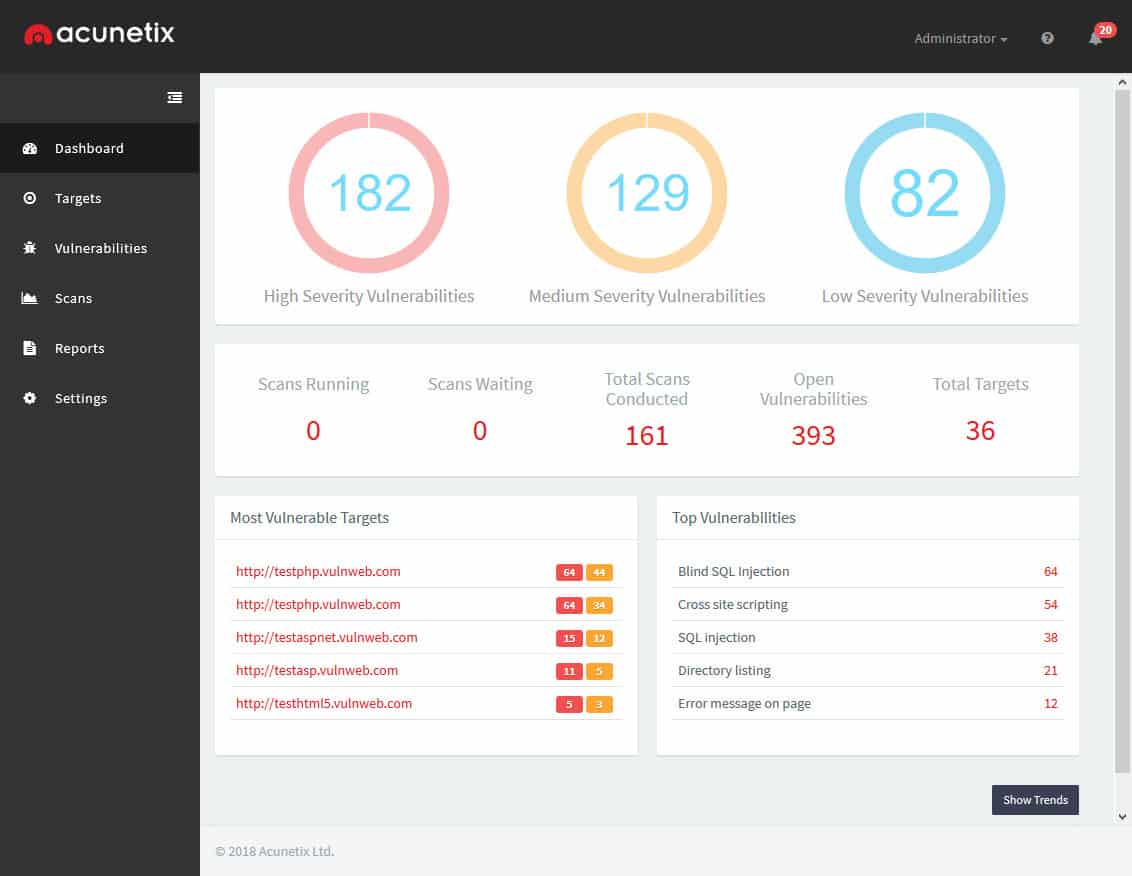
Acunetix is a powerful network and web application scanner that can help you discover open ports, hidden services, and vulnerabilities across your network. Acunetix is unique in combining both web scanning, and network scanning into one easy to use graphical tool that’s compatible for both Windows and Linux.
Key Features:
- Web Application Security Scanning: Excels at identifying vulnerabilities like SQL injection, cross-site scripting (XSS), and broken authentication through a combination of static and dynamic analysis.
- Network Scanning: Conducts in-depth network scanning to identify security weaknesses and potential threats across the network infrastructure.
- AcuSensor Technology: This technology analyzes web application behavior, allowing Acunetix to identify vulnerabilities within the application logic and crawl behind login forms to access deeper content.
- Misconfiguration Detection: Can detect and alert administrators when misconfigurations or security gaps are identified, enabling proactive risk management.
- Reporting and Remediation: Acunetix generates detailed reports with vulnerability descriptions, potential impact, and remediation guidance.
Why do we recommend it?
Acunetix is a similar tool to Invicti, except that it adds on network vulnerability scanning. The network scanner in this package is actually the addition of the well-known OpenVAS system. This package can be used to secure applications and networks by revealing security errors.
The web scanning tool allows you to scan your website for any exposed ports, vulnerable services, or information leaks that could give attackers information to use against you. Even though you’re working in a GUI, you don’t feel at all limited in what you can scan for or filter out.
The network scanning component of Acunetix can integrate with OpenVAS, an open-source Linux based scanner. When combined, these two scanners work together in tandem and create a network security assessment tool that provides auditing, and an action plan for remediation.
Who is it recommended for?
Acunetix can be used as a vulnerability manager as well as a web application security tester. This is a complex system that is probably not suitable for small businesses and enterprises that produce and manage web applications will benefit the most from the package. Runs on Windows and Linux.
Pros:
- Ease of Use: Balances powerful scanning capabilities with user-friendly features, making it accessible to both experienced security professionals and beginners.
- Combined Functionality: While not a full-fledged network scanner, Acunetix offers basic network scanning capabilities alongside its web application security features, potentially reducing the need for separate tools.
- Application Security Focus: Designed specifically for application security, ensuring thorough scanning and detection of vulnerabilities within web applications.
- Integration Capabilities: Integrates with numerous other tools such as OpenVAS, allowing for enhanced security analysis and remediation.
- Trusted by Organizations: Used by reputable organizations like NASA, demonstrating its reliability and effectiveness in the cybersecurity landscape.
Cons:
- Lack of Trial Version: Only offers a demo version instead of a full trial, which may limit users’ ability to fully evaluate the platform before making a purchase decision.
- Cost: Acunetix is a commercial tool, and its pricing structure might not be ideal for all budgets.
For the most up-to-date pricing, you’ll have to schedule a demo with Acunetix. Our research estimates that the professional version costs about $415.00 (£335.15) per month for the web vulnerability scanner.
8. GFI LanGuard
GFI LanGuard is a network security scanner that can discover any device on your network, as well as perform a complete network security assessment to let you know how vulnerable your network is to specific types of attacks. It’s the interface is easy to navigate like AngryIP, and provides deep insight into security issues, vulnerabilities, and missing patches your connected devices may need.
Key Features:
- Agent and Agentless Scanning: Offers both agent-based and agentless scanning options.
- Network Discovery and Scanning: Automatically discovers devices on your network, including computers, laptops, servers, mobile devices, printers, and network equipment.
- Automated Reporting and Alerts: Generates reports on network security vulnerabilities, missing patches, and device inventory.
- Vulnerability Detection: Detects vulnerabilities across multiple platforms such as Microsoft, Linux, and Mac, helping organizations identify and prioritize security risks.
- Remediation Recommendations: Offers remediation recommendations based on detected vulnerabilities, guiding security teams in addressing identified issues.
- Third-Party Application Patching: Supports patching for popular third-party applications like Adobe, Java, and Runtime, enhancing overall security posture.
Why do we recommend it?
GFI LanGuard is not a free tool like Angry IP Scanner but it is a much more complex service and it is worth paying for. This is a vulnerability scanner and patch manager, so it doesn’t compete directly with IP scanners. It is a security package that provides facilities to fix discovered weaknesses.
Once GFI LanGuard has discovered devices on your network you can manage them by deploying remote agentless scans, or installed agents. These agents will provide you with more details such as what programs are installed, open ports and their services, critical vulnerabilities, and system information.
On a separate tab, GFI Languard will recommend action to resolve security issues it found during its discovery process. You can also produce reports in just a few clicks, and have them automatically emailed to you on a regular basis. This is especially useful for HIPAA and PCI DSS compliance audits.
Who is it recommended for?
GFI LanGuard is priced per node with the minimum package being for 10 devices. Thus, the system is affordable for small businesses, particularly as the rate per node per yeast is reasonable. There is no upper limit on the size of network the GFI LanGuard can scan.
Pros:
- Multi-Platform Support: Supports multiple platforms including Microsoft, Linux, and Mac, catering to diverse IT environments.
- All-in-One Solution: Combines network scanning, vulnerability assessment, and patch management into a single tool, streamlining your security management.
- Easy to Use: Offers a user-friendly interface that simplifies network security tasks even for users without extensive technical expertise.
- Scalability: Can scale to accommodate small and large networks.
- Automated Patch Management: Automates patch deployment, saving you time and ensuring your systems are kept up-to-date with the latest security fixes.
- Reporting and Alerts: Provides valuable insights into your network security posture with reports and alerts, allowing you to proactively address potential issues.
Cons:
- False Positives: Like many scanners, GFI LanGuard might generate some false positives, requiring manual verification of reported issues.
- Limited Free Version: The free version of GFI LanGuard offers basic features but lacks key functionalities like automated patch deployment and advanced reporting options.
GFI LanGuard is compatible in all modern Windows environments and starts at just $26.00 (£20.96) per node, per month. If you think LanGuard might be right for your network, you can start a free 30-day trial.
9. SoftPerfect Network Scanner
SoftPerfect Network Scanner is much like AngryIP with some additional options if you’re looking for a scanner with a bit more functionality. Both products are very similar, but upon testing I found AngryIP to perform faster than SoftPerfect Network Scanner. With that being said, SoftPerfect’s scanner did have some nicer quality of life features that make it worth keeping around.
Key Features:
- Extensive Network Discovery: Automatically discovers devices on your network, including computers, laptops, servers, mobile devices, and network equipment.
- Multi-Threaded Scanning: Utilizes multiple threads to expedite network discovery and information gathering, making scans faster.
- Port Scanning and Service Identification: It scans for open ports on discovered devices and attempts to identify the services running on those ports.
- Remote Commands and Scripting: Advanced users can execute remote commands (SSH, PowerShell, VBScript) on discovered devices for further exploration or management tasks.
- Remote System Information Retrieval: It retrieves various system information from discovered devices, including logged-in users, configured user accounts, uptime, and software versions.
Why do we recommend it?
SoftPerfect Network Scanner is very similar to Angry IP Scanner. This system has an easy-to-use GUI interface and it installs on Windows and macOS. The big difference between these two scanners is that the full SoftPerfect tool is not free to use. You can use it for free to scan 10 devices at a time.
The interface is simple to use and just like AngryIP you start by specifying a range on your network to start scanning from. For larger networks, features like remote registry and the ability to filter scanned IP addresses will be useful, especially for larger environments. Since the features are so basic I feel that SoftPerfect Network Scanner is more geared towards larger home networks and enthusiasts.
Under the Actions tab, you can find quick and helpful commands you can run such as finding duplicate IP addresses, scanning for DHCP servers, or even creating a batch script on the fly.
Who is it recommended for?
The limit on the capacity of the free edition of SoftPerfect Network Scanner makes it less appealing than Angry IP Scanner. If you are scanning a network because you don’t know anything about it, one of the things you hope to discover is how many devices there are.
Pros:
- User-Friendly Interface: Easy to navigate interface, making it suitable for users of all technical skill levels.
- Wide Range of Features: Goes beyond basic network discovery by offering port scanning, service identification, shared folder discovery, and remote system information retrieval.
- Flexibility: Provides various scanning options and customization possibilities, allowing you to tailor scans to your specific needs.
- Lightweight and Portable: A small program that doesn’t require complex setup. A portable version is available, making it convenient to use on different machines.
- Cost-Effective: A free version with a good range of features is available, with paid options unlocking advanced functionalities like remote shutdown and Wake-on-LAN.
Cons:
- Limited Free Version: The free version of SoftPerfect Network Scanner is fairly limited in terms of features and functionality compared to paid versions.
- Security Concerns with Remote Commands: Executing remote commands on discovered devices carries potential security risks, especially on networks with strict security requirements. Caution and proper authorization are crucial.
SoftPerfect Network Scanner is compatible in modern Windows environments and is free to use in a limited capacity. Licensing is unlimited and starts at $29.00 (£23.38) for home users and $49.00 (£39.50) for businesses.
Conclusion
While AngryIP Scanner might be a household name, there are plenty of alternatives when it comes to discovering devices on your network or auditing your network’s security. For a small to mediums sized business, We recommend SolarWinds PortScanner for its intuitive features, ability to discover and manage devices in a business environment.
For security testing, it’s hard to beat Nmap. Nmap has continued to be a staple in cybersecurity for good reason. It’s flexibility and no-frills approach to device security make it my personal favorite tool when testing the security of my local network connections.
And lastly, if you’re looking for a security-focused network scanner that has more “done for you” scanning features built-in, GFI LanGuard is a solid option. LanGuard provides network discovery, vulnerability scanning, and remediation in a single dashboard.
Angry IP Scanner FAQs
Is Angry IP Scanner legal?
Angry IP Scanner is a legal tool. It is frequently used by both black hat hackers and white hat hackers because it helps to probe weaknesses in a network device. However, many network utilities can be used for good or evil and that doesn’t make them illegal. For example, Ping can be used by hackers but it doesn’t break the law.
How do I ping an IP range?
Create a Ping loop to scan a segment of your network. This can be written with a DOS FOR command. For example:
for /l %i in (1,1254) do @ping 192.168.1.%i -n 1 -w 100 | find "Reply”
If you want to scan a range that isn’t just a sequence through the last octet of an IP address, then the programming requirements get a lot more complicated. In that case, you would be better off just using the Angry IP Scanner or one of the other tools explained in this article.
Is Angry IP Scanner safe?
Angry IP Scanner is safe to use. The utility is just a monitor and doesn’t have the power to make any changes to your device settings. The information that the service returns is simply a list of IP addresses that are in use, with any gaps in a range implying IP addresses that are unused.














Thanks for compiling this detailed list of good alternatives. I am now trying Wireshark and also trialling Softperfect. Unfortunately Softperfect is not free, but it seems pretty good. So I might splurge on a locense after all.